#usb data recovery online
Link

Data recovery software is often the easiest and most reliable way to restore lost files from a USB drive. Such software can help you scan the drive and recover all recoverable data. Recover deleted files from a USB drive is often daunting, but with the right tools and techniques, it can recover your data.
Our software can recover your lost crucial word documents, excel spreadsheets, PowerPoint slides, images, photographs, and other precious deleted data from USB storage media. Visit us: www.sdcarddatarecovery.org/sdcarddatarecovery/usb-drive.html
#recover deleted files from USB drive#usb data recovery online#usb drive data recovery software#recover lost data from usb#restore deleted files from usb drive#recover deleted files usb drive
0 notes
Text
Audience’s Device Preference For Streaming
In today's world, audience preference for video streaming through various streaming devices has changed. Due to everyone's taste, we will discuss some streaming devices in this article.
Smart Tvs And Android Tvs
Smart TVs and Android TVs are mostly the same but run on different operating systems. Smart TVs come equipped with intuitive interfaces, making navigation through various apps and settings effortless. An additional significant advantage of smart TVs is their app ecosystem. Moreover, smart TVs often include built-in connectivity options like Bluetooth and Wi-Fi, allowing seamless integration with other smart devices in your home. Despite offering a plethora of digital features, smart TVs prioritize picture and sound quality. Most smart TVs available today support high-definition (HD) or even 4K Ultra HD resolutions, delivering stunning visuals and vibrant colors. This convergence of advanced technology and user-friendly design has made smart TVs an indispensable part of modern entertainment setups.
Streaming Boxes And Sticks
Streaming sticks or boxes plug into any TV with a USB port, transforming a basic TV into a smart one. The stick connects to the internet, granting access to media from specific streaming services. Choosing between a streaming stick or box depends on your space and media needs, but both options offer numerous benefits. Streaming sticks are highly portable, fitting into a pocket or purse, ideal for taking to a friend's house or on vacation. Additionally, streaming devices are more affordable than smart TVs, enabling easy replacement without breaking the bank if needed. Some models provide specialized streaming services not found on smart TVs, ensuring precise content access. Most modern TVs work with streaming sticks, requiring minimal additional equipment or home theater system reconfiguration. Some sticks and boxes integrate with smart home systems and mobile devices via an app, allowing convenient control via voice commands or smartphones, in addition to the device's remote. Examples include the Amazon Fire TV Stick, Google Chromecast, or Roku Express.
Gaming Consoles
Gaming consoles are used to play games online using a console gaming system. They store information in a similar fashion to computers since they are basically computers. Many people use their gaming system not just for playing games, but also to browse the Internet and watch movies. Information is stored on the hard drive inside the gaming console, allowing for the recovery of information, including deleted data. Console games receive commands from the player through the use of an input device, commonly called a controller. Unlike a PC, which uses a keyboard and mouse, or a mobile device that uses a touch interface, console games are limited in their control schemes by the available hardware for the console.
Mobile Devices
Yes, it's entirely possible to live stream from both Android and iPhone devices. Simply acquire the appropriate live streaming apps for your phone's operating system, such as Facebook, Twitch, YouTube, or Instagram. Streaming encompasses delivering any media content—live or recorded—to computers and mobile devices via the internet, allowing real-time playback of podcasts, webcasts, movies, TV shows, and music videos. This method eliminates the need to download content before viewing or listening.
Considering the current proliferation of mobile devices and their integration with video streaming technology, you might be contemplating leveraging this trend for business growth. Before diving in, it's crucial to understand the intricacies of video streaming to mobile devices. Mobile networks now support high-quality video streaming, with data transmission rates reaching up to 2Mbps or more in local area coverage and up to 384 Kbps or more in wide area coverage. Understanding these dynamics can propel your business towards greater success.
Other Devices
In conclusion, the world of streaming devices offers a diverse array of options catering to various preferences and needs. From Samsung's Tizen and LG's WebOS to Amazon's Fire OS and Roku's TV OS, each platform brings its unique features and functionalities to the table. Panasonic's Firefox OS and Apple's tvOS further enrich the streaming landscape with their distinct offerings. Among the notable devices is the Amazon Fire TV Stick 4K Max, enhancing the viewing experience with its advanced capabilities. At www.formuler.com, we pride ourselves on providing the best Android OTT Streaming Box solutions. Our product lineup includes a range of options such as the Formuler Z11 Pro with BT1 Remote, Formuler Z Mini with BT1, and the Formuler GTV, catering to diverse preferences and ensuring an unparalleled streaming experience for our users.
0 notes
Text
Should You Be Working in the Cloud Computing

When you save files on your computer or USB, you have probably already set up a folder structure to suit your needs, and you know exactly where you are placing the files for storage and retrieval.
Cloud computing is a term used to refer to storing and accessing data and programs over the internet. At a simplistic level, the cloud is a network of connected servers. Typically cloud service providers have systems comprising thousands of servers stored in enormous data centers or server warehouses.
You may not know where your data is being physically held, as the provider may be based in the UAE for example, but their servers might be in China, the USA, or anywhere else in the world. In addition to storing data, you may also use software from the cloud, known as SaaS or Software as a Service.
You can access any of your data stored in the cloud via the internet by logging in to the cloud service platform of your chosen provider – using any device, from any location, and at any time.
On a personal level, you are probably already using cloud computing daily to send emails, create and edit documents, store pictures, listen to music, or play games online.
However, many people hesitate to move their organisational data or systems into the cloud, and their concerns tend to centre around three critical misconceptions:
1. the cloud is not secure
2. using the cloud is expensive
3. you lose control of your data security
1. The cloud is not secure:
Security is one of the most common concerns. As cloud-based systems and data are available anytime and from any device, there is a perception that protection is low, and anyone can access your information. Although no IT systems are ever completely secure, for many companies, cloud computing offers the safest environment possible for their needs.
