#ndr predictions
Text
So Ras apparently works for Someone and has recruited Jordana. And she has raw Source Dragon energy. None of that's good. BUT I'm thinking Jordana will eventually come to regret that decision.
Sora unlocked her True Potential, which I'm so happy for! She didn't go all golden like the others, so maybe her powers work a little differently?
Arin's def going thru it. Poor kid. He saw his parents for the first time in years. And it didn't look like they aged at all. I wonder where they are and what they've been up to. Maybe frozen in a pocket? That's possible.
It's basically been confirmed that Wyldfyre doesn't have fire powers. It's something else. Something that produces a significant amount of heat to melt aluminum cans and glow blue around her hands. I just have no idea what it is.
There's gotta be a confrontation between amnesia!Jay and the other ninja at some point.
We're def going to be getting more of the Administration in the next season. I just don't know how much.
Alright, I'm going go thru my correct and incorrect predictions tomorrow at some point. It's getting late here and I'm a little sleepy. Tomorrow is also movie night, so I'll be started up the second season the day after. Until then!
#liveblogging#ninjago dragons rising#dragons rising#season 1#episode 20#the power within#ndr s01e20#ndr predictions
23 notes
·
View notes
Note
Sky, sapphire, azure please xx
Sky - how many pillows do you sleep with?
This is an interesting question, because I never thought about it - and I should, considering that sleeping has always been an issue for me since I was four. And that made me realize that, sometimes, I sleep with one pillow, and, sometimes, with two. I suppose that, unconsciously, it may have something to do with how I am feeling during a determinate period - probably, if I am feeling more confident (or comfortable with my current situation), I can do without that extra dose of... well, of cosiness.
Hopefully, in the last few weeks, I've been sleeping with just one pillow. And, for an insomniac, I am sleeping a fairly decent number of hours.
sapphire - how do you feel about surprises? do you like them? why or why not?
Surprises can be a mixed bag, can't they? And, all over the years, I had my fair share of surprises - many of them quite bad, but some surprisingly good. Maybe, those bad surprises forced me to be in a state of constant vigilance - so, when something bad happens, I am somehow already expecting it, and the bad surprise is no longer an actual surprise. Being so, that means that all surprises end up being good...
... unless something surprisingly wicked (like being stabbed in the back by the very person I trusted and loved the most) happens. Sadly, evil can always find new and surprising ways of making you suffer. I said previously that one can always try to be aware regarding negative events, but there are things you could never predict.
But this doesn't answer directly to your question, does it? The truth is that, despite all the vigilance and all the care, I accept that life is always full of surprises, and, to be honest, I would execrate a life without them - even the ones that broke my heart in pieces.
NDR: Birthday surprise parties do not count as a surprise. Few know when I was born, and even less know where I shall be on that day - probably, taking photos.
azure - if you were to repaint your room right now to match your current vibe, what color would it be?
Considering my current situation, I have no idea where my room is, but let's imagine a metaphoric bedroom, shall we?
Taking in consideration that I am about to start my PhD, yellow - a colour that stimulates the intellect - would be appropriate.. but no, I hate yellow. So, I reminded myself of the answer you gave to this very question - light aqua. And that's, probably, the right answer for me as well. It's a colour that brings creativity (the sea has always been my muse), clarity of thought, and tranquility. Also, it's a colour associated with the sense of belonging - and the gods know how much I crave for that.
So, light aqua it shall be. It's a wonderful colour, by the way.
(thank you very much:)
5 notes
·
View notes
Text
NDR Logistics Works Efficiently to Ensure Timely Cargo Transportation
In present times, time is money. So, businesses depend on efficient cargo transportation services to keep their operations running smoothly. In this pursuit of excellence, NDR Logistics has emerged as a beacon of efficiency, leveraging cutting-edge logistics technology and a dedicated team to ensure timely deliveries and reduced transit times. With years of experience and a sterling reputation, NDR Logistics has solidified its position as a trusted partner in the logistics industry.
How is NDR Logistics Ensuring Timely Delivery?
When it comes to cargo transportation, technology plays an important role in streamlining operations and improving efficiency.
a. Route Optimization
NDR Logistics uses modern route optimization software for charting the most efficient route for each shipment. With this technology, we can learn about weather conditions, traffic patterns, and road closures to ensure the cargo reaches its destination through the safest and quickest route.
b. Real-Time Tracking
Transparency is important when it comes to the logistics industry and NDR Logistics excels in this field. Its real-time tracking system lets customers monitor the progress of their shipments at each stage.
c. Inventory Management
Efficient cargo transportation is not just about shifting goods from one point to the other, it is about managing inventory effectively. NDR Logistics uses top-notch inventory management systems to make sure that the cargo is accounted for and is available in times of need.
A Dedicated Team Works Efficiently
While technology plays an important role, it is the people working behind the scenes who make the real difference. NDR Logistics takes pride in having a dedicated team at its disposal that ensures that each shipment is delivered on time.
a. Expertise
NDR Logistics’ team has experienced professionals who have in-depth knowledge of the logistics industry. Their experience extends to different sectors, including international shipping regulations, customs clearance, and local nuances, which can impact the process of transportation.
b. Driver Excellence
Central to NDR Logistics' commitment to timely deliveries is its team of experienced and trustworthy drivers. These professionals are not only skilled in driving but are also dedicated to ensuring that your cargo reaches its destination on schedule and in pristine condition.
c. Problem Solvers
Logistics isn’t predictable. However, NDR Logistics thrives on looking for solutions. No matter it is rerouting shipments because of unforeseen circumstances or speeding up customer clearance, there are professionals who are adept at overcoming challenges more efficiently.
d. Round the Clock Support
Logistics don’t adhere to a 9-to-5 schedule and neither does NDR Logistics. Their 24/7 customer support makes sure that assistance is only a phone call away, regardless of the nature of the query or time zone.
NDR Logistics Quotes Competitive Rates
The cargo transportation company offers remarkably affordable transportation prices. Check out how pricing is a standout feature of NDR Logistics.
a. Competitive Rates
NDR Logistics offers competitive rates in the Indian transportation industry. The pricing has been designed to be affordable while maintaining the best service standards. Thus, they are an attractive choice for businesses that want to optimise their transportation budget without compromising on their work quality and efficiency.
b. Transparent Pricing
Transparency is important when it comes to pricing. NDR Logistics makes sure that its pricing structure is straightforward and clear. Hence, you know exactly what to expect. There aren’t any unexpected charges or hidden fees. So, you know that you plan your budget for the logistics with confidence.
c. Cost Saving
NDR Logistics’s commitment to efficiency extends to cost savings for their customers. through technology-driven solutions, route optimization, and experienced logistics management, they reduce operational costs. Thus, you can save a lot of money on cargo transportation.
d. Value for Money
Even though the prices are competitive, NDR Logistics doesn’t compromise on the value we offer. Our dedication to timely deliveries, excellent customer service, and secure handling ensures that you receive exceptional value for the rupee you spend on their transportation services.
