#latest Cyber tools
Text


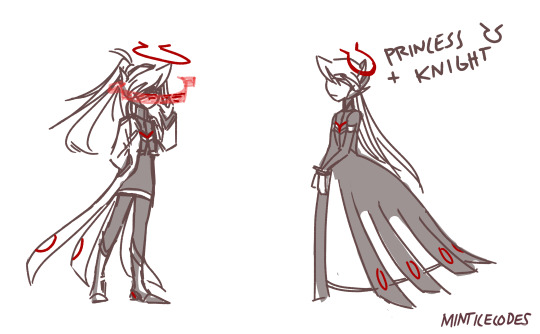



MMZ roleswap au where Copy X tries to defeat Ciel and Omega.
Lore stuff under the cut:
Ciel:
Ciel's the latest in a line of Neo Arcadia's rulers raised and genetically altered with a biocode to control Omega, and thus all reploids.
Instead of doing that Ciel uses her links to reploids as a bunch of cameras and weapons to control the human and reploid populations.
She met Alouette before her brain got stitched to Omega's and was the only person to care for her wellbeing.
It /seems/ like she's using Omega as a tool but she still cares for his safety and gets scared when he's damaged. She sees him as her only reliable partner in this mess. Without him, she's alone.
If this were an actual production you wouldn't hear her voice until the very end. She talks through having nearby reploids talk in legion-speak.
Copy X:
As the only immune reploid, X has a difficult job ahead.
He wakes up with a massive memory gap, red eyes, a higher pitched voicebox, and a cryptic cyber elf insisting he get up and fight.
Cyber Elf X takes a more active role since he can grant mass resistance to allies.
Unlike with Zero, Cyber Elf X has much less patience or fondness guiding Copy X, since all he can see is his own mistakes and past self.
Towards the end it's revealed he's a copy of X created by Ciel before she linked with Omega, in an attempt to have some way to oppose the two and any future for Neo Arcadia's government.
#mega man#mega man zero#rockman zero#x#copy x#ciel mmz#alouette mmz#alouette#omega#omega zero#mega man zero spoilers#tw child death#tw child injury#mmz spoilers#mega man fanart#tw eyestrain#this started because I thought Weil's tentacle robe could make a cute dress#and i kinda wanted to draw Ciel being mean.#but then with a lot of villain AUs I feel eh because it doesn't feel like the same character anymore#so thus the whole convoluted backstory to try and explain the differences
151 notes
·
View notes
Text

Northrop Grumman releases update on the program and progress of the B-21 Raider
Fernando Valduga By Fernando Valduga 09/192023 - 6:00 p.m. in Military
At last week's Air, Space and Cyber Conference of the Association of Air and Space Forces, the leadership of the U.S. Air Force and the Department of Defense discussed the B-21 program in terms of effective program management, production readiness, and early integration of support elements as fundamental to the effective delivery of operational capacity.
In addition, the U.S. Air Force announced that Northrop Grumman has driven the B-21 engines, a significant milestone in the aircraft's ground testing program. Although the first flight of the B-21 is a data-driven event closely monitored by Northrop Grumman and the U.S. Air Force, key decisions and programmatic strategies are putting the program in a positive position in the future.
Production representative aircraft

A key to the overall program strategy established from the beginning was to build a first test article representative of production. Instead of a prototype, the first test article of the B-21 Raider was built with rigorous production processes on the same manufacturing line with the same tools that will be used to continue to shape the B-21 fleet. Exclusive to aircraft development programs, the first test article of the B-21 is equipped with its primary mission systems, such as communication and navigation systems.
The decision to build a highly representative test vehicle will allow Northrop Grumman and USAF to conduct a robust flight test campaign and discover what is necessary, in alignment with the program's execution strategy from the beginning.
"The B-21 program is an excellent example of how the industry can be a capable partner in providing systems that meet critical needs efficiently. The first test aircraft was built by our technicians using factory production processes; we are doing this learning and refinement in parallel, which will allow us to reach a stable and constant production more quickly," said Tom Jones, president of the sector of Northrop Grumman Aeronautics Systems.
Support influencing design

In addition to focusing on production in the early stages of the program, the B-21 program took into account the support during the design phase. In addition to boosting long-term efficiency, this approach also produces more short-term benefits.
“Given Northrop Grumman's focus on support at the beginning of development, the B-21 is much more advanced in technological data than we would normally expect in a new program at this time,” said Doug Young, vice president and general manager of the division, Northrop Grumman Aeronautics Systems. "Content development such as product support, material preparation and training is well underway, giving the B-21 an initial advantage in support and support operations before delivery to the user community."
Proven fidelity of the digital model

Developed with a digital line throughout the life cycle of the program, the B-21 Raider uses the latest in digital tools and resources, from design to development and testing and, finally, in support. This focus on the B-21 digital ecosystem, along with investment in laboratories and testing facilities, allowed the Northrop Grumman team to digitally model the B-21's performance before physical movements or needs.
As the B-21 undergoes several ground tests, digital models are surpassing industry standards with twice the accuracy. This is evident in the initial tests, with the first test article presenting the expected performance; the tests of the engines, weapon compartment doors, landing gear and control services demonstrated the expected results and indicate the effectiveness and value of digital modeling.
Defining the capacity of the sixth generation

The B-21 Raider is the world's first sixth-generation aircraft, supported by decades of experience in stealth technology and optimized for cutting-edge threat environments. With its open architecture and cloud technology application, the B-21 Raider was built for seamless incorporation of software updates and new features. Northrop Grumman has already demonstrated that the B-21 will be able to integrate third-party technology, supporting the maximum focus of the program on modernization and the need to keep the weapons system at the forefront of future threats.
The new approach of the program to the execution of the program, together with the effective application of digital technologies, demonstrates a focus on delivering exceptional capacity, effectively and efficiently.
Tags: Military AviationB-21 RaiderNorthrop GrummanUSAF - United States Air Force / U.S. Air Force
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
MILITARY
Philippine Air Force introduces Cessna C-208B surveillance aircraft donated by the U.S.
19/09/2023 - 14:00
HELICOPTERS
IMAGES: Bell presents the Czech AH-1Z and UH-1Y combat helicopters
19/09/2023 - 12:00
MILITARY
Paramount declares first Mwari operational and reveals additional sales for two operators
19/09/2023 - 09:00
MILITARY
Australia will upgrade the P-8A Poseidon fleet and acquire the fourth MQ-4C Triton
19/09/2023 - 08:14
AIRCRAFT ACCIDENTS
Wreckage of the U.S. Marine Corps F-35B jet is found in South Carolina
18/09/2023 - 23:26
MILITARY
VIDEO: USAF receives the first T-7A Red Hawk in the production standard
09/18/2023 - 19:30
21 notes
·
View notes
Text
Mobile App Maintenance and Support: Ensuring a Seamless User Experience