Cloud service providers typically provide multi-layered security and anti-virus protection at a lower cost than if you were to try to manage this in-house. Also, they take care of software updates and patches to ensure that they have the latest protection in response to any external threats.
2. Using the cloud is expensive:
When you place your data in the cloud, you will typically pay for only the services you use. This means that you do not have redundant systems and you lower operating costs whilst being able to scale up your operations whenever needed. Cloud computing provides you with improved collaboration and productivity and removes the need for you to purchase and manage expensive hardware infrastructure. The software is continuously updated, and the service platform provider takes care of your disaster recovery needs.
3. You lose control of your data security:
Protecting your data is ultimately the responsibility of those that have access to it. Careless use of browsers in public places can leave your systems open to access by non-authorized individuals.
Similarly, losing a laptop or mobile device can compromise your cloud security if someone can gain access to your login information. The only recourse is to ensure that everyone who has access to your systems and data in the cloud is aware of the consequences of careless use and lack of attention to security risks.
Cloud-based computing is not fault-proof, and of course, you can experience outages or server failures. Still, cloud use is increasing significantly and, if you select your service provider carefully, it can be a very secure and cost-effective way to manage your IT demands.
Contact us at HRBluSky today to learn how you can take advantage of all the cloud has to offer.
0 notes
Text
External & Portable Hard Disk Recovery

We are also capable of data recovery for heavy disk drives, solid state disks, external and portable hard disk recovery, desktop and laptop hard drive recovery, server and exchange data recovery. Any recovery we do may trigger extra loaded data, you can talk to us to get your lost data recovery plan back. Data recovery company is considered as one of the most famous all information companies in India. If your system HDD is working but your files are lost or deleted and you can’t access your files, then it is bad for you. Don’t worry, data recovery services are any kind or tedious. The model of the drive or the lost data may well get the solution - Hard Disk Data Recovery.
We use data recovery services which will ensure that we give you the best chance of getting your data back. The biggest motto of data recovery company is recovery specialist, who has gained knowledge from many software systems across the country. We have one of the best tools for the business people to compensate for the loss through data loss in their business. We have experience, information, information recovery tools and facilities to recover data from all types of exhaust drives, USB flash drives, water or drained hard drives, burnt drives and notebook computers. The most essential factor to do data recovery is the knowledge of recovery software that our company has.
Customers are very satisfied with the service received from data recovery services. Our company is fully data recovery savvy which is made the choice. Our data recovery company has specialized hardware imaging equipment allowing most of the data to be recovered in perfect condition. You can apply on our website online every time anytime. We are well equipped and ready to handle the most complicated HDD recoveries regardless of the damage to your hard disk drive. You will also find that you will be offered a variety of recovery options that will be best performed on your hard disk data recovery services. You will get that you stand a higher chance of successful full - HDD Data Recovery. For more information, please visit our site https://www.nowdatarecovery.com/
0 notes
Text
qnap storage
Unleash the Power of QNAP: Deep Dive into Advanced Features and Applications
QNAP NAS devices aren't just glorified storage boxes; they're versatile powerhouses packed with advanced features and applications that go beyond basic file sharing. Let's delve deeper into the exciting world of QNAP functionalities that elevate your data management experience:
Security and Protection:
Data encryption: Secure your sensitive data with AES-256 encryption, ensuring that only authorized users can access it.
Snapshot technology: Create instant backups of your entire system to roll back to any previous state in case of accidental modifications or security breaches.
Anti-virus and malware protection: Keep your NAS safe from malicious software with built-in anti-virus and malware scanning tools.
Access control: Define granular access permissions for different users and folders, ensuring data privacy and security.
Productivity and Collaboration:
Virtualization station: Run multiple virtual machines and operating systems directly on your NAS, ideal for running specific applications without needing dedicated hardware.
Containerization: Deploy containerized applications for flexible and resource-efficient operation, allowing you to experiment and run diverse software with ease.
File server and remote access: Access your files remotely from anywhere in the world using secure protocols like WebDAV and VPN.
Office productivity applications: Collaborate seamlessly with built-in applications like WPS Office, allowing document editing and file sharing within your team.
Multimedia and Entertainment:
Plex Media Server: Turn your NAS into a powerful media center, enabling you to stream movies, music, and photos to any device with Plex apps.
DLNA and Chromecast support: Seamlessly stream your media to any compatible device like Smart TVs or speakers.
Karaoke station: Transform your NAS into a personal karaoke hub with apps like QMusic that provide song management and scoring features.
Surveillance station: Build a comprehensive security system by connecting IP cameras to your NAS, allowing remote monitoring and recording.
Automation and Efficiency:
Scheduling and automation: Automate tasks like backup routines, system maintenance, and file transfers, freeing up your time and effort.
Mobile apps: Manage your NAS and access files on the go using intuitive mobile apps for iOS and Android devices.
IFTTT and QNAP IFTTT Agent: Connect your NAS to various smart home and online services via IFTTT, enabling automated workflows and interactions between different devices and platforms.
Hybrid cloud storage: Connect your NAS to various cloud storage services like Amazon S3 or Google Drive for offsite backup and disaster recovery.
QNAP beyond NAS:
QNAP's vision extends beyond traditional NAS functionalities. They offer a diverse ecosystem of accessories and add-ons that expand your NAS's capabilities:
USB 3.2 Gen 2 external enclosures: Add additional storage capacity or improve transfer speeds with high-performance external enclosures.
PCIe expansion cards: Enhance your NAS with features like 10GbE networking, M.2 NVMe SSD caching, or even graphics cards for GPU-powered applications.
QNAP QTS App Center: Discover a vast library of third-party apps that add further functionality to your NAS, ranging from productivity tools to gaming servers.
The possibilities are endless with QNAP:
Investing in a QNAP NAS opens doors to a world of digital possibilities. From secure storage and data protection to powerful applications and entertainment options, QNAP empowers you to take control of your data and unlock its full potential. Explore the diverse range of QNAP models and delve into the exciting world of features and functionalities that await. Embrace the freedom and flexibility of a personal cloud powered by QNAP, and transform the way you manage, protect, and enjoy your digital life.
