#original: mitm
Text
Kakashi: Why is Naruto in a box?!
Sakura: He thinks he's being delivered to another country.
Kakashi: What?! Can he breath in there?!
Sasuke: He's still making noises.
Kakashi: ... and he has water and food?
Sakura: Yeah.
Kakashi:
Kakashi: Alright, then.
#naruto#naruto uzumaki#sasuke#sasuke uchiha#kakashi sensei#kakashi#kakashi hatake#team 7 naruto#team 7#team seven#team kakashi#naruto incorrect quotes#incorrect naruto quotes#incorrect team 7#incorrect team seven#sakura#sakura haruno#original: mitm
509 notes
·
View notes
Text

Monster in the Mountain, an Undertale fanfic (18+)
Chapter 18: Anywhere and Anything
Summary: The vacationing couple continues traveling the world, having endless fun until Frisk slowly grows sad and Asriel finds a risky way to make them happy again.
Chapter 17 / Chapter 19
#friskiel#frisk/asriel#Frisk x God of Hyperdeath#adult!frisk#adult!asriel#undertale fanfiction#Fanfic Monster in the Mountain#so I originally posted these MitM chapter covers on tumblr in April 2023#I got up to chapter 17 and then depression/anxiety overtook me and I completely forgot???#then in July 2023 I came back and decided to reblog my Growing Pains stuff instead#it's clear I have favoritism issues#I have treated MitM so poorly#BUT I'M BACK NOW!!#UNFORTUNATELY NOBODY IS WATCHING
2 notes
·
View notes
Text
Tagged by @fezwearingjellybananas! thank you!
1. How many works do you have on AO3?
117 (115 of which are solo authored)
2. What’s your total AO3 word count?
810,361 (717,002 of which are solo authored, and more than a quarter of that is just mitm 😂)
3. What fandoms do you write for?
Whatever catches my attention long enough to give me a fic idea that I finish writing, honestly! I'm fully of the 'scroll twice to get to the end of my fandoms list' writer. But for specifics I'll try to just stick to the past two years, where I've collaborated on fic for USS Interpreter - a cast of original Star Trek ttrpg characters, the Spider Gwen comics (and Squirrel Girl comics), Star Trek Strange New Worlds (and Discovery, and a bit of TOS), Spider Man 2017, Raimi Spider Man, The Flash, IDW Transformers, The Untamed by way of Murderbot fusion/crossover, and Arcane
4. What are your top five fics by kudos?
Does It Hurt? - MCU CACW fix-it fic, with Tony and Bucky, and tonyrhodey
Don't Miss It - Ford and Mabel Gravity Falls Weirdmaggedon fic, optimistic speculation at the time
Meet in the Middle - My very, very, veeery long-ongoing driftrod fic
More than This - Aro (and ace) Obi-Wan
What You (Don't) Need to Hear - Aro Stanford and Dipper Pines
I do love that 2/5 of these are aro-centric fic
5. Do you respond to comments? Why or why not?
Yes! I love comments and I enjoy replying, and from talking to regular readers I think it helps encourage folks to comment. It's never something I expect from when I comment on other's fics, I just want to share my appreciation, but I always am happy to get replies myself.
6. What’s the fic you wrote with the angstiest ending?
Restraining myself to the past two years for specifics, I think You're Just A Little Boy, my transmasc La'an fic, has the most outright Unhappy Ending - at least for this fic, I might write a more hopeful follow up. I'll throw in when you're gone we won't say a word (but you know that's okay), my alternate future Pike fic, goes in for the most bittersweet, and I've definitely cried the most over it
7. What’s the fic you wrote with the happiest ending?
I write a lot of happy endings, but they're often threaded with a bit of angst or bittersweetness. Fungus Not-Amongus is altogether pretty delightful fluff for Tilly and Pike, though.
8. Do you get hate on your fic?
I have once or twice, but not for a good long while, I've been quite lucky
9. Do you write smut?
Not yet! Got a project or two down the pipe that might have some, but it's not something I typically write
10. Do you write crossovers?
Yes! All the time. In the past couple years, I've written Ghosts in Your Head, Ghosts in My Head, The Flash fic in a Pacific Rim setting, more of a fusion setting, but I'll count it. Intersections, with Spider Gwen & Squirrel Girl, which are technically both Marvel Comics, but I'll count them as a crossover event in the comics spirit. Artificial Survivor is more of a Untamed fic in a Murderbot fusion setting, but the Murderbot characters are technically alluded to, so I'll count that too. Plus there's the Star Trek/Star Wars crossover with Star Trek OC's I'm helping out on. Generally you can find a lot of crossovers I've written, I find them really fun.
11. Have you ever had a fic stolen?
Not to my knowledge
12. Have you ever had a fic translated?
Yes! A reader asked to translate a tonyrhodey fic a few years back
13. Have you ever co-written a fic?
Given that I specified solo-authored fics above, you can probably guess the answer to that is yes! 😁 I'm co-writing fic about ttrpg Star Trek characters - I play & write Chief Engineer Piper Hawthorne. @severeannoyance is our captain and @plokoonsdisapprovingeyebrows is our Star Wars expert for our Star Wars crossover fic.
