#since the monitor comes with a cell phone that is constantly transmitting data to the place. which they said they'll call you
Text


sneepy cozy....
#cats#(medical stuff mention for tags)#poasting confortable image of boye for peace and serenity and such forthe#I have little weird episodes sometimes where I get shaky (but like violently like 'would spill a drink if you were holding it beacuse#your hands are moving so much' type shaky) and weird and sick feeling but usually it passes in an hour or less. but last night I just#literally couldnt sleep I was shaking so much and my heartrate was up a ton and wouldn't go down even after like 6 hours plus super nausea#so I went to the hospital and now shall wear a heart monitor for a week. which hopefully it's just some weird drastic low blood sugar#event or something and there's nothing actually going on. ekg + ct scan for blod clots + virus panel + almost all of the blood work seems#normal so... aa.......#Though me being so privacy focused hrggh... I basically have a constantly bluetooth connected device around me#since the monitor comes with a cell phone that is constantly transmitting data to the place. which they said they'll call you#if they see anything weird which is also scary. random phone calls... but definitely better than letting an issue go unadressed lol#the phone is also not meant to be more than 10 feet away from the monitor at any time so I put on this old tactical fishing#vest thing thats like navy green with 100 pockets and im just using one of the giant pocketson the side as a phone holder#my enormous silly vest just to keep one little phone#ANYWAY... because I got up early the morning before and didn't sleep at all and spent nearly all day in waiting rooms and such#I have been awake for like 32 hours striaght. which I'm sure also does not help with an elevated heartrate lol#feeling shrimp emotions or whatever people talk about unlocking at a certain level of stress and sleep deprivation#and also no food or water. after a while they brought me like 3 saltines and some ice water but I basically also haven't eaten since 3am#last night and it's 2pm now..#thus............ bapy............. baby boye....... he will help ease all ailments with his baby powers...#And no I dont drink energy drinks or anything with caffiene really I'm afraid of all substances on the planet essentially#My body just likes to become shaky and weird randomly even when I'm not conciously anxious about anything/have had no caffiene/etc#and I guess I'm always more nervous about getting anything heart related checked out because of my arm/shoulder/chest area injury stuff#... i literally have constant chest pain all the time. it moves around but i nearly always have some sort of pain or pressure in my chest#so when people are like 'oh well a little weird heartrate is fine but watch out if you have pain!' it's like... i always do lol.. how am I#supposed to tell the Bad Pain apart from the Always Pain when the descriptions of Bad Pain are very very similar#AAAANYway.... hrghh... i wanted to be very productive and finally post drafts and wrok on things today. but alas..#I can at least post small image of soft boye.. though he recently got into stuff in the bathroom whilst left#alone and knocked things into the toilet.. So perhaps not an innocent and NICE boy.. but still.. a soft one .. beautfile....
21 notes
·
View notes
Text
Why is a Bluetooth Beacon so Appealing to Marketers?
What is a Bluetooth beacon?
A beacon could be defined as a device that transmits packets of data using the wireless technology Bluetooth, it is powered by batteries. “Beacon” like its name states, provides guidance. These devices are used to transmit data with the use of (BLE) Bluetooth Low Energy signals. Any mobile phone that possesses the function of Bluetooth can be used to detect and display these devices around us. One of the most useful service beacons provides is that it could be used for advertising in places such as, shopping malls, stores, parks, events and any venue that consists of people.
It is necessary to have a device that is compatible with the beacon in order to be used with it. Bluetooth beacon transmitters are available in various forms and factors such as; USB Sticks, small coin cell devices, Bluetooth 4.0 supported USB Dongles, etc.
Which devices support Bluetooth beacon?
The number of Bluetooth beacon supported devices was limited in the past. However, almost every smartphone built in the last decade has the compatibility to be used with Bluetooth beacon. In order for a device to support Bluetooth beacon, it is necessary for the device to have Bluetooth connectivity and Bluetooth low energy connectivity.
A number of devices support Bluetooth beacon, iPhone 4 or newer, iPad, Android phones/tablets with Android 4.3 or later version.
What’s the difference between iBeacon, Eddystone and Bluetooth beacon?
iBeacon
It was introduced by Apple in 2013. Many experts believe it is developed to help the retail industry by simplifying the payment methods and enabling the use of on-site offers. McDonald’s has used iBeacon devices to give special offers to customers in its outlets.
Different hardware iBeacons are available in the market ranging from $5 to $30. All of these iBeacons have varying default settings for their iBeacon advertisement and default transmit power frequency. iBeacons have different advertising frequencies, some may operate at 1Hz while many can be as fast as 10 Hz. One well-reported such software quirk exists on Android with support of Android 4.4 or later.
Eddystone
Eddystone is developed by Google. It is capable of supporting three types of packets, Eddystone-URL, Eddystone-UID, and Eddystone-TLM, while iBeacon does not support these packets. It is said that Eddystone-UID is very similar to Apple’s iBeacon. However, it supports additional telemetry data with Eddystone-TLM. The telemetry information is sent along with the UID-data. Displayed beacon information includes beacon temperature, battery voltage, number of packets sent since last boot and beacon up-time.
Using this protocol, Google developed Google nearby that allowed Android users to receive beacon notifications without installing any third-party application. Google nearby was stopped by Android on Dec 6, 2018.
Bluetooth Beacons
Bluetooth beacons are used to transmit data to nearby devices. This technology enables devices to perform actions when close to a beacon supported device. Eddystone by Google and iBeacon by Apple are Bluetooth beacon platforms.
The structure of a Bluetooth beacon
BLE data transfer is one-way communication.
Let’s take an example of a BLE Beacon trying to communicate with a mobile phone that is available within its range. A Bluetooth low energy beacon is used to transfer data in the form of data packets at regular intervals.
These data packets are scanned/detected by pre-installed services or any third-party applications on the mobile phone. This leads to action such as promoting an app.
To behave energy efficient and provide much better data transfer speed, the entire communication system consists of 40 Frequency channels with the separation of 2Mhz. 3 of these are considered primary channels while the remaining 37 are said to be secondary channels. This Bluetooth communication begins with the 3 primary channels and then moves on to the secondary channels.
What does a Bluetooth beacon transmit?
Bluetooth beacons can be used to send any packet of information that has a universally unique identifier (UUID). This UUID is used to activate events specific to the beacon.
In Apple’s iBeacon the UUID will be identified by an application on the user device that will activate the event. This event is totally manageable by application developers. However, with a UID Based system, the user’s device must connect to any online server which is capable of understanding the beacons UUID.
Why is a beacon so appealing to marketers?
In the present time, most of the people are frequent smartphone users. Beacons are proven to be quite useful in order to engage with consumers if they are within the range of beacon.
Marketers can use a beacon to track the movements of clients/customers that are available within the spot, they can even assess how long a consumer stays in a store and they are able to send the specified messages on the basis of location.
Beacons are quite similar to analytics tools & website tracking that are used by companies to monitor the pathways that clients take to reach a purchase decision. Companies can use the specific location of clients in a store as the beacon picks up.
Bluetooth signals from their smartphone can be used to deliver personalized or promotional messages. If a retailer uses any branded mobile application. It makes sending push notifications even easier to highlight any content such as discounts or sales.