Remember, this is just a starting point. Feel free to ask any specific questions you may have about QNAP features, applications, or model recommendations. I'm here to help you navigate the exciting world of QNAP NAS solutions and find the perfect fit for your needs!
0 notes
Text
youtube
Upgrading the SSD in an iMac involves several steps, and it may vary depending on the specific model. Here's a general guide that covers the process for some iMac models. Before proceeding, make sure to check the compatibility and warranty implications, and if you're not comfortable with the process, consider seeking professional help.
Note: This information is for educational purposes only, and I am not responsible for any damage that may occur during the upgrade process. Proceed at your own risk.
Tools and Materials Needed:
Compatible SSD: Ensure the new SSD is compatible with your iMac model.
Screwdrivers: Typically, you'll need a Phillips screwdriver.
Opening tools: Plastic or metal spudgers for safely opening the iMac.
External Drive Enclosure (optional): If you need to clone data from the existing drive.
Backup: Ensure you have a backup of your important data before starting.
Procedure:
Check Compatibility:
Verify that the SSD you have is compatible with your iMac model.
Backup Data:
Perform a backup of your important data. You can use Time Machine or any other backup method of your choice.
Power Off and Disconnect:
Power off your iMac and disconnect it from any power source.
Ground Yourself:
Use an anti-static wrist strap or regularly touch a grounded metal surface to discharge static electricity.
Open the iMac:
Follow the iMac's user manual or online guides to open the case. This often involves removing screws and using opening tools to release clips.
Locate the SSD:
Identify the existing SSD or HDD and its location within the iMac.
Remove Existing SSD:
Carefully disconnect and remove the existing SSD. It might be held in place by screws or connectors. Take note of how it's installed for reference.
Install the New SSD:
Place the new SSD in the same location and connect it securely. Make sure to follow any specific installation instructions provided with the SSD.
Close the iMac:
Carefully close the iMac and secure any screws that were removed.
Clone Data (Optional):
If you're not performing a fresh installation of the operating system, you may need to clone the data from the old drive to the new SSD. Use an external drive enclosure and cloning software for this purpose.
Boot Up and Test:
Power on your iMac and check if the new SSD is recognized. If you've cloned data, ensure that everything is working as expected.
Install macOS (If Necessary):
If you've installed a new, empty SSD, you may need to install macOS. You can do this using macOS Recovery or a bootable USB drive.
Format the New SSD (If Necessary):
If the new SSD is not recognized or needs formatting, use Disk Utility to format it correctly.
Remember to consult the specific documentation for your iMac model, as the procedure can vary. If you're uncertain or uncomfortable with any step, bring it to applefix Hamilton new Zealand 124 ward street Hamilton
0 notes
Text
Introducing Home Assistant Green - A Privacy-focused and Easy-to-use Home Automation Hub
Home Assistant is 10 years old and an affordable smart home hub launched to celebrate the 10th anniversary. The initial 1000 Home Assistant Green hubs were soon sold out, which proves its popularity. Given that everything you need for Home Assistant is included in a single box, it serves as an entry-level smart hub for consumers who are just starting out in home automation. The hub can be activated by only plugging in the included network and power wires.
What is Home Assistant Green?
Home Assistant Green is a brand new smart home hub sold at $99. Here I am gonna to introduce its hardware and software.
Hardware
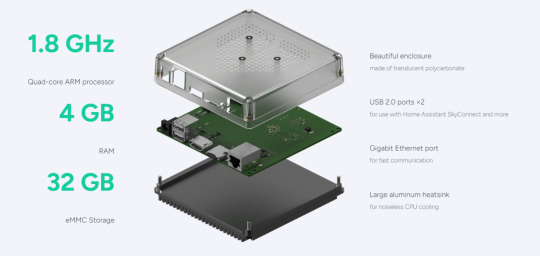
Source: screenshot from home-assistant.io
From the inside, a powerful 1.8 GHz quad-core CPU developed based on RK3566 SoC, which is from a Chinese fabless semiconductor company, to run applications smoothly and quickly. RK3566 SoC is a high-end SoC featuring Arm Cortex-A55 CPU and 1TOPs@INT8 NPU.
What makes it outstanding is 4 GB LPDDR4X of RAM and 32 GB eMMC flash drive of storage, this enables users to running Home Assistant on the device for a long time, and make it simple to get going without the need for manual setup or flashing a memory card from another PC. For individuals who wish to try Home Assistant without having to deal with the technical difficulties of setting up the storage themselves, this is highly beginner-friendly.
Interfaces of Home Assistant Green includes three status LEDs, a 12 V DC power supply (1 A), an optional battery, two USB 2.0 Type-A Host ports for use with Home Assistant SkyConnect and more, an HDMI output port solely for diagnostic purposes, one MicroSD slot for recovery purposes, and a Gigabit Ethernet port for the purpose of greater network reliability and fast communication.
Software
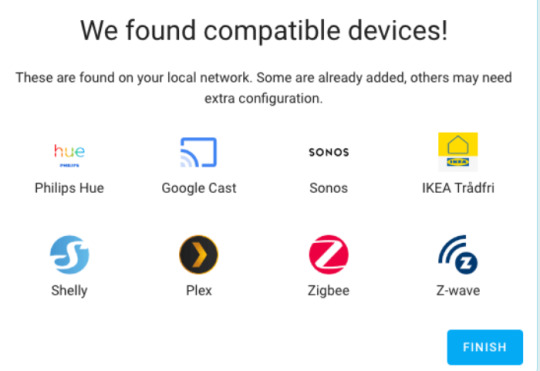
Source: screenshot from home-assistant.io
Home Assistant app is impressively potent, with more than 1000 built-in integrations catering to a diverse range of smart devices and online services. Additionally, a thriving community consistently contributes updates and expansions. In a simple word, everything in your home can be encompassed in Home Assistant.