14. What‘s your all-time favourite ship?
Given that MITM is 1/4 of my solo wordcount, and I have updated it in the past two years, it's probably gotta be driftrod, at least for this ask. ask me next week, you might get a different answer 😂
15. What’s the WIP you want to finish but doubt you ever will?
I have a West Wing / X-Men 2 crossover that's been sitting in docs for many many years. I might release some of the finished scenes at some point, like I did with E2bard, because there's lots of good stuff and I always have fun with the West Wing character voices
16. What’s your writing strengths?
Dialogue, introspection, and replicating particularly strong character and narrative voices
17. What’s your writing weaknesses?
I tend to repeat phrases and overuse dashes, and don't expect much setting description XD
18. Thoughts on writing dialogue in another language for a fic?
I usually just indicate that something's in another language and keep it in the same language as the rest of the fic - English for me, I'm currently pretty monolingual, but I think other options are perfectly workable for other authors.
Not actually related to the question, but I've gotten comments in other languages or with phrases in other languages, and I always find them an especially high compliment - that my fic was not only worth reading in a language that wasn't someone's first, but that they also put in the time to leave a comment. I usually have to use a bit of google translate and ask my bilingual friends for help translating (thank you), but all the comments have been very nice.
19. First fandom you wrote for?
I think I wrote what was Star Wars fanfic for vocab assignments back in middle school, though I didn't know that was what it was called. My first published fic was for Bleach.
20. Favourite fic you’ve ever written?
Sticking in the past two years, Ghosts in Your Head, Ghosts in My Head is one I'm really proud of. And of course I have to mention Meet in the Middle, something I've stuck with for more than five years at this point.
tagging @severeannoyance and @plokoonsdisapprovingeyebrows plus @philcoulsonismyhero and @vetoing-clocks if yall want! Plus a blanket tag for anyone who wants to!
3 notes
·
View notes
Text
the thing about a mitm reboot is if they made reese gay it would retroactively make the original series make more sense.
#TO ME#malcolm in the middle#talk tag#episode one of the reboot they do a flashback montage to clips from the original series and at the end youre like huh well okay#i guess he was!
11 notes
·
View notes
Text
DNSSEC: Peace of Mind for Your Online Safety
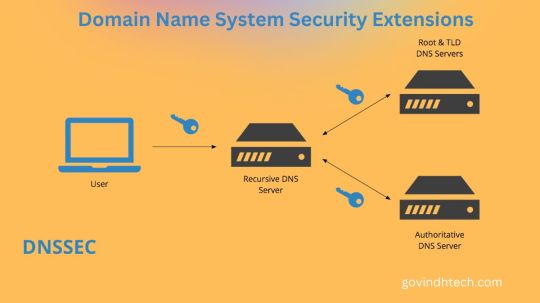
What is DNSSEC?
A feature of the Domain Name System (DNS) that verifies answers to domain name lookups is called Domain Name System Security Extensions (DNSSEC). Although it keeps attackers from tampering with or contaminating DNS query responses, it does not offer privacy protections for those lookups.
Not really. DNSSEC uses a different method than encryption public key cryptography to defend networks from man-in-the-middle attacks. Put differently, Domain Name System Security Extensions offers an authentication method but not a confidentiality method.
DNSSEC: Internet Foundation Protection
Domain Name System (DNS) converts human-readable domain names into machine-readable IP addresses for online security in the digital age. Security issues make traditional DNS vulnerable to manipulation and attacks. DNSSEC safeguards DNS data.
Major Advantages of DNSSEC:
DNSSEC uses public-key cryptography and digital signatures to verify DNS responses. This means a domain name’s IP address is authentic and hasn’t been changed from the authorized source.
Data Integrity: Phishing attempts and malicious website redirects can result from DNS data manipulation. DNSSEC prevents hackers from altering vital DNS records by cryptographically verifying them.
Middleman (MitM) Attack Prevention: DNSSEC guarantees authenticity and data integrity, reducing the risk of MitM attacks, in which attackers intercept and alter DNS responses to trick users.
Domain Name System Security Extensions protects DNS lookups from malicious and tampering, giving users and organizations confidence to use online services.
Is DNSSEC important?
Public/Private Key Pairs: Public keys are published in the DNS by domain owners, while private keys are kept confidential.
Digital Signatures: By digitally signing DNS records with the private key, a “fingerprint” that confirms their legitimacy is created.
Signature Validation: To make sure received DNS records haven’t been tampered with, resolvers the programs that convert domain names into IP addresses verify the signatures using the public key that has been released.
Chain of Trust: Signatures are verified through a chain of trust that originates from the root of trust that is present at the top of the DNS hierarchy.
How to implement DNSSEC
Adoption: DNSSEC is being implemented more often, despite not being widely used. It is supported by a large number of prominent domain registries and registrars, and it is frequently free for organizations to enable.
Benefits Exceed Difficulties: Although DNSSEC setup and configuration may call for some technical know-how, the advantages greatly exceed the drawbacks. Organizations that are concerned about security ought to give it serious consideration for their domains.
What distinguishes public key cryptography from encryption?
DNS queries are digitally “signed,” or authenticated, using public key cryptography by DNSSEC. The receiving device can compare the data it receives with the original data sent by the authoritative server when DNSSEC is enabled on a zone record. A digital signature that authenticates data using public keys makes this possible.