What is a beacon used for?
Beacons can be used for numerous purposes. Such as to provide important information, to check the status of an airport, etc.
It is also used on vehicles to attract the attention of surrounding pedestrians and other vehicles. Emergency vehicles, ambulances, cop cars, etc. use the vehicular beacons.
It can be used for navigation to help navigators find their destination. Type of navigational beacons is radio beacons, radar reflectors, visual and sonic signals. Handheld beacons are also provided in aircraft marshaling and are used to deliver instructions to the crew in the aircraft.
It can be used for defensive communications as well in such a way as a fire is lit on the top of a mountain or any high place. Its work is similar to a lighthouse that is used for navigation at the sea.
Beacons basically act as a bonfire and are used to celebrate any event or mark any occasion and therefore have many other uses.
How to activate, install and maintain a Bluetooth beacon?
Beacon Activation
The activation process varies on the type of beacons you are using. Some beacons require batteries whereas some beacons come with inbuilt batteries.
Depending on the beacon, batteries are needed to be put in beacon and then you need to press and hold the power button. After following this process, the beacon will be activated and it will be ready to transmit data. Once activated, it will start working and transmitting to the smartphones within its range.

Beacon Installation
It takes several test runs with real customers before a retailer could establish beacon connectivity to its best.
Plot the floor plan
Start from figuring out the place where do you need the beacon to be placed. An ideal plan should be to cover the entire floor with minimum devices without forming a dead zone in between.
2. Install the beacons
Once you have arranged beacons with your floor plan, install beacons on all of those locations and invite a few people you know with their mobile phones in order for them to check beacons for any dead zone and if any dead zone is found. You can replot the floor plan in accordance to the fix.
3. Run the Trials
Your customers’ mobile phones will start detecting the beacon if they have a Bluetooth service. If you wish to see how effective they are on your crowd, you can run a few trials such as running exclusive beacon offers.
Beacon Maintenance
Beacons are well known for their cost-efficient maintenance costs. A pair of AA batteries can be used to constantly keep running a beacon for up to 5 years and Bluetooth Low Energy (BLE) plays an important role in this. Five years of battery life might be impossible to be achieved in real but if compared with any other battery-powered technology, even 2 years of a lifetime sounds good enough for Beacons. The frequency of signals affects battery life. The lower the frequency, the less battery life gets consumed.
Physical inspection, firmware updates, and battery monitoring also require persistent care and checkup.
How do end-users interact with a beacon?
When any beacon is activated to transmit the specified data, it broadcasts them to all the Bluetooth enabled mobile-phones available within its range. iPhone requires a third-party application that supports beacon services meanwhile Android users can instantly scan and start receiving the broadcast on their phone. Whoever connects with the beacon can start receiving the specified information that beacon has been provided with to broadcast. It can be any type of advertisement, URL, etc. It can appear as a notification to the users and after users click on it, users will be taken to the campaign.
These are some ways to make users interact with your broadcast:
Relevant Videos
The use of relevant videos in your broadcast can appear to be very appealing to the users and can leave a good impact on them.
Call to action
Using this feature, you can provide users any email, phone number, email or URL to any website where they will be redirected for further interaction.
How to buy a Bluetooth beacon?
There are a number of things that need to be considered in order to buy the beacon of your requirement,
Battery Life
Transmission Range
Indoor Vs Outdoor
Protocols Supported (iBeacon or Eddystone)
Budget
Portability
Beacon Platform
Battery Life
Battery life plays an important role in the Bluetooth beacons:
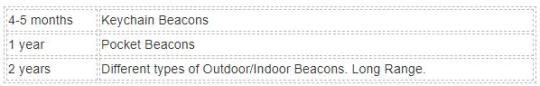
Transmission Range
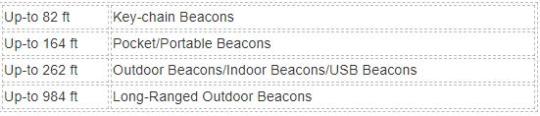
Based on the usage
Indoor Beacons
Helping guests to check-in the hotel
Offering free Wi-Fi in certain locations
Navigating their way into different stores
Confirming the availability of a product by the use of it.
Outdoor Beacons
Outside stores.
At bus stops.
Sports venues or any relevant place.
Beacon Application
Besides this, you need a beacon compatible app that is downloadable on the user’s smartphone in order for them to connect with the beacon and receive the specified content.
There are a number of apps available i.e. NearBee. And if you wish to develop your own application, that’s a possibility too using App building platforms.
Based on budget
The iBeacon/Eddystone beacon price mentioned below is for a pack of 3

Based on Protocol of beacons
All Mokosmart beacons support both iBeacon and Eddystone protocols. This means you don’t have to buy iBeacons or buy Eddystone beacons separately. The minimum OS version on Android should be 4.3, iOS 7.1, Windows 7, and Mac OS X 1.
There is a number of beacon manufacturers in the market but Mokosmart makes sure you get what you desire and we are willing to provide you with beacons made of best material. We believe in thinking ahead for the betterment of our client’s future and we wish for you to join us on our path to success and help us develop a better community that can improve our technology and methods.
The timeline of beacon technology
Beacons are easy to use, cheap and can be executed on batteries. A beacon has been able to connect the physical world with digital due to a beacon being able to inform any mobile phone of their location and context.
As we know Bluetooth is necessary for the use of beacon technology, Bluetooth has evolved and come a long way since it was first introduced in 1989 by Dr. Nils Rydbeck CTO.
Different versions of Bluetooth technology have appeared in the market from time to time, there was a time when Bluetooth technology had the maximum transfer rate of 700 Kbit/s which was called Bluetooth 1.2.
The release of Bluetooth 2.0 as a successor of Bluetooth 1.2, increased the transfer speed up to 3Mbit/s. Bluetooth 2.1 was introduced with improved connection speed and better security. Bluetooth 3.0 was quite a big step in the technology of Bluetooth as it was capable of handling data transfer speed up to 24Mbit/s. In 2010, Blue tooth 4.0 was released that possessed the feature of being power efficient.
Bluetooth is basically used as a two-way communication but with the help of Bluetooth 4.0 that isn’t the only case anymore, Bluetooth now can be used as one-way communication and it does not require a paired connection like previous Bluetooth supported devices.
The future and trend of Bluetooth beacon
The global beacon market is more likely to evolve in the future as it has in the past.
According to a report by several business insights;
The market of beacon technology is likely to expand at a good rate due to the impact of advancements in technological industries. The increasing number of Bluetooth devices has played a major role in the growth of the global beacon market. According to a report by Bluetooth SIG, around 4Bn Bluetooth devices were manufactured in 2018.
The growth of artificial intelligence (AI) concepts has created numerous opportunities for the growth of the global beacon market. Various companies have stepped in to contribute to the assistance of the growth of global beacon technology.
Link in https://www.mokosmart.com/bluetooth-beacons/ and contact us for more info about Bluetooth beacon!
0 notes
Text
How To Tell If Your Phone Is Being Tapped, Tracked And Monitored?

There are several things or tricks that suggest your phone is being tapped, tracked or being monitored in some way. These signs could be really minor to judge but when you know what to look out for, they can also be glaring.