The ultimate testament to NDR Logistics' efficiency is the satisfaction of their customers. Repeat business and referrals are a common occurrence, underscoring the trust and loyalty they have built over the years. As the world of logistics continues to evolve, NDR Logistics remains at the forefront, consistently exceeding expectations and setting new standards for efficiency and reliability. Contact Us .
1 note
·
View note
Text
Considering an XDR Purchase? Here Are Our Lessons Learned.
Lessons learned from our search for, and integration of, our XDR
Trusted Internet is now deploying Stellar Cyber XDR –as a SOC-monitored solution or as an Infrastructure as a Service.
The marketing hype around XDR is deafening for those of you considering an XDR. It’s hard to sort through the slick websites and marketing noise to tell what’s actually real. So, I thought I share a few lessons learned –from the viewpoint of the CEO of a self-funded MSSP, I hope this helps in your buying decisions.
For the last four years, we’ve been a died-in-the-wool Fortinet MSSP. We love our Fortinet firewalls, with our people certified through NSE7, working hard to tune the feature-packed high-speed machines to bend to our will. For various reasons, we decided about two years ago to begin the search for a way to accommodate the requests from would-be clients to not have to rip and replace their existing security systems.
As well, SOC, NOC, EDR, MDR, NDR, MSSP. Why would someone not combine them all into one box that understands ALL of their logs and uses a bit of machine learning to train AI to better assist SOC analysts? I have an old friend that used to refer to this as the God Box. It knows all.
XDR is the beginning of the God Box.
Our requirements:
***It must integrate all those other vendors in a client’s environment without requiring them to rip and replace their existing infrastructure.***We didn’t want to have an agent deployed to every computer. They already have AV and Anti-Evasion. We didn’t want to load on another endpoint system.
We want the ability to integrate network flow analysis for anomaly detection but may not want it 100% of the time. Flow produces heavy volumes of data that we wanted to be able to turn on and off as needed based on other indicators.
***It must accommodate all NIST 800-171 log-collection/analysis requirements.***While ISO, CIS, HIPAA, or PCI require the aggregation and analysis of all of these logs, NIST 800-171 requires monitored log entries from just about every device for every event –infrastructure, endpoints, and security.
We need to find a better way to get eyes on these logs and do it in a way our SMB-focused client base can afford. To do that, we need to be able to bring them into one system that understands each of the required logs.
It must be multi-tenant.
At the time, I had no idea how much doubt I would have in AI until after I watched the various XDRs run. Be ready with a smart team.
We compared one to another, performing A|B testing while using FortiAnalyzer and raw log data in our Lucene stack as baselines
Ideally, the XDR must accommodate any vendor, not just those built by the XDR vendor.
Some XDR vendors we looked at built their own AV, IPS, etc. Others OEM’d someone else’s but wouldn’t discuss it.
Regardless, I want to know that the tools built into the XDR are mature and tested.
***If there’s a cloud component, I want proof that their cloud environment is secure.***All of our clients’ vulnerability data will end up residing there. I don’t want a data breach in our XDR vendor leaking customer vulnerability information. From an espionage perspective, this is an AMAZINGLY rich target. It MUST be safe.
We evaluate the backend security of all of our vendors. When we did this during our search, one XDR vendor had an amazing product but offered services in a cloud environment had never been security tested!
Compliance is good, but more importantly? Walk me through how you protect data. Make me feel comfortable that you have taken the measures to protect the data. I was surprised by more than one who couldn’t do this.
The price structure must be 100% predictable. Variable costs kill. I wanted to make sure we weren’t going to have any surprises. If an XDR vendor asks you, “How many endpoints do you have?” RUN. The pricing structure must accommodate our ability to build it into our subscription costs, at a reasonable margin.
In the MSSP world, SOC costs can make us fail faster than anything else. How does an MSSP scale without breaking the bank on increasingly expensive information security labor costs?
Our search for the Cinderella XDR (the one that fits us perfectly!):
We looked at dozens of vendors - you’ve heard their names. after nearly two years of competitive analysis, demos, and trials from nearly a dozen XDR companies, we narrowed our focus to two, both undergoing trials, with Stellar Cyber winning us over.
This was a significant capital investment for us. We wanted to make sure we did this right and were able to recoup our investment in added volume and efficiencies. Rather than going with their cloud version, we purchased the 88-core, 20Tb server. The system is designed to parse and analyze vast amounts of data from dozens of infrastructure devices, endpoint logs, and security systems. We wanted it protected, so we racked it up in our secured facility in Iron Mountain Datacenter and performed our first ‘eat your own dog food’ trial during the early summer of last year.
We have MANY lessons learned. I won’t be able to share them all in one short paper, but I thought it might be good to share a few of the bigger ones.
XDR offers a wonderful solution for bringing just about any piece of information that you can imagine into one pane of glass. We found it overwhelming.
This is not an entry-level tool. XDR can introduce ambiguity where none should exist. You’ll need a smart team to evaluate every XDR hit before activating SOAR. While the AI learns from the XDR vendor’s larger customer base, it also learns through actions performed by your analysts. They need to be smart.
Most XDR solutions want to price by the endpoint. This is a deal killer. If a salesperson asks, “How many endpoints do you have?”… RUN.
XDR offers a wonderful solution for bringing just about any piece of information that you can imagine into one pane of glass. We found it overwhelming.
XDR is a fantastic idea, but bad execution will ruin your day. IT guys want to immediately throw everything (and the kitchen sink) at this magic box. And while I fully understand the geek desire for ‘more data is good,’ it made the training curve for our SOC analysts brutally hard.
These things will consume just about any amount of data you can shove into them. We recommend against putting more than one stream into it at a time; at least until you get used to what the machine is going to spit it back out. Why? The machine will produce results on its own, based on preset rules. You’ll find that some are good, but not all -and there will be a lot of them. Your SOC analysts have to know better, They will initially, have to slog through every single alert to verify and validate -did the XDR call it? Was it wrong? What action(s) must be taken? AI, Automation? The magic box? All good things, but without a solid underlying knowledge of what the machine calls good and bad, you could find yourselves overwhelmed. We did. There’s a lot hidden in the black box. Go slow. Let your analysts learn. Bring in one data stream at a time.
Stutzman’s recommendation: Speed kills. Go slow. Start with one data feed. Get it normalized, then add the next.
Know this. XDR is not an entry-level tool.
I take a few SOC shifts every quarter to keep my skills sharp. It keeps me in touch with my SOC, and maybe I do it because it’s one of my favorite jobs! Anyway, during my first shift with a new operational Stellar in our first XDR client, I found myself (at about 2 AM) looking at internal activity behind the firewalls but clearly on the network, with an alert telling me that clear text passwords are being passed at high volume, to fifteen different systems. This bank was not open at 2 AM.
