Text
Everything about Bluetooth SIG Mesh
Bluetooth SIG mesh is a Bluetooth technology owned by Bluetooth Special Interest Group (SIG). It was launched in July 2017. Generally, it can be defined as computer networking that allows communication between many-to-many communiqué devices.
It’s perfectly designed to enable extensive networking among devices. According to Bluetooth SIG, Bluetooth mesh was created to suitably build automation and offer several Internet of Things (IoT) solutions, where thousands of devices can communicate effectively and securely.
It also allows thousands of nodes to communicate efficiently without any connection but within the same network. It is a reliable method of sharing information in large networks.
How Does Bluetooth Mesh Work?

Bluetooth mesh operates under one principle; Flood network. This is where the nodes relay messages in a certain manner, either in uncontrolled flooding or controlled flooding.
In uncontrolled flooding, every node shares the same message to all its neighbors unconditionally. In controlled flooding, each node plays both roles of transmitting or receiving the message.
Bluetooth Mesh has a message cache that prevents conveying similar messages or messages relayed recently. The figure below shows how a Bluetooth mesh network operates.
Characteristics of Messages Relayed In Bluetooth Mesh
1. All messages relayed must begin with an opcode as shown below;
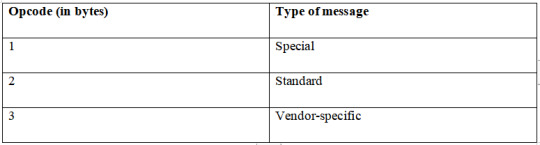
2. All messages have the sender and receiver addresses.
3. They all have sequence numbers which are essential as they defend the network against all attacks.
4. They all have time to live (TTL).
5. They are all encrypted and authenticated using the following keys;
· Network keys
· Application keys
6. Each message sent should not exceed 384 bytes. However, most of the messages relayed are 11 bytes long.
The Bluetooth Mesh works flawlessly in a network of several compatible devices like;
· Laptops
· Smartphone
· Televisions
· Desktops
· Speakers
· Headphones
· Other low power devices
BLE Mesh Communication Protocols
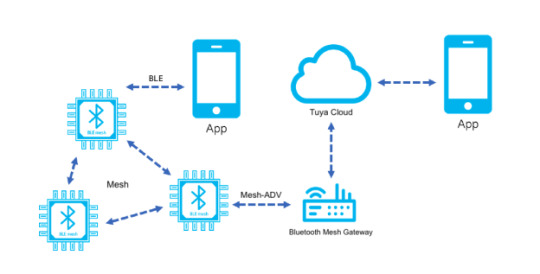
Bluetooth mesh uses a variety of protocol stacks during communication. The core stacks are divided into two;
· Host stack, which deals with high-level data and acts as a segment of the operating system.
· Controller stack
However, the most important component of the Bluetooth communication protocol is the Generic Access Profile (GAP). This element of Bluetooth mesh technology manages the scanning and broadcasting processes of all Bluetooth devices.
GAP also plays an important role in controlling how the devices connect to other nearby devices. Bluetooth 4.1 and 5.0 enables all devices to connect and broadcast data directly to other devices.
Advantages of Bluetooth Mesh
Although many solutions have been offered using different wireless technologies, the best is Bluetooth Mesh technology. It has several advantages over other wireless networks. Read on.
1. It’s more reliable as it provides vendor interoperability. For instance, Nordic Bluetooth Mesh technologies, especially nRF52 Series Soc and nRF Bluetooth Mesh, are reliable, as they have multiple paths from sender to receiver, which operate without failure. The Bluetooth mesh stack in this nRF helps in implementing Bluetooth mesh profile specifications.
2. It extends range, unlike other wireless technologies like WI-FI.
3. It uses low energy, especially Bluetooth low-energy mesh.
4. It can operate efficiently on other existing Bluetooth hardware, especially Bluetooth 4.0.
5. It is more secure than other wireless networks. For instance, all messages in this technology are encrypted and authenticated.
6. It is quick and easy to install.
Application of Bluetooth Mesh Network
Bluetooth mesh network is widely used globally. It’s used in education sectors, health centers, cities and many other places, where other wireless networks become unreliable.
1. Bluetooth Mesh in Schools
University and college students and staff widely use Bluetooth Mesh. This technology is also being embraced in high schools.
It is convenient in education centers as it can help students and lecturers download large learning files, especially when WI-FI becomes unreliable. Also, due to the wide internet connection coverage by Bluetooth mesh, students and staff’s security is guaranteed as they can get information easily in case of emergency.
2. Bluetooth Mesh in Cities
With Bluetooth mesh, it’s now easy for cities to connect citizens with this connection. Commuters can easily check their emails and other social networks wherever they are around the city. The technology has also enhanced security in towns as communication through the internet is easy and quick in emergency cases.
3. Bluetooth Mesh in Health Centers
Many hospitals prefer Bluetooth mesh network instead of traditional ones as they are convenient and easy to install. Internet connectivity in this sector is vital as patients’ files need to be updated every day for convenience. Also, doctors can track patients and other colleagues from their laptops or tablets on the premises easily.
4. Bluetooth Mesh in the Hospitality Sector
Bluetooth mesh technology has become the rule in most restaurants and hotels around the globe. It is easy and quick to install both outdoors and indoors. It’s effective than a wired network, especially during outdoor concerts in these resorts. It’s also less expensive as compared to WI-FI.
5. Bluetooth Mesh in Warehouses
Most modern warehouses depend on this technology to keep track of all warehouse logistics.
Security in Bluetooth Mesh Network
One major issue that need to be addressed concerning Internet of Things is security. It is a reoccurring concern that can interfere with the Internet of Things benefits like convenience and flexibility. It should be the number one priority, especially in Bluetooth mesh networking.
The main reason why Bluetooth mesh security should be mandatory is that many devices are involved. Generally, it is built on thousands of Bluetooth mesh devices that communicate with each other. However, in Bluetooth low-energy mesh, security is optional as only a single device is involved.
Fundamentals of Bluetooth Mesh Security
These security statements should apply to all Bluetooth mesh networking devices.
1. Encryption and authentication
All the messages shared among the Bluetooth mesh networking devices must be encrypted and authenticated to enhance security.
2. Separation of concerns
Three types of security keys are used in Bluetooth mesh network security. They include;
· App keys, which address application security concerns.
· Network keys (Netkey), which solves network security issues.
· Device key (Devkey), which address device security issues.
All of them are used to tackle different security issues in Bluetooth mesh networking. In other words, all security issues are addressed independently.
3. Area isolation
In Bluetooth mesh, the network is sometimes divided into different subnets. In this case, each subnet is given its own key and can only communicate with subnets with the same key.
4. Key refresh
As seen above, most Bluetooth mesh nodes have their special security keys. But these keys might need replacement in case a node becomes faulty. In this case, a key refresh procedure is done, and all other nodes are issued with new security keys.
5. Message obfuscation
Obfuscation prevents the messages sent within the network from being tracked. It also ensures that nodes are secure.
6. Replay attack protection
A replay attack is where an eavesdropper captures a message being transmitted and retransmits it later to make the recipient to do something that the invader is not allowed to do. The Bluetooth mesh security helps in preventing such episodes.
7. Trashcan attack protection
When faulty nodes are removed from the network, they can no longer use their network keys as the remaining nodes are issued with new keys. This helps in preventing trashcan attacks.
8. Secure device provisioning
The process of adding more nodes and devices to Bluetooth mesh network is safe and secure.
Bluetooth Mesh Software Development Kit
To benefit maximally from the Bluetooth mesh features, you need Bluetooth mesh software. Some of the features that the Bluetooth mesh development kit helps improve are;
· Angle of arrival (AoA)
· Angle of departure (AoD)
· 2M and LE Long Range PHYs
· Advertisement sets
· LE Data Length Extensions
· LE Dual Topology
· Scan event reporting LE Secure connections
Are Products Embracing Bluetooth Mesh Technology?
Various products in the market are using this Bluetooth technology. For a product to have Bluetooth mesh networking potential, it must undergo a Bluetooth mesh qualification process. This ensures that it has all the Bluetooth requirements.
Read on for the Bluetooth qualification process that all products must undergo to qualify as Bluetooth mesh products.
Bluetooth Qualification Process
This process enables the companies that want their products to be enabled with Bluetooth features to comply with;
· Bluetooth patent and copyright license agreement.
· Bluetooth trademark license agreement.
· Bluetooth specifications.
To qualify for this process, your products must have all Bluetooth designs. This means they must have the required hardware and software for Bluetooth mesh specifications as explained in the Bluetooth mesh profile.
To qualify your products, you need to keep in mind various things;
1. For your creation to be considered as a Bluetooth product, qualification process is key.
Even if your supplier’s product has undergone a qualification process, your products must also undergo the process. In short, you can’t inherit the qualification rights from your supplier.
Also, the product can complete the qualification process successfully if it’s under the Member Company’s account and not under the supplier’s account.
2. Check the qualification of the products if you are reselling.
It’s always advisable to check whether the products you are reselling from another company have completed the qualification process. This is important, especially if you are reselling it as a Bluetooth mesh product.
3. Don’t market your products if not completed the qualification process.
It’s illegal to sell your merchandise as Bluetooth enhanced products when not qualified yet. You can only distribute them after the qualification process is successful. Also, during the process, ensure you give the correct details that exactly match your products.
Latest versions of Bluetooth Mesh
Internet of things wireless communication technology is experiencing a lot of issues. The solution to these issues is the introduction of the latest versions of Bluetooth mesh. One of these versions that are widely used around the globe is Bluetooth 5.0 mesh network.
Overview of Bluetooth 5.0 mesh
This Bluetooth specification was unveiled in 2016. It was mainly an improvement of Bluetooth 4. Some of these improvements that make the two versions different as shown in the illustration below;

From the above table, it’s evident that the Bluetooth 5.0 mesh has more improved features that can help solve some of the internet of things issues. These features include;
· Improved speed
· Increased message length
· Increased message sending capacity
· Increased data transfer rate
· Increased output power
· Increased range
All the above features make Bluetooth 5 mesh more advantageous than other versions like Bluetooth 4.0. All latest smart devices now support this version of Bluetooth technology.
Other Bluetooth 5.0 Mesh Features
Other things that this latest version of Bluetooth brings to the table include the following;
1. Bluetooth low-energy for headphones
Bluetooth low-energy uses less power as devices communicate with each other. The feature is essential for devices like phones and headphones as they rely on batteries for power.
Although Bluetooth low-energy was introduced and enabled in Bluetooth 4.0 mesh, it wasn’t as helpful as in Bluetooth 5. It was only applicable to small internet of things devices, wearable, and beacons. Therefore, headphones and other large gadgets would continue using high-power Bluetooth connections.
All devices can now communicate over Bluetooth low-energy with the introduction of Bluetooth 5 mesh. This increases the battery life of these communication devices.
2. Bluetooth dual audio
This simply means connecting more than one audio device to a source. For instance, you can connect two headphones or two speakers to your laptop. This is possible with Bluetooth 5.0 mesh.
Other Certified Bluetooth Mesh Models
ESP32 Bluetooth mesh is another model of this Bluetooth technology that is certified by Bluetooth SIG. It’s features include;
1. Has Both Bluetooth and WI-FI Chips
ESP32 has SPI and SDIO interfaces that enable it to provide Bluetooth and WI-FI functionalities. It can also perform as a standalone system, and can be used for various applications.
2. Has a Robust design
ESP32 performs effectively in industrial environments under –40°C to +125°C temperature range.
3. It Has Ultra-Low Power Consumption
ESP32 is effectively used in internet of things applications and mobile devices as it consumes low power. It has dynamic power modes and power scaling features.
4. It Is Highly Integrated
ESP32 is in-built with various features that make your applications function properly. They include;
· Filters
· Power amplifiers
· Antenna switches
· Power management modules
· Low noise amplifiers
Future of Bluetooth Models
There is a major development in Bluetooth technology as it is opening new and great opportunities for innovators to experiment and show their creativity. The Bluetooth Special Interest group has recently announced the development of Bluetooth 5.1 mesh.
Although it may take some time for Bluetooth 5.1 to be functional in most Bluetooth mesh devices, it will soon find its way. This technology will have various new features, as discussed below.
1. Improved Accuracy
The current Bluetooth technology, especially Bluetooth 5.0, can tell how far a device is by detecting its signal strength. But it cannot guess the direction of that device, i.e., where the device is heading or coming from.
Interestingly, the new Bluetooth 5.1 technology will have this direction-finding feature. This technology will have the ability to assess the device’s exact location, the direction it’s coming from, and the distance.
Therefore, this Bluetooth technology will be vital in the future for easier tracking of networking devices. For instance, if you lose your smartphone or laptop, the direction feature will make the search process quicker and easier.
2. Improved Connection Speed
Bluetooth 5.1 will be connecting to other devices faster than Bluetooth 5.0 as it will have better caching. The technology will also save the time customers spend going through service discovery as they connect to Bluetooth. This will make the connection faster.
3. Less Power Consumption
Like Bluetooth 5.0, this new Bluetooth technology will be low-energy. This means that even as it performs all its functions aggressively, the power consumption rate is low.
4. Advertising Advancements
Bluetooth 5.1 will have more developments on connection advertisements. This means it will have several connections to announce its presence to all nearby Bluetooth devices. The technology will also help reduce the chances of interference when several Bluetooth devices are in the same area.
What Does A Wireless Mesh Network Do?
A wireless mesh network is a network device formed by several wireless radios with software that helps them work harmoniously without coordination. This technology is different from traditional networks, as it has no central coordination or computer to handle all the network traffic. Instead, the devices communicate with each other easily and efficiently.
The wireless mesh network has wirelessly connected routers, which act as wireless access points for its customers, such as smartphones and laptops.
These routers are connected via a backbone that resembles a mesh-like structure. For the customers to send or receive information, this mesh-like backbone network is used. The routers also help these clients to access the network.
To connect to the internet, an external network, you must connect some routers to a wired network. These routers help in acting as gateways.
Types of Wireless Mesh Network
This technology is divided into two topologies;
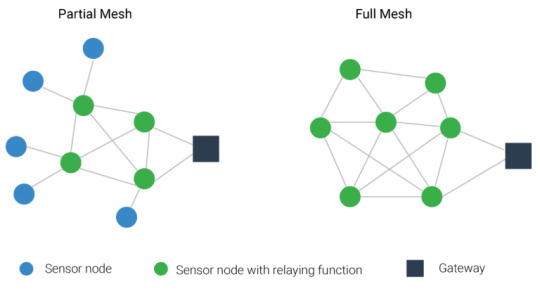
· Partially-connected mesh network
· Fully-connected mesh network
Fully-connected is the one that creates a mesh-like pattern of network connections. In this technology, all nodes are connected to each other and communicate harmoniously. Also, the nodes must cooperate as they distribute information.
In partially-connected technology, some nodes will be inter-connected, and they communicate through hubs and switches.
The figure below shows how a wireless mesh network works in the process of sharing the internet.
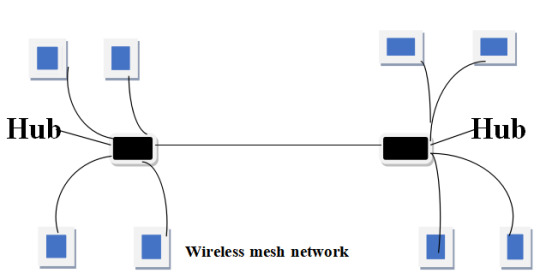
As you can see in the figure above, only one node is required to be wired to the internet in a wireless mesh network. It then shares an internet connection with all the nodes near it wirelessly. So, all these nodes require a power supply like solar panels or batteries but not wires to function outdoors.
Do Mesh Networks Really Work?
Yes. Mesh networks function perfectly in connecting the entire city to a network. It does this through wireless, reliable, and existing technology.
Unlike traditional networks, which rely on wired technology to connect users, wireless mesh networks rely on several wireless mesh nodes to connect users in a whole city to a network.
Advantages of Mesh Network
1. It’s Scalable
Every node in the mesh network acts as a router. It’s, therefore, not necessary for additional routers. So, you can conveniently increase the size of your network, depending on your needs.
For instance, if you want to add some desktops and smartphones to a meeting room, you can do it easily. The best part is the added gadgets will connect to the network automatically.
You can also add light sources to your conference room or other additional offices quickly as you control the whole network system without requiring extra management.
2. Can Easily Resist Problems
Another advantage of a mesh network is its self-healing capability. If one node stops functioning or loses the signal, it doesn’t affect the entire networking process. Other nodes can easily complete the mesh as the failed node heals itself.
The reason behind this healing is the capability of each node to send, receive, and translate information. The redundancy created in the process helps in keeping the nodes running even if one of them fails.
3. It’s Affordable
Generally, mesh networks use a few wires. This means that the installation cost is low. So, even if you want to set up a network that can cover a large area, you can easily afford it.
4. It’s Easy to Add A Range
You can easily add a range that you want your mesh network to cover. You simply do this by adding more nodes or connecting some of your nodes to gateways.
5. It’s Convenient
Mesh networks are suitable where there are no Ethernet wall connections. For instance, if you have a concert in an outdoor venue, this network is more appropriate. It’s also convenient in almost all transportation settings.
6. It’s Self Configuring
As said earlier, you can increase the number of nodes of a mesh network if you want to increase the range it’s covering. In this case, the added nodes don’t require any network administrator to adjust the network for them to work.
The network incorporates them automatically as they are self-configuring.
7. It’s Easy To Install
Normally, the nodes in mesh networks are easy to install and uninstall. This makes it easy to change the coverage area, depending on your requirements.
Disadvantages of a Mesh Network
1. Complicated Initial Network Set up
Setting up a mesh network from scratch can be very complicated and tedious. Establishing the perfect place to set up each node is also complex and time-consuming as you have to install them where there’ll be no latency problems. But once you’re done with the initial set up, it’s easy and quick to add more nodes.
2. Consumes More Power
Each node in a mesh network acts as both transmitter and receiver. For this reason, the nodes strain as they try to play both roles. So, for them to operate effectively, more power is needed.
This might be a small issue for large nodes as they are wired to the electrical system directly, unlike the small battery-powered ones.
3. Latency Problems
Latency is the time a message consumes to move from each node to the gateway. This time can affect the entire mesh networking setup. You can easily improve the latency issue by using a mesh network with additional memory, power, and bandwidth.
However, for low-power, wide-area networks, latency becomes a major problem for mesh networks.
4. Complicated Workload
Mesh networks are highly scalable and require adding more nodes depending on the needs. Complications arise when you have latency problems, and you’re required to add more nodes to help solve the problem. The entire network planning becomes more difficult as you have to deploy various equipment types for the network to function properly.
What Makes Bluetooth Mesh Different
The Bluetooth mesh makes home automation better than other wireless networks, especially WI-FI. Even though you can turn on your house power with your smartphone or laptop with WI-FI, Bluetooth mesh offers a better experience.
You can turn on your entertainment system, air conditioning, or alarm system by just opening your front door. This is enabled by Bluetooth mesh technology.
Also, Bluetooth mesh is less expensive and more efficient than other wireless technology like WI-FI. For instance, the technology has made tracking of devices simpler and has also enhanced wireless security.
Other traditional wireless networks are not convenient when communication is among many people. WI-FI makes the problem worse as high power is needed to make a WI-FI signal cover a wide area. In such cases, Bluetooth mesh technology is effective as devices connect to each other and pass information from one device to another, forming a communication web.
Conclusion
Bluetooth SIG mesh is a computer networking that allows communication to take place between many-to-many communiqué devices. It also allows thousands of nodes to communicate efficiently without any connection but within the same network. It is a reliable method of sharing information in large networks as compared to other wireless networks.
This test is from https://www.mokoblue.com/what-is-bluetooth-sig-mesh/,if you would like to learn more,pls feel free to contact us!
0 notes
Text
The Emergence of Bluetooth 5.0
Do you know that it took more than 15 years since the introduction of the Bluetooth technology for Bluetooth 5.0 to emerge? Bluetooth is found in almost every device, from smartphones and smartwatches to wireless headsets and wireless mice. The latest versions have great additional features that are unsupported by older versions. This article will explore the difference between Bluetooth versions, specifications of different Bluetooth versions, ranges of Bluetooth devices by class, and reasons you should update your Bluetooth to version 5.2.
Bluetooth versions' main differences are that the most recent Bluetooth versions provide a high data transfer speed. Their connection range and stability are great, more energy-effective, and offer improved security than older Bluetooth versions.
Bluetooth Classic: Version 1.0 – 3.0
We have 3 factors that enable someone to distinguish the different Bluetooth versions. They are power consumption, range, and data speed. Data packets used and modulation schemes are the primary determinates of these factors. The first Bluetooth version's release paved the way for the emergence of wireless items such as speakers, headphones, and game controllers used today.
Bluetooth Low Energy: Versions 4.0 – 5.0:
Bluetooth 4.0 was announced to the marketplace forming a new grouping named Bluetooth Low Energy (BLE). It was geared towards installing applications that require low power consumption and a GFSK modulation scheme that would enable it to return insufficient data output of 1Mbps. Even though its maximum data output is 1Mbps, BLE is still unsuitable for products that need continuous data streaming.
Specifications and Features from Bluetooth 1.0 to Bluetooth 5.0
a) Bluetooth 1.0
It was invented in 1998 was a significant groundbreaking discovery. As the technology was somehow immature, challenges such as no anonymity were encountered, but the technology is now outmoded with today's standards.
Some of the minor challenges were fixed by Bluetooth version 1.1, but the most significant problems were fixed after Bluetooth version 1.2. Significant improvements included sustenance for adaptive frequency-hopping spread spectrum (AFH) that minimized interference, quicker speed transmissions of close to 721kbit/s, Host Controller Interface (HCI), improved discovery, and Extended Synchronous Connections (ESCO).
b) Bluetooth 2.0
This version 2.0 was released in 2004. GFSK and phase-shift keying modulation (PSK) are some of the main improved features in this version. The role of GFSK is to improve the speed of data transfer by supporting the Enhanced Data Rate (EDR).
The technology improved further after the launch of Bluetooth version 2.1 by supporting a new feature dabbed "simple, secure pairing" (SSP). It enhanced the pairing experience, security, and extended inquiry response (EIR), thus allowing improved devices' filtering before establishing a connection.
c) Bluetooth 3.0
This Bluetooth version was announced into the market in 2009. Over a collocated 802.11 link, the Bluetooth 3.0 through the High Speed (HS) mode enables transfer of data with speeds of up to 24 Mbps. The Bluetooth version 3.0 comes with other new specifications such as Ultra-wideband, Enhanced Power Control, L2CAP Enhanced modes, Unicast Connectionless Data, and Alternate MAC/PHY. Its high rate of power consumption has significant drawbacks.
d) Bluetooth 4.0
Bluetooth version 4.0 was released in 2010. Back in those days, the version was marketed as Bluetooth Smart and Wibree, although it still supported all the previous versions' features. BLE devices are powered by coin-cell batteries making power consumption its significant change.
e) Bluetooth version 4.1
Bluetooth version 4.1 was released in 2013, hence improving the users' experience further. This version enabled easy transfers of bulk data. It also allowed multiple simultaneous roles and co-existed with LTE.
Other new features supported by this version include:
· 802.11n PAL
· Minor duty cycle directed publicizing
· Partial time of discovery
· L2CAP Connection
· Dual-mode and topology
· LE link-layer topology
· Comprehensive interlaced scanning
· A fast interval of data advertising
· Mobile wireless coexistence signaling services
· Wideband speech from audio architecture updates
f) Bluetooth version 4.2
After the release of Bluetooth version 4.2 in 2014, it made it possible for the release of Internet of Things (IoT). Its main area of improvements includes:
· Link-layer privacy that extended the policies for scanner filters
· Low energy secure connection that extended the length of Data packets
· Version 6 of the Internet Protocol Support Profile (IPSP)
g) Bluetooth 5.0
The version was presented by Bluetooth SIG in 2016, although it was Sony in their product Xperia XZ Premium who first implemented this technology. Both Bluetooth 5 vs. 4.2 primarily focused on refining connectivity and experience of the Internet of Things (IoT), thereby offering a unified flow of data. Between Bluetooth 5.0 vs 5.1, the Bluetooth 5.1 range is a bit higher. Its main areas of improvements include:
· Slot Availability Mask (SAM)
· Extensions of LE Advertising
· 2 Mbit/s PHY for LE
· LE Channel Selection Algorithm #2
· Long-range LE Long
· Non-Connectable advertising high duty cycle
h) Bluetooth version 5.1
Bluetooth 5.1 was unconfined in 2019. When Bluetooth 5.0 vs. 5.1 are compared, the version 5.1 which was the first to support the Mesh-based model hierarchy. Its main improvements areas are;
· The angle of Departure (AoD) and Angle of Arrival (AoA)
· GATT Caching
· Periodic Advertising Sync Transfer
· Advertising Channel Index
Bluetooth Version 5.2
The latest Bluetooth version 5.2 was introduced by the Bluetooth SIG during the CES 2020 which was held on January 2020. This version was introduced into the market alongside the next generation of Bluetooth LE Audio. The most significant change made between Bluetooth 5.1 vs. 5.2 was that the version 5.2 has Isochronous Channels (ISOC). Isochronous Channels supports BLE devices with Bluetooth 5.2 or later where it acts as the base during the implementation of LE Audio. Other 3 features that comes with Bluetooth version 5.2 are;
· Isochronous Channels (ISOC)
· Enhanced Attribute Protocol (EATT)
· LE Power Control (LEPC)
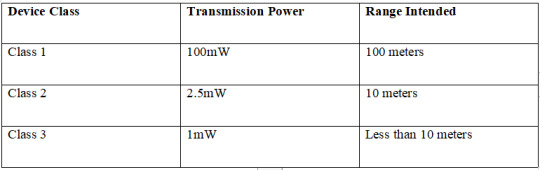
Bluetooth devices Ranges by class
Bluetooth devices have 3 classes that compromise 3 standard anticipated ranges. Class 1 devices have a range of 328 feet or 100 meters, transmitting at 100 mW. Class 2 devices have a range of 33 feet or 10 meters, transmitting at 2.5 mW, whereas the range of Class 3 devices is less than 10 meters transmitting at 1 mW.
These are the anticipated ranges, where they can radically decrease due to an obstacle between the two devices, for instance, walls that weaken signals. Therefore, the transmitter's strength, the device's proximity obstruction, and the receiver's sensitivity are the most common factors influencing the range of Bluetooth devices.
Difference between Bluetooth 5.0 and 4.2
When New Bluetooth versions are used with compatible peripherals, they come with improvements. Before the invention of Bluetooth 4.2 back in 2014, the other major version of the standard, Bluetooth 4.0, was in 2011. On the other hand, Bluetooth 5.0 is configured with far better improvements than previous standards (Bluetooth 4.0 & 4.2). The specifications of Bluetooth 4.2 features are ratified. Hence it can be supported by everything ranging from mobile phones to beacons. The table below will highlight the typical basic features that differentiate Bluetooth 5.0 and Bluetooth 4.2 versions.
Features or Specifications