The data in DNSSEC is not encrypted; instead, the authentication keys are secured through cryptography. Traffic protected by Domain Name System Security Extensions can still be intercepted and read. The receiving server will be able to detect that something is wrong if the data is altered somewhere along the data pathway and sent on to its destination because the public keys will not match.
On the other hand, encryption encrypts the data by using cryptography. By altering what an attacker would see if they were to intercept a query somewhere along the data pathway, encryption ensures confidentiality. Until the attacker uses an encryption key to decipher the signal, it renders the data unintelligible. Data is shielded from manipulation by encryption because the key isn’t disclosed to the public.
What is DNSSEC in cybersecurity?
Among the Internet’s more traditional protocols is DNS. The Internet was much smaller when it was first developed, and almost everyone there was acquainted. Data Security was not given much thought.
DNS was used so extensively by then that any major alteration would have brought down the entire system, even before the issue of Internet security arose. Instead of attempting to create a completely encrypted protocol to take the place of DNS, an authentication mechanism was added to the pre-existing system.
DNSSEC was vulnerable. By enabling the authentication of queries and data, it improved protocol security. However, it did so without altering the underlying architecture, allowing the Internet to expand further without requiring any new engineering. Domain Name System Security Extensions deployment was left optional so that organizations could make the switch whenever they felt ready.
If DNSSEC isn’t encrypted, why use it?
One major reason to use DNSSEC is to prevent DNS cache poisoning, also called DNS spoofing. A DNS spoofing attack involves replacing a legitimate DNS query response with an unauthenticated one. After that, the response becomes stuck in the cache, returning the incorrect response and sending users to malicious websites until the “time to live” runs out.
By authenticating DNS responses and guaranteeing that only accurate responses are returned, DNSSEC defends against these types of attacks. DNS spoofing attacks cannot be prevented by encryption, but it may safeguard the underlying data in a DNS connection.
Is DNSSEC still used if it isn’t encrypted?
Sadly, DNSSEC is only used to validate about 20% of Internet traffic. Even though it’s a big improvement over a few years ago, that amount is still far below what it ought to be. That substantial gap can be attributed to a combination of informational gaps, laziness, and usability issues.
By offering a straightforward deployment procedure, NS1 encourages all of its clients to implement DNSSEC. Through IBM’s Dedicated DNS offering- NS1 even offers Domain Name System Security Extensions as a backup provider or redundant DNS option, in contrast to other providers.
Gazing Forward
Security continues to be the primary concern as the internet develops. One of the most important steps toward a more secure DNS ecosystem is Domain Name System Security Extensions. It encourages trust and confidence in online interactions by defending against critical vulnerabilities, protecting users and organizations from malicious activities.
Read more on Govindhtech.com
#technology#govindhtech#technews#news#dns#Domain Name System Security Extensions#ns1#cryptography#DNSSEC
0 notes
Text
Exploring Common Cryptographic Attacks
Cryptographic attacks pose a significant threat to the security of encrypted data and the underlying cryptographic systems. Understanding the most common types of cryptographic attacks is crucial in order to develop effective defense mechanisms. We will delve into several prevalent cryptographic attack techniques and their implications.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the best ethical hacking course in Coimbatore becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

Brute-Force Attacks:
One of the well-known types of cryptographic attacks is brute-force attacks. These attacks involve exhaustively trying every possible combination of keys or passwords until the correct one is found. Although time-consuming, brute-force attacks can compromise weak or poorly implemented encryption algorithms.
Known-Plaintext Attacks:
Known-plaintext attacks exploit scenarios where an attacker possesses both the encrypted data and its corresponding plaintext. By analyzing multiple pairs of known plaintext and ciphertext, attackers attempt to deduce the encryption key or extract other sensitive information.
Cipher Text-Only Attack:
A cipher text-only attack involves an attacker having access only to the encrypted data without any knowledge of the encryption algorithm or key. The goal is to deduce the original plaintext or obtain information about the encryption key.

If you want to learn more about this, I highly recommend Ethical Hacking course at online because they offer certifications and job placement opportunities. Experienced teachers can help you learn better.
Man-in-the-Middle (MITM) Attacks:
Man-in-the-Middle attacks intercept and manipulate the communication between two parties. In the realm of cryptography, this type of attack involves intercepting encrypted communication, decrypting it, and then re-encrypting it to forward it to the intended recipient. MITM attacks allow the attacker to eavesdrop on the communication or even modify the transmitted data.
Side-Channel Attacks:
Side-channel attacks exploit information leaked during the execution of cryptographic algorithms, such as timing information, power consumption, or electromagnetic radiation. By analyzing these side channels, attackers can extract sensitive information like encryption keys, bypassing the need for direct decryption.
Being aware of common cryptographic attacks is vital for both developers and users of cryptographic systems. By understanding the techniques employed by attackers, it becomes possible to implement robust security measures that can withstand these threats.
Staying informed about advancements in cryptography and adhering to best security practices are key to mitigating the risks posed by cryptographic attacks.
0 notes
Text
A Step-by-Step Guide on How to Scrape Data from Mobile Apps

A Step-by-Step Guide on How to Scrape Data from Mobile Apps
Oct 26, 2023
Introduction
In the dynamic landscape of mobile app development, extracting valuable data has become essential for informed decision-making and enhanced user experiences. This step-by-step guide aims to demystify the process of scraping data from mobile apps, providing a comprehensive roadmap for beginners and seasoned developers.
