#data loss prevention
Text

https://ukuzimanya.co.za/astutus-cyber-security-solutions/
Cyber Security is no longer a product that resolves attacks but a Solution that Investigates and Prevents an attack.
The world has evolved to a more hybrid working concept and with that Cyber Criminals have become more daring in the manner in which they attack and whom they attack.
1 note
·
View note
Text
5 Easy Ways To Improve Salesforce Data Backup Recovery Strategy
In today's data-driven world, businesses rely heavily on Customer Relationship Management (CRM) systems like Salesforce to manage their customer information, track sales, and drive growth. However, even the most robust platforms are not immune to data loss or system failures. That's why having a solid Salesforce data backup and recovery strategy is crucial for ensuring business continuity. In this blog post, we'll explore five easy ways to enhance your Salesforce data backup and recovery strategy.
Regularly Scheduled Backups:
The foundation of any effective data recovery strategy is regular data backups. Salesforce provides a built-in data export tool that allows you to export data in a structured format, such as CSV or Excel. Set up a routine schedule for these exports to ensure that your data is backed up consistently. Depending on your organization's needs, you may choose to perform daily, weekly, or monthly backups.
Automate Your Backups:
Manually exporting data can be time-consuming and prone to errors. To streamline the process, consider automating your Salesforce data backups using third-party backup solutions. These tools can schedule and execute backups automatically, ensuring that your data is consistently and reliably backed up without manual intervention.
Store Backups Securely:
Backing up your Salesforce data is only half the battle. Equally important is where you store those backups. Utilize secure and redundant storage solutions, such as cloud storage platforms like Amazon S3 or Google Cloud Storage. Implement encryption and access controls to safeguard your backups from unauthorized access.
Test Your Recovery Process:
Having backups is essential, but they're only as good as your ability to recover data from them. Regularly test your data recovery process to ensure that it works as expected. Document the steps, and make sure that your team is familiar with the recovery procedures. Conducting mock recovery drills can help identify and address any potential issues before they become critical.
Monitor and Alerting:
Proactive monitoring is key to identifying data backup and recovery issues early. Implement monitoring and alerting systems that notify you of any backup failures or anomalies. This way, you can take immediate action to rectify issues and minimize data loss in case of a failure.
Consider Salesforce Data Archiving:
As your Salesforce database grows, it can become challenging to manage large volumes of data efficiently. Salesforce offers data archiving solutions that allow you to move older or less frequently accessed data to a separate storage location. This can help reduce storage costs and improve system performance, making your data recovery strategy more manageable.