Can Bluetooth 4.0 connect to multiple devices?
The Bluetooth version 4.0 specification has two modes of devices; dual-mode devices and single-mode devices. All passive Bluetooth 4.0 devices can implement both or either of the ways. The classic mode (BR/EDR) and Low energy mode are the two Bluetooth version 4.0 modes.
To the question, A single-mode low-energy-only device cannot connect to classic mode devices. A dual-mode Bluetooth version 4.0 device can connect with several Bluetooth Low Energy (BLE) devices.
Difference Analysis on Bluetooth 4.0 vs. Bluetooth 4.1 vs. Bluetooth 4.2
New standards that add new features or more Hardware resources required for running more complicated protocols and algorithms are issued by the SIG each year. Hence, without the latest software, it becomes tough to eliminate old natural hardware. The main differences between the 3 versions are;
Bluetooth 4.0 vs. Bluetooth 4.1
1. Increased rate of data transfer
The Bluetooth version 4.1 has a single packet data of 20 bytes, while Bluetooth 4.1 has a maximum transfer maximum of 23 bytes. This raises the rate of data transfer by 15%. Modifying the transmission rate of 23 bytes when the chip is supporting Bluetooth version 4.0 is irrelevant as it drops the packet or complies with an error.
2. Master-slave coexistence
The Bluetooth version 4.2 has an updated link-layer topology that allows concurrent master-slave coexistence and topology with master-to-multiple slave connection.
3. Supports the 32-Bit UUID
The broadcast packet carries a 32-Bit UUID. This UUID is not about the attribute list that has the 16-bit and 128-bit. To obtain the full 128-bit UUID on Bluetooth version 4.1, you only need to broadcast the 32-Bit UUID mapping as it increases the active broadcast data length in a broadcast packet.
Bluetooth 4.1 vs. Bluetooth 4.2
1.LE connection security
The AES-CCM encryption bases the specifications of pairing encryption links of Bluetooth versions 4.0 and 4.1; because Bluetooth 4.1 stocks the identical key, some dangers, and vulnerabilities might be cracked. The Diffie-Hellman Key Exchange algorithm encrypts the pairing link of Bluetooth version 4.2. Every Bluetooth 4.2 device has two keys; a private key and a public key. The users' private key and the other party's public key encrypts the encrypted file, while the receiver decrypts both the transmitting party’s private and public keys. This effectively prevents the intermediary from key event cracking.
2. Privacy protection
Bluetooth continuously broadcasts a Bluetooth device address with a unique Bluetooth Mac address. The address is essential to some applications, for instance, logistics tracking app which fixes logistics equipment as stated by Bluetooth device address.
3. Improved data transmission rate
When it comes to transmission of single packet data, Bluetooth version 4.1 supports up to 23 bytes, whereas Bluetooth version 4.2 provides up to 255 bytes, thereby improving the rate of data transmission.
Is Bluetooth 4.0 the same as BLE?
Bluetooth version 4.0 rebranding by the group controlling technology helped individuals differentiate Bluetooth Smart and Bluetooth Low Energy. The Bluetooth SIG stated that version 4.0 devices would be called Bluetooth Smart Ready and Bluetooth Smart to distinguish the products featuring this technology.
Bluetooth Smart will characterize a new class of Bluetooth 4.0 peripherals. It features sensor-type devices such as pedometers and heart-rate monitors specially made to collect unique data. Meanwhile, devices using dual-mode radios referred to as Bluetooth Smart Ready can handle both the Bluetooth 4.2 BLE technology and classic Bluetooth capabilities, for instance, connecting to a hands-free device or transferring files.
Why you should Update your Bluetooth to 5.2
Since the introduction of Bluetooth 5.0 in December 2016, the technology has become more user-friendly and advanced. The Bluetooth SIG introduced into the market a radical Bluetooth version 5.2 receiver known as Bluetooth LE Audio on 7 January 2020. The version is modified with an LE Audio that enables multiple devices to share data. However, it has a limit of two devices where files can be transferred from a phone, tablet, or computer. Also, the LE Audio gives a better audio experience to individuals with hearing problems. Some of the technical specifications of the latest Bluetooth Version 5.1 vs. 5.2 are;
Enhanced Attribute Protocol (EATT)
A combination of enhancements to the Generic Attribute profile and an upgraded version of Attribute Protocol (ATT) lead to the birth of Enhanced Attribute Protocol (EATT). This new protocol enables end-users to reduce end-to-end latency with development in the sensitivity of applications.
Low Energy Power Control
Bluetooth 5.2 devices have an LE Power control that exercises an essential part in improving transmission power when two devices are connected. They can also enthusiastically demand transmission power changes to lower power usage and trade-off the signal's quality.
Some benefits of LE Power control are;
Less power consumption.
It enhances the receiver signal dependability.
Growth of existing and upcoming wireless devices
Low Energy Isochronous Channels
Improved quality of sound hearing aids has been made promising by the introduction of Low Energy Isochronous Channels. The Isochronous Channels have made broadcasting and connection of sound to multiple devices possible. Also, multi-language audio systems have been developed due to this technology.
a) Low Energy Audio
LE Audio transmits sound data on low-energy spectrum devices. A new compression algorithm is used to maintain the Bluetooth's quality.
b) LC3 – Low Complexity Communication Codec
LE Audio encompasses the new low robust and high-quality audio codec LC3. With better audio high-quality and less power consumption, inventors now have a colossal elasticity as they can design new wireless merchandise easily.
c) Hearing Aid Improvements
Many individuals have benefited from Bluetooth technology, where wireless calling has made driving safer. Productivity has increased as people can take calls while driving to the office or home.
How to tell your Smartphone's Bluetooth version
Recognizing the Bluetooth version supported by your smartphone is essential. In case the latest Bluetooth standard version is installed in the devices connecting to your smartphone, its performance and efficiency will be great with less interference.
Therefore, before heading into a shop to buy Bluetooth accessories, here are methods that can help you to know the Bluetooth version of the accessory
Method 1: How to check the Bluetooth Version of an Android Phone:
· Step 1: Enable the device's Bluetooth and tap on "Settings."
· Step 2: Select the "ALL" tab in the application
· Step 3: Select Bluetooth share on the Bluetooth icon.
· Step 4: Check the Bluetooth version on the Application Info.
However, first, enable the Bluetooth's power for this step to work effectively, or else the Bluetooth version info won't show on the application.
Method 2: Check on the device Specification sheet
Method 1 doesn't work for several devices, and in case it doesn't work for you, read the device's specification sheet to find its Bluetooth version. An all-inclusive database of smartphone specifications is available at Gsmarena, where a phone's Bluetooth field can be searched.
Method 3: Install an Application of Bluetooth checker
On the other hand, the process can be more straightforward by installing a Bluetooth version checker on your device. Go to the google play store and find the best app, then do a quick search.
AIDA64 is the most recommendable application. You only need to download and install the application on your smartphone, tap on "system," and scroll down to the Bluetooth row.
Link in https://www.mokoblue.com/bluetooth-versions-5-0/ to learn more about bluetooth products with different version.
0 notes
Text
What is Beacon Frame Format
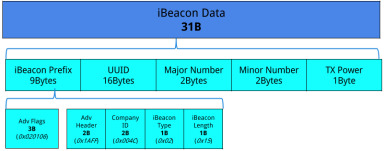
A beacon is a small, wireless device that sends signals to and receives signals from other smart devices around it. Using low-energy Bluetooth, this wireless transmitter broadcasts a radio signal with a series of letters and numbers, then transmits them at short but regular intervals within a range of approximately 70 meters.
The signal broadcast by a beacon is in a format type known as beacon format. The beacon format is a communication protocol that contains the peculiarities of a beacon. Usually these information are a string of numbers and characters put together as the beacon’s signal.
What is Beacon Frame
A beacon frame is a management frame that is prevalent in IEEE 802.11 based Wireless Local Area Networks (WLANs). The IEEE 802 is a set of Local Area Network (LAN) technical standards that specify the set Medium Access Control (MAC) and Physical Layer (PHY) protocols used for implementing a Wireless Local Area Network (WLAN) computer communication. These standards are created and monitored by the Institute of Electrical Electronics Engineers (IEEE) LAN Standards Committee, hence, IEEE 802.
Before a frame can be transmitted, every network information needed by a station must be input in the broadcasting beacon frame. These frames are used to communicating and synchronizing devices present in a WLAN. In other words, all the devices in a beacon frame format, all the connected devices communicate with each other through the AP to confirm the channel or station status.
How Often Are Beacon Frames Sent?
The interval between two concurrent broadcasted beacon frames in a beacon is its beacon interval. Beacon intervals are typically measured in Time Units (TUs); each Time Unit (TU) is equal to 1024 microseconds. Therefore, one can approximate the default period between beacons to be 100 milliseconds. This interval is usually configurable to be higher or lower on many beacon devices like the MOKOSmart W1 Wearable Beacon.
Functions of Beacon Frame
There are several functions of the beacon frame in WLAN.
· The most critical significance of beacon frame is that it announces network availability to other devices. In other words, the primary function of beacon frame is to advertise the presence of an AP at a particular location while also providing the details of such network viz-a-viz its capacity, configuration and security information to the network's connected devices.
· Apart from this, beacon frame is also used to maintain tasks and synchronize data between connected devices and the network.
· Beacon frames are usually transmitted at intervals in order for mobile stations (smartphones, wearables, laptops, etc.) which are connected to the network to find the network, identify it, and connect to it afterward.
General Beacon Frame Format
Generally, a beacon frame format comprises the 802.11 Medium Access Control (MAC) header, a body, and a Frame Check Sequence (FCS), also known as the trailer. Usually, beacon frames are created by the MAC server, which has its address as that of the frame address as well. And when frames are sent through the access point (AP), the AP deploys its wireless interface and converts it to the transmitter address. The address of the AP’s interface is the BSSID. Subsequently, beacon frames get sent to the client – which is the receiver and destination.
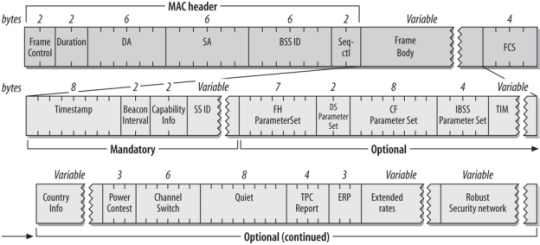
Components of a Beacon Frame
The header consists of beacon information related to where the frame is going, the cipher suite used for data frames encryption, the data rate, and so much more. Four address fields – source, destination, transmitter, and receiver – are the components of a Bluetooth beacon format header.
The body of a BLE beacon frame consists of the beacon information, which is enclosed and secured. The size of the body of a frame strongly depends on the amount of transmission done.
The trailer comprises a 32-bit Cyclic Redundancy Check (CRC), that works with Frame Check Sequence (FCS). This sequence is used to validate the content of the beacon frame to understand whether they have not been tampered with or corrupted during transfer. All the values got from the frame header and body are run through a calculation, and their results are subsequently stored in the FCS field.
Mandatory Fields in a Beacon Frame
The significant fields in the body of a beacon frame include:
Timestamp (8 bytes): which is the time in reference to the beacon frame used by connected devices to synchronize with the WLAN.
Beacon Interval (2 bytes): which is the time interval between two consecutive beacon transmissions in the frame.
Capability Information (2 bytes): which provides information about the capability of the network or device. It ascertains whether the network type in use is an ad hoc network or infrastructure network.
Service Set Identifiers (SSIDs): which are also known as network names, are primary components of all beacons and a core part of their processes.
Supported Rates: is an 8-octet field defines the channel's transmission rates. This can be found in all beacon types and their processes.
Direct Sequence (DS) Parameter Set (2 bytes)
IBSS Parameter (4 bytes): which is present only in an ad hoc network beacon frame.
Traffic Indication Map (TIM): which is present in only AP-generated beacon frames. The network's AP sends it at intervals, and it is useful in BLE beacon format low power mode.
Contention Free (CF) Parameter Set (8 bytes)
Frequency Hopping (FH) Parameter Set: which is used by legacy FH stations.
Beacon Frame Types
All of the 802.11 beacon frames can be categorized into three types, which are; Management, Control, and Data. Usually, the management frame is the beacon itself, the control frame is a request to send (RTS), and the data frame is a QoS data frame. In the same vein, the management frame is in charge of a frame’s basic service set (BSS), the control frame coordinates the medium access, and the data frame contains layer 3-7 information.
Generally, all these frame types have the same header. However, there is usually a difference in the frame’s body, as it carries more detailed information about the frame type it is a part of.
Eddystone Beacon Format
A ubiquitous beacon format is the Eddystone beacon format (powered by Google) which supports both iOS and Android devices. It can transmit one beacon packet format at a time through three different frame types, namely, Eddystone URL beacon format, beacon UUID format, and beacon TLM format.
The Eddystone URL beacon format transmits a website link (URL) to the connected device. This beacon data format makes it possible to connect outside of an installed mobile app.
The beacon UUID format is a 16-digit linked-up character that recognizes a beacon. For example, the UUID/UID can activate an installed app on your mobile device to initiate a connection to a beacon.
The beacon TLM format allows for beacon data to be communicated between a beacon and a device using telemetry. For example, a beacon's battery level or temperature level can be communicated using TLM.
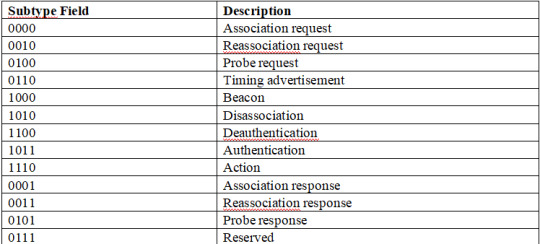
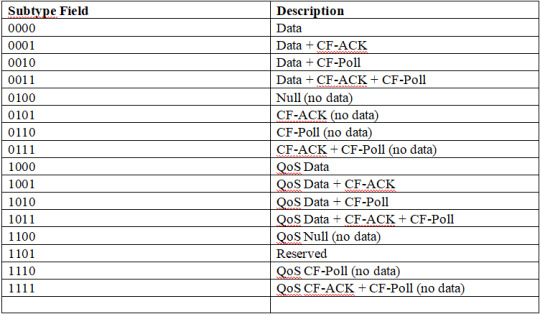
Management Frame Subtypes
In a wireless network, management frames are generally used to control the Basic Service Set (BSS). The management frame controls activities such as probing, associating, roaming, and disconnecting devices from the BSS. In this frame type, the type field 0 indicates management.
For the management frame subtypes, a combination of different numbers between 0 and 1 have various descriptions within the frame header.
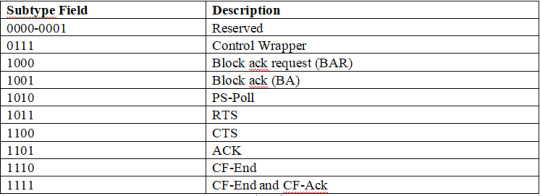
Control Frame Subtypes
Control frames assist data and management frames with their deliveries and are used for frame acknowledgment. A control frame usually has a header and a trailer but does not have a frame body. In this frame type, type field 1 typically indicates control.
For the control frame subtypes, a combination of different numbers between 0 and 1 has various commands.
Data Frame Subtypes
Usually, data frames are used to transfer information or initiate a command which will, in turn, lead to an event. It is important to note that some data frames contain only a header and trailer, but no body.
HCF Controlled Channel Access (HCCA) and Point Coordination Function (PCF) are the types of wireless networks that utilize data frame subtypes.
Specific Service Set Identifier (SSID) of Beacon Frames
The Service Set Identifier (SSID) of a network typically names the network's service set or extended service set. Usually, what the beacon frame does is to broadcast the SSID through beacon packets, and eventually, the presence of a network – in the form of a wireless network name – will be announced and visible to users for a possible connection.
SSIDs usually range from 0 byte to 32 bytes and are usually in a renowned language like English. Unlike the common types of set identifiers, SSIDs usually give room for customization. Before associating with a wireless network, it is essential that a station knows the network's SSID. This information can be either obtained from a beacon's broadcast via its base station or by knowing the SSID beforehand through other means (possibly from a previous configuration) in a case where a base station advertising is absent.
So, when connection is initiated between a device and a network, the device sends the SSID in a probe request. Afterward, a response is sent by an access point on the condition that the SSID in the probe request matches an SSID in sync with the access point. If all these conditions are not met, the access point will not respond to the probe request, resulting in an unsuccessful connection.
Virtual APs and Multiple SSIDs
The concept of SSID in 802.11 does not allow for one AP to connect with multiple IDs because it is a service set identifier initially designed for a single AP and service set at a given time. However, it is no surprise that businesses are beginning to demand for enterprise-class APs that can work with multiple SSIDs simultaneously. For this to be possible, the access point is divided into a number of virtual APs within the same single hardware platform. This is present in modern-day multi-provider spaces like airports, train stations, bus stations, etc.
These Virtual APs copy the operation system of a physical AP with IP layers within a MAC; however, the radio frequency layer is absent.
Any Difference Between a BLE Broadcast Frame and BLE Beacon Frame?
In a Bluetooth Low Energy transfer, communication is usually unidirectional and initiated by a broadcast or advertisement. For instance, in a communication between a BLE beacon and another device close to it, the BLE beacon device broadcast data packets regularly, waiting for the device – which must have scanned for such BLE broadcast and be familiar with the beacon device’s network – to detect the transmitted data packets and connect afterward. In other words, a BLE beacon frame is a distinct payload transmitted within a BLE broadcast frame.
Quite a number of BLE devices function by transmitting advertisements, but except a device is specifically built to work as a BLE beacon, every other BLE devices do not transmit BLE beacon frames. So, beacon frames are only peculiar to BLE beacon devices, despite the fact that there are other BLE devices on the market.
To sum up, a BLE beacon is a special kind of BLE device that is built to emit a broadcast using BLE broadcast frame technology, but its uniqueness lies in the fact that unlike other BLE devices like smartphones, a BLE beacon also transmits its peculiarities via a beacon frame.
For more information about beacon format,pls link in https://www.mokoblue.com/what-you-should-know-about-beacon-frame-format/
0 notes
Text
What is beacons?
Technology enables us to interact with various activities each day without even questioning. I.e., when turning on a car, through flipping on a switch to turn on light bulbs, and when a Wi-Fi signal promptly enables internet browsing. These simple things become connected through a technology called Bluetooth Beacons. In this article, we will discuss the basis of beacons and beacon technology, what beacons are used for, how to make a beacon structure, how they differ from Geo-fencing, and how they can be used concurrently with mobile apps.
What is beacon?
A Beacon is a small device comprising insignificant amounts of data that often transmit radio signals to nearby smart phones and tablets. The time between each movement sent and the signal strength is configured to draw the wanted coverage. Mobile apps are used to snoop the signals broadcast, where they trigger an action on the phone anytime they hear a relevant alert. Beacons can only disclose information to the phone but cannot read; hence they operate in one direction. Most of the data transmitted through current beacons does not change frequency as it is usually hard coded. Once it is set when configuring, it relies on a device that listens to do something intelligent with the information. With the advancements in technology, this is likely to change in the future.
How far do beacons reach?
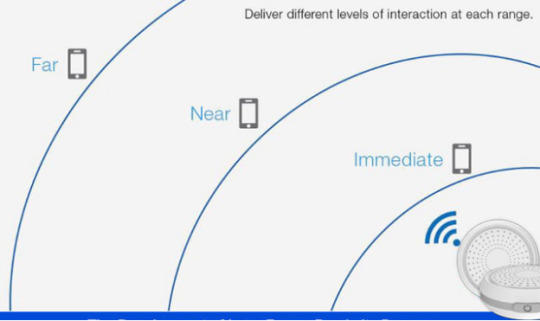
Though Beacons can have up to a range of 70m without any obstructions, walls made of bricks and metals can drop the coverage significantly. Thin stud walls have fewer minor effects. Most beacon portal operates with three distance ranges in which the device does different things with each range. They include;
· Far range distances – They are specially made such that your device can do something when close to hear a beacon, i.e., after walking past a retail shop.
· Near range distances – They are designed to operate when the device is in the same room with the beacon, i.e., walking into a retail shop.
· Immediate range distances– They are made to function once the device is almost close to touching a beacon, i.e., touching the point of sale in a retail shop.
Beacon packet
A beacon packet is the continuous transmission of signals in a beacon network that advertises the base station's presence. It persistently signals any fault condition in a nominal ring network such as FDDI. A beacon packet enables network administrators to pinpoint any faulty node in the system.
Beacon frame
It is a management frame category that detects a basic service set (BSS) designed by several 802.11 devices. A beacon frame comprises network data required by a station before transmitting a frame. Beacon frames are used to synchronize devices and announce the existence of devices in a WLAN connection.
As beacon frames are part of the basic service set, they are also wireless router access points that form the base stations for access. Communication through devices occurs with each other through access points where the beacon frames are periodically transmitted. This enables the devices connected to identify the position of the network channel. Independent basic service sets communicate to other devices based on peer-to-peer, allowing the beacon generation to be distributed among the connected devices effectively. It consists of the body, the IEEE 802.11 MAC header, and a Frame check sequence.
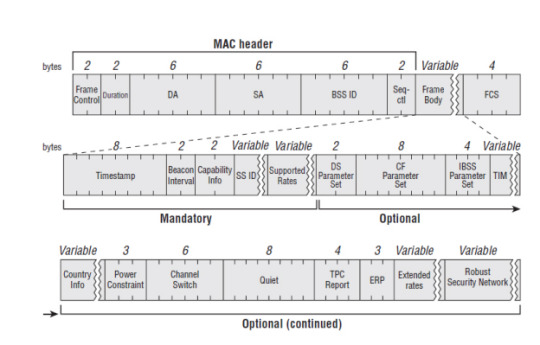
The body of a beacon frame has other vital fields, which include;
· Timestamp − It is the period with which a frame is directly associated with the beacon portal. A timestamp synchronizes a device while in the WLAN connection. It also helps the device to update its local clocks.
· Beacon interval – It is the time recess amid two repeated transmissions.
· Capability information − It comprises all data regarding the ability of the network. The capability information determines if the network used is ad hoc or infrastructure-based.
· SSID – It identifies the service set for networks.
· Supported rates − It expresses the speed of transmission acceptable by the channel.
· Frequency-hopping Limit Set
· Direct-Sequence Limit Set
· Contention-Free Limit Set
· Traffic indication map − It is an electronic image used in IEEE 802.11. A traffic indication map is periodically sent by the access point where it must pay attention to at least one beacon all through the beacon interval.
Types of Beacon protocols
a) Apple Beacon
Apple announced its first beacon protocol, iBeacon, in December 2013. It works with Google's Android and also Apple's iOS. This beacon uses the iBeacon protocol to transmits UUID that has a string of 24 numbers. The UUID communicates with a Mobile App installed.
Pros:
1. Broadly supported
2. Implementing Apple Beacon is easy and simple
3. Consistent performance while working on iOS.
b) Eddystone (Google)
Eddystone was announced in the market by Google in July 2015. Initially, Eddystone was known as Uri Beacon. Beacons that Eddystone supports are specially made such that they can transmit three different frame-types. Eddy stone perfectly functions with both Apple's iOS and Google's Android. A single beacon has enough strength that can send all three Google Eddystone's frame types. The three frame types of Google's Eddystone are:
1. URL - It is a website link transmitted to the device, eliminating the mounted Mobile App's prerequisite.
2. UID – It is similar to Apple's UUID, but UID has a string of 16 numbers that identifies an individual beacon. A UID can efficiently activate an installed Mobile App.
3. TLM – This beacon frame type communicates administrative and sensor data through telemetry.
Pros:
1. It sends out an URL that removes the need for telemetry information and installed mobile apps.
2. Flexible to open and format.
3. Can easily integrate with Google Products.