Understanding the Importance:
Mobile apps house valuable information, from user behavior and preferences to performance metrics. Extracting this data can offer crucial insights for app optimization, market analysis, and strategic decision-making. However, the intricacies of data scraping can be daunting, necessitating a systematic approach.
Key Considerations:
Before delving into the step-by-step process, it's essential to consider ethical and legal aspects. Respecting user privacy, adhering to app terms of service, and ensuring compliance with data protection regulations are paramount.
Step 1: Setting Objectives:
Define clear objectives for your data scraping endeavor. Whether it's analyzing user engagement, monitoring app performance, or competitive analysis, having well-defined goals guides the entire process.
Step 2: Choosing the Right Tools:
Selecting the appropriate tools is critical. From no-code solutions to programming languages like Python, the choice depends on your technical proficiency and project requirements.
This guide will systematically walk you through each process stage, offering insights into tools, techniques, and best practices to empower you in effectively scraping data from mobile apps. Whether you're a developer, analyst, or business professional, mastering this skill opens doors to a wealth of actionable information and data-driven success.
Understanding the origin of the data your app consumes involves monitoring network traffic, a process that Android complicates. Fortunately, the community has devised solutions. Discover how to combine tools for valuable insights seamlessly.
For Android, Google imposes certain obstacles to monitoring network traffic, but we can overcome them with community support. One effective solution is Mobile App Scraping, offering cross-platform traffic checking for Android apps and readily available code. Our tool, apk-mitm, is instrumental in modifying the network security profile information within your app's APK file, enabling you to observe the traffic flow.
Essential tools for this process include Android Developer Studio, apk-mitm, MITMProxy, and NodeJS. Contact Mobile App Scraping for guidance and code assistance to make the most of these resources.
By leveraging these tools, you gain valuable insights into your app's network interactions, facilitating a deeper understanding of data consumption. Follow our instructions to seamlessly navigate the network monitoring process and unlock the potential of your Android app data.
Initiating Your Android Virtual Device
Embarking on Android app development necessitates creating and initiating an Android Virtual Device (AVD). This foundational step is integral to testing and refining your applications before deployment. Follow this comprehensive guide to develop and start your Android Virtual Device seamlessly.
To commence, navigate to the AVD Manager within the Android Developer Studio's tools menu. This accessible interface streamlines the process, allowing users to craft an emulator tailored to their needs. The beauty of this step lies in its simplicity; no intricate settings are required. Regardless of experience, any user can select a phone model and Android version of their preference.

By mastering the initiation of Android Virtual Devices, you pave the way for robust app development. This guide empowers developers of all levels to navigate the AVD creation process effortlessly, facilitating efficient testing and refining of Android applications.
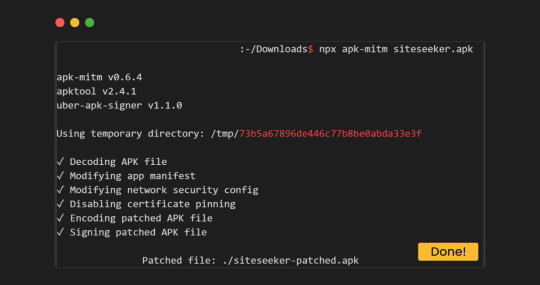
Obtaining And Analyzing APK Files With APK-MITM: Streamlining The Process For Emulator Testing
In the journey to run applications on your Android emulator, securing an APK file is the initial requirement. This pivotal step sets the stage for testing and evaluation on your virtual device. Once the APK file is in your possession, seamlessly integrate it into your emulator experience using the APK-MITM tool.
Acquiring APK files for testing is simplified through platforms like https://apkgk.com. Here, a diverse array of applications is available for download, catering to various testing scenarios on the emulator. Choose an app that aligns with your testing objectives and download it to your local machine.
The next phase involves the efficient utilization of APK-MITM. With a straightforward command, this tool becomes an invaluable asset in evaluating the APK file within the emulator environment. The seamless integration of APK-MITM ensures a smooth testing process, allowing you to gain insights into the app's performance, security, and functionality on the virtual device.
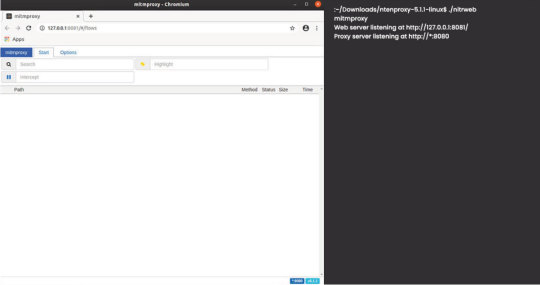
Configuring The Proxy For Seamless Emulator Testing: Optimal Setup Using Mitmweb On Ubuntu
Setting up a proxy for a refined testing environment on your Android emulator is paramount, and mitmweb emerges as the preferred choice among various mitmproxy tools. This step-by-step guide illustrates the process, mainly focusing on Ubuntu.
Initiating the proxy setup on Ubuntu entails downloading the necessary tools and executing a simple command. The tool of choice, mitmweb, offers a user-friendly web-based interface that enhances the overall experience of monitoring network traffic.
To commence, navigate to the download source for mitmproxy tools. Once acquired, execute the command "./mitmweb" in the terminal to launch the mitmweb interface. This action initializes the proxy server, making it ready to intercept and analyze network traffic between your emulator and the desired applications.
