Text
Electronic Waste Removal
“E-waste”, “electronic waste”, “e-scrap” and “end-of-life electronics” are terms often used to describe used electronics that are nearing the end of their useful life, and are discarded, donated, or given to a recycler.
There are multiple ways the asset can be benefited from, this totally depends upon the owner of the asset. The owner can decide whether he wants to resell the device, recycle the material, or donate it.

0 notes
Text
White-Glove Service
What is White-Glove?
White-glove is a service providing premium delivery of goods with special attention, with certain items that require utmost care while transportation and delivery.
White-glove service is popularly used for delivering specialty goods which include fragile, valuable, climate-sensitive items, artwork, expensive equipment, etc. It is the service attitude of white-glove that sets their delivery special apart from the rest.

White-Glove Service Attitude
It is their service standard of delicate treatment from special packaging till delivery of the goods in pristine condition. White glove service providers are been trusted for their team of experienced professionals having expertise in end-to-end service.
Pristine Delivery
The professionals at white-glove make additional efforts and take utmost care in delivering the goods in pristine condition, that means in their original condition.
The trained experts follow standard protocols and guidelines while carefully handling the consignments throughout the delivery process.
Delivery Standard
This includes careful packaging, placing, and shipment of delicate and oversized freight and the service for specific category goods in the purpose-built vehicles such as padded vans, temperature and climate-controlled trucks and monitoring the valuable goods while they are in transit till the impeccable and meticulous delivery.
Special Packaging
White-glove offers customized packaging of goods depending upon their nature, size, fragility, and value including corrugated containers, custom boxes, and specially designed crates that easily pass international shipping standards.
Time Precision
Completing a task on time with perfection adds extra value to the service. White-glove not only provides special service but also completes the task by delivering the goods safely at a time best suiting to the customer.
The team gets in touch with the customer for understanding any specific delivery needs to arrange a tailored and convenient time slot for the customer.
Real-Tim Freight Tracking
White-glove service offers transparency to the customers to track real-time progress over every stage of the delivery. They use business intelligence tools and applications to track the shipments right from the pick-up to till the safe delivery of the goods at the destination.
Premium Customer Service
White-glove transporters provide flawless customer service for a great experience for the customers. They offer 24x7 customer service throughout the process. They have a dedicated team to communicate and serve the customer in the best possible way, ensuring quality service.
0 notes
Text
Mobile Hard Drive Shredding
Mobile Hard Drive Shredding
The ongoing evolution of business and industries results in changing the technologies, equipment, and assets of the organization. With the changes in technologies, computer equipment also changes. While replacing the essential assets like a hard drive or any storage media it is important to secure the data which is present in that storage media or hard drive. Information stored for a long time includes various methodologies on which a company is running, important details of that organization, and other important data.

To eliminate the risk of data breaching, the storage devices are destructed. There are various forms and techniques of destructing the assets- data shredding, crushing, and degaussing. These processes eliminate any chance of data being recovered from any destroyed media. The most effective way of protecting the data of storage devices is their destruction.
Destructing storage devices by shredding them is a great to protect your data. While considering shredding the storage media, Patriot IT Solutions, LLC come to the rescue. We offer the most effective level of convenience and security for shredding mobile hard drives. We strive for quality service and assure the destruction of the media.
Our services include:
Fast and efficient hard drive destruction
Auditable reports
PCI compliant
Environmentally-friendly disposal of scrap
Certification of destruction, etc.
The services we provide are cost-effective and secure for shredding hard drives, this includes:
On-site and off-site hard drive shredding service
Documentation of each process
Reporting
Asset tag removal
Chain of custody documentation
Secure real-time asset tracking logistics
#mobile hard drive destruction#hard drive destruction#hard drive shredding#on site hard drive shredding#off site hard drive shredding#data security#it solutions
0 notes
Text
The Importance of Data Security
The process of protecting digital information from corruption, data manipulation, and unauthorized access, throughout its lifecycle. It is important to protect your data under organizational policies and procedures. Data security is the observation of assuring the confidentiality, integrity, and accessibility of the information.