c) AltBeacon
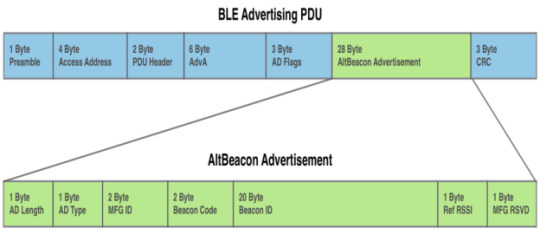
AltBeacon was introduced into the market by Radius Networks in July 2014. The main aim of announcing this open-source beacon protocol was to help overcome the protocols that favor one vendor.
Pros:
1. AltBeacon is an open-source beacon protocol.
2. It is compatible with other mobile operating platforms
3. It is more flexible when using a customizable source code.
d) Geo-Beacon
GeoBeacon was announced into the market by Tecno-World in July 2017. Due to its compact type of data storage, the GeoBeacon open-source beacon protocol is specially designed for Geocaching applications.
Advantages:
1. This beacon protocol is open-source.
2. It is compatible with other mobile operational platforms.
3. Its coordinates are of high resolution.
4. It uses 8 bytes of user data.
Types of power solutions
Power solutions are of 3 types. They are;
1. Battery-powered beacons that use AAA, AA batteries or coin cell batteries.
2. Electricity plug-powered beacons.
3. USB-powered beacons.
Types of location technology
Most beacons apply Ble Beacon technology solutions to effectively communicate with other devices, which is effective as it retrieves the data location. However, besides Bluetooth technology, other location technologies exist in the market. They include;
a) Bluetooth low energy (Ble Beacon technology solutions)
Most beacon location technology relies on Bluetooth low energy technology. Compared with the classic Bluetooth technology, the BLE technology has a lower range, consumes less power, and transmits less data. The Bluetooth low-energy technology is specially designed for sporadic transmissions of minimal amounts of data.
b) Wi-Fi Aware
The Wi-Fi Alliance announced Wi-Fi Aware in July 2015. It is specially made for indoor locations. The rate of power consumption of Wi-Fi Aware is lower in comparison to regular Wi-Fi.
c) Combined technologies
Rather than focusing on merely one beacon technology, most vendors combine several location technologies.
How Do Beacons Work?
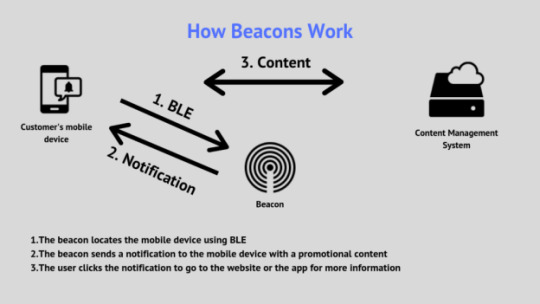
Any signal transmitted by a Beacon has a unique identification number that enables the data Centre (Content Management System) to fathom which device’s content needs to be pushed. These applications on beacon technology are developed so that they suit the requirements of the business.
Beacons are responsible for pushing all the content found on the CMS to the mobile devices by beacons, allowing change of content at any particular time. This is because data is stored in the cloud and not in the application. iBeacon, a protocol developed by Apple, is used to communicate, making it possible to transmit small amounts of data. Also, Google has developed Eddystone, which is an alternative to iBeacon.
Communication in these devices happens through Bluetooth Low Energy, a power-efficient disparity of the Standard wireless Bluetooth. The BLE technology enables beacons to work for almost 24 months using a coin cell battery. Most modern portable devices such as smart watches, smartphones, and tablets are installed with BLE chips.
The mobile phone is the last element in this chain. It receives contents in the form of notifications from the beacon. Customers are always directed into the seller’s application whenever they click on it. In case the device has no application installed, the customer can use the web to view the content.
Beacons Communication Mode
For effective communication, beacons use the Consultative Committee for Space Data Systems (CCSDS). The (CCSDS) telecommunications service is also used in the uncommunicated spacecraft through the deep space network. It is mainly designed to transmit the spacecraft's telecommunications status and its health information. It uses a simple signal that is easily detectable with a moderately-sized projection. Also, the beacon mode permits spacecraft to link with each other daily, letting one spacecraft to performance as an information proxy for the other.
The CW tone is transmitted using the CCSDS tone beacon mode that configures the transceiver. Besides, it is used as an indicator for other spacecraft when transferring data to an artificial satellite. However, its crucial role is to convey the health information of spacecraft. While using the four exceptional CW frequencies with 16 probable tones, it can address multiple spacecraft. UHF frequencies cannot be used in the outer solar system, but instead, the required technique is transmitted through a programmed backup transmitter. Outside the beacon mode service, spacecraft can retort to any transmit configurations that are compatible within force artificial satellites.
What data do beacons send to phones?
Beacons never convey any significant data. Alternatively, they convey short identifiers where the mobile app makes good use of the data sent and does something useful. For instance, the mobile app detects a broadcast of short numbers using a beacon, then converts the numbers into messages after connecting to the internet. Later, it triggers a push note to the receiver. With no internet, beacons can also send push notes but only of those with short characters. In short, beacons are replica devices that publicize temporary identifiers.
Theoretically speaking, beacons transmit an insignificant amount of customizable data and less data comprising a unique identifier. The identifier notifies the mobile app to twitch listening and does something that gives extra information for processing. The identifier is made of three parts; a "UUID," which is the identification document of the beacon vendor, and a "Minor" and "Major" identification documents, which are made to indicate different regions. All the data transmitted is unencrypted in a broad publicized format. This ensures there is standardization between platforms and manufacturers. To ensure that there is nothing sensitive transmitted over BLE, mobile apps should first understand this feature.
Can beacon work without an app?
An app must be configured to a particular beacon, although some transmission modes are specific to certain manufacturers. All beacons convey data using the same setup; hence they are interchangeable. For the mobile app to respond as planned, it must identify the beacon it is listening to; every beacon manufacturer has a set of tools available to assist in this process.
What can I track with beacons?
With the evolution of the Bluetooth Low Energy beacon technology, new and innovative ideas have been set by service contractors. This influences the aptitude to track people and assets at service locations and in workplaces. Beacons are used in numerous diverse surroundings in which security workers and janitorial operate. Some of the items trackable by beacons are;
· Roaming of mobile devices.
· Proximity detection of roaming assets.
· Fixed BLE receivers tracking
· Piggy-backing off the location of a mobile device.
· Augmenting a BLE solution with GPS, Geo-fencing, or Wi-Fi
· Tracking requests for things like payments
Timeline of Beacon technology
As it is now clear on what beacon technology entails and how it works, next, we will cover when the beacon technology was first technologically advanced and how it has been adopted worldwide.
On June 10, 2013: - During the Worldwide Developer Conference, Apple introduced iBeacon as part of iOS 7.
From September 1 to November 10, 2013: - Titan mounted 500 beacons in Manhattan telephone booths for maintenance.
On December 6, 2013: - Apple installed 254 beacons in their United States shops hence providing clients with in-store notices about deals, stuff, and product reviews.
On July 31, 2014: - More than 50 of the leading 100 United States stores examine beacons in their shops.
On August 12, 2014: - 3 UK retail shops test beacon technology in their dummies to provide prices and links to clients' online purchases when they cross the threshold of the beacon's 50-meter range. By then, clients had to download a mobile app to attain the beacon's data. Also, customers were tracked on how long they spent searching for an item and their purchase method to form a more precise and custom-made marketing strategy.
On September 29, 2014: - The single most significant bacon technology bid in retail to date happened when over 4,000 devices were installed in their shops.
On November 21, 2014: - The blue-dot indoor navigation is successfully implemented by Aruba Networks using beacons. It offered economic and inferior maintenance substitutes to Wi-Fi for indoor steering.
In early 2015: - The largest apps with the most download, such as Shazam and Facebook, joined beacons into their functionality.
On July 14, 2015: - Google introduces Eddystone into the market, a podium-agnostic contestant to Apple's iBeacon. Eddystone was planned to offer location-based content to smartphones. Being well-suited across platforms, Eddystone aimed at encouraging inventors on how to toil with beacon technology.
On April 14, 2016: - Google announced Eddystone-EID. When connected to a beacon, it turns the phone on into an encoded mark, hence safeguarding users when clicked.
In late 2016: - With users required to download apps to obtain propinquity marketing from beacons, its popularity in retail began to stand.
In Aug 2017: - The beacon technology was set by Bluetooth as the Internet IoT foundation.
Late 2017 - Present: - Google pilots the Beacon Project.
Beacon use cases
Beacons have several uses. They include:
a) Pointing out location
Beacons help to point to your physical space offering precision down to a meter. Geofence is a bit precise with a range of up to 5 meters, although it does not work indoors.
b) Engagement
When used with smartphones, beacons trigger various functions such as lights turning on anytime you enter into a room, Coupons sent to your phone once you enter into a shop. Beacons trigger an event depending on the business case. Also, beacons are loyalty programs of clients; they assist in rewarding customers who make purchases.
c) Navigation
With traditional geofence technology, there is no way to locate someone indoors, but beacons are ideal for finding people indoors. Beacons can perform perfectly well indoors the same way Google Maps does for the outdoors. They describe where someone is heading to either in stores, bus stations, or museums.
d) Analyzing & Data Collection
Beacon accuracy enables an individual to collect more reliable information than Wi-Fi signals or from GPS. They allow shop owners to learn how and where clients are moving throughout the shop. Although beacons do not gather information by themselves, they use proximity podiums like Bleesk to collect significant clients' metrics through an app. Some of the collected data can expand the product listings, improve the clients' journey, modify imminent marketing campaigns, and boost in-store alterations.
e) Asset & People Tracking
Beacons can help to acquire information from more practical cases. I.e., In the transport and manufacturing sectors, managers can use beacons to know the precise location of where the products are at any given time.
f) Interaction
Beacons can automatically send notifications to mobile app users and property owners regarding a safety issue. I.e., They assist patients in heading to the right or warns factory workers of scary changes. Also, beacons can be joined with geofencing to add a coat to information security.
Steps to make a beacon structure
1. First Layer of the Pyramid – To form the first layer of the pyramid, align 81 blocks of either gold, iron, emerald, or diamond in a structure of 9x9.
2. Second Layer of the Pyramid – To form the second layer, place 49 blocks of either gold, iron, emerald, or diamond in a 7x7 structure.
3. Third Layer of the Pyramid – To create the third layer, align 25 blocks of either gold, iron, emerald, or diamond in a 5x5 structure.
4. Fourth Layer of the Pyramid – To make the fourth layer, place 9 blocks of either gold, iron, emerald, or diamond in a 3x3 structure.
5. Insert a Beacon at the Center – At the center of this structure; insert a beacon at the center. This displays a vertical beam of light that appears to be going up to the sky.
6. Expose the Beacon Menu – Opening the Beacon menu reveals the 5 options of primary power, including Jump Boost, Haste, Strength, Resistance or Speed, and Regeneration as the secondary power option.
7. Organize the Beacon - Add 1 gold, iron, emerald, or diamond into a vacant box, then select a status effect for primary power, either Jump Boost, Haste, Strength, Resistance, or Speed. Then choose regeneration as the secondary power. After configuring the beacon, click on the green checkmark button.
8. Beacon Status Effects – In this last step, the beacon displays the given primary and secondary power status effects. The status effects start at 16 seconds, ticks down, and then resets back again to 16 seconds. This enables players within the beacon range to continuously receive the selected primary and secondary power status effects.
Pros and Cons of Beacon Technology
Pros
· Beacons have significant value factors and price in comparison to other technologies.
· They are easy to implement and use.
· Beacons have several applications such as navigation, engagement, navigation, and analysis.
· Enables one to understand clients well by gathering the clients' behavior information.
· Enables one to retarget clients even after they walk away from the shop.
· Beacons work in various verticals, including retail shops, events, offices, education, airports, hotels, culture, etc.
Cons
Clients are usually put off by organizations having entree to their information. Although most customers are conscious that organizations possess their data, clients do not like to be stunned by how much the organization knows regarding marketing communications.
· Beacon marketing is restricted to Bluetooth Low Energy signal. Hence, in case a client does not have an enabled Bluetooth, the beacon technology cannot in any way detect them.
· Most beacon brands rely on installed mobile apps for the beacon technology to effectively transfer data to the client's device.
How are beacons different from Geofencing, NFC and Wi-Fi?
Beacons Vs. Geofencing
Beacons and Geofencing mainly vary as beacons use Ble Beacon technology solutions to enhance communication with smartphones, while geofencing uses GPS signals. GPS has a significant effect on the client's mobile device's battery life as it needs satellites and cell phone towers to identify the precise location. When compared to geofencing, beacons are more exact and works relatively well indoors. Geofencing works better for propinquity marketing outdoor and does not work indoors.
Beacons
Geofence
Battery
Consumes less power
Consumes moderate power
Range
It has a range of up to 230 feet or 70 meters
Its range has no limit
Accuracy
It has a low accuracy of up to a meter
Has a high accuracy of close to 5 meters or 16 feet
Cost
Low
Low cost with no infrastructure
Best For
Ideal for indoor locations, indoor Campaigns, customer analytics, and loyalty
Suitable for outdoor areas, outdoor campaigns, and customer analytics
Beacons vs. Wi-Fi
Beacons and Wi-Fi are similar to each other. Both of their routers can send radio signals easily detectable by a mobile device to pinpoint and deliver a propinquity campaign. However, beacons and Wi-Fi vary hugely as beacons routers are cheaper compared to Wi-Fi routers. Conversely, most shops, malls, and offices have at least one Wi-Fi router. Thus, no setup cost is involved during the installation process. As the beacon device's price is lower, most organizations prefer using more than one beacon hence acquiring more accurate data regarding the client's location and sends authentic propinquity marketing campaigns. Wi-Fi propinquity marketing campaigns do not offer this kind of accuracy.
Beacons
Wi-Fi
Battery
Beacons use batteries to operate
Wi-Fi uses AC hence does not work with batteries
Range
Have a range of up to 230 feet or 70 meters
Has a range of up to 33o feet or 100 meters
Accuracy
It has a low accuracy of up to a meter
Its accuracy is a bit high (1-5 meters)
Cost
Cheap
Relatively expensive
Best For
Ideal for indoor locations, indoor Campaigns, customer analytics, and loyalty
Suitable for indoor Campaigns, basic customer analytics, and loyalty
Beacons vs. NFC
Beacons and NFC mainly vary in that beacons use batteries to operate, whereas NFC does not require any battery to operate. Also, NFC tags are a bit cheaper than beacon devices, although NFC provides limited data regarding the clients' behavior and only works when selected.
Beacons
NFC
Battery
It uses batteries to operate
Requires no battery to operate
Range
It has a range of up to 230 feet or 70 meters
It has a range of a few centimeters
Accuracy
Has an accuracy of up to a meter
It has an accuracy of a few centimeters
Cost
Very cheap
Relatively cheap
Best For
Ideal for indoor campaigns, Indoor location, loyalty, and customer analytics
Best for commitment, security spot check, and delivering information at a go
If you would like to learn more about beacon,then link in https://www.mokoblue.com/what-is-beacon/
0 notes
Text
The Definitive Guide on Bluetooth Sensors
How Bluetooth Sensors Transmits Data
At the moment, the world has been made more brilliant by the rapid advancements in technology. New devices and ideas have risen continuously, thereby improving the prevailing technologies and generating new market sections. Similarly, Bluetooth technological advances have contributed to the birth of Bluetooth Low Energy (BLE), also referred to as Bluetooth Smart. The Bluetooth Low Energy is a short-range, low-power with a less-data-rate wireless communication protocol developed by the Bluetooth Special Interest Group (SIG). Its encrusted protocol stack is designed in such a way that it competently transfers insignificant amounts of data with less consumption of power. Due to this, Bluetooth Low Energy is the most preferred wireless protocol for battery-operated applications. This article will explore the technical features of a Bluetooth sensor, how to connect and use Bluetooth sensors, how Beacon sensors can be used for business, and how to read and control sensor data in Arduino using Bluetooth.
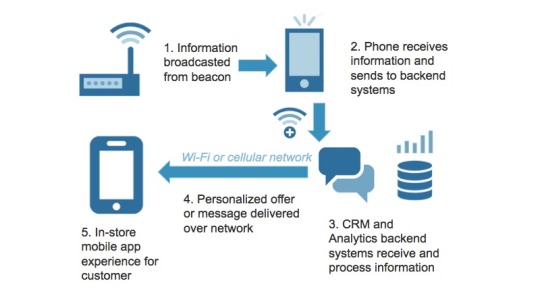
How to Transmit Data using Bluetooth Beacon sensors?
Bluetooth Beacon sensors are small transmitters that broadcast signal to close portable devices using the Bluetooth Low Energy technology. They have an action range of around 90 meters and can only transmit data but cannot receive. Once the sensor detects the nearby devices, it sends digital messages to the targeted devices. Currently, beacons are used proportionally with mobile applications. These mobile applications obtain a unanimously unique identifier to perform several functions, such as triggering a location-based action and tracking customers.
Technical Features of a Bluetooth Sensor
a) Radio interface
The Bluetooth IoT sensors work with the same spectrum range of between 2.400–2.4835 GHz ISM band as classic Bluetooth technology. The only difference is that Bluetooth Low Energy uses a different set of channels. It has forty 2-MHz channels, whereas classic Bluetooth has seventy-nine 1-MHz channels. The Gaussian frequency shift modulation is used to transmit data within a channel in the BLE technology. It has a bit rate of 1 Mbit/s but with an option in Bluetooth 5 of 2 Mbit/s. Also, it has a maximum transmit power of 10 mW and 100 mW in Bluetooth 5.
b) Advertising and discovery
Bluetooth Low Energy sensors are spotted through a technique based on broadcasting advertising packets. It is usually done using 3 distinct frequencies to decrease interference. The advertising device sends packets of not less than one of the three frequencies with a repetition period termed as the advertising interval. In each advertising interval, there is an addition of a random delay of 10 milliseconds that reduces the chance of numerous consecutive collisions. The scanner attends to the frequencies for a period termed as the scan window, which is occasionally recurrent after each scanning interval.
c) Battery impact
Bluetooth Low Energy sensors are specially designed to work even with shallow power consumption. Various power necessities are required for devices with central and peripheral roles. A study conducted by a beacon software company Aislelabs conveyed that computer peripherals, for instance, propinquity beacons, regularly function for up to 2 years using a 1,000mAh coin cell battery. The Bluetooth Low Energy protocol makes this possible due to its power efficiency. BLE transmits small packets; hence it's ideal for high and audio bandwidth data compared to Bluetooth Classic.
d) 2M PHY
A new doubled symbol rate transmission mode has been introduced by Bluetooth 5. Initially, Bluetooth Low Energy sensors only transmitted 1 bit per symbol, but with Bluetooth 5, they can data with double rates. However, the new transmission mode pairs the bandwidth to 2 MHz from about 1 MHz, making more intrusions on the edge areas. The ISM frequency band segmentation has 40 channels with a spaced distance of 2 MHz, which is essentially different from the Bluetooth 2 EDR.
e) GATT operations
The GATT protocol is essential to the user as it offers several commands regarding the discovered information about the server. These commands include:
· Discovering UUIDs for each principal services
· Finding a given UUID for every service
· Finding subordinate services for a given principal service
· Discovering every feature for a specific service
· Finding features that match a specified UUID
· Reading all signifiers for a precise distinctive
Pairing a Bluetooth Sensor with a Smartphone
In this section, we will describe the steps followed when pairing Bluetooth-compatible sensors using a smartphone. The Aventura receives the sensor pairing data together with the settings once the pairing process is complete.
1. Ensure that (Connect) is on, then from the (MENU) tap (Device).
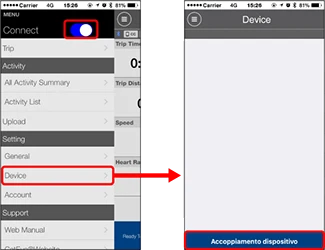
To search for pairable sensors, tap (Pairing)
2. Start the sensor.
Once the Bluetooth smart sensor signal is detected, it displays a message on the smartphone.
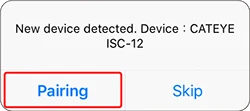
To complete the pairing process of the already displayed sensor, tap (Pairing).
· Press (Skip) if the gadget's name is dissimilar from the expected, then tap (Pairing) again. Repeat this occasionally till the anticipated device is shown.
· When using the Bluetooth le sensor to pair, the sensor name is displayed with an "A."
· Over 18 distinct sensor identifications, including the P.C, can be paired.
3. Establish the tire circumference for any sensor with speed measurements.
Press (Device), and also tap the Sensor name > [Tire Circumference]. Tire circumference is the approximate length of the outer rim in each tire. Sensors that cannot measure speed are never displayed.