I thought there were only two possible explanations: compromise or vulnerability scanning. As it turned out the client was running OpenVAS to test our response (we passed!), but… how did we see it? I’m looking at internal data from places we’d not seen before! We were now capturing Windows logs, infrastructure logs, authentication logs, and network flow from the 60-person bank. We were pulling in nearly 40 GB of logs per day. I felt like Mr. Magoo, who finally got good glasses and was seeing color for the first time!
As we fully integrate, we’ve retained our FortiAnalyzer and Lucene Stack to allow our analysts to step away from the XDR environment and see data presented in a way they’re familiar with. We’ll do a parallel cutover at some point when old licenses expire. However, as we transition, our Tier 1 analysts (triage analysts) are being forced to learn deeper skillsets. Triage will likely be a thing of the past as XDR takes on automated actions for more mundane tasks like blocking a new scanner or validating the findings of tools before escalating them for action.
Stutzman’s recommendation: Your analysts need to be smart enough to understand what is happening in the data before the AI and Automation take over and the new machine implants mistakes. I’m sixty years old and have been doing this for a long time, but I still wanted a second set of eyes. This is not an entry-level tool. It’s an expert-level tool.
Most XDR solutions want to price by the endpoint. This is a deal killer.
If an XDR vendor asks, “How many endpoints do you have?” RUN!! Endpoint counting doesn’t work in XDR pricing. You will not like the surprise. I cannot stress this enough.
We learned this the hard way. Nirvana for an MSSP is having data from multiple devices on one pane of glass. We installed Stellar Cyber operationally last summer for our own internal operations. We believe in “eat your own dog food” before going live with sales (we use everything we sell).
I asked my IT Director to go one step at a time. Place one information flow into the system, and let’s see how it normalizes. Unfortunately, following our vendor’s lead, he put a span port in our core switch and pushed everything we had into Stellar. The firehose came alive. The XDR generated pseudo flow for over 40,000 devices. Every IOT, mobile, computer, server, every single device with an IP address sitting behind one of our firewalls, anywhere in our client portfolio, was now counted as an endpoint. Our sales team was great. We didn’t get charged while we figured out how to normalize, so we turned off the firehose and started with one client at a time, starting with our own infrastructure. We didn’t want to lose fidelity, so we ended up doing a volume license based on amounts of data, not numbers of endpoints.
Stutzman’s recommendation: Ask for this upfront, then throw as much as you want to at it.
We’ve had our system in for nearly a year now, first as the proof of value starting last March, then going operational during the summer, and now fully operational, deploying it in support of the many NIST 800-171 related projects that we’ve been involved in, and where we’ve got clients who have heterogeneous environments. It’s done a great job. Are we 100%? No. We still require parsers to be written for tools that aren’t already available. We have not yet fully turned on SOAR, and frankly, I’m hesitant to do so in some of our more fragile customer locations where we don’t know what kind of ripple effect the automated action(s) might take.
Are we happy we bought into XDR? Absolutely. The system costs about the same as a couple of good analysts, but I’m confident that it will allow us to scale into clients that we previously would not have been able to access.
Sharing is caring. We had some hard lessons learned and some scary budgetary moments when I thought we were going to have to write some big checks to pay for this thing for —more money than I’d have in our account for a year. Our Stellar team has been amazing, even though we’re a small fish in their bigger pond. I hope this was helpful as you consider your own XDR purchase. Or, if you prefer, contact us. We’d be more than happy to create your XDR in our new multi-tenant Stellar Cyber environment.
0 notes
Text
Network Monitoring Market Growth, Status and Forecast by 2027
The Field of Network Monitoring, a crucial component of the present IT infrastructure, is anticipated to witness a breakthrough shift in the forthcoming years. As networks continue to evolve and expand swiftly with growing advancements and complexities, the need for monitoring stands critical for businesses across the globe to mitigate server downtimes and network failures and enhance productivity.
Network monitoring software help analyze the performance in real-time, i.e., they send an immediate alert in case of any network failure enabling one to take instant corrective action while minimizing potential downtime
Request for a sample copy of this report @ https://www.gminsights.com/request-sample/detail/3015
It is a proactive approach that eliminates the need for manual checks and physical system administrator and helps determine the exact problem areas of a network, saving a lot on company time and expenses. The reports generated from this software support enterprises to identify the trends and patterns in the system performance and document the necessity for any upgrade or replacements.
This could be due to the countless product benefits like network visibility, maintaining compliance, preventing downtime, quickly finding and fixing issues, uncovering security threats, capacity planning, etc.
In the last few years, there has been a substantial rise in internet users across the globe. This could be attributed to the surging digitalization, increasing smartphone penetration, and rapid prevalence of social media and online gaming trends. The sudden onset of the COVID-19 pandemic has further contributed to the numbers due to the integration of remote working and e-learning culture following the stringent social distancing norms across several economies. As per new estimates by the International Telecommunication Union, the number of internet users across the globe surged to 4.9 billion in 2021.
Remote working exposes the company networks due to increasing system access and poses severe security risks. This is why network monitoring is so crucial; it helps meet the enterprise requirements for reliable and robust tools to monitor IP assets and optimize the required speed.
Request for Customization @ https://www.gminsights.com/roc/3015
Increasing adoption of 1 and 10 Gbps ethernet across enterprises and metropolitan networks to offer two-layer networking for mere high-speed applications in the data center or server room has significantly improved the segment growth over the last few years.
10 Gbps data ethernet helps prevent data bottlenecks by enabling efficient data transfer and storage solutions. It is also a convenient alternative if the company plans to expand its server capabilities. Moreover, high bandwidth has gained a lot of traction given its unparalleled speed and reliable security.
The network monitoring industry has witnessed several innovations over the years as a result of increasing focus by the industry players to foster trade associations and keep up with the rising consumer demand.
Browse report summary @ https://www.gminsights.com/industry-analysis/network-monitoring-market
Below are a couple of instances illustrating this trend:
• In February recently, Telstra announced its collaboration with Intellihub with its AU$100 million deal to outfit the latter's smart meters with IoT sims. The partnership will benefit Intellihub and its customers to control energy demand more efficiently and deliver a real-time understanding of the energy network.
• In the same month, Cynamics launched a cloud NDR offering, terminating network visibility obstacles by bolstering network monitoring, prediction, and detection capabilities across any hybrid-cloud or cloud-native atmospheres into a single-pane view adapting to deviating requirements of contemporary organizations.
Key participants contributing towards network monitoring market growth include Accedian Networks, Inc., Apcon, Inc., AppNeta, Inc., Arista Networks, Inc., Broadcom, Inc., Cisco Systems, Inc
About Global Market Insights Inc.
Global Market Insights Inc., headquartered in Delaware, U.S., is a global market research and consulting service provider, offering syndicated and custom research reports along with growth consulting services. Our business intelligence and industry research reports offer clients with penetrative insights and actionable market data specially designed and presented to aid strategic decision making. These exhaustive reports are designed via a proprietary research methodology and are available for key industries such as chemicals, advanced materials, technology, renewable energy, and biotechnology.