In today’s digital landscape, mobile applications have become an integral part of our lives. From social networking to e-commerce and productivity tools, mobile apps have transformed the way we communicate, work, and interact with the world. However, developing a successful mobile app is just the first step; to ensure its long-term success, regular maintenance and reliable support are crucial.
The Importance of Mobile App Maintenance
Mobile app maintenance refers to the process of updating, optimizing, and enhancing an application to meet changing user expectations, market trends, and technological advancements. It involves fixing bugs, addressing performance issues, and adding new features to keep the app relevant and engaging.
Regular maintenance is essential for several reasons:
1. Bug Fixes and Performance Optimization
No app is perfect, and bugs are an inevitable part of the development process. Regular maintenance allows developers to identify and fix these bugs promptly. This ensures that users have a smooth and seamless experience while using the app. Moreover, performance optimization helps in enhancing the app’s speed, responsiveness, and overall user satisfaction.
2. Compatibility with OS Updates
Operating system updates are released frequently, introducing new features and security patches. Mobile app maintenance ensures that your application remains compatible with the latest versions of operating systems, such as iOS and Android. Failure to update the app may lead to compatibility issues and a deteriorating user experience.
3. Security Enhancements
With the increasing number of cyber threats and data breaches, maintaining robust security measures is of paramount importance. Regular maintenance allows developers to identify vulnerabilities and apply necessary security patches, reducing the risk of unauthorized access or data leakage. This helps in building trust among users and safeguarding their sensitive information.
4. User Feedback and Feature Updates
Users provide valuable insights and feedback on the app’s performance, usability, and desired features. Mobile app maintenance enables developers to gather this feedback and make informed decisions regarding feature updates and improvements. By addressing user needs and expectations, you can enhance user engagement and increase user retention.
The Role of Mobile App Support
Mobile app support complements maintenance efforts by providing assistance and resolving user queries and concerns. Effective app support ensures a positive user experience and builds customer loyalty. Here are some key aspects of mobile app support:
1. Prompt Issue Resolution
Users may encounter technical issues, difficulties in navigating the app, or have questions about its functionality. A responsive support team can address these concerns promptly, providing solutions and guidance to users. This helps in reducing user frustration and ensures that they continue to use and recommend the app.
2. Help Desk and Documentation
A comprehensive help desk and well-documented resources, such as FAQs, tutorials, and user guides, can empower users to find answers to common questions on their own. This reduces the burden on the support team and enables users to troubleshoot minor issues independently, thereby improving their overall satisfaction with the app.
3. User Engagement and Feedback Management
App support channels provide an opportunity to engage with users, understand their needs, and gather feedback. Support agents can collect valuable insights about user preferences, pain points, and feature requests, which can inform future maintenance and development efforts. By actively listening to users and acting upon their feedback, you can foster a sense of community and loyalty among app users.
Conclusion
Mobile app maintenance and support are indispensable for ensuring the longevity and success of your application. Regular maintenance allows you to fix bugs, optimize performance, enhance security, and incorporate user feedback. Meanwhile, effective app support ensures prompt issue resolution, empowers users with self-help resources, and facilitates user engagement. By prioritizing these aspects, you can deliver a seamless user experience, build customer loyalty, and stay ahead in today’s competitive app market.
Source
#AppDevelopment#WebDevelopment#MobileApps#WebApps#SoftwareDevelopment#UIUXDesign#MobileDevelopment#WebDesign#CodeLife#TechSolutions#AppDesign#MobileTech#WebDev#DigitalTransformation#ResponsiveDesign#Innovation#TechIndustry#AppSolutions#WebSolutions#CodeNerds
22 notes
·
View notes
Text
It Was The Night Of The Meteor Shower
Inspired loosely by a prompt, Danny’s friends and family did not survive the events of The Ultimate Enemy. Knowing what he could’ve been, he decides to find his own way through his grief. Although the ghosts of future are dealt with, he now uncovers ghosts of past, and it seems he misunderstood the ghosts in the present.
Pov: Danny going through quite possibly the worst week of his life whilst reliving the worst days of his life.
Link to prompt!
I’ve been thinking back on life lately. Like, was any of that a dream, or was it too real?
- - -
The lab in the basement was always a little unnerving to be in. Exposed wires on unfinished projects, cables running haphazardly across the ground, loose tools scattered everywhere, honestly it’s always been a mess at best. If this were a well known work place, our house would’ve definitely been condemned by now! Walking in now, I immediately regret my decisions up till now. Mom and dad’s latest project may be a bust, but they clearly haven’t cleaned up after they were done!
“Woah! Watch your step there!” Tucker jokes, but this isn’t the first time the floor has been covered in some mysterious substance, let alone a step on the stairs. At least Tucker and Sam seem to be enjoying themselves while I’m stuck with keeping them safe, but what are friends for? “Promise you won’t touch anything in here?” It may be obvious, but I have to ask!
Sam tisked at me sarcastically. “Psh, yeah, I was planning on drinking from mysterious flasks myself. Maybe chew on some cables or steal something radioactive.”
“Sam, I don’t think there would be anything radioactive in here! Danny lives just upstairs from here, wouldn’t he get poisoned if there was?”
“Cable,” I pointed out, just as Tucker was about to trip right over an extension cord, pulling him back for good measure. “Look, I know! Technology, cryptozoology, general weird cyber-goth stuff; I get it! But this stuff is dangerous! You’ve gotta trust me here!”
Sure, they understood of course, but it’s not like they were as serious about it. I’ve lived with this, I know how dangerous the equipment here can be, and I know you need to approach everything here with extreme caution. Maybe that’s why they figured they are safe here with me. Maybe they think I can protect them. I honestly have no idea where they got the idea I could protect anyone.
I could see Tucker shaking, trying so very hard not to pick up the gizmos and gadgets littering the lab to look at closer, but it’s for his safety he doesn’t touch them. I keep an eye on him the most, since Sam is only taking pictures with the camera she brought. I think she brought it so we could work on some project for school, but honestly making memories is more fun. Well, more fun when it’s not in your parents’ ghost hunting lab, anyway. I was watching Tucker lean to look at another side of some kind of circuit board when I heard from Sam again.
“Hey wait! Danny, you have a suit?”
“Ah- maybe? Huh?” Startled, I shot to attention to find Sam picking up a black and white jumpsuit. “Wh- hey!”
I rush over to snatch it from her hand. It’s safe, clean in fact, and mostly unworn. The jumpsuit itself may not be dangerous, but it’s definitely a blow to an already fragile ego. I hold it out to try and fold it back up properly, but then I hear a click-snap. The camera shutter makes me flinch and I can’t help but glare at Sam.
“Oops?” Sam grins mischievously, brightly, and knowingly. “Hey! Maybe you can try it on!” I really didn’t want to, and she could see it. Sam followed up her request. “Please? I just wanna see it! I’m sure it looks good on you!”
I sigh, knowing defeat and knowing it’s a fairly innocent request. I can wear a jumpsuit fine, and I know it’s tailored to fit me. Heck, maybe it’ll be easier to prevent disasters if I’m protected too! So I step away to put it on over my clothes, listening in on their conversation about the portal itself. Ugh, the portal.
“So they really made a portal?”
“Supposedly, yeah! His parents really seem to believe it could work!”
“But why? We don’t even know if ghosts are real!”
I zip up the front and walk back over to rejoin the conversation, only to find Tucker leaning in closer. He seems to be listening to the hum of machinery. To be honest, it is a nice sound, pretty calming at times, but it can get annoying and usually indicates something live and active. I pull him away by the shoulder as I chime in.
“Well, I think they tried this in college too. Whatever results they found must’ve proven it in their heads that this could work.”
Sam starts snickering, but I can tell by the look she’s giving me that it’s not something I said. In fact, I know exactly what it is. Without saying anything, she walks over and rips off a huge decal of dad’s face from my chest. Honestly, good riddance. I’m sure dad wouldn’t mind a little defacing, as a treat.
“Oh! Idea!” Tucker snaps and points to me as he continues. “We should get a picture of you in the portal like that!”
“Oh yeah!” Sam chimes in. “Yeah in the hollow space there! With you in the suit, standing in front of all of this machinery here, it would look so cool and, maybe even professional!”
Well, it is an interesting idea, and it would look pretty cool. I agree! The jumpsuit has a hood and goggles to protect your scalp and eyes respectively, but we’re not doing anything except posing for a picture. It would look better without the hood anyway, so I leave it down. With that, Sam and Tucker get in position further away while I step inside.
I’ve never been so close, let alone inside of one of my parents’ inventions. Walking in feels surreal. The lights, dots, and lines running across the walls and ceiling are vast and interwoven, and yet so organized and strategically oriented. It’s like one massive circuit board with so many mechanical bits exposed. Clearly this part of the portal wasn’t meant to be seen. As I’m looking around, I feel something hit my foot as I try to take another step, sending a jolt up my spine in a panic. I feel myself lose balance and instinctively I stumble to catch myself. My hand lands on something, usually it would be fine to hold the wall, but in this case I feel something give under my palm. The hum of the portal grows louder, something whirs to life around me, and taking my hand off the wall reveals a button that reads “on” just below it. Realization hits, and I look to Sam and Tucker, but it’s too late. The last thing I see is their panic reflecting mine, before a sharp pain in the back of my neck introduces itself.
- - -
I woke up on the floor. Reality spun for a bit, and I wasn’t sure where I was. I could feel I was laying on some kind of concrete, and I almost thought I was in the lab again. It would’ve been an easy mistake, but I remember now.
I’m in a warehouse, in some city I’ve never known, and I am alone. Sitting up, I rub my hand through my hair, taking a moment to remember where I am and why. I am here because I, Daniel Fenton, am running for my life. Some strange ghosts have been popping up more and more frequently lately, and they’ve been chasing me far more aggressively than any ghost I’ve ever met. Not even Skulker is as bad as these guys!
In the beginning, there weren’t that many, so they were easy to handle. It was always so strange that they made sounds but never spoke, and they seem to follow pure instinct and emotions. These ghosts don’t banter, have no obvious obsessions, and sometimes I see weird tattoos on them. In fact, there seems to be multiples of them, like blob ghosts. I could fight them off for a while, and I could stop them from attacking random people. A lot of ghost hunters got their infamy and fame for getting rid of these guys too, so it wasn’t that big of a deal. Now, however, it feels like swarms of them are tracking me down at all times.
Just as I was thinking I could never get a rest from them, I feel a chill and see an icy trail of smoke leave my mouth. It seems it’s time to get moving again. I stand and slap myself in the face for a quick burst of energy before transforming. Almost as if on queue, the shadows cast on the ground rise into solid shapes, puffs of black smoke appear and strange knight looking guys drop in the smoke’s place, and all of their beady yellow eyes stare back at me with what I’ve come to understand is killing intent.
Knowing where they are now, I bolt in the opposite direction, flying straight through walls and ceilings, getting as far from my assailants as possible. These guys are persistent, but it seems most of them don’t know how to fly. Problem is, some do. Once I’m outside, I catch sight of some more of the strange ghosts, these ones winged and colorful. “Are the wings really necessary?” No response, as always. It seems there’s only about, say, 7 total? At least 3 different shapes at a glance. Since they’re in the air, it’s probably safe to say a few ecto-blasts should take care of them no harm done!