The tire size list is displayed once tapping is done. The tire circumference is selected per the tire size shown on the tire side.
· Original value: 2096 mm
· To any Bluetooth door sensor capable of speed measurements, it is recommendable to set the tire circumference.
· It is possible to cancel pairing and changed the device names from this screen.
After following all those steps, the pairing process of the Bluetooth sensor is now complete.
· Repeat the same procedure when pairing with another Bluetooth sensor.
· After completing the pairing process, it is essential to mount the Bluetooth motion sensor close to you. Also, follow the guidelines written on the individual sensor's instruction manual appropriately to determine the suitable place to mount the sensor.
Important Information
· Pair every usable sensor.
· Never pair Bluetooth smart sensors in the exact location or at any venue with many other users. Doing this can make the sensors pair up with other irrelevant devices. A Bluetooth mesh sensor can epitomize a sole physical BLE sensor.
· When working with third-party Bluetooth sensors, only an Android smartphone can transfer data to the Aventura, whereas an iPhone cannot.
Bluetooth Sensors Functionality
Bluetooth wireless sensors are insignificant, relatively cheap devices fitted onto or into an existing system. They are ideal for placement in remote areas or locations without power since they are battery-powered and wireless. Batteries last according to how often the sensors give report values, with some lasting even 5 years.
Besides, Bluetooth wireless sensors convey regular Bluetooth Low Energy publicity applied by commercial equipment, fitness trainers, and healthcare diplomacies. The publicizing information can be configured as iBeacon with bytes pack the recognized data with a patented format. Smartphones, gateways, or single-board computers, for instance, Raspberry Pi, can be used to grasp information once beacons are scanned. Scanning only sees the data broadcasted to everyone, but it does not link to the beacon.
Additionally, the scanning device termed as Bluetooth GATT connection enables a connection with some sensors. This permits the scanning device to notify whenever there is a change in values or view the present sensor values, allowing a large output of changes. However, advertising can be stopped by a connection; in so doing, other devices cannot connect since they cannot view the sensor.
The already built-in Bluetooth libraries enable the receipt devices to scan for beacons and link via GATT. Since communication is Bluetooth Low Energy, discrete sensors, specifically SDKs, are unnecessary. Also, there is no need to have subscriptions on the server-side stages.
Business Uses of Beacon Sensors
December 6, 2013, was when the first instance of the beacon was registered for business use. Up to date, iBeacons have been activated in its 254 retail stores across the United States by the Apple Company. Later, McDonald's used the sensors in its stores to run special offers to its clients.
The Bluetooth Low Energy beacon sensors have numerous use choices in various areas. The technology has numerous benefits, the main one being that it can send advertising and informational data to prospective clients. Generally, beacon sensors act as a bridge between the concepts, offering business information to clients. Multiple beacon sensors can be mounted inside an area, such as in airports, stores, institutions, clubs, public rooms, thereby broadcasting appropriate information to propinquity portable devices. Once the users receive the data, they can either use it for navigation purposes, react to the data, share the information or other tenacities reliant on the message received.
Marketers can also use Bluetooth beacon sensors when connecting with probable clients. Businesses that use beacon sensors have higher chances of attaining targeting returns in brick-and-mortar standings. These beacon sensors offer several reimbursements to a business. They include;
· Beacons achieve more customer insight. For instance, a retailer learns how long it takes for a customer to make the next visit to the store. The seller also recognizes where exactly most clients spend in that particular store. The data can be helpful when updating advertising networks and applications or when retargeting a specific market.
· Beacons increase the loyalty of clients. Beacons provide promotion information through click-and-collect orders and by rewarding the physical presence of clients in the store.
· Sales increase. Using Bluetooth beacon sensors in line with its application rises the products and services orders. This is mostly seen in stadiums during sports events. Via beacons and the stadium's application, visitors get into a position of receiving messages about food and beverage offers that endorses sales by times.
The options above do not naturally limit anyone on the use of Bluetooth Low Energy beacon sensors. Everything subject to creativity and fantasy.
Arduino: Reading and Controlling Sensor Data Using Bluetooth
This section aims at gathering sensor data from a simple temperature sensor then transmit it to a computer through Bluetooth communication. On one side of a computer, a simple Bluetooth sensor Arduino sketch must be written. It will later be uploaded on the Arduino board, assisting to time on the serial monitor and see the sensor data.
The following items must be available for the experiment to run smoothly
· Arduino uno Microcontroller
· HC-05 Bluetooth communication module
· Temperature sensor
· USB cable
· Jumper Wires
· Breadboard
Step 1: Set Up the Circuit Connections
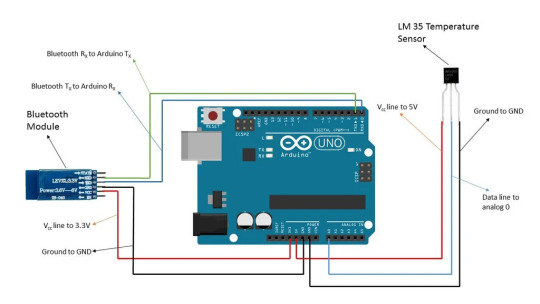
To begin the process, arrange the Arduino board circuit connections as in the diagram above. The Bluetooth connections between the Bluetooth module and the computer are established after making these connections.
A voltage divider circuit is used to connect the HC-05 Bluetooth modules to the voltage lines. The HC-05 may get damaged if it isn't strong enough to sustain a 5V line. It is advisable to connect it to a 3.3V line, which keeps you on the safe side. The Bluetooth TX module is connected to the Arduino's R.X, while the Bluetooth R.X pin module is connected to the Arduino's TX pin.
Step 2: Establish Bluetooth Connections
After successfully setting up the circuit's connections, you should be able to see a blink on the Bluetooth module signifying that it is operational and is ready for pairing with the P.C.
In case the computer you are using doesn't have in-built Bluetooth, set up the connection with a Bluetooth dongle. If an inbuilt Bluetooth is present in the computer, go to the Contol Panel section and select -> Hardware and Sound -> the add a Device on the Bluetooth icon section on the taskbar. The computer should detect the HC-05 Bluetooth module and pair the computer with the HC-05 module. Use either '1234' or '0000' as the pairing code.
Step 3: Download Arduino Code
Open the Arduino IDE after successfully pairing the Bluetooth module. Download and understand the codes but do not include any special libraries.
Step 4: Upload Your Arduino Code
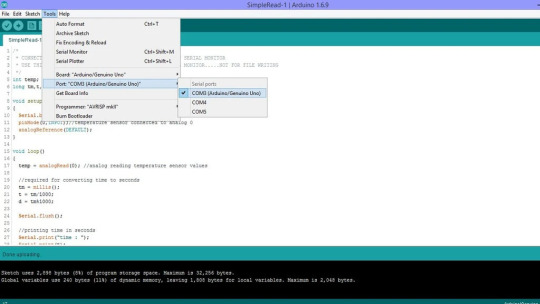
First, make sure you have well understood and verified your sketches before uploading. Make the necessary changes if there is any needed. After ascertaining the graphic, select the correct board and pick the right port to connect with the Arduino board. Then go to Tools -> Port and Tools -> Board correspondingly. To perform the procedure correctly, click the Arduino Uno to COM3.
After establishing the correct port and board, disconnect the R.X pins and the TX from the Arduino board, then upload your Arduino code. You are likely to get an error indicating the COM port is busy when you haven't disconnected the TX and R.X. pins. Upload the code once you have disconnected, and connect the TX pins and the R.X. to their usual positions.
Step 5: Getting the Final Data
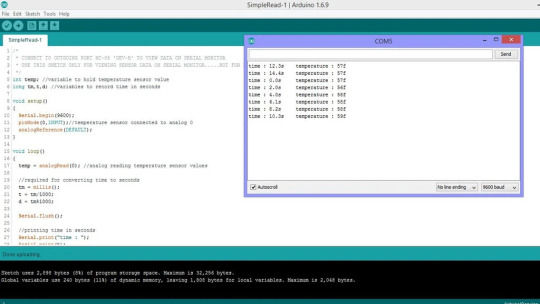
Connect the power source to the Arduino board and disconnect the USB cable connecting the Arduino board's computer. With this setup, the Arduino board remotely gathers sensor data through Bluetooth communication is transferred to the computer with a USB cable.
Next, establish which COM port connects the Bluetooth module to see the serial monitor's sensor data. On the taskbar, click the Bluetooth icon and choose 'Open Settings,' then snap the 'COM Ports tab.' You should be able to see some COM ports connecting to the HC-05 module. Make sure you have carefully taken note of the 'outgoing' port, then go to the Arduino sketch and tap on Tools -> Port. Chose the port that parallels the 'outgoing' port. Once everything is set, open the port's serial monitor where time and the temperature sensor data are displayed. Press the Arduino's board rest button to assess data from zero seconds onwards.
Step 6: Troubleshooting
After noticing a time interval of 2 seconds in both time data on the serial monitor and temperature on the Bluetooth accelerometer sensor, know that everything is proceeding well. However, a slight delay of a few milliseconds may arise between the expected and normal successive readings while transferring data. You are more likely to encounter several problems and errors if you are new to using Arduino's Bluetooth connection. To avoid any of these problems, make sure you have correctly followed the following points.
· Counter-check that the R.X pins and TX connections are firm and correct.
· Recheck that the Bluetooth module is well connected, and to be safe enough, use a voltage divider circuit or connect the HC-05 to the 3.3V. Never use the 5V.
· A loose connection may cause the Bluetooth module to stop working. Ensure there is a continuous LED blink on the Bluetooth module, indicating that it is powered.
· While uploading sketches, select the appropriate COM ports and boards. Besides, think of choosing the suitable Bluetooth module's outgoing COM port to enable you to view the data on the serial monitor.
· As described in step 4, upload the sketches and remember to disconnect and reconnect when uploading the sketch.
· Make sure that the HC-05 Bluetooth module is within the range of your computer before experimenting with it.
Arduino Bluetooth communication is simple to connect when frequently used. Once someone gets comfortable with it, it becomes straightforward to send and receive data.
0 notes
Text
What you can expect from Thethings Conference 2021
Tthe things conference is coming online from Jan 25th to 29th, 2021. There’s more than 5 years’ history of #LoRaWAN, this event explores LoRaWAN’s latest innovations,common mistakes, and obstacles to help you mitigate risks during LoRaWAN development.
Let’s find out what you can expect from #thethingsconference2021
1.Technical deep-dives and LoRaWAN fundamentals
Cover the fundamentals of LoRaWAN through 101 sessions, workshops, and live coding sessions.
2.RFP Marketplace
Posting or responding to Request for Proposals to initiate collaborations.
3.LoRaWAN Wall of Fame
Experience top-shelf LoRaWAN devices and #gateways remotely, select the right solutions for your IoT development.
4.The Things Certification
Join this event to test and prove your #IoT skills on LoRaWAN basics, security, and network management.
5.Virtual networking and curated Matchmaking
Find new business partners during 1-on-1 meetings and small networking groups around specific LoRaWAN topics.
MOKOSMART has already attended this event, we will showcase innovative LoRaWAN products and solutions that are leveraging long range and low power consumption.
You can find more about us on this event through https://lnkd.in/g9HqPhg
0 notes
Text
Meet MOKOSMART at the #LoRaWAN event
Meet MOKOSMART at the #LoRaWAN event online on Jan 25-29 2021. Get connections with industry leaders and discover more #LoRa products and solutions at #TheThingsConference:
http://ow.ly/jkIX50xl9Qb


