#cybersecurity in telecom
Text
ANOTHER TRILLION DOLLAR CASE:? TikTok Hit in MASSIVE CIPA Suit Over Its Business Model of Profiting from Advertising by Collecting and Monetizing User Data
ANOTHER TRILLION DOLLAR CASE:? TikTok Hit in MASSIVE CIPA Suit Over Its Business Model of Profiting from Advertising by Collecting and Monetizing User Data
Data privacy lawsuits are EXPLODING and one of our country’s most popular mobile app — TikTok’s privacy issues keep piling up.
Following its recent $92 million class-action data privacy settlement for its alleged violation of Illinois Biometric Information Privacy Act (BIPA), TikTok is now facing a CIPA and Federal Wire Tap class action for collecting users’ data via its in-app browser without…

View On WordPress
#business#CIPA#Cybersecurity#data collection#data privacy#Internet#legal#Litigation#media#Social Media#TCPA#telecom#TikTok
2 notes
·
View notes
Text
Infographic - Top 10 Risks for Telcos in 2024 & Beyond
Infographic - 2024 brings a new wave of challenges for the telecom industry.
Dive into our infographic to explore top 10 risks for telcos.
Learn more: https://www.avisysservices.com/blog/how-testing-is-solving-the-most-annoying-problems-for-telcos/
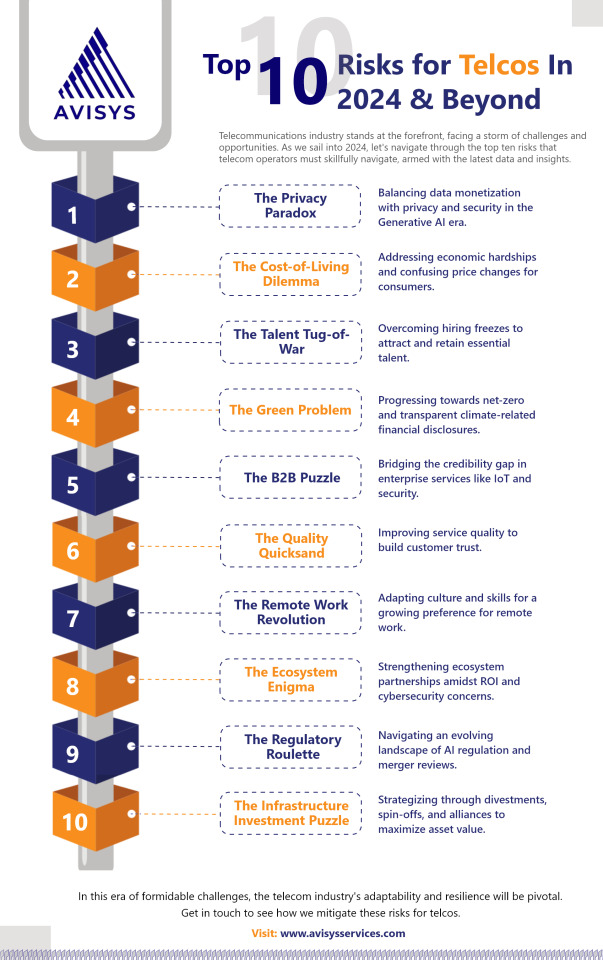
#TelecomChallenges#Telecom2024#Infographic#telecom#RiskManagement#DataPrivacy#GenerativeAI#IoTSecurity#ServiceQuality#RemoteWork#qa#RegulatoryCompliance#Cybersecurity#NetworkQuality#b2b#AssetValueOptimization#RegulatoryRisks#qualityassurance#datamonetization#telecomtesting
0 notes
Text
Businesses today must deal with the combined challenges of protecting their digital assets and streamlining communication routes in the ever changing telecommunications industry. In order to overcome these obstacles, AT&T Unified Communication Services and Cybersecurity Consulting Services have become essential foundations in the USA. This article examines how these offerings are changing how companies handle unified communication and cybersecurity.
0 notes
Text
Website: https://www.savacomkc.com
SAVACOM is a reputable telecom expense management specialist, offering a range of services including expense management, network solutions, IT solutions, mobility solutions, voice solutions, and security solutions. With over 50 years of experience, the company is known for its efficient, honest, and professional approach. SAVACOM provides unbiased consultations and strives to deliver the best in-class telecommunications services, ensuring customer satisfaction through open communication and expert support.