A bit of blasting, a bit of punching, a few scratches here and there, and the numbers start dwindling! Sometimes after hitting them enough, they’ll poof and turn into weird heart shaped cores, so I stuff them in the thermos! I can’t exactly dispose of them anywhere, not anymore especially, so this thing is getting a bit crowded. The good news is I don’t try to stuff every ghost I see in there. In fact, the number of flying guys has increased dramatically over time already, so I figured I gotta leave again.
Of course they followed me. I tried to stop somewhere for a moment when I thought I got enough distance, but there they are! In the distance! Flying towards me! From this vantage point, it’s easy to see just how many of them there are total. I see the ones from inside the building scrambling out, and I can see many more from the shadows and side streets all skittering out as a crowd. “Oh boy,” here we go again.
- - -
Back then, I woke up to a weird feeling that has since become normal. Everything was light and tingly, and yet so, so weak. I could hear shouting, though too muffled to understand right away. When I finally tried to open my eyes, there was a red flashing, giving way to a green glowing light occasionally. When I came to, I saw Tucker and Sam’s faces, panicked and every crying, yelling and begging for me to say something or give a sign that I was ok. I didn’t feel ok, but I tried at least sitting up at the time.
White hair, white gloves, black suit. There might have been a decal, something tells me there wasn’t, but the decal looks cool enough it might as well have always been there. With help I stood up, and we found our way to a mirror so I could see the damage for myself. I was glowing, but not in a figurative way, but more in the way a hot iron will glow white with heat, or maybe how some toxic goo would glow like a vat of glow-sticks. There were my eyes, staring back like green neon signs on a horribly scratched up sign. As I began to panic, I watched my face twist in the mirror into something else, which only made me panic more. The more I panicked the less human I looked, and the less human I looked the more I panicked, but Tucker helped ground me again. Sam comforted me and had me take deep breaths. Before I knew it, I was myself again, black hair and all. Life had never been the same since that day. The way everyone else in Amity Park know it, that was the night of the meteor shower.
- - -
I finally found another moment’s rest. Ironically, it was the presence of another ghost that calmed my nerves. Unfortunately it was Skulker that decided to stop by.
“Well, you sure are far from home, aren’t you?”
“Can you really say I have a home anymore? You know what happened.”
Of course Skulker knew. He smiled knowingly before thankfully changing the subject. “Those shadow ghosts really have it out for you huh? They should really know their place!”
“Heh, yeah, I wonder what I did to piss so many off them off like this!”
“Oh, what didn’t you do!”
Admittedly, he got a laugh out of me. Feeling a bit more at ease, I sit down on a dumpster nearby. Skulker can make himself comfy on his own. I can’t help finding it strange that Skulker is the only other ghost I know that’s approached me so far. I have been running for a few weeks now, so I have gotten pretty far from the ghost portal, but even then there are other ghosts out there! And yet, it almost feels like everyone’s avoiding me. Skulker is the only one that I’ve been able to confide in lately.
“So what do you think their deal is?” I don’t wanna change the subject yet. I have had plenty of time with these guys and I wish I knew what they’re doing.
“You think I would know? You think I would send them after you like that?”
“What? Nah! You hunt alone don’t you?”
“Exactly that, welp! I don’t need any hounds chasing you and herding you to me! I can and will catch you on my own terms!”
“Oh goodie. Always wanted to be mounted on a wall.” The sarcasm might’ve been lost on Skulker, but it helps me stay calm.
“Maybe some day, but today is not that day! I need you in top performance before I can hunt you down proper! For now, I will help you in your time of need. Hunter’s honor.”
“Hunter’s honor…” I respond a little quieter, honestly not sure if that’s a thing. Something about it feels less like a promise, and more like camaraderie. I suppose I could have been considered a hunter, but, “I can’t be a hunter. I’m not hunting anything.”
“Oh, aren’t you? I believe I remember you were hunting for a solution to your uh… situation…”
My situation is not the same! I can’t say that, I couldn’t even bring myself to answer. My situation… it’s hard to explain, it was a stupid spur of the moment decision. Meeting clockwork, seeing Amity Park’s future, knowing what I could become, it’s all a mess I wish I could forget. I stare at a nearby wall, holding my chest, and feeling not only my pulse but a soft drumming of something foreign and new.
I failed to save them. I failed to save my friends from disaster. I don’t know what gave them the impression I could save them, especially if I was the one that put them in danger. After that explosion, there were no survivors of that accident. I saw some kind of light leaving their bodies, I could hear a soft hum from each of the lights. The hum was familiar, but much quieter than the one I’m familiar with. I was scared, and I didn’t want to lose what little what left of my friends and family. So I grabbed on. I rushed to scoop up those little lights before they flew away or shattered with how young and fragile they were. I held them close in grief, and then, they were gone. I could still feel them now, but they weren’t in my arms anymore. What’s left of everyone is right here, with what’s left of me.
“I can’t find a solution if I’m dead.” I realize my poor choice in wording immediately. “Gone. Turned to dust. Reduced to atoms. Nothing could save them then.”
“Well, you wouldn’t have to worry about your grief anymore if, you know, you weren’t conscious anymore? I could put your cores in a jar and put it up on my mantle!”
“Oh what are you, a heartless?”
A beat. A… Heartless?
“Oh, so the welp doesn’t know grammar either, it seems!”
I don’t respond, and he seems to catch on. Why did I say that? Why is it getting to me? What is a heartless and why does it feel familiar? I try to stand again, but my legs start feeling a bit wobbly, and my head gets fuzzy. A heartless. What is a heartless? Why do I know this? My energy is spent, and as the world goes dark I hear a vague shout, and I hit the ground.
#Danny Phantom#Kingdom Hearts#Dp#Kh#DPxKH#KHxDP#not sure what order you’re supposed to put those crossover tags let alone if those tags exist yet#Danny Fenton#Sora kh#kh Sora#Written#Usually I like making comics for the stories I come up with so I can practice my drawing skills#but in this case I guess I wanted to write it out as a fic proper#I hope this is alright- I put way too much effort into the first 2 paragraphs and I’m still not sure it’s good
9 notes
·
View notes
Text
Tails' Solo Adventure - Prologue Preview
Summary:
“When this is all over… I think I need to go it alone for a while. I can’t grow into my full potential if I always fall back on you.”
Tails decides to embark on his own journey, without Sonic.
Takes place after the events of Sonic Frontiers.
Chapters: 8/?
Rating: Teen And Up Audiences
Read the Full Prologue Here!
“Alright everyone, prepare for landing!”
After what had been hours flying above the ocean, and a pit stop at Angel Island to drop off Knuckles, Tails, the trusty pilot of the Tornado, was ready for descent. He adjusted his goggles, flipped a couple switches, gripped the yoke, and pushed down, feeling the nose of the plane drop ever so slightly. The gust of wind that followed tickled and cooled his fur from the harsh sun above.
In some ways, this was his favorite part about flying, right after takeoff and maintaining altitude. After being stuck within Cyberspace in the Starfall Islands, Tails had realized how much he had taken the sensation of touch, and holding things, for granted, and was happy to be back in his beloved plane. His excitement was only second to the sight of their home came into view - the sparkling waves of the ocean leading them to Green Hill in the distance.
Tails' signal was welcomed by his passengers, Sonic and Amy, who were more than ready to put the latest chapter of their adventures to rest.
“Sonic, you might want to hold on!” Tails called out over the roar of the Tornado's engine.
“Hold on?” Sonic, standing on the left wing of the plane, looked over at Tails with that charismatic grin of his. “But I’m having such a great time up here!” Playfully, Sonic spread his arms out in defiance. With the wind blowing through his quills, and the sun glowing against him, it was as if he had never been touched by the cyber corruption that had nearly taken him over just earlier.
“Sonic, be careful!” Amy pleaded from the passenger’s seat. While Sonic was quick to move on, for Amy, Sonic just fought tooth and nail against the largest threat to humanity to date about seven hours ago. Sure, they were used to saving the world by the skin of their teeth, but the last thing she needed was for Sonic to meet his end just because he was acting reckless. “You know there’s just a huge ocean below us, right?”
“Eh, fiiine,” Sonic sighed, rolling his eyes but not really - he knew Amy was just looking out for him. With an easygoing smile, he lowered himself from standing to sitting on the wing of the plane, hands gripping the edge. “But even if I fell, Tails would’ve caught me, right buddy?”
Tails caught Sonic’s mischievous smile in a brief glance, before focusing on the skies ahead and the nose of the plane. “Mm, if I felt like it,” he joked, shooting Sonic an equally smug look. Then, quickly, “Nah, I’m kidding- of course I would!”
The three of them laughed, as the plane soared steadily towards the landscape of Green Hill. The air felt sweet with the scent of the ocean, the sun beginning to dip towards the horizon. Tails savored this moment, for once they landed, it wouldn't be long until they all went their own adventures.
--
After what was at least a solid four hours of tuneups, minor repairs, and refueling, Tails slumped himself into the chair of his workshop’s hangar, hands and face covered in sweat and grease. Letting out a sigh, he hung his head back to stare at the ceiling, and wiped the back of his hand over his forehead, feeling the sweat beneath his fur. This was pretty standard routine after an adventure, but it didn’t make it less taxing.
Besides, he needed to make sure the Tornado was in tip-top shape before he left tomorrow morning. His duffel bag was packed next to his desk with all the essentials — some food and water for the road, toothbrush, some advanced weapons, basic tools, and a jacket just in case, to name a few. It was going to be one of his first adventures on his own, without Sonic, or really, anyone he knew. And while he knew there was no rush to leave, Tails wanted to just get a head start and do something meaningful and heroic, and take a risk, instead of hanging out at the sidelines again. At first, Tails didn't know where to go - he thought about approaching this like Sonic, just taking himself wherever the wind led to. But when you needed to think about fueling a plane, and regular maintenance, he decided that Station Square was a good place to start, and he could figure things out from there. Adventure seemed to follow Sonic, so maybe that rubbed off on him, too.
Beneath the anticipation though, he was also dreading it. Was he really ready for this? While he had his heroic moments, Tails wasn't proud to admit the number of times he cowered in fear behind Sonic, or ended up needing to be rescued altogether- in his own words, he was wildly inconsistent. The decision to call this off was tempting.
But no, he needed to do this. He can't keep relying on Sonic to save him forever. He knew that Sonic was always supporting him, and believed in Tails more than Tails believed in himself. He needed to put everything he’s learned to the test, and see what he’s truly capable of.
The weight of it all was coming down on Tails as he sank into the chair, staring at the ceiling. Slowly, he closed his eyes, letting out a deep, full body sigh. This chair felt softer, more comfortable than usual. He could almost fall—
“Hey Tails!”
Sonic’s voice rang out from the front of the hangar. It jolted Tails awake, as he sat up straight with his heart racing, a fox in the headlights. “Amy’s heading out soon!”
That’s right, Amy was coming up today to say goodbye. Not even four days after they’ve arrived back, Amy was headed on a road trip with Sticks and Cream towards Spagonia. According to Amy, it was only going to be the best girls trip ever.
“Coming! Give me a minute!” Tails called out, pulling himself up from his chair. He quickly made his way to the sink in the back of the room, caught a glance at the dark grease and dust that caked his fur, and cringed. Yeah, he was going to need a little longer than a minute to clean himself up.
Read the Full Prologue Here!
#tails the fox#miles 'tails' prower#sonic frontiers#sonic the hedgehog#sth#i do plan on putting the next chapter out soon!!#I spent a lot of time actually revising these chapters#which is why I haven't actually updated with a new chapter in a month#added like an additional 7k words#hope you enjoy!
7 notes
·
View notes
Text
Cisco Exposes State-Sponsored Hackers Exploiting Cisco Firewall Zero-Days CVE-2024-20359