0 notes
Text
LoRaWAN Parking Sensor
Thanks to the LoRaWAN parking sensor, whether a parking space is free or occupied can be reported. The flat, circular sensors are attached to the desired parking spaces. There are also models that can be installed directly on the floor and are therefore invisible.
The LoRaWAN parking sensor LW005-PS from MOKOSmart delivers precise vehicle detection in real-time – even from electric cars.
The LW005-PS has three high-performance geomagnetic sensors that detect the consumption of the earth’s magnetic field and can detect the presence or absence of a car in a parking space in real-time. The LoRaWAN parking sensor has proven itself as one of the few products in the field of electromobility and can intelligently detect and filter out the interference magnetic fields generated during the charging process of an electric car. This ensures error-free detection of e-cars, which is not always the case with competitor products.
Detection of free parking spaces and parking spaces
LoRaWAN parking sensor solves the most important aspects of today’s parking lot management, such as real-time vehicle detection and location of available parking lots, for cities, municipalities and municipal companies. It also enables private parking space management. You can see further areas of application in hotels, airports, supermarkets, clinics, charging stations, parking spaces for the disabled, detection of incorrect parking and long-term parking, no-parking zones (fire lane access, garage access) as well as park-and-ride parking spaces.
The product has three geomagnetic sensors that detect the consumption of the earth’s magnetic field and can detect the presence or absence of a car in a parking space in real-time. The LoRaWAN parking sensor arranged in the X, Y and Z axes not only detect the magnetic field strength but also analyze patterns. Different types of vehicles generate different signal patterns. These can, therefore, be distinguished. Algorithms reliably filter out disruptive interference fields that are generated, for example, by subways and overhead lines. In this way, incorrect measurement results can be avoided.
The LW005-PS is currently used by over 80 companies – worldwide. These include well-known locations such as California’s Central Valley, Montreal, Stratford (Ontario), El Monte (California) and the University of British Columbia in Vancouver.
Expertise from 30 years of R&D flows into the development of the LW005-PS
All of MOKOSmart’s expertise comes into play in the development of the LW005-PS, because the company is not a start-up, but has been developing and manufacturing high-precision magnetic field sensors and electronic compass solutions for more than 10 years. For example, the LW005-PS can also be used in larger multi-level parking garages without the vehicles at different levels interfering with each other in their clear recognition.
LoRaWAN parking sensor LW005-PS makes finding a parking space easier
In November 2017, the city of Stratford installed LW005-PS in the city center and city hall parking lots to help drivers find free parking spaces. The city uses a public LoRaWAN, in which the sensors exchange data with Canada’s Open Data Exchange IoT program.
The real-time parking data is evaluated in order to identify trends in parking behavior, to track the use of parking spaces and to optimize parking space resources. The LW005-PS was not only chosen for its accuracy in parking lot detection but also convinced the decision-makers with its robustness, as it delivers reliable results even in snow and harsh weather conditions
LoRaWAN parking sensor benefits
By transmitting the occupancy status in the managed parking space, there are many options for optimizing the search for a parking space. Accordingly, experiences with the LoRaWAN parking sensor are also interesting for our municipal partners. Possible applications are places where parking is not permitted under any circumstances (e.g. fire brigade access). In addition, the connection to the charging infrastructure for electric vehicles also makes sense. The parking sensors can report to users whether a parking space in front of a charging station is free. On the other hand, operators can use this to determine whether electric vehicles are only parked in the parking lot in front of the charging station or whether they are refueling. This is possible by comparing the data from the charging station and the LoRa smart parking sensor.
• Reduce the time to find a parking space
• Reduction of emissions (fine dust, CO2, noise, …)
• Resource efficiency through “smart” parking space management
• optimal parking space utilization, congestion avoidance
• The basis for intelligent parking guidance systems (guided parking)
• Transparent traffic planning (number of parking processes and parking times)
• Additional service for park-and-ride in local and long-distance traffic
• Needs-based checks of parking bugs
• Reduction of incorrect allocation e.g. free customer parking spaces,
Disabled parking spaces, restricted areas, loading zones, fire service access
• eMobility services, such as determining free charging stations and service life
• Innovation through digitization (service apps, rental unused
Areas, measurement of ground temperature for winter service, ..)
Functions and Features of LW005-PS
Support standard LoRaWAN CLASS A
With triaxial reluctance sensor, support the magnetic induction of XYZ in three directions;
Support BLE wireless transparent transmission
With built-in Li-SOCl2 battery
Built-in temperature sensor
Complete plastic shell design, IP68 protection
Wide operating temperature range for industrial use of -40℃~+85℃
Strong resistance to interference and easy installation
High detection accuracy to >98%
Ultra-low power consumption, last for 3~4years, according to the actual application scenarios
High reliability, and support watchdog to protect the internal circuit
Low construction and maintenance cost
Hardware parameters of LW005-PS

0 notes
Text
What is Wifi smart switch
WiFi Smart Switch is one part of the Smart Home devices. At first glance, the WiFi switching module can be hooked into your own MOKO MokolifeX app and thus the consumer can be switched on / off depending on the location using the smartphone. “Nice” for the small price.
The really great thing about the switching module, however, is that it can be flashed with an alternative firmware and thus integrated into open-source home automation solutions such as HASS.io, ioBroker or openHAB.
WiFi Smart Switch: MOKO WS001 & WS002
Product description & product data
WS001 is a 2-channel universal wifi wall switch for your smart home system to remotely and automatically turn on / off household appliances and electronic devices via phone APP. It can connect and control two devices at the same time, which means that 1 Sonoff Dual corresponds to 2 basic switches. In the smart switch APP MokolifeX, you can switch each of the two connected devices on and off independently. It also supports timing when the appliances are turned on / off at a specific time and allows sharing with others so that you can control your smart home with your family. You can also control your home appliances via Amazon Alexa and for Google Home / Nest, enjoy intelligent living and make your home smarter.
Parameters of WS001

