#ddos attack protection service
Text
Amazon Web Service & Adobe Experience Manager:- A Journey together (Part-12)
In the previous parts (1,....8,9 , 10 &11) we discussed how one day digital market leader meet with the a friend AWS in the Cloud and become very popular pair. It bring a lot of gifts for the digital marketing persons. Then we started a journey into digital market leader house basement and structure, mainly repository CRX and the way its MK organized. Ways how both can live and what smaller modules they used to give architectural benefits.Also visited how they are structured together to give more on AEM eCommerce and Adobe Creative cloud .In the last part we have discussed how we can use AEM as AEM cloud open source with effortless solution to take advantage of AWS, that one is first part of the story. We will continue in this part more interesting portion in this part.
As promised in the in part 8, We started journey of AEM OpenCloud , in the earlier part we have explored few interesting facts about it .In this part as well will continue see more on AEM OpenCloud, a variant of AEM cloud it provide as open source platform for running AEM on AWS.
I hope now you ready to go with this continues journey to move AEM OpenCloud with open source benefits all in one bundled solutions.
So let set go.....................

After AEM OpenCloud Full-Set Architecture & Consolidated Architecture and environment management in previous parts we have seen, how it arrange and work to deliver full functionality.
Now we will see more on security of these environments and more from this.
Security:-
The security of the AEM hosting environment can be broken down into two areas:
1st)Application security and
2nd)Infrastructure security.
A crucial first step for application security is to follow the Security Checklist for AEM and the Dispatcher Security Checklist.
The checklist is meant to be applied from top to bottom.
Security Checklist for AEM
Main Security Measures.
-Run AEM in Production Ready Mode
-Enable HTTPS for transport layer security
-Install Security Hotfixes
-Change Default Passwords For the AEM and OSGi Console Admin Accounts
-Implement Custom Error Handler
-Complete Dispatcher Security Checklist
Verification Steps
-Configure replication and transport users
-Check the Operations Dashboard Security Health Checks
-Check if Example Content is Present
-Check if the CRX development bundles are present
-Check if the Sling development bundle is present
-Protect against Cross-Site Request Forgery
-Some OSGI Settings
These checklists cover various parts of security considerations, from running AEM in production mode to using mod_rewrite and mod_security modules from Apache to prevent Distributed Denial of Service (DDoS) attacks and cross site scripting (XSS) attacks.
Dispatcher Security Checklist:-
-Use the Latest Version of Dispatcher
-Restrict Clients that Can Flush Your Cache
-Enable HTTPS for transport layer security
-Restrict Access
-Make Sure Access to Administrative URLs is Denied
-Use Allowlists Instead Of Blocklists
-Run Dispatcher with a Dedicated System User
-Prevent Denial of Service (DoS) Attacks
-Configure Dispatcher to prevent CSRF Attacks
-Prevent Clickjacking
-Perform a Penetration Test
From an infrastructure level, AWS provides several security services to secure your environment. These services are grouped into five main categories – network security;data protection; access control; detection, audit, monitoring, and logging; and incident response.
In this interesting journey we are continuously walking through AEM OpenCloud an open source variant of AEM and AWS. Few partner provide quick start for it in few clicks.So any this variation very quicker and effortless variation which gives deliver holistic, personalized experiences at scale, tailoring each moment of your digital marketing journey.
For more details on this interesting Journey you can browse back earlier parts from 1-11.
Keep reading.......
#aem#adobe#aws#wcm#aws lambda#cloud#programing#ec2#elb#security#AEM Open Cloud#migration#CURL#jenkins the librarians#ci/cd#xss#ddos attack#ddos protection#ddos#Distributed Denial of Service#Apache#cross site scripting#dispatcher#Security Checklist#mod_rewrite#mod_security#SAML#crx#publish#author
1 note
·
View note
Link
Though many organizations are realizing the importance of DDoS Protection services, selecting the right service is often tough. Some often asked questions are: Why choose a managed service? How to evaluate DDoS protection services? How to ensure that the chosen service would deliver on the day of the attack? In this article, we will help you find answers to these questions and enable you to effectively evaluate the service before onboarding
0 notes
Text
Why is Cloudflare blocking me?