You can also choose to make Home Assistant work together with you existing Apple HomeKit, Google Home, Samsung SmartThings, and Amazon Alexa. In other words, you can integrate Home Assistant into your existing smart home setup. The Home Assistant’s great compatibility ensures that the transition to using Home Assistant will not disrupt or require a sudden change in the way your household interacts with your smart devices.
As it’s not a typical Home Assistant Zigbee gateway, for users whose places have Zigbee device to connect, you may need extra configuration. For Zigbee, you can add a tiny blue Home Assistant SkyConnect to connect Zigbee devices. It is the easiest way to add Zigbee support to your Home Assistant instance and make it Matter-ready. A future firmware update will bring Thread support, allowing SkyConnect to power Matter and Zigbee networks at the same time. If you need to connect Z-Wave or Bluetooth devices, you also have the flexibility to utilize third-party USB devices to expand Z-Wave or Bluetooth functionality.
Build Privacy-focused Smart Home Easily

Home assistant proposed a “Open Home” vision centered on three core principles: privacy, choice and durability. Privacy means that the devices can operate locally by default, with an opt-in cloud connectivity, putting the control right in the hands of the users. Choice means that connected devices communicate via local APIs, free from vendor restrictions of limiting your access to your data or limiting the interoperability of your devices. Durability means that devices should be designed to provide long-lasting performance and ongoing support, without worry that the support is stopped or functions are crippled.
Easy-to-use for Beginners

Home Assistant Yellow is a smart home hub with with a wide array of features smart home enthusiasts want, and is a good fit for advanced users. However, for those just embarking on their smart home journey, the full spectrum of Home Assistant Yellow's capabilities might be unnecessary and somewhat challenging to initiate.
Setting up Home Assistant Yellow requires users to procure their own Raspberry Pi or similar hardware, and due to global component shortages, the Home Assistant Yellow required Compute Module 4 has become more expensive and less accessible. Consequently, Home Assistant Yellow may no longer be an ideal choice for beginners.
As we previously mentioned, Home Assistant Green offers a remarkably straightforward setup process. To activate it, you need to follow just three simple steps: power, setup, and go!
Final Word
Home Assistant Green stands out as the easiest and most privacy-focused solution for effortless home automation. With its straightforward setup, this platform empowers you to seamlessly manage all your smart devices through a single system, ensuring that your data remains securely stored locally by default. Benefitting from the vibrant Home Assistant ecosystem, this board undergoes continuous enhancements through open-source contributions every month.
Feel free to harness its capabilities for a wide range of applications, including smart home control, home security, energy management, remote operation, and much more. The possibilities are virtually endless.
0 notes
Text
Why Is Data Loss Such a Serious Problem?
Data loss is a serious problem because it can cause long-term damage to individuals. Data loss can result in lost personal images videos, files confidential information, and other important data that can be difficult or impossible to recover. And while we’re talking about a USB file, it requires special software to repair the drive and extract the data.
There are several USB drive data recovery software available, but it is important to make sure you choose the right one for your device.

Here we present an easy-to-use USB data recovery online tool for photos, videos, music, contacts, and other data from a damaged or corrupted situation. The recovery process is fairly straightforward, and users can recover their data in minutes rather than hours. This software can recover lost data from USB drive, important word documents, spreadsheets, PowerPoint slides, pictures, photographs, and other erased data from USB storage media. Visit our website at https://bit.ly/3LLInm1
#restore deleted files from usb drive#recover deleted files usb drive#recover lost data from usb#usb data recovery online#data recovery software#usb data recovery tool
0 notes
Text

🌟 Seagate Expansion 1TB External HDD Portable Hard Drive 🌟
Looking for extra storage space? Don't miss out on this fantastic deal!
💡 Product Details 💡
🔹Digital Storage Capacity: 1 TB
🔹Hard Disk Interface: USB 2.0/3.0
🔹Connectivity Technology: USB
🔹Brand: Seagate
🔹Special Feature: Portable, Data Recovery Service
🔹Hard Disk Form Factor: 2.5 Inches
🔹Hard Disk Description: Mechanical Hard Disk
🔹Compatible Devices: Laptop, Desktop
🔹Installation Type: External Hard Drive
🔹Colour: Black
💡 Features 💡
✅ High Capacity: Store all your important files, documents, photos, and videos with ease.
✅ Portable: Take your data on the go with this sleek and compact hard drive.
✅ Data Recovery Service: Enjoy added peace of mind with Seagate's data recovery service.
✅ Plug and Play: No complicated setup required. Just plug it in and start using it.
✅ Compatibility: Works with laptops and desktops.
This Seagate Expansion 1TB External HDD Portable Hard Drive is in excellent condition and ready to serve your storage needs. It's perfect for backing up your important files or expanding your computer's storage capacity.
🚚 Delivery: We offer island-wide delivery, ensuring the secure packaging of your order.
⚖️ Delivery charges: Calculated in accordance with the weight of your package.
💰 Payment methods: Facilitated through card payments (PayHere), Koko pay, bank transfers, and cash on delivery.
🤖 Pay in 3 interest-free installments with Koko pay, utilizing any debit or credit card.
💳 Installment plans: Spanning up to 12 months, are available through DFCC, Commercial, Sampath, and HNB Credit Cards.
📲 Reach out to us at +94 76 774 9986
👩💻 Connect with our digital assistant via https://wa.me/94767749986/
📍Our location? Discover it here: https://goo.gl/maps/kDtEUL2mbkWe9ngd7 @ Athurugiriya
🛒 Visit our website and make your purchases online: https://www.technodora.lk/
Hurry, this won't last long! Grab it before it's gone. 💼💾🏃♂️
0 notes
Text
Preserving Memories With Best Photo Recovery Services
In the digital age, our precious memories are often captured in the form of digital photographs. However, the unfortunate reality is that data loss can happen to anyone, and when it does, the impact can be devastating. This is where Kim Tian Colour Centre steps in as a savior, offering top-notch Photo Recovery Services Singapore. In this article, we will explore the invaluable role that Kim Tian Colour Centre plays in preserving your cherished photographic memories.