Cisco has uncovered a sophisticated state-backed hacking group exploiting two previously unknown vulnerabilities in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023. The malicious cyber espionage campaign, dubbed "ArcaneDoor," has successfully infiltrated government networks worldwide, compromising crucial security infrastructure.
Weaponizing Zero-Day Exploits for Cyber Espionage
The threat actors, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, leveraged two zero-day vulnerabilities—CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—to breach Cisco firewalls. These previously undisclosed security flaws allowed cybercriminals to deploy sophisticated malware implants, granting them persistent access and remote control over compromised devices.
One implant, dubbed "Line Dancer," is an in-memory shellcode loader capable of executing arbitrary payloads, disabling logging mechanisms, and exfiltrating captured network traffic. The second implant, a persistent backdoor named "Line Runner," incorporates multiple defense evasion techniques to evade detection while enabling the attackers to execute arbitrary Lua code on the hacked systems.
Hallmarks of State-Sponsored Cyber Threats
Cisco's analysis reveals that the threat actor's bespoke tooling, espionage focus, and in-depth knowledge of targeted devices are hallmarks of a sophisticated state-sponsored actor. The malicious actors exploited their access to exfiltrate device configurations, control logging services, and modify authentication mechanisms for lateral movement within compromised environments.
Urgent Call for Mitigation and Enhanced Security
In response to this severe cyber threat, Cisco has released security updates to address the two zero-day vulnerabilities and strongly recommends that customers promptly upgrade their ASA and FTD devices to the latest patched software versions. Administrators are also urged to monitor system logs for suspicious activity, implement strong multi-factor authentication, and ensure devices are securely configured and logged to a centralized location.
As state-sponsored cyber threats continue to escalate, organizations must prioritize proactive security measures, regular patching, and robust incident response strategies to safeguard critical infrastructure and sensitive data. Complacency in the face of such advanced cyber espionage campaigns can devastate national security and organizational resilience.
Read the full article
2 notes
·
View notes
Text