Cloudflare is a content delivery network (CDN) and security service that helps protect websites from various threats, such as DDoS attacks, malicious bots, and hackers. If Cloudflare is blocking you, it’s likely because the security settings on the website you’re trying to access have identified your connection as potentially suspicious or harmful. Some common reasons for Cloudflare blocking your access include:
IP reputation: Cloudflare maintains a list of IP addresses known for spam, hacking attempts, or other malicious activities. If your IP address is on this list or has a poor reputation, you may be blocked.
High security settings: The website owner might have set their Cloudflare security settings to a high level, causing more aggressive filtering of incoming traffic. In such cases, even legitimate users might be blocked or challenged.
Rate limiting: Cloudflare can block or limit access from IP addresses that make too many requests within a short period, as this can indicate a DDoS attack or automated scraping attempts.
Browser or user agent issues: Using an outdated browser, a non-standard user agent, or having disabled cookies and JavaScript might trigger Cloudflare’s security measures.
VPN or proxy usage: Using VPNs, proxies, or Tor can sometimes cause Cloudflare to flag your connection as suspicious, as these tools are often used to hide malicious activities.
Firewall rules: The website owner may have set specific firewall rules in Cloudflare that block certain IP addresses, countries, or user agents.
To resolve the issue, you can try the following:
Clear your browser cache and cookies, and ensure JavaScript is enabled.
Update your browser to the latest version or try using a different browser.
Temporarily disable your VPN or proxy, if you are using one.
Check your internet connection and restart your modem or router to obtain a new IP address.
If you suspect your IP address has been mistakenly flagged, you can contact the website owner or Cloudflare support to request a review of your IP address.
Remember that these measures are in place to protect websites and their users from security threats. While blocking can be frustrating, the intent is to maintain a safe online environment for everyone.
Source @ao3org
103 notes
·
View notes
Text
I get that your favorite pet site being DDOS'd is stressful, but some of you need to take off your tinfoil hats about the DDOS thing. DDOSing is an incredibly common internet occurrence. One time a rabbit care forum I was on was overwhelmed for over a week solid, for some reason, and then it just went away. All that happens is you can't access the site if the protection service is lousy or the webmaster decides to shut service off to wait out the weirdos.
It's dirt cheap to run a service-denial attack. People do it for fun. There is absolutely NO proof that those people who claimed credit for the AO3 attack were the ones actually behind it. There is NO proof they are the ones flooding FR. DDOSing is a crime and any sane person isn't going to admit to it in public. There is even less evidence supporting the theory that it's a state sponsored extortion attack targeting niche pet sites comprised mostly of minors with no personal income. I cannot emphasize enough that these sorts of attacks are extremely commonplace on the internet, and just because nearly all major social networking/streaming is owned by the same mega-corporation who can afford absurd levels of ddos mitigation doesn't mean it doesn't happen.
If you don't' believe me please feel free to research it yourself before getting panicked over FR getting DDOS'd. Technically the userbase has accidentally DDOS'd it offline several times in the past during big releases lol. It's just a petty thing that weirdos on the internet do to try and disrupt service, it can get expensive depending on how dedicated said weirdo is, but it's not going to bug out the servers to the point they'll be unusable and user data will be wiped (unless they're already barely functional, but that's another issue). It literally just prevents people from accessing the site by overloading traffic. Like trying to fit too many people through a doorway.
Seems like the attacks are over already anyway. Frankly with how popular FR is I'm surprised it didn't happen sooner lol. If you see the numbers spiking again just take a breath and relax, it's just a waiting game! Inconvenient, but nothing that will kill the site.
30 notes
·
View notes
Text
People are already trying to use the fallout from the recent ddos attack to claim you shouldn't donate to OTW. Sigh.
They almost certainly didn't pay the ransom, and are not to blame for the fact that people primed for anti-Muslin sentiments by right wing politicians don't listen to reason. The OTW volunteers turned to Cloudflare, a well known protection service from rddos attacks, and advised people to stop being assholes in the comments. What more do you expect them to do?
10 notes
·
View notes
Text
A Ukrainian hacker group [...] carried out a destructive attack on the servers of a Moscow-based internet provider to take revenge for Kyivstar cyberattack. The group, known as Blackjack, successfully hacked into the systems of M9com, causing extensive damage by deleting terabytes of data. Numerous residents in Moscow experienced disruptions in their internet and television services. Additionally, the Blackjack hacker group has issued a warning of a potentially larger attack in the near future.