Unusual sounds during calls- If you hear some clicking sounds, static or distant voices coming through your phone during conversations it could be a sign that you’re being snooped on. This thing is not normal for today’s phones on digital networks. It’s a thing that is associated with old-style analogue networks.
This is not the best of signs when taken alone, though, since echoes, static and clicking can also be caused by random interference or a bad connection.
High-pitched humming is an even greater indication.
You can check for sounds that your ear cannot pick up by using a sound-band-width sensor on a low frequency. If the indicator pops up several times per minute, your phone may very well be tapped.
Use your phone around other electronic devices- If you suspect that there might be a tap on your phone, walk over to a radio or television during your next phone call.
You should also look for distortion when you are not on actively using the phone. An active wireless phone signal could disrupt the transmission of data even without additional software or hardware being installed on your phone, but an inactive signal should not.
Some bugs and taps use frequencies close to the FM radio band, so if your radio squeals when set to mono and dialled into the far end of the band, one of these devices might be in use.
Taps can interfere with TV broadcast frequencies on UHF(Ultra High Frequencies) channels. Use a TV with an antenna to check the room for interference.
Decreased battery capacity- Another indication of a bugged cell phone is reduced battery performance. If a mobile phone is tapped it is recording your activities and transmitting them to a third part. This leaves a footprint in the form of increased battery usage and as a result the battery loses life faster. A tapped cell phone can also be constantly recording conversations in the room, even when the phone appears to be idle, and as a result it will chew through battery life.
Phone shows activity when not in use- Is your phone making noises or lighting up its screen when not it use? Does is also reboot for no reason at all? If so it’s possible that someone has remote access to your device.
If your phone lights up, shuts down, starts up or begins to install an app without you doing anything, there might be someone hacking into your phone and controlling it through a tap.
On the other hand, any of this could happen if there is random interference during the transmission of data.
Phone takes a long time to shut down- Before a smart phone shuts down it must complete any tasks that are procession. If your phone is transmitting data to someone it will have to complete the process before it shouts down. As a result if a phone takes longer to turn off especially after a call, text, email or web browsing it could be sending information to a third party.
Pay close attention to determine if your mobile takes longer to shut down than usual or if the backlight remains on even when you shut it down.
Increased data usage- Some of the less reliable spy apps use extra data to send the information collected from your phone, so look out for any un-explained increase in your monthly data usage. The best spy software programs data usage has been reduced and will be almost impossible to spot but the poor programs will show significant data use.
Read the full article
0 notes
Text
Personalized Mobile Progression
Personalized Mobile Progression
Mobile sector has actually viewed incredible development in the final handful of years along with the introduction of manies thousand of foreign advancement centers. Listed here personalized progression jobs are actually managed through creators that possess years of expertise in making and also establishing mobile phone apps to comply with the min demands of a service.
Along with the amount of consumers accessing the Internet via their mobile phone phones, the necessities for such custom-made apps has actually raised notably. It is actually no shock that profession and also trade titans such as ebay.com, Amazon and so on released their very own mobile phone functions numerous years back. Custom Software Development Company Florida
Along with the advancement of 3G and also wise phones, bulk of organisations are actually appearing at mobile phone advancement to market their services. The top quality that has actually produced this kind of progression such an appealing proposal is actually the simple fact that mobiles are actually zero much longer limited as interaction unit simply, however have actually come to be a comprehensive mixeds media tool.
Important Tips for Custom Mobile Development
Make sure that your use is actually light in weight as this is actually much easier for customers to install and also utilize. Inquire your programmers certainly not to utilize excessive resources and also factors in your application. Portable unit consumers like straightforward applications, which could be worked utilizing a handful of switches.
Launch frequent spots and also updates and also remain in sync along with the most recent equipment growth in the field. This will definitely certainly not just improve your customer foundation yet likewise your reliability in the marketplace.
Carry out discountenance overdesign, as this is just one of the primary oversights, services dedicate when it concerns customized progression of their apps for different portable gadgets. Your request requires to become straightforward and also there is actually no damage in attracting creativity coming from productive treatments Miami.
Contemplate the function in your thoughts prior to coming close to the creators. This is vital as you recognize your organisation much better than any person else, as well as recognize your assumptions coming from the application Florida.
To possess an efficient advertising project, pick multi-platform mobile phone growth, which will definitely make certain that you target consumers utilizing primary os Jacksonville.
Custom-made Mobile Development for Businesses
Everybody possesses various criteria for his or even her mobile phone. It is actually virtually inconceivable for mobile phone advancement firms to comply with all demands along with their nonpayment functions.
The intro of Smartphones such as Blackberry and also apple iphone has actually extremely improved the personalized mobile phone progression market. They progressively have actually begun attempting their good luck at bring in customized mobile phone applications for significant services. Along with expanding attraction of customized mobile phone application happens improving conclusion amongst the little and also mid-level organizations to maintain in the market.
Maintaining an eye on the increasing requirement for individualized mobile phone functions for services, mobile phone firms are actually pressuring even more on this advancement. Various organisation homes call their mobile phone supplier in purchase to develop a certain kind of mobile phone app. The conveniences of customized mobile phone app growth are actually massive; nevertheless, this is actually one of the simple factors that custom-made mobile phone advancement for organisation is actually receiving therefore a lot recognition.
Threats linked with customized mobile phone growth:
Regularly tally the performance of function along with ROI (Return On Investment). If ROI is actually more than the expenditure, the application costs getting, else certainly not.
Regularly focus on the system software of your mobile phone just before acquiring a custom-made app. If the application is actually inappropriate along with the Operating System, your assets will certainly be actually totally lost.
You constantly must note the intended usage of the function. If the application complies with each one of all of them, and also certainly not a number of all of them, merely after that you need to opt for acquiring it.
Along with mobile phone phones, consistently happens the concern of mind area. Devoting very a lot room for the app would certainly not be actually a practical tip for any sort of company.
Mobile Development for Android
The dawn of mobile phone phones have actually created our lifestyle much easier than in the past as well as many thanks to the improved variations like that of apple iphone, contact display phones, Smartphones and so on that numerous mobile phone modern technologies are actually put together right into one unit. Mobile Development Orlando for Android is actually mostly located on Java.
Developers, that really want to remain in this hectic as well as very competitive market, have to accept Android Mobile Development Orlando. Much, even more than 50000 Android mobile phone functions have actually currently been actually created for Android powered mobile phone phones.
There are actually 3 models of Android os accessible for various mobile phone apps:
It is actually a closed up exclusive mobile phone advancement system. A brand new layout foreign language Metro permits mobile phone designers to include the operating device along with 3rd celebration and also various other Microsoft companies.
Mobile phone growth has actually come to be one of the very most very competitive regions for the programmers. Around the planet, mobile phone programmers make use of mobile phone systems for the advancement of some remarkable applications.
Apple iphone - The i-generation's progression system, iphone is actually made use of through mobile phone creators to generate requests for the apples iphone, ipad tablets and also Apple TELEVISION. It is actually only utilized for apple iphone growth, as Apple carries out certainly not accredit its own iphone for installment on 3rd party equipment. This system is actually stemmed from Mac Operating System X and also is actually consequently a Unix-like system software naturally Orlando.