4 September 2023: Crown Prince Hussein attended the opening of the Artificial Intelligence in Defence Technologies and Cyber Security Exhibition and Conference (AIDTSEC 2023) at the King Hussein bin Talal Convention Centre at the Dead Sea.
The conference and exhibition showcases the latest technologies and developments in AI, aimed at finding dynamic solutions for operations in defence, cyber security, and big data analysis and protection. (Source: Petra)
Speaking at the opening, Assistant to the Chairman of the Joint Chiefs of Staff for Planning and Defence Resources Brig. Gen. Tawfiq Marzouq said there is a global need for cooperation and expertise exchange to counter major threats related to data and information security.
For his part, National Cybersecurity Centre Director Bassam Maharmeh said AI models can help pre-empt threats and crises, noting that the centre employs AI tools in various operations.
The AIDTSEC 2023 conference, first launched two years ago, is aimed at the exchange of expertise between innovators, experts, and start-ups working in defence AI and cyber security technologies.
A number of ministers and senior officers and officials attended the opening ceremony.
7 notes
·
View notes
Text
10 Web Developer Secrets You Need to Know for Success in 2024

In the fast-paced world of web development, staying ahead of the curve is essential for success. As we venture into 2024, it's crucial to uncover the latest secrets and strategies that can propel your web development endeavors to new heights. Let's delve into ten invaluable insights that every web developer should know for a prosperous year ahead.
Embrace Progressive Web Apps (PWAs)
In 2024, the prominence of Progressive Web Apps (PWAs) continues to soar. These innovative web applications offer users an immersive, app-like experience directly from their browsers. By embracing PWAs, developers can enhance user engagement, improve performance, and seamlessly integrate features like push notifications and offline functionality.
Prioritize Mobile-First Design
With mobile devices dominating internet usage, prioritizing mobile-first design is non-negotiable. Crafting websites with mobile users in mind ensures optimal responsiveness and usability across various devices and screen sizes. Embrace responsive design principles to deliver a seamless browsing experience that caters to the needs of your audience.
Harness the Power of AI and Machine Learning
AI and machine learning technologies are revolutionizing the field of web development. From personalized content recommendations to intelligent chatbots, incorporating AI-driven solutions can elevate user experiences and streamline processes. Explore AI-powered tools and frameworks to unlock new possibilities and stay ahead of the competition.
Optimize for Core Web Vitals
In 2021, Google introduced Core Web Vitals as essential metrics for evaluating user experience. To rank higher in search results and provide users with a smoother browsing experience, prioritize optimizing for Core Web Vitals. Focus on metrics like loading speed, interactivity, and visual stability to ensure your website meets Google's standards and delights visitors.
Implement Voice Search Optimization
The prevalence of voice-enabled devices continues to grow, shaping the way users interact with the web. To capitalize on this trend, implement voice search optimization strategies to make your website more discoverable through voice queries. Consider natural language patterns and long-tail keywords to optimize content for voice search queries effectively.
Enhance Security with HTTPS
Security remains a top priority for web developers, especially in an era marked by increasing cyber threats. Transitioning your website to HTTPS not only encrypts data transmitted between the user's browser and your server but also instills trust and credibility among visitors. Prioritize security protocols to safeguard sensitive information and protect your users' privacy.
Leverage Content Delivery Networks (CDNs)
Content Delivery Networks (CDNs) play a pivotal role in optimizing website performance and reliability. By distributing content across multiple servers worldwide, CDNs reduce latency and ensure faster loading times for users across the globe. Integrate CDNs into your web development workflow to deliver content swiftly and efficiently, regardless of geographical location.
Stay Abreast of Accessibility Standards
Accessibility is an integral aspect of web development, ensuring that websites are inclusive and accessible to all users, regardless of disabilities or impairments. Stay abreast of accessibility standards such as the Web Content Accessibility Guidelines (WCAG) and implement best practices to make your website more usable and navigable for everyone.
Embrace Serverless Architecture
Serverless architecture offers a streamlined approach to web development, eliminating the need to manage servers and infrastructure manually. By leveraging cloud-based services and functions, developers can focus on writing code and delivering value without worrying about scalability or maintenance. Embrace serverless architecture to enhance agility, reduce costs, and accelerate development cycles.
Cultivate Continuous Learning and Adaptation
In the dynamic landscape of web development, continuous learning and adaptation are paramount. Stay curious, explore emerging technologies, and embrace new methodologies to evolve with the industry's ever-changing demands. Cultivate a mindset of lifelong learning, experiment with new tools and techniques, and adapt your skills to thrive in the digital ecosystem.
As we navigate the complexities of web development in 2024, embracing these secrets and strategies can position you for success in an ever-evolving landscape. By staying ahead of trends, prioritizing user experience, and leveraging innovative technologies, you can unlock new opportunities and achieve remarkable feats in the realm of web development.
#web development company#app development#web development services#web development#mobile app development
2 notes
·
View notes
Text
Even before U.S. Air National Guard member Jack Teixeira was arrested on Thursday as the leaker of dozens of classified government documents that have made their way around the internet in recent weeks, the inevitable comparisons with Chelsea Manning and Edward Snowden suggested that he was the latest in a long line of mass leakers of intelligence. As one journalist reported on the most generic of similarities, “Like Manning and Snowden, Teixeira has a military or intelligence tie as a member of the Massachusetts Air Force National Guard.”
Indeed, in the last decade, a new digital generation of insider threat has emerged to challenge secrecy in the U.S. intelligence community, a phenomenon that author James Bamford has described as a “uniquely postmodern breed of whistleblower.” That’s true as far as it goes, but Teixeira should not be thought of in this vein. It would be like saying a Yugo is like a Mercedes because they both have four wheels and an engine. Sure, everyone working in the U.S. Defense Department’s sprawling intelligence apparatus is part of that bureaucracy, but that’s a tautology. It would also be correct to observe that nearly every spy in American history has had a “military or intelligence tie” as well, but that doesn’t explain much in the Teixeira case.
The real but superficial comparisons to leakers like Snowden and Manning classify Teixeira as a mass leaker on a personal crusade. But this is incorrect. Snowden and Manning leaked classified documents to journalists and activists to help bring about the kind of world they wanted to live in—one of citizen-enforced governmental transparency where states have less power. While foolish and misguided, they were ideologically motivated in taking their reckless actions.
In contrast, it seems that Teixeira simply displayed terrible judgment and was showboating his access to privileged information to increase his street cred with pals on the internet. In that sense, he was more like an irresponsible teenager who took his parents’ Ferrari out joyriding with his gearhead friends. Teixeira isn’t a “new breed” of insider threat, and he certainly isn’t a whistleblower seeking to publicize some perceived wrong.
Snowden’s mass leaks in 2013 were not the first digital challenge to the U.S. intelligence community. Three years before, then-U.S. Army Private Manning provided 500,000 classified documents to WikiLeaks, which published them to great fanfare for transparency advocates and caused much consternation in Washington. These are not isolated cases; if anything, the tempo of such mass public disclosures seems to be increasing. In March 2017, the CIA fell victim to what is known as the “Vault 7” series, in which sensitive computer tools for digital surveillance and cyber operations were given to WikiLeaks and published online.
Disgruntled former CIA software engineer Joshua Schulte was found guilty of the breach (and also of possessing child pornography, again suggesting an anemic background investigation). Although Manning, Snowden, and Schulte represent the most significant mass leakers of classified information, others have played smaller roles. For instance, National Security Agency (NSA) contractor Reality Winner printed a sensitive document from the NSA computer system and sent it to the self-described publisher of “adversarial journalism,” the Intercept, run by journalist-activists originally linked to the Snowden leaks.
Yet treating Teixeira as another in an increasingly long and embarrassing line of leakers impedes the lessons that can and should be learned from this case, which is marked by social adherence to a gaming community more than a cause. What these leakers do have in common with Teixeira is that—as far as anyone has proven—not one of them carried out the intelligence breach acting as a recruited agent on behalf of a foreign power. They are thus not “spies” in the traditional sense of the word.
Instead, they are what we have described in our academic research as self-directed insider threats: intelligence professionals who chose to betray their oath to protect classified information and did so on their own initiative. Some acted on their political or ideological beliefs, others for disgruntlement, to show off, or even to win arguments in gaming chat rooms. As the Teixeira charging documents allege, his intent was to “discuss geopolitical affairs and current and historical wars.” It was not some kind of misguided protest about U.S. domestic or foreign policy. Washington is apparently not yet prepared to understand such a vector of counterintelligence vulnerability.
To be sure, Teixeira otherwise shares much in common with leakers such as Snowden and Manning. They were all young people of junior rank (despite Snowden’s ludicrous claims that he was some kind of “senior advisor”) in sensitive positions in the U.S. intelligence community who abused their access to classified information to share it with people who had no right nor reason to know it. They were all grandiose enough to think that they wouldn’t get caught (or, if they were, would be lionized enough to avoid criminal penalties), and none of them realized the broader geopolitical or diplomatic ramifications of their actions.
In practice, whatever the motivations, the damage is just as real as if they were spies. As long-serving Director of Central Intelligence Allen Dulles explained in 1963, providing secrets for public consumption has the same net effect as “betraying it to the Soviets just as clearly as if he secretly handed it to them,” and it is thus reasonable to charge Teixeira under the same criminal codes as the other mass leakers. But that’s where the similarities end.
Ideologically driven betrayal is a well-trodden path in the annals of espionage, from the communism-inspired “Cambridge Five” spy ring during the Cold War to the Cuban sympathies that motivated Ana Montes, who was recently released from prison after serving 20 years for spying for Cuba. Preventing those with divided loyalties from accessing state secrets has given rise to the modern system of periodic background checks, invasive polygraph testing, and the requirement that those with security clearances document any foreign travel or meaningful foreign associations. Yet very few of these measures seek even to identify, much less prevent, self-directed insider threats such as Winner, Manning, Snowden, and the like.
Effective frameworks for personnel security and counterintelligence require understanding the varied (and often multiple) motivations for insider threats. In this case, it seems that Teixeira’s access to classified systems far exceeded his professional remit. Further, it seems clear that the counterintelligence vetting process failed to pick up some rather radical and distasteful views, but these views do not seem to be his motivation for leaking. It seems more likely that Teixeira’s narcissism, bad judgment, and arrogance got the best of him, although some of these traits can be hard to uncover in a traditional background investigation that is often more concerned with blackmailable behaviors than judgment. The U.S. intelligence community will almost certainly conduct a thorough post-mortem of the Teixeira case for lessons learned, and it may be prudent to look beyond his recklessness to discern not only how he got a clearance and why he had such unfettered system access, but also why the government was unaware that its secrets were circulating around the dark corners of the internet for months before he was arrested. The task of counterintelligence trolling of the internet for loose secrets will doubtless require new protocols and legal authorities. In the meantime, the Band-Aid of “security refresher training” will be urgently added to the schedule for the hundreds of thousands of clearance holders—the vast majority of whom already understand the responsibility that comes with a clearance.
Such a post-Teixeira study may suggest that it is time to revisit the post-9/11 collaborative framework of “need to share” and revert to the Cold War’s stricter “need to know” principle. Perhaps the Defense Department will close off intelligence as an initial career thrust for the most junior personnel in the same way that certain specialties (such as working in embassies or in special operations) requires a higher rank and more professional experience. Could the intelligence community differentiate accesses to intelligence between those who need to use the information for their jobs and, on the other hand, those who just need to keep the systems running? For instance, while Manning, Winner, and Schulte had substantive roles dealing with classified intelligence as part of their jobs, Snowden and Teixeira were essentially system administrators. Further, might access to national secrets prudently require an age minimum, just as the Constitution requires for officeholders in the Senate or presidency? After all, the prefrontal cortex responsible for judgment and restraining impulses develops well into one’s mid-to-late 20s.
Or perhaps there is simply an irreducible minimum of bad apples and poor judgment in an enormous—by international comparison—U.S. intelligence community that is comprised, after all, of people. Important decisions will need be made about insider threat protocols, and further actions need to be taken in light of this event. It does no one any good to peddle in false comparisons, such as painting Teixeira as another crusading mass leaker. Only with clarity can the intelligence community hope to learn from this unfortunate event.
This is the analysis of the authors alone and represents no official U.S. Defense Department or government position.
18 notes
·
View notes
Text
A Deep Dive into the Services of IT Consulting in Washington DC