There are 3 main concerns to protect data effectively:
1. Losing Business: Cyber attackers can not only breach your data by accessing it, rather they can also exploit sensitive data or delete an equivalent statement. This results in a great loss of the business. They may even add extremely harmful viruses that can infect the entire system.
2. Degradation of Reputation: Privacy and security of information are really important, as that effects ultimately your customers. Any such action of their security breach or service that is not up to the satisfaction level of your customer may result badly and this affects the reputation of your organization. This action of customers results greatly defames your organization. Customers lose their level of confidence in your organization and probably won’t work with your organization in future.
3. Costly Fines and Litigations: Information breaching is typically a serious issue that may result in legal actions from the client for the organization. Data protection laws result in heavy fines. This increases the risk of losing reputation, ultimately customers.
Every company have data of their personnel files, client data, service information, money transactions, product information, techniques, etc. These are the basic assets of any company to remain active in the market. Data security is the least that the owner or the customer expects. Data protection is the first and foremost priority of any organization.
DATA SECURITY CONTROLS
· Access Control- Ensuring each device is password-protected and is solely accessible to licensed staff helps for securing the data. Information access management restricts the access of information so that the data or the code may not get manipulated.
· Authentication- By applying the authentication measures for access restrictions and proper individual identification, before providing the access to the information. Pins, passwords, security tokens, swipe cards, etc. are some common examples.
· Backup Recovery- A proven technique to securely access in case any of these occurs: information of a system failure, information corruption, disaster of code, security breach. To restore the information you require a copy of the backup information.
· Data Destruction- Discarding the data frequently is critical, destruction of data is preferable, as it destroys the media in which the data is stored.
· Data Masking- Data masking of code protects letters and numbers with proxy characters and helps in hiding the information.
· Data-Resilience- Data privacy is often enforced by incorporating resilience into code and hardware. Avoiding power outages and mitigation of natural catastrophes as these factors breaches data security.
· Encryption
Encrypting data that can be decrypted by only those who have access to being licensed, those with acceptable keys. All the data of files and databases which is to be mailed should be secured.
Two primary types of cryptography are biracial cryptography and uneven cryptography. Cryptography is often called public-key cryptography.
0 notes
Text
Patriot IT provides Certified Hard Drive Destruction/Equipment Disposal, Professional Relocation of Office Equipment, Specialized Relocation of Rack-Mounted Equipment, and Government Services.
0 notes
Text
ITAD - IT Asset Disposition
What is IT Asset Disposition (ITAD)?
The process of perfectly decommissioning and disposing of electronic devices and hardware is known as ITAD.
https://bit.ly/3wNpuaW
Why ITAD is important for IT Lifecycle Management?
Asset Lifecycle: Series of stages involving asset management from the planning phase, where the need of an asset is identified including all the phases, till the eventual disposal of that asset.
ITAD is an essential part of IT lifecycle management.
https://bit.ly/3DipzEV
Data breach or theft protection is one of the main causes of IT asset disposition. Organizations store their data or work with any IT asset, while they are of no further use they are preferred to be destructed and disposed of securely in order to secure the data which is stored in it. Millions of records are stolen, to ensure the security of your data the asset is destructed.
Where does the asset go after performing ITAD to it?
There are multiple ways the asset can be benefitted from, this totally depends upon the owner of the asset. The owner can decide whether he wants to resell the device, recycle the material, or donate it.
https://www.patriotitsolutions.com/disposal-and-destruction-services
https://www.patriotitsolutions.com/
0 notes
Text
Steps for Successful Rack Integration
Every company wants its official objects to relocate safely and securely at the destination or data center. Moving to a new location requires racking the objects and reinstalling them at the new place.
What is Rack and Stack?
Racking also refers to rack integration, it is the process of assembling computer hardware systems of individual server nodes and their components such as cables, routers, office furniture, network equipment, etc. into computer server cabinets, making them simple to integrate, easy to ship, ease in unloading and simple to set up with the hardware and types of equipment at the destination. Whereas, Stacking is transporting and deploying the racks to the destined location or the data center.

What is the need of hiring professionals for rack integration?
When companies move from one location to another, they also need to safely relocate their hardware, components, office furniture, routers, etc. to the new place. It is not appropriate to ask the employees to relocate everything. This will consume a lot of time, energy and it is not guaranteed that the objects will get relocated safely at the destination.
To perform the integration in optimum time, the company needs to take the service of rack integration providers for quality service assurance. Taking the service, packing, transporting, and integrating the objects at the new location saves time. This helps in safely relocating and reinstalling the objects at the destined location.
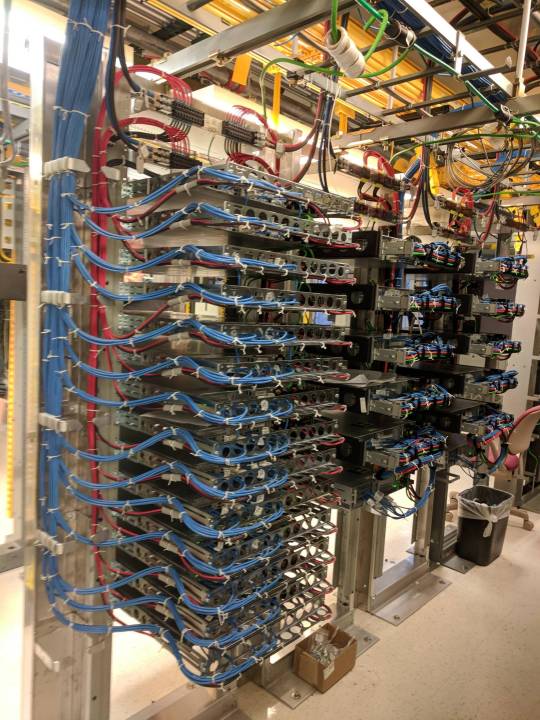
How rack integration is done?
Each component is carefully mounted upon each other (rack), before moving it to the data center for its safe deployment (stack). Racking services are usually offered by professional vendors to equip the objects efficiently and reinstall them accurately at the destination in a minimal time.
What to consider before starting the process of racking and stacking?
Following a systematic approach of cable deployment eliminates several problems and provides ease in performing their work in a managed way.