- Easier information transactions throughout various mobile phone systems is among the major conveniences of Android. There are actually GSM, Bluetooth, UMTS, EDGE, EV-DO, CDMA, as well as Wi-Fi solutions in Android to transmit information.
- Android made it possible for phones possess a broad amount of functions including Touchscreen, Video Camera, accelerometer as well as magnetometer, as well as GPS.
- All the Android phones possess IPC or even Interprocess interaction information passing location.
- Android powered phones provide different collections for 2D and also 3D graphics. There are actually likewise an amount of collections for video clip, sound, and also graphics.
- There is actually SQLite for holding information.
- There are actually lots of non-code application resources including design, picture as well as chain data, which must be actually device-specific. Designers possess to develop distinct format documents for a variety of monitor measurements.
- Each of these components should be actually switched on individually.
- Android Apps have to be actually combined along with much more than one function component. Commonly, an Android function features several solutions, tasks, program recipients, and also information suppliers.
- Each of these parts ought to conduct distinctive duties.
- Files ought to proclaim the parts together with their criteria. If the part needs a distinct components arrangement, it must be actually discussed in the equivalent report.
- Benefits of mobile phone growth for Android: There is actually a trigger, contacted 'User-friendliness'. The mobile phone innovation that strikes the trigger, are going to succeed royalty of level of popularity. Allow's check out the benefits of Android permitted cellphones over various other mobile phones.
Google.com Android - Mobile progression was actually changed since the launch of Android, which is actually located upon a tweaked variation of the Linux piece. This easy to use system's program pile contains Java functions operating on a Java-based, object-oriented function platform in addition to Java center public libraries. Android began as an Operating System coming from a little start-up provider and also was actually eventually gotten through Google.
BlackBerry Operating System - This is actually an exclusive growth system built through Research In Motion for its own BlackBerry units. EDGE makes it possible for 3rd party designers to compose software application utilizing the offered BlackBerry API (use shows user interface) courses. There are actually much more than 15,000 downloadable requests, which are actually created utilizing this system.
Popular Mobile Development Platforms.
Android 1.5
Android 2.0/ 2.1.
Android 1.6.
Possessed through Google and also a team of virtually 65 mobile phone providers, Android uses a freedom to step in to mobile phone function growth. Android has actually provided programmers the location to build any kind of Android mobile phone function on a variety of systems like Linux, Windows, as well as Mac Operating System X.
Symbian Operating System - Holding some of the most extensive cooperate the marketplace, Symbian Operating System is among the faves one of mobile phone designers. It is actually a free resource system software (Operating System) and also advancement system created for cell phones as well as preserved through Nokia. The Symbian piece (EKA2) assists completely prompt real-time action to create a single-core phone around it.
A few of these systems are actually only confined to the agencies, which create items while others are actually on call for 3rd party use. There are actually offshore advancement facilities around the globe, which are actually utilizing these systems for the progression as well as jogging of remarkable uses, which work on these systems. You can easily contract out custom-made advancement tasks to such facilities Orlando.
A handful of traits to consider: If you are actually an Android creator, you need to always keep a handful of factors in thoughts prior to working with mobile phone growth for Android.
Popular Development Platforms.
0 notes
Text
2 Ways to Find My iPhone on Mac OS
Get the best 2 Ways to Find My iPhone on Mac
It could be devastating when you lose an iPhone or not happen to find one. Every detail of our lives is successfully stored in these mini gadgets and the moment we are unable to locate a device, dark thoughts invade us. From involving the risk of information exposure to unable to get help in times of emergencies, anything can go wrong when you are not with your device.
Get the best 2 Ways to Find My iPhone on Mac
Luckily, the market today is practically brimming with multitudes of tracking software and spying apps to locate lost cell phones. However, how far is this software applicable? Do they really perform as well as their creators claim? Fortunately, with iPhone, you shall never have to know the answers as Find My iPhone feature installed in every Apple device helps locate your phone in emergencies. However, if you are looking for an alternative there are tons of other similar apps that provide additional features to tweak the potential of their purpose.
What is the first thing to do when your phone is lost/stolen?
Before trying to activate the Find My iPhone service through iCloud or the app installed, you need to make sure that your data is secure. It is always recommended to begin by securing your iPhone with a password and a fingerprint lock. Secondly, it is time for damage control. Log out of all accounts in your iPhone by using your Mac or another device.
It is better to inform the authorities, nevertheless, to speed up the process of finding your device. Locating an iPhone from a Mac is fairly simple, as the latter, too, is an Apple device. Besides the Find My iPhone feature you can also install tracking apps on your Mac to locate an iPhone. Although iPhone comes with plenty of backup options in case you lose the priceless gadgets, the Apple Store is not shy of providing you with numerous alternative options.
2 of the best ways of locating your iPhone with Mac
There are several tracking apps online claiming to be bestsellers. While most of them are compatible with Apple, Android, Blackberry and Windows, a majority of them appear to be frauds after installation. How are customers supposed to differentiate between an authentic spying app and a swindle? Experts and tech engineers claim two distinctly outstanding apps that provide you with a more precise location update.
iHound
Website: https://ihoundgps.com
One of the leading ways to identify a fraud application from a genuine one is by assessing their subscription packs. If an app claims to perform a myriad of functions free of cost, it is possibly scamming you. iHound, on the contrary, justifies their expensive price tag by adding a plethora of features to help locate your iPhone.
For $3.99/month iHound, besides providing excellent tracking services, even monitors your morning jog and your kid’s arrival at the school. The app tweaked its functionality radically by including the geo-fencing feature. This feature notifies your Mac about your phone crossing the boundary set on the map of your iPhone. The app constantly updates you on the location of your phone. It will also send you Yelp alerts in case your iPhone has checked in to a Yelp restaurant, building or service.
Its tracking features are one of the best in the market, as it not only includes GPS and Wi-Fi tracking abilities but also cell tower triangulation. It will allow you to track your iPhone on multiple devices and even updates you on any substantial location change. You can set iHound prior to losing your device for emitting different alarm sounds.
Undercover
Website: http://bit.ly/1njIHSY
One of the most expensive iPhone tracking software for Mac, Undercover charges a whopping $49 for its installation but its array of benefits seem to be worth it. There are two versions of the software and naturally the iPhone version is cheaper. Undercover comes with one flaw: it attempts to locate the device via GPS, Wi-Fi or cell tower triangulation only depending on what is obtainable on the device. If you try the Mac version of Undercover then you can even be able to take sneaky photos via the webcam, take screenshots and even avail the keylogging feature. However, a Mac being stolen is much less likely to happen than an iPhone being lost/stolen.
Undercover does one smart trick for the last cry for help. It stagnates the screen of your Mac by displaying a hardware error, which ultimately forces the thief to take it in for repair. It is then that you can display the information that your Mac is actually a stolen possession. The mobile version of Undercover is even smarter. Since the app does not run on the background, the thief is actually required to run the app. Since it is practically impossible for a thief to weave his own trap, the app disguises itself as a game constantly pushing URLs and creating messages in order to get the thief to use it.
The moment the thief runs the app, Undercover immediately sends the location update to your Mac. Also, every data it sends is encrypted in transit as it forwards data via SSL.