Introduction
In the bustling heart of technological innovation, Washington DC stands as a hub for businesses seeking to harness the power of Information Technology (IT). Amidst the dynamic landscape, IT consulting services emerge as a guiding force, offering a myriad of solutions to propel organizations towards efficiency, growth, and success.
The Essence of IT Consulting
1. Strategic Planning and Advisory:
At the core of IT consulting services lies strategic planning. Consultants in Washington DC work closely with businesses to align IT strategies with overarching organizational goals. This involves conducting thorough assessments, identifying opportunities for improvement, and providing advisory services that pave the way for a technology roadmap tailored to the unique needs of the capital's diverse industries.
2. Technology Integration and Implementation:
IT consultants play a pivotal role in integrating new technologies seamlessly into existing infrastructures. This includes the implementation of cutting-edge solutions, software, and systems to enhance operational efficiency. In Washington DC, where staying ahead in the tech race is crucial, consultants ensure that businesses adopt the latest innovations to maintain a competitive edge.
3. Cybersecurity Solutions:
In the era of digital transformation, safeguarding sensitive data is paramount. IT consulting Washington DC address cybersecurity challenges by implementing robust measures. This encompasses risk assessments, developing cybersecurity strategies, and deploying advanced tools to protect businesses from evolving cyber threats.
4. Cloud Computing Services:
Cloud computing has revolutionized the way businesses operate, and IT consultants are instrumental in guiding organizations through cloud adoption. From selecting the right cloud model to migrating data and applications, consultants in Washington DC ensure a smooth transition to the cloud, optimizing scalability, and fostering collaboration.
5. Data Management and Analytics:
The abundance of data in the digital age necessitates effective management and analysis. IT consulting services delve into data governance, helping businesses in Washington DC derive valuable insights. Consultants implement robust data management strategies, ensuring data integrity, security, and harnessing the power of analytics for informed decision-making.
6. IT Infrastructure Optimization:
Consultants evaluate and optimize IT infrastructures to enhance performance and reduce costs. Whether it's streamlining processes, upgrading hardware, or implementing virtualization, the goal is to create a resilient and efficient IT environment tailored to the unique needs of businesses in Washington DC.
7. Managed IT Services:
Many organizations opt for managed IT services, outsourcing day-to-day IT operations to consultants. This allows businesses in Washington DC to focus on their core activities while ensuring that their IT infrastructure is expertly managed, monitored, and maintained by professionals.
8. Training and Change Management:
Implementing new technologies often requires a cultural shift within organizations. IT consultants provide training programs and change management strategies to facilitate a smooth transition. This is crucial in Washington DC, where adapting to technological changes is key to staying relevant in a competitive market.
The Impact of IT Consulting in Washington DC
In a city where innovation and efficiency are paramount, the services of IT consulting make a profound impact on the business landscape. By leveraging these services, organizations in Washington DC position themselves to thrive in a rapidly evolving digital ecosystem.
1. Increased Operational Efficiency:
Strategic planning and technology integration lead to increased operational efficiency. IT consultants in Washington DC streamline processes, eliminate bottlenecks, and ensure that technology aligns seamlessly with business objectives.
2. Enhanced Cybersecurity Posture:
With the ever-present threat of cyber-attacks, IT consulting services bolster cybersecurity postures. Consultants implement robust measures to safeguard sensitive data, providing businesses in Washington DC with the confidence to navigate the digital landscape securely.
3. Informed Decision-Making:
Data-driven decision-making becomes a reality through effective data management and analytics. IT consultants empower businesses in Washington DC with the tools and insights needed to make informed strategic decisions.
4. Adaptability to Technological Changes:
The dynamic nature of technology requires organizations to be adaptable. IT consulting services not only ensure the smooth adoption of new technologies but also provide the necessary training and change management strategies for seamless transitions in Washington DC.
5. Cost Optimization:
Efficient IT infrastructures and strategic planning result in cost optimization. IT consultants in Washington DC help organizations make informed investments, ensuring that every dollar spent on technology contributes to business growth.
The Future of IT Consulting in Washington DC
As technology continues to evolve, the role of IT consulting services in Washington DC will become even more critical. The need for strategic guidance, innovative solutions, and adaptive IT environments will drive businesses to seek the expertise of consultants to navigate the ever-changing landscape.
In conclusion, the services of IT consulting in Washington DC encompass a wide array of strategic initiatives aimed at propelling businesses towards success in the digital age. From aligning IT strategies with organizational goals to implementing cutting-edge technologies, IT consultants play a vital role in shaping the future of businesses in the capital city. As Washington DC continues to be a hotspot for innovation, the services of IT consulting will remain a cornerstone for organizations aspiring to thrive in the dynamic and competitive tech-driven ecosystem.
#it consulting#it services#it management#artificial intelligence#it support#it support services#it company#it services provider#IT Consultancy services
2 notes
·
View notes
Note
zane for the character ask thing?
YESSSS
favorite thing about them: waaahhhh so much. god i love zane. his character arc is so so good. His dub voice is I think my single favorite dub voice so far ( a high honor; I love a lot of the dub voices!!), I love how he can go from mumbling to a snarling roar in an instant. I love his Hell Kaiser design, I love the way the show storytells through his deck and how he plays it. He's also in my Single Favorite GX Duel so I think that counts as a Favorite Thing.
least favorite thing about them: genuinely trying to think about. what my least favorite thing about him is. hm. I do adore dub zane but it's a shame a lot of his relationship with respect re: dueling and himself and others got cut in order to play up a little bit of a "edgy mid-2000's tough guy bully older brother" characterization with him in the dub; the respect thing is such an important part of his character and it sucks to lose that!!
favorite line: sorry theyre all dub lines but "CYBER END DRAGON.... IT'S BEEN REAL" *EXPLOSION* still makes me go absolutely insane and "he's got one" re: jaden desperately telling him that he cant go, that syrus needs a big brother, literally makes me start crying. Also special shoutout to the fact that the dub specifically had zane tell syrus he loves him on two separate occasions!!!! That's so dear to me. Sub wise I do also love "I don't need an assistant" re: yubel being like 'i'll help you down on your way to hell.' he just goes hard.
brOTP: his bond with syrus is my single favorite yugioh siblings dynamic and every time i think about them im just like ;__; aauuaaghhhwwaahhhh......could talk about them. for ages. I also love his friendship with Jaden and Alexis!!! Zane Truesdale has Three Whole Little Siblings!!!!!!!!! I know and see the truth!!!!!
OTP: you know i gotta be on that idolship babeeeyyy!!! I did not expect a gx ship to weasel into my brain but he and Atticus just make me so soft. Why don't you come with me into the light and maybe you'll fucking calm down. love CAN bloom between a NIN fan and a Jimmy Buffett fan.
nOTP: never could vibe much with zane/jaden as a ship????? idk. thats his little brother to me. also again if you ship him with syrus im biting you. and im biting you. and im biting you. and im killing you.
random headcanon: zane alan truesdale my autistic aromantic gay nonbinary competitive pokemon player........... he is transneutral to me. his ideal gender is a 2 1/2 by 2 1/2 by 2 1/2 floating steel cube with the hell kaiser jacket on it. He listens to Tool. He'd go to raves and stand again the wall with his arms crossed. His special interest as a small child was printers. He loves old computers. His favorite Pokemon is Dialga. i could go on.
unpopular opinion: HE'S NOT. EVIL?!?!?! PEOPLE ALWAYS ARE LIKE "my sexy evil husbando >:3" WITH HELL KAISER AND IT'S LIKE. HES NOT EVEN EVIL!!!! HES JUST MENTALLY ILL!!!! HES HAVING A MANIC EPISODE SOMEONE HELP HIM. also. his 'death' is better in the dub than in the sub imo (it's the telling sy he loves him. for me.) <3
song i associate with them: Heel Turn 2 by tmg is the Zane Song Ever for me but also Bleed Out off their latest album.... "I will go down punching, but I will go down/ and my corner men won't bring me back around...."
favorite picture of them: sorry it's not an in-show screenshot but it's always going to be this pic from tag force