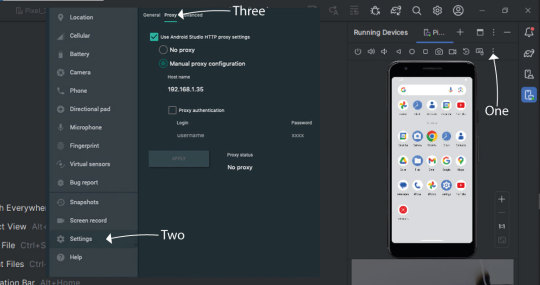
Configuring AVD For Proxy Usage: Enhancing Emulator Testing With Seamless Integration
Optimizing your Android Virtual Device (AVD) for proxy usage is crucial in refining emulator testing. This guide elucidates the process, ensuring seamless integration between your AVD and the proxy for effective network traffic monitoring.
Navigate to the advanced settings of your AVD and access the settings menu. Locate the proxy settings section within this interface and configure it according to the specifications below. Set the proxy address to 127.0.0.1 and choose an appropriate port number. Upon making these adjustments, click "Apply" to implement the changes.
To finalize the setup, reboot your AVD. After the reboot, initiate a long press on the power button to resume regular operation. This ensures that the AVD utilizes the configured proxy settings to intercept and analyze network traffic during testing.
Securing Emulator Communication: Installing Mitmproxy CA Certificate On Your AVD
Ensuring a secure channel for communication within your Android Virtual Device (AVD) involves the installation of the mitmproxy Certificate Authority (CA) certificate. This step-by-step guide elucidates the process of safeguarding your emulator environment.
Commence by launching the browser within your Android emulator and visit https://docs.mitmproxy.org/stable/. On the website, locate the Android symbol and click on it to initiate the download of the mitmproxy CA certificate.
Following the download, navigate to your AVD's Settings. Within the Security section, access Encryption & Credentials, then proceed to Install a Certificate and select CA Certificate.
Choose the downloaded mitmproxy certificate for installation. Confirm the installation to establish a secure connection between your AVD and the mitmproxy tool. Check if mitmproxy appears in your Trusted Credentials to verify the correct installation.
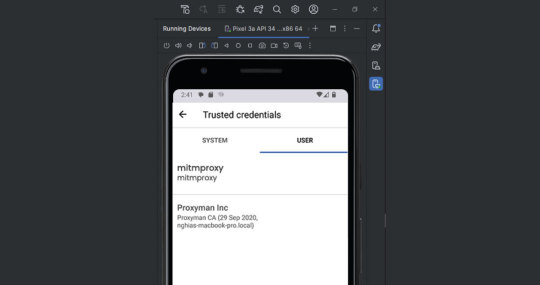
App Installation And Traffic Observation: Unveiling Insights With Mitmproxy
Completing the installation and observing network traffic is the culminating step in harnessing the power of mitmproxy for your Android emulator. This guide navigates you through the process, from app installation to unveiling the intricacies of network interactions.
Initiate the installation by dragging the file generated in step 2 onto the screen of your device emulator. This action triggers the installation process for the selected program. Upon successful installation, launch the application to commence traffic observations.
Open the mitmproxy screen to witness real-time insights into the network activities of the installed app. A dynamic traffic display, in this instance, fetching a JSON file from AWS S3, unfolds on the mitmproxy screen. This visualization empowers developers to scrutinize data exchanges, analyze requests and responses, and identify potential optimizations or concerns within the application's network interactions.
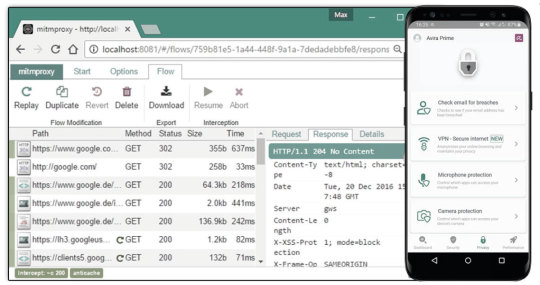
Conclusion: Mastering Mobile App Scraping For Informed Insights
Navigating the intricate landscape of mobile app data extraction has been demystified through this comprehensive step-by-step guide. From setting up your Android Virtual Device (AVD) to configuring proxies and analyzing network traffic, you've acquired the skills to scrape valuable insights from mobile apps.
As you conclude this guide, consider the transformative impact of Mobile Apps Scraping on your data-driven initiatives. Whether you're a developer seeking detailed analytics or a business professional aiming for competitive market insights, the ability to extract and analyze data from mobile apps is a game-changer.
Take the next step in optimizing your data extraction processes. Contact Mobile App Scraping to explore the vast opportunities this tool offers. Seamlessly integrate scraping into your projects, refine your strategies, and unlock the full potential of mobile app data for informed decision-making. Start your journey toward data-driven success today!
know more:
https://www.mobileappscraping.com/scrape-data-from-mobile-apps.php
#ScrapeDatafromMobileApps#MobileAppsDataScraper#MobileAppsDataCollection#ExtractMobileAppsData#MobileAppsDataExtraction
0 notes
Text
Jiraiya *running*: Quickly, who wants to earn 10 bucks?