Our photos document our lives, from milestone moments to everyday snapshots. Losing these visual memories due to accidental deletion, hardware failure, or data corruption can be heart-wrenching. This is where professional photo recovery services become essential. These recovery services and Online Digital Printing Service utilize cutting-edge technology and expertise to recover lost or damaged photos, ensuring that your precious memories are not lost forever.

Kim Tian Colour Centre stands out as a premier provider of photo recovery services in Singapore. Here’s why they are the trusted choice for countless individuals and businesses:
Expertise and Experience: With years of experience in data recovery, Kim Tian Colour Centre’s team of experts possesses in-depth knowledge of photo recovery techniques. They have successfully recovered photos from a wide range of storage media.
State-of-the-Art Technology: Kim Tian Colour Centre invests in the latest technology and tools, ensuring that they stay at the forefront of photo recovery advancements. Their cutting-edge equipment enables them to recover photos from various storage devices, including hard drives, SD cards, and USB drives.
Data Privacy and Confidentiality: Kim Tian Colour Centre places a premium on data privacy and confidentiality. They ensure that your recovered photos remain secure and confidential throughout the entire recovery process.
Affordability: Photo recovery doesn’t have to be a costly endeavor. Kim Tian Colour Centre offers competitive pricing, making professional photo recovery accessible to individuals and businesses of all sizes.
Timely Service: They understand the urgency of photo recovery, especially when it involves irreplaceable memories. Kim Tian Colour Centre strives to provide quick turnaround times to reunite you with your lost photos as soon as possible.
Kim Tian Colour Centre’s commitment to photo recovery in Singapore ensures that your precious memories are never lost to the digital abyss. Their expertise, state-of-the-art technology, and dedication to data privacy make them the go-to choice for individuals and businesses alike. In times of despair when your treasured photos are at risk, trust Kim Tian Colour Centre to bring them back to life. With their professional photo recovery services, your memories remain intact, ready to be cherished once more.
0 notes
Text
Which Data Collection and Storage System is right for your needs?

Data Collection and Storage System
An infrastructure that includes tools, procedures, and technologies for compiling, arranging, and safely storing data from various sources is known as a data collection and storage system. Data from sensors, devices, surveys, databases, or external systems must be collected, integrated, and transformed into a standardized format. In order to provide storage for the data that has been gathered and processed, the system makes use of databases, data warehouses, distributed file systems, or cloud storage options. Sensitive data is protected by data security measures, and data management strategies guarantee effective archiving, indexing, and retrieval.
Strategies for backup and disaster recovery are used to reduce the risk of data loss. Users can query, analyse, and visualise data with the help of these systems' frequently available interfaces and tools for data retrieval and analysis.
Data archiving: What is it?
Data archiving is the process of methodically and securely storing data for future access and long-term retention. It entails transferring data to a different storage environment created especially for long-term preservation that is no longer actively used in daily operations. Data archiving's main goal is to maintain the accuracy, usefulness, and accessibility of data over a long period of time, usually for compliance, legal, regulatory, or historical purposes.
What kinds of data storage are there?
Data storage technologies and techniques come in a variety of forms, each with unique features, benefits, and applications. Here are a few typical formats for data storage:
Offline Data Storage: The practice of storing data on tangible media that is not connected to a network or computer system is referred to as offline data storage. By separating the data from potential online threats like malware or hacking, it adds an extra layer of security. External hard drives, USB flash drives, optical discs, tape drives, and even paper-based storage are examples of offline storage devices. For backups, archives, and long-term storage of important or sensitive data, offline data storage is frequently used.
Cold Data Storage: Data that is rarely accessed or used is stored in "cold data storage," as the term suggests. In order to maximise resources, this data is typically stored in a way that is both economical and energy-efficient. Solutions for cold data storage frequently make use of higher-capacity, lower-cost storage media, like tape drives or cloud-based archival storage. While cold storage is appropriate for data that must be kept for compliance or regulatory purposes but does not require immediate accessibility, retrieval times may be longer than for hot data (frequently accessed data).
Secured Data Storage: Secured data storage is any method of storing information that places a high priority on data security and protection. To protect data from unauthorised access, security breaches, or data loss, various security measures must be put in place. This could involve physical security measures, adherence to pertinent data protection laws, access controls, authentication methods, data backup and disaster recovery plans, encryption of stored data, and so on. Data that requires strict confidentiality and integrity, such as sensitive data, personal information, or confidential business information, must be stored securely.
Digital evidence storage: This term specifically refers to the management and storage of digital evidence gathered during inquiries, court cases, or any other circumstance where electronic evidence is relevant. In order to guarantee the consistency, veracity, and usability of the evidence for use in legal or investigative processes, it entails the secure and controlled storage of digital files. Digital evidence storage must take chain of custody, security, and adherence to legal requirements into account.
Long-Term Data Storage: On the other hand, long-term data storage is the practice of keeping data for lengthy periods of time, usually for archival purposes or to satisfy legal and regulatory requirements. It includes the preservation of a variety of data types, such as business records, historical records, research data, and any other data that must be kept for an extended period of time but may not always be used as evidence in court.
Difference between Data Backup and Data Storage
Data backup: To prevent data loss in the event of hardware failures, unintentional deletion, data corruption, or other unforeseen events, data backup entails making copies of current or active data. In the event of a data loss incident, data backup is primarily intended to ensure data recovery and restore operations. The most recent or frequently changing data is typically the focus of backups, which are meant to be easily accessible for speedy restoration.
Data Archive: The long-term storage and preservation of data that is no longer actively used in day-to-day operations but may still be valuable for future reference, compliance, or historical purposes is known as data archiving. Data archiving's main goal is to keep data for longer periods of time while maximizing storage capacity and enabling quick data retrieval when necessary.