Based on the information provided by Ukrinform, the cyber attack on M9com deleted approximately 20 terabytes of data. The attack targeted various critical services of the company, including its official website, mail server, and cyber protection services. Furthermore, the hackers managed to access and download over 10 gigabytes of data from M9com's mail server and client databases. To make matters worse, they made this stolen information publicly accessible via the Tor browser. [...]
Based on the nature of the attack on M9com, it appears that when the hackers hit Moscow, they were able to gain access to the back-end operations of the company. This allowed them to effectively delete data from the servers, similar to what occurred in the Kyivstar incident. It is worth noting that this type of attack, which involves directly targeting and compromising the servers, is less common compared to the more frequently observed distributed denial-of-service (DDoS) attacks. DDoS attacks overwhelm a system by inundating it with automated requests, causing the service to become inaccessible.
2 notes
·
View notes
Text
Get a free .com domain with any of our web hosting plans for just $1/month.
Web Hosting Plans
When building a website, start here. Our shared service delivers a powerful, proven platform that’s perfect for hosting your websites. With our AMD-powered servers with NVMe storage, WordPress pages load up to 300% faster than ordinary servers.

S E R V E R F E A T U R E S
Simple & Powerful
1-click WordPress Installer
All our web hosting plans come with 1-click WordPress Installer. This means that you can easily install WordPress with a single click in just a few seconds.
Therefore, no manual installation is required to create a website.
Free Website Migration
Need help transferring your website to us? No worries! Let our professional team handle the hard work!
We will get your websites transferred smoothly onto our servers absolutely for free.
AMD-powered servers with NVMe
All our web hosting servers are powered by AMD CPU's. That being said, we only use NVMe storage drives to keep your websites blazing fast. We also use RAID-10 configuration on our NVMe drives to keep your data secure.
With such technology, WordPress pages load up to 300% faster than ordinary servers.
DDOS Protected with Real-Time Malware Scanners
To keep our customer websites secure and online, we have real-time malware scanners running that scans every file that is uploaded. If a malware is detected, it is deleted instantly.
That being said, all our servers are DDOS protected. So your websites are fully secure from all sorts of network layer attacks.
Auto Daily Remote Backups
Backups are made automatically on a daily basis of all websites hosted on our web hosting servers.
For added security, all backups are kept on our remote servers at a different data center.
This feature is included for free with all our web hosting plans.
24/7 Live Support
Our team is available to help you 24/7 via live chat, emails or by phone.
We are available around the clock. So if you need any help, just drop us a message and we will get to you right away.

#hosting#who is hosting jeopardy this week#apex hosting#web hosting#inmotion hosting#image hosting#free hosting#website hosting#free web hosting#wordpress hosting#hosting a website#best web hosting#best wordpress hosting#best hosting#best free minecraft server hosting#best web hosting for small business#best email hosting#bluehost hosting plans#best podcast hosting platform#hosting checker#hosting companies#hosting costs#cloud hosting#cheap web hosting#cloudflare hosting#cheap hosting#cpanel hosting#cheapest web hosting#cheap email hosting#marketing101
13 notes
·
View notes
Text
Are you facing security challenges in Online Survey?

Online surveys can face several security challenges, including:
Data Privacy: Ensuring the confidentiality of respondents' data is crucial. Unauthorized access to personal information collected in surveys can lead to privacy breaches.
Data Integrity: Maintaining the accuracy and consistency of survey data is essential. Malicious actors might attempt to manipulate or corrupt data, impacting the reliability of survey results.
Survey Fraud: Individuals may attempt to manipulate survey results by providing false information or submitting multiple responses (known as ballot stuffing), compromising the survey's integrity.
Phishing Attacks: Fraudulent emails or survey links may be used to trick respondents into providing sensitive information or downloading malware.
DDoS Attacks: Distributed Denial-of-Service attacks can disrupt survey platforms by overwhelming servers with excessive traffic, causing downtime and hindering survey completion.
To address these challenges, survey administrators often implement various security measures:
Encryption: Utilizing encryption techniques to protect data transmission and storage.
Authentication: Requiring user authentication to prevent unauthorized access to surveys and data.
Firewalls and Anti-Malware: Employing security software and firewalls to mitigate the risk of cyber threats.
Captchas and IP Blocking: Implementing measures to prevent automated responses and restrict multiple submissions from the same IP address.