Naruto: How?
Jiraiya: I need someone to take the fall.
Tsunade *from the background*: Oh, my God!
Naruto: What did you do?
Jiraiya: I can't tell you.
Tsunade: Oh, my God!
Jiraiya: Yes or no, no questions asked.
Tsunade: Oh, my God!
Naruto: Make it twenty.
Jiraiya: Done.
Tsunade: I'll kill you!
Jiraiya: You're a good kid. *Takes him by the arm* I got him, Tsunade! I got him! *Whispering* Don't worry, she'll make it quick.
#naruto#naruto incorrect quotes#incorrect naruto quotes#naruto uzumaki#jiraiya#naruto and jiraiya#tsunade senju#tsunade#sannin#senju tsunade#uzumaki naruto#original: mitm
114 notes
·
View notes
Note
Wait, so how did Ligaya end up back in Ebott if Asriel took the souls a year after she left?
Oh no, you finally noticed, that's one of the screwy things I was struggling with, right, so, we can do two things to force it to make sense.
Asriel hypnotized/brainwashed Ligaya and Andres and brought them back to America himself.
Or
Asriel DID literally tear through the fabric of reality, whos to say he managed to make it work in his own way?
Either way, I appologize, I tried my best but I'm guilty of originally not thinking it all the way through and its regetfully a plot hole that I couldn't figure out how to fill in time (MitM has come a long way from being just a smut fic though, haha)
So! You can choose one of my ideas to fix the plot hole, either way, I think its a subject that won't come up in the story because I'm focusing on going foward. Frisk will be a little confused at the passage of time though, rightfully so.
#fanfic monster in the mountain talk#Speaking of plot holes#I've been thinking of the movie Holes#If Hector was accidentally responsible for getting Stanley in trouble..then how was he there at the camp before Stanley got there?#Did he end up going back to the camp multiple times...or..?
6 notes
·
View notes
Text
The Risks of Using Public Wi-Fi and How Proxies Can Help

Introduction:
In today’s digital age, staying connected to the internet has become essential for most people. Whether we’re traveling, working remotely, or simply grabbing a cup of coffee at a local café, public Wi-Fi networks offer convenience and accessibility. However, using public Wi-Fi networks comes with its own set of risks. In this article, we will explore the potential dangers of public Wi-Fi and discuss how proxies can be used as a solution to enhance online security and privacy.
Public Wi-Fi networks are widely available in places such as coffee shops, airports, hotels, and shopping malls. They provide a convenient way to access the internet without consuming mobile data. However, these networks are often unsecured, making them prime targets for hackers and cybercriminals.
One of the main risks of using public Wi-Fi is the potential for data interception. Hackers can easily set up malicious hotspots that mimic legitimate networks, tricking unsuspecting users into connecting to them. Once connected, hackers can intercept sensitive information, such as login credentials, credit card details, or personal data.
Another risk is the presence of snooping individuals on the same network. Public Wi-Fi networks are typically shared among multiple users, which means that someone with malicious intent can monitor your online activities and capture your private data.
Man-in-the-middle (MITM) attacks are also a significant concern when using public Wi-Fi. In these attacks, hackers position themselves between you and the websites or services you are accessing, allowing them to intercept and manipulate the data exchanged between you and the target server.
To mitigate these risks, one solution is to use a proxy server. A proxy acts as an intermediary between your device and the websites you visit, routing your internet traffic through a separate server. This can help protect your identity and sensitive information by adding an extra layer of security.
When you connect to a public Wi-Fi network and use a proxy, your data is encrypted before it leaves your device. This encryption makes it significantly more difficult for hackers to intercept and decipher your information
Proxies also offer the advantage of hiding your IP address. Your IP address is a unique identifier that can reveal your approximate location and other details about your internet connection. By using a proxy, your online activities appear to originate from the proxy server’s IP address, providing an additional level of anonymity.
An important consideration when using proxies is to choose a reliable and trustworthy provider. Some proxies may log your online activities or even sell your data to third parties. It’s crucial to research and select a reputable proxy service that prioritizes user privacy and security.
Another type of proxy that can be useful in public Wi-Fi settings is a Virtual Private Network (VPN). VPNs create a secure and encrypted connection between your device and the internet, protecting your data from potential eavesdroppers. They also offer additional features such as masking your IP address and bypassing geographical restrictions.
While proxies and VPNs can enhance your online security, it’s important to remember that they are not foolproof solutions. They can help mitigate risks associated with public Wi-Fi, but it’s still essential to practice good cybersecurity hygiene and be cautious about the websites you visit and the information you share online.
When using public Wi-Fi networks, it’s advisable to avoid accessing sensitive information such as online banking or entering passwords for important accounts. Save those activities for secure and trusted networks, preferably using your mobile data or a trusted private Wi-Fi network.
Additionally, ensure that your devices are up to date with the latest software and security patches. Regularly updating your operating system, web browsers, and applications can help protect against known vulnerabilities that hackers often exploit.
Enabling two-factor authentication (2FA) whenever possible adds an extra layer of security to your online accounts. Even if someone manages to obtain your login credentials, they would still need access to your secondary authentication method, such as a unique code sent to your mobile device.
It’s also a good practice to disable automatic Wi-Fi connections on your devices. This prevents them from automatically connecting to any available public Wi-Fi network, reducing the chances of inadvertently connecting to a malicious hotspot.