Efficient Cabling Tips for Rack and Stack:
· Port mapping and cable traceability help greatly in ongoing maintenance.
· Using colored cables helps in proper allocation according to the functions of the cables, this practice helps in saving time.
· It is advisable not to use slack with more than 12 inches, as it can increase weight.
· Keep every type of cable separately, electromagnetic interference occurs by binding them together.
Tips for documented Rack Layout:
· Detailed asset reports containing inventory should be maintained for ongoing and future requirements.
· Maintain a list of cables that are in use for a project and the total cables which are there.
· Marking cables according to their use, helps technicians to easily maintain and adjust them.
Effective Planning for Rack and Stack
Prepare a structured plan according to your requirements, this helps in expected results by reinstalling all the IT equipments easily and saves time as well.
For more questions and support, reach us at: https://www.patriotitsolutions.com/
0 notes
Text
Data Shredding: The Process of it and Need To Perform this Technique

Our secure data shredding service destroys storage media physically, by ensuring it can't be recovered ever again. We follow the highest standards to train our professionals for destroying the storage media. Our process provides a certified auditable strategy for the disposal of your old disk drives, SSDs, and magnetic tapes securely.
Importance of Securely Destruction of your Old Storage Media
It can be enticing to remove storage media like hard disk drives, solid-state drives, magnetic tape, mobile hard drive shredding, IT asset destruction, or any other storage media and store those within your company. You can simply dispose of these storage media without worrying about your data protection as it is cheap and easy.
It is really important to ensure that your data is secure, but storing the old data in bulk is not safe though. If somehow any unauthorized person accesses your storage location, you cannot guarantee the security of your data ever again, you must always opt to destroy data for ensuring its security.
There must always be an extremely valid reason to archive old data storage media – the physical destruction of old media is the most secure and reliable option.

Considering the Storage Density
Storage density depicts the volume of data that can be stored in given physical media storage. Sized flash chips data can store the amount of data depending upon its storage size, using storage media of greater size can store a higher amount of data into it.
It is still possible to retrieve data from the small fragments even after performing the shredding process. To prevent data recovery, storage media with higher density must always be more finely shredded for destructing and ensuring its security. The higher the density of the storage media the more finely shredding is required to ensure the security of data.

The Problems Faced with SSDs
SSDs are splendid as they offer read and write feature, they can enhance the speed of an operating system by offering higher storage capacity in any portable device.
However, it has drawbacks as well. The storage of these runs out faster as compared to traditional hard drives. To overcome this issue software is built into the drive which uses the algorithm “wear leveling” for ensuring to store data to the most un-utilized part of the SSD, increasing its life. Doing this, it makes much more difficult for the SSDs to encrypt and gives the least chance to securely wipe.
This intends that the only secure option for SSDs is to physically destruct the data of the drive storage. There are many portable devices whose data destruction is done most effectively and that is physical destruction, it is called hardware end of life.


Traceability and Auditing
At the point when you should have the option to verify secure data destruction to keep away from possibly tremendous fines, paying somebody to destruct your old media storage isn't sufficient, especially if you process personal data under the General Data Protection Regulation. We work to ISO accredited standards for the reliable process and by following the secure chain of custody. We not only offer the best service but also a certificate of destruction after every disposal.
Our highly trained staff is always ready to offer their best service of disposal and destruction of any of your data. We offer certified data destruction and on-site hard drive shredding, of any industry or any work, we are here to serve you the best and guide you through every process of securing your data by destructing it efficiently.
For any questions or support, reach us at: https://www.patriotitsolutions.com/
#hard drive shredding#data destruction#hardware end-of-life#on site hard drive shredding#it asset destruction#certified data destruction#destroy data#secure chain of custody
1 note
·
View note