Honourable mentions
While Undercover and iHound managed to stand out of the crowd, several other apps offer services close to these two. Some of the honourable mentions include:
Prey
Prey is the only tracking app available on the Apple Store that comes with an open source code. Hence, you can tweak or modify the app prior installation. There is a paid and an unpaid version of this app. The paid version enables you to take photos from the stolen iPhone, transmit your data via SSL and update location on demand.
PhoneSpying
If you are baffled by the plethora of functions that many apps come with, try PhoneSpying App. It performs the most basic task of locating your iPhone via cell tower triangulation, GPS or Wi-Fi with utmost precision.
GadgetTrak
Another mainstream iPhone tracking app, GadgetTrak will find your iPhone only within a matter of hours. In addition, its creators claim of securing the backend database in a physically secured data centre.
The post 2 Ways to Find My iPhone on Mac OS appeared first on PhoneSpying.
0 notes
Text
Learn How Social Media Addicted Teens Become Media Obsessed Adults with Cell Phone Spy App

The digital age kids who have opened their eyes under the shadow of the technology boom are more likely to be obsessed with social media and at the end of the day become the obsessed online media adults. Yes, there is a new study published over the web that lights some fascinating details about the teenagers who use too much social media. Cell phone spy app, a popular phone monitoring application will tell you more about this problem in today’s blog.
Most of us the people are already aware of the contemporary social media platforms such as Facebook, WhatsApp, Instagram, Snapchat and many others alike which have recently become popular among the teenagers as well. Teenagers used to spend most of their time on instant messaging applications and on social media websites using their smartphones connected to the internet all the time.
Almost 95% of the teenagers have access to smartphones. 45% of the teenagers claim that they are constantly online. Over 71% over the teenagers are using Facebook and over 56% of the teenagers use the Instagram every day. They spend over 2 to 5 hours daily on these social media platforms.
A recent study was published by the University of California, which claims that the moment teenagers are online, they keep on thinking about how they should present themselves on it. All the people who are reading this blog will be wondering that if the teenagers are using this much amount of social media everyday, what will their lives be as an adult. One thing is for sure when the kids will spend almost five hours of a day on the social media apps, they have become social media teens at the end of the day. They will become the addicted adults of social media later in their lives.
Teenagers try to have a favorable internet presence
A social media addicted have been adopted by the teens these days that are just tweens. The teens have got smartphones and all types of gadgets at a very young age. Hence, when the tweens become teens, they try to make a favorable presence over the internet. This when they get into the habit of thinking all day about what should they share over the social media platforms and the pictures and videos which they should upload to their social media accounts.
In the early age, none of it seems like a trouble to the parents, cell phone spy app phone monitoring application turns out to be an effective solution in this regards which help the parents to view all the things which their kids are sharing over the social media applications. With the help of a cell phone spy app, parents can check if their kids are doing the right activities or just setting up a trap for themselves.
Teens always want to share something which should portray a fascinating image of them to get appreciation. In most of the scenarios, to become popular, the kids have always wanted to look attractive to become a popular entity. And in doing so, they create a pit for themselves and the future of their family. Cell Phone tracker app in this regards updates the parents about all the things that are happening in the kids lives all the time so that the parents could keep an eye on their teens all the time.
How to safeguard kids online?
One thing which all the parents need to keep in mind is that just the way you keep an eye on the kid's physical activities all the time, in the same manner, you should also keep an eye on the kid's digital lives as well. Today, the technology has taken a rapid shift where everything is transmitting over the web only. Nothing is on papers anymore. Hence, it is always suggested that as soon as you offer a digital device to your kids to use, at the same time, you should also apply a proactive approach to the activities of your kids on it.
Spy phone app phone monitoring applications in this regard play a major role of offering the parents the ability to actively track all the kid's activities on their digital Android devices on its control panel, and share them with the parents.
The cell phone spy app needs to be installed on your kid's cell phone in order to monitor all that is happening on the kids mobile phone at all time. Once you have the data of your kids, you can read the data and view the activities which they are getting involved at any point in time.
Using a cell phone spy app phone monitoring application to get the job done

There are many other ways as well in which the parents can monitor their kid's cell phone at all time. However, installing a cell phone spy app to the kid's cell phone to keep an eye on the kid's activities all the time is the best way to do it since mobile phones have become an eminent part of our lives. Among all, ONESPY cell phone spy app is the most effective phone monitoring solution which you can get in the market at an affordable price tag. The cell phone spy app comes with one unique feature which does not get removed from the device even after multiple factory resets.
ONESPY spy phone software is an amazing phone monitoring application that offers over 30 amazing features listed below. All you have to do is just visit www.onespy.in and install the application to their kids mobile phones.
Features offered by ONESPY cell phone spy app:
Call Logs
Call Recordings
Applications
Contacts
SMS Messages
Photos
Surroundings
Locations
Internet History
WhatsApp Chats
WhatsApp Calls
Facebook Chats
Hike Chats
IMO Chats
Instagram Chats
Snapchat Chats
Tinder Chats
Kik Chats
Line Chats
Skype Chats
Viber Chats
Google Emails
Yahoo Emails
Outlook Emails
Photo Capture
Screenshots
100% Hidden
Device Change
Chat Support
Technical support
#spy phone software#spy phone app#spy phone#cell phone spy app#cell phone spy#how to track cell phone#how to hack my girlfiriend's cell phone
0 notes
Text
Know About Detective Equipment

Whether you're known as a private detective or an expert investigator, then you'll require some simple detective gear. Individuals can be used by private customers, the authorities or law enforcement agencies. Irrespective of the places, the fundamental assumption is exactly the same. On the other hand, the gear will change somewhat. The government has their own normal issue as do police departments. On the other hand, the private sector has the maximum flexibility, which is typically only limited by financing. Get best Detective Equipment by clicking on Prisluskivaci.
The Basics to Build Upon
As a detective, you may be an insurance agent, an expert restoration expert or focus in locating people. Basically, as a private detective or accountant you may perform various activities for customers. Your work is to ascertain facts and locate answers to queries. But you'll require technology's aid in solving the majority of the circumstances. This list is by no means comprehensive.
Digital Camera with Zoom Lens
Hand Held Video Recorder That is effective at Transmitting Video to a Computer or Cellular Phone
Hand Held Digital Voice Recorder for Taking Notes and Recording Conversations
Binoculars with Night Vision Technology plus also a Built in Camera
Night Vision Spotter Scope using a Range Finder
Mobile Phone Capable of Recording Conversations
Throw away Phones or What Many Refer to as Burn Phones
Laptop -Computer With Your Own Wi-Fi Card
A Program on a CD Rom That Will Wipe The Hard Drive
Bundle Of Cigarettes Matches and Lighter
Multi Purpose Tool
Global Positioning System or GPS
The listing is a great beginning, so irrespective of your subject of experience this detective gear is versatile. It might be impractical to believe that everything you might possibly want is neatly tucked away in a briefcase. But by constantly carrying the fundamentals You're assured that you can execute most surveillance operations.