In conclusion, using public Wi-Fi networks can expose you to various security risks. However, by employing the use of proxies or VPNs, you can significantly enhance your online security and privacy. Remember to choose reputable providers and complement these solutions with good cybersecurity practices to ensure a safe browsing experience, even on public Wi-Fi networks.
By staying vigilant and adopting these proactive measures, you can enjoy the convenience of public Wi-Fi without compromising your personal information or falling victim to cyber threats.
0 notes
Text
Web Application security threats and their solutions
Discover the various forms of web application attacks, how they can impact your company, and the steps you can take to protect yourself from them.
Cross-site scripting (XSS) attack:
An attacker launches a cross-site scripting (XSS) assault on a reputable website or web-based application by inserting a piece of malicious code into the target. The user's web browser will run the script because it believes it originated from a reliable source, which is very likely the case. Attacks using cross-site scripting (XSS) have the potential to steal data or carry out other harmful actions on the computer of a visitor. This technique, despite its low level of sophistication, is quite widespread and has the potential to cause significant damage.

SQL injection attack:
This type of attack involves injecting malicious SQL code into a vulnerable website's database. This can lead to data breaches, data manipulation, and data destruction. SQL injections take place when an attacker intervenes in every query that a web application sends to its corresponding database. An SQL injection vulnerability (SQLI) can give unauthorized users access to sensitive information stored in a database. An attacker can alter or remove this data, as well as insert code that can change the way the web application behaves or the content it displays.
Cross-site request forgery (CSRF) attack:
This attack involves tricking a user into acting on a website without their knowledge or consent. It takes place when an attacker uses deception or coercion to get an end user to perform undesirable activities on an application in which they have already authenticated themselves. This may be carried out by a link sent in an email or through a chat session, and if it is successful, it may result in, for instance, a transfer of funds or a change in email address.

Denial-of-service (DoS) attack:
In this type of assault, the attacker deliberately overwhelms the target website with traffic to make it unavailable to its intended audience. Because of this, businesses risk losing money and having their reputations harmed. These assaults occur when an attacker overwhelms a server with a large number of HTTP requests. This type of attack, which can paralyze a server and block genuine users from accessing your services, can be launched by a network of infected machines or bots.
Man-in-the-middle (MitM) attack:
In a man-in-the-middle (MITM) attack, a hacker arranges a meeting between two targets and then uses their trust in each other to gain access to the information the targets were trying to provide to each other. A man-in-the-middle assault allows an adversary to sabotage a message that is meant for another recipient or is not supposed to be transmitted at all, with little chance of detection until it is too late. MITM attacks can be referred to in several different ways.
Tips for Preventing Website Attacks
There are many different types of web application assaults, but there are also ways to fight against them. A few important tools are mentioned below.
Automated scanning:
It assists enterprises in detecting, analyzing, and mitigating vulnerabilities and misconfigurations – ideally before an attack occurs. It will help enterprises in identifying security flaws that must be addressed.
Secure development testing:
It identifies the security threats and attacks early and also aids in the development of efficient strategies for preventing and mitigating the effects of breaches.
Firewalls for web applications:
These are hardware and software solutions that safeguard applications by preventing harmful traffic from reaching the online application.

Web application attacks can be disastrous for organizations, which is why it is critical to understand the different types of attacks and how to best defend web applications. Businesses can limit risks and secure their online applications by using suitable development, testing, and security processes.About Us
This blog is brought to you by Tripund Solutions, a rapidly expanding IT company headquartered in Mumbai, India. We are committed to providing customers worldwide with seamless web and mobile solutions, customized software development, software testing, and maintenance services. If you are looking for a technology partner, then look no further, get in touch with us today at [email protected]
#website development#website design#application development#cyber security#it security#software development#software testing#software security#software and applications#development#apps#information technology#tripund solutions
0 notes
Note
You need to make a post that’s like “Hal mitm was the original dilf #facts”
ok
10 notes
·
View notes
Text
Dane Dnssec DNS Technology

DNS is susceptible – Cannot be reliable, no developments since 1983 and practice of functionality and amount has extended.
Besides, security be unsuccessful with Opportunistic Encryption which leads to illegal and negotiated certificates, Man-in-the-Middle invader may lower session to non-TLS at the time of email communications.
Hacker can interrupt TLS message by plotting documentation from the way of MITM and unsuitable formations accepts self-signed certificates.
DANE is a technology that might modify our existing and upcoming days via Cloud Adoption Solutions Devops. It’s a DNSSEC trust structure for X.509 certificates that deliver encoded email communications.
DANE – DNS built Authentication of Named Entities delivers layered security by fastening the X.509 certificate of a website to the DNS. This channel provides details about X.509 certificate to the user who can use to validate certificate.
DANE uses DNSSEC —-> DNS turn into policy channel —-> DNSSEC affix trust layer
DNSSEC – DNS Security Extensions (DNSSEC) adds security to the DNS by personifying public key coding into the DNS pyramid. When carried out via an outbreak on a network’s or an ISP’s structure, all of the entity’s users are affected.
NCDRC’S TAKE ON DNSSEC AND DANE
At, National Cyber Defense Research Center, it has been tested DNSSEC authentication on resolvers by using Bind9, Mozilla, Chrome and Gateway, which means resolvers always authenticate enquiries for fields that have been signed using DNSSEC. Operators mechanically benefit as soon as a domain is signed using DNSSEC.
