#Managed IT Services Palo Alto
Text
Refresh Your Space with Maid4You!
Transform your home with Maid4You's reliable cleaning services! Say goodbye to hidden costs and hello to honest pricing. Trust us for expert cleaning you can rely on, Offering Free Quotations
Phone: 408-889-6187
Website: cleaningmaid4you.com
We provide Cleaning services in California, Bay Area
Residential Cleaning
Commercial Cleaning
Window Cleaning
Carpet Cleaning
Gutter Cleaning
Salon Cleaning Services
Restaurant Cleaning Services
#Maid4You #CleaningServices
#bay area#business#california#cleaning#palo alto#san jose#home cleaning#cleaning tips#cleaningservices#cleaning service#carpet cleaning#house cleaning#window cleaning#gutter cleaning#junk removal#san francisco#cleaning house services#commercial cleaning#property#realestate#property management#property managers
1 note
·
View note
Text
With the exceptions of North Korea and Cuba, the communist world has merged onto the capitalist highway in a couple different ways during the twenty-first century. As you’ve read, free-trade imperialism and its cheap agricultural imports pushed farmers into the cities and into factory work, lowering the global price of manufacturing labor and glutting the world market with stuff. Forward-thinking states such as China and Vietnam invested in high-value-added production capacity and managed labor organizing, luring links from the global electronics supply chain and jump-starting capital investment. Combined with capital’s hesitancy to invest in North Atlantic production facilities, as well as a disinclination toward state-led investment in the region, Asian top-down planning erased much of the West’s technological edge. If two workers can do a single job, and one worker costs less, both in wages and state support, why pick the expensive one? Foxconn’s 2017 plan to build a U.S. taxpayer–subsidized $10 billion flat-panel display factory in Wisconsin was trumpeted by the president, but it was a fiasco that produced zero screens. The future cost of labor looks to be capped somewhere below the wage levels many people have enjoyed, and not just in the West.
The left-wing economist Joan Robinson used to tell a joke about poverty and investment, something to the effect of: The only thing worse than being exploited by capitalists is not being exploited by capitalists. It’s a cruel truism about the unipolar world, but shouldn’t second place count for something? When the Soviet project came to an end, in the early 1990s, the country had completed world history’s biggest, fastest modernization project, and that didn’t just disappear. Recall that Cisco was hyped to announce its buyout of the Evil Empire’s supercomputer team. Why wasn’t capitalist Russia able to, well, capitalize? You’re already familiar with one of the reasons: The United States absorbed a lot of human capital originally financed by the Soviet people. American immigration policy was based on draining technical talent in particular from the Second World. Sergey Brin is the best-known person in the Moscow-to-Palo-Alto pipeline, but he’s not the only one.
Look at the economic composition of China and Russia in the wake of Soviet dissolution: Both were headed toward capitalist social relations, but they took two different routes. The Russian transition happened rapidly. The state sold off public assets right away, and the natural monopolies such as telecommunications and energy were divided among a small number of skilled and connected businessmen, a category of guys lacking in a country that frowned on such characters but that grew in Gorbachev’s liberalizing perestroika era. Within five years, the country sold off an incredible 35 percent of its national wealth. Russia’s richest ended the century with a full counterrevolutionary reversal of their fortunes, propelling their income share above what it was before the Bolsheviks took over. To accomplish this, the country’s new capitalists fleeced the most vulnerable half of their society. “Over the 1989–2016 period, the top 1 percent captured more than two-thirds of the total growth in Russia,” found an international group of scholars, “while the bottom 50 percent actually saw a decline in its income.” Increases in energy prices encouraged the growth of an extractionist petro-centered economy. Blood-covered, teary, and writhing, infant Russian capital crowded into the gas and oil sectors. The small circle of oligarchs privatized unemployed KGB-trained killers to run “security,” and gangsters dominated politics at the local and national levels. They installed a not particularly well-known functionary—a former head of the new intelligence service FSB who also worked on the privatization of government assets—as president in a surprise move on the first day of the year 2000. He became the gangster in chief.
Vladimir Putin’s first term coincided with the energy boom, and billionaires gobbled up a ludicrous share of growth. If any individual oligarch got too big for his britches, Putin was not beyond imposing serious consequences. He reinserted the state into the natural monopolies, this time in collaboration with loyal capitalists, and his stranglehold on power remains tight for now, despite the outstandingly uneven distribution of growth. Between 1980 and 2015, the Russian top 1 percent grew its income an impressive 6.2 percent per year, but the top .001 percent has maintained a growth rate of 17 percent over the same period. To invest these profits, the Russian billionaires parked their money in real estate, bidding up housing prices, and stashed a large amount of their wealth offshore. Reinvestment in Russian production was not a priority—why go through the hassle when there were easier ways to keep getting richer?
While Russia grew billionaires instead of output, China saw a path to have both. As in the case of Terry Gou, the Chinese Communist Party tempered its transition by incorporating steadily increasing amounts of foreign direct investment through Hong Kong and Taiwan, picking partners and expanding outward from the special economic zones. State support for education and infrastructure combined with low wages to make the mainland too attractive to resist. (Russia’s population is stagnant, while China’s has grown quickly.) China’s entry into the World Trade Organization, in 2001, gave investors more confidence. Meanwhile, strong capital controls kept the country out of the offshore trap, and state development priorities took precedence over extraction and get-rich-quick schemes. Chinese private wealth was rechanneled into domestic financial assets—equity and bonds or other loan instruments—at a much higher rate than it was in Russia. The result has been a sustained high level of annual output growth compared to the rest of the world, the type that involves putting up an iPhone City in a matter of months. As it has everywhere else, that growth has been skewed: only an average of 4.5 percent for the bottom half of earners in the 1978–2015 period compared to more than 10 percent for the top .001 percent. But this ratio of just over 2–1 is incomparable to Russia’s 17–.5 ration during the same period.
Since the beginning of the twenty-first century, certain trends have been more or less unavoidable. The rich have gotten richer relative to the poor and working class—in Russia, in China, in the United States, and pretty much anywhere else you want to look. Capital has piled into property markets, driving up the cost of housing everywhere people want to live, especially in higher-wage cities and especially in the world’s financial centers. Capitalist and communist countries alike have disgorged public assets into private pockets. But by maintaining a level of control over the process and slowing its tendencies, the People’s Republic of China has built a massive and expanding postindustrial manufacturing base.
It’s important to understand both of these patterns as part of the same global system rather than as two opposed regimes. One might imagine, based on what I’ve written so far, that the Chinese model is useful, albeit perhaps threatening, in the long term for American tech companies while the Russian model is irrelevant. Some commentators have phrased this as the dilemma of middle-wage countries on the global market: Wages in China are going to be higher than wages in Russia because wages in Russia used to be higher than wages in China. But Russia’s counterrevolutionary hyper-bifurcation has been useful for Silicon Valley as well; they are two sides of the same coin. Think about it this way: If you’re a Russian billionaire in the first decades of the twenty-first century looking to invest a bunch of money you pulled out of the ground, where’s the best place you could put it? The answer is Palo Alto.
Malcolm Harris, Palo Alto
53 notes
·
View notes
Text

NASA’s Psyche Mission on Track for Liftoff Next Month
Bound for a metal-rich asteroid of the same name, the Psyche mission is targeting Oct. 5 to launch from NASA’s Kennedy Space Center in Florida.
The spacecraft’s solar arrays are folded like an envelope into their stowed position. Xenon gas – fuel for the journey to the asteroid belt – is loaded. All four thrusters have passed their final tests. Engineers have confirmed the massive high-gain antenna is set to transmit data. The software is tested and ready. The science instruments – a multispectral imager, magnetometer, and gamma-ray and neutron spectrometer – that will investigate the asteroid Psyche are poised for action.
NASA’s Psyche spacecraft has less than 30 days to go before the opening of its launch period, which runs from Thursday, Oct. 5 through Wednesday, Oct. 25. What the mission learns from the metal-rich asteroid may tell us more about how planets form.