The List of Not So Basic Equipment
Covert Listening Device That Can Transmit To a Receiver and Recorder Using Radio Frequencies or RF
Handheld RF Receiver
Numerous Covert Cameras Disguised as Common Objects
Smoke Bombs Which can be Usually Available at any given --Pyrotechnics Store or Fireworks Shop
Steel Stun Baton, Stun Gun or Handgun for Personal Protection
Pepper Spray or Mace to utilize Against Individuals and Animals
Plastic Cable Ties Instead of Handcuffs Because Most Criminals from -Habit Carry a Key
Protective Vest and also to Find One You Can Shop An Army Surplus Store -For a Flax Jacket or Vest
An RF Intrusion Detection Device This Device Will Pick Up RF --Transmissions
Police Scanner One That Can Unscramble Encrypted Transmissions
Weather Resistant Back Pack
You are able to add to or remove from any listing of detective gear. A lot of what you might want is dependent upon the assignment at hand. Some situations will be clarified together with the basic and not so basic collection of gear.
Move In and Set Up Your New Office
Your workplace will become your automobile in several cases. Ensure that you have the correct chargers for your gear. Many newer vehicles have a USB link to control laptops and lots of cellular phones. Maintain a converter box at the back that may work as a book. Utilize the correct safeguards on your personal computer to reduce hacking when using a Wi-Fi. But, it's strongly recommended you use a card supplied by an Internet supplier.
Proof Collection Is Your Number One Consideration
Video proof has a direct effect in court, and it's crucial to safeguard your own evidence. Never list over any erased content when taping a topic. An investigation of this recording will reveal it had been utilized to document. The integrity of this video is going to be contested. Always use a brand new memory card for each and every operation. No talking while taping since, it is going to wind up on the sound part. Confirm where you are by listing some notable landmarks. It's important your goal's location can be confirmed from the pictures on tape.
Audio or video proof recorded by covert means might not be admissible, but it might confirm known details, which was accessed by other means. Thus, using secret detective gear is required lots of times to help solidify theories, and also to point you in the Ideal direction.
Many surgeries will be run at night. Possessing the capacity to see is vital. Never look directly at the goal from the dark, always rely on your peripheral vision. Utilize the spotter extent because distances could be misleading, the extent will decide on the scope for you. When the space is famous use the night vision binoculars for image taking. Knowing the space can determine the elevation of a goal by comparing the subject to famous item dimensions. Additionally, it may reassure you that you're out of range of any firearms.
Adapt To Your Surroundings
You don't smoke why smokes? The sight of a person grabbing a smoke at a door is so common most individuals don't give them another look. Cigarettes are props, so use them if running an investigation. Use urban camouflage to blend in, as an instance, a mobile phone to the ear using a paper and coffee. Individuals might assume any item on your hands is a telephone.
Prevent Physical Contact Any Target nevertheless be Prepared Just In case
Flax coats can absorb blows from fists, dull objects also it will help divert Tasers as well as bullets. Many are not thought to be bulletproof vests, but they do provide security. Wear one when the situation dictates, and cover it with a huge coat or shirt. In addition, it can be utilised to cover you in case an explosion looks probable. Body armor is a essential bit of detective gear.
Smoke makes the ideal concealment medium. Additionally, it creates confusion letting you escape or enter a room without being viewed. Dip a smoke bomb and begin crying for folks moving and to instill anxiety. Chaos functions in your favor. Put it so people can't recognize the origin instantly.
Always Think Beyond the Next Curve
Always back up your data when using your PC. Email documents to your account or offer another way. Don't permit a stolen notebook to stop the operation. Surveillance is dull and lots of inexperienced detectives become impatient. Contrary to what's portrayed in the films, you don't run a monitoring mission before the subject's house. This is where technology comes in to play.
Your detective gear will consist of covert surveillance cameras. Installing theses devices in crucial regions permits you to keep an eye on your goal well from the sight. Be imaginative, cameras may be concealed as a birdhouses, yard decorations, and even attached to your mailbox. You are able to set up surveillance out of a parking lot where your vehicle won't draw attention. The camera will transmit the pictures to your personal computer or telephone. You might even attach a GPS monitoring device to your own motor vehicle. The perfect time to put a gadget is whenever the subject is wrapped at a store parking lot, but you should be mindful of any cameras found in the region.
The GPS tracker includes multiple functions. You might find it necessary to go into a subject's house. Track them in your telephone as you're inside installing listening devices or collecting information. 1 word of warning, don't enter a victim's home till you've tracked the place for many days. Make sure no other service or person is conducting surveillance. It can get problematic, based on who else might be seeing them.
Exercise Awareness Of Your Situation
Maintain the scanner to your local police division. Scanner frequencies can be obtained on the Internet or by simply scanning through the several bands. If you're using a rental vehicle, memorize the license plate number. Frequently cautious citizens will report that a suspicious vehicle parked someplace. You're able to listen to the telephone onto the scanner. Apparently, you would like to learn this so you'll be able to get another place. Park when possible to help keep someone out of coming up . Use one of those covert cameras set in the rear of the vehicle to track what's behind you. Some vehicles have back up cameras, which participate when the car is changed to reverse. Be creative and think about your car or truck component of your detective gear. With just a little creativity, you'll see different uses for your automobile camera.
Always check your automobile when you're out of it for over a couple of minutes. Utilize the RF scanner to test for apparatus and search for cameras and GPS trackers. Whenever leaving your cell office require any memory cards . Pros will merely spend the memory card or flash drives from your automobile becausethey understand notebooks can be monitored.
Additional you as a trained operative shouldn't add a memory card or thumb drive into a computer which may be tracked to you. Thus, any evidence gathered at the area's resident ought to be managed with caution. Viruses could be written and put on just about any device, to add USB flash drives.
Stay Mobile and Never Look Back
There are numerous cardinal rules that have to be adhered to if working in the area. When leaving a living space for any reason assume you won't ever return. Including going for lunch or just down the hall for ice hockey. To put it differently, whatever detective gear is left in the area is really a throw away and can't be traced to you. Take the essentials in a bunch that's always with you. Nobody finds carrying out a bunch to be from the normal anywhere on the planet. Don't go to a living area. 1 night for some rapid relaxation is okay. Use gift cards throw away cash cards for payments. The throwaways are bought at checkout in many shops and they're untraceable. Take several with smaller numbers which may be left behind.
Regardless of what you might see on tv most professionals not take fake identification unless they're connected with the authorities. Doing this raises questions and legal problems, and many are quickly seen. Thus, your history has to be exploited to account for the reason why you're where you're. You might just be a certified investigator working for a private citizen, which means that you may be obscure. But, avoid any circumstance aside from interaction with law enforcement, in which you need to present identification. The top operatives would be those which blend in. They're not flashy, never brag about what they do and they exercise avoidance.
Personal Protection as Part of Your Detective Equipment
Selecting personal protection has to be carried out cautiously, and you need to think about the legality of your selection of weapons. Handguns naturally are a sensible option. Every state has their version of concealment. A weapon wrapped in the vehicle or glove compartment is futile, as is a one. Revolvers are dependable and they don't render brass behind, but they need more actions to pull the trigger. The trustworthy .45 is also an option as are 9mm handguns. Know the legislation in the respective states. Stun guns may be hidden and they're useful, as are stun batons. The telescoping batons have been utilized to prevent anyone from reaching from the window.
Following the Mission is Successfully Completed
Wipe the hard disk of computers used. Use an excellent program that over simplifies and writes the documents. Much of what has been accumulated may need to be stored, so make sure it stays on the recoding medium. Gently burn off any throw off telephones, and remove all equipment from the motor vehicle. Clean and inspect all your detective gear for another assignment.