So far techies deploying DNSSEC on their domain names – “sign” domain names or ask Registrar for DNSSEC (Enable DNSSEC validation on originations/ISP DNS resolvers). World really needs lots of DNS resolvers. Besides, ask ISP about DNSSEC and support on their ISP DNS resolvers.
Both DNSSEC and SSL depend on public key cryptography. DNSSEC deals with “where”, and SSL deals with “how” and “who”.
DANE is targeted by Security providers, Government or Private Email users with known security needs, Online-Payment sites, insurance providers, banks, Enterprises and Internet of Things.
#AI In healthcare Sector#digital transformation in healthcare#Artificial Intelligence in Healthcare Industry#healthcare transformation#healthcare compliance#healthcareAI#aiinhealthcare
0 notes
Text
How VPN Protects You from Online Fraud or Theft?
VPN is a virtual private network, which is used to connect multiple different locations that are geographically located close to each other but are not in the exact physical location.
Identity theft is the fraudulent use of someone’s identity, usually to obtain credit cards, bank accounts, or other forms of financial gain. A major way that Identity Theft Happens is through a breach in an organization's database system.
Protect yourself against online fraud, cyber-attack, and identity theft. VPN hides all your personal information, encrypts your data, and protects you from hackers.
Due to how easy it is to obtain personal information from unaware users, Wi-Fi hotspot hacking is growing in popularity. Anyone with little intelligence and access to the Internet can successfully carry out a hack, as demonstrated by a grade school student. Additionally, a hack doesn't just affect the information on your computer; it also gives hackers access to the data on your phone, tablet, or any other device that is connected to a Wi-Fi network, including photos, messages, contacts, and browsing history.

The location of your most embarrassing Google searches, the date of your most recent vacation, and even where you live are just a few examples of the information that can be gleaned from network hacks.
A Man-in-the-Middle (MitM) Attack is a type of hack that deceives your Internet-connected device into thinking the hacker's computer is the authorized intermediary between your computer and the Internet.
Any data sent over the Internet will first pass through the hacker's computer, allowing them to see all of the network traffic without any of the victims being aware that their data has been compromised. Unfortunately, it gets worse if you go to a place you've already been to. Your information becomes accessible when you use Wi-Fi at the same location repeatedly, like your favorite coffee shop, before you even consciously start to browse the Internet. Without you even taking your phone out of your pocket, hackers may have access to your information because the majority of devices will automatically connect to a network that has been used before. Some apps, like email or location services, periodically retrieve your most recent messages or location data from the Internet as a convenience.
A hacker could find your name and precise location with this auto-retrieval method in a matter of minutes. The things in your Amazon shopping cart or the Facebook pages you recently liked can give people a pretty good idea of how you look, but that's not the end of it. Since hackers can view the data that is stored on connected devices, this encourages them to carry out more covert attacks, such as setting up a fake Wi-Fi hotspot with the name of a trustworthy network to appear trustworthy to unwary users.
The good news is that having a VPN shields your data from this simple attack. There is no doubt that identity theft is on the rise as a result of payments shifting to mobile devices and everything else becoming digital. But with Strong's dependable VPN service, you can relax knowing that your data is securely protected.
All data sent over a VPN for mac, including its contents and origin and destination, is encrypted. As a result, neither network administrators nor skilled hackers nor even your Internet Service Provider will be able to see the data you're sending or receiving. Therefore, all of your social media passwords, credit card information and SSNs are secure.
0 notes
Text
[Media] WiFi Pineapple Mark VII by Hak5
WiFi Pineapple Mark VII by Hak5
The Hak5 WiFi Pineapple is a highly advanced WiFi auditing and MITM platform. The original "RougeAP" device - the WiFi Pineapple provides an end-to-end workflow to bring WiFi clients from their trusted network to your rouge network.
Hak5's latest generation V7 brings sees updates in three key area: performance, management tools and framework upgrades.
The PineAP suite is a cross-platform control panel for the WiFi Pineapple devices, providing fine-grained control over all elements of your audit.
The elegance of the WiFi Pineapple Platform is in its simplicity. Previously onerous, inefficient and prone to collateral damage - WiFi Auditing and Offensive Operations are now highly targeted, covert and very simple.
Advanced mitm attacks: Perfectly mimicks target networks, allowing for seamless client capture via the highly targeted deAuth mechanisms. Once captured, all standard network vectors are available: DNSSpoofing, Packet Capture, etc.
Wifi reconnaissance: Covertly discover, visualise and map WiFi networks and client hierarchies. Build lists of existing networks, and even client historical SSID connections. Continuously scan, add notes, filter clients, networks, logs and more.
Automated wifi infiltration: Capture and pipe WiFi Encryption credentials in pcap / hashcat or JTR formats. WEP, WPA & WPA Enterprise.
Highly targeted, highly covert: Keep your "Get Out of Jail Free" letter firmly in your pocket. The PineAP suite allows for fine-grained, highly targeted actions, ensuring no detection and no collateral damage.
Buy online:
🛒 https://ali.ski/aRCSNt (aliexpress)
🛒 https://amzn.to/3VxMHbd (amazon)
#pineapple #wifi

1 note
·
View note