“These missions take so many people and so much meticulous, rigorous, personally driven work,” said Lindy Elkins-Tanton, principal investigator for Psyche at Arizona State University. “I am ready to be ecstatic. We all are, but we are not ecstatic yet. Let’s launch and establish communications – then we can scream, jump, and hug each other!”
Within two weeks, technicians will begin encapsulating the spacecraft in its payload fairing – the cone at the top of the rocket – and the spacecraft will move to SpaceX facilities at NASA’s Kennedy Space Center in Florida. Psyche is set to launch atop a SpaceX Falcon Heavy from the center’s Launch Complex 39A at 10:38 a.m. EDT on Oct. 5.
“It’s getting increasingly real,” said Henry Stone, Psyche’s project manager at NASA’s Jet Propulsion Laboratory in Southern California. “We are counting the days. The team is more than ready to send this spacecraft off on its journey, and it’s very exciting.”
After escaping Earth’s gravity, Psyche will use solar electric propulsion to accomplish its six-year journey to the asteroid. The efficient propulsion system works by accelerating and expelling charged atoms, or ions, of the neutral gas xenon – creating a thrust that gently propels the spacecraft with a force akin to what you’d feel holding a single AA battery in your hand. Technicians recently loaded 2,392 pounds (1,085 kilograms) of xenon onto the spacecraft over the course of about two weeks.
Measuring roughly 173 miles (279 kilometers) at its widest point, the asteroid Psyche presents a unique opportunity to explore a metal-rich body that may be part of a core of a planetesimal, the building block of an early planet. Once the spacecraft reaches Psyche in the main asteroid belt between Mars and Jupiter, it will spend about 26 months orbiting the asteroid, gathering images and other data that will tell scientists more about its history and what it is made of.
More About the Mission
Arizona State University leads the Psyche mission. A division of Caltech in Pasadena, JPL is responsible for the mission’s overall management, system engineering, integration and test, and mission operations. Maxar Technologies in Palo Alto, California, provided the high-power solar electric propulsion spacecraft chassis.
A technology demonstration called Deep Space Optical Communications (DSOC) will fly on Psyche in order to test high-data-rate laser communications that could be used by future NASA missions. JPL manages DSOC for the Technology Demonstration Missions program within NASA’s Space Technology Mission Directorate and the Space Communications and Navigation program within the Space Operations Mission Directorate.
Psyche is the 14th mission selected as part of NASA’s Discovery Program, managed by the agency’s Marshall Space Flight Center in Huntsville, Alabama. NASA’s Launch Services Program, based at Kennedy, is managing the launch service.
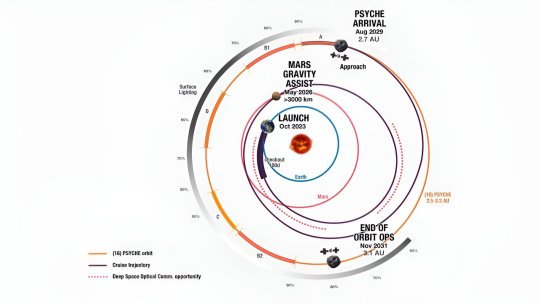
TOP IMAGE....NASA’s Psyche spacecraft will take a spiral path to the asteroid Psyche, as depicted in this graphic, which is labeled with key milestones of the prime mission. The test periods for NASA’s Deep Space Optical Communications (DSOC) technology demonstration are indicated with red dots. Credit: NASA/JPL-Caltech
LOWER IMAGE....NASA’s Psyche spacecraft will take a spiral path to the asteroid Psyche, as depicted in this graphic, which is labeled with key milestones of the prime mission. The test periods for NASA’s Deep Space Optical Communications (DSOC) technology demonstration are indicated with red dots. Credit: NASA/JPL-Caltech
2 notes
·
View notes
Text
Financial Services Cybersecurity Systems And Services Market Forecast 2024-2033
Overview and Scope
Financial services cybersecurity systems and services are the technology, methods, and strategies used by financial institutions to protect their digital assets, sensitive data, and operations against cyber threats. These service and technology are essential for protecting sensitive financial information, ensuring regulatory compliance, and maintaining customer trust.

The financial services cybersecurity systems and services market size is expected to see rapid growth in the next few years. It will grow to $41.49 billion in 2028 at a compound annual growth rate (CAGR) of 13.0%. The growth in the forecast period can be attributed to rising in ransomware attacks, rising in demand for threat intelligence, growing emphasis on cyber resilience, increasing regulatory scrutiny, continued expansion of digital banking. Major trends in the forecast period include the adoption of AI-driven technologies, blockchain technology, automation, cybersecurity training, integration of deception technologies, multi-factor authentication.
Segmentation & Regional Insights
The financial services cybersecurity systems and services market covered in this report is segmented –
1)By Product: Endpoint Security, Identity And Access Management, Mobile Security, Security Information And Event Management, Content Security, Datacenter Security
2)By Deployment: Cloud, On-Premise
3)By Organization Size: Small And Medium Enterprises, Large Enterprises
4)By Application: Banking And Insurance Institution, Stock And Funds Institution, Government, Other Applications
North America was the largest region in the financial services cybersecurity systems and services market in 2023. Asia-Pacific is expected to be the fastest-growing region in the forecast period. The regions covered in the financial services cybersecurity systems and services market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa.
Major Driver Impacting Market Growth
The rising instances of cyberattacks are expected to propel the growth of the financial services cybersecurity systems and services market going forward. A cyber-attack is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization. The rising instances of cyberattacks are due to several factors, such as increasing digitization, rising connectivity, and a lack of cybersecurity awareness. Financial services cybersecurity systems and services helps in safeguarding the integrity, confidentiality, and availability of critical financial infrastructure and customer information amidst the growing sophistication and frequency of cyberattacks . For instance, in February 2023, according to the Australian Cyber Security Centre, an Australia-based government agency for cyber security, the number of cyberattacks received in 2022 was 76,000, up 13% from the previous year. Therefore, the rising instances of cyberattacks are driving the growth of the financial services cybersecurity systems and services market.
Key Industry Players
Major companies operating in the financial services cybersecurity systems and services market are International Business Machines Corporation, Cisco Systems Inc., Ernst & Young Global Limited, Broadcom Inc., Palo Alto Networks Inc., Fortinet Inc., Check Point Software Technologies Ltd., Trend Micro Incorporated, CrowdStrike Holdings Inc., Proofpoint Inc., FireEye Inc., Rapid7 Inc., Forcepoint LLC, CyberArk Software Ltd., Varonis Systems Inc., SentinelOne Inc., Trustwave Holdings Inc., Cylance Inc., LogRhythm Inc., SecurityScorecard Inc., Sophos Group plc, BitSight Inc.
The financial services cybersecurity systems and services market report table of contents includes:
1. Executive Summary
2. Financial Services Cybersecurity Systems And Services Market Characteristics
3. Financial Services Cybersecurity Systems And Services Market Trends And Strategies
4. Financial Services Cybersecurity Systems And Services Market — Macro Economic Scenario
5. Global Financial Services Cybersecurity Systems And Services Market Size and Growth
.
.
.
31. Financial Services Cybersecurity Systems And Services Market Other Major And Innovative Companies
32. Global Financial Services Cybersecurity Systems And Services Market Competitive Benchmarking
33. Global Financial Services Cybersecurity Systems And Services Market Competitive Dashboard
34. Key Mergers And Acquisitions In The Financial Services Cybersecurity Systems And Services Market
35. Financial Services Cybersecurity Systems And Services Market Future Outlook and Potential Analysis
Explore the trending research reports from TBRC:
Contact Us:
The Business Research Company
Europe: +44 207 1930 708
Asia: +91 88972 63534
Americas: +1 315 623 0293
0 notes
Text
Diabetes care services | Right at Home
Looking for Customized Diabetic in Home care for senior in San Mateo and Palo Alto, CA? Right at Home helps seniors age safety at home with personalized Diabetic Care. Contact Us Now.