In conclusion, enhancing your Salesforce data backup and recovery strategy doesn't have to be complicated. By implementing these five easy steps, you can significantly improve your organization's ability to recover critical data in the event of data loss or system failures. Remember that data is the lifeblood of your business, and a robust backup and recovery strategy is your insurance policy against unforeseen disasters.
#Salesforce best practices#Data loss prevention#Backup automation#Data retention policies#Data encryption#Salesforce customization#Data recovery testing#Backup monitoring#Data recovery procedures#Data backup optimization#Salesforce data protection#Backup reliability#Data restoration#Backup storage solutions#Data backup documentation#Salesforce metadata backup#Data backup strategy evaluation#Data backup policies#Salesforce data backup best practices
0 notes
Text
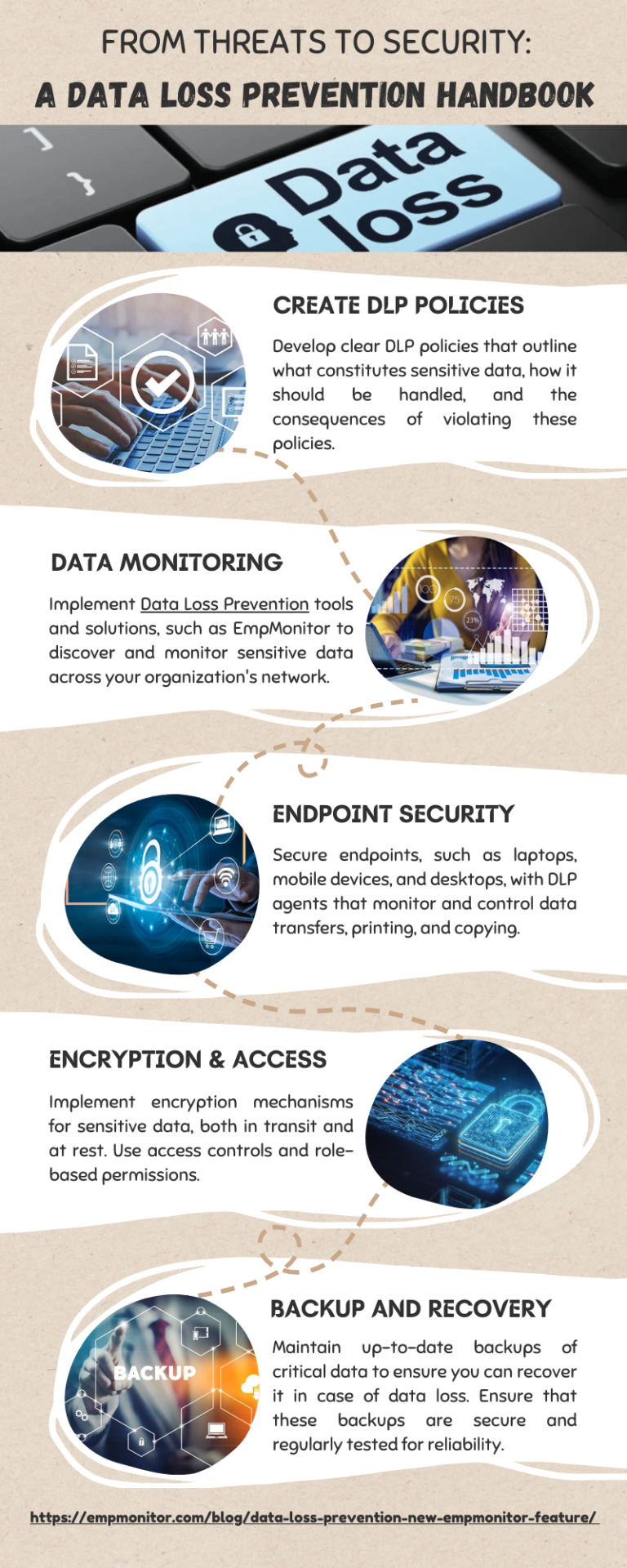
DLP is a set of strategies and technologies designed to protect sensitive information from being accessed. In this infographic, you will get to know about data loss prevention.
0 notes
Text
How To Back Up Your Data Before Taking Your Computer To A Computer Repair Service?

Oh no! Has your laptop or PC stopped working suddenly? Is it a software problem? Then, it is high time that you go to a computer repair service. But, when you decide to take your system to a service center or you have to drop it off for repair, the private information on the drive, which you do not want anyone to see, frequently brings worry.
Your data is safe if you know the technician or service center personally. But it can not be the same each time. You must be careful when backing up your data, personal files, and privacy. In this blog, we will discuss these things to keep you away from cyber threats.
Why Is It Necessary To Have a Data Backup?
We know you don't want to take any risks during your PC or laptop repair. For this, you must keep copies of all your contents securely. Data loss, theft, or other data-related issues can occur unexpectedly. A solid and sound data backup strategy can help you reduce the risk factors of data loss.
Removing personal data before repairing or confirming the data is crucial. No matter how trustworthy and reliable a business is, there is always a chance of a bad occurrence. If you want to ensure that your personal and essential data is safe from loss or theft, make sure you remove it from the system before taking it to a computer repair service. But opting for a backup method is best because there could be issues if someone can access the password-protected or locked data.
Choose a Solid Backup Method - Processes for Simplifying the Task
Numerous backup methods depend on preferences, budget, needs, and available storage devices. Backup software, a cloud service, an external hard drive, or even a flash drive are all practical and highly advanced methods for data backup. You can also read it at: "Computer Repair Service: Steps for Data Backup Pre-Visit".
Other than this, you must consider several factors like price, how convenient the method is, accuracy, and speed. For example, if you use an external hard drive, you can get the chance to store a massive amount of data. But unfortunately, it comes with damage and loss tendencies.