Features of WS001
• Suitable for ordinary lamps, such as incandescent lamps, fluorescent lamps, led lamps, etc.
• Built-in standard ESP-12F module, support WiFi communication
• Can work with MOKO MokolifeX APP
• Supports standard MQTT V3.1.1 protocol and TLS V1.2 transport layer encryption protocol
• Can connect to standard MQTT servers, such as Mosquitto MQTT and EMQTT; also can connect to AWS IoT /Azure IOT HUB /Aliyun IOT
• Support API for APP and cloud server developing
• Customized service:
• Support customized hardware with Zigbee, Z-wave, Bluetooth and other wireless types
• Schematic diagrams are available for customers to develop firmware
Parameters of WS002
Features of WS002
• Applicable to common lamps, such as incandescent, fluorescent lamps, led lamps and so on.
• Built-in standard ESP-12F module, support WiFi communication
• Can work with MOKO MokolifeX APP
• Supports standard MQTT V3.1.1 protocol and TLS V1.2 transport layer encryption protocol
• Can connect to standard MQTT servers, such as Mosquitto MQTT and EMQTT; also can connect to AWS IoT /Azure IOT HUB /Aliyun IOT
• Support API for APP developing
• Customized service:
• Support customized hardware with Zigbee, Z-wave, Bluetooth and other wireless types
• Schematic diagrams are available for customers to develop firmware
Basic functions:
* Switch your devices on or off using your smartphone
* Voice Control: Works with Amazon Echo, Echo Dot, and Amazon Tap to manage your devices via voice
* Timing function: timer automatically turns appliances on and off
* Wireless standard: Wi-Fi 2.4 GHz b / g / n, WEP / WPA-PSK / WPA2-PS
Networking your home and controlling it from anywhere in the world – that doesn’t necessarily have to be expensive.
If you want to network your home, you first think of expensive solutions from Innogy or Bosch. But you don’t necessarily have to spend a lot of money on a networked home – at least if you can make a few cuts in the range of functions.
Installation: Special notes
Important note: You should only have electrical installations carried out by approved electricians. In the event of damage, many insurance companies accept no liability for circuits that you have created yourself. Even worse: in the event of damage by third parties, you can be held liable. In addition, you may only connect insulated devices with a smart plug without earthing to the switch, since there is no terminal for earthing. Little or no electrical experience? Stay away and have a professional do it!
First, you need MOKOSmart’s WiFi switch. Of course, you also need a functioning WLAN network with internet access on site.
The Setup
First, the specialist must install the Wifi smart switch on your device, such as a lamp. To do this, he cuts the lamp’s power cord at any point. Caution: Be sure to disconnect all cables from the power beforehand or to trigger the fuse. The person skilled in the art isolates all cores from both cable ends and fastens the ferrules. Now you put the smart network switch between both ends. It should be noted that the side with the device is created at “Output” and the side with the current in the “Input” of the smart power switch. The blue wire belongs to the N connection. The phase (brown cable) comes to the phase connection “L”.
Connect the wifi smart switch to the WLAN
If the smart switch is set up correctly, you can now switch the lamp on and off using the small, black button. Now the setup follows via the app. To do this, download the free “MokolifeX” app from the Google Play Store or Apple AppStore and create an account. You can then use the “+” symbol to set up your WLAN switch.
If the green LED lights up permanently, the setup was successful and the device is connected to the network. If the LED flashes, you will find a legend for the various error messages here.
In operation: protection against burglary & schedules
If you have successfully set up the device, you can now create schedules in the app or control the Wifi smart switch manually. For example, you can set the lights in the living room to turn off at 3 a.m. every day or in the kitchen every evening between 7 p.m. and 10 p.m. Perfect if you are traveling and you don’t want your own four walls to appear deserted. Control on the go is also possible.
You can also share each device with other users for control. They also need the app and their own account. For example, the whole family has access to the lights in the living room.
Cloud storage is required to enable control via the app. This is currently free of charge and can be used at any time. Unfortunately, you have no control over where and how your data and that of your devices are stored on the servers.
Also interesting: the best smart light switch
Compatibility: Control via the app, Alexa or Google Home
In addition to the app, the smart life switch is also compatible with current voice assistants. In the test, the sensor worked perfectly with Google Home. The switches only have to be named in the home app and assigned to a room. Then it’s enough: “Ok, Google. Turn on the light in the living room “- and it was already bright. Amazon Alexa also supports the manufacturer, according to its own information.
Conclusion: Smart home from China
Once the smart home switches are properly installed, the system works perfectly. But there are too many things to consider before commissioning: A certified electrician must install the device and ensure that there is no danger to third parties. This switch is only for professionals. If you are looking for a simple plug-in solution, you should rather spend a little more money in your hand.
Smart control of existing lighting without replacement – possible thanks to Wifi Light Switch
With the smart wall light switch, existing lights and illuminants that are normally not Apple HomeKit-capable can be integrated via the system. No bulbs need to be replaced. In addition, the conventional, familiar control via switch is retained. Furthermore, the Wifi light switch can be easily adapted to the existing device on the wall and can be installed in different versions. If there are some Wifi smart switch in a circuit, the replacement of just one switch is enough to control the lights. Thanks to the compatibility of the smart wall switch with Apple HomeKit, the functions can be controlled via the app or with the Siri voice control.
There is also the possibility to use scenes. Several devices are addressed and activated or deactivated with one command. For example, you could combine switching on the ceiling light in the living room with activating a table lamp that is connected to an Eve Energy socket. In addition, smart life light switch has built-in schedules that are easily programmable. This makes it very easy to automate the switching of your own lighting. The schedules are saved on the device and can be set with times and reference values such as “sunrise” or similar specifications.
The brilliant Light Switch presents itself in a very inconspicuous simple design, which easily replaces conventional wall switches. The normal function is retained and can be used at any time.
Install the Smart Wifi Light Switch on the electrical wire
It only takes a few minutes to set up your Wifi Light Switch. If you cannot determine which is a load and a power cord, or if you are unfamiliar with electrical work or feel unsafe, please contact a professional electrician.
User-added image
The wall box must be five (5) centimeters deep
User-added image
IMPORTANT: Metal covers are not suitable for the Wifi light switch (these can cause interference with the WLAN network) and it is only suitable for dry indoor areas (living areas).
When you have met the electrical requirements, follow the electrical installation instructions below.
Step 1: Turn the main wifi smart switch or fuse of the switch you are replacing OFF. Multiple main switches may need to be turned OFF to ensure that the switch you are working on is turned off and no electricity is present.
IMPORTANT NOTICE: CHECK WITH A CONTACT-FREE VOLTAGE DETECTOR whether there is no more voltage or press the best light switch several times to check it.
Step 2: Use a screwdriver to disconnect the wiring from the old light switch.
Step 3: Determine the conductors on your smart Light Switch.
Jumper wires (live/outer conductor): the two (2) live conductors are marked black on this light switch. Each light switch is equipped with these two conductors. However, they can also be marked in red or black and red.
Neutral conductor: is required by your Wifi Light Switch, but is not available in every electrical installation. If available, you will usually find it in the wall socket, secured with a clamp.
It is usually marked green or copper-colored. If you don’t find a ground, that’s not a problem. It is not absolutely necessary for the wifi Light Switch.
Step 4: Install the Wifi Light Switch. Connect the two (2) black conductors of the Wifi Light Switch to the existing switching conductors (live conductor / outer conductor) of the wall socket. If there are several conductors, fix them in the clamp.
NOTE: The clamp is the attachment that connects the conductors together.
0 notes
Text
What is the LoRaWAN transmission range?
The most important ability of IoT devices is that of communication. there are different protocols with different areas of application. While WiFi, Bluetooth, Zigbee or other radio standards are often used for short distances in the home, devices have to be located elsewhere use alternative technologies. Such a group of technologies is LoRaWAN transmission. However, these have the advantage of a significantly longer range and better energy efficiency than most other radio standards at the expense of bandwidth. The picture below shows LoRaWAN compared to some other wireless communication protocols. LoRaWAN technologies are mostly used when end devices are installed in locations that only work with other technologies that are difficult to achieve, or when energy efficiency is of great importance. In this LoRaWAN is used as LPWAN technology.
However, range and power consumption are not the only important points in the IoT. One issue that is often neglected is the security of networked devices. Between 2017 and 2018 alone, the number of known malware for IoT devices increased almost quadrupled. But malware isn't the only threat. Lots of IoT devices send data inadequately protected, causing attacks on that data and thus also on the IoT infrastructure. Espionage, manipulation of data and the complete takeover of systems are exemplary attack scenarios.
Another relevant topic in IoT security is firmware updates; they enable manufacturers to bring new functions to devices and, in the event of security incidents, to remedy them without the user having to become active. It is extremely important that the updates are also carried out in a secure manner so that attackers are unable to inject fake firmware into a device.
Combining firmware updates and end devices that use a LoRaWAN protocol for data transmission creates a completely new challenge. While for IP-based technologies, such as B. W-LAN, there are already some suggestions for specific protocols, updates via LoRaWAN are still largely unexplored. The reason that the classic protocols cannot be used can be found in the restrictions of LoRaWAN technologies. LoRaWAN, for example, has high limitations in terms of data rate and LoRaWAN transmission speed and has no standardized transport protocol, which compensates for losses in data transmission could.
1.1 The smart mailbox
In this work, a specific application is considered and various topics of IoT security are examined. A smart mailbox was developed, which notifies the user via their smartphone when mail is in the mailbox has been received.
1.1.1 Use case
The basic idea of the smart mailbox is to make sure that the user doesn't constantly have to open his mailbox to find out if there is any mail in it. Instead, he should receive a notification on his mobile device as soon as there is mail is in the mailbox. This has the advantage that the time of the user is not unnecessary due to mailboxes that are far from the user or that rarely contain mail Is claimed.
The functions of the application are deliberately kept small because of the focus on security and energy efficiency. In addition, the application was developed as an "extension". It should be possible to do this with little effort on the part of the user to install any letterboxes. Battery operation and a small form factor are thus also requirements for the project.
1.1.2 Examined topics with LoRaWAN transmission
As mentioned earlier, the focus of the work is on IoT security. In addition, energy efficiency is considered. From these priorities, there are several subtopics that are examined using the smart mailbox have been the first point is the secure, E2E-encrypted data LoRaWAN transmission. Especially With mailboxes in public areas, it is important that an attacker does not find out can determine whether and how much mail is in the mailbox. This prevents who can easily find out if a break-in would be worthwhile. Protection is also important against manipulation to prevent the user from receiving false information about the condition of the mailbox. In addition, it is examined to what extent the negotiation of cryptographic keys for these tasks is a secure way can be carried out without the manufacturer of the device or third parties can find out.
The next main point of investigation is the secure firmware updates via LoRaWAN. There is currently no official standard regarding the transfer of firmware. Updates via LoRaWAN. In this respect, it is one of the main tasks of this work
to design and test. In the end, the smart mailbox should be able to carry out firmware updates via LoRaWAN without user intervention. These updates must also be cryptographically secured to prevent manipulation. Finally, it is examined how mail is thrown into a mailbox device that can be recognized. Various technologies were examined and a suitable one was identified.
2.1 LoRaWAN
LoRaWAN is a LoRaWAN solution for IoT applications with a small amount of data energy-efficient and can be transmitted wirelessly over large distances. It consists of the one hand of LoRa radio, a protocol for physical data LoRaWAN transmission and on the other hand of LoRaWAN itself, a MAC protocol which is based on LoRa builds up and provides a standardized procedure for the transfer of data via LoRa. LoRaWAN, as one of the key points in this work, was used for communication with the end devices, including the smart mailbox.
2.1.1 What is LoRa
LoRa is a frequency modulation process developed by Semtech wireless communication between two communication partners allowed. It is, therefore, a physical protocol (OSI Layer 1), which only takes over the modulation of the physical data transmission. LoRa uses frequency-modulated chirps to encode symbols. The chirp modulation used uses “chirps” to transmit symbols. The frequency is continuously changed across the bandwidth over a defined period of time. The symbols transferred are about the beginning of the chirp are defined.
The primary advantages that this modulation offers compared to FSK or PSK are the long-range and the robustness against noise. Both are from the spreading factor and bandwidth used. The spreading factor determines how long a single chirp lasts, ie how wide it is spreading”. A higher factor means wider symbols, which ensures longer LoRaWAN transmission ranges, but also slower data transmission. In LoRa spreading factors from 7 to 12 is defined, which means LoRaWAN transmission speed from a maximum of 37.5 kbit / s to a minimum of 300 bit / s can be achieved. The bandwidth is fixed at 125 kHz, 250 kHz or 500 kHz and also influences the range and speed of the signal. The concrete choice of these parameters is determined by LoRaWAN.
The frequencies that LoRa uses depend on the region. In Europe, you can 868 MHz or at 433 MHz can be sent. It is important to mention that these frequencies are license-free spectra, so there is no license fee to use them. To compensate for this, apply temporal, send restrictions that all devices must adhere to. These are between 0.1% and 10%, depending on the frequency used.
2.1.2 What is LoRaWAN
LoRaWAN is a MAC protocol (OSI Layer 2), which is based on LoRa (but also with FSK can be used), and also some elements of a network protocol (OSI Layer 3) contains. It defines a message format, as well as MAC commands to control the transfer. The parameters for the underlying LoRa transmission are also determined by LoRaWAN. The first part is the actual specification, which defines the message formats, the MAC commands, and the sequence. The regional parameters, which specific settings for LoRa, as well as some adjustments or additions to the LoRaWAN protocol, are available as an extension define depending on the respective region.
A LoRaWAN network consists of several groups of participants and is organized in a star-by-star topology, as shown in Figure 5. In the middle is the network server, which is the server-side administration of the LoRaWAN network and offers an API for client applications. Manage LoRaWAN applications and both send and send messages to receive. This server communicates with several gateways via an IP connection. Their primary task is to forward the LoRaWAN packets received from the network server to the end devices via LoRa and vice versa. Accordingly, they serve as an interface for changing the physical medium. Stand at the end than the end devices that communicate with one or more gateways to transmit their data. The LoRaWAN protocol is only between the gateway and the end devices used. No standard is defined for the remaining paths and that format, therefore, depends on the specific applications used.
In this context, LoRaWAN takes on some tasks, which are explained further below. This includes the different communication classes that are used data can be transmitted in different ways, the two options for adding devices to a LoRaWAN application, the encryption and integrity check of transmitted data, and the various MAC commands for controlling the connection. The latter will not be explained further because they are very specific and are not relevant to this work.
2.1.3 LoRaWAN Data transmission modes
LoRaWAN supports three different modes for data transmission. Each of these Modi has specific use cases, as well as advantages and disadvantages, which are listed below.
Class-A
Class-A mode is the primary LoRaWAN transmission mode used by all end devices and gateways must be supported. It allows bidirectional communication between terminal and gateway based on the ALOHA principle. In the case of LoRaWAN, this means a terminal can send data at any time, but only for two short one's Intervals after sending a data packet can also receive data.
The advantage of this mode is that a terminal device only while sending data and shortly after this turn on the LoRa transceiver to receive a response got to. This means that it can remain deactivated most of the time, which saves energy. The disadvantage, however, is that the terminal does not have any data at all other times can receive. In addition, only one can be received for each data packet sent become.
Class A operation, therefore, makes the most sense when primarily sending uplink messages and rarely downlink messages. Since LoRaWAN preferably in sensors and similar low-performance end devices that normally only provide status information for an end application is used for most end devices the preferred data transfer mode.
Class-B
Class-B is an extension that does not have to be supported by end devices. By this mode can be used by end devices in addition to Class-A at regular intervals. Receive data from the gateway without first having to send it yourself. To the beacon sends a so-called beacon every 128 s, which contains some status information about the gateway. End devices that receive this can then use the beacon and the ping slot periodicity to calculate the times at which data can be received. This allows them to be at the right time for short moments switch on the LoRa transceiver to receive any data that may be present. The process is shown below.
Class-B offers a good balance between accessibility and energy consumption since the ping slot periodicity can be adjusted to control how often it should be received. This means that more energy is used than for pure Class A operation, but there are still long periods in which the LoRa transceiver can be turned off. Another advantage of Class-B is the ability to store data in 8 to be able to transmit multicast to several devices simultaneously, as long as the address and the keys are the same. Multicast groups can, therefore, be created.
The use of Class-B makes sense if a device has to receive data more often without sending data itself, but the device still has to work energy-efficiently. A typical application would be end devices that are regular can be controlled without being time-critical.
Class-C