0 notes
Text
Security Orchestration Automation and Response (SOAR) Market to Witness Steady Growth with a CAGR of 10.9% by 2032
It is anticipated that the global Security Orchestration Automation and Response (SOAR) market would reach US$ 3.8 billion by 2032, a stunning 10.9% compound annual growth rate, from an estimated value of US$ 1.3 billion in 2022.
Over the course of the anticipated year, the SOAR market is anticipated to have a fantastic expansion because to the growth of technologies like blockchain, cloud, and IoT. In order to influence future developments in the SOAR sector, several companies place a high priority on security and safety.
It is hard to rule out the chance, nevertheless, that SOAR’s shortage of security personnel may restrict the market for the duration of the predicted period.
Future Market Insights has entailed these facts with insights in its latest market study entitled ‘Security Orchestration Automation and Response (SOAR) market’. It has its team of analysts and consultants to deploy a bottom-up approach in its primary, secondary, and tertiary modes of research.
Get a Sample of this Report:
https://www.futuremarketinsights.com/reports/sample/rep-gb-14733
“With large volumes of IT application and cloud data being analysed for gauging sophisticated responses to the threats detected, the global SOAR market is bound to grow on an explicable note in the forecast period”, says an analyst from Future Market Insights.
Key Takeaways from SOAR market
North America holds the largest market share. This could be reasoned with wholesome investment done by the US against cyber-attacks.
Europe holds the second-largest market share with Germany and the UK leading from the front. This could be attributed to rules imposed by the governments in this regard.
The Asia-Pacific is expected to grow at the quickest rate in the SOAR market with China ruling the roost.
Competitive Analysis
XM Cyber, in May 2021, did announce integration with Palo Alto Network’s Cortex XSOAR security orchestration automation and response technology.
Securonix, in May 2021, did announce that its next-gen SIEM platform bagged the Best SIEM Solution award. The company was thus adjudged as a Trust Award Winner for cloud-first SIEM multi-cloud and hybrid businesses.
Bugcrowd, in May 2022, entered into collaboration with IBM for bringing SOAR Space and IBM Resilient Integration on the same platform. Security teams make use of SOAR called IBM Resilient.
Palo Alto Networks, in May 2022, did announce that it entered into collaboration with Cohesity with the objective of integrating SOAR platform with the latter’s AI data management platform for lowering customers’ risk to ransomware.
ThreatConnect, in September 2020, completed acquisition of Nehemiah Security. The basic purpose is that of adding Cyber Risk Quantification to the former’s SOAR platform that exists.
Splunk, in March 2022, did join hands with Ridge Security for shortening reaction times.
Ask an Analyst:
https://www.futuremarketinsights.com/ask-the-analyst/rep-gb-14733
What does the Report state?
The research study is based on component (solution and services), organization size (small & medium enterprises, large enterprises), deployment mode (cloud and on-premises), application (threat intelligence, network forensics, incident management, compliance management, workflow management, and likewise), and by vertical (BFSI, government, energy & utilities, healthcare, retail, IT & telecom, and likewise).
With product management, supply chain, sales, marketing, and various other activities getting digitized, the global SOAR market is expected to grow on an arduous note in the forecast period.
Key Segments
By Component:
Solution
Services
By Organisation Size:
Small & Medium Enterprises
Large Enterprises
By Deployment Mode
Cloud
On-Premises
By Application:
Threat Intelligence
Network Forensics
Incident Management
Compliance Management
Workflow Management
Others
By Vertical:
BFSI
Government
Energy & Utilities
Healthcare
Retail
IT & Telecom
Others
By Region:
North America
Latin America
Europe
Asia Pacific
Middle East and Africa (MEA)
0 notes
Text
Palo Alto Networks and IBM announce partnership

Palo Alto Networks and IBM announced a major partnership this week, in which they will jointly offer cybersecurity solutions and IBM will provide consulting services for Palo Alto’s platforms.
Key elements of this partnership include IBM expanding its internal use of Palo Alto Networks security platforms and designating Palo Alto as its preferred partner for network, cloud, and security operations center (SOC) services.
Additionally, IBM will collaborate with Palo Alto on security operations, DevSecOps, and threat management. IBM plans to train over 1,000 security consultants on the migration, deployment, and adoption of Palo Alto products.
Moreover, IBM Consulting will become a preferred Managed Security Service Provider (MSSP) for Palo Alto customers, and the two companies will establish a joint SOC and a cyber range.
"IBM's experts, with their global, regional, and local delivery capabilities, will leverage Watsonx, IT automation, and threat intelligence to bolster advisory efforts and promote the growth and adoption of Palo Alto Networks security platforms," the companies announced.
Palo Alto Networks has agreed to acquire IBM's QRadar SaaS assets, which IBM initially obtained in 2011 through its acquisition of Q1 Labs. Following the completion of the QRadar assets acquisition, the companies will assist QRadar customers in transitioning to Palo Alto's recently launched Cortex XSIAM SOC platform.
The financial terms of the transaction have not been disclosed, but it is expected to close by the end of September.
Read the full article
0 notes
Text

Huge Solar Arrays Permanently Installed on NASA’s Psyche Spacecraft
The Psyche mission is speeding toward its Oct. 5 launch date, preparing for the last of its launch-preparation milestones.
Robotically unfurling in a clean room near NASA’s Kennedy Space Center in Florida, the Psyche spacecraft’s jumbo solar arrays were tested and permanently installed on the orbiter in preparation for its 2.5 billion-mile (4 billion-kilometer) journey to study a metal-rich asteroid. The launch period opens Oct. 5.
After passing the deployment test, the twin wings were re-stowed and will remain tucked away on the sides of the orbiter until the spacecraft leaves Earth. Psyche is scheduled to reach its destination – a mysterious asteroid of the same name, in the main asteroid belt between Mars and Jupiter – in July 2029. Then the spacecraft will orbit the asteroid from various altitudes for 26 months to gather images and other data.
Scientists hope that learning about the asteroid, which may be part of a core of a planetesimal (a building block of a planet), will tell us more about planetary cores and Earth’s own formation.
youtube
This final installation of the solar arrays took place at Astrotech Space Operations, near Kennedy. The arrays were deployed during testing last year at NASA’s Jet Propulsion Laboratory in Southern California. At 800 square feet (75 square meters), the five-panel, cross-shaped solar arrays are the largest ever deployed at JPL. With the arrays unfurled in flight, the spacecraft will be about the size of a singles tennis court.
Although they will produce more than 20 kilowatts of power when the spacecraft is near Earth, the solar arrays are primarily designed to work in the low light of deep space. The asteroid Psyche is so far from the Sun that even these massive arrays will generate just over 2 kilowatts of power at that distance.
That’s only a little more power than a hair dryer uses but is ample energy to meet Psyche’s electrical needs, including running science instruments, telecommunications, equipment that controls the orbiter’s temperature, and the spacecraft’s superefficient solar electric propulsion engines. The system’s thrusters use electromagnetic fields to accelerate and push out charged atoms, or ions, of the neutral gas xenon. The expelled ions create the thrust that pushes Psyche through space and emit a blue glow.
This thrust is so gentle, it exerts about the same amount of pressure you’d feel holding the weight of one AA battery in your hand. But it’s enough to accelerate Psyche through deep space. With no atmospheric drag to hold it back, the spacecraft will accelerate to speeds of up to 124,000 mph (200,000 kph) relative to Earth during its interplanetary journey to the asteroid belt.
In mid-August, a crew is scheduled to begin loading all 2,392 pounds (1,085 kilograms) of xenon onto the spacecraft over the course of a couple weeks.
A SpaceX Falcon Heavy is targeted to launch Psyche from Launch Complex 39A at Kennedy Space Center no earlier than 10:38 a.m. EDT (7:38 a.m. PDT) on Oct. 5, with additional opportunities scheduled through Oct. 25.