On the other hand, a cloud backup service is excellent for providing complete access and automatic backups just with a stable internet connection. Sometimes, we can also use data backup software because it simplifies the whole backup process with encryption; but it can be expensive and require installation. So, you must choose the system that suits your needs.
Start With Data Preparing
Before backing up the data, you must start making minimal preparation for a smoother and easier process. Remove all the duplicate or unnecessary files, clear up the recycle bin, and uninstall all the unused programs for taking data backup.
You must create labels to organize all your data. Then, you can create folders for various file types, like music, documents, photos, and business or private works, to complete everything systematically. Additionally, ensure the amount of data and check how much space is required for the complete backup.
Choose an External Hard Drive
It is necessary to keep all your important files safe with a complete data backup. An external hard drive is considered as one one of the most reliable methods. A USB cable is connected to this via your computer to secure the data. Before taking your pc or laptop to a computer repair service, you can easily follow the process. You might like reading: "Credit Repair Software: Your Digital Solution to Common Credit Issues".
After connecting the external hard drive to your computer, you can use it as a backup service without waiting to be recognized. Then, choose the files and folders from my files or file explorer, then copy and drag the files to the external hard drive. Once completed, verify the backup's accuracy. Finally, keep the external hard drive in a safe location before removing it.
Use a Cloud Service

Besides those ways, a cloud backup is an advanced process to back up your data. You can easily use Google Drive, Dropbox, iCloud, or OneDrive. As it is an online platform for data storage with remote servers, you can also easily access the data from any device with a stable internet connection. You must create an account and log in to back up your data with a cloud platform.
You can even download and install the cloud service app on your computer to simplify the method. Locate the files and folders for backup and then drag and store them to the cloud app or website. Wait a few times to upload it, check if the loading is completed, and then you can log out of the cloud service by keeping all the details safe.
Use a Backup Software
There are different backup software available for backing up your important data. With this software, people can automate all the tasks from encryption to recovery. Download and install the advanced software to take a complete data backup. After that, start the software and select the backup type that best suits your requirements.
You must also determine the source, like the hard drive or cloud. Go for setting configurations like passwords, encryption, and other things for starting the backup process. Finally, wait to get it finished. Close the software, and your data is safe.
Conclusion
Taking your pc or laptop to a computer repair service is stressful if you don't feel safe or protected about your data. Having the data stored in a backup is essential for mental peace and satisfaction. Moreover, you also allow the technicians to quickly handle your pc or laptop issues by taking a backup of all the data.
Now that you know how to back up your data, you can apply this and take your computer or pc to Find My Service Center for efficient repair. You can avail of a wide range of premium-quality services for different types of PC or computer. The experienced and wells-skilled technicians will closely check your PC to identify the real problem and offer accurate and effective solutions.
#Computer Repair Service#Data Backup#Data Protection#Pre-Repair Steps#Data Loss Prevention#Repair Service Preparation#PC Maintenance#Data Security#Safe Repair Practices#Computer Maintenance
0 notes
Text
O365 Security Overview
Office 365 is a popular cloud-based productivity suite that offers many benefits for businesses of all sizes. These Top 5 Security Settings in O365 should help you get started on your path towards a more secure cloud. However, with great power comes great responsibility. As an O365 administrator, you need to ensure that your organization’s data and users are protected from cyber threats and…

View On WordPress
#Cybersecurity#data loss prevention#Exchange Online#Microsoft#Microsoft Intune#Multi-Factor Authentication#O365#Outlook
1 note
·
View note
Text
Don’t let flaws compromise the integrity of the app!

In the modern digital era, where cyberattacks are getting more complex and frequent, application security is essential. App vulnerabilities can compromise the integrity of your app and put your users’ sensitive information at risk. Therefore, ensuring your application is secure and protected from potential cyber threats is essential. This blog will discuss how application security protects your apps by attaining, fixing, and strengthening the security once we deploy them. Read More: Don’t let flaws compromise the integrity of the app!
#app encryption#cloud app security#cloud security#critical infrastructure protection#cybersecurity and infrastructure security agency#data encryption#data encryption standard#data loss prevention#data security#database activity monitoring#endpoint security#firewall in computer network#infrastructure security#network admission control#network firewall security#Network Security#prisma cloud#secure cloud storage#security on the internet#web application security
0 notes
Text
Each business contains information, some of it more sensitive than others. Personal identifying information (PII) is present in sensitive file sets, which risks customer privacy. Financial and payment-related information are two types of sensitive papers that, in the event, they are lost, misused, or disused, may contribute to forgery and identity theft. Other significant data sources include corporate secrets and intellectual property (IP).