Contact Us:
Arun Hegde
Corporate Sales, USA
Global Market Insights Inc.
Phone: 1-302-846-7766
Toll Free: 1-888-689-0688
Email: [email protected]
0 notes
Link
I don’t really understand this project. Maybe you can by reading the link to this EcoWatch story about it. Here’s a short video from the NDR Elbphilharmonie Orchestra that explains how the Vivaldi piece has been altered to address how the climate has been changing. After that short video, I’m posting a link to a longer version of the evolved piece performed by the orchestra. Then a short description of the project from EcoWatch.
Here’s a link to the project website. That might provide a better explanation.
youtube
youtube
Excerpt:
Three hundred years ago in 1723, Antonio Vivaldi composed "The Four Seasons," a series of violin concertos inspired by the natural world. Now, scientists, composers and designers have reimagined the classic to help envision what the future might feel like in 2050 — a world forever changed by the climate crisis.
Tim Devine, executive creative director of AKQA, the design firm that masterminded the project, told EcoWatch, "On the surface, the original Four Seasons is about weather and seasonal variation, but it is very much about our human relationship to the world. That's what makes it a great fit for the narratives that climate science tells us the future could be like."
The collaborators on the updated Vivaldi score used algorithms to predict specific impacts of global warming in 2050, and to interpret those changes in sonic terms. The result is "The [Uncertain] Four Seasons." In it, they explored how to "derive a lived experience of climate science predictions for RCP 8.5 in 2050," Devine explained. (RCP 8.5 is an emissions scenario for global warming.)
Hugh Crosthwaite, the composer of the piece, told EcoWatch, "The data tells us things are looking grim. Without urgent and profound action, the world will be absolutely and starkly diminished."
9 notes
·
View notes
Text
Frauen Bundesliga week 9

It’s a battle of rivals this week in the Frauen Bundesliga
Turbine Potsdam takes on Eintracht Frankfurt
The battle for third place continues, can league leading goal scorer Laura Freigang help secure enough points to keep Frankfurt close enough to grab the third spot?
All of the women’s Bundesliga matches are streamed in our discord HERE, it’s free to join and we have a prediction competition going on!
What time: Friday November 13th at 19:15 (CET) | 18:15 (GMT) | 13:15 (EST)
How to watch: Discord, Eurosport Germany, USAGoals, Joyn (VPN)
Bayern takes on Wolfsburg
With Wolfsburg only being 2 points behind Bayern, will they finally be the ones to break the 8 game clean sheet streak? Bayern’s defence has been impressive this season, but this is going to be a vital game for both teams.
What time: Sunday November 15th at 14:00 (CET) | 13:00 (GMT) | 08:00 (EST)
How to watch: Discord, BR, Sportschau, NDR
#woso#wofo#womens football#womens soccer#how to watch#womens bundesliga#frauen bundesliga#Eintracht Frankfurt Frauen#VFL Wolfsburg Frauen#Turbine Potsdam#FC Bayern Frauen
21 notes
·
View notes
Text
JOACHIM KORTLEPEL ON THE WORK HE’S PROUDEST OF
We often ask our jury to reflect on the work that they’re proudest of. This week, we feature Joachim Kortlepel, Executive Creative Director at Jung von Matt/AG in Hamburg – the agency behind the award-winning ‘For Seasons’ campaign.
Last year, Joachim Kortlepel was a judge at AD STARS 2020, where his agency scored big winning the Radio & Audio Grand Prix for ‘For Seasons’ – an ingenious campaign for NDR Elbphilhamornie Orchestra Hamburg that uses climate data to recompose the ‘Four Seasons’ by Vivaldi. This campaign also won Gold in the Data Insights category.

Is there a campaign you’re proudest of making, Joachim?
I’m proudest of projects that involved music in one way or another to solve a problem, to raise awareness or to create a meaningful impact. As a standalone project, most likely the global marketing campaign for the opening of the Elbphilharmonie in Hamburg back in 2017 was a once-in-a-lifetime effort. Because it does not happen all too often that you have a building only for music and art like this one, and a client’s construction delay crisis like the one we faced when we began to work.
As the leading creative I spent some 1.5 years solely dedicated to this project (the grand opening is pictured above). It was worth the effort and I can look at the Elbphilharmonie every day when I pass by it on my bike. That’s awesome and sort of a permanent reminder of my own work when you look at how it has become a concert house for truly everybody and how we managed to turn public opinion around.

From here, you created the ‘For Seasons’ campaign for the same client. Can you explain the concept and what were the biggest challenges in bringing this idea to life?
Climate change has become the biggest threat to life on earth. After numerous scientific reports, extensive media coverage and a whole generation having taken to the streets, we should have all got the message by now. Yet, it seems the magnitude of the crisis is so overwhelming, many prefer to ignore it. Our client, the NDR Elbphilharmonie Orchestra from Hamburg, a city predicted to be flooded by 2050, could not remain silent. We wanted to use the power of music to send an unmistakable signal against climate change that would finally get people to listen.
In order to make that happen, we took the most famous musical depiction of nature, Vivaldi’s Four Seasons and adapted it to today’s weather conditions using historical climate data. Vivaldi wrote the Four Seasons in 1723. His work was a revolution in musical composition: In each concerto, he portrayed the characteristics of the seasons and their natural phenomena like gentle winds, violent storms, frozen landscapes and even singing birds.
Can you explain how you used data to create this campaign?
We engaged a collaborative team of sound artists, software developers and music arrangers and converted the original Four Seasons into a new score: For Seasons. From temperature anomalies to CO2 emissions and to species extinctions, more than 10 data sets were comprised from the 18th century until the present day. The collected data was then fed into multiple custom-made algorithms which transformed what Vivaldi had expressed in his masterpiece into what we experience now.
For instance, the algorithms adjusted the duration of the seasons: today’s Winter is 51 bars shorter. Motifs of Summer already arrive in Spring. Vivaldi represented “Summer’s occasional thunderstorms” with flashing solo violins. The algorithms placed unexpected thunderstorm motifs throughout the entire piece according to the dramatic increase in natural catastrophes. The violin trills, mimicking bird sounds were reduced by 15%, signifying the decline in bird populations.
When did this campaign launch, and how was it received?
After months of work and rehearsals, For Seasons premiered at Elbphilharmonie Hamburg to a sold-out crowd and to 150,000 live viewers on Facebook. Led by world-renowned conductor Alan Gilbert, the philharmonic orchestra performed the altered concertos to a visibly shocked audience. The concert ended with a 7-minute standing ovation. Only two days after the concert, the United Nations reached out to us hoping to “work together to fight climate change”. For Seasons is now partnering with the United Nations Development Program and more concerts are being arranged, and the score is freely available to any orchestra in the world. In the end, we made climate change audible and people finally started to listen.
Was the client always on board, or was there a period of persuasion?