More About the Mission
Arizona State University leads the Psyche mission. A division of Caltech in Pasadena, JPL is responsible for the mission’s overall management, system engineering, integration and test, and mission operations. Maxar Technologies in Palo Alto, California, provided the high-power solar electric propulsion spacecraft chassis.
JPL also is providing a technology demonstration instrument called Deep Space Optical Communications that will fly on Psyche in order to test high-data-rate laser communications that could be used by future NASA missions.
Psyche is the 14th mission selected as part of NASA’s Discovery Program, managed by the agency’s Marshall Space Flight Center in Huntsville, Alabama. NASA’s Launch Services Program, based at the Kennedy Space Center, is managing the launch service.
3 notes
·
View notes
Text
Thermador Repair Fix
As the manager of Thermador Repair Fix, I am passionately committed to ensuring our clients in Palo Alto, CA, experience unparalleled customer satisfaction and the highest standards of service. Our local company takes pride in specializing in the repair and maintenance of Thermador appliances, understanding the sophistication and importance of these high-end appliances in your home. Our expertise spans across the entire Thermador product line, including cooktops, ovens, ranges, refrigerators, and dishwashers. We recognize the essential role these appliances play in your daily routines and culinary adventures, which is why we are dedicated to providing prompt, efficient, and effective on-site repair services tailored to meet your specific needs.
1 note
·
View note
Text
what type of vpn is globalprotect
what type of vpn is globalprotect
GlobalProtect VPN overview
GlobalProtect VPN is a robust virtual private network (VPN) solution designed to provide secure and seamless access to corporate networks and resources from anywhere in the world. Developed by Palo Alto Networks, GlobalProtect offers advanced security features to safeguard sensitive data and ensure confidentiality.
One of the key features of GlobalProtect VPN is its ability to establish secure connections over any network, including public Wi-Fi, ensuring that data remains encrypted and protected from unauthorized access. This is especially important for remote workers or employees traveling abroad who need to access corporate resources securely.
GlobalProtect employs a multi-layered approach to security, incorporating features such as strong encryption, multi-factor authentication, and threat prevention capabilities. This helps to mitigate the risk of data breaches and cyber attacks, providing organizations with peace of mind knowing that their network remains secure.
Another advantage of GlobalProtect VPN is its ease of use and flexibility. With support for a wide range of devices and operating systems, users can connect to the VPN seamlessly from their desktops, laptops, smartphones, and tablets. Additionally, GlobalProtect offers a user-friendly interface and intuitive controls, making it easy for both IT administrators and end-users to manage and configure VPN settings.
Furthermore, GlobalProtect provides granular access controls, allowing organizations to define policies based on user roles, device types, and locations. This ensures that only authorized users can access specific resources, helping to prevent unauthorized access and data leakage.
In summary, GlobalProtect VPN offers a comprehensive solution for securing remote access to corporate networks. With its advanced security features, ease of use, and flexibility, it is an ideal choice for organizations looking to protect their data and maintain compliance with regulatory requirements.
Features of GlobalProtect VPN
GlobalProtect VPN is a powerful tool that offers a wide range of features to ensure a secure and private online experience for users. One of the key features of GlobalProtect VPN is its ability to encrypt internet traffic, making it nearly impossible for hackers or third parties to intercept sensitive information such as passwords, financial data, or personal messages.
Another important feature of GlobalProtect VPN is its ability to mask a user's IP address, allowing them to browse the internet anonymously. This not only helps protect user privacy but also enables access to geo-restricted content by making it appear as though the user is browsing from a different location.
GlobalProtect VPN also offers advanced security features such as malware protection, DNS leak prevention, and kill switch functionality. These features help ensure that users are protected from online threats and that their data remains secure at all times.
Furthermore, GlobalProtect VPN supports multiple devices and platforms, including Windows, Mac, iOS, and Android, allowing users to secure their internet connection on all their devices with a single subscription.
In conclusion, GlobalProtect VPN is a comprehensive solution for anyone looking to enhance their online security and privacy. With its robust encryption, anonymous browsing capabilities, advanced security features, and multi-platform support, GlobalProtect VPN is a reliable choice for securing internet connections and ensuring peace of mind while browsing the web.
GlobalProtect vs other VPN types
GlobalProtect is a popular VPN solution that offers secure remote access to companies and individuals. When comparing GlobalProtect to other types of VPN services, there are several key differences that set it apart.
One major advantage of GlobalProtect is its focus on enterprise-level security. Unlike some other VPN services that may prioritize low cost or ease of use, GlobalProtect offers strong encryption protocols and advanced security features to protect sensitive data and ensure privacy. This makes it a preferred choice for businesses and organizations that need a high level of security for their remote connections.
Another distinguishing factor of GlobalProtect is its scalability and flexibility. With support for a wide range of operating systems and devices, GlobalProtect can be easily integrated into existing IT infrastructure and scaled up or down to meet changing needs. This makes it a versatile option for companies of all sizes looking to implement secure remote access solutions.
In terms of performance, GlobalProtect is known for its reliability and speed. By leveraging a global network of servers, GlobalProtect can provide fast and stable connections for users located anywhere in the world. This can be especially beneficial for businesses that have employees working remotely or traveling frequently.
Overall, while GlobalProtect may come at a higher cost compared to some other VPN services, its robust security features, scalability, and performance make it a strong contender for those in need of a secure and reliable VPN solution.
GlobalProtect for remote access
GlobalProtect is a robust solution that provides secure and seamless remote access to corporate networks for employees working from various locations. With the increase in remote work arrangements globally, the need for secure access to company resources has never been more critical. GlobalProtect offers a reliable and encrypted connection, ensuring that sensitive data remains protected and confidential.
One of the key benefits of using GlobalProtect for remote access is its ability to authenticate users and devices before granting access to the network. This helps prevent unauthorized access and potential data breaches, enhancing the overall security of the network. Additionally, GlobalProtect's advanced threat prevention features help identify and block malicious threats in real-time, further safeguarding the network from cyber attacks.
Moreover, GlobalProtect offers a user-friendly interface, making it easy for employees to connect to the corporate network securely. Whether employees are working from home, a coffee shop, or a co-working space, GlobalProtect ensures that they can access company resources without compromising security. This flexibility and ease of use contribute to increased productivity and efficiency for remote workers.
In conclusion, GlobalProtect is a valuable tool for organizations looking to provide secure remote access to their employees. By leveraging its advanced security features, ease of use, and reliability, businesses can ensure that their networks remain protected while enabling employees to work from anywhere in the world.
GlobalProtect security benefits
Title: Enhancing Cybersecurity with GlobalProtect: A Comprehensive Overview of its Benefits
In today's rapidly evolving digital landscape, ensuring robust cybersecurity measures is paramount for organizations of all sizes. With cyber threats becoming increasingly sophisticated, businesses are constantly seeking innovative solutions to safeguard their sensitive data and networks. One such solution that has gained significant traction is GlobalProtect.
GlobalProtect, developed by Palo Alto Networks, is a comprehensive cybersecurity platform designed to provide advanced protection against a wide range of cyber threats. By leveraging cutting-edge technologies and innovative features, GlobalProtect offers several key benefits to organizations:
Secure Remote Access: GlobalProtect enables secure remote access to corporate networks from anywhere in the world. This feature is particularly crucial in today's remote work environment, allowing employees to connect securely to corporate resources without compromising data integrity or network security.
Threat Prevention: GlobalProtect incorporates powerful threat prevention capabilities, including next-generation firewall, intrusion prevention, and advanced malware protection. By continuously monitoring network traffic and proactively identifying potential threats, GlobalProtect helps organizations mitigate risks and prevent cyber attacks before they can cause harm.
Granular Policy Control: With GlobalProtect, organizations can define granular security policies based on user identity, device type, location, and other contextual factors. This level of policy control ensures that only authorized users with compliant devices can access sensitive resources, minimizing the risk of unauthorized access and data breaches.