0 notes
Text
Cost of a Data Breach

A data breach creates both direct and indirect costs. The cost of a data breach can vary greatly depending on several factors, including the sensitivity of the data that was lost or stolen, the number of people affected, the length of time the breach went undetected, and the costs associated with remedying the breach and any resulting damage.
According to a recent study carried out by IBM Security and the Ponemon Institute, the global average cost of a data breach is $4.35 million The same report says that 83% of organizations studied have experienced more than one data breach. Stolen or compromised credentials were the primary attack vector in 19% of breaches in the 2022 study and also the top attack vector in the 2021 study, having caused 20% of breaches. However, Eleven percent of breaches in the study were ransomware attacks, an increase from 2021, when 7.8% of breaches were ransomware, for a growth rate of 41%. Forty-five percent of breaches in the study occurred in the cloud.
Direct Costs of a data breach include engaging Security & forensic experts, lost revenue, fines, penalties, legal costs, and third-party vendor fees, etc. Indirect costs include in-house investigations and communication, diminished customer confidence, and lost reputation. Damage to a company’s reputation proves one of the most elusive costs to determine. Customers sometimes don’t complain about the breach, they just stop buying services or products.
Possible reasons for a data breach
Weak or stolen passwords.
Vulnerabilities in software or hardware
Phishing attacks
Physical theft.
Insider threats:
The recommended strategy to reduce the cost of a data breach
Data Inventory and Classification.
Multi-Factor Authentication
Protecting sensitive data with encryption
Data Loss Prevention systems
Regular Vulnerability assessment and Penetration testing
Incident response plan and regular testing.
1 note
·
View note
Text
Follow to read tips, updates related cybersecurity, data loss prevention, risk management and everything related cybersecurity awareness.
1 note
·
View note
Text
Balance Theory Scores Seed Funding for Secure Workspace Collaboration
Balance Theory Scores Seed Funding for Secure Workspace Collaboration
Home › Cyberwarfare
Balance Theory Scores Seed Funding for Secure Workspace Collaboration
By Ryan Naraine on December 05, 2022
Tweet
Balance Theory, a seed-stage startup working on technology to help security teams collaborate and manage data flows securely, has closed a $3 million funding round.
The Columbia, Maryland-based Balance Theory said the early-stage investment was led by DataTribe with…
View On WordPress
#accel#asset discovery#asset management#balance theory#compliance#crowdstrike#data loss prevention#dlp#financing#funding#hubble technology#identity and governance#paladin#seed stage#venture capital#workspace collaboration
0 notes
Text
Data Loss Prevention Market Growth, Overview with Detailed Analysis 2022-2028
Data Loss Prevention Market Growth, Overview with Detailed Analysis 2022-2028
The Data Loss Prevention Market research report 2022-2030 provides an in-depth analysis of the changing trends, opportunities, and challenges influencing the growth over the next decade. The study includes a detailed summary of each market along with data related to demand, supply and distribution. The report examines Data Loss Prevention market growth strategies adopted by leading manufacturers…
View On WordPress
#Covid-19 Impact Analysis#Data Loss Prevention#Data Loss Prevention forecast#Data Loss Prevention Industry#Data Loss Prevention Market#Data Loss Prevention price#Data Loss Prevention report#Data Loss Prevention research#Data Loss Prevention share#Data Loss Prevention trends
0 notes
Text
Intuitive vs Zero-Trust, an MSME Perspective

With an increasing number of MSMEs in exports, becoming a dependable link in the supply chain to large enterprises and MNCs, and going global with their own products, I strongly sensed the need to write this blog. It is now the writing on the wall that MSMEs are subject to global standards of competition. They need to run the business by systems, policies, and processes. IT adoption is essential to transforming businesses driven by systems, policies, and processes. Let us focus on policies and ways to enforce policies by systems and processes. There could be intuitive or zero-trust policies. Let us understand the difference between intuitive and zero trust policies by examples.