What turned out to be a great success, was in the beginning very difficult to explain to our client. Simply because we did not know what to expect - nor what to explain ;-) when you let data recompose a musical masterpiece. And as long as we did not know, it was extremely difficult for the musicians of the orchestra to get the project going, without knowing the outcome. What will it sound like? Will it be disturbing enough? Will it be a wake-up call? Are we happy if they applaud us or should they rather leave the concert somewhat scared?
These were the most difficult questions we faced. So, we put everthing to a test. We first took the Spring, altered the score with climate data, listened to it on the basis of computer-generated midi files and then went into the Elbphilharmonie and actually played the Spring and recorded everything. From there on we moved forward: step by step.
AD STARS first introduced the Data Insights category in 2018. To enter this category in the AD STARS 2021 Awards, visit adstars.org – the deadline is 15th May!

1 note
·
View note
Text
Final Blog Post
New York City & Puerto Rico: A Comparison of Mitigation Strategies and Recovery
New York City and Puerto Rico are located near large bodies of water that make them susceptible to coastal related natural disasters. Hurricanes and the damage that ensue because of them puts both islands at risk. Even though each city has been heavily affected by hurricanes, when you think of them individually, Puerto Rico is associated with more catastrophic effects and a lengthy recovery process.
Why are New York City and Puerto Rico prone to natural disasters, specifically hurricanes?
What sort of mitigation and recovery measures are taken and how do they differ?
Geography Of New York City and Puerto Rico
New York City is almost completely surrounded by water as it sits on the Atlantic Ocean and Hudson River. Located not even 5 meters above sea level, the low lying island of Manhattan is in a vulnerable position as they are at extreme risk of facing damage from hurricanes and cyclones in the Atlantic, such as storm surges and extreme coastal flooding. Given the population and infrastructure density of this coastal city, the damage that would result from this disaster is extensive.
Puerto Rico is located in the Caribbean Sea, specifically on the hurricane belt which puts the island in danger of deadly hurricanes and coastal storms [3]. While this is already unfortunate for Puerto Rico, climate change is acting as a catalyst for the intensity and frequency of hurricanes in this area. Hurricanes also have a wide range of impacts on the island including landslides, flood damage, storm surges, and tornados [6]. These different factors pose a serious threat to the livelihood of citizens and infrastructure in Puerto Rico.
Comparison of Mitigation Strategies
New York City has a few different mitigation strategies including the SLOSH storm surge model or Sea, Lake, and Overland Surges from Hurricanes. This storm surge model is used to predict the surges and provide a forecast of the different components of the surge including the storm position and size [4]. The city also has a Coastal Storm Plan put in place for the event of a hurricane. This plan includes a multitude of frameworks regarding “Interim Flood Protection Measures (IFPM), evacuation (including healthcare facility evacuation), sheltering, logistics management, donations and volunteer management, commodity distribution, debris management and public information” [7]. The city is also in close contact with the National Hurricane Center and the National Weather Service when there are dangerous, weather related threats and have different methods for altering people of these threats.
Puerto Rico’s preparedness for hurricanes differs a little bit as it relies more on the individual being ready for hurricanes. Being stocked up on food and water, having a survival kit, being familiar with evacuation routes and comfortable with your communities warning system for hurricanes is the responsibility of the citizen [5]. Sadly, mitigation strategies are lacking in Puerto Rico which is unfortunate considering their vulnerability.
Comparison of Recovery: Hurricane Sandy and Hurricane Maria
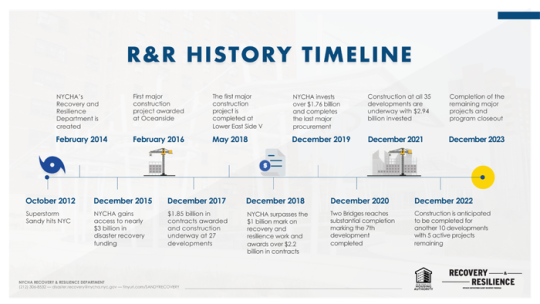
New York City has a couple different recovery or action plans in place including the Community Development Block Grant Disaster Recovery Program. This program “provides communities with resources to address a wide range of community development needs” as well as outlining how it “will use its CDBG-DR allocations to support recovery from Hurricane Sandy and to build resiliency to the challenges of climate change” [2]. This plan also intends to support “housing, businesses, coastal resiliency, infrastructure, and other city services” and the total allocation amount is $4,213,876,000 [2]. The city has also been awarded a significant amount of money from the NDR competition or the U.S Department of Housing and Urban Development’s National Disaster Resilience, which helps aid with coastal protection [2]. When Hurricane Sandy hit New York in 2012, it was very destructive towards housing and infrastructure, causing $3,000,000,000 in damage. Since then, the New York City Housing Authority has made significant progress in developing safer infrastructure protection by improving reinforcements for storm surge protection and designing safer homes for citizens [8].
https://www1.nyc.gov/site/nycha/about/recovery-history.page
Puerto Rico on the other hand is reliant on other aid from others. Hurricane Maria left the island in pieces, destroying thousands of homes and the recovery process is slow and minimal. While residents of Puerto Rico are citizens of the United States, the aid and response time from the U.S is saddening as other areas, like Texas or Florida, had priority even though the impacts were less severe there, highlighting the injustice Puerto Rico suffers [3]. According to FEMA, Hurricane Maria “left $90 billion in damages and Congress allocated at least $63 billion for disaster relief and recovery operations”, however around %71 of those funds have not reached the communities that need them [1]. However, Puerto Rico is making an effort to increase its environmental sustainability by pledging to strictly use renewable energy by 2050 and are planting trees along the coast to help fight land loss [3]. These changes are in the hopes that they will help minimize the effects of climate change and disaster on the island.

http://www.aksik.org/node/3597#:~:text=Puerto%20Rico%20is%20uniquely%20susceptible,temperatures%20(IPCC%2C%202014).
Final Thoughts
While both New York City and Puerto Rico are at risk from natural disasters such as hurricanes, Puerto Rico is disproportionately affected by them because they don’t have the economic or governmental stability to mitigate and recover from these disasters as well as NYC does. This is further reinforced by the lack of prioritization by the United States in ensuring that Puerto Rico has a quick recovery. As New York City has solid recovery plans being implemented and substantial progress being made, Puerto Rico is still facing the aftermath of Hurricane Maria.
Changes from my first draft
My first draft focused on the northeastern region of the United States and I discussed mitigation strategies for hurricanes in NYC and Puerto Rico. However, this was a very broad topic and did not feel very cohesive at all. For my final draft, I switched my focus to comparing hurricane mitigation strategies and recovery in New York City and Puerto Rico and as a result I have more depth to my blog and a better understanding for each location. I have also added a visual component to my blog to make it more interesting.
References
[1] Acevedo, Nicole. “Puerto Rico, four years after Hurricane Maria, far from recovery.” NBC News, 20 September 2021, https://www.nbcnews.com/news/latino/puerto-rico-four-years-hurricane-maria-far-recovery-rcna2073. Accessed 6 May 2022.