Integrated Security Ecosystem: GlobalProtect seamlessly integrates with other Palo Alto Networks security products, creating a cohesive security ecosystem that offers enhanced visibility, coordination, and response capabilities. This integrated approach enables organizations to detect and respond to security incidents more effectively, reducing the impact of cyber attacks.
In conclusion, GlobalProtect offers a comprehensive suite of security benefits that are essential for protecting modern digital environments against evolving cyber threats. By adopting GlobalProtect, organizations can enhance their cybersecurity posture, mitigate risks, and safeguard their critical assets with confidence.
0 notes
Text
does palo alto support policy based vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does palo alto support policy based vpn
Palo Alto VPN configurations
Palo Alto Networks is a leading provider of cybersecurity solutions, offering a range of products and services to help organizations protect their networks from cyber threats. One of the key offerings from Palo Alto Networks is its Virtual Private Network (VPN) technology, which allows users to securely connect to their organization's network from anywhere in the world.
Configuring a Palo Alto VPN is a critical step in ensuring that the connection is secure and reliable. One of the first steps in configuring a Palo Alto VPN is setting up the necessary policies and rules to govern the traffic flow between the VPN users and the organization's network. This includes defining which users are allowed to connect to the VPN, what resources they can access, and what level of encryption is required for the connection.
Another important aspect of configuring a Palo Alto VPN is setting up authentication mechanisms to verify the identity of users before allowing them to connect to the network. This can include using usernames and passwords, two-factor authentication, or integrating with existing authentication systems such as Active Directory or LDAP.
In addition to policies and authentication, configuring the encryption settings of the VPN is crucial to ensuring that data transmitted over the connection is securely encrypted and protected from eavesdropping or tampering. Palo Alto Networks offers a range of encryption options, including different algorithms and key lengths, to meet the security requirements of different organizations.
Overall, configuring a Palo Alto VPN involves a combination of setting up policies, authentication mechanisms, and encryption settings to ensure a secure and reliable connection between users and the organization's network. By following best practices and guidelines provided by Palo Alto Networks, organizations can create a robust VPN configuration that meets their security needs.
Policy-based VPN setup Palo Alto
In a policy-based VPN setup using Palo Alto Networks' firewall, administrators can create granular policies to control access between different networks securely. This type of VPN setup allows for more flexibility and control over traffic flow based on specific criteria defined in the policies.
To configure a policy-based VPN on Palo Alto firewall, administrators need to define security policies that determine which traffic will be encrypted and sent over the VPN tunnel. These policies can be based on various parameters such as source and destination IP addresses, applications, services, and users.
One of the key advantages of using policy-based VPNs is the ability to apply different security policies to different types of traffic. This allows organizations to enforce stricter security measures for sensitive data while allowing less critical traffic to flow through a less secure path.
Additionally, policy-based VPNs are scalable and can accommodate the increasing demands of a growing network. By creating specific policies for different types of traffic, administrators can ensure optimal performance and security for all network communication.
Overall, setting up a policy-based VPN on Palo Alto Networks' firewall provides organizations with a powerful tool to protect their network resources and secure communication between different network segments. By implementing granular security policies, administrators can effectively manage and control traffic flow while maintaining a high level of security across their network infrastructure.
Palo Alto VPN tunnel policies
Title: Understanding Palo Alto VPN Tunnel Policies: Ensuring Secure Connectivity
In the realm of network security, Palo Alto Networks stands out as a leading provider of robust solutions, including VPN (Virtual Private Network) technology. VPNs are essential for establishing secure connections over the internet, especially for remote workers accessing corporate resources. Within Palo Alto's VPN framework, tunnel policies play a crucial role in governing how traffic is encrypted and transmitted between network endpoints.
Tunnel policies in Palo Alto VPNs define the parameters for establishing and maintaining secure communication channels between network devices. These policies outline the encryption algorithms, authentication methods, and other security measures used to safeguard data in transit. By configuring tunnel policies, organizations can ensure that sensitive information remains protected from unauthorized access and interception.
One key aspect of Palo Alto VPN tunnel policies is the ability to create granular rules based on specific criteria. Administrators can define policies based on source and destination addresses, application types, user identities, and other factors, allowing for fine-tuned control over network traffic. This granularity enables organizations to enforce security policies tailored to their unique requirements and compliance standards.
Furthermore, Palo Alto VPN tunnel policies support the implementation of advanced security features such as threat prevention and intrusion detection. By integrating these capabilities into VPN traffic flows, organizations can detect and mitigate potential threats in real-time, enhancing overall network security posture.
In summary, Palo Alto VPN tunnel policies are instrumental in establishing secure and reliable communication channels for remote access and site-to-site connectivity. By configuring and enforcing these policies effectively, organizations can mitigate security risks and ensure the confidentiality, integrity, and availability of their data across the network.
Implementing VPN policies on Palo Alto
Implementing VPN policies on Palo Alto firewalls is a crucial step towards securing network communications and ensuring data privacy. A Virtual Private Network (VPN) establishes an encrypted connection between a device and a network, providing a secure tunnel for transferring sensitive information over the internet. Palo Alto Networks offers advanced firewall solutions with robust VPN capabilities, allowing organizations to enforce strict access controls and encryption standards for remote connections.
To implement VPN policies on Palo Alto firewalls, administrators can utilize the user-friendly interface of the PAN-OS operating system. By creating security rules and profiles, administrators can define parameters such as allowed applications, IP addresses, and encryption protocols for VPN traffic. Palo Alto firewalls support a wide range of VPN technologies, including SSL VPN, IPSec VPN, and GlobalProtect, catering to diverse connectivity requirements.
Furthermore, Palo Alto firewalls provide granular visibility and threat prevention features for VPN traffic. Through integrated threat intelligence and behavior-based analytics, organizations can detect and block malicious activities within the VPN tunnel. By implementing VPN policies on Palo Alto firewalls, businesses can enhance network security, mitigate risks of data breaches, and ensure compliance with privacy regulations.
In conclusion, Palo Alto Networks offers a comprehensive set of features for implementing VPN policies on its firewalls, enabling organizations to establish secure remote connections with ease. By leveraging Palo Alto's advanced security capabilities, businesses can safeguard their sensitive data and maintain a secure communication environment in today's digital landscape.
Palo Alto firewall VPN rules
Palo Alto Networks is a renowned name in the cybersecurity industry, known for its cutting-edge firewall solutions. One of the key features that Palo Alto firewalls offer is VPN functionality, allowing organizations to securely connect remote users and branch offices to their network.
VPN rules on Palo Alto firewalls are essential for establishing secure and controlled communication channels over the internet. These rules define how inbound and outbound traffic is permitted or denied within the VPN tunnels, ensuring that data is encrypted and safe from prying eyes.
Setting up VPN rules on a Palo Alto firewall involves configuring policies that determine which traffic is allowed to flow through the VPN tunnel. Administrators can create rules based on specific criteria such as source and destination IP addresses, ports, protocols, and users. By carefully defining these rules, organizations can enforce strict security measures and protect their network infrastructure from unauthorized access.
Moreover, Palo Alto firewalls support advanced features like GlobalProtect, which provides secure remote access to users located anywhere in the world. With GlobalProtect, employees can connect to the corporate network securely, regardless of their physical location, ensuring productivity and data protection.
In conclusion, Palo Alto firewall VPN rules play a crucial role in establishing secure communication channels and safeguarding sensitive data. By implementing robust VPN policies and leveraging advanced features like GlobalProtect, organizations can enhance their cybersecurity posture and mitigate the risks associated with remote connectivity.
0 notes
Text
does azure need a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does azure need a vpn
Azure VPN requirement
Azure VPN is a vital tool for organizations looking to ensure the security and privacy of their network connections. However, before setting up an Azure VPN, there are certain requirements that need to be met to guarantee a successful deployment.
One of the primary requirements when setting up an Azure VPN is a valid Azure subscription. This subscription allows users to create virtual networks, gateways, and other necessary resources to establish a secure connection. Additionally, organizations must have the right permissions and access to configure and manage the VPN resources within their Azure environment.