Data Centralization Policy
Enterprises centralize data to achieve data protection objectives. They invest in on-premise or on-cloud servers to centralize and access data from central infrastructure. They can devise an intuitive or zero-trust policy to achieve the objective of data centralization. Admin can educate the users about the hazards of data decentralization or scatteredness and request the user to store the data on central infrastructure. It is an intuitive policy. If the user follows the instructions, the objective of data centralization is achieved. The objective is not achieved if the user keeps saving data on local computers. Let’s see what happens in a zero-trust policy approach. The user’s computer system is hardened, forcing him only to save the data in central infrastructure, whether the user wants it or not. Thus the zero trust policy leaves no room for digression from the policy. Our product BLACKbox hardens the computer system of the user such that the user can save data on a central location or secure local drive created by the BLACKbox and enforces a zero trust data centralization policy.
Data Deletion Policy
Enterprises require the users to delete the data with accountability. It is done by requesting the users to be responsible while deleting the data, and that too, without using the shift+del command for permanent deletion. It is an example of an intuitive policy. If the user uses the shift+del command, one can delete all the data, and data may not be recoverable. Let’s see what happens in the zero-trust policy approach. By this policy, whatever data is deleted using the shift+del command is captured and made available for restoration. Not only that, but also a system is devised to inform who deleted the data using shift+del. By such a zero-trust policy, the data is not lost no matter whether the user used shift+del and identification of the user who deleted the data can be done. Our product BLACKbox captures the deleted data and makes it available for restoration to maintain business continuity and hold the user accountable with evidence.
Data Backup Policy
Enterprises need to back up their application, email, and file data. They have the policy to take multiple backups, on-premise and off-premise, to deal with disaster or hardware failure. They have the policy to maintain multiple versions of the data backup to deal with ransomware. They advise users to regularly copy their email and file data to a central backup location. They engage IT Admin to take backup of applications on multiple hardware. They also depend on manual off-premise backup. It is an example of an intuitive policy. Here, the fate of backup depends on the user’s discretion. Suppose the users or admin are not sincere in following the backup processes; the enterprise will lose business continuity in the event of data loss due to deletion, ransomware, disaster, or hardware failure. It calls for a zero-trust policy of backup. It will automatically backup applications, files, and email data, maintain backup versions, and push data off the premise to the cloud or data centre. It will also generate the report on the status and report any backup errors proactively. Our product BLACKbox helps enterprise zero trust backup policy with nil involvement of users or admin with a proactive report on backup health status.
Data Leakage Prevention Policy on USB Port
A policy of blocking USB ports does not serve the purpose as users need to use USBs for keyboard, mouse, and printer. A few users need USB port access to the HASP license dongles, digital signatures, or equipment testing. Few users genuinely need to copy data over a USB as a genuine business need. As a part of the intuitive policy, users are requested to use USB ports with integrity, accountability, and responsibility. If some users use a USB port to leak or steal enterprise data, an enterprise can be competitively exploited; or held liable for breach of non-disclosure agreements with the customers. With a zero trust policy, an enterprise can allow only keyboard, mouse, and printer type of non-mass storage devices over USB so users cannot leak the data. For users who need access to a USB port for digital signatures, HASP license dongles, or equipment testing, USB ports can be allowed only to inward the data and prevent it to outward the data so users cannot leak the data. For the users who need to copy data on USB media, the enterprise can allow the user to outward data over USB with a report to the supervisor about what data is outwarded to USB. Our product BLACKbox offers these controls on USB to enforce a zero-trust IT policy.
Data Leakage Prevention Policy on Acceptable Email
The users use enterprise emails to communicate with the world. The email system is an enabler of communication and can also be misused to leak enterprise data. The enterprise must have a well-jotted email usage policy. The intuitive method of defining email usage policy includes educating the users to use the email system for communication and avoid its misuse to leak the data. At the same time, the zero trust policy includes framing the policy around email usage as required by the user’s job profile. Under the zero-trust approach, one can divide users into various categories defining the permissions and rights in the email system. E.g. A group of users can be categorized to be able to send emails internally only in the organization. Another group of users can be categorized to be able to send emails only to white-listed parties in their professional circle. Another group of users can be categorized as able to send emails only if the superior approves. Such policy defines controls on attachments exchanged over emails. The enterprise can allow certain users to send emails to anyone worldwide, but it is reported to the superior as a copy of the email.