The last, also optional, the transmission mode is Class-C. In this, the switches terminal permanently on reception to be able to receive data from the gateway at any time. The option of transmission with Class-A remains as in the picture below.
The advantage of Class-C is that data can be received at any time. However, the price for this is high energy consumption, since the end device must keep the LoRa transceiver active at all times. Multicast LoRaWAN transmission is also possible here.
Class-C should only be used when large amounts of data have to be transferred over a short period of time or when time-critical transfers occur. Such end devices should have a permanent power supply since this mode consumes too much energy for battery operation.
This article is from https://www.mokosmart.com/lorawan-transmission-speed/
If you’re interested in developing LoRa or LoRaWAN Products, know us more by https://www.mokosmart.com/ !
0 notes
Text
What exactly is a Beacon Sensor?
In the rapidly growing world of today, businesses have fierce competition among them. So, marketing professionals have to rely on sophisticated tools such as a beacon sensor for reaching out to your customers. Most people today especially the millennials have a very short attention span which they mostly dedicate to new information, social media communication, and digital news. Hence, it is very easy for people to get distracted today. Therefore, if you want your business to succeed then you have to come up with a unique positioning for it. Beacon sensor is also known as Bluetooth beacon or Proximity beacon and is a great tool for increasing your potential customers and prospective sales.
But we need to remember that beacons are not only a great instrument for business owners but also a great asset for IoT deployments. Hence, we can also use them for various purposes such as operations in an airport, sports coverage, large conferences, universities and other educational institutions, recreational places, galleries and museums, and concert arena. This will allow us to interact with more people and get to know their tastes, behavior patterns, attributes, and preferences. The beacon sensor is great for increasing customer engagement and hence increasing the revenue generation and brand loyalty. We can also use beacons for supply chain and logistics operations. A number of use cases have suggested that we can also use beacons in hospitals for taking care of critical patients and monitor their health at all times.
In this article, we would like to tell you about the beacons sensor and how you can use it for developing your own business app.
What exactly is a Beacon Sensor?
Beacons are small transmitters that always stay on and use Bluetooth technology for broadcasting important information to close by smartphones and other devices. They always stay on and yet they consume very little power. On top of that, they have a pretty good range of access.
A beacon sensor is capable of transmitting data however, it is incapable of receiving it. If there is a smart device nearby then the beacon sensor will detect it and then send digital notifications to that device. Many experts use the analogy of lighthouses for the beacon sensor because they are capable of sending signals to the nearby smart devices and guide them towards a particular action.
Today, we mostly use beacons in combination with dedicated software and mobile apps. The beacon sends a unique identifier to such apps and each identifier relates to a specific function like tracking the location of a device, showing notifications of a product to a customer, and tracking the shopping behavior of a customer.
History of Beacon Sensor
Bluetooth technology was introduced in 1989. It was introduced by Ericsson and its primary purpose was to develop headphones that were wireless. After that Bluetooth technology evolved considerably and is now a standard for IoT communications.
The Bluetooth beacons started appearing in 2013 hence they are the latest development in the field of IoT. They were first introduced by the tech giant, Apple. Apple introduced them so that it was possible for Apple devices such as the MacBook, iPhone, and iPad to detect nearby Bluetooth devices and react to the signals coming from them.
In 2015, their competitor i.e. Google decided to announce their own version of Bluetooth beacons. Google named its technology Eddystone which was their way of paying homage to a famous British lighthouse. The difference between the beacons introduced by Apple and those introduced by Google is that the platform provided by Google is completely open-source which means that anyone can use them without any restrictions. Additionally, there are significant differences in how the two platforms are implemented.
Since the inception of beacons, many other competitors have sprung up in the market and all of them have introduced their own beacons. Most of them are open source, however, some of them are able to send URLs instead of an identifier but these are not open source so you have to pay for them.
How Effective is a Beacon Sensor?
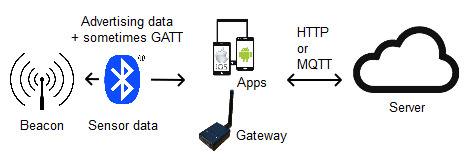
We can use Bluetooth beacons for broadcasting signals on a short distance. They have a low power consumption so they keep on working for extended time periods. On top of that, beacons are very economical and save you up to 65-87% of operating costs. We often use Bluetooth for advanced applications that require large data transmissions. Simple business apps require frequent data transfer so beacon sensors are a good fit for them.
The performance given by a Bluetooth beacon is comparable to that of Wi-Fi and GPS. However, neither GPS nor Wi-Fi is capable of providing a pinpoint location of a smartphone within a dense building. However, a beacon is capable of pinpointing the location of a smart device within a building. Proximity beacons are capable of sending a notification to the nearby smart devices. Hence, they are a one-way channel for data transmission therefore it is more beneficial in dense buildings and restricted spaces. Additionally, you don’t have to spend a lot of time or lose your battery life to pair your smart device in comparison to Bluetooth. On top of that, proximity beacons have a good range and we can use special techniques to further extend it.
Protocols of a Beacon Sensor
Bluetooth beacons have different protocols in rotation and they are provided by different companies. All of these protocols are almost similar in their role and function but they have some differences which make it possible for us to distinguish them from each other. In this section, we will take a look at some of them.
iBeacon
This was the first Bluetooth beacon protocol ever and it was launched by Apple. Hence, it is ideal for devices operating on iOS. The beacon sensors which operate on the iBeacon broadcast a UUID which engages with a dedicated app. We frequently use this protocol and it is very simple to implement.
AltBeacon
This protocol was launch after the iBeacon in the year 2014. It was the first-ever open-source protocol for smart beacons. Since it is open source so it is compatible with all operating systems i.e. Android, iOS, Windows, etc. This protocol also has increased flexibility which enables us to use this protocol for executing custom source code.
Eddystone
This protocol is introduced by Google and it has many more functions than any of its competition. Additionally, this protocol allows us to transmit three types of structure i.e. TLM, UID, and URL. This protocol works with both Android and iOS. On top of that, this protocol has the best features from both of the previous protocols/
How can we use a Beacon Sensor for a Business App?
The very first use cases for Bluetooth beacons came to light at the end of 2013. Apple deployed a large number of beacons in over 254 of its retail stores in the USA. After that, McDonald's deployed beacons for providing special discount offers within their franchises.
The Bluetooth beacons have a large number of deployment solutions across multiple sectors. However, the biggest benefit of this technology is that you can use it for marketing purposes. You can use it for sending promotional content and dedicated advertisements to your potential buyers. The Bluetooth beacons provide a bridge between products and offers, information and promotions, needs and advertisements, etc.
You can set up numerous beacons inside a franchise, departmental store, shop, or malls. We can then use them for broadcasting relevant information to the smart devices in close vicinity. Therefore, the customers receive promotional offers for the products they are looking for and they can have a unique shopping experience.
Perks of using beacon sensors for Business Owners
Business owners must use proximity beacons for communicating with prospective buyers. Brick and mortar stores are facing significant competition with e-commerce retailers. So, if you own a brick and mortar store then you should harness the power of beacon sensors to gain a significant edge. There are many advantages of using beacons sensors for your business.
You can gain better customer insight via beacons, for instance, you can learn how much time your customers spend in your store and which products they like to browse. We can then use this data for customizing our advertisement campaigns and send discount codes via our business app.
The use of beacon sensors enables us to build strong brand loyalty among our customers. We can promote our products and compel customers to visit our stores by giving them certain rewards. In order to do this, we need some precedent data which is provided by a beacon sensor.
We can use beacon sensors for increasing our sales. The use of beacon sensors with our business app will increase the number of orders we receive. So, we can sell more of our products or services. The visitors to your store will receive customized notifications about ongoing promotional discounts and offers. Hence, they are more likely to buy what you are selling.
It goes without saying that the benefits mentioned above barely scratch the surface and what you can achieve with beacon sensors is dependent on your creativity and imagination.
Costs to Develop a Beacon Sensor App
The companies we mentioned earlier neither manufacture nor distribute beacons. Companies like Google and Apple only develop protocols and network architectures for the beacons to work on. Beacon sensors are manufactured and distributed by vendors and companies like MOKOSmart. So, if you want to buy beacons then you will have to reach out to companies like these to fulfill your needs. Each company has its own prices so you might want to do some research beforehand.
The beacon sensors are very economical and their prices vary depending on their data capacity, click to action rate, and battery life.
Any beacon project is not entirely dependent on the beacon sensors but it is also dependent upon your goals and the target devices. It can mean actions like pushing out notifications, enhancing customer interaction, delivering navigation withing indoors, close by payments, to name a few. The costs for developing your business app will vary as per your goals. It will also depend on the type of hardware you use and the costs associated with the maintenance of that hardware.
Estimation of costs
You should develop an app that can grab the attention of your buyers. For this purpose, you can choose between two available alternatives. First, you can either develop in house customized app or second you can go with a third-party app. If you develop an app on your own then it will incur significant costs, you will need a lot of time and expertise. The advantage of this option is that you will get an app that is tailored to your needs. On the other hand, a third-party app is very economical but it will limit your control and won’t meet all of your requirements.
Most of the third-party apps come with a dedicated suite. This means that you can access the desired customer data on the website along with the app as well. The customers also have the option to interact with the website as well. Hence, customers can go through notifications as per their convenience. This may limit your control but no data will face corruption or losses.
When you estimate the hardware costs then you need to look for a reliable vendor who has a good track record. You should then ask them for a quote and it can help you to put together an accurate estimate for possible hardware costs. If you want the vendor to provide extra services then you can ask for those as well and then you will then need to include them in your estimate as well.
You also need to consider the API. You will need a CMS or an API if you are looking to effectively manage your beacon project. Therefore, you need to keep the cost of the API in your mind as well.
0 notes
Text
LoRa frequency range
LoRa uses the CSS (Chirp Spread Spectrum) modulation which uses a frequency spreading method as a modulation technique. So-called chirp pulses are sent as symbols, which increase or decrease in LoRa frequency continuously over time. The data transmission is then realized by the sequential sequence of these chirp pulses.
Special properties
Since LoRa works in the ISM frequency bands (433 MHz, 868 MHz and 915 MHz), the radiated transmission power is limited. In order to have a larger radio range than conventional modulation types such as To achieve FSK (Frequency Shift Keying), the receiver sensitivity has been significantly improved with LoRa. The LoRa receiver can still successfully receive and decode a useful LoRa signal up to 20 dB below the noise level, which results in a receiver sensitivity of a maximum of -149 dBm. Compared to the maximum FSK sensitivity of approx. –125 dBm to -130 dBm, LoRa offers a significant improvement. With the FSK receiver, the signal can only be successfully decoded if the useful signal is approx.
Thanks to the property that LoRa can still successfully receive a useful signal up to 20 dB below the noise level, the robustness to radio interference is significantly better than that of FSK. FSK systems only work correctly if the interference signal is at least 10 dB weaker than the useful signal. In the best case, LoRa systems can still receive the useful signal if the interference signal is 20 dB stronger than the useful signal.
Limitations
From the graphic above you can see that LoRa can receive about 30 dB weaker signals than with FSK. However, there are two restrictions that somewhat relativize this big difference.
• First, the LoRa modulation is broadband than the FSK modulation, which means that the noise level of the LoRa receiver is generally higher than that of the FSK receiver. Specifically, doubling the bandwidth increases the noise level by 3 dB.
• Secondly, LoRa can only receive a useful signal up to 20 dB below the noise level at very slow data rates of ≤ 0.5 kbit / s. As soon as the data rate is increased, either the negative signal-to-noise ratio increases further towards zero or the bandwidth has to be increased further, which in turn increases the noise level.
Comparison measurement between LoRa and FSK
To find out how good LoRa really is, a direct comparison between LoRa and FSK should be carried out. For this purpose, our previously used standard FSK transceivers (CC1020 and CC1101) are compared with the data from the LoRa / FSK transceiver SX1261.
TransceiverModulation
Max sensitivity according to the datasheet
Data rateRX- bandwidth
CC1020FSK-118 dBm2.4 kBit/s12.5 kHz
CC1101FSK-116 dBm0.6 kBit/s58 kHz
SX1261FSK-125 dBm0.6 kBit/s4 kHz
SX1261LoRa-149.2 dBm0.02 kBit/s8 kHz
According to the information from the datasheets, LoRa achieves at least a 24dB better maximum sensitivity than with the best FSK transceiver (SX1261). Compared to the old FSK transceivers (CC1020 and CC1101), the maximum sensitivity is even 31 or 33 dB better. Since it can be assumed that the radio range can be doubled for every 10 dB more sensitivity, a 4 to 8 times the radio range should be possible with LoRa compared to FSK.
However, it is also noticeable that the maximum LoRa sensitivity is achieved with an extremely slow data rate of only 0.02 kbit / s. In order to obtain a direct, meaningful comparison between the different transceivers, the sensitivity of all transceivers is determined at the same data rate. According to Semtech's manufacturer, LoRa would have to achieve about 7 to 10 dB more sensitivity at the same data rate as FSK.
The SX1261 transceiver with LoRa modulation achieves 4 - 6 dB more sensitivity than with FSK modulation. In comparison to the CC1020 8 - 11 dB and in comparison to the CC1101 13 - 17 dB more sensitivity is achieved. It is striking that the lower the data rate is chosen, the more sensitivity gain can be achieved with LoRa.
Another view shows the energy-saving potential of LoRa. In order to achieve the same sensitivity as with FSK, approximately 4 times the data rate can be used with LoRa. The same radio telegram thus becomes 4 times shorter and the energy consumption also drops by a factor of 4.
Conclusion:
As with all radio transceivers, the maximum LoRa sensitivity of -149 dBm is only achieved at the lowest data rate. This data rate for LoRa is only approx. 0.02 kbit / s and is therefore unusable for many applications. However, if such low data rates can be used, 4 times the radio range is theoretically possible compared to modern FSK transceivers.
If the LoRa data rate is increased to 1.2 kBit / s to 10 kBit / s, LoRa achieves approx. 4-6 dB more sensitivity compared to modern FSK transceivers. Compared to older FSK transceivers such as the CC1101 or CC1020, the radio range can even be doubled or tripled with LoRa.
There is an interesting energy-saving option in applications where the current FSK sensitivity was sufficient. If the same sensitivity is to be achieved with LoRa, the data rate can be increased by a factor of 4 compared to FSK, whereby the energy consumption can also be reduced by a factor of 4.
For us, LoRa technology represents an interesting alternative for applications with data rates up to 10 kbit / s, since the radio range can be increased massively compared to the older transceivers. Of particular interest to us is the possibility of connecting to the LoRaWAN network, as this means that IoT applications can be connected to the Internet practically anywhere.
With our LoRa module "TRX433-70" we are ready for future innovative LoRa projects.
Radio transmission with LoRa
The meter readings, switching commands and other information can be transmitted from the concentrator module to the router and back in a variety of ways. If the wired transmission is not possible or too expensive, radio transmission with LoRa can be an alternative for remote reading.
The LoRa radio standard
LoRa stands for Long Range, i.e. high (radio) range and is an alternative radio standard to the known technologies such as UMTS or LTE. In many countries, LoRa has already established itself as the basis for a communication standard in the so-called Internet of Things (IoT), for machine-to-machine (M2M) communication and for industry and smart city applications.
The LoRa radio standard, like other radio technologies, uses the free LoRa frequency bands from the license-free ISM bands (Industrial, Scientific and Medical). In Europe, these are the bands in the 433 and 868 MHz range. By using a special radio procedure, the so-called frequency spread, the technology is almost immune to interference. The range between transmitter and receiver is between 2 and 15 km, depending on the environment and built-up area. Due to the high sensitivity of -137 dBm, high penetration of buildings can be achieved. The radio signals penetrate deep into the interior of buildings and basements. Especially at campsites where the metallic covers of the caravans and mobile homes often weaken the signal strength of WLAN, radio transmission with LoRa is superior here. The data rate at LoRa is between 0.3 and 50 kbit / s.
Applications for LoRa
LoRa is mainly used in applications in which very little data is to be transmitted over a long distance in a very energy-saving manner. These data are usually measured values, status signals or manipulated values.
Differences between WLAN, LoRa and mobile radio
WLAN and mobile radio are designed to transmit large amounts of data. Relatively short ranges are accepted. LoRa, on the other hand, is optimized for the transmission of small amounts of data over large distances. The following table shows some differences between the different radio standards.
LoRaWAN (long range wide area network)
Low Power WANs (LPWANs) are network concepts for the Internet of Things (IoT) and machine-to-machine communication (M2M). LPWANs are characterized by the fact that they can cover distances of up to 50 km and require very little energy. There are several technical approaches to realizing the LPWANs. One from ETSI: ETSI GS LTN, other names are LoRaWAN, Weightless and RPMA, which stands for Random Phase Multiple Access.
So that the bridgeable distance is not impaired too much by the free space attenuation, some of the LPWAN concepts mentioned use frequencies in ISM bands at 433 MHz and 868 MHz. Few also work in the ISM band at 2.4 GHz.
For example, as regards SigFox as LoRaWAN (Long Range Wide Area Network), it uses the ISM band at 868 MHz (USA 915 MHz) in Europe. The bridgeable distance range is over 5 km in the urban area and over 15 km outside the city. There are also radio transceivers in the LoRa frequency range of 2.4 GHz with which a range of 10 km can be bridged. LoRa transmission is a combination of Chirp Spread Spectrum (CSS) and Software Defined Radio (SDR). A key advantage is that signals that are up to 20 dB below the noise level can still be detected. The LoRaWAN concept supports bidirectional communication, mobility and location-based services.
The end devices are connected to a base station, which in turn receives the information encrypted from a backbone via TCP / IP and the SSL protocol.
To ensure that the battery life of the end components is as long as possible, all data rates and the RF output signals are managed by the LoRaWAN network and the end components are controlled via an adaptive data rate (ADR). There are three-terminal device classes: Class A devices can communicate bidirectionally and have a planned transmission window in the uplink, class B devices also have a planned transmission window in the downlink and the transmission window for class C devices is continuously open. The LoRaWAN technology is standardized by the LoRa Alliance.
LoRaWan - Framework for wireless networks
LoRaWan is a specification and describes a framework for wireless networks. It is used in networks with little data traffic, for example in sensor networks. LoRaWan (LongRangeWideAreaNetwork) is a so-called LPWAN (Low Power Wide Area Network) protocol. This article shows the frequencies used by LoRaWan and the available classes of end devices.
LoRa frequency varies in different regions of the world. However, it is necessary here to get more information before starting up a LoRa device in order to set the correct frequency. The following table shows the correct frequencies for each country or continent:
LoRaWan is also treated like a star topology. Gateways forward messages from the end devices to a specific access server. The gateways are connected via the standard server via standard internet connections.
Bidirectional devices
There are three main bidirectional classes handled by End:
Class A
The uplink data always originate from the end device. The uplink message is followed by 2 short reception windows for downlink messages. These downlink messages can also be included for confirmation messages as well as for device parameters. Since the communication between the terminal and the gateway will only ever be from the terminal, there may be a waiting time between the detailed new device parameters and the implementation of the terminal.
Between the actual transmission time contacts, Class A devices can put their LoRa module completely in an energy-saving mode. This will change energy efficiency.
Class B
Class B, others to class A's fault windows, become further reception windows. Class B devices are synchronized via cyclically sent beacons. These beacons are used to communicate, and other reception windows are open at other times. The loss is that the latency can be determined in advance, the loss of energy consumption as a component number. However, the energy consumption remains low enough for battery-operated applications.
Class C
Class C significantly reduces the latency for the downlink, since the receiving window of the end device is always heard as long as the device itself does not give any messages. For this reason, the trusted server can start a downlink transmission. A time change between class A and C is particularly important in battery-powered legal contracts, for example, "firmware-over-the-air" updates.
This article is from https://www.mokosmart.com/lora-frequency/
Follow and know us more on https://www.mokosmart.com/ if you’re interested in developing LoRa products!
0 notes
Text
Complete Guide on Bluetooth Location Beacon
A Bluetooth location beacon is basically a small Bluetooth radio transmitter that is powered by batteries. These are analogical to the functionality of a lighthouse. These devices continuously transmit Bluetooth Low Energy (BLE) signals. Most smart devices today are capable of receiving, interpreting, and displaying BLE signals.
We can install Bluetooth Location Beacons on real estate properties, large events, store-fronts, amusement parks, and other public venues. These help in location tracking and broadcasting relevant notifications.
Deploying Bluetooth Location Beacon is very flexible and simple. We can install these devices discreetly by using housings of various colors. These devices require very little energy to operate so their batteries can last from 2-8 years, and they don’t have to rely on any continuous external power source.
Bluetooth Location Beacons are also capable of providing sensor data. This may include the detection of movement, air pressure, temperature, light, humidity, and magnetism. This allows us to benefit from these devices in home automation, retail, healthcare, and industrial operations.
BLE Location Beacon Vs. Alternative Location Position Technologies
Bluetooth Beacon Technology is at the core of indoor positioning systems. It is one of the few latest technologies which have managed to become an industry-standard soon after their emergence. Bluetooth Location Beacons are small, cost-effective, and have long battery life. This technology allows for detecting the signal from the Bluetooth Location Beacon and then roughly calculate the distance to that beacon. Hence, it allows for effective location positioning. Now we will objectively look at some of the alternative location positioning technologies,
Wi-Fi
We can use Wi-Fi for location positioning in a similar way as Bluetooth Location Beacons. It will allow for a stronger signal and will cover more distance. However, Wi-Fi-based deployments have a higher setup cost, require expensive equipment, and rely on an external power source.
Near Field Communication (NFC)
NFC technology uses small chips that don’t need a power supply. The smart devices detect the chip, and if the device is within 30 cm of the chip, then it will read the serial number of the chip. This will allow for precise location positioning within 30 cm. However, NFC technology is available in only cutting-edge devices and the latest smartphones, so it will take some time for it to establish a foothold.
Magnetic field detection
Magnetic field detection via a compass sensor on a device is also used for location positioning. Fingerprinting technology is helpful for mapping the magnetic fields within the area of deployment. The device can then use this map for location positioning. The limitation of this technology is that we can use it only in certain settings where the magnetic fields are free from any kind of interference.
Equipment required for BLE Location Beacons
Bluetooth Location Beacon is a tiny device that makes them very practical. A Bluetooth Location Beacon has three main components,
A smart Bluetooth connectivity Module
One or more batteries for powering the whole assembly
A tiny ARM Computer. The CPU of this ARM computer has an attached antenna that broadcasts electromagnetic waves of specific frequency and wavelength.
To use Bluetooth Location Beacons, you may need some additional equipment,
External Power Supply: Some Bluetooth Location Beacons don’t come with batteries of their own, so they require some external power supply. We can integrate them into existing power supply networks because they consume very little power. Typically, Bluetooth Location Beacons are installed with lightings. This allows for masking their installation, and they can use the same power supply nodes as used by the lightings. Bluetooth Location Beacons which require external power supply are mostly used when they are required to function in limited hours. That is why we integrate them into existing power supply networks so that we can turn them on or off with other operations.
App: Typically, Bluetooth Location Beacons require an app for providing visitors location and navigation triggered content via their tablets and smartphone. Organizations have to choose between branded and generic apps, usually. Branded apps are mostly preferred because they do a better job of promoting the organization. This is because branded apps are dedicated to customers who are using only their content.
Content Management System (CMS): A CMS allows you to place Bluetooth Location Beacons, establish floor plans, control the content, and set up trigger points. CMS is usually maintained by the system provider and is mostly hosted online.
Use Cases of Bluetooth Location Beacons
There are many scenarios that require the application of Bluetooth Location Beacons. Here are some prominent examples,
Theft Protection
We can attach Bluetooth Location Beacons to expensive and valuable objects. Security personnel will receive a notification or an alarm will trigger when a beacon leaves a defined region or area.
Evacuation

Indoor navigation at Railway Stations/Airports
Bluetooth Location Beacons allow indoor navigation for railway or airline passengers. They can easily find the right track or gate, and important places of interest like restrooms, ticket counters, and cash machines. They can find these by using an app on a smart device.
American Airlines uses Bluetooth Location Beacons for sending location triggered content to nearby passengers through the American Airlines App. Passengers can use the American Airlines App to get information like boarding time, distance to gate, and nearest security clearance line.
Identification of Goods

Bluetooth Location Beacons can make it easier for workers in large warehouses to navigate through the storage sections. It will also make picking and delivering workflows more efficient.
Better Tourism Experience

We can deploy Bluetooth Location Beacons at tourist attractions to enable a better and more informed experience. Eldheimar museum in Iceland uses Bluetooth Location Beacons for providing visitors with necessary navigation information and location triggered content.
In-Store Positioning and Marketing

Stores use Bluetooth Location Beacons for sending discount coupons and special offers to customers in their stores via push notifications.
How to use the BLE Beacon position?
BLE technology allows for using Beacon position and gathered data in different ways. The way you use the BLE beacon position depends on your desired application.
Client-based
If you want to display the beacon positioning data directly on the smart device, then the device will receive Bluetooth signals directly from the installed beacons. The signals from these beacons will then allow for estimating the location by measuring the signal strength. The range of a client-based system is 30 meters, and the accuracy is 1-3 meters.
Server-based
In the server-based positioning, the Bluetooth beacon attached to the desired object sends BLE signals to Locator Nodes, which are deployed in the monitored area. The Locator Nodes process the gathered data and send it to a central server. This data then gives a position which is shown on a map for live tracking. The range of a server-based positioning is 75 meters, and its accuracy is less than 8 meters.
Positioning accuracy of BLE location beacon
The smartphone measures the strength of the incoming Bluetooth signal to estimate the distance to the Bluetooth beacon. This approach though efficient isn’t very precise in certain settings. The signal strength drops quickly for the first 1-2 meters, so BLE positioning is relatively accurate at these distances. However, the further the distance from the Bluetooth beacon, the less accurate the distance measurements. Certain other factors, like physical hurdles and signal reflections, also affect the signal strength, which in turn affects the estimation of distance.
For the purpose of generalization, we divide the detection of beacon proximity into three categories, which are near, immediate, and far. Immediate means 0.6 meters away, near mean 1-8 meters away, and far means 10-40 meters away. Mostly Bluetooth beacons give ideal performance within immediate and near applications. If we require positioning in the far region, then we simply detect the proximity of the smartphone to a beacon and then measuring the distance of that beacon to the nearest beacon and so on. If we adopt this approach, then we will need a larger number of Bluetooth beacons. That is why in large industrial spaces, we use a mix of immediate, near, and far beacons with a variance of 5 meters. Hence, the accuracy increases significantly, and we can obtain better results.
If you are looking to use BLE technology or deploying Bluetooth Location Beacons for improving the positioning of your workflows or facilitating your clients but can’t manage to do so due to the sophistication involved, then you should consider MOKO Smart. We will look at the specific requirements of your business and design a custom BLE positioning system tailored to meet your needs. We will optimize it to facilitate your workflows, and we will help you with mass deployment as well. Feel free to contact us if you have any questions or if you want to inquire about a quote.
0 notes
Text
Background on beacon asset tracking
Before we start talking about beacon asset tracking, let’s understand what is an asset in this context. Assets are equipment or items owned by a company. These items include transfer pumps, pallets, and trailers. Moreover, it further holds different manufacturing parts.
There is a difference between compressors and trailers. Compressors contain an onboard engine but trailers don’t. The assets that don’t have an internal battery or power source referred to as a non-powered asset.
There are thousands of non-powered assets out there. All non-powered assets have one property in common. Nobody is familiar with their exact location. So here asset tracking comes in usage.
What is asset tracking?
Asset tracking is a solution to track the usage and location of all types of assets. By using this method, you can track both indoor and outdoor assets.
There are different techniques used for asset tracking. However, some of these methods exist for a long time such as RFID or barcode scanning. Asset tracking has become very advanced after the arrival of modern asset tracking devices. Let’s talk about different technologies used for asset tracking:
Types of technology used for asset tracking
Before explaining different methods, let’s understand the difference between the traditional method and new asset tracking approaches.
Traditional approaches use a unique digital identity for all pieces of your equipment by assigning a specific number or code. You can achieve this by attaching the label to the equipment that holds a number. Besides the labels, you need the complete scanning infrastructure at different locations where you want to scan your asset. RFID, NFC, and barcodes are the most common types of traditional approaches.
New approaches use battery-powered tags for asset tracking. These batteries last up to 5 years that are capable to determine your asset’s location. All these processes use the internet as a communication medium.
The most popular type of new approaches is GPS and beacon asset tracking.
You can use any technology for asset tracking depends on your business. Let’s understand these technologies briefly:
RFID