Anonymity and Confidentiality: Ensuring respondents' anonymity and safeguarding their sensitive information.
Regular Security Audits: Conducting periodic security audits to identify vulnerabilities and enhance overall security.
While these measures can mitigate risks, no system is entirely immune to security threats. Survey administrators must stay vigilant, update security protocols regularly, and adhere to best practices to protect the integrity and privacy of survey data.
To know more:
online market research platform
fraud prevention solution
fraud detection and reporting tool
Online Project Management Platform
#market research#onlineresearch#samplemanagement#panelmanagement#datacollection#fraud detection#datainsights
2 notes
·
View notes
Text
Nov. 23 (UPI) -- Hackers hit the European Parliament website with a "sophisticated" cyberattack on Wednesday, shortly after the body declared Russia as a state sponsor of terrorism.
The cyberattack disrupted the website's service moments after the members took their vote. The Parliament cannot officially designate Russia as a terrorism sponsor, but with its vote urged the European Union to do so.
"The [European Parliament] is under a sophisticated cyberattack," President Roberta Metsola said in a statement on Twitter. "A pro-Kremlin group has claimed responsibility. Our IT experts are pushing back against it and protecting our systems. This, after we proclaimed Russia as a state-sponsor of terrorism."
Jaume Duch, the European Parliament's spokesman, said the attack has created "high levels of external network traffic" from the breach.
"This traffic is related to a DDOS attack (Distributed Denial of Service) event," Duch said on Twitter. "EP teams are working to resolve this issue as quickly as possible."
Eva Kaili, Greek member and vice president of the European Parliament, said there is a strong indication that the pro-Russian group Killnet is behind the attack.
"This is my information, but it is under control," Kaili said. "It only cut the external access to the Parliament's website... Unless there is extra attacks we expect it to be back and accessible very soon."
Earlier in the day, the European Parliament voted 494-58, with 44 abstentions for a resolution recognizing Russia as a state sponsor of terrorism, and called on European Union states to "put in place the proper legal framework and consider adding Russia to such a list."
The designation would make Russia more vulnerable to more restrictive sanctions. And penalties by the European Union. The move was made in connection with Russia's ongoing invasion of Ukraine, which is now in its 10th month.
#nunyas news#did y'all learn nothing from admiral Adama#stop networking your computers#need to update the website put everything on a drive#and plug it in to the one computer on the innternet#everytning else on the intranet
12 notes
·
View notes
Text
Learn about negative SEO tactics and how to protect your website from malicious actions
In today’s highly competitive online landscape, businesses and website owners face not only the challenge of optimizing their websites for search engines but also the threat of negative SEO tactics. Negative SEO refers to the practice of using unethical and malicious strategies to harm a competitor’s website’s search engine rankings and online reputation. This dark side of search engine optimization can lead to devastating consequences for innocent website owners.
In this article, we will explore various negative SEO tactics and provide valuable insights on how to safeguard your website from such attacks.
Link Spamming and Manipulation
One of the most common negative SEO tactics is the mass creation of low-quality, spammy backlinks pointing to a targeted website. These malicious backlinks can lead search engines to believe that the website is engaging in link schemes, resulting in penalties and ranking drops. Website owners must regularly monitor their backlink profiles to identify and disavow any toxic links.
Content Scraping and Duplication
Content scraping involves copying content from a target website and republishing it on multiple other sites without permission. This can lead to duplicate content issues, harming the original website’s search rankings. Regularly monitoring your content for plagiarism and submitting DMCA takedown requests can help address this problem.
Fake Negative Reviews
Negative SEO attackers may leave fake negative reviews on review sites and business directories to damage a website’s reputation. Monitoring and responding to reviews promptly can help mitigate the impact of such attacks.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks overload a website’s server with an excessive amount of traffic, causing it to become slow or crash. Implementing DDoS protection services can help safeguard your website against such attacks.
Regularly Monitor Backlinks
Use tools like Google Search Console and third-party SEO software to monitor your website’s backlink profile. Regularly review and disavow toxic links to prevent negative SEO attacks based on link spamming.
Secure Your Website
Ensure your website is secure with HTTPS encryption and robust security measures. This will help protect your website from hacking attempts and potential negative SEO attacks like content manipulation.
Frequently Check for Duplicate Content
Use plagiarism checker tools to identify if your content has been copied elsewhere. If you find duplicate content, reach out to the website owners to request removal or use the Google DMCA process.