0 notes
Text
Remote Installed Cell Spy Software – Does It Work?
You’ve might have heard of it and some of you have possibly experienced the consequences of having cell spy software installed on your device without even knowing it. The possibility of remote cell phone spying using hidden software is non-existent and in fact, there are many apps being advertised and used for that purpose yet all of them fail to deliver what it is being advertised.
The reasons that remote install is not possible are many and we will go into details on why it cannot happen without some kind of previous user interaction. Most of the modern cell phones come with a locked operating system. Factory restricted access to the system prevents any kind of unauthorised remote access and makes such access to sensitive data stored on the device virtually impossible. Not to mention that it is completely illegal to install spying software without the owner’s knowledge.
The best rule to follow is that you do not browse through online content you’re not sure of and to follow simple guidelines which we will further discuss in our guide. We will also explain how most of the harmful software operates and how you can take measures to protect your devices from unauthorised data breaches.
Is my device safe from remote installs of spying software?
You can be sure that your brand-new phone is clean and secure from unauthorised access as long as you bought it from a retail store which is authorised to sell devices from the manufacturers. Buying from shady eBay dealers or any other place at suspiciously low prices could spell trouble for the authenticity and safety of the software that comes pre-installed on the device. Some of the Chinese-based online retailers are well-known for installing malware and harmful software which sends private user data and logs activity which is sent to remote servers.
Android phones which are rooted are automatically susceptible to security risks and it wouldn’t matter that the devices are running the latest security patches and the latest operating system if the harmful app gets installed. The same goes for Apple devices which are jailbroken. Their security is thus compromised.
The amount of data that can be monitored and transmitted to a remote location is staggering. Complete phonebooks, messaging, emails, IM apps chat history and even sensitive credit card information – all of that information can be stolen remotely given the right circumstances.
How to best protect yourself from the spy software?
First of all, make sure not to install any software that is not from the official app store from your device. For Android it is the Google Play store, for Apple users, it is iTunes store and for Windows phones, there is the official Windows Store.
Even though you will install apps from the official online store some of them come with inbuilt advertisements. This can be a serious security concern too since the links of those ads can lead straight to the installation of harmful spy software. The same goes for browsing websites and clicking on tempting headlines which can also lead to the installation of malware apps.
There is absolutely no way to remotely install remote spy software on any device without some sort of local user input.
Do not leave Bluetooth connection set to always on and if you must – in order to use your connected Bluetooth devices – make sure to make your device Bluetooth visibility switched off. Do not accept Bluetooth connection requests from unknown devices. This is a great way to allow unauthorised remote access to your device and all of your sensitive data stored on it.
When it comes to Wi-Fi connections over unknown and open routers they equally pose a danger to the security of your device. Do not connect to routers and access points that you do not recognise and that do not have any sort of password protection. Surfing online over unsecured connection will expose your login information and potentially allow hackers to steal your identity.
Ignore the temptation to click on the links that offer something expensive for free and just for you. There is no such thing as free stuff without something in return. In this case, a simple click can turn your sensitive data from being private to being in someone else’s possession. This is how most digital ransom schemes work. There is plenty of extortion happening because phones and computers get locked by spy software and then the hackers demand payment to unlock and return data to the owners.
The main warning signs that your device is running malware is if you are constantly seeing nagging screens that warn you how your security is compromised or if you notice that your phone is constantly uploading something over your data connection even when you’re not using it.
Make sure that you only install the applications from the official stores. Do not root or jailbreak your device. This will disrupt the inbuilt security measures and it will make your device vulnerable. Only surf over secured connections!
Install some of the popular system monitoring tools and antivirus software which will show you which of the apps are using the most memory and are active and always running in the background on your device. Spy software works in the background to monitor all user activity so it should be visible in the process monitoring tools.
Install apps that will also show you the network traffic your device makes when it is connected to any type of network. The apps which look unfamiliar to you and which have constant data usage are the possible malware or spyware apps that are installed on your device.
The only thing to do in such cases is to check the list of installed apps and try to manually remove them from the inbuilt device application manager found in the settings. However, if the spy software is installed and hidden then you would have to find it manually. If you still suspect that your device is monitored but you can’t find the cause of it then it is best to completely wipe the device clean with a factory reset.
Do not follow links which pop up on your cell phone which promise the same and prompt you to fill your credit card details. These are the ways scammers operate! Be careful! Stay safe online!
So how does spying software work?
Spy software exists for any device capable of running any type of software code and in fact, there are plenty paid monitoring solutions that people use every day. People turn to such software when there are security concerns for their children, their property or even their personal safety. These types of professional monitoring tools are put to good purpose and with the knowledge of the owners of the monitored devices.
Most of the spy software works by monitoring users activity on the target devices and collects all of that information for later analysis and viewing. Most of the current generation monitoring tools include an inbuilt functionality to remotely send the data to remote servers, view Emails and SMS messages too. Some of the most advanced ones have the ability to track devices in real-time using the inbuilt GPS modules and relay every second of the tracked devices to a remote viewer on a detailed map.
Most of the premium cell spy tools offer an online user interface where every single activity on the target device is displayed just as it happens in real-time. These services accept PayPal and have an established user base so if you need their services make sure that they are verified.
In case you decide to use some of the legit device monitoring/spy software make sure to get in touch with the company offering such service and check their online user feedback. Google their company name and see what their users have to say about the quality of the company and its products.
Most of the customers using these monitoring applications have serious security concerns for their children and want to make sure that they are safe when they are not in their proximity. With geofencing – concerned parents can even set virtual boundaries and get notified when they stray outside of it.
To conclude our findings and ease your worries we have to point out that the chances that your device and your own digital security get compromised are very low if you adhere to these simple rules. No one can externally gain control over your phone or your private data unless you allow them too. The funny thing is that most of those harmful programs ask you just that – to click the “Allow” button to grant them full access to all your stuff. By staying vigilant and adhering to basic security protocols it is virtually impossible to get monitored remotely.
In case that you would like to hire monitoring services for your devices, we suggest that you opt for tried and tested premium software companies that allow money back guarantee so that you can try and see if the service suits your needs. For those that stumble upon websites which offer free spying/monitoring software – steer away from them. They are sure to be some sort of a scam and will only take your money and do you more damage than you can imagine.
The post Remote Installed Cell Spy Software – Does It Work? appeared first on CellSpy.org.
from CellSpy.org http://ift.tt/2mYvOJz
via IFTTT
0 notes
Text
Personalized Mobile Progression
Personalized Mobile Progression
Mobile sector has actually viewed incredible development in the final handful of years along with the introduction of manies thousand of foreign advancement centers. Listed here personalized progression jobs are actually managed through creators that possess years of expertise in making and also establishing mobile phone apps to comply with the min demands of a service.
Along with the amount of consumers accessing the Internet via their mobile phone phones, the necessities for such custom-made apps has actually raised notably. It is actually no shock that profession and also trade titans such as ebay.com, Amazon and so on released their very own mobile phone functions numerous years back. Front End Developer Miami
Along with the advancement of 3G and also wise phones, bulk of organisations are actually appearing at mobile phone advancement to market their services. The top quality that has actually produced this kind of progression such an appealing proposal is actually the simple fact that mobiles are actually zero much longer limited as interaction unit simply, however have actually come to be a comprehensive mixeds media tool.