Yelp: https://www.yelp.com/biz/savacom-palm-coast
Keywords:
telecom expense management
collaboration tools for business
voip solutions for small business
sip trunking services
it infrastructure solutions
cybersecurity solutions for small businesses
business collaboration tools
telecom expense management companies
telecom expense management services
voip solutions for business
it infrastructure management solutions
small business collaboration tools
online collaboration tools for business
telecom invoice audit
outsourced telecom expense management
telecom expense management audit
telecom expense management consulting
telecom expense management system
sip trunk service provider
siem solutions for small business
best business collaboration tools
remote collaboration tools for business
best voip solution for small business
best telecom expense management
global telecom expense management
mobile telecom expense management
telecom expense management outsourcing
telecom expense management solution
top telecom expense management service provider
it infrastructure monitoring solution
it infrastructure solutions and services
cybersecurity solutions for businesses
social business collaboration tools
it infrastructure security solution
it infrastructure solutions provider
cloud computing for organizations
voip solutions for large business
voip solutions for medium business
best ucaas systems for enterprise business
ucaas for enterprise
telecom expense management auditing invoice processing
#telecom and it expense management services#telecom expense management asset and service#telecom expense management service costs#best sip trunk service#global sip trunking connect service#good sip trunk service#hybrid it infrastructure solutions#infrastructure it solution#it infrastructure solution provider near me#dedicated internet access solutions#cost-effective cybersecurity solutions for small businesses#cloud computing for healthcare organizations#standard organizations for cloud computing#best small business collaboration tools
1 note
·
View note
Text
TELECOMMUNICATIONS BILL 2023
0 notes
Text
Displaying Global Technological Excellence on a Grand Stage with Odoo, in partnership with Bassam Infotech at Gitex