Another essential requirement is a compatible VPN device or software. Azure VPN supports a wide range of VPN devices, including those from major vendors like Cisco, Juniper, and Palo Alto Networks. Organizations must ensure that their VPN device is compatible with Azure VPN to establish a secure connection seamlessly.
In addition to a compatible VPN device, organizations need to have a dedicated public IP address for the VPN gateway. This public IP address serves as the endpoint for the VPN connection and enables secure communication between on-premises networks and Azure resources.
Furthermore, organizations must have a proper understanding of their network topology and routing requirements. This includes configuring the necessary routing settings to ensure that traffic flows correctly between on-premises networks and Azure virtual networks through the VPN gateway.
By meeting these essential requirements, organizations can set up an Azure VPN successfully and create a secure and reliable connection for their network resources. Implementing an Azure VPN not only enhances network security but also enables seamless connectivity between on-premises and cloud environments.
VPN necessity in Azure
In the ever-evolving digital landscape, the use of Virtual Private Networks (VPNs) has become a necessity for ensuring secure communication and data transmission. This holds especially true in cloud computing environments like Azure, where sensitive information is stored and exchanged regularly.
Azure, Microsoft's cloud computing platform, offers a robust set of services for building, deploying, and managing applications through its global network of data centers. While Azure provides various security measures to safeguard data, using a VPN adds an extra layer of protection by encrypting all data traffic between the user's devices and the Azure network.
By utilizing a VPN in Azure, users can establish a secure and private connection over the internet, significantly reducing the risk of cyber threats such as hacking, data breaches, and malware attacks. This is particularly crucial for businesses and organizations that deal with confidential data or operate in regulated industries where compliance with data protection laws is mandatory.
Moreover, a VPN in Azure allows users to bypass geographical restrictions and access region-locked content or services securely. This is beneficial for businesses with a global presence or remote workforce, as it enables seamless and secure communication across different locations.
In conclusion, implementing a VPN in Azure is essential for enhancing security, maintaining privacy, and ensuring seamless connectivity in the cloud. Whether you are a small business owner or a large enterprise, investing in a reliable VPN service for Azure can go a long way in safeguarding your digital assets and sensitive information.
Azure network security
Title: Enhancing Cyber Defense with Azure Network Security
In today's digitally connected world, safeguarding networks against cyber threats is paramount. With the rise in sophisticated cyber attacks, organizations are turning to robust solutions like Azure Network Security to fortify their defenses.
Azure Network Security offers a comprehensive suite of tools and services designed to protect networks hosted on the Microsoft Azure cloud platform. These tools encompass various layers of security, ranging from perimeter defense to advanced threat detection and response mechanisms.
One of the key features of Azure Network Security is its ability to establish secure network perimeters through features like virtual networks, network security groups, and Azure Firewall. These components allow organizations to define and enforce access controls, filter network traffic, and protect against unauthorized access from both external and internal sources.
Moreover, Azure Network Security provides advanced threat protection capabilities through services like Azure DDoS Protection and Azure Security Center. These services leverage machine learning and AI algorithms to detect and mitigate threats in real-time, helping organizations stay ahead of evolving cyber threats.
Another crucial aspect of Azure Network Security is its compliance and governance capabilities. With built-in compliance controls and continuous monitoring, organizations can ensure adherence to industry regulations and standards while maintaining visibility into their network security posture.
Furthermore, Azure Network Security integrates seamlessly with other Azure services, enabling organizations to create a unified security ecosystem. This integration enhances operational efficiency and allows for centralized management of security policies and configurations.
In conclusion, Azure Network Security offers a robust and scalable solution for protecting networks in the cloud. By leveraging its comprehensive suite of tools and services, organizations can enhance their cyber defense posture and mitigate the risks associated with modern cyber threats.
Virtual Private Network for Azure
A Virtual Private Network (VPN) for Azure is a critical tool for ensuring secure communication and data transfer within the Azure cloud environment. By utilizing a VPN, users can create a secure and private connection to Azure resources, enabling them to access data and applications securely from anywhere in the world.
One of the key benefits of using a VPN for Azure is enhanced security. VPNs encrypt data during transmission, making it extremely difficult for unauthorized users to intercept and access sensitive information. This encryption helps to protect data privacy and integrity, especially when transferring sensitive data over public networks.
Moreover, a VPN for Azure enables users to establish secure connections between on-premises networks and Azure resources. This allows organizations to extend their local networks to the cloud securely, facilitating seamless data access and communication between different environments.
In addition to security benefits, utilizing a VPN for Azure also helps improve network performance and reliability. By creating a dedicated connection to Azure resources, users can experience reduced latency and more stable network connectivity, leading to improved user experience and operational efficiency.
Overall, a Virtual Private Network for Azure is a crucial component for enhancing security, connectivity, and performance within the Azure cloud environment. By leveraging a VPN, organizations can better protect their data, streamline network operations, and ensure a seamless and secure cloud experience.
Azure connectivity options
Azure is a powerful cloud computing platform that offers a variety of connectivity options to cater to different business needs. Understanding these connectivity options is crucial for businesses looking to optimize their operations efficiently.
One popular connectivity option offered by Azure is Virtual Network (VNet) peering, which enables connecting virtual networks seamlessly. This option allows different VNets to communicate with each other securely within the Azure network, making it ideal for businesses with multiple virtual networks.
Another connectivity option is ExpressRoute, which provides a private connection to Azure for enhanced security and reliability. ExpressRoute offers dedicated connections that do not traverse the public internet, ensuring better performance and privacy for critical business applications.
Azure also provides VPN Gateway for establishing secure connections over the internet. With VPN Gateway, businesses can connect their on-premises networks to Azure securely, creating a hybrid cloud environment that enables seamless data transfer and resource access.
For businesses looking to extend their on-premises networks to Azure, Azure Site-to-Site VPN offers a viable solution. This option allows businesses to establish secure connections between their on-premises network and Azure, enabling seamless integration of resources and data flow.
In conclusion, Azure offers a wide range of connectivity options to cater to diverse business needs. Whether it's connecting virtual networks, establishing private connections, or setting up secure VPNs, Azure's connectivity options provide flexibility and scalability for businesses looking to leverage the power of the cloud.
0 notes
Text
do you need license for vpn on palo alto
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need license for vpn on palo alto
VPN licensing Palo Alto
A Virtual Private Network (VPN) is essential for businesses looking to securely connect their remote employees to the company's network. Palo Alto Networks is a renowned provider of security solutions, including VPN services. When it comes to VPN licensing options offered by Palo Alto, there are several factors to consider.
Palo Alto Networks offers VPN licensing based on the number of concurrent users or devices connecting to the VPN. This means that businesses can choose a licensing model that best fits their operational needs. Whether you have a small business with a limited number of remote employees or a large enterprise requiring a scalable VPN solution, Palo Alto Networks has licensing options to accommodate your requirements.
Palo Alto's VPN licensing also includes additional features such as advanced security functionalities, user authentication mechanisms, and integration capabilities with other security tools. This ensures that your VPN connection is not only secure but also optimized for performance and user experience.
By investing in Palo Alto's VPN licensing, businesses can benefit from top-tier security protocols, centralized management, and robust support services. This translates to a reliable and secure VPN infrastructure that protects your sensitive data and network resources from cyber threats.
In conclusion, Palo Alto Networks' VPN licensing offers businesses the flexibility, scalability, and security needed to establish a reliable and secure VPN connection for their remote workforce. Whether you are a small business or a large enterprise, Palo Alto's VPN licensing options can cater to your specific requirements and enhance your network security posture.
Palo Alto VPN requirements
Title: Understanding Palo Alto VPN Requirements
In the digital age, ensuring secure connectivity for remote workers and branch offices is paramount. Palo Alto Networks, a leading cybersecurity company, offers robust VPN (Virtual Private Network) solutions designed to meet the evolving needs of modern enterprises. However, before implementing a Palo Alto VPN, it's crucial to understand the requirements involved to ensure seamless integration and maximum security.