Implement Review Monitoring
Keep an eye on reviews and mentions of your brand across various platforms. Respond professionally to negative reviews and report fake reviews to the respective platforms for removal.
Optimize Website Performance
A fast-loading website can better withstand DDoS attacks. Optimize your website’s performance by compressing images, using caching, and leveraging Content Delivery Networks (CDNs).
Regularly Backup Your Website
Frequent website backups will ensure that even if an attack occurs, you can quickly restore your website to its previous state without losing valuable data.
Use Webmaster Tools and Analytics
Stay vigilant by setting up alerts in Google Webmaster Tools and Google Analytics. These alerts can notify you of sudden drops in website traffic or other suspicious activities.
Conclusion
As the digital landscape continues to evolve, negative SEO tactics remain a persistent threat. Understanding these malicious strategies and proactively taking steps to protect your website is crucial for every website owner.
Discover countermeasures against negative SEO tactics, safeguarding your site from harm. Shield your website with insights from an experienced SEO company in Chandigarh for robust defense strategies.
2 notes
·
View notes
Note
cloudflare also is awful for privacy as they collect tons of data on you. so they are all around shit, plus the internet's over reliance on cloudflare causes centralization of the internet and mass outages. we are better off without cloudflare imo
True tbh. I get wanting the added security and protection from ddos attacks but the fact that cloudflare has near to a monopoly on those services means if anyone was able to take down cloudflares servers for even a day or if anything happened to their servers then any site that relies on them would be fucked
Like idk maybe it's better to just have your site down for a couple days than it is to pay for a company to protect it while selling your data to God knows who. And when I see people doing fund drives or making sites for people who are in dangerous living situations and they use cloudflare like what's keeping them from getting ordered to out you to authorities and shit I dunno in this state of the world I just don't trust companies to not be lapdogs anymore.
9 notes
·
View notes
Text
Amazon Web Service & Adobe Experience Manager:- A Journey together (Part-11)
In the previous parts (1,2,3,4,5,6,7,8,9 & 10) we discussed how one day digital market leader meet with the a friend AWS in the Cloud and become very popular pair. It bring a lot of gifts for the digital marketing persons. Then we started a journey into digital market leader house basement and structure, mainly repository CRX and the way its MK organized. Ways how both can live and what smaller modules they used to give architectural benefits.Also visited how they are structured together to give more on AEM eCommerce and Adobe Creative cloud .In the last part we have discussed how we can use AEM as AEM cloud open source with effortless solution to take advantage of AWS, that one is first part of the story. We will continue in this part more interesting portion in this part.
As promised in the in part 8, We started journey of AEM OpenCloud , in the earlier part we have explored few interesting facts about it .In this part as well will continue see more on AEM OpenCloud, a variant of AEM cloud it provide as open source platform for running AEM on AWS.
I hope now you ready to go with this continues journey to move AEM OpenCloud with open source benefits all in one bundled solutions.
So let set go.....................

After AEM OpenCloud Full-Set Architecture in earlier part -10 we have seen how it arrange and work to deliver full functionality.
Now another variation we will see how it fit into your AEM solution for digital marketing .
Consolidated Architecture:-
A consolidated architecture is a cut-down environment where an AEM Author Primary, an AEM Publish, and an AEM Dispatcher are all running on a single Amazon EC2 instance.
This architecture is low-cost alternative suitable for development and testing environments.
This architecture also offers those three types of backup, just like full-set architecture, where the backup AEM package and EBS snapshots are interchangeable between consolidated and full-set environments.
This option is useful, to restore production backup from a full-set environment to multiple development environments running consolidated architecture.
Another use case is to upgrade an AEM repository to a newer version in a development environment, which is then pushed through to testing, staging, and eventually production.
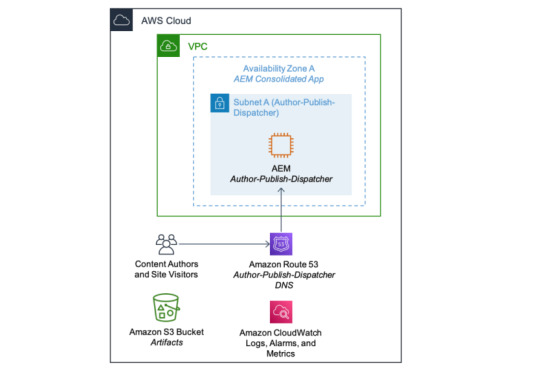
Now both require environment management full-set and consolidated architectures.