Data Leakage Prevention Policy on Acceptable Internet Usage
The users need the Internet as a resource for research, business development, government compliance, bidding, banking, etc. The Internet is an enabler and can be misused to leak enterprise data. The enterprise must have a well-jotted internet usage policy. The intuitive method of defining internet usage policy includes educating the users to use the internet system for research, business development, and compliance and avoid its misuse to leak the data. At the same time, the zero trust policy includes framing the policy around Internet usage as required by the user’s job profile. Under the zero-trust approach, one can divide users into various categories defining the permissions and rights in the Internet system. The enterprise can define its users’ minimum required list of websites and allow those websites without any restrictions. When the user needs to access a website that is not included in the list can be accessed with permission or by isolating sensitive enterprise data. Our product BLACKbox provides on-demand Internet access for such websites and automatically isolates sensitive enterprise data.
It is about defining enterprise IT policies with either an intuitive or zero-trust approach.
Tags:
Data Cyber Risk Solutions
Laptop Security Software India
BlackBox Software Solution
#Data Cyber Risk Solutions#Laptop Security Software India#BlackBox Software Solution#Data Loss Prevention#Hardware Data Security#Data Theft Mitigation#Data Backup Solutions#Security Software India#Blackbox Service#Blackbox Security#Gmail Recovery#Gmail Recovery Software Solution#NAS India#Laptop Security Software#Data Backup Software
0 notes
Text
Data Loss Prevention

How Businesses Can Prevent Data Loss
Did you know “zettabyte” was a non-existent term before 2012? Today, there are more than 40 zettabytes or 40 trillion gigabytes of data floating around. With so much data, comes greater responsibility for those who handle this data!
Data is the new oil as they say, so imagine the ramifications of this data getting lost, and worse, falling into wrong hands. There are a lot of numbers that attest to this. For instance:
40-60% of small businesses won’t reopen after data loss.
The average cost of downtime for companies of all sizes due to data loss is almost $4,500/minute.
Up to 50% of data loss cases are caused by human error.
Failures like data loss can happen to anyone but businesses must be prepared for any contingencies that can arise from it.
Did you notice, that we spoke about “data loss” specifically and not “data leak” or “data breach”? These terms are often used interchangeably; however, there is a subtle difference.
Difference Between Data Loss, Data Leak, and Data Breach
Data leaks are usually a result of organizations accidentally exposing sensitive data. This could be due to ignorance, security vulnerabilities, or plain simple mistakes. Such incidents are not initiated by cyber attackers.
Data breaches are a form of cyberattack, where cybercriminals persistently and deliberately compromise sensitive resources. In fact, any event that exposes sensitive data due to cybercriminal activity is considered a data breach.
So, a breach is when someone “knowingly” exposes sensitive data and a leak is when the data is exposed to the public “unknowingly.” In both cases, the data is compromised but the key differentiator would be the intent and the final outcome.
Data loss is another term that is used loosely with both data leaks and data breaches, and is the topic of our discussion here. Data loss describes incidents where sensitive information is misplaced and can’t be retrieved. The differentiating factor here is the data lost due to both human or system errors (corruption or deletion – accidentally or intentionally) as well as thefts through cyberattacks or insider threats.
So, what goes into preventing data loss in businesses? To understand that, let’s first deep dive into what causes data loss.
Causes of Data Loss
Primarily, there are three reasons why a business may lose data.
Unintentional human error – This is said to be the number one cause of data leaks today. This can occur due to various reasons like failing to restrict or update access permissions, losing or leaking data in the public domain (think laptop left unattended or leaving a file with sensitive information unencrypted on an open server), or even failing to comply with the organizational procedures.
Cyberattacks – Using techniques like phishing, malware, or ransomware, email impostors are able to penetrate the security firewalls and get hold of sensitive data.
Insider threats – Mostly understood as “corporate espionage.” Here, a bad actor (generally bitter), compromises the user accounts and leaks information to outsiders for personal gains.
The costs from data losses are exponential. Per an IBM security analysis report, a customer’s personally identifiable information (PII) was the most common type of record lost, included in 44% of breaches with each record costing $180.