Compatible Hardware: Palo Alto VPN solutions require compatible hardware, such as Palo Alto Network firewalls or VPN gateways. These devices play a pivotal role in establishing secure connections and enforcing access policies.
License and Software Version: A valid license for the Palo Alto VPN feature is essential. Additionally, it's imperative to ensure that the firewall or gateway is running a supported software version compatible with the VPN functionality.
Network Infrastructure: The effectiveness of a VPN relies heavily on the underlying network infrastructure. Organizations must have a stable internet connection with sufficient bandwidth to accommodate VPN traffic without compromising performance.
Authentication Mechanisms: Palo Alto VPNs support various authentication mechanisms, including pre-shared keys, digital certificates, and integration with external authentication services like LDAP or RADIUS. Administrators need to configure authentication methods based on security policies and user requirements.
Encryption and Tunneling Protocols: Palo Alto VPNs support industry-standard encryption and tunneling protocols such as IPsec (Internet Protocol Security) and SSL/TLS (Secure Socket Layer/Transport Layer Security). Selecting appropriate encryption algorithms and key strengths is crucial to maintaining data confidentiality and integrity.
Access Control Policies: Granular access control policies should be defined to regulate VPN usage and restrict unauthorized access to sensitive resources. This involves configuring firewall rules, VPN profiles, and user/group-based access policies according to organizational security guidelines.
By adhering to these requirements, organizations can deploy Palo Alto VPNs effectively to safeguard their networks and ensure secure remote access for employees and partners. With robust encryption, centralized management, and advanced threat prevention capabilities, Palo Alto VPN solutions offer a comprehensive approach to network security in today's dynamic business landscape.
Licensing for Palo Alto VPN
When utilizing Palo Alto VPN services, having a clear understanding of licensing is crucial. Palo Alto Networks offers various licensing options tailored to meet different business needs.
The Palo Alto VPN licensing model typically includes subscriptions for different features and services. These subscriptions may encompass functionalities such as next-generation firewall security, threat prevention, URL filtering, GlobalProtect VPN, WildFire malware analysis, and more.
One of the commonly used licensing models for Palo Alto VPN is based on the number of concurrent users or devices. This model allows organizations to scale their VPN connectivity based on their requirements, paying for the number of simultaneous VPN connections needed.
Moreover, Palo Alto Networks may offer licensing options based on the duration of the subscription, such as annual or multi-year plans. These plans often come with additional support services, software updates, and access to threat intelligence to ensure the VPN infrastructure remains secure and up to date.
Understanding the licensing for Palo Alto VPN is essential for businesses to ensure they have the appropriate features and support needed to maintain secure remote access for their users. By choosing the right licensing model and subscription plan, organizations can effectively leverage Palo Alto VPN services to enhance their network security posture.
Palo Alto VPN license necessity
In today's increasingly interconnected digital landscape, ensuring the security and privacy of online communications is paramount. For individuals and businesses alike, utilizing Virtual Private Network (VPN) technology has become a common practice to safeguard sensitive data from prying eyes and malicious actors. One prominent player in the VPN market is Palo Alto Networks, renowned for its robust security solutions. However, the question arises: Is a Palo Alto VPN license a necessity?
The answer largely depends on the specific requirements and security objectives of the user. Palo Alto VPN licenses offer a range of features and functionalities tailored to meet diverse needs, including advanced encryption protocols, secure remote access capabilities, and comprehensive threat prevention mechanisms. For organizations handling sensitive information or operating in regulated industries, such as finance or healthcare, investing in a Palo Alto VPN license can be crucial for maintaining compliance with data protection regulations and safeguarding against potential cyber threats.
Moreover, Palo Alto VPN licenses often come bundled with additional security services and support options, providing users with peace of mind and ongoing assistance in managing their network security infrastructure. From real-time threat intelligence updates to proactive security monitoring and incident response, these added benefits can significantly enhance the overall effectiveness and resilience of an organization's cybersecurity posture.
Furthermore, in today's remote work environment where employees frequently access corporate networks from various locations and devices, deploying a Palo Alto VPN solution ensures secure connectivity and seamless access to critical resources without compromising data integrity or confidentiality. By encrypting all communication channels and enforcing strict access controls, Palo Alto VPNs help mitigate the risk of unauthorized access and data breaches, thereby bolstering the overall resilience of the organization's IT infrastructure.
In conclusion, while the necessity of a Palo Alto VPN license may vary depending on individual circumstances, its value in enhancing cybersecurity and safeguarding sensitive data cannot be overstated. For organizations prioritizing security and compliance, investing in a Palo Alto VPN license is a prudent decision that pays dividends in terms of risk mitigation, regulatory adherence, and peace of mind.
VPN license on Palo Alto firewall
A VPN license on a Palo Alto firewall is essential for ensuring secure and encrypted communications over virtual private networks. Palo Alto Networks offers different types of VPN licenses to cater to various business needs and requirements. These licenses enable organizations to establish secure connections between remote locations, cloud infrastructures, and mobile users.
By obtaining a VPN license on a Palo Alto firewall, businesses can enhance their network security and protect sensitive data from unauthorized access or cyber threats. These licenses provide advanced features such as strong encryption, secure tunneling protocols, and multi-factor authentication to ensure the confidentiality, integrity, and availability of data transmitted over VPN connections.
One of the key benefits of a VPN license on a Palo Alto firewall is the ability to establish site-to-site VPN connections, allowing different branch offices or remote locations to securely communicate with each other over the internet. This facilitates seamless collaboration and data sharing between geographically dispersed teams without compromising security.
Furthermore, VPN licenses on Palo Alto firewalls offer scalability and flexibility, enabling businesses to easily expand their VPN infrastructure as their network requirements evolve. With robust security capabilities and centralized management, Palo Alto firewalls with VPN licenses provide a comprehensive solution for organizations looking to establish secure and reliable connectivity across their network.
In conclusion, investing in a VPN license on a Palo Alto firewall is a prudent decision for organizations seeking to bolster their network security and establish encrypted communication channels. By leveraging the advanced features and capabilities of Palo Alto firewalls, businesses can mitigate cybersecurity risks and safeguard their critical assets from potential threats in today's digital landscape.
0 notes
Text
Diabetes Care | Services | Right at Home
Looking for Customized Diabetic in Home care for senior in San Mateo and Palo Alto, CA? Right at Home helps seniors age safety at home with personalized Diabetic Care. Contact Us Now.

0 notes
Text
Advocating for Mental Health: The Journey of Dr. Bobby Kato
Dr. Bobby Kato is a prominent figure in the healthcare industry, known for his expertise, dedication, and innovative approach to mental health advocacy. With a background in psychology and organizational behavior, Dr. Kato has made significant contributions to the field through his academic achievements, clinical practice, and advocacy efforts.

Dr. Kato's academic journey began with a Bachelor's degree in Psychology from Hunter College, followed by a Master of Science in Psychology from Palo Alto University. He furthered his education by earning a Doctor of Philosophy (Ph.D.) in Industrial and Organizational Psychology from Capella University, demonstrating his commitment to understanding human behavior in various contexts.
As the founder and owner of Nova Lux Counseling, Dr. Kato has accumulated over 20 years of experience in healthcare. His roles have included administrator, consultant, provider, and founder, showcasing his versatility and dedication to improving healthcare practices. Through Nova Lux Counseling, Dr. Kato has provided invaluable support to individuals struggling with mental health issues, promoting holistic well-being through his clinical expertise.
In addition to his clinical practice, Dr. Kato has held administrative positions, highlighting his proficiency in managing healthcare systems. His consulting services for healthcare organizations further demonstrate his industry knowledge aimed at enhancing operational efficiency and patient outcomes.