Environment Management :-
To manage multiple environments with a mixture of full-set and consolidated architectures, AEM OpenCloud has a Stack Manager that handles the command executions within AEM instances via AWS Systems Manager(described as below in picture) .
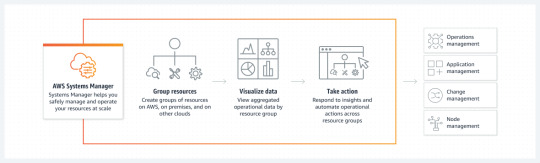
These commands include taking backups, checking environment readiness, running the AEM security checklist,enabling and disabling CRXDE and SAML, deploying multiple AEM packages configured in a descriptor, flushing AEM Dispatcher cache, and promoting the AEM Author Standby instance to Primary.
Other than the Stack Manager, there is also AEM OpenCloud Manager which currently provides Jenkins pipelines for creating and terminating AEM full-set and consolidated architectures, baking AEM Amazon Machine Images(AMIs), executing operational tasks
via Stack Manager, and upgrading an AEM repository between versions, (i.e. from AEM 6.2 to 6.4, or from AEM 6.4 to 6.5)
AEM OpenCloud Stack Manager
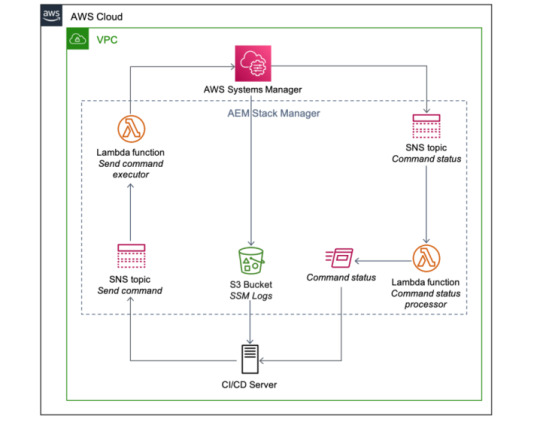
In this interesting journey we are continuously walking through AEM OpenCloud an open source variant of AEM and AWS. Few partner provide quick start for it in few clicks.So any this variation very quicker and effortless variation which gives deliver holistic, personalized experiences at scale, tailoring each moment of your digital marketing journey.
For more details on this interesting Journey you can browse back earlier parts from 1-10.
Keep reading.......
#aem#adobe#aws#wcm#aws lambda#cloud#programing#ec2#elb#security#AEM Open Cloud#migration#CURL#jenkins the librarians#ci/cd#xss#ddos attack#ddos protection#ddos#Distributed Denial of Service#Apache#cross site scripting#dispatcher#Security Checklist#mod_rewrite#mod_security#SAML#crx#publish#author
1 note
·
View note
Text
@anon asking what an XSS attack is
I was gonna just submit this as an ask but my explanation got long - anyway, ill explain this as best I can from a cyber security standpoint: (also dont @ me for being a nerd on a salt blog i just wanted to explain)
To start, XSS is cybersecurity short hand for cross site scripting. on a base level, XSS if a form of an "injection" attack, in this case, the attacker is "injecting" a script (ie lines of python) into the target. I believe the original ask was on the emergency downtime that flight rising went into because of this very attack. I'll just use them as an example--
what the particular attack does is it allows the attacker to firstly, search for vulnerabilities in their target's security, in this case, flight rising's security, such as their protections on user data and things like a users website cookies. one thing an attacker could do with your data, ie the cookies i mentioned, is use your login session cookies and essentially trick the website into thinking that they are you, and would basically be logged into your account without knowing your password.
Since this is a CS blog, I'll also put this into a CS perspective. CS and FR are very similar. Put simply, an attacker could access similar data on CS. My main concern is how CS stores other important data, such as c$ payment info of which I am not completely aware of - if it's open info on CS, I just haven't seen it. I'm also not completely sure how CS stores things like login sessions, but if it's anything similar to FR, an attacker could access that too.