This is where data loss prevention (DLP) comes in handy as a security best practice. It’s not just an obligation on the part of businesses to protect the personal identifiable information of customers but is also enforced by several regulatory standards, such as GDPR, HIPAA, PCI-DSS, and even the new cybersecurity executive order signed by President Biden!
How Data Loss Prevention Can Help
There has been a rise of 47% in data breaches since 2020 as a result of the pandemic. With the acceleration of remote working, more data is being shared outside the company network and personal devices. It’s critical to protect not only the networks but the devices as well, besides extending that protection to data in transit and data at rest. Equally important is raising awareness on encrypting messages, human error prevention, and data protection, even when it has been shared.
Data Loss Prevention can stop this. It’s essentially a set of tools and processes to ensure that your sensitive data isn’t lost, misplaced, or exploited by bad actors. At the same time, it also classifies regulated, confidential, and business-critical data and ensures regulatory compliances.
Data loss prevention solutions’ primary job is to classify and prioritize data security. However, to counter today’s sophisticated threats, the DLP tools must go beyond simple detection to offer alerts, enforce encryption, and isolate data.
Typically, good DLP solutions offer:
Visibility into who is accessing data and systems, when, and from where
Restrict suspicious or unidentified activity
Reports for auditing
Identify vulnerabilities and provide forensic context to IT security teams
Such tools protect data in many ways.
Data in use – Data loss prevention software protects data that is being accessed, erased, processed, updated, or read by any user.
Data at rest – DLP tools protect data at rest across several storage mediums, including databases, file server systems, mobile devices, laptops/computers, and the cloud. They do this via controls to ensure only authorized users are accessing the data and to track their access.
Data in transit – DLP solutions are needed to ensure that the sensitive data in transit across a network is routed securely and doesn’t fall into wrong hands. Encryption and email security play a key role here.
There are several techniques through which DLP is accomplished, such as:
Pattern matching: Classifying text by the likelihood of it matching a certain pattern of protected data as a DLP technique. For example, a 16-digit number quoted in an email response or subject line could be classified as a credit card number, or a nine-digit SSN could be a social security number – both protected and sensitive information.
Keyword matching: Classifying and flagging text per specific keyword phrases set by the IT administrators as a DLP technique. For example, phrases like “wire transfer,” “invoice,” “payments,” etc.
Fingerprinting: Another example of a DLP technique is looking for an exact match in databases.
File matching: Looking for hashes of files and matching them against exact fingerprints for DLP.
For more information: https://rmail.com/learn/data-loss-prevention-dlp
0 notes
Text
didn't save 12 hours worth of writing and editing, having a nervous breakdown and am ready to never write a single word again
#I'm literally the girl crying incoherent in German meme#and if anyone is going to come with well meant recovery file tips I'm going to end them#I've been through every recovery trick google has to offer#the audacity of those pages also to end their list of solutions with a “how to prevent data loss in the future” tips#writing
10 notes
·
View notes
Text
Ahmedabad's Digital Guardians: Top Data Loss Prevention Companies

Ahmedabad, a hub for business and innovation, thrives on the secure flow of information. But with this digital growth comes a rising concern: data loss. Sensitive information can be accidentally leaked, stolen by malicious actors, or even lost due to technical glitches. This is where Data Loss Prevention companies step in, acting as your digital shield.
DLP solutions go beyond basic antivirus software. They proactively identify, classify, and protect sensitive data across your network, devices, and cloud environments. Here's a look at some of Ahmedabad's leading DLP providers:
Comprehensive Protection:
SecureU: A national leader in data security, SecureU offers a robust suite of DLP solutions tailored to businesses of all sizes. Their advanced features include data discovery and classification, endpoint encryption, and content filtering to prevent unauthorized data transfers.
Adit Microsys:
This company focuses on providing secure DLP solutions for both enterprises and mid-sized businesses. Their offerings include real-time data monitoring, customizable policies, and integration with existing IT infrastructure, ensuring comprehensive data protection.
0 notes
Text
Unlock the secrets to safeguarding your data! Dive into our latest blog on Secure Your Data: Tips For Implementing Data Loss Prevention (DLP) and keep your valuable information safe.
1 note
·
View note