[2] “Action Plan – Community Development Block Grant Disaster Recovery Program.” NYC.gov, https://www1.nyc.gov/site/cdbgdr/action-plan/action-plan.page. Accessed 6 May 2022.
[3] Canty, Margaret Marie. “Climate Change in Puerto Rico.” Aksik, http://www.aksik.org/node/3597. Accessed 6 May 2022.
[4] Colle, B. A., Buonaiuto, F., Bowman, M. J., Wilson, R. E., Flood, R., Hunter, R., Mintz, A., & Hill, D. (2008). New York City’s Vulnerability to Coastal Flooding. AMS Journals, 89(6), 829–842.
[5] “How to Prepare for a Hurricane | Hurricane Preparedness 101.” Together Puerto Rico, http://www.togetherpuertorico.com/preparing-for-a-hurricane/. Accessed 6 May 2022.
[6] NYC Emergency Management. “Plan for Hazards – Coastal Storms & Hurricanes.” NYC.gov, https://www1.nyc.gov/site/em/ready/coastal-storms-hurricanes.page. Accessed 6 May 2022.
[7] Palm, Risa, and Michael E. Hodgson. 1993. “Natural Hazards in Puerto Rico”. Geographical Review 83 (3): 280–89. doi:10.2307/215730.[8] “Sandy Recovery & Progress.” NYC.gov, https://www1.nyc.gov/site/nycha/about/recovery-resiliency.page. Accessed 6 May 2022.
[8] “Sandy Recovery & Progress.” NYC.gov, https://www1.nyc.gov/site/nycha/about/recovery-resiliency.page. Accessed 6 May 2022.
By: Grace Axlund
0 notes
Text
So, Jordie got the gun working for Trixie. That's not going to end well. I'm still saying that thing is going to blow up in Beatrix's face. And take her out with it.
I absolutely should have predicted that RAPTON was the spy for the ITRF. For some reason, LaRow made sense to me, especially considering her refusal in the last episode. But Rappy disappeared, so I should have known.
He's absolutely only going to help out the 1 time. For now. He might help out again in s2.
Ras is absolutely going to manipulate the guard into thinking he was wrongfully imprisoned by Trixie. And he's going to get out of there.
Something is up with Riyu. Other dragons seem to really listen to him. I'm pretty certain he's a Source Dragon, but like an Alpha Source Dragon. Like HTTYD Alpha. If that makes sense?
Ok, I'll be finishing off s1 tomorrow. So, until then!
#liveblogging#ninjago dragons rising#dragons rising#season 1#episode 19#we are all dragons#ndr s01e19#ndr predictions
23 notes
·
View notes
Text
Who Decided 20% Makes a Bull or Bear Market?

No one. And I don’t care for it. But since most everybody else in the world defines Bulls and Bears by 20% I have learned to deal with. But I still disagree and don’t use it. I think 20% is an arbitrary number. In reality bull and bear markets are more nuanced than an arbitrary level like 20%. Why 20%? Why not 18% or 17.5%? Perhaps it has something to do with classic usury or loan shark rates charging a fifth or 20% of the principal dollar amount lent.
So, regarding the bull market anniversary on Friday, March 9, 2018 (or today for the intraday low on 3/6/2009) is March 9, 2009 the correct way to date the beginning of the current bull? Yes and no. March 9, was an important date in market history. It marked then end of a long severe decline in stock prices, the end of the bear and the beginning of the end of the Great Recession, which the National Bureau of Economic Research (NBER) determined ended in June 2009.
At Stock Trader’s Almanac we have long been proponents of the Ned Davis Research (NDR) definition of bull and bear markets as it combines time and magnitude and has parameters for quick, sharp bulls and bears as well as and longer, shallower cycles:
A Bull Market requires a 30% rise in the Dow Jones Industrial Average after 50 calendar days or a 13% rise after 155 calendar days. Reversals of 30% in the Value Line Geometric Index since 1965 also qualify.
A Bear Market requires a 30% drop in the Dow Jones Industrial Average after 50 calendar days or a 13% decline after 145 calendar days. Reversals of 30% in the Value Line Geometric Index also qualify. This applied to the 1987, 1990 and 1998 high and low.
This is how we have two additional bull/ bear cycles in the 2018 Almanac. In 2011 the US debt crisis had the market in a tizzy and then on August 5, 2011 Standard & Poor’s lowered the credit rating of the United States from AAA to AA+, which pushed the market over the edge culminating in a bear market bottom on October 3, 2011 with DJIA down -16.8% over 157 calendar days from the April 29, 2011 top.
Then in 2015 a collapse in oil prices impacted and depressed other assets as economic struggles in Europe and diverging monetary policy paths of the European Central Bank (ECB) and the US Federal Reserve Bank create uncertainty on The Street. Then 145 days after the market high on May 19, 2015 DJIA was down over 13% on January 20, 2016 we noted that we had reached NDR bear market territory.
However this was a tad premature. Our Bear declaration in January 2016 inspired NDR to clarify their bull and bear market definition criteria. The criteria had not changed, but they have added new language to clarify the definition. NDR contacted us saying they added the following clarifying statement to the criteria:
“Bull and bear markets are measured at peak and trough dates, so both the time and price criteria must be met as of the peak and trough dates.”
So while Bull Market Anniversary well wishes are fine and well this week, we feel the February 2016 bear market low is more instructive. This bull is younger than many realize. The average DJIA Bull Market move on page 131 of the 2018 Almanac is 85.6%. From the low of 15660 on 2/11/16 an 85.6% move would put DJIA at 29000. I’m not predicting 29000 this year per se, but best case scenarios bring that level into play before this bull is over.
2 notes
·
View notes
Text
XDR will converge from different directions: XDR, Open XDR, Native XDR, Hybrid XDR -> XDR
2022 Predictions By Aimei Wei

Initial definitions of XDR envisioned eXtended Detection and Response – a single platform that unified detection and response across the entire security kill chain. According to Rik Turner, who coined the XDR acronym, XDR is “a single, stand-alone solution that offers integrated threat detection and response capabilities.” To meet Omdia’s criteria to be classified as a “comprehensive” XDR solution, a product must offer threat detection and response functionality across endpoints, networks and cloud computing environments.
Gartner’s definition is similar in that it points to features such as alert and incident correlation, built-in automation, multiple streams of telemetry, multiple forms of detections (built in detections), and multiple methods of response. However, Gartner requires XDR to be achieved through consolidating multiple proprietary vendor specific security products.

Open XDR was initially created by Stellar Cyber as with the same features with Gartner except that not all the security products/components have to be from the same vendor, the platform has to be open and integrate with 3rd party security tools. Some components are built in and others are through deep 3rd party integrations.
Open XDR was later on picked up by vendors who purely rely on a wide ecosystem of 3rd party tools for telemetry sources and response without any built-in components.