i cannot fucking believe this is a real picture of ryozane marufujitruesdale from a Real PSP Game that Really came out and that you can play but it IS. emulate Tag Force 3. my final message.
#ygo posting#THANK U ANON IM ALWAYS IN A MOOD TO TALK ABOUT ZANE. MY BELOVED OLD DESKTOP COMPUTER OF A GUY#asks#anonymous
12 notes
·
View notes
Text
The art evolution and the cyberart hegemony
André Arruda Bruno
Comparing the markets of old Renaissance art and modern digital art, we all know that they show significant divergences. The renaissance brings more tangible, realistic art and is older, otherwise digital art is the latest form of artistic expression. It surrounds many types of art such as animations, illustrations, digital paintings, etc. The main differences between Renaissance art and digital art are their form, how they're made, and how they're shared.
Renaissance art was a really important time in art history. As we know, Classical ideas came back and artists had more freedom to create. Furthermore Rich people or groups and organizations with money, called patrons, helped the artists a lot. They gave financial support to the artists. Art groups, known as guilds, also played a part, making sure that the works were of good quality. The market itself based their judgements on the classical ideas that remained from the past.
The 20th century opened a door for a new era of technological advancements, stimulating a digital art revolution. The computers and digital tools transformed the art universe, and this marked a big change in how art was created and dissolved as we know from the past paragraphs. Artists, now, had access to new mediums and techniques, opening a new horizon of artistic expression.
This technological advance stimulated the creation of new tools to create a new type of art. The so-called cyberart. According to wikipedia this term "cyberart" is vague and relatively new; An example of a common type of cyberart is produced programmatically by applying a set of design rules to a natural or preexisting process, generating an digital software made art. Some of the known types of cyber art are the NFTs (non-fundable tokens), Augmented reality (AR), Pixel art, animation etc.
Opposed to the renaissance market, the modern digital art market has evolved in their most various mediums. In the creation and dissolution of art, a big move was brought about by the digital era; The Technology became a special tool for artists. Online galleries and NFTs have become fundamental for the digital art market. These online platforms provided a global reach for artists to exhibit their work, and NFTs have revolutionized the concept of owning a piece of art in the digital niche, creating a new market dynamic. With the internet age, online platforms became the pillar of the digital art movement. Nowadays, there are many types of galleries in which the most various types of art are exhibited, as well as the online markets, which the NFTs dominate and make a lot of success. never could Da Vinci think that technology would change the way how se see art like today’s vision
Concluding, the Renaissance art market started in the 14th century and the changes over the 7 centuries shows how the technologies affected not only the arts itself but also the perspective upon the pieces of art, and how these perspectives affected the dynamic of the art market nowadays.
6 notes
·
View notes
Text
"Hacking Unveiled" – An Exploration into the Dark World of Cybercrime
Dive into the heart-pounding realm of hacking and cybercrime with “Hacking Unveiled.” This thrilling journey uncovers the mysterious world of hackers and their techniques, guiding you through the preventative measures you can take to safeguard yourself.
Discover the diverse types of hackers and their motivations, from ethical hackers to cyber criminals. Unveil the intricacies between “white hat” and “black hat” hackers, and learn how to become an ethical hacker yourself.
Enter into the infamous world of the “famous hackers and their stories” and the notorious “anonymous group and their attacks.” Get an inside look into the “hacking techniques used by cybercriminals” and the profound impact these actions have on businesses.
Get a sneak peek into the latest “hacking tools and software” used by both ethical hackers and cybercriminals, and delve into the subjects of “penetration testing” and “protecting against social engineering attacks.” Stay ahead of the game with the latest “hacking news and updates” and uncover the captivating “career opportunities in ethical hacking and cybersecurity.”
Be aware of the ever-evolving future of hacking and cyber threats. Let “Hacking Unveiled” guide you through the unknown, demystifying the complexities of cybercrime.
White Hat Hackers
Black Hat Hackers
Anonymous
Gray Hat Hackers
State-sponsored Hackers
Hardware Hackers
Crackers
The Spectrum of Cybercrime: Understanding the Different Types of Hackers
White Hat Hackers
White hat hackers, or “ethical hackers,” use their skills for good. They work alongside organizations, acting as “cybersecurity experts,” to identify and fix system vulnerabilities, protecting individuals and companies from cyber attacks.
Black Hat Hackers
In contrast, white and “black hat hackers” engage in illegal or malicious activities, such as stealing personal information, disrupting services, and spreading malware.
Anonymous
The loosely organized international group of hackers, “anonymous,” is known for participating in high-profile cyberattacks and spreading political messages.
Gray Hat Hackers
Sitting between white and black hat hackers, “gray hat hackers” may use their skills to identify vulnerabilities but exploit them for personal gain or to draw attention to the issue.
State-sponsored Hackers
The ominous “state-sponsored hackers” work on behalf of governments, using their skills for espionage or political sabotage, potentially significantly impacting national security and international relations.
Hardware Hackers
In addition to software hacking, there are also “hardware hackers,” who specialize in manipulating physical devices, such as breaking into intelligent homes or hacking into cars.
Crackers
A synonym for black hat hackers, “crackers” use their skills to crack into systems, software, or networks, gaining unauthorized access.
Cybercrime: Understanding Standard Techniques
To safeguard against malicious cyber attacks, knowing the most frequently employed tactics, including phishing scams, password attacks, and exploiting software vulnerabilities, is crucial. This post delves into the most prevalent hacking methods, from social engineering and phishing to malware and advanced persistent threats (APTs). Stay alert and ensure your software and security systems are always up-to-date to minimize the risk of falling victim to cybercrime.
Social Engineering: The Deceptive Tactic
Cybercriminals often resort to social engineering to manipulate individuals into divulging sensitive information or performing actions they wouldn’t otherwise. This tactic can take various forms, including phishing scams, pretexting, baiting, and more. To guard against these attacks, it is critical to be suspicious of unsolicited requests for personal data, be cautious when clicking on links or downloading attachments from unknown sources, and keep your software and security programs up-to-date.
Phishing: The Tricky Scam
Phishing is a form of social engineering that seeks to deceive individuals into surrendering confidential information, such as login credentials, financial details, or sensitive personal data. These scams often come in email or text messages, posing as credible sources. To avoid falling prey to phishing attempts, it is recommended to look out for suspicious messages, particularly those asking for personal information, verify the authenticity of links before clicking on them, and be wary of downloading attachments or clicking links from unknown sources.
Malware: The Harmful Threat
Malware, including viruses, trojans, and ransomware, is specifically designed to cause harm to computer systems. Installing and updating a reputable antivirus program is essential to protect your computer.
Additionally, be mindful of the files you download and links you click, especially if they are from unknown sources, as they may contain malware.
APTs: The Persistent Threat
Advanced persistent threats (APTs) are cyber attacks by state-sponsored hackers or highly-skilled cybercriminals. These attacks are known for their persistence as the attackers often go undetected for an extended period. To detect and fend off APTs, it is crucial to have an up-to-date antivirus program installed on your computer and to be cautious of unsolicited emails or text messages, especially those asking for personal information.
Defending Against Cyber Threats: Strategies for Keeping Your Data Safe
Essential Tactics to Outwit Hackers and Stay Secure
Essential tactics to protect against cyberattacks include using robust passwords, safeguarding personal information, regularly updating software, and securing devices. These may sound simple, but neglecting to do so can have severe consequences.
The Importance of Strong Passwords and Up-to-Date Software Keeping software current helps to avoid vulnerabilities that older versions may have. Strong, unique passwords for each account can provide an easy yet effective layer of security.
Tips to Protect Personal Information and Devices Being mindful of phishing scams, using privacy settings on social media, and being prudent about what personal information is shared online are critical in securing personal information. Ensure devices are protected with a passcode or fingerprint and backup important files regularly.

The Mysterious World of the Dark Web
The dark web may sound like a concept from a hacker movie, but it’s real and can be a bit frightening. It’s crucial to understand what it is, how it differs from the regular web, and the type of activity. This article will shed some light on the enigmatic side of the internet.
Accessing the dark web requires special software and is invisible to the general internet user. It’s often linked to illegal activities, such as buying and selling illicit items, hacking services, and trafficking personal information. Exercise caution when accessing the dark web and take steps to protect personal information.
The dark web is a collection of websites that can only be accessed using specialized software, such as the Tor browser. Despite being often linked to illegal activities, not all its use is illicit.
However, accessing the dark web carries risks and can threaten personal information and security. Be cautious and take measures to protect personal data when accessing the dark web.
Why Access the Dark Web
Accessing the dark web can be dangerous and threaten personal information and security. Exercise caution and take necessary measures to protect personal data when accessing the dark web.
How to Enter the Dark Web
The most popular way to access the dark web is by using the Tor browser. It’s a free, open-source browser that routes traffic through multiple layers of encryption, making it challenging to trace activity. However, accessing the dark web comes with risks and requires using a VPN, never sharing personal information, and avoiding using real names.
Now that you have a better understanding of the dark web, the choice is to delve into the mysterious side of the internet.
Don’t Fall Victim: How to Protect Yourself from Identity Theft
Be Alert! Identity Theft Lurks, Stalking Unsuspecting Victims
It’s a modern-day nightmare – cybercriminals prowling the internet, seeking out unsuspecting individuals and businesses to victimize through identity theft. From phishing scams to data breaches, the tactics used by these criminals are sophisticated and ever-evolving. The consequences of falling prey to such a crime can be devastating, leaving financial losses and a tarnished reputation in its wake.
Beware! Know Your Enemy.
Cybercriminals use various methods to obtain personal information, including phishing scams, data breaches, dumpster diving, and even purchasing it on the dark web. Stay informed and take proactive measures to protect yourself and your information.
The Aftermath – A Life Turned Upside Down
The impact of identity theft is far-reaching, affecting victims’ finances and reputation and often causing emotional stress as they work to regain control of their personal information.
Don’t Be a Statistic – Defend Yourself!
Fortunately, you can take steps to safeguard yourself against identity theft. Regularly updating software, using strong and unique passwords, being cautious about sharing personal information, and remaining vigilant for unsolicited phone calls or emails are just a few examples.
Protect Your Information and Devices
In addition to these basic measures, take extra steps to secure your personal information and devices. Keeping personal information offline, using anti-virus software and firewalls, encrypting sensitive data, and ensuring your devices with locks and PINs are crucial for maximum protection.
If Disaster Strikes – Have a Plan
If you suspect you have fallen victim to identity theft, acting quickly is essential. Notify your bank, credit card companies, and credit reporting agencies to place a fraud alert on your accounts. Turn to resources such as the Federal Trade Commission’s IdentityTheft.gov and the Identity Theft Resource Center for guidance on reporting and recovering from the crime.
Stay Protected – Stay Vigilant
Identity theft is a constant threat that requires ongoing attention and preventative measures. By staying informed, protecting yourself and your information, and knowing where to turn in the event of a breach, you can reduce your risk of falling victim to this malicious crime.
Stay Ahead of the Game – Subscribe to Our Blog!
Remember to subscribe to our blog for more informative and helpful articles on cybersecurity and protecting yourself. Stay ahead of the game in the fight against identity theft!
This article is originally posted at https://nikolin.eu/tech/hacking-unveiled-a-fascinating-dive-into-the-world-of-cybercrime-and-its-prevention/
#hacking#hackers#black hat hackers#white hat hackers#gray hat hackers#cybercrime#cybersecurity#dark web
10 notes
·
View notes
Text
How to Get the Best Deals on Products .The Ultimate Guide to Buying Products on Sale .
Know before Buying Products on Sales.