Overall, it is not at all like a DDOS. While DDOS is still dangerous, an injection like XSS is a lot more endangering to data. A DDOS is, put simply, a form of attack where the attackers intent is to significantly overload the target, basically causing a severe influx of traffic to and from the target, causing the target a multitude of issues. The main goal with a DDOS is a denial of service, as DDOS is short for "Distributed Denial of Service" - basically make server catch on fire, no more service for you, hence why XSS is more severe.
Hope this makes sense!! Ik this isn't entirely CS related but it is still worrying that this type of attack happened to a game a lot of CS players also frequent. Always be wary of what cookies you're actually saving and be safe.
2 notes
·
View notes
Text
How can you prevent your WordPress platform from cyber attack.
WordPress is a CMS-based web development tool. This open-source platform provides easy and high-performing app development of online shopping apps, banking apps, social media forums and many more. As a result, WordPress is the extensively popular CMS platform. But its popularity has made it overlooked hence threats of cyber-attack are present with the WordPress website. However, vulnerable data of a WordPress website can easily be targeted but there are various ways, through which you can prevent your valuable web platform. The top 10 ways in this regard are underneath:-
Add CDN-level firewall
Undoubtedly, not only WordPress but website designed using any platform is open to attack from bots and other nefarious actors. An overloaded server can crash and become inoperable as a result of a distributed denial of service (DDoS) assault. CDN-level firewall adds an extra degree of protection by seeing and removing questionable traffic before it reaches the server. By doing this, you can defend your website against bot and DDoS attacks.
Update credentials regularly
However, updating passwords is a common practice but regular practices of credentials gradations minimize the chances of security threats. Additionally, limitations of login attempts reduce the hackers’ chances to hack the website.
Update the WP version and remove plugins
If you are running an older WP version then it provides the opportunity for the hacker to hamper the vulnerable data. Hence it is advisable to timely update the WP version along with the regular update of the login password.
Block comment section
The comment section of a website is the entry door for hackers to take entry into a website’s source code. Due to the regular lack of moderation in this section, it is simple for hackers to smuggle malicious code into otherwise innocent-looking comments. To prevent your website from cyber-attack you can also block the comment section.
Remove plugins
Plug-ins are one of the most appealing features of a WordPress website that enhances the development process and makes the website SEO and user-friendly. But, since these plugins are pre-defined and can be used anywhere during the development process, as a result, it creates the opportunity for hackers to attack the block of the most vulnerable data. So to prevent WP admin it is good to use least or remove plug-ins from the website.
Auto update on plugins
A simple approach to guarantee that all installed plugins and themes are current is to use WordPress' inbuilt auto-update capability. This is particularly crucial for plugins and themes that deal with private information like credit card numbers or personal records. Auto-updates not only provide security benefits but also make sure that all installed software is compatible with the most recent version of WordPress, increasing the reliability of your website.
Security headers
Cross-site scripting threats are reduced by security headers, which stop malicious code insertion. Additionally, adding them lessens the possibility of malware infecting your website and blocks payload-based attacks. Some security header instances are:-
Referrer regulations.
Secure Transport Protocol over HTTP (HSTS).
a code of content security.
X-Frame choices.
X-Content-Type-Options.
Protection from XSS (cross-site scripting).
If you are unaware of the core of web development then it is good to connect with a Digital creative solutions provider who provides WordPress website security along with end-to-solution of your web development need.
4 notes
·
View notes
Text
Cloudfare has Blocked Kiwifarms

As of the time of posting, this is the error you see upon visiting the website.

Context for those who don't know: Kiwifarms is a website dedicated to the discussion of certain online figures deemed as "lolcows" by the site's users. The site is largely used for doxxing, stalking, and harassment - queer and disabled people (and their loved ones) being their most common targets. Many of KF's users have also stalked and assaulted their targets in real life. The site's collective harassment campaigns have driven multiple people to suicide.
Cloudflare is a digital security service used to protect websites against DDoS attacks and other security risks. Cloudflare, after much social media pressure, has finally dropped Kiwifarms from their services.
3 notes
·
View notes
Text
I am not a tubbo main but anyone being mean about tubnet not working will get shot by me on sight.
Like I don't think they grasp that they're having not only an issue with a service provider but also the sheer number of people attempting to join is likely registering as a DDoS attack accidentally which is probably tripping the fuckin protection for that.
There is. so much traffic going through. Honestly only disappointed this is going down so much cause it means the beta test is messing up for him
3 notes
·
View notes