Forrest’s definition of XDR requires the platform to be anchored around an EDR. It defines Native XDR as EDR integrating with vendor’s own security tools; Hybrid XDR as EDR integrating with 3rd party security tools; SAP (Security Analytics Platform) as a platform without built in EDR, but with built-in NAV and SOAR with 3rd party integrations; and SSA (Standalone Security Analytics) as those purely rely on 3rd party tools for telemetry sources and responses.
We predict that in 2022, XDR will converge from different directions.
XDR will trend to be open and integrate with 3rd party security tools, to allow best of breed tools being used and existing investment preserved. Even those that have historically been closed because they realize they can’t deliver the outcomes enterprises need while attempting to own the entire stack.
XDR doesn’t have to anchor from EDR as long as high efficacy detections are achieved through integration with EDR products
XDR platforms will have some built-in components and others through 3rd party integration. The more built-in components, the more value to get up-front without needing to acquire 3rd party tools. The more out of the box integrations, the more existing investment can be preserved and choices of best of the breed products.
Our definition of XDR is that it’s a unified security incident detection and response platform that:
Provides high-efficacy detections across ALL the data sources: endpoint, network, cloud, application, user, assets, email etc. through either built-in EDR, NDR, CDR, TIP or out-of-the-box third-party integration.
Includes automatic alert correlation across all the data sources and security tools to speed up the validation and investigation, automation of more advanced workflows with sophisticated attack correlation.
Enables automatic responses across different security tools through built-in or out-of-the-box integration with SOAR.
Incorporates threat hunting across all the data sources by allowing analysts to visualize and store large volumes of data for long periods of time through a built-in, next-gen SIEM or out-of-the-box integration with third-party SIEMs.
XDR is about automatic detection and response across the entire attack surface, and that means anything less than everything is not enough. XDR ultimately means “Everything Detection and Response.”
0 notes
Link
1 note
·
View note
Text
Antibiotics, Vol. 7, Pages 12: Diversification of Secondary Metabolite Biosynthetic Gene Clusters Coincides with Lineage Divergence in Streptomyces
We have identified Streptomyces sister-taxa which share a recent common ancestor and nearly identical small subunit (SSU) #rRNA gene sequences, but inhabit distinct geographic ranges demarcated by latitude and have sufficient genomic divergence to represent distinct species. Here, we explore the #evolutionary dynamics of secondary metabolite biosynthetic gene clusters (SMGCs) following lineage divergence of these sister-taxa. These sister-taxa strains contained 310 distinct SMGCs belonging to 22 different gene cluster classes. While there was broad conservation of these 22 gene cluster classes among the genomes analyzed, each individual genome harbored a different number of gene clusters within each class. A total of nine SMGCs were conserved across nearly all strains, but the majority (57%) of SMGCs were strain-specific. We show that while each individual genome has a unique combination of SMGCs, this diversity displays lineage-level modularity. Overall, the northern-derived (NDR) clade had more SMGCs than the southern-derived (SDR) clade (40.7 ± 3.9 and 33.8 ± 3.9, mean and S.D., respectively). This difference in SMGC content corresponded with differences in the number of predicted open reading frames (ORFs) per genome (7775 ± 196 and 7093 ± 205, mean and S.D., respectively) such that the ratio of SMGC:ORF did not differ between sister-taxa genomes. We show that changes in SMGC diversity between the sister-taxa were driven primarily by gene acquisition and deletion events, and these changes were associated with an overall change in genome size which accompanied lineage divergence. http://bit.ly/2BXj6lN #MDPI
0 notes
Photo

Build delivery predictability and reduce RTO by providing next-day and 2-day delivery. Auto reattempt deliveries with our NDR management tool. Choose the best, Choose Quickshift!
0 notes
Text
The Cybersecurity Stories We Were Jealous of in 2019
Cyber! Cyber! Cyber! We all love information security here at Motherboard. It seems no one can have enough cyber in their lives these days.
Yet, 2019 was actually kind of a slow year in terms of cybersecurity news, perhaps because hackers are saving their best shots for 2020. Still, there were some truly astounding and enthralling stories published on the internet about hackers, digital privacy, and surveillance.
As we did last year, we’re rounding up our favorite stories not written by us. We call it Motherboard’s Cyber Jealousy list, our annual hat tip to our awesome competitors, friends, and enemies at other outlets. Thanks for being awesome and pushing us to do better and working with us to give readers important stories they need to care about. We love scooping you, we hate being scooped by you, but in the end we’re all working toward the same goal: writing impactful cybersecurity stories in the public interest.
Without further ado, here’s our list of the best infosec stories published elsewhere. Enjoy and see you in 2020!
The Untold Story of the 2018 Olympics Cyberattack, the Most Deceptive Hack in History
By: Andy Greenberg
This is the blow-by-blow account of how Russian government hackers targeted the Pyeongchang's Winter Olympics in South Korea, shutting down part of its IT infrastructure during the opening ceremony. The most surprising part of this hack is that the perpetrators cleverly hid their provenance, with layers of false flags to deceive investigators looking into the hack. The hackers, for example, used a data-deleting tool used by North Korean government hackers, and password-stealing code previously used by Chinese government hackers in an attempt to lead investigators to point the finger to the wrong country. In this story, an excerpt from his new book Sandworm, Andy Greenberg tells us how researchers were able to unravel the web of planted clues and find the real culprits.
The Sinkhole That Saved the Internet
By: Zack Whittaker
In May of 2017, an unprecedented ransomware outbreak hit hundreds of thousands of computers all over the world, including systems belonging to the UK’s National Health Services, forcing health care facilities to turn patients away and close emergency rooms. The virus was called WannaCry, and its viral spread was stopped by two clever security researchers who realized the malware included a kill-switch. This enthralling piece details for the first time what it was like to stop WannaCry directly from the point of view of the two researchers, Marcus Hutchins—aka MalwareTech—and Jamie Hankins.
Inside The UAE’s Secret Hacking Team Of American Mercenaries
By: Christopher Bing and Joel Schectman
DarkMatter, the shadowy cybersecurity company from Dubai, has long been under scrutiny for its alleged shady practices. Chris Bing and Joel Schectman published this bombshell of a story that finally showed faces and concrete stories: the company was using former US intelligence operatives to run espionage operations on behalf of the United Arab Emirates government. A former NSA analyst went on the record for this story, providing documents and other data that showed how American DarkMatter employees targeted journalists and human rights workers, sometimes using a sophisticated iPhone hacking tool to hack their targets. The Reuters duo followed up this deep-dive with another scoop just a few days ago, revealing that White House cybersecurity veterans played a key role in building the UAE’s intelligence apparatus in the late 2000s and early 2010s.
Beto O’Rourke’s Secret Membership In America’s Oldest Hacking Group
By: Joseph Menn
This incredible story about Texas politician Beto O’Rourke’s membership in one of the oldest American hacking collectives, Cult of The Dead Cow, is a wild ride. As part of the hacktivist group in the 1980s, O’Rourke wrote a murder fantasy in which the narrator drives over children, imagined a world without money, and stole long distance phone calls. He didn’t actually hack much, but he was an active member and attended hacker conferences. His membership in the group was kept secret for decades, until Joseph Menn revealed it in this article, part of his book on the hacktivist group. O’Rourke’s presidential bid is over, but, perhaps, his story will help normalize how Americans see hackers in the future.