How does disaster recovery for offline data work?
The process of data recovery and IT service restoration following a significant data loss event, such as a natural disaster, power outage, cyberattack, or hardware failure, is known as offline data disaster recovery. To restore systems and data to a functional state, it depends on redundant copies of data stored in a secure offsite location or offline backups of data. The company sets up a reliable backup strategy, creating backups of important data frequently and storing them off site on external hard drives, tapes, or other removable storage devices. The company activates its disaster recovery plan in the event of a disaster and gets the offline backups from the offsite storage.
Which Data Collection and Storage System is right for your needs?
1. Purpose and Data Types: Consider the purpose and types of data when gathering and storing information. Are you compiling scientific data, customer data, transactional data, or multimedia files? Various data types may have different needs for archiving, processing, and retrieval.
2. Scalability: Determine your needs for future growth and scalability. Will the amount of your data grow significantly over time? Make sure the system you choose can handle anticipated growth and is simple to scale up to meet growing data requirements.
3. Performance and Accessibility: Choose the level of performance and simplicity you require for data access. While some systems may favour cost-effectiveness over immediate accessibility, others might offer faster retrieval times. Take into account your performance requirements and the frequency of your data access needs.
4. Security and Compliance: Consider your needs in terms of data security and compliance. Make sure the system has strong security features like encryption, access controls, and audit logs if you deal with sensitive or personally identifiable information. Additionally, adherence to pertinent laws and regulations like GDPR and HIPAA should be taken into account.
5. Cost and Budget: Determine your budget and the costs associated with various data storage solutions. While some systems might have high initial or ongoing costs, others might provide more affordable alternatives. Think about the total cost of ownership, which includes the costs for the hardware, software, upkeep, and operations.
6. Backup and Disaster Recovery: Evaluate the system's backup and recovery capabilities. Regular backups, redundancy, and other safeguards must be in place to protect your data from loss or damage.
7. Integration and Compatibility: Consider the compatibility and integration of the data collection and storage system with the workflows, applications, and infrastructure that you already have in place. Implementation can be sped up, and data integration can be assured with the help of compatibility with your existing technology stack.
8. Vendor Support and Reputation: Consider the reputation and dependability of the system vendor. Vendor support. Check out the company's track record of offering dependable support and timely updates, customer testimonials, and references.
About Us: All Pro Solutions
Since 1996, All Pro Solutions, Inc. has been producing a variety of IT equipment, such as printing, publishing, and data archiving systems, as well as producing and offering a variety of digital services, such as disc duplication, document imaging, scanning, and conversion. Since then, All Pro Solutions has established an outstanding reputation for offering products, services, and customer support of the highest calibre.
0 notes
Text
Selecting Data Recovery Services
If you work around computers and digital storage devices for long enough, you will probably need the services of a data recovery company at one point. These are companies that specialize in retrieving lost or deleted files from damaged or corrupted hardware devices, such as hard drives, SSDs, flash drives, mobile phones, and even RAID arrays. While there are many data recovery companies available, not all of them are created equal. Some offer better guarantees and prices than others, while some have more experience and expertise in a variety of data recovery services.
There are a few things you should look for when selecting a recovery service, such as how much they charge for their services, the likelihood of success, and whether or not they offer a warranty. You should also consider whether or not they can recover the data you need, and what kind of turnaround time to expect. Some companies provide a rapid turnaround, while others take up to two weeks or longer.
Choosing the right data recovery company is important for your business, and you can find a good one by doing some research online. The best ones will have a good reputation in the industry and will offer a money-back guarantee for failed recoveries. They should also have the ability to handle all types of hard drive and external storage devices, including SSDs and USB drives.
DataTech Labs offers a fast, reliable, and affordable data recovery service for both individuals and businesses. Their certified engineers have years of experience in recovering files from both traditional and solid-state drives. Their facility is equipped with a cleanroom, so they can safely open and repair mechanically damaged devices without voiding the manufacturer’s warranty. They can also restore data from cameras, drones, and other recording devices.
If you have a device that has been damaged or compromised, you should disconnect power from it immediately. This will prevent any more damage from being done to the hardware or overwriting your existing files. You should also avoid running software on the device, as this can cause additional issues and could ruin your chances of a successful recovery.
Ace Data Recovery has been in the data recovery business for more than 30 years, and their technicians can recover files from almost any type of damaged or malfunctioning storage device. Their customers include many computer repair businesses and managed IT services providers, who recommend them to their clients. Their free evaluation and no-data-no-charge policy make them a great choice for those who need help with recovering their important information.
Secure Data has a 96 percent success rate and SSAE 16 Type II certification, making them a top data recovery service for large enterprises. They can also retrieve deleted files from action cameras, drones, and other recorders. They have the experience and expertise to recover data from both mechanically damaged and logically corrupted hard drives and other storage devices, such as SSDs, tapes, and SAN systems.
1 note
·
View note
Text
AddROM FRP Bypass - Unlock Your Device Hassle-Free
In today's digital age, smartphones have become integral to our lives, holding our most personal information and providing access to various online services. To safeguard the privacy and security of users, smartphone manufacturers introduced the Factory Reset Protection (FRP) lock. While FRP lock offers security, it can also cause inconvenience for users who forget their Google account credentials after a factory reset or purchase a second-hand device. Fortunately, AddROM FRP Bypass is here to rescue you from this predicament, allowing you to regain control of your device without any hassles.

The Basic Introduction For AddROM FRP Bypass
The FRP lock, also known as Google Account Verification, is a security feature introduced by Google to prevent unauthorized access to a device after it has been reset to factory settings. When a device with FRP lock is reset, it prompts the user to enter the Google account credentials that were previously associated with the device. This security measure ensures that even if your device falls into the wrong hands, the person won't be able to use it without your Google account information.
What is FRP Lock?