Buying products on sale is a great way to save money. But with so many sales and discounts available, it can be difficult to know where to start. Here is an ultimate guide to help you find the best deals on products and save money.
Best deals on products Seasonal sales
Many retailers offer discounts on seasonal items during the off-season. For example, you can find great deals on winter clothes in the spring and summer. and also Holidays like Black Friday and Cyber Monday are a great time to find deals on a variety of products. Retailers often have clearance sales to get rid of excess inventory. This is a great way to find deals on discontinued items or last-season styles. and Outlet stores sell discounted merchandise from brand-name retailers. This is a great place to find deals on name-brand products.
Second-hand stores sell used items, including clothes, furniture, and electronics. This is a great place to find deals on gently-used items.
Buying products on sale .
Do your research: Before you buy anything, do your research to find out the fair market value of the product. This will help you avoid overpaying. check price on the online platform like Amazon , Flipkart and all . Because to know the price difference from offline retailer and online platform so that you can compare the best product at good price .
Use price comparison tools: There are a number of websites and apps that allow you to compare prices from different retailers. This is a great way to make sure you're getting the best deal. There are many number of the tools which give You the best Analytics graph of price difference so that people can check the price up and down on that product in the online platforms because they want to give you the best .
Sign up for retailer newsletters: Many retailers offer email newsletters that notify you of sales and promotions. This is a great way to stay up-to-date on the latest deals. Here one thing you can also do is giving your Mobile number if you know them or trust them because through this they can send you the message of offers and high sales and Seasonal discount on the each product which help you to reduce the time of research .
Use coupons and promo codes: Many retailers offer coupons and promo codes that can save you money on your purchase. Be sure to check for these before you checkout. Uncover a treasure trove of savings through coupons and promotional codes. Retailers frequently provide these codes, translating into significant price reductions when applied during checkout. Remember to scout for these virtual keys to savings.
Shop around: Don't just buy from the first retailer you see. Compare prices from different stores to make sure you're getting the best deal.
Negotiate: If you're buying a big-ticket item, don't be afraid to negotiate the price. Many retailers are willing to negotiate, especially if you're a loyal customer and Embarking on a significant purchase journey? Don't hesitate to flex your negotiation muscles. Retailers often respond favorably, particularly when dealing with loyal customers. Your prowess in negotiation can unveil hidden discounts.
How to get discounts
Be a loyal customer: Many retailers offer discounts to loyal customers. Sign up for their loyalty program and start earning points or rewards . and Forge a digital connection with your preferred retailers on social media platforms. Their posts often unveil hidden gems – sales and promotions that would otherwise remain concealed. Stay effortlessly updated on the latest deals through these channels.
Use a credit card with cash back rewards: There are a number of credit cards that offer cash back rewards on your purchases. This can be a great way to earn money back on your shopping.
Shop with cashback websites: There are a number of websites that offer cashback rewards when you shop through their website. This is a great way to earn money back on your shopping.
Use a price drop protection service: There are a number of services that will refund you the difference if the price of an item drops within a certain period of time after you purchase it. This is a great way to ensure you're getting the best deal.
Shopping tips
Set a budget: Before you start shopping, set a budget and stick to it. This will help you avoid overspending.
Make a list: Before you go shopping, make a list of the items you need. This will help you stay focused and avoid impulse purchases.
Shop online: Online shopping can be a great way to find deals. Many retailers offer discounts and promotions on their websites.
Shop during off-peak times: Retailers are more likely to offer discounts during off-peak times, such as weekdays or during the off-season.
Conclusion
Embrace Timing Flexibility: Not all sales are born equal. The off-season and weekdays often play host to some of the most remarkable deals. Keep your shopping schedule versatile.
Explore Every Avenue: The first option isn't necessarily the best. Allow yourself the luxury of exploring multiple retailers, comparing prices, and ensuring you're capturing the most favorable deal.
Seek Expert Advice: If the path to remarkable deals seems intricate, don't hesitate to seek assistance. Sales personnel possess a wealth of insights that can steer you toward the most lucrative deals. A simple question can lead you in the right direction .By following these tips, you can find the best deals on products and save money. So don't wait any longer, start shopping today!
2 notes
·
View notes
Text
From Zero to Hero: Dominate the Digital Realm with Dot Net Training!
In today's fast-paced digital world, where information and technology (IT) play a crucial role, staying ahead of the curve is essential. It is no secret that the demand for skilled IT professionals continues to rise. To excel in this competitive landscape, individuals often seek opportunities to enhance their knowledge and skills. One such avenue that has gained immense popularity is Dot Net training. This comprehensive training program equips individuals with the necessary skills to navigate the digital realm and emerge as true heroes. In this article, we will explore how Dot Net training can empower you to transform from zero to hero in the digital sphere.

Why Dot Net Training Matters in Education
Keeping Pace with Technological Advancements
The world of IT is continuously evolving, with new tools and technologies emerging regularly. As a result, it is crucial for individuals seeking a career in this field to stay updated with the latest trends and advancements. Dot Net training provides a solid foundation for individuals to keep pace with these changes. It familiarizes them with the latest tools and techniques, ensuring they remain at the forefront of technological developments.
Widening Career Opportunities
Dot Net training opens up a plethora of career opportunities for individuals. With the increasing reliance on technology across various industries, the demand for skilled professionals who can effectively utilize Dot Net technology is skyrocketing. By acquiring expertise in Dot Net, individuals can tap into a broad range of job roles, spanning from web development to software engineering. Moreover, the market value of Dot Net professionals is on the rise, making it a lucrative career choice for aspiring individuals.
Enhancing Problem-Solving Skills
Problem-solving is a important skill needed in the IT industry. Dot Net training emphasizes the development of problem-solving abilities, enabling individuals to overcome complex technical challenges. The comprehensive nature of the training equips learners with the knowledge and skills to identify and resolve issues efficiently. By honing their problem-solving skills, individuals can become invaluable assets to their organizations, making them indispensable in the digital realm.

The Power of Dot Net: Information and Empowerment
Versatility and Compatibility
One of the key strengths of Dot Net is its versatility and compatibility with different platforms. It allows developers to create applications that can seamlessly run on various operating systems, including Windows, macOS, and Linux. Such versatility empowers individuals to develop and deploy applications that can reach a wider audience, regardless of their preferred platform. This adaptability also enhances the user experience by delivering seamless performance across different devices.
Security and Reliability
In an era where data breaches and cyber threats are ever-present, security and reliability are paramount concerns for businesses. Dot Net provides a robust framework that prioritizes security, ensuring the confidentiality and integrity of sensitive data. With the training received, individuals become proficient in implementing various security measures, thereby contributing to the safeguarding of valuable information. By utilizing Dot Net technology, they can develop applications that have a reliable defense against common vulnerabilities and attacks.
Increased Productivity and Efficiency
Dot Net offers a range of tools and libraries that streamline the development process, increasing productivity and efficiency. It provides access to a vast ecosystem of pre-built components and frameworks, eliminating the need to reinvent the wheel for every project. This accelerates the development timeline and enables individuals to focus on delivering high-quality solutions. Dot Net also offers built-in support for testing, debugging, and performance optimization, further enhancing productivity and ensuring efficient application development.
In today's information-driven world, empowered individuals who possess the necessary skills to navigate the digital realm are in high demand. Dot Net training at ACTE Institute bridges the gap between zero knowledge and becoming a hero in the IT arena. By acquiring expertise in Dot Net, individuals unlock a world of opportunities, enabling them to contribute significantly to technological advancements. From widening career prospects to enhancing problem-solving skills, and from versatility and compatibility to security and reliability, Dot Net emerges as a powerful platform that empowers individuals to dominate the digital realm. So, take the leap, embrace Dot Net training, and embark on a journey towards becoming a digital hero!
6 notes
·
View notes
Text
"Unveiling the Future: How Data Science is Revolutionizing Upcoming Industries"
Data science continues to have a substantial impact on various industries, and its scope is expected to expand as new technologies emerge and businesses realize the potential of data-driven insights. Here are some upcoming industries where data science is likely to play a significant role:
Healthcare and Life Sciences: Data science can aid in personalized medicine, drug discovery, predictive analytics for patient outcomes, and healthcare operations optimization.
Financial Services: Financial institutions use data science for fraud detection, risk assessment, algorithmic trading, customer behavior analysis, and credit scoring.
Retail and E-Commerce: Data science helps optimize inventory management, pricing strategies, recommendation systems, and customer segmentation for targeted marketing.
Energy and Utilities: The energy sector benefits from data analytics for smart grid management, predictive maintenance of equipment, and energy consumption optimization.
Manufacturing: Data science improves manufacturing processes through predictive maintenance, quality control, supply chain optimization, and demand forecasting.
Agriculture: Precision agriculture utilizes data science to optimize crop yield, resource allocation, pest control, and environmental monitoring.
Transportation and Logistics: Data science plays a role in route optimization, fleet management, demand forecasting, and autonomous vehicles.
Telecommunications: Data science assists in customer churn prediction, network optimization, and personalized service offerings.
Media and Entertainment: Content recommendation, audience segmentation, and analyzing viewer engagement are areas where data science is making an impact.
Real Estate: Data science helps in property price prediction, market trend analysis, and investment decision-making.
Environmental Conservation: Data science aids in monitoring and analyzing environmental data, including climate patterns, pollution levels, and habitat preservation.
Education: Data science can personalize learning experiences, assess student performance, and optimize educational resources.
Government and Public Services: Data-driven decision-making is becoming increasingly important for optimizing public services, policy formulation, and resource allocation.
Insurance: Insurers use data science for risk assessment, claims processing, fraud detection, and customized pricing.
Travel and Tourism: Data science enhances traveler experiences through personalized recommendations, pricing optimization, and destination insights.
Pharmaceuticals: Data science plays a role in drug discovery, clinical trials optimization, and pharmacovigilance.
Smart Cities: The concept of smart cities involves integrating data science for efficient urban planning, traffic management, energy consumption, and public services.
Cybersecurity: Data science helps in identifying and responding to cyber threats by analyzing patterns and anomalies in network data.
As technology continues to advance and businesses recognize the value of data-driven insights, certybox is creating a difference in providing the top professional courses along with job assistance. It's essential for professionals in the field to stay updated with the latest developments and tools to make the most of these opportunities.

5 notes
·
View notes