Dr. Kato's contributions to mental health research have been profound, with studies revealing important insights into the relationship between psychological distress and cardiovascular illness. His research emphasizes the importance of incorporating mental health evaluations into patient care, advocating for a more holistic approach to healthcare.
Dr. Kato is also dedicated to improving healthcare workflow and reducing burnout among healthcare professionals. He has been involved in projects aimed at reducing stress for nurses, highlighting his commitment to improving healthcare practices and promoting well-being in the workplace.
Furthermore, Dr. Kato has shed light on the impact of political factors on Latino mental health, discussing how anti-immigration ads and rhetoric can affect the mental well-being of Latinos. His insights underscore the importance of considering socio-political contexts in mental health care, advocating for a more comprehensive and inclusive approach to patient care.
Dr. Bobby Kato is a healthcare professional who exemplifies excellence in mental health advocacy. His dedication to improving patient care, advancing healthcare practices, and advocating for holistic well-being serves as an inspiration to others in the field. Dr. Kato's innovative approach and commitment to advocacy continue to make a significant impact on the healthcare industry.
0 notes
Text
Shadi Rostami, SVP of Engineering at Amplitude – Interview Series
New Post has been published on https://thedigitalinsider.com/shadi-rostami-svp-of-engineering-at-amplitude-interview-series/
Shadi Rostami, SVP of Engineering at Amplitude – Interview Series
Shadi is SVP of Engineering at digital analytics leader Amplitude. She is a passionate, seasoned technology leader and architect experienced in building and managing highly proficient engineering teams. Prior to Amplitude, she was VP of Engineering at Palo Alto Networks. She has innovated and delivered several product lines and services specializing in distributed systems, cloud computing, big data, machine learning and security.
Amplitude is built on modern machine learning and generative AI technologies that enable product teams to build smarter, learn faster, and create the best digital experiences for their customers.
What initially attracted you to computer science and engineering?
I grew up in Iran and originally pursued a high school path that would enable a career in medicine, which was the path my father wanted me to take and the one my brother did. About a year and a half in, I decided it was not the path for me. Instead, I pursued engineering and ended up becoming the first girl in Iran to go to the Informatic Olympiad (IOI) and won the Bronze medal, a yearly competition for high school students around the world competing in math, physics, Informatics, and chemistry. That led me to pursue engineering at Sharif University of Technology in Iran and later get my Ph.D. in computer engineering at the University of British Columbia in Canada. After that, I worked for startups for a few years and then spent a decade at Palo Alto Networks, eventually becoming a VP responsible for development, QA, DevOps, and data science. Five years ago, I moved to Amplitude as the SVP of Engineering.
Could you discuss Amplitude’s core AI philosophy that AI should aid humans in improving their work rather than replacing them?
AI is quickly transforming almost every industry, and with the transformation comes questions about how companies will use the technology. We feel strongly about getting AI right. This belief led us to develop our customer-centric AI philosophy, which stands upon five main principles: (1) collaborative development and thought partnership, (2) data governance and user data protection, (3) transparency, (4) privacy, security, and regulatory compliance, and (5) customer choice and control. We know these principles are key as companies continue to adopt and test AI and eventually become truly data-driven. For our purposes, this means building AI tools that help people get to insights faster. When harnessed properly, these insights lead to faster, better decisions that drive bottom-line results. Using AI as a tool to complement human intelligence and creativity is where I see AI having its greatest impact.
Can you explain the concept of ‘data democracy’ in the context of today’s AI-driven business environment?
“Data democracy is driven by the knowledge that teams function better, faster, and more efficiently when they can access the right data insights at the right time. In today’s rapidly advancing AI-driven environment, teams can’t afford to wait days or weeks for data pulls. To mitigate this, companies must empower their teams to leverage data in a self-service way. Now, this doesn’t mean data chaos with no parameters. At the end of the day, bad data leads to bad AI. But with the right tools and processes in place, businesses can balance data democratization with data governance, enabling better business outcomes.”
What key shifts in organizational culture do you believe are essential for enabling true data democracy in the age of AI?
Establishing a true data democracy within your organization starts with two foundational culture shifts: providing the right, most accessible tools and conducting organization-wide efforts around data literacy. This means adopting self-service tools that allow non-technical team members, such as marketing or customer success teams, to not only access data but also analyze and take action on it. I believe self-service data analytics can and should fuel collaboration across teams, inspire curiosity and exploration, scale data literacy, and place a bias on action and impact. Also, it is important to spend joint efforts between the central data team and line of business teams to do continuous data governance to make sure data quality does not degrade over time.
In your experience, what are the most significant challenges organizations face in achieving data democratization, and how can they overcome these obstacles?
In the past, companies have tried to centralize data within one team of experts, leaving the rest of the organization reliant on this team to deliver analysis and key insights that may be critical to their day-to-day operations and decision-making. While democratizing data access is critical to solving this bottleneck, it can also be challenging. When I speak to data leaders about operationalizing self-service, it’s clear there is a spectrum. On one end, you have low setup tools for non-technical and line-of-business teams. Ultimately, these tools do not give the depth and breadth of answers that these teams need. On the other end, you have more technical tools for more technical teams. They are much more flexible in terms of analysis, but they are slow, and likely very few people can even use them. We refer to these tools as creating a “data breadline” … you’re always waiting for answers. Teams need a solution in the middle. Think out-of-the-box solutions that encourage, not inhibit, exploration and experimentation. With the proper tooling and team education, companies can more easily bridge the data democratization gap.
How crucial is data literacy in the process of data democratization, and what steps should companies take to improve it among their employees?
Fostering an environment of data democratization across your teams is a cultural challenge that requires education and company-wide buy-in. In my experiences with teaching data processes to non-technical members, the best way to develop these skills is through a combination of training and hands-on learning. I recommend developing a comprehensive training program to ensure employees feel comfortable and confident in the insights they’re pulling from their data. Make sure you are using a tool that does not prohibit non-technical users: for example, any tool that requires knowledge of SQL would marginalize folks without programming expertise. From there, provide opportunities for employees to dive in and start playing around with the data. Finally, implement a tool that fosters exploration and collaboration. The less people are working in silos, the more they can bounce ideas off of each other, leading to more illuminating insights. If you are a data professional teaching a non-technical team member, remember that you have spent years learning how to obtain and use data, so you think about it differently from the casual user. Be open to teaching others rather than doing everything yourself. Otherwise, you’ll never have any free time to do anything aside from answering people’s questions.
With the rapid evolution of data tools and generative AI technologies, how should companies adapt their strategies to stay ahead in data management and utilization?
Data governance is one of the main challenges companies still face, and it’s something every organization must nail down to empower meaningful AI and data experiences. AI is only as good as the data that powers it, and clean data leads to more impactful insights, happier users, and business growth. In this way, companies must be proactive about data cleanup and taxonomy, and there are opportunities to use generative AI to manage your AI governance and quality. For example, at Amplitude, we launched our AI-powered Data Assistant product last year, which offers intelligent recommendations and automation to make data governance seamless and help users take charge of data quality efforts.
How does Amplitude enable enterprises to better understand the customer journey?
Building great digital products and experiences is hard, especially in today’s competitive landscape. Today, many companies still don’t know who they’re building for or what their customers want. Amplitude helps businesses answer questions like, “What do our customers love? Where do they get stuck? What keeps them coming back?” through quantitative and qualitative data insights. Our platform helps businesses better understand the end-to-end customer journey by surfacing data to help drive the customer acquisition, monetization, and retention cycle. Today, more than 2,700 customers, including enterprise brands like Atlassian, NBC Universal, and Under Armour, leverage Amplitude to build better products.
Thank you for the great interview, readers who wish to learn more should visit Amplitude.
#ai#ai tools#AI-powered#amplitude#Analysis#Analytics#Atlassian#automation#Bias#Big Data#box#brands#bridge#Building#Business#business environment#Canada#career#challenge#chaos#chemistry#Cloud#cloud computing#Collaboration#collaborative#Companies#compliance#comprehensive#computer#Computer Science
0 notes