FRP lock is a security feature embedded in Android devices running Android 5.1 Lollipop or higher. It requires the user to enter the Google account credentials associated with the device after a factory reset. The purpose of this lock is to deter theft and protect user data by preventing unauthorized access to the device.
Challenges Faced with FRP Lock
While FRP lock enhances device security, it can pose challenges for users in certain situations. Forgetting Google account credentials, purchasing a second-hand device with a locked FRP, or encountering issues with account recovery can all lead to frustration and a lack of device access. Thankfully, tools like AddROM FRP Bypass offer a solution to these challenges.
What is AddROM FRP Bypass?
AddROM FRP Bypass is a powerful tool designed to bypass the FRP lock on Android devices, allowing users to regain access to their smartphones or tablets. This tool is widely used by technicians and individuals alike to unlock devices and remove the FRP lock, enabling users to set up their devices without needing Google account credentials.
How Does AddROM FRP Bypass Work?
AddROM FRP Bypass utilizes advanced techniques to bypass the FRP lock on Android devices. It exploits vulnerabilities in the device's software to temporarily turn off the FRP lock verification process. This enables users to set up their devices, install and use apps without restrictions.
Benefits of AddROM FRP Bypass
User-Friendly: AddROM FRP Bypass has a simple and intuitive interface, making it easy for technicians and beginners.
Time-Saving: By bypassing the FRP lock, AddROM saves users valuable time, eliminating the need for complex account recovery procedures.
Compatibility: AddROM Bypass is compatible with a wide range of Android devices, ensuring that users can unlock various smartphones and tablets.
Security: AddROM takes the necessary precautions to ensure the security of your device during the bypass process, protecting your data and privacy.
Step-by-Step Guide for Using AddROM FRP Bypass
Follow these steps to unlock your device using AddROM FRP Bypass,
Step 1: Backup Data - Before initiating the bypass process, it is essential to back up your device's data to prevent any potential loss.
Step 2: Download AddROM FRP Bypass - Visit the official website of AddROM and download the latest version of the FRP bypass tool.
Step 3: Enable USB Debugging - On your Android device, go to "Settings," then "Developer Options," and enable USB debugging mode.
Step 4: Connect Device to PC - Connect your device using a USB cable.
Step 5: Launch AddROM FRP Bypass - Launch the AddROM FRP Bypass tool on your PC.
Step 6: Follow On-Screen Instructions - The tool will guide you through the bypass process with detailed on-screen instructions.
Step 7: Restart Device - After the bypass process, restart your device.
Step 8: Set Up Your Device - Now, you can set up your device without encountering the FRP lock.
Precautions to Take When Using AddROM FRP Bypass
While AddROM FRP Bypass is a reliable tool, it is essential to take certain precautions when using it,
To avoid potential security risks, you must download the tool from the official AddROM website.
Always back up your device's data before initiating the bypass process to prevent any loss of important information.
Follow the instructions provided by AddROM FRP Bypass carefully to ensure a successful bypass and setup.
Use AddROM Bypass responsibly and only on devices you own or have legal authorization to unlock.
Conclusion
AddROM FRP Bypass is a game-changer when it comes to unlocking Android devices with FRP lock. Its user-friendly interface, compatibility with various devices, and secure bypass process offer a hassle-free solution for those facing FRP lock-related challenges. Users can regain control of their devices by following the step-by-step guide, taking necessary precautions, and enjoying a seamless setup experience.
FAQs
Is AddROM FRP Bypass compatible with all Android devices?
Yes, AddROM Bypass is compatible with a wide range of Android devices running Android 5.1 Lollipop or higher.
Can I use AddROM FRP Bypass on a device that doesn't belong to me?
No, it is important to use AddROM Bypass only on devices you own or has legal authorization to unlock.
Will use AddROM FRP Bypass void my device's warranty?
The use of AddROM Bypass may void your device's warranty. It is recommended to check your device manufacturer's warranty policy before using the tool.
Is it necessary to back up my device before using AddROM FRP Bypass?
Yes, backing up your device's data before initiating the bypass process is highly recommended to avoid any potential loss.
Where can I download AddROM FRP Bypass?
You can download AddROM Bypass from the official AddROM website. You must download it from a trusted source to avoid any security risks.
0 notes
Text
The Best Data recovery in Dubai by Atdoorstep
Data loss could happen anytime and to any person at any moment. Whatever you do, no matter how cautious you are when using your devices, accidents could occur and cause loss of data. It is essential to have a solution for Best data recovery Dubai installed so that you can retrieve the data you lost as fast as possible.
There are many reasons that data loss may be a problem. The most frequent reason is due to human error. If you accidentally delete an entire document or overwrite the file, errors occur. Another reason that is commonly cited for data loss is a hardware malfunction. This could be due to various factors like power surges or physically damaged devices or software malfunction.

In certain instances, it is possible that data loss occurs because of malicious intention.
Whatever the reason behind the loss of data, it’s crucial to have a trustworthy data recovery program installed so that you can retrieve lost files and go back to work as fast as possible.
Data Recovery can recover lost data
Data Recovery is a powerful software for data recovery that can retrieve deleted information from computers. It is able to retrieve lost data from hard drives, USB drives, memory cards as well as many other devices for storage. It is also able to recover deleted data from email accounts and social media accounts as well as other online services.
Through Data Recovery it is possible to retrieve deleted information from your computer with only one or two clicks. You don’t have to be concerned about losing important data any longer. Thanks to Atdoorstep.

Data Recovery, you will be able to get lost data back within a matter of minutes.
Data Recovery is simple to make use of
If you’re in search of an easy-to-use solution for data recovery,
Data Recovery is an excellent choice. It’s designed to make use of for easy and has a user-friendly interface that makes it simple to retrieve deleted or lost files. It’s also compatible with Windows and Mac computer systems.
Data Recovery is also an efficient solution, with an efficiency rate of more than 98 percent. This means you’re more likely to to successfully retrieve your deleted or lost files with Data Recovery.