#GitexGlobal#Gitex2023#TechExpo#InnovationHub#TechShowcase#DigitalTransformation#TechConference#EmergingTech#BusinessOpportunities#NetworkingEvent#FutureTech#GlobalTech#SmartCities#Cybersecurity#Metaverse#DataEconomy#MobilitySolution#HealthTech#Telecom#IoT#FutureUrbanism#SuperBridge#MarketingMania#FutureBlockchainSummit#Tech#TechEvent#Connectivity#communicationtechnology#CommunicationPlatform
0 notes
Text
#datacenter#cloud#technology#cloudcomputing#data#tech#networking#server#cat#network#dataprotection#it#cybersecurity#cloudstorage#bigdata#cisco#networksecurity#networkengineer#telecom#software#database#serverroom#informationtechnology#business#ccna#security#cloudservices#storage#datacenters#o
0 notes
Text
Researchers Reveal Method To Squelch Malicious Robocalls

Researchers at North Carolina State University on Wednesday revealed a novel method for foiling malicious robocalls.
https://jpmellojr.blogspot.com/2023/08/researchers-reveal-method-to-squelch.html
0 notes
Text
Certified Cisco CCNA and CCNP training course in Dehradun

Cisco Certified Network Associate CCNA and CCNP is the associate level Certification in Networking provided by Cisco Systems. CCNA once was known as CCNA Routing and Switching covers the basics of Cisco Networking and routing switching technologies accompanying IP addressing projects, routing basics, switching, WAN technologies, Network Security basics, Network Automation and Network Programmability basics. After the completion of Cisco CCNA course, candidates get familiar with installation, configuration and troubleshoot Cisco Routers and Switches for medium sized networks. Further after the completion of this CCNA Certification training, students can go for higher level of Cisco Course which includes CCNP Enterprise, in addition to strengthen your Routing & Switching and Network Security skills.
The CCNA endorses basic potentiality in installing, supporting, and repairing wired and cordless networks. One can choose from a number of tracks that includes Cloud, Cooperation, Cyber-Ops, Data Facility, Industrial, Routing, and Switching, Safety, Service Provider, and Wireless.
Cisco Certified 200-301 training
The Cisco CCNA qualification, that represents Cisco Qualified Network Partner, represents a uniformity of technological expertise which Cisco certification offers to the IT globe. Cisco Certified Network Associate experts can interrelate to remote websites using a broad-area network (WAN), also reduce the basic network security threats, and recognize basic networking concepts and terminologies. The Cisco Certified CCNA and CCNP training course is to train the engineers, procedure control experts, and plant administrators, in addition to standard network and system designers those which deal with these industrial networks.
In accordance with, there are few Cisco CCNA networking routing and switching tracks that one can opt for:
· CCNA Routing and also Switching
· Cloud
· Partnership
· Information Facility
· Safety and security
· Cisco Certified Network Associate Provider
· Cyber ops
· CCDA
· Cisco Certified Network Associate Wireless
The Cisco CCNA and CCNP routing and switching certification training has surprisingly enlarged to become one of the most distinguished IT trainings across the globe. The main objective of Cisco CCNA and CCNP certification is to prioritize pushes building pertinent abilities to compare the lightening distribution of the modern technologies in today’s refined networking atmosphere. Having a CCNA and CCNP training course certification certifies that you can create primary networking abilities.
About CCNA and CCNP certification
Along with your CCNA certification, you can elevate your understanding of Cisco Networking routing and switching; this furnishes you coherent understanding that you can utilize in building your career. Today the networking world is tremendously expanding. The modern technologies are abnormally improving the networking domain and introducing different task functions. Therefore, this Cisco CCNA and CCNP certification course makes you an absolute fit for the task functions in the IT domain. The future of Cisco CCNA and CCNP certification is the best if you have a keen interest in networking. But it is the basics of networking certification. If you want to build your future in networking then you should go for it. And if you want to continue for the advanced, then Cisco Certified Network Associate goes for CCNP correspondingly.
The CCNA training course offers different occupation courses like Network Specialist, Helpdesk Engineer, Network Support Designer, Solution Desk Engineer, and many other options. In CCNP training course, you can also acquire several task probabilities like Network Analyst, Equipment and Network Designer, Network Professional, and IT Group Leader.
Through our CCNA and CCNP training course, you can find out networking principles as well as advanced concepts with practical techniques and simulations to elevate your abilities. Cisco Certified Network Associate Routing and Switching curriculum, evolve the abilities you need to get your dream job related to networking computer systems, devices, and things.
We are the Best Institute for Cisco CCNA-CCNP routing and switching training course. Our modules are designed as per the requirements of CCNA and CCNP Certification exam and the syllabus provided by Cisco. In order to get prepared for CCNA 200-301 exam conducted by Cisco, candidates must work on real devices instead of depending on simulators. We also provide the best Networking routing and switching Project based Industrial and Summer Trainings in Dehradun and Delhi. If you are looking for training on 200-301 CCNA Certification, then Brillica Services Pvt. Ltd is the best choice for you. We provide the best offline and online training on Cisco CCNA and CCNP – networking routing and switching.
For more information: https://www.brillicaservices.com/
0 notes
Text
SUPERBOWL CIPA SUNDAY: Does Samsung’s Website Chat Feature Violate CIPA?
Happy CIPA and Super Bowl Sunday TCPA World!
So, Samsung is under the spotlight with a new CIPA case brought by a self-proclaimed “tester.” You know like Rosa Parks?? Back to that in a bit.
The California Invasion of Privacy Act (“CIPA”) prohibits both wiretapping and eavesdropping of electronic communications without the consent of all parties to the communication. The Plaintiff’s bar is zoning…

View On WordPress
#business#CA privacy law#California#CIPA#Communications#Cybersecurity#Internet#legal#media#privacy#Samsung#TCPA#telecom law#Wiretapping
1 note
·
View note
Text
Case Study Spotlight: AI Transforming Telecom!
Check out how we helped a leading Australia-based #MVNO soar with a 40% increase in efficiency and 30% cost reduction.
Dive into our case study: https://www.avisysservices.com/casestudies/ai-in-telecom-case-study/

#AIInTelecom#SuccessStory#CaseStudy#AvisysServices#ArtificialIntelligence#AI#CSP#MNO#Telecom#Telco#Telecommunications#DigitalTransformation#5GTechnology#IoT#CustomerExperience#PredictiveAnalytics#TelecomInnovation#Cybersecurity#SustainableTech#OperationalEfficiency#TechSolutions#BusinessGrowth#AIForBusiness#TelecomAustralia
0 notes
Photo

Falsified SMS message attacks can result in direct financial losses for telecom carriers. Operators charge varying prices for terminating different sorts of SMS messages, however an attacker might use a forged terminating SMS to send out advertising or phishing messages without paying the operator's expenses. Terminating SMS messages provided by companies such as banks, social networks, and #Internet services generates a significant percentage of revenue for operators.
0 notes
Text
Secure your work from SS7 attack with SecurityGen
The SS7 protocol is used everywhere and is the leading protocol for connecting network communications around the world. .Because it is so common and used by both intelligence agencies and cell phone operators.From a surveillance perspective, it is very effective. As such, SS7 is an attacker's best friend, giving them access to the same surveillance capabilities as intelligence agencies and law enforcement.
To protect your work from ss7 attackers, SecurityGen has developed an Artificial Cybersecurity Expert platform or the ACE platform . ACE is the first AI-enabled breach and attack simulation platform in the telecom cybersecurity space. It automates the entire process of inspection, detection by giving network owners continuous, efficient 24x7 protection and saving millions of dollars.
#breach and attack simulation market#oss bss#ddos attack prevention#telecom cybersecurity#network attack protection#network breach detection#ss7 attack#signalling security
0 notes
Text
Bassam Infotech's Gitex Voyage with Odoo
Unveiling the Future with Bassam Infotech's Exciting Voyage at Gitex, Partnering with Odoo.

#GitexGlobal#Gitex2023#TechExpo#InnovationHub#TechShowcase#DigitalTransformation#TechConference#EmergingTech#BusinessOpportunities#NetworkingEvent#FutureTech#GlobalTech#SmartCities#Cybersecurity#Metaverse#DataEconomy#MobilitySolution#HealthTech#Telecom#IoT#FutureUrbanism#SuperBridge#MarketingMania#FutureBlockchainSummit#Tech#TechEvent#Connectivity#CommunicationTechnology#CommunicationPlatform
0 notes
Text
#datacenter#cloud#technology#cloudcomputing#data#tech#networking#server#cat#network#dataprotection#it#cybersecurity#cloudstorage#bigdata#cisco#networksecurity#networkengineer#telecom#software#database#serverroom#informationtechnology#business#ccna#security#cloudservices#storage#datacenters#o
0 notes
Text
Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has launched some of the most disruptive cyberattacks in history against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv.
On Tuesday, a cyberattack hit Kyivstar, one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a statement posted by Ukraine’s Computer Emergency Response Team, or CERT-UA.
Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, according to Reuters, that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.”
“We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.”
The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU.
“We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!”
Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.”
If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a wide variety of covers, hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its attack on the 2018 Winter Olympics.
Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information.
While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched more data-destroying wiper attacks on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled thousands of Viasat satellite modems across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, caused a blackout in a Ukrainian city just as it was being hit by missile strikes, potentially hampering defensive efforts.
It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids.
“Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
44 notes
·
View notes