Important Tips for Custom Mobile Development
Make sure that your use is actually light in weight as this is actually much easier for customers to install and also utilize. Inquire your programmers certainly not to utilize excessive resources and also factors in your application. Portable unit consumers like straightforward applications, which could be worked utilizing a handful of switches.
Launch frequent spots and also updates and also remain in sync along with the most recent equipment growth in the field. This will definitely certainly not just improve your customer foundation yet likewise your reliability in the marketplace.
Carry out discountenance overdesign, as this is just one of the primary oversights, services dedicate when it concerns customized progression of their apps for different portable gadgets. Your request requires to become straightforward and also there is actually no damage in attracting creativity coming from productive treatments Miami.
Contemplate the function in your thoughts prior to coming close to the creators. This is vital as you recognize your organisation much better than any person else, as well as recognize your assumptions coming from the application Florida.
To possess an efficient advertising project, pick multi-platform mobile phone growth, which will definitely make certain that you target consumers utilizing primary os Jacksonville.
Custom-made Mobile Development for Businesses
Everybody possesses various criteria for his or even her mobile phone. It is actually virtually inconceivable for mobile phone advancement firms to comply with all demands along with their nonpayment functions.
The intro of Smartphones such as Blackberry and also apple iphone has actually extremely improved the personalized mobile phone progression market. They progressively have actually begun attempting their good luck at bring in customized mobile phone applications for significant services. Along with expanding attraction of customized mobile phone application happens improving conclusion amongst the little and also mid-level organizations to maintain in the market.
Maintaining an eye on the increasing requirement for individualized mobile phone functions for services, mobile phone firms are actually pressuring even more on this advancement. Various organisation homes call their mobile phone supplier in purchase to develop a certain kind of mobile phone app. The conveniences of customized mobile phone app growth are actually massive; nevertheless, this is actually one of the simple factors that custom-made mobile phone advancement for organisation is actually receiving therefore a lot recognition.
Threats linked with customized mobile phone growth:
Regularly tally the performance of function along with ROI (Return On Investment). If ROI is actually more than the expenditure, the application costs getting, else certainly not.
Regularly focus on the system software of your mobile phone just before acquiring a custom-made app. If the application is actually inappropriate along with the Operating System, your assets will certainly be actually totally lost.
You constantly must note the intended usage of the function. If the application complies with each one of all of them, and also certainly not a number of all of them, merely after that you need to opt for acquiring it.
Along with mobile phone phones, consistently happens the concern of mind area. Devoting very a lot room for the app would certainly not be actually a practical tip for any sort of company.
Mobile Development for Android
The dawn of mobile phone phones have actually created our lifestyle much easier than in the past as well as many thanks to the improved variations like that of apple iphone, contact display phones, Smartphones and so on that numerous mobile phone modern technologies are actually put together right into one unit. Mobile Development Orlando for Android is actually mostly located on Java.
Developers, that really want to remain in this hectic as well as very competitive market, have to accept Android Mobile Development Orlando. Much, even more than 50000 Android mobile phone functions have actually currently been actually created for Android powered mobile phone phones.
There are actually 3 models of Android os accessible for various mobile phone apps:
It is actually a closed up exclusive mobile phone advancement system. A brand new layout foreign language Metro permits mobile phone designers to include the operating device along with 3rd celebration and also various other Microsoft companies.
Mobile phone growth has actually come to be one of the very most very competitive regions for the programmers. Around the planet, mobile phone programmers make use of mobile phone systems for the advancement of some remarkable applications.
Apple iphone - The i-generation's progression system, iphone is actually made use of through mobile phone creators to generate requests for the apples iphone, ipad tablets and also Apple TELEVISION. It is actually only utilized for apple iphone growth, as Apple carries out certainly not accredit its own iphone for installment on 3rd party equipment. This system is actually stemmed from Mac Operating System X and also is actually consequently a Unix-like system software naturally Orlando.
- Easier information transactions throughout various mobile phone systems is among the major conveniences of Android. There are actually GSM, Bluetooth, UMTS, EDGE, EV-DO, CDMA, as well as Wi-Fi solutions in Android to transmit information.
- Android made it possible for phones possess a broad amount of functions including Touchscreen, Video Camera, accelerometer as well as magnetometer, as well as GPS.
- All the Android phones possess IPC or even Interprocess interaction information passing location.
- Android powered phones provide different collections for 2D and also 3D graphics. There are actually likewise an amount of collections for video clip, sound, and also graphics.
- There is actually SQLite for holding information.
- There are actually lots of non-code application resources including design, picture as well as chain data, which must be actually device-specific. Designers possess to develop distinct format documents for a variety of monitor measurements.
- Each of these components should be actually switched on individually.
- Android Apps have to be actually combined along with much more than one function component. Commonly, an Android function features several solutions, tasks, program recipients, and also information suppliers.
- Each of these parts ought to conduct distinctive duties.
- Files ought to proclaim the parts together with their criteria. If the part needs a distinct components arrangement, it must be actually discussed in the equivalent report.
- Benefits of mobile phone growth for Android: There is actually a trigger, contacted 'User-friendliness'. The mobile phone innovation that strikes the trigger, are going to succeed royalty of level of popularity. Allow's check out the benefits of Android permitted cellphones over various other mobile phones.
Google.com Android - Mobile progression was actually changed since the launch of Android, which is actually located upon a tweaked variation of the Linux piece. This easy to use system's program pile contains Java functions operating on a Java-based, object-oriented function platform in addition to Java center public libraries. Android began as an Operating System coming from a little start-up provider and also was actually eventually gotten through Google.
BlackBerry Operating System - This is actually an exclusive growth system built through Research In Motion for its own BlackBerry units. EDGE makes it possible for 3rd party designers to compose software application utilizing the offered BlackBerry API (use shows user interface) courses. There are actually much more than 15,000 downloadable requests, which are actually created utilizing this system.
Popular Mobile Development Platforms.
Android 1.5
Android 2.0/ 2.1.
Android 1.6.
Possessed through Google and also a team of virtually 65 mobile phone providers, Android uses a freedom to step in to mobile phone function growth. Android has actually provided programmers the location to build any kind of Android mobile phone function on a variety of systems like Linux, Windows, as well as Mac Operating System X.
Symbian Operating System - Holding some of the most extensive cooperate the marketplace, Symbian Operating System is among the faves one of mobile phone designers. It is actually a free resource system software (Operating System) and also advancement system created for cell phones as well as preserved through Nokia. The Symbian piece (EKA2) assists completely prompt real-time action to create a single-core phone around it.
A few of these systems are actually only confined to the agencies, which create items while others are actually on call for 3rd party use. There are actually offshore advancement facilities around the globe, which are actually utilizing these systems for the progression as well as jogging of remarkable uses, which work on these systems. You can easily contract out custom-made advancement tasks to such facilities Orlando.
A handful of traits to consider: If you are actually an Android creator, you need to always keep a handful of factors in thoughts prior to working with mobile phone growth for Android.
Popular Development Platforms.
0 notes