In addition, Data Recovery offers no-cost technical support in the event you require assistance using the program. They also offer a money-back assurance if you aren’t satisfied with the outcome. Contact us at +97145864033.
0 notes
Text
A Beginner's Guide to Installing Windows Operating System
Installing another operating system can seem daunting, yet with the right information and tools, the process can be straightforward and sans stress. In this article, we'll take you through the steps to install Windows operating system on your PC.
Before we start, make sure you have the accompanying items:
A Windows installation disk or USB drive
A PC that meets the base system requirements for Windows
An item key for your version of Windows
Step 1: Backup Your Data
Before you start the installation process, make sure to back up any important data on your PC to an external hard drive or distributed storage service. This is important because the installation process will erase all of the data on your PC's hard drive.
Step 2: Insert Installation Media
Insert the installation disk or USB crash into your PC and restart it. At the point when your PC restarts, it should automatically boot from the installation media. In the event that it does not, you may have to change the boot request in the BIOS settings. Consult your PC's manual or search online for instructions on the most proficient method to do this.
Step 3: Choose Language and Different Preferences
After the installation media has loaded, you'll be asked to choose your language and different preferences, such as time region and keyboard layout.
Step 4: Install Windows
Click on the "Install Now" button to start the installation process. Follow the prompts to accept the license agreement and choose your installation type. You can choose to play out a clean install, which will erase all of the data on your PC's hard drive, or a custom install, which will allow you to choose which files and settings to keep.
Step 5: Enter Item Key
When incited, enter your item key for Windows. This key should be incorporated with your installation media or gave to you separately.
Step 6: Choose Partition and Format Hard Drive
Then, you'll have to choose which partition on your hard drive to install Windows on. Assuming your PC just has one hard drive, you'll typically choose "Drive 0" or "Disk 0". You'll also have to choose whether to format the partition, which will erase all of the data on it. In the event that you're playing out a clean install, you should choose to format the partition.
Step 7: Install Windows and Drivers
After you've selected the partition and formatting options, Windows will start the installation process. This can take anywhere from 10 minutes to 60 minutes, contingent upon your PC's speed. When the installation is finished, you'll have to install any necessary drivers for your PC's hardware, such as your graphics card or sound card.
Step 8: Install Updates and Programs
After you've installed Windows and your hardware drivers, it's smart to install any necessary updates and programs, such as antivirus software or Microsoft Office. Get More Info insert your windows installation or recovery media
In conclusion, installing Windows operating system can be a straightforward process on the off chance that you follow the steps framed in this article. Recollect to backup your data prior to starting the installation process and choose the right installation type for your needs. With just enough patience and expertise, you'll be ready to go with your new operating system in a matter of seconds.
0 notes
Text
What is UPN (User Principal Name)?
As the name proposes, Pen Drive Data Recovery Chief Name (UPN) is the name of Office 365 client. This is accessible in the organization of email address. Each new client gets an UPN, which is likewise their dynamic registry ID (essential email ID). For instance, a client named Alice turns into a client of Office 365 space "tastyicecream" and both her essential email address and UPN will be [email protected].
Presently, in the event that she moves to another space called info@pendrivedatarecovery, her UPN will be [email protected].
Notwithstanding, her essential email address will be something very similar: [email protected].
Clients should recollect that in the event of space change, the UPN of a client will change however not their essential email address. Thus, a client's ongoing UPN and essential email address can be something similar or unique.
Parts of Office 365 UPN
A standard UPN comprises of three sections:
Area name (otherwise called UPN postfix)
To expand, we will take the case of [email protected]. In this UPN, "Alice" is the username, "@" is separator and "tastyicecream.onmicrosoft.com" is the area name.
What Occurs In the event that Office 365 Clients have Different Essential Email and UPN
As it has been examined before, there can be circumstances when the login UPN and essential email address doesn't coordinate. All things considered, clients might confront challenges getting to various Office 365 applications. Here, we will give a rundown of circumstances when the disarray with respect to UPN might happen:
Office membership based enactment
- The end client needs to give their UPN, and NOT their email address for confirmation.
Skype for Business
- To verify, UPN must be placed.
- However the default Meeting Commencement Convention (Taste) address in MS Office 365 is UPN, clients can change this physically.
Office 365 Online interface
- UPN ought to be utilized to verify instead of email address.
Trade ActiveSync (EAS)
- For this situation, likewise, clients should utilize their UPN. EAS profile's programmed setup expects clients to include on a subsequent screen.
Office Portable Applications
- The end-client ought to give their UPN instead of their email address to get to versatile uses of Office 365.
Instructions to Confirm or Alter Office 365 client UPN
Microsoft Office 365
To Check UPN address present in Office 365 (appointed to each new client naturally), go to Microsoft 365 administrator community. Then click on Clients > Dynamic clients.
Investigate
In the event that Office 365 clients deal with the issue when UPN contains domain.onmicrosoft.com design instead of your space's postfixes (for example my-organization.com), they need to alter UPN address. USB Drive Data Recovery this, take the assistance of Sky blue Dynamic Catalog Module for Windows PowerShell.
To import Purplish blue Dynamic Catalog Module for your PowerShell:
import-module MSOnline
To associate with Office 365 by running this cmdlet:
$msolcred = get-qualification
interface msolservice - qualification $msolcred
To change the UPN address of the client:
Set-MsolUserPrincipalName - UserPrincipalName - NewUserPrincipalName
Microsoft Trade Server
In Return, follow these moves toward check or change an UPN.
1. Send off Dynamic Catalog Clients and PCs on the area regulator (DC) machine. Right-click on the mane of any clients and snap on Properties.
#Pen Drive Data Recovery#USB Drive Data Recovery#Pen Drive Recovery#USB Drive Recovery#Pen Drive Recovery software#USB Drive Recovery software#Pen Drive Data Recovery software#USB Drive Data Recovery software
0 notes