Undercover Agents Target Cybersecurity Watchdog
By: Raphael Satter
This was legitimately one of the most grotesque stories of the year. Spies working for a private intelligence company targeted researchers at Citizen Lab, a digital rights watchdog known for tracking spyware companies. The spies approached the researchers under false premises and were unmasked when one of the targets, John Scott-Railton, worked with journalist Raphael Satter to set up a sting operation against the spies. When Scott-Railton met in New York City with one of the spies, Satter crashed the meeting along with videomakers to confront the spy. The spy’s operation was so weird and sloppy that Satter described it as “half John Le Carré and half Mr. Bean.”
Inside Google’s Team Fighting to Keep Your Data Safe From Hackers
By: Robert McMillan
This was a good profile of a little-known Google security team that tracks government hackers: the Threat Analysis Group, or TAG. In this piece, The Wall Street Journal’s Robert McMillan scored one of the first ever interviews with TAG’s leader, Shane Huntley, who is a former Australian government hacker himself. Huntley talked about what his team does and what hackers they track, sharing details about some of the operations they derailed for the first time. (Note: Huntley later came onto our podcast CYBER.)
Attacking the Heart of the German Industry
By: Hakan Tanriverdi, Svea Eckert, Jan Strozyk, Maximilian Zierer, and Rebecca Ciesielski
It's always impressive and rewarding when reporters take tools usually reserved for cybersecurity professionals but use them to uncover something journalistically. In this case, a joint investigation by German public broadcasters BR and NDR found that Chinese state-backed hackers had broken into German companies. They didn't do this based entirely on talking to sources, but by scanning company servers for signs of Chinese malware.
"In all cases where Winnti was installed, the malware will respond to our request. This tells us: That company has been hacked," the article reads, referring to the specific strain of malware.
A Multimillionaire Surveillance Dealer Steps Out Of The Shadows . . . And His $9 Million WhatsApp Hacking Van
By: Thomas Brewster
Perhaps the most bizarre cyber story of the year. This is the profile of a shady Israeli surveillance maker, who sells a $9 million hacking van, which is supposed to be able to hack nearby phones equipped with WhatsApp—“the A-Team truck spliced with a Bond car,” as the author of the piece, Thomas Brewster, put it. In the article, the surveillance maker, named Tal Dilian, defended his industry’s reputation, saying people like him, or the controversial spyware maker NSO Group, “are not the policemen of the world, and we are not the judges of the world,” meaning it’s up to their customers to do the right thing, they just provide the tools. Dilian clearly is a believer, as he agreed to show Brewster the van for an accompanying video.
These Hackers Made an App That Kills to Prove a Point
By: Lily Hay Newman
Medical devices’ security has been under scrutiny and under suspicion for a few years now. But this story drives home how dangerous flaws in these devices can be. A group of researchers made an app that can remotely control insulin pumps, potentially giving hackers the ability to hurt—and perhaps kill—patients. "We’ve essentially just created a universal remote for every one of these insulin pumps in the world," said one of the researchers in what’s truly a terrifying quote captured by Lily Hay Newman.
The Inside Story Of The World's Most Dangerous Malware
By: Blake Sobczak
In 2017, an oil refinery in Saudi Arabia was hit by what some described as the most dangerous malware ever used, which had the ability to interact with the plant’s safety systems, potentially causing physical damage and hurting people in the refinery. At the time, the identity of the victim, as well as many of the details of the attack, stayed out of the public’s view. In this long and well-sourced feature, E&E News’ Blake Sobczak revealed the name of the company hit by the malware, the oil giant Petro Rabigh, the people who investigated it, and how the hackers played cat-and-mouse with attempts to kick them out of the company’s network. This story wasn’t easy, as most of the people and organizations involved declined to talk to Sobczak on the record, as it usually happens in such high-profile cyberattacks.
How The U.S. Hacked ISIS
By: Dina Temple-Raston
It’s very rare for hackers who work for intelligence agencies—especially those fighting terrorists—to talk to journalists, given that their work is often classified. NPR veteran reporter Dina Temple-Raston somehow convinced several people who worked for the U.S. military on operations to hack ISIS to do just that. In this story, she reveals how the U.S. Cyber Command and the NSA identified and took down key infrastructure used by the terrorist organization at the height of its popularity—an absolute must-read.
The Cyber speaks: What will actually happen in 2020
By: Kelly Shortridge
As we approach the end of the year, cybersecurity companies—for some reason I can’t really fathom—rush to compile relatively vague, mostly meaningless predictions of what will happen in the hacking world. It’s a yearly tradition very few cherish. No one made fun of it in such a smart was as Kelly Shortride did in this article on Cyberscoop. Shortridde forced a bot to read more than 1,000 (!) cybersecurity predictions and then come up with its own predictions using machine learning. The results are simply hilarious. “Don’t be chilled by what you don’t know. You ain’t cybersecurity.” Amen, dear bot.
Ghost Ships, Crop Circles, And Soft Gold: A GPS Mystery In Shanghai
By: Mark Harris
This story has it all. How do you not want to read this after seeing that headline? Summarizing it may be spoiling it, so just trust us and read this bamboozle of a piece.
Tracking Phones, Google Is a Dragnet for the Police
By: Jennifer Valentino-DeVries
These two companion pieces are as shocking as well reported by veteran Jennifer Valentino-DeVries, someone who was writing about digital surveillance way before many cared about it. In this investigation, she reveals how investigators are using precise locations gathered by Google to track criminals all over America. These investigations relied on a giant, and previously unknown, Google database eerily called Sensorvault, which “turn the business of tracking cellphone users’ locations into a digital dragnet for law enforcement,” as the Times put it.
All The Incredible Ring Scoops All Over The Internet
By: Sam Biddle; Dell Cameron and Dhruv Mehrotra; Kari Paul; Alfred Ng
Ring, Amazon’s dystopian front-door camera surveillance startup, has really been one of the hottest stories of the year. It’s been thoroughly written about and meticulously dissected by so many journalists that it would be almost unfair to single out just one story. So we decided it’s better to name a bunch of them (and forgive us to remind you to read Motherboard own series by Caroline Eha):
Amazon’s Ring Planned Neighborhood “Watch Lists” Built On Facial Recognition
Ring’s Hidden Data Let Us Map Amazon's Sprawling Home Surveillance Network
Everything Cops Say About Amazon's Ring Is Scripted or Approved by Ring
Amazon's Doorbell Camera Ring Is Working With Police – And Controlling What They Say
Ring Let Police View Map Of Video Doorbell Installations For Over A Year
Subscribe to our cybersecurity podcast, CYBER.
The Cybersecurity Stories We Were Jealous of in 2019 syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes