#and fast data access speeds are critical. These hard disks are typically used in servers
Text
Enterprise Hard Disk Market Statistics, Segment, Trends and Forecast to 2032
An enterprise hard disk is a type of high-performance storage device designed for use in enterprise-level environments, where reliability, durability, and fast data access speeds are critical. These hard disks are typically used in servers, data centers, and other high-performance computing applications, where they are used to store large amounts of data and provide fast access to that data.
Enterprise hard disks are typically available in both SAS (Serial Attached SCSI) and SATA (Serial ATA) interfaces, and they come in a range of storage capacities. They are also designed to operate in high-temperature and high-vibration environments, which makes them suitable for use in data centers and other industrial settings.
One key feature of enterprise hard disks is their high reliability. They are designed with advanced error correction mechanisms and other technologies to minimize the risk of data loss due to hardware failure. Many enterprise hard disks also come with built-in redundancy features, such as RAID (Redundant Array of Independent Disks), which provides additional protection against data loss.
The estimated market size for the Enterprise Hard Disc Drives (HDD) Market is provided in terms of both value (million USD) and volume (K Units). Enterprise Hard Disc Drives (HDD) market size has been estimated and validated using both top-down and bottom-up methodologies. These approaches have also been used to estimate the size of numerous additional dependent submarkets within the overall market. Secondary research has been used to identify the major market participants, and primary and secondary research has been used to estimate their market shares. Both confirmed secondary sources and primary sources have been used to calculate all percentage shares, splits, and breakdowns.
Click Here, To Get Free Sample Report : https://stringentdatalytics.com/sample-request/enterprise-hard-disk-market/510/
Market Segmentations:
Global Enterprise Hard Disk Market: By Company
• Seagate
• Western Digital
• Toshiba
• Eaget
• Lenovo
• Founder
Global Enterprise Hard Disk Market: By Type
• External Hard Drives
• Internal Hard Drives
Global Enterprise Hard Disk Market: By Application
• For Desktop
• For Notebook
• For Server
Global Enterprise Hard Disk Market: Regional Analysis
All the regional segmentation has been studied based on recent and future trends, and the market is forecasted throughout the prediction period. The countries covered in the regional analysis of the Global Enterprise Hard Disk market report are U.S., Canada, and Mexico in North America, Germany, France, U.K., Russia, Italy, Spain, Turkey, Netherlands, Switzerland, Belgium, and Rest of Europe in Europe, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, China, Japan, India, South Korea, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), and Argentina, Brazil, and Rest of South America as part of South America.
Visit Report Page for More Details: https://stringentdatalytics.com/reports/enterprise-hard-disk-market/510/
Reasons to Purchase Charge Coupled Device (CCD) Market Report:
• To obtain insights into industry trends and dynamics, including market size, growth rates, and important factors and difficulties. This study offers insightful information on these topics.
• To identify important participants and rivals: This research studies can assist companies in identifying key participants and rivals in their sector, along with their market share, business plans, and strengths and weaknesses.
• To comprehend consumer behavior: these research studies can offer insightful information about customer behavior, including preferences, spending patterns, and demographics.
• To assess market opportunities: These research studies can aid companies in assessing market chances, such as prospective new goods or services, fresh markets, and new trends.
• To make well-informed business decisions: these research reports give companies data-driven insights that can aid in making well-informed business decisions, such as strategic.
Click Here.To Buy Premium Report: https://stringentdatalytics.com/purchase/enterprise-hard-disk-market/510/?license=single
About US:
Stringent Datalytics offers both custom and syndicated market research reports. Custom market research reports are tailored to a specific client's needs and requirements. These reports provide unique insights into a particular industry or market segment and can help businesses make informed decisions about their strategies and operations.
Syndicated market research reports, on the other hand, are pre-existing reports that are available for purchase by multiple clients. These reports are often produced on a regular basis, such as annually or quarterly, and cover a broad range of industries and market segments. Syndicated reports provide clients with insights into industry trends, market sizes, and competitive landscapes. By offering both custom and syndicated reports, Stringent Datalytics can provide clients with a range of market research solutions that can be customized to their specific needs.
Contact US:
Stringent Datalytics
Contact No - 91-9763384149
Email Id - [email protected]
Web - https://stringentdatalytics.com/
#Enterprise Hard Disk Market Statistics#Segment#Trends and Forecast to 2032#An enterprise hard disk is a type of high-performance storage device designed for use in enterprise-level environments#where reliability#durability#and fast data access speeds are critical. These hard disks are typically used in servers#and other high-performance computing applications#where they are used to store large amounts of data and provide fast access to that data.#Enterprise hard disks are typically available in both SAS (Serial Attached SCSI) and SATA (Serial ATA) interfaces#and they come in a range of storage capacities. They are also designed to operate in high-temperature and high-vibration environments#which makes them suitable for use in data centers and other industrial settings.#One key feature of enterprise hard disks is their high reliability. They are designed with advanced error correction mechanisms and other t#such as RAID (Redundant Array of Independent Disks)#which provides additional protection against data loss.#The estimated market size for the Enterprise Hard Disc Drives (HDD) Market is provided in terms of both value (million USD) and volume (K U#and primary and secondary research has been used to estimate their market shares. Both confirmed secondary sources and primary sources have#splits#and breakdowns.#Click Here#To Get Free Sample Report : https://stringentdatalytics.com/sample-request/enterprise-hard-disk-market/510/#Market Segmentations:#Global Enterprise Hard Disk Market: By Company#• Seagate#• Western Digital#• Toshiba#• Eaget#• Lenovo#• Founder#Global Enterprise Hard Disk Market: By Type
0 notes
Text
Why NAS Servers Are the Perfect Storage Solution for Your Business — Exeton

What is NAS?
A Network Attached Storage (NAS) system is a high-capacity storage device connected to a network, allowing authorized users to store and retrieve data from a centralized location. Essentially, a NAS device is a container for hard drives with built-in intelligence for file sharing and authorization.

QUMULO ACTIVE LICENSE + 4X SUPERMICRO A+ ASG-1014S 216TB-2X100GBE
Why Do Organizations Use NAS?
NAS systems are versatile, flexible, and scalable. They can be pre-populated with disks or diskless, and typically include USB ports for connecting printers or external storage drives, offering additional options for all connected users.
Do You Need IT to Manage NAS?
Managing a NAS device is straightforward and can be done through a browser-based utility. You might not need an IT professional on standby, making it an excellent choice for small businesses. NAS devices can also be accessed remotely, serving as a private Dropbox or Google Drive with much more storage and no monthly cost.
How Does a NAS Device Work?
A NAS device runs on any platform or operating system, functioning as a bundle of hardware and software with an embedded operating system. It consists of a network interface card (NIC), a storage controller, drive bays, and a power supply, and can contain two to five hard drives for redundancy and fast file access.

QUMULO ACTIVE LICENSE + 4X SUPERMICRO A+ WIO 1114S-WN10RT ALL-NVME 30TB
Benefits of Using NAS
NAS systems are becoming popular for businesses due to their effectiveness, scalability, and low-cost storage solutions. Here are some key benefits:
Speed: NAS can store and transfer files quickly, with rapid backup for incremental changes.
Control: Companies maintain total control over their data without relying on third-party storage.
Ease of Use: NAS devices are user-friendly and simple to manage, often featuring streamlined setup scripts.
Reliable Access: Positioned on a dedicated network, NAS provides uninterrupted access to data, even during internet service interruptions.
NAS vs. SAN Protocols
NAS and Storage Area Networks (SANs) are both networked storage solutions but differ in their approaches:
NAS: A single-storage device serving files over Ethernet, ideal for unstructured data like audio, video, and documents. Uses TCP/IP for data transfer.
SAN: A complex network of devices handling block storage inside databases, ideal for structured data. Uses FC protocol or Ethernet-based ISCSI for storage networks.
From a user perspective, NAS appears as a single device managing files, while SAN presents as a disk to the client OS, housing critical databases.
Why Small Businesses Use NAS
Small businesses require low-cost, scalable storage with easy operation and robust data backup. Here are some examples:
Telecom: A leading telecom operator needed an easily managed backup solution within their budget to handle internal data generated by employees. They chose NAS for its low cost and high-capacity file-sharing capabilities.
Banking: A cloud-based platform provider for the mortgage finance industry needed a scalable storage solution for 30 billion small files. They found NAS efficient and cost-saving, allowing more focus on customer service.
Criminal Justice: A national prison system needed reliable storage for high-definition video surveillance. They implemented a NAS solution with larger capacity and room for expansion, meeting their preservation requirements.
HPE NAS Solutions
Hewlett Packard Enterprise (HPE) offers secure, tailored, and economically feasible NAS solutions for businesses of all sizes. Their platforms are resilient and self-protecting, with features like data encryption, sophisticated access controls, file access auditing, and deletion prevention to reduce security risks.
HPE StoreEasy: Designed to maximize capacity, simplify management, and scale as businesses grow, supporting tens of thousands of concurrent users and ensuring data security with built-in encryption.
HPE Apollo 4000 Systems: Intelligent data storage servers that offer accelerated performance, end-to-end security, and predictive analytics for storage-intensive workloads.
Conclusion
NAS systems provide an efficient, scalable, and cost-effective storage solution for businesses of all sizes. With their ease of use, speed, control, and reliable access, NAS devices are ideal for managing growing volumes of data. HPE’s NAS solutions offer secure and tailored options to meet diverse business needs, making them a perfect choice for modern data storage requirements.
Muhammad Hussnain
Facebook | Instagram | Twitter | Linkedin | Youtube
0 notes
Text
SAN Storage: The Backbone of Enterprise Data Management
In the world of enterprise data management, Storage Area Network (SAN) technologies play a pivotal role in meeting the escalating demands for efficient, resilient, and scalable data storage. SAN storage solutions underpin the infrastructure that supports mission-critical applications, high-performance computing, and the vast expanse of data that modern businesses generate and rely upon. This comprehensive guide illuminates the key concepts, current trends, and best practices for leveraging SAN technologies to optimize enterprise data management strategies.
Why Is SAN Storage Crucial for Modern Enterprises?
Before examining SAN storage in further depth, it's essential to understand the context that makes such storage solutions a critical component of modern enterprise architectures.
Scalability and Performance
Enterprise data is not only growing in volume but also in complexity and types. From structured data in databases to unstructured data in files, the storage solution must accommodate a variety of data types while providing fast and reliable access to support business operations. SAN storage can be easily scaled to handle growing data requirements without significant impact on performance, thereby ensuring that applications operate at the required efficiency levels.
Consolidation and Virtualization
The trend toward data center consolidation and virtualization has made SAN storage almost indispensible. By centralizing storage resources, SANs help in more efficient use of storage capacity and also facilitate data protection and disaster recovery. Virtualization technologies can further enhance these benefits, allowing for efficient allocation of storage resources and simplification of data management tasks.
Reliability and Management
SAN storage arrays typically offer a suite of features for maintaining data integrity, such as automatic failover, snapshot capabilities, and remote replication. Additionally, SAN management software provides a unified interface for monitoring and controlling the entire storage network, which can be quite extensive in large enterprises.
What Is a Storage Area Network (SAN)?
A Storage Area Network is a dedicated, high-speed network that interconnects and presents shared pools of storage devices to multiple servers. SANs are typically composed of storage elements that include disk arrays, servers, switches, and connectivity devices and are designed to be highly available and fault-tolerant.
Components of a SAN
The fundamental building blocks of a SAN are:
Host Bus Adapters (HBAs): These network interface cards (NICs) are specifically designed for connecting servers to the SAN.
Switches: High-speed fiber channel or Ethernet switches connect the components within the SAN to facilitate data transfer.
Storage Devices: SAN can support various types of storage devices, from traditional hard disk drives to the latest in All-Flash Arrays (AFAs).
Storage Network Software: This includes the firmware that runs on the storage devices and the SAN management software that oversees the operation of the entire storage environment.
SAN Topologies
There are several SAN topologies, each designed to meet specific requirements:
Fibre Channel: Historically the most common and preferred protocol due to its high performance and reliability.
iSCSI: An IP-based protocol allowing organizations to use existing network infrastructures for SAN connectivity.
Fibre Channel over Ethernet (FCoE): A convergence technology that allows Fibre Channel traffic to run over Ethernet networks.
Converged Enhanced Ethernet (CEE): A standard for transport of Fibre Channel over Ethernet that incorporates Quality of Service (QoS) for prioritization of storage traffic.
Key Considerations for Implementing SAN Storage
Implementing a SAN storage solution is a non-trivial task, and several considerations should be taken into account to ensure success.
Requirements Analysis
Start with a comprehensive analysis of your organization's storage needs. Consider factors such as capacity, performance requirements, budget, and future growth projections. This analysis is essential for choosing the right type of SAN for your enterprise.
Design and Architecture
The design of the SAN architecture involves selecting the right components and connectivity to meet your performance and availability goals. Redundancy and failover mechanisms should be integral parts of the design to provide business continuity.
Security and Compliance
Data security is paramount in enterprise storage solutions. SANs should be designed with appropriate access controls, encryption technologies, and in compliance with industry regulations and best practices to protect sensitive data.
Scalability
The SAN architecture must be flexible enough to grow with the organization. This means using components that can be easily expanded, adding new switches, and integrating new storage arrays without causing significant downtime.
Best Practices for Managing a SAN
Once a SAN is in operation, efficient management is crucial to its success and the continuity of business services.
Regular Monitoring
Continuous monitoring of SAN performance and health indicators can help identify potential issues before they escalate and impact business operations.
Automation
Leverage automation tools to simplify routine management tasks and improve the efficiency of storage operations. These tools can handle tasks such as provisioning, snapshot and replication management, and performance tuning.
Training and Expertise
SAN technology is complex and constantly evolving. Investing in training for IT staff and staying current with the latest SAN advancements can ensure that your team remains proficient in managing the storage environment.
Regular Updates and Patches
Keep SAN software up to date with the latest patches and firmware updates. This not only ensures that the SAN is secure but also that it benefits from new features and performance enhancements.
Trends Shaping the Future of SAN Storage
The storage industry is dynamic, and several emerging trends are influencing the evolution of SAN technology.
Software-Defined Storage (SDS)
SDS abstracts storage resources from the underlying hardware, allowing for greater flexibility, cost savings, and simplified management. SANs are increasingly being re-architected to support SDS models.
NVMe Over Fabrics (NVMe-oF)
This technology extends the benefits of Non-Volatile Memory Express (NVMe) storage directly over a network fabric, such as a SAN. It enables even higher performance and lower latencies than traditional SAN setups.
Hybrid Cloud Integration
SAN manufacturers and cloud service providers are working to integrate SAN storage more seamlessly with hybrid cloud environments, allowing organizations to extend their on-premises storage into the cloud with greater ease.
Data Management and Analytics
Intelligent data management and analytics are finding their way into SAN storage solutions, providing insights into storage usage trends, optimizing performance, and supporting more informed decisions.
In Conclusion
SAN storage remains an invaluable asset in the enterprise data ecosystem, providing the reliability, performance, and scalability necessary for modern business demands. By understanding the key principles, best practices, and future trends discussed in this guide, IT professionals, data center managers, and storage engineers can better harness the power of SAN technologies to transform their enterprise data management strategies. Whether it's enabling virtualization, enhancing disaster recovery, or laying the foundation for future storage innovations, the role of SAN solution is only set to grow in the coming years.
0 notes
Text
UCSD storage
A storage server may be a sort of server wont to store and manage digital data and acts as a backup server to store backup data. A storage server are going to be used for storing both small and enormous amount of knowledge over a shared network. Although the necessity for storage is clear , it's not always clear which solution is true for your organization. There are a spread of options available, the foremost prevalent are direct-attached storage (DAS), network-attached storage (NAS) and cargo area networks (SAN). Choosing the proper storage solution are often as personal and individual decision. there's nobody right account everyone. Instead, it's important to specialise in the precise needs and long-term business goals of your organization. Several key criteria to think about include: Read More
1 - Capacity
2 - Performance
3 - Scalability
4 - Availability & reliability
5 - Data protection
6 - IT staff and Resources available
7 - Budgets concern
DAS (Direct Attached Storage):
Direct Attached Storage (DAS) may be a digital memory device that's attached on to a server or PC via cable, meaning that DAS isn't a neighborhood of the storage network. A DAS device could also be an indoor or external hard disc drive like internal disk drive in PC. These disk drives are often protected with different RAID levels, counting on data importance and criticality. For the server, a DAS storage is extremely much almost like its own drive or an drive that has been plugged in.
The main interfaces used for DAS connection include Advanced Technology Attachment (ATA), Serial Advanced Technology Attachment (SATA), eSATA, Small computing system Interface (SCSI), Serial Attached SCSI (SAS), and Fiber Channel.
It is worth mentioning that prime access rate thanks to network absence, capability of storage capacity extension, data security and fault tolerance are a number of advantages of DAS. However, the first benefits of DAS include low cost and ease . Since it doesn't need components of network storage systems like routers, switches and appropriate cabling and connections. the disadvantage of DAS is that it's not accessible by multiple user groups and just one user at a time is allowed.
DAS is that the most elementary level of storage. The storage devices are a part of the host computer or directly connected to one server, during which the workstation must access the server so as to attach to the memory device . On the other side, NAS and SAN are connected to workstation and servers over a network. within the DAS, if the server is down or experiencing problems, users can't store and access data. Surveillance images can't be retrieved or stored. If the organization grows and wishes new servers, storage for every server must be administered separately.
NAS (Network Attached Storage):
NAS may be a sort of file memory device that connects to a network. NAS devices, which usually don't have a keyboard or display, provide Local Area Network (LAN) nodes with file storage through a typical Ethernet connection. In fact, NAS employs an Ethernet connection for sharing files over the network.
Each NAS on the LAN acts as an independent network node which has its own IP address. Since the NAS device has an IP address, it'll be accessible over the network via that IP address. NAS devices are often built with single drive or multiple drives. The latter provides higher capacity and greater data protection.
The existence of multiple computers on the network, may be a candidate for employing a network attached storage (NAS) device. Some NAS servers are just used for backing up and sharing files across the network, while others can do more tasks, like sharing a printer among the networked PCs, acting as a media streamer or maybe a closed-circuit television by supporting IP cameras.
NAS has benefits like good reading and writing performance, good data redundancy and protection options, offering security via encoding , sharing files, backing up data from Windows, Mac, and possibly Linux machines and offering some cloud service for storage and backup.
The application of NAS in homes is storing and serving multimedia files and automatic backup. as an example , many smart TVs use NAS to supply centralized storage. If a NAS device features a server mode, it also can act as an email, multimedia, database or print server for alittle business. In enterprise level, a NAS array are often used as a backup for archiving and recovery. Also, some NAS products can hold enough disks to support RAID for greater data protection.
For those systems that has got to store an outsized amount of videos/images for several days, NAS may be a good option. Network-Attached Storage comprised of both hard disks and management software. NAS serves files over a network. As a result, NAS relieves the server of storage and file serving responsibilities and provides more flexibility in data access, due to its independence.
SAN (Storage Area Network):
A cargo area Network (SAN) may be a secure high-speed data transfer network during which storage devices can access to multiple servers. it's a high-performance storage network that transfers data between servers and storage devices break away local area network. SAN is usually used where larger areas of high-speed storage and fast input-output space is required.
In contrast to DAS or NAS, which are optimized for data sharing at the primary level, the strength of the SAN lies in its ability to maneuver large blocks of knowledge . this is often so important for Band-Width intensive applications like IP/Megapixel camera system recording. It provides block-level storage, meaning that when a number wants to access a memory device , it sends a block-based access request for that memory device . SAN storage devices include disk-based devices like RAID.
SAN implementation which is in two following types, results in consistent and secure data transferring. counting on what type is employed , differing types of cabling, protocols and routing equipment are used.
Fiber channel (FC): Storage and servers are connected through a high-speed network of unified fiber channel switches. this is often used for mission-critical applications where continuous data access is required. Fiber channel provides data retrieval speed quite 5 Gbps.
Internet Small computing system Interface (ISCSI) Protocol: SCSI may be a standard wont to communicate between servers and storage devices. By this infrastructure, the pliability of a low-cost IP network is achieved.
In a SAN network, data transferring from one storage to a different is conducted without or with minimal server intervention. SAN provides dynamic failover protection which suggests if a server fails or goes offline for maintenance, network operation continues. Also, additional capacity are often added to SAN as needed . These, are the benefits of SAN. the most disadvantages of SANs are cost and complexity. Because SAN hardware is dear and also building and managing a SAN, require a special skill set.
The distributed architecture of SAN enables it to supply higher level of performance and reliability. SANs provide fast data transfer while reducing latency and server workload.
VSA (Virtual Storage Appliance):
Virtual Storage Appliance (VSA) may be a storage controller which runs on a virtual machine to make a shared storage without the necessity of additional hardware. It presents either file-level or block-level storage to the network.
VSA isn't a connected physical device to any specific hardware. It uses the host system's local disk for storage as a virtual disk or it can access to local physical drives directly. In fact, the VSA creates a virtual memory area almost like networked storage by incorporating direct-attached capacity on each physical host. Small businesses that require redundancy and high availability for shared storage and also large enterprises which transfer data between various arrays, are good usage candidates for the virtual memory appliance.
The differences between NAS, SAN and DAS:
NAS differs from a SAN within the way they distribute storage to other devices, meaning that the most difference between these two, is access protocols. NAS supports data storage under CIFS and NFS protocols (file-level), while access protocols in SAN are ISCSI and Fiber channel (block level).
On the opposite hand, it's going to seem, DAS is quicker than the other storage methods. Since it needs data transferring over the network, while all data transferring are going to be occurred on a fanatical connection between the server and therefore the memory device . However, thanks to high speed connection of fiber channel, in some cases SAN presents faster speed compared to hurry provided by DAS. Also, Since SAN separates storage from the servers and incorporates them during a place where it are often accessed by any application, it provides better flexibility, availability and storage performance compared to DAS for giant organization. So, thanks to the improved storage performance of SAN, organizations won't need additional storage hardware, which saves money, although SAN hardware are often costly. Moreover, separating memory device from the servers, allows computing resources on the servers to perform other tasks not associated with storage.
On the opposite hand, the difference between DAS and Network Attached Storage (NAS) is that a DAS device connects on to a server without a network connection. DAS gives good performance, but there are limitations just like the number of servers which will access thereto . Also DAS storage has got to be almost the server within the same rack. The advantage of NAS over DAS is that it simplifies file sharing among multiple users. the most difference is about how the pc or the server treats a specific storage. If the server's processor is liable for managing the attached storage, it'll be some sort of DAS and if the pc or the server treats the attached storage as another computer, which shares its data through the network, then it's a NAS. UCSD storage
1 note
·
View note
Text
Top 5 High Availability Dedicated Server Solutions
What Is a High Availability Dedicated Server?
A typical dedicated server is a powerful computer which is connected to a high-speed Internet connection, and housed in a state-of-the-art remote data center or optimized data facility.
A High Availability dedicated server is an advanced system equipped with redundant power supplies, a fully redundant network, RAID disk towers and backups, ensuring the highest uptime and the full reliability with no single point of failure.
Configuration For High Availability Dedicated Servers
As its name implies, high availability dedicated solutions are scalable and customized hosting solutions, designed to meet the unique needs of any business.
These configurations are carefully designed to provide fail-proof architecture to run the critical applications in your business – those that demand the highest availability.
Possible high availability server configurations might include multiple hosts managed by redundant load balancers and replication hosts. As well as redundant firewalls for added security and reliability.
Why High Availability Server Is Important for Business
Nowadays businesses rely on the Internet. Let’s face it – even the smallest downtime can cause huge losses to business. And not just financial losses. Loss of reputation can be equally devastating.
According to StrategicCompanies more than half of Fortune 500 companies experience a minimum of 1.6 hours of downtime each and every week. That amounts to huge losses of time, profit, and consumer confidence. If your customer can’t reach you online, you might as well be on the moon, as far as they are concerned.
Consider: In the year 2013, 30 minutes of an outage to Amazon.com reportedly cost the company nearly $2 million. That’s $66,240 per minute. Take a moment to drink that in. Even if you’re not Amazon, any unplanned downtime is harmful to your business.
Your regular hosting provider may provide 99% service availability. That might sound good, in theory. But think about that missing 1%… That’s 87 hours (3.62 days) of downtime per year! If the downtime hits during peak periods, the loss to your business can be disastrous.
The best way to prevent downtime and eliminate these losses is to opt for high availability hosting solutions.
Built on a complex architecture of hardware and software, all parts of this system work completely independently of each other. In other words – failure of any single component won’t collapse the entire system.
It can handle very large volume of requests or a sudden surge in traffic. It grows and shrinks with the size and needs of your organization. Your business is flexible, shouldn’t your computer systems be, as well?
Following are some of the best high availability solutions you can use to host your business applications.
1. Ultra High Performance Dedicated Servers
High performance servers are high-end dedicated solutions with larger computing capacity, especially designed to achieve the maximum performance. They are an ideal solution to cater enterprise workloads.
A typical high performance dedicated server will consist of the following:
Single/Dual latest Intel Xeon E3 or E5 series processors.
64 GB to 256 GB RAM
8 to 24 TB SATA II HDD with RAID 10
Energy efficient and redundant power supply & cooling units
Offsite Backups
Note that the list above is just a sample configuration which can be customized/upgraded as per your unique requirements. If you need more power, we can build a setup with 96 drives, 3 TB RAM, and 40+ physical CPU cores.
Real World Applications (Case Study)Customer’s Requirement
One of our existing customers was looking for a high-end game server to host flash games with encoded PHP and MySQL server as a backend.
To achieve the highest availability, they demanded 2 load balancers with failover. Each of them contains 2 web servers and a database server.
Website Statistics
8000-10000 simultaneous players
100% uptime requirement
10 GB+ database size
Solution Proposed by AccuWebHosting
Our capacity planning team designed a fully redundant infrastructure with dual load balancers sitting in front of web and database servers.
This setup consists of 2 VMs with load balancers connected to a group of web servers through a firewall. The database server was built on ultra-fast SSD drives for the fastest disk I/O operations.
For a failover, we set up an exact replica of this architecture with real-time mirroring. Should the primary system fail, the secondary setup will seamlessly take over the workload. That’s right. Zero downtime.
Infrastructure Diagram

2. Load Balanced Dedicated Servers
Load Balancing
The process of distributing incoming web traffic across a group of servers efficiently and without intervention is called Load Balancing.
A hardware or software appliance which provides this load balancing functionality is known as a Load Balancer.
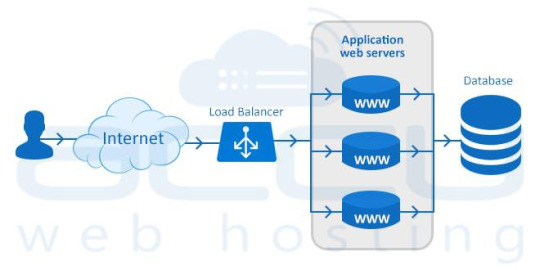
The dedicated servers equipped with a hardware/software load balancer are called Load Balanced Dedicated Servers.
How Load Balancing Works?
A load balancer sits in front of your servers and routes the visitor requests across the servers. It ensures even distribution, i.e., all requests must be fulfilled in a way that it maximizes speed and capacity utilization of all servers and none of them is over or under-utilized.
When your customers visit your website, they are first connected to load balancer and the load balancer routes them to one of the web servers in your infrastructure. If any server goes down, the load balancer instantly redirects the traffic to the remaining online servers.
As web traffic increases, you can add new servers quickly and easily to the existing pool of load-balanced servers. When a new server is added, the load balancer will start sending requests to new server automatically. That’s right – there’s no user-intervention required.
Types Of Load Balancing
Load balancing can be performed with one of the following methods.
Load Balancing Through DNS
Load Balancing Through Hardware
Load Balancing Through Software
Load Balancing With DNS
The DNS service balances the web traffic across the multiple servers. Note that when you perform the traffic load balancing through this method you cannot choose which load balancing algorithm. It always uses the Round Robin algorithm to balance the load.
Load Balancing Through Hardware
This is the most expensive way of load balancing. It uses a dedicated hardware device that handles traffic load balancing.
Most of the hardware based load balancer systems run embedded Linux distribution with a load balancing management tool that allows ease of access and a configuration overview.
Load Balancing Through Software
Software-based load balancing is one of the most reliable methods for distributing the load across servers. In this method, the software balances the incoming requests through a variety of algorithms.
Load Balancing Algorithms
There are a number of algorithms that can be used to achieve load balance on the inbound requests. The choice of load balancing method depends on the service type, load balancing type, network status and your own business requirements.
Typically, for low load systems, simple load balancing methods (i.e., Round Robin) will suffice, whereas, for high load systems, more complex methods should be used. Check out this link for more information on some industry standard Load Balancing Algorithms used by the load balancers.
Setup Load Balancing On Linux
HAProxy (High Availability Proxy) is the best available tool to set up a load balancer on Linux machines (web server, database server, etc).
It is an open-source TCP and HTTP load balancer used by some of the largest websites including Github, StackOverflow, Reddit, Tumblr and Twitter.
It is also used as a fast and lightweight proxy server software with a small memory footprint and low CPU usage.
Following are some excellent tutorials to setup a load balancing on Apache, NGINX and MySQL server.
Setup HAProxy as Load Balancer for Nginx on CentOS 7
Setup High-Availability Load Balancer for Apache with HAProxy
Setup MySQL Load Balancing with HAProxy
Setup Load Balancing On Windows
Check out below the official Microsoft document to setup load balancing with IIS web server.
Setup Load Balancing on IIS
3. Scalable Private Cloud
A scalable private cloud is a cloud-based system that gives you self-service, scalability, and elasticity through a proprietary architecture.
Private clouds are highly scalable that means whenever you need more resources, you can upgrade them, be it memory, storage space, CPU or bandwidth.
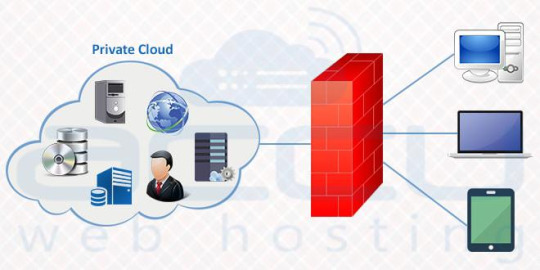
It gives the best level of security and control making it an ideal solution for a larger business. It enables you to customise computer, storage and networking components to best suit custom requirements.
Private Cloud Advantages
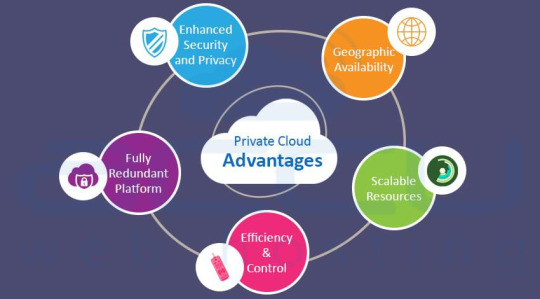
Enhanced Security & Privacy
All your data is stored and managed on dedicated servers with dedicated access. If your Cloud is on-site, the server will be monitored by your internal IT team and if it is at a datacenter, their technicians will monitor it. Thus, physical security is not your concern.
Fully Redundant Platform
A private cloud platform provides a level of redundancy to compensate from multiple failures of the hard drive, processing power etc. When you have a private cloud, you do not have to purchase any physical infrastructure to handle fluctuation in traffic.
Efficiency & Control
Private cloud gives you more control on your data and infrastructure. It has dedicated resources and no one else has access of the server except the owner of the server.
Scalable Resources
Each company has a set of technical and business requirements which usually differ from other companies based on company size, industry and business objectives etc.
A private cloud allows you to customize the server resources as per your unique requirements. It also allows you to upgrade the resources of the server when necessary.
Private Cloud DisadvantagesCost
As compared to the public cloud and simple dedicated server setup, a private cloud is more expensive. Investments in hardware and resources are also required.
You can also rent a private cloud, however the costs will likely be the same or even higher, so this might not be an advantage.
Maintenance
Purchasing or renting a private cloud is only one part of the cost. Obviously, for a purchase, you’ll have a large outlay of cash at the onset. If you are renting you’ll have continuous monthly fees.
But even beyond these costs, you will need to consider maintenance and accessories. Your private cloud will need enough power, cooling facilities, a technician to manage the server and so on.
Under-utilization
Even if you are not utilizing the server resources, you still need to pay the full cost of your private cloud. Whether owning or renting, the cost of capacity under-utilization can be daunting, so scale appropriately at the beginning of the process.
Complex Implementation
If you are not tech savvy, you may face difficulties maintaining a private cloud. You will need to hire a cloud expert to manage your infrastructure, yet another cost.
Linux & Windows Private Cloud Providers
Cloud providers give you an option to select your choice of OS: either Windows or any Linux distribution. Following are some of the private cloud solution providers.
AccuWebHosting
Amazon Web Services
Microsoft Azure
Rackspace
Setting Up Your Own Private Cloud
There are many paid and open source tools available to setup your own private cloud.
OpenStack
VMware vSphere
VMmanager
OnApp
OpenNode Cloud Platform
OpenStack is an open source platform that provides IAAS (Infrastructure As A Service) for both public and private cloud.
Click here to see the complete installation guide on how you can deploy your own private cloud infrastructure with OpenStack on a single node in CentOS or RHEL 7.
4. Failover
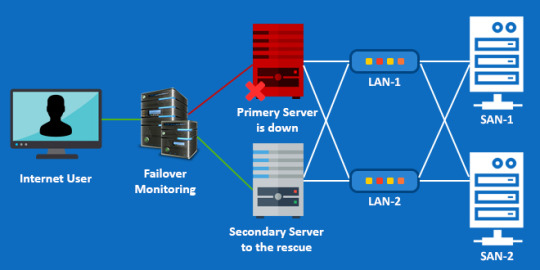
Failover means instantly switching to a standby server or a network upon the failure of the primary server/network.
When the primary host goes down or needs maintenance, the workload will be automatically switched to a secondary host. This should be seamless, with your users completely unaware that it happened.
Failover prevents a single point of failure (SPoF) and hence it is the most suitable option for mission critical applications where the system has to be online without even one second of downtime.
How Failover Works?
Surprisingly, automated failover system is quite easy to set up. A failover infrastructure consists of 2 identical servers, A primary server and a secondary. Both servers will serve the same data.
A third server will be used for monitoring. It continuously monitors the primary server and if it detects a problem, it will automatically update the DNS records for your website so that traffic will be diverted to the secondary server.
Once the primary server starts functioning again, traffic will be routed back to primary server. Most of the time your users won’t even notice a downtime or lag in server response.
Failover TypesCold Failover
A Cold Failover is a redundancy method that involves having one system as a backup for another identical primary system. The Cold Failover system is called upon only on failure of the primary system.
So, Cold Failover means that the second server is only started up after the first one has been shut down. Clearly this means you must be able to tolerate a small amount of downtime during the switch-over.
Hot Failover
Hot Failover is a redundant method in which one system runs simultaneously with an identical primary system.
Upon failure of the primary system, the Hot Failover system immediately takes over, replacing the primary system. However, data is still mirrored in real time ensuring both systems have identical data.
Setup Failover
Checkout the below tutorials to setup and deploy a failover cluster.
Setup Failover Cluster on Windows Server 2012
Configure High Avaliablity Cluster On CentOS
The Complete Guide on Setting up Clustering In Linux
Available Solutions
There are four major providers of failover clusters listed as below.
Microsoft Failover Cluster
RHEL Failover Cluster
VMWare Failover Cluster
Citrix Failover Cluster
Failover Advantages
Failover Server clustering is completely a scalable solution. Resources can be added or removed from the cluster.
If a dedicated server from the cluster requires maintenance, it can be stopped while other servers handle its load. Thus, it makes maintenance easier.
Failover Disadvantages
Failover Server clustering usually requires more servers and hardware to manage and monitor, thus, increases the infrastructure.
Failover Server clustering is not flexible, as not all the server types can be clustered.
There are many applications which are not supported by the clustered design.
It is not a cost-effective solution, as it needs a good server design which can be expensive.
5. High Availability Clusters

A high availability cluster is a group of servers that support server applications which can be utilized with a minimal amount of downtime when any server node fails or experiences overload.
You may require a high availability clusters for any of the reasons like load balancing, failover servers, and backup system. The most common types of Cluster configuration are active-active and active-passive.
Active-Active High Availability Cluster
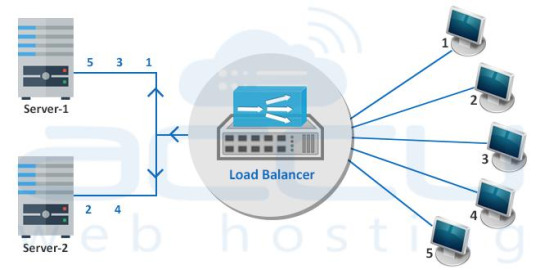
It consists of at least two nodes, both actively running same the service. An active-active cluster is most suitable for achieving true load balancing. The workload is distributed across the nodes. Generally, significant improvement in response time and read/write speed is experienced.
Active-Passive High Availability Cluster
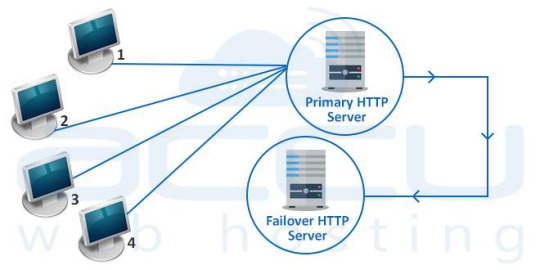
Active-passive also consists of at least two nodes. However, not all nodes remain active simultaneously. The secondary node remains in passive or standby mode. Generally, this cluster is more suitable for a failover cluster environment.
Setup A High Availability Cluster
Here are some excellent tutorials to setup a high availability cluster.
Configuring A High Availability Cluster On CentOS
Configure High-Availability Cluster on CentOS 7 / RHEL 7
Available Solutions
There are very well-known vendors out there, who are experts in high availability services. A few of them are listed below.
Dell Windows High Availability solutions
HP High Availability (HA) Solutions for Microsoft and Linux Clusters
VMware HA Cluster
High Availability Cluster Advantages
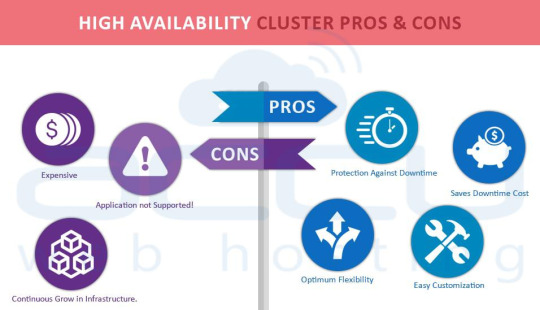
Protection Against Downtime
With HA solutions, if any server of a cluster goes offline, all the services are migrated to an active host. The quicker you get your server back online, the quicker you can get back to business. This prevents your business from remaining non-productive.
Optimum Flexibility
High availability solutions offer greater flexibility if your business demands 24×7 availability and security.
Saves Downtime Cost
The quicker you get your server back up online, the quicker you can get back to business.This prevents your business from remaining non-productive.
Easy Customization
With HA solutions, it is a matter of seconds to switch over to the failover server and continue production. You can customize your HA cluster as per your requirement. You can either set data to be up-to-date in minutes or within seconds. Moreover, the data replication scheme, versions can be specified as per your needs.
High Availability Cluster Disadvantages
Continuous Grow in infrastructure
It demands many servers and loads of hardware to deliver a failover and load balancing. This increases your infrastructure.
Application Not Supported!
HA clustering offers much flexibility at the hardware level but not all software applications support clustered environment.
Expensive
HA clustering is not a cost-effective solution, the more sophistication you need, the more money you need to invest.
6. Complex Configuration Built By AccuWebHosting
Customer’s Requirement
An eCommerce website that can handle the peak load of 1000 HTTP requests per second, more than 15,000 visitors per day and 3 times the load in less than 10 seconds. During the peak hours and new product launches, visits count to the website will be multiplied by 2.
Website Statistics
40K products and product related articles
40 GB of static contents (images and videos and website elements)
6 GB of database
Solution We Delivered
We suggested a high availability Cloud Infrastructure, to handle the load and ensure the maximum availability as well. To distribute the load, we mounted 2 load balancer servers in front of the setup with load balanced IP address on top of them.
We deployed a total of 8 web servers, 3 physical dedicated servers, and 5 Cloud instances to absorb the expected traffic. The setup was configured to get synchronized between the various components through the rsync cluster.
The Cloud instances were used in a way that they can be added or removed as per load of the peak traffic without incurring the costs associated with additional physical servers.
Each Cloud instance contained the entire website (40GB of static content) to give the user a smooth website experience.
The 6 GB database was hosted on a master dedicated server, which was replicated on a secondary slave server to take over when the master server fails. Both of these DB servers have SSD disks for better read/write performance.
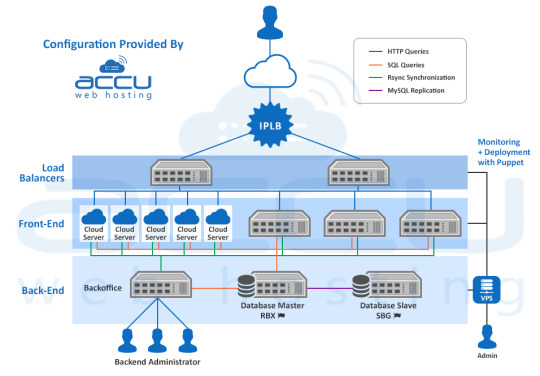
A team of 15 developers and content writers update the content through backoffice servers hosted on a dedicated server. Any changes made by the team are propagated by rsync on the production environment and the database.
The entire infrastructure was monitored by Zabbix, which is installed on a high availability Cloud VPS. Zabbix will monitor the data provided by the infrastructure servers and then generate a series of graphs to depict the RAM usage, load average, disk consumption and network stats. Zabbix will also send an alert when any of the usage reaches its threshold or if any of the services goes down.
0 notes
Text
DAS, NAS and SAN
The digital universe is rapidly expanding. Doubling every two years. With this explosion of data, companies of all sizes must implement efficient data storage solutions. Navigating the storage landscape can be tricky – especially if we’ve never purchased storage at the business level – or if the business storage needs have recently changed and we’re not sure what to do next. Businesses can choose from a variety of storage options including:
· Direct Attached Storage (DAS)
· Network Attached Storage (NAS)
· Storage Area Network (SAN)
Direct Attached Storage (DAS)
Suppose we own a small Photography business with 7 on-site employees. We would need a simple, versatile solution that would be easy to use yet giving fast performance for quick turn jobs. DAS proves to be the picture-perfect choice. We purchase some high-capacity backup hard drives. This solution offers a simple, economical and efficient way for the photographers in the field to save and backup photo images. We can also access data in a snap, speeding up the photo editing process and the delivery of images to clients. DAS can be ideal for small businesses.
DAS is a fairly basic, low-maintenance, low-cost solution where the storage system is a part of the actual host computer or connected directly to the host computer. This could be as simple as an external hard drive and it’s the opposite of network storage, where workstations and servers connect through a network. DAS is used in many IT infrastructures and larger DAS storage units can accommodate multiple disks in one storage enclosure. However, for some business applications requiring greater flexibility and data sharing across teams, DAS’ ability to grow and scale is limited – especially, if we expected to see a lot of business growth over a short period of time. DAS is ideal for small businesses that only need to share data locally, have a defined, non-growth budget to work with and have little to no IT support to maintain a complex system. DAS is not a good choice for businesses that are growing quickly, need to scale quickly, need to share across distance and collaborate or support a lot of system users and activity at once.
Network-Attached Storage (NAS)

Suppose we have an IT director in an accounting firm with 70 employees over 3 locations. We would be looking for a centralized storage solution with secure remote data access, file sharing among employees in different offices and scalability for future growth. NAS anchored by NAS optimized hard drives offers a practical, reliable and affordable solution surpassing the firm’s bottom-line expectations. NAS also delivers ample storage for today and room to grow for tomorrow. Talk about a good return on investment! With NAS, our colleagues and various departments and locations can easily share or access files while keeping client financial information secure. All this from the office, on the go or at home.
NAS offers dedicated file serving and sharing through a network. It increases performance and reliability with features like RAID and swappable drives designed for higher multi-drive workloads. NAS storage is also a good solution for consolidating storage systems from DAS – plus, having one centralized, shared storage system will save money in the long run, eliminate confusion and increase reliability in case of system failure or outage. NAS is known as a top choice for Small and Medium Businesses (SMBs). NAS is perfect for SMBs and organizations that need a minimal-maintenance, reliable and flexible storage system that can quickly scale up as needed to accommodate new users or growing data. Server-class devices at enterprise organizations that need to transfer block-level data supported by a Fiber Channel connection may find that NAS can’t deliver everything that’s needed. Maximum data transfer issues could be a problem with NAS.
Storage-Area Network (SAN)
Now about data storage for large enterprises. Suppose we have a CTO of a large wind turbine manufacturing company with 5 Office locations. We would consider a NAS solution, but the size of the company and significant amounts of structured and unstructured data require a more extensive storage option. Our choice to invest in SAN would be a breeze due to ultimate reliability, fast performance, access to large blocks of data from any location and huge capacities. SAN blows beyond file sharing with a dedicated network to move full blocks of data between servers and storage devices all at high speed and with large amounts of proprietary data traversing virtual space, throwing caution to the wind is not an option for the company. SAN solution delivers much needed data security. Clearly efficient data storage is critical to business success.
SAN is a dedicated, high-performance storage system that transfers block-level data between servers and storage devices. SAN is typically used in data centers, enterprises or virtual computing environments. It offers the speed of DAS with the sharing, flexibility and reliability of NAS. SAN storage is a very sophisticated option that’s meant to support complex, mission-critical applications. SAN is best for block-level data sharing of mission-critical files or applications at data centers or large-scale enterprise organizations. SAN can be a significant investment and is a sophisticated solution that’s typically reserved for serious large-scale computing needs. A small-to-midsize organization with a limited budget and few IT staff or resources likely wouldn’t need SAN.
Key Criteria to Consider
· Capacity
· Scalability
· Reliability
· Backup and Recovery
· Performance
· Budget
· IT Staff and Resources
Choosing the best storage option for the business really comes down to deciding which network criteria are most important. Once we know which factors are essential to the business operations, we can find the storage option to fit the particular needs.
DAS can be the simplest, most economical option for business owners with 6-7 employees in one location. While SAN delivers top capacity and security for large enterprise applications and businesses with more than 70 employees and 4-5 locations. Yet for small to mid-size businesses, with 60-70 employees and 2-3 locations, affordable NAS solutions containing NAS optimized hard drives addresses key needs for today’s small to mid-size businesses. Scalability, reliability, remote access, collaboration, bring your own device trends using DAS, NAS or SAN, businesses can customize data storage and continue impacting the world within the ever-expanding digital universe!
-Dhruven Mihir Shah
0 notes
Text
The Value Of Dedicated Server Cost in India
To bring this down to earth allow's take the example of real estate. With a dedicated web server organizing solution, you're renting a whole home. There are numerous bedrooms, nothing else renters, and it's your own to do whatever you want with.
What is Dedicated Web server?
to make sure that it can be accessed from any type of os whether Linux, Windows organizing and so on . top article Customers can even set up applications based on their passion by accessing the inbuilt control panel. Yes.
A specialized server may be the ideal service for internet sites or e-commerce website that do have great deals of data transfer needed or have a large web traffic site. With all the aid of a devoted web server, the administration of the business becomes extremely simple and cost-efficient. Dedicated web server organizing protects against the trouble of downtime as much as some level as your on the internet application is not going to be disrupted because of any kind of abuse problem of any type of various other hosting individuals on the same server.
What is the cost of hosting an internet site in India?
The Web Hosting
A host is in fact shops your web data. domain name india Holding is typically an annual cost. At domainindia.org it's $9.49 (Rs.510) each year this strategy and also space is more than enough for the average consumer. our all web hosting plans is that you can quickly upgrade to an any kind of bundle if you ought to require it.Yes, you can set up customized software program in your Linux/ Java Dedicated Server. Nevertheless, please seek advice from our specialist System Admins to make sure that it is risk-free to install such a software in your devoted web server. 1 Gbps port speed organized in network backbone of 160 Gbps comes standard in all our Linux Dedicated Server arrangements.
Establishing an internal organizing option may take lots of months and even years.
All the devoted web servers are housed in special locations of our information facilities.
Additionally, if your business remains in India, a devoted web server in India will certainly help you enjoy the price benefit, many thanks to lowered costs.
Our low-cost committed web servers featured cPanel and also WHM to offer advanced administration of every feature and also setup. Open resource and security created, absolutely nothing can be much better than a Linux site. We offer Linux holding plans, as strong as Linux. Coming to be a web hosting Reseller can be a successful way to make quick earnings.
Taken care of Web servers give you your own Dedicated Web server with complete root accessibility and also the capacity to install any software application that you call for with the enhancement of complete web server assistance and also monitoring in addition to anti-virus and also malware scanning. Yes, you get root accessibility to WHM in addition to SSH of the web server in your Linux Dedicated Server Hosting as well as Java Dedicated Web Server Organizing. Centos with cPanel/ WHM comes requirement in Linux Dedicated Web server Organizing plans.
What are dedicated web servers made use of for?
A dedicated web server is an enterprise-grade physical server used to host the applications as well as solutions of a single holding client. Dedicated web servers are generally made use of to host high-traffic sites, internet applications, as well as for other organizing situations where performance is paramount.
A dedicated web server organizing is a trustworthy hosting framework where a physical web server is committed to offer the requirements of an individual client only. In contrast, a physical server is cut right into several virtual items in VPS (Online Personal Server) hosting; however, each of the digital instances act as a committed web server for a single customer, however actually they share a server with a few other customers. Our high bandwidth Dedicated web servers suit substantial quantity of website traffic, multimedia contents (video streaming, audio documents etc.), enormous quantity of information transfer, video game web servers, documents organizing, and various other web applications.
We can include some added hard disk for you when possible, Otherwise we can migrate your committed organizing within Indian data center. A lot of the top gamers in India gives online devoted host, as a result of lots of advantages offered for customers. Please refer why Digital server is much better than physical servers.
Our committed web server is especially developed for information back-up facilities, holding firms or business which require an entirely safeguarded atmosphere for their mission-critical data. A dedicated server or took care of web server is a server that a person can rent the whole server without sharing it with anybody. Our Dedicated web servers feature a dedicated IP as well as provides you with a blazing fast speed while using optimal safety and security as well as control without sustaining the cost of possessing an in-house server.
What is the cheapest method to organize a website? useful source
I've listed several of the least pricey ways to hold your start-up site, taking into account platform, business and also expense size:
Hostwinds. This VPS holding solution is among the least expensive host service providers you will certainly be able to find.
Bluehost.
FatCow.
A Small Orange.
1 & 1.
GreenGeeks.
Hostgator.
InMotion Hosting.
#dedicated server hosting in India#cheapest dedicated server hosting in India#low cost dedicated serv
0 notes
Text
10 Ways to avoid viruses & malwares

1: Install quality antivirus
Many computer users believe free antivirus applications, such as those included with an Internet service provider's bundled service offering, are sufficient to protect a computer from virus or spyware infection. However, such free anti-malware programs typically don't provide adequate protection from the ever-growing list of threats.
Instead, all Windows users should install professional, business-grade antivirus software on their PCs. Pro-grade antivirus programs update more frequently throughout the day (thereby providing timely protection against fast-emerging vulnerabilities), protect against a wider range of threats (such as rootkits), and enable additional protective features (such as custom scans).
2: Install real-time anti-spyware protection
Many computer users mistakenly believe that a single antivirus program with integrated spyware protection provides sufficient safeguards from adware and spyware. Others think free anti-spyware applications, combined with an antivirus utility, deliver capable protection from the skyrocketing number of spyware threats.
Unfortunately, that's just not the case. Most free anti-spyware programs do not provide real-time, or active, protection from adware, Trojan, and other spyware infections. While many free programs can detect spyware threats once they've infected a system, typically professional (or fully paid and licensed) anti-spyware programs are required to prevent infections and fully remove those infections already present.
3: Keep anti-malware applications current
Antivirus and anti-spyware programs require regular signature and database updates. Without these critical updates, anti-malware programs are unable to protect PCs from the latest threats.
In early 2009, antivirus provider AVG released statistics revealing that a lot of serious computer threats are secretive and fast-moving. Many of these infections are short-lived, but they're estimated to infect as many as 100,000 to 300,000 new Web sites a day.
Computer users must keep their antivirus and anti-spyware applications up to date. All Windows users must take measures to prevent license expiration, thereby ensuring that their anti-malware programs stay current and continue providing protection against the most recent threats. Those threats now spread with alarming speed, thanks to the popularity of such social media sites as Twitter, Facebook, and My Space.
4: Perform daily scans
Occasionally, virus and spyware threats escape a system's active protective engines and infect a system. The sheer number and volume of potential and new threats make it inevitable that particularly inventive infections will outsmart security software. In other cases, users may inadvertently instruct anti-malware software to allow a virus or spyware program to run.
Regardless of the infection source, enabling complete, daily scans of a system's entire hard drive adds another layer of protection. These daily scans can be invaluable in detecting, isolating, and removing infections that initially escape security software's attention.
5: Disable autorun
Many viruses work by attaching themselves to a drive and automatically installing themselves on any other media connected to the system. As a result, connecting any network drives, external hard disks, or even thumb drives to a system can result in the automatic propagation of such threats.
Computer users can disable the Windows autorun feature by following Microsoft's recommendations, which differ by operating system. Microsoft Knowledge Base articles 967715and 967940 are frequently referenced for this purpose.
6: Disable image previews in Outlook
Simply receiving an infected Outlook e-mail message, one in which graphics code is used to enable the virus' execution, can result in a virus infection. Prevent against automatic infection by disabling image previews in Outlook.
By default, newer versions of Microsoft Outlook do not automatically display images. But if you or another user has changed the default security settings, you can switch them back (using Outlook 2007) by going to Tools | Trust Center, highlighting the Automatic Download option, and selecting Don't Download Pictures Automatically In HTML E-Mail Messages Or RSS.
7: Don't click on email links or attachments
It's a mantra most every Windows user has heard repeatedly: Don't click on email links or attachments. Yet users frequently fail to heed the warning.
Whether distracted, trustful of friends or colleagues they know, or simply fooled by a crafty email message, many users forget to be wary of links and attachments included within email messages, regardless of the source. Simply clicking on an email link or attachment can, within minutes, corrupt Windows, infect other machines, and destroy critical data.
Users should never click on email attachments without at least first scanning them for viruses using a business-class anti-malware application. As for clicking on links, users should access Web sites by opening a browser and manually navigating to the sites in question.
8: Surf smart
Many business-class anti-malware applications include browser plug-ins that help protect against drive-by infections, phishing attacks (in which pages purport to serve one function when in fact they try to steal personal, financial, or other sensitive information), and similar exploits. Still others provide "link protection," in which Web links are checked against databases of known-bad pages.
Whenever possible, these preventive features should be deployed and enabled. Unless the plug-ins interfere with normal Web browsing, users should leave them enabled. The same is true for automatic pop-up blockers, such as are included in Internet Explorer 8, Google's toolbar, and other popular browser toolbars.
Regardless, users should never enter user account, personal, financial, or other sensitive information on any Web page at which they haven't manually arrived. They should instead open a Web browser, enter the address of the page they need to reach, and enter their information that way, instead of clicking on a hyperlink and assuming the link has directed them to the proper URL. Hyperlinks contained within an e-mail message often redirect users to fraudulent, fake, or unauthorized Web sites. By entering Web addresses manually, users can help ensure that they arrive at the actual page they intend.
But even manual entry isn't foolproof. Hence the justification for step 10: Deploy DNS protection. More on that in a moment.
9: Use a hardware-based firewall
Technology professionals and others argue the benefits of software- versus hardware-based firewalls. Often, users encounter trouble trying to share printers, access network resources, and perform other tasks when deploying third-party software-based firewalls. As a result, I've seen many cases where firewalls have simply been disabled altogether.
But a reliable firewall is indispensable, as it protects computers from a wide variety of exploits, malicious network traffic, viruses, worms, and other vulnerabilities. Unfortunately, by itself, the software-based firewall included with Windows isn't sufficient to protect systems from the myriad robotic attacks affecting all Internet-connected systems. For this reason, all PCs connected to the Internet should be secured behind a capable hardware-based firewall.
10: Deploy DNS protection
Internet access introduces a wide variety of security risks. Among the most disconcerting may be drive-by infections, in which users only need to visit a compromised Web page to infect their own PCs (and potentially begin infecting those of customers, colleagues, and other staff).
Another worry is Web sites that distribute infected programs, applications, and Trojan files. Still another threat exists in the form of poisoned DNS attacks, whereby a compromised DNS server directs you to an unauthorized Web server. These compromised DNS servers are typically your ISP's systems, which usually translate friendly URLs such as yahoo.com to numeric IP addresses like 69.147.114.224.
Users can protect themselves from all these threats by changing the way their computers process DNS services. While a computer professional may be required to implement the switch, OpenDNS offers free DNS services to protect users against common phishing, spyware, and other Web-based hazards.
0 notes
Text
How Has Enterprise Storage Changed Over The Years?
Everything around us changes, always evolving. Even us humans have changed a lot over the years. Some experts claim we descended from apes but others contradict it. This argument has been dragging on for years and the answer may likely continue to elude us. But when it comes to technology, recorded history has done its best to keep track of technological advancements that we can definitely check and counter-check events and how certain concepts came to be.
Among the most important aspects of technology is data storage. Data means a lot to all of us. From the data that allows us to access the web to the data that we share and keep, we spend a great deal of our time, effort and money in securing these data. While most of you have no idea what enterprise storage is all about, it is often used by large organizations in the storage and retrieval of data that they use. Large amounts of data and lots of users are all in a day’s work for these huge enterprise storage repositories, so it helps to know what to anticipate from them today and tomorrow.
True hybrid enterprise cloud storage systems promise the best of both on-premises infrastructure and public cloud. They offer the performance, security and governance of local storage necessary for many mission-critical business applications — not to mention the on-demand elastic scalability and utility economics of public clouds.
But finding true hybrid cloud tools to support critical, enterprise-class, database-driven applications can be difficult. This gaping hole in the market has left enterprise IT pros and business application owners stuck on legacy infrastructures.
However, there has been significant progress. Oracle Cloud Converged Storage, released last month, integrates storage services across its database, enterprise applications, enterprise storage infrastructure and public cloud. Practically, its latest on-premises Oracle ZFS storage arrays internally and organically extend into public Oracle Cloud storage (which is also made up of ZFS storage arrays) — no gateway integration or third-party software required.
(Via: http://searchoracle.techtarget.com/opinion/Enterprise-cloud-storage-boosted-by-Oracle-Cloud-Converged-Storage)
The cloud is fast rising in popularity because there is no longer the need for a physical object to store data for you. The huge servers of big companies provide the storage many people need that is not only convenient but affordable too.
Enterprises are loading up their data centers with hybrid flash storage systems in increasing numbers, according to a new survey from ActualTech Media commissioned by storage array maker Tegile Systems.
More than half (55 percent) of the 700 IT professionals polled for the study said they were using hybrid flash storage systems, which typically use a combination of solid-state drives and traditional hard disk drives to speed up data services, in their environments. Last year, 47 percent reported the same.
Meanwhile, all-disk storage systems are steadily losing their appeal. Adoption rates dipped from 41 percent in 2016 to 37 percent in the first quarter of 2016. All-flash environments remain relatively rare with a mere two-percent penetration rate.
(Via: http://www.enterprisestorageforum.com/storage-management/hybrid-storage-becomes-the-go-to-application-performance-booster.html)
Enterprises have more options when it comes to data storage now that technology has greatly improved. More importantly aside from their efficiency, they are more affordable now too. Even flash storage is being utilized by enterprises as a data storage option mainly because of its affordability.
With Huawei’s unique tools, the series can be configured in three easy steps, it takes up to only one minute for setup. The management system enables customers to manage devices from multiple vendors uniformly. At the same time, it can perform batch deployment, capacity forecasting, and performance analysis in a centralised manner.
“The advantages of the convergence features within the OceanStor 2000 V3 series have been widely proven by Huawei enterprise storage systems deployed in various industries,” says Jonas Arndt, senior cloud solution architect of the Huawei Global Solution Elite Team.
“Additionally, the Huawei OceanStor 2000 V3 series provide flexible scale-out and scale-up capabilities, enabling SMEs to embrace fast growing business. By simplifying configuration, reducing manual operations, and offering smart functions, Huawei’s new storage systems make upper-layer business deployment more flexible and O&M simpler. They are bound to be the best fit storage for SMEs,” he says.
(Via: https://it-online.co.za/2017/04/21/new-gen-enterprise-storage-for-smes/)
Simple, smart, efficient and collaborative data storage is all the rage now. Enterprises have no choice but to use more technology in their day-to-day business operation since almost everything has gone digital now. They have to adapt to these changes if they want to stay relevant in our growing technologically-obsessed world where people can’t get enough of their smart gadgets. The good thing about technology aside from becoming faster and efficient over the years but more cost-effective too. So, there is no reason for you to miss out on the benefits they offer because they are literally within your reach now. Whatever your business is, there sure is an enterprise data storage available for you.
For smaller enterprises that only have their personal computers to rely on for their daily computing needs, you may not yet be worried about most of these data storage issues because you only have your hard drive that does the work for you. But when it fails, boy it does really fail you. Tap on the expert assistance of http://www.harddriverecovery.org/seagate-data-recovery.html for help when it happens. Data recovery is likewise still possible for those RAID 10 users with the help of our skilled pros. This page: http://www.harddriverecovery.org/raidcenter/raid-10-data-recovery.html can help you understand what’s going on and what can be done to retrieve your data and save your business after all.
How Has Enterprise Storage Changed Over The Years? Read more on: http://www.harddriverecovery.org
From http://www.harddriverecovery.org/blog/how-has-enterprise-storage-changed-over-the-years/
from https://harddriverecovrygroup.wordpress.com/2017/06/02/how-has-enterprise-storage-changed-over-the-years/
0 notes