Radio Frequency Identification uses radio waves to transmit the identity and some other characteristics of an object wirelessly. This method is most often used to track the mobility of people and other objects. All you need to put an RFID tag on the object. So an RFID system tracks it when it comes into the tracking range. Its tracking circle is almost 1 meter. The main advantage of RFID is its easy maintenance. Moreover, it is cost-effective.
Barcodes
In this way, a unique series of lines printed on a package of a product. We all know these lines as a barcode. It is another most popular way of asset tracking. You can print these lines on any material by using ink. However, you couldn’t print RFID on all types of products.
For tracking your asset, all you need to scan your barcode by using a barcode reader or a smartphone. Although it is a more-cast effective way but less reliable over time. Moreover, it doesn’t provide the possibility of automating your entire process.
NFC
Near Field Communication is almost similar to RFID asset tracking. However, it doesn’t require special RFID equipment. In this method, you can track your assets by using a smartphone. The most common example of NFC technology usage is a contactless payment system. NFC reader can read the tag within almost ten centimeters. You have to read all items separately.
GPS asset tracking
It is the most powerful way to track your assets globally. All previous devices depend on some installed infrastructure. However, GPS asset tracking doesn’t depend on such infrastructures. You can use these tracking devices to track any asset in the world.
These types of trackers don’t depend on the battery of vehicles. They rely on their own internal battery. It is the most precise method to track your assets. The main downside of GPS tracking is that it needs some energy.
GPS trackers have typically global usage. They use public telecommunication networks for communication purposes. You are very well familiar with different types of telecommunication networks such as 3G and 4G.
Beacon asset tracking
Beacon asset tracking is the latest and most effective way of tracking. You can use beacon asset tracking in different ways. First and foremost you can use fixed-location based beacons for asset tracking. They emit ID so different Bluetooth enabled devices use this ID for the connection. Secondly, you can use a moving tracker that also emits BLE (Bluetooth Low Energy). So different devices will pick these signals.
This asset tracking technology has some advantages over other tracking methods. It doesn’t depend on existing IT infrastructure for communication. This geolocation technology works precisely both indoors and outdoors. The accuracy depends on the number of beacons. More beacons mean high accuracy in tracking results. Another major advantage of beacon technology is that the battery life lasts for many years.
A brief history of beacon asset tracking
Bluetooth Low Energy (BLE) beacon technology is an innovative way to track people and other assets. Beacons arrived onto the scene back somewhere in 2013. They provided a unique way to the developers for tracking users in a physical space. Beacons were very cheap. So almost all major smartphone manufacturers adopted this technology rapidly.
This technology was very useful and had a lot of advantages over other traditional methods. GPS was the most effective way for asset tracking but that drained the smartphone battery. Furthermore, GPS was quite ineffective indoors.
The implementation of beacons is straightforward. In addition to this, beacons have diverse usage, therefore, they have a lot of usages. So all major companies start using this technology for asset tracking. Let’s understand the complete working mechanism of beacon asset tracking.
How does beacon asset tracking works?
There are different ways to track assets by using beacons. So all beacons have almost a similar working mechanism. Let’s discuss one by one:
1. Asset proximity detection, roaming mobile and asset beacons
In this approach, the asset is at a fixed location. You can attach different tags on each asset. It is the most convenient way to find the location of an asset. When a user comes close to an asset or a physical object. You can trigger an event when a user carrying an app comes close to the asset. So this is very helpful for your customers to easily find the location of an object.
2. Beacon asset location tracking with fixed BLE receivers
In this scenario, you mount beacons to the permanent fixtures. Moreover, you allocate specific tags to the assets that you want to track. When a specific asset comes close to the beacons, the BLE receiver broadcasts specific information. So beacons send the complete information about assets back to the receiver. Beacons use Wi-Fi or cellular data to send this information.
There are different advantages to use beacons for asset tracking. In this case, you don’s require any mobile application. Furthermore, you can track the location of tons of assets in real-time.
What asset should you check?
Locating your assets is an essential part of your business. Especially, when you have enough assets and don’t know where they are. And when they will arrive. Now the question is: what type of assets you want to track. You can check different types of assets both.
Let’s have a look at a few use cases that are very useful for asset tracking:
You can combine indoor and outdoor asset tracking to track different components. The components that are constantly on the move. And you want to know about their location frequently.
Track RTPs in real-time as they move in the international department and various warehouses. RTP stands for Returnable Transport Packaging. Moreover, you can enhance the rotation rate and avoid abuse by tracking your RTPs.
You can also track different rental equipment that transits across different countries to your potential customers.
Furthermore, monitors different supply chain KPIs. Measure subcontractor compliance and improve capacity management.
You can easily monitor logistics. For example, you can check parcel-movement through warehouses. Asset tracking further speeds up the entire process and eliminate errors.
The beacon asset tracking helps you in hospital management. You can enhance the use of medical devices and increase doctor performance by the exact location of the asset position. Moreover, you can monitor the location of staff in real-time to reduce their wastage time.
Asset tracking is very helpful in manufacturing firms. You can improve the efficiency of workers by monitoring their movement. Furthermore, you can keep your eyes on the goods movement for better management.
In short, you can use beacon asset tracking in almost all fields. It is because you can easily manage your all assets and monitor your employees to enhance their quality work.
The benefit of beacon asset tracking
If you implement a beacon asset tracking system successfully, you will notice many advantages. Here are some key benefits of beacon asset tracking.
Automated inventory: You can automate your entire inventory process. Deploy this tracking system and eliminate human error and frequent calling.
Optimized asset usage: You can understand over-usage, non-usage, and use-rate on your fleet.
Better customer service: It will enhance the management practices that will improve your customer service.
Reduced risk: You can timely detect the risk of theft and abuse of your assets.
Increase operational efficiency: Know the real-time location of your assets.
The promise of beacon asset tracking
Now, it has become evident that different firms can utilize beacons in more than one area. It is because beacons speed up the process of tracking and managing assets. Moreover, it also eliminates many common mistakes made during the process.
Tracking and managing all assets in the most important aspect of your businesses. Otherwise, resulting in lost equipment and incorrect data. So different types of industries and retails are utilizing this technology to boost their business performance.
This article is from https://www.mokosmart.com/how-can-beacon-asset-tracking-helps-you/
Contact MOKOSmart and we will help you with our beacon solutions and devices!
0 notes
Text
LoRaWAN Solutions VS. 5g Network
LoRaWAN solutions have the greatest quantity and variety of sensors today. On top of that, it emerged ahead of the 5G ecosystem and is the most reliable end-to-end solution available today. LoRaWAN solutions have deployments in more than 140 countries worldwide. Additionally, IoT experts and analysts are predicting that LoRaWAN solutions will constitute more than 80% of the LPWAN market in the next decade. In this article, we will try to explore whether LoRaWAN will show a dominant trend or will it co-exist with the 5G.
Development of LoRaWAN Solutions
LoRaWAN is very effective for long-range, wireless, and low-power radio networking. It operates in unlicensed frequency bands. Therefore, we can deploy it without any difficulty. Hence, it is easier and more convenient for devices with small footprints to communicate with other frameworks and devices on large scales.
LoRaWAN solutions are fairly simple to understand. The communication of star networks is analogous to the conversation in a classroom. The gateway is capable of communicating with the nodes and nodes are free to do the same.
Let’s suppose that your LoRaWAN solution has one node and four gateways. In such a case, the nodes will randomly transmit into the radio spectrum. The gate which can hear the transmission will catch it and forward it to the cloud. It is quite a possibility that all of the gateways will listen in on the message and forward it to the cloud. This eliminates the risk for loss of data due to weak communication links or interference of any sort.
Once your message reaches the cloud, the system will generate an acknowledgment receipt. However, this process is not automatic. In order for this to work, the nodes in LoRaWAN solutions will have to request acknowledgment receipts. If a node requests for an acknowledgment then the cloud chooses one gateway for responding after a fixed interval. This adds another layer of quality assurance. Almost all LPWAN systems have multiple receiving channels and LoRaWAN is no exception. LoRaWAN solutions are capable of receiving up to 8 messages at the same time across different frequency channels.
Challenges in Development of 5G

Like any emerging technology, 5G also faces some challenges during its development. We will take a look at some of these challenges in this section.
Manufacturing Costs and Retail Prices
It is expensive to build a 5G network as it requires sophisticated resources. 5G plans will incur high initial costs as it is not as simple as building another layer on top of an existing network. This is because 5G is a completely different technology altogether. According to market analysts, the total spending on 5G will reach $88 billion before a viable solution comes to market. Therefore, its high manufacturing costs are a big hurdle.
Restricted Frequency bands
Current LTEs operate on frequency bands below 6GHz. However, 5G requires frequency bands of up to 3000 GHz. Although, these bands have a greater capacity and promise faster speeds but their licensing is a big challenge. Licensing of these bands will most likely involve bidding before rolling out of respective 5G solutions. In the US alone, bidding of the 28 GHz band reached $690 million by the end of 2018.
Lack of Device Support
Many talks are going on for the manufacturing of smartphones and other devices that support 5g. However, their availability is tied to how quickly 5G becomes viable and how much is their manufacturing cost. Therefore, it is certain that we won’t see many devices with 5G support for some years to come.
Coverage and Deployment
5G offers a significant increase in bandwidth and speed. However, it has a limited range. Therefore, it will require further infrastructure before widespread deployments. Higher frequencies mean that the radio waves are highly directional as well. Therefore, it is easier to target them. This practice is called beamforming and has a threat for exploitation.
Another challenge is that the 5G antennas are able to handle more data but they have short-range coverage. The base stations and antennas are getting smaller but we have to install them on homes or buildings. Smart cities will have to install extra repeaters to allow spreading out of the waves over longer ranges. Hence, it will maintain consistent transmission speeds in densely populated areas. So, it is quite clear that the 5G network will take some time for maturing.
We intend to replace the Wi-Fi routers and modems in the future with 5G small cells. Therefore, we can bring 5G connections to our homes and small businesses. Hence, we will replace the conventional wired internet connections. So, it is a great challenge to spread the access of 5G to rural areas.
Privacy and Security
Ensuring security and privacy is a great challenge with any data-driven technology. However, 5G will have to ensure measures against sophisticated as well as standard cyber threats. Authentication and Key Agreement (AKA) is a system for establishing trust between networks and 5G falls under it. This will allow for tracking people nearby through the location of their smart devices. It will even allow them to eavesdrop on your ongoing phone calls.
Hence, it is the responsibility of 5G developers to ensure the digital safety of their customers and protect their privacy. The connectivity will surely increase as the data speeds get faster than current levels. Therefore, data virtualization services and cloud servers must ensure airtight security and protect the privacy and personal data of their users. However, their users must ensure that they are more vigilant and careful in sharing their sensitive data.
Pros of LoRaWAN Solutions over the 5G
Here are some of the pros of LoRaWAN over the 5G,
Cost-effective and Economical
LoRaWAN deployments are very economical and cost-effective. This is because they consume very little power and have a long battery span. On top of that, they are very small in size. Hence, installment and maintenance costs tend to reduce significantly.
Unlicensed Frequency Bands
LoRaWAN operates on unlicensed frequency bands. Therefore, it is easier and more convenient to deploy because no licensing fees are involved. Additionally, it allows for better inter-platform support and improved accessibility.
Widespread Support
LoRaWAN provides widespread support across sensors and devices of various types. It requires simple nodes to operate hence there is no need for any sophisticated frameworks. Therefore, we can use it for mass deployments and vast IoT implementations.
Long-Range Coverage
LoRaWAN supports long-range communications on its own. However, we can further increase its effective range by integrating a cloud service. This allows LoRaWAN to effectively communicate over the long-range as well as the short-range. The nodes in LoRaWAN networks communicate by first transmitting to the nearest gateways and then that gateway further transfers the data to the cloud server. The LoRaWAN gateways are efficient at picking up data packets so the chances of interference or noise are very low. On top of that, we can add additional layers of security in the form of acknowledgment receipts. These receipts allow us to ensure that the data packets are smoothly transmitting.
Privacy
LoRaWAN allows us to make hybrid public-private networks. This allows us to control user access to classified data and information. We can devise filters and implement screening mechanisms to avoid malicious attempts. Therefore, LoRaWAN allows us to have broad control over the degree of privacy we want our network to have.
Current and Future Trends of LoRaWAN and 5G
The depth and complexity of the 5G use cases mean that the sophistication of 5G is “too much” for certain networks. This will lead to a need for a “right-size technology” for supporting the existing applications in the market. IoT experts argue that 5G LTE provides better performance but it does so at the expense of certain key parameters. And these key parameters are well covered by the LoRaWAN solutions. Experts predict that LoRaWAN will exploit this limitation of 5G and try to capitalize on it. Analysts foresee that 5G might narrow the technology gap to a certain extent. However, there is always room for highly targeted and specialized solutions like LoRaWAN.
How LoRaWAN Solutions May Prevail?
Industry experts go as far as to claim that LoRaWAN will remain a De facto unlicensed standard even in the 5G era. They suggest that LoRaWAN is more convenient for mass adoption as it offers low battery consumption and enables hybrid public-private networks. The developments in 5G up till now are focused on critical communications and broadband services. Therefore, we can’t effectively use them for a large IoT deployment. Hence, we can clearly conclude that LoRaWAN will surely play its role in future IoT frameworks due to its optimal properties and promising traits.
If you are thinking about implementing LoRaWAN for your IoT implementation then you are in the right place. MOKO Smart can help by providing you the necessary LoRaWAN modules which you can deploy as per your requirements. Feel free to reach out to us if you want to know more about our products and services. We are hoping to hear from you soon.
0 notes
Text
Use Cases of LoRaWAN IoT in Satellite
Up till now, we have established why we need IoT in satellite and how LoRaWAN is a good fit for it. So, now we can take a look at some of the use cases of LoRaWAN in the satellite.
Fossa Systems

In the first week of December 2019, Fossa systems successfully launched their satellite. They are now operating it via their control mechanisms. This satellite is capable of directly communicating with the LoRaWAN devices deployed on Earth. The satellite is very small in size and Fossa claims that it is successfully communicating and picking up information from the LoRaWAN gateways and nodes.
Fossa systems named this satellite FOSSASAT-1. They launched it into orbit through a Rocket Launch from New Zealand. They launched it on the morning of 6th December 2019. The launch was a huge success as the satellite safely reached the orbit.
This satellite weighs 200 grams or 0.2 Kg and is built on the open-source standard names “PocketQube 1P”. The satellite is in the shape of a cube and its dimensions are 50 millimeters. The total expense for building and launching this satellite was around 25,000 euros. The success of this satellite venture might inspire other industry competitors and it may soon lead to a swarm of low-cost LoRaWAN satellites which are put into orbit for collecting information from the various IoT devices.
Fossa put a lot of effort into this venture and they had to spend some time on establishing a secure communication link. According to the company’s press releases, they are currently working on a complete deployment of the satellite’s solar cells.
Lacuna Space
Their satellite supports LoRaWAN IoT and LoRa hardware. Lacuna Space developed this satellite through another collaboration with Nano Avionics. The press releases of Lacuna Space claim that the satellite is performing extremely well and the results are beyond expectations even in the initial phase.
CTO of Lacuna Space, Thomas Telkamp claims that the test sensors are deployed in various countries and they are successfully communicating with the satellite. The countries include the Netherlands, South Africa, England, the United States, Japan, Slovenia, India, and some remote islands in the Indian oceans. Thomas claims that all of the sensors in these geographical locations were able to successfully communicate with the satellite’s gateways.
Lacuna Space is planning on establishing the “Lacuna Constellation”. For this purpose, they intend to launch three more LoRaWAN satellites by the end of 2019. Therefore, they can enhance the overall performance of their IoT network. Lacuna Space is also working on their novel adaptive Radio system which allows for signal detection even from remotest of sensors.
Lacuna Space is planning to perform an extensive demonstration of its network by the end of 2019 or the beginning of 2020. For this purpose, they are going to receive support and funding from the U.K. Space Agency and the European Space Agency.
LoRaWAN IoT Used In Satallite
If you are seeking help with your LoRaWAN IoT deployments then you are in the right place. MOKOSmart specializes in LoRaWAN gateways and we can develop dedicated LoRaWAN modules and other LoRaWAN products as per your needs and requirements. If you would like to know more about our services or if you want a quote on our specialized products then feel free to contact us.
LoRaWAN IoT is the latest development in LPWAN (Low-power, Wide-area Network) technologies. It is specifically designed for connecting battery-operated devices to the internet is global, regional, or national networks. This allows us to target the main IoT (internet of things) requirements such as end-to-end security, bi-directional communication, localization, and mobility services.
LoRaWAN network architecture is modeled on the star-of-stars topology. In this topology, gateways relay messages between a central network server and end-devices. Therefore, the gateways use standard IP connections to communicate with the network server. Hence, they act as a transparent bridge for the conversion of IP packets to RF packets and vice versa.
LoRaWAN technology allows communication over a long-range by using the capabilities of the LoRa physical layer. So, it allows for a single-hop link between the gateways and the end-devices. Therefore, all modes are capable of bi-directional communication. Therefore, it gives us support for multicast addressing groups for efficient use of the spectrum during various tasks. These tasks include mass distribution messages and FOTA (Firmware Over-The-Air) upgrades.
Need for IoT in Satellite
The growth momentum of IoT can play a vital role in Satellite technology. Here are some reasons which advocate the need for IoT in Satellite,
Transforming satellite connectivity through LoRaWAN IoT
Satellite technology serves as a major tool for development across various industries and can transform the IoT connectivity as we understand it today. So the satellite operators can deliver strategic advantages over various domains for all customer segments by harnessing the potential of IoT.
Connectivity for remote assets
Many business operations extend to remote environments and therefore, businesses have to rely on satellites for critical communication. Hence, we need a remote facility for monitoring unmanned sites, offshore platforms, and real-time asset management.
Use of sensor networks
Mining and energy companies often have to indulge in offshore exploration projects. Therefore, these companies need extensive usage of satellite driven sensor networks. Hence, IoT can help with establishing such networks on any given scale of application.
Improving the infrastructure
Cargo Vehicles, maritime vessels, and trains rely more and more on broadband connectivity as a consequence of the burgeoning trend across the global landscape. Therefore, the use of IoT in satellite communications is empirical for enabling the next generation of transport services.
Smart and sustainable cities
Smart city developers and administrators are working hard to harness the power of IoT. So that they can efficiently use the available energy and perform better resource allocation. Hence, this will allow them to make smarter and more sustainable cities. However, terrestrial networks fall short in some remote areas. Hence, IoT in satellite services can help the development of smart grids in such remote regions. It can also act as a reliable backup network for critical tasks and services such as security and safety.
Vehicle Connectivity
Most car manufacturing companies are providing safety features in their vehicles which includes airbag deployment notifications and automated emergency calls. However, we can only achieve the availability of such services if we ensure IoT supported satellite coverage allover the world.
Fitness & Healthcare
Most athletes rely on small sensors for tracking their location and collecting bio-data. This bio-data includes blood pressure, oxygen levels, and heart rate. So, we can use this gathered data for tracking health risks, identifying the location of injured athletes in remote areas, and monitoring the training progress.
Mobile banking and retail
We can use LoRaWAN in satellites as the integral backbone of banking communication. This will help in keeping wireless ATMs and mobile applications running smoothly in all geographical regions.
Features of LoRaWAN IoT
Here are some distinguishing features of LoRaWAN IoT
Long Range
A single base station working on LoRaWAN allows for deep penetration capability for indoor coverage and urban environments. It allows for connecting with sensors that are more than 15-30 miles away in rural areas.
Low Power
LoRaWAN IoT deployments allow for low power consumption. Therefore, it is possible for batteries to have a lifespan of up to 10 years (this may vary according to the application).
Geo-location
It allows for tracking applications without consuming additional power or relying on GPS.
Low Cost
LoRaWAN IoT deployments require low investments. Additionally, they have low installment and maintenance costs. Since they consume less power, therefore, they have low operating costs as well.
Open Standard
LoRaWAN works on the open standard provided by the LoRa Alliance. Therefore, it is ideal for IoT deployments because it allows for interoperability among devices. Hence, it is well-suited for telecom operators and IoT solution providers because it is easier and convenient to adopt.
Final Word
LoRaWAN IoT in the satellite is a new yet promising market. There is a dire need for more startups to step in and come up with a cost-effective and small time-to-market solution. Lacuna Space and Fossa Systems have successfully launched their LoRaWAN IoT satellites and there is open space for more competitors. Market analysts predict that companies that make a move now towards LoRaWAN IoT in the satellite will manage to secure promising returns in the long runs.
We are moving toward a smart future where IoT deployments and enhanced connectivity will play a vital role. Therefore, it is empirical that a strong and reliable framework exists for handling big data and massive traffic. LoRaWAN IoT has shown a lot of potentials in this regard and hence it is slowly becoming the de facto standard for long-range communication between various IoT nodes. LoRaWAN IoT devices will keep gaining popularity and its embedding in satellites will lead to a new era of smart networks.
0 notes
Text
What is LoRaWAN Technology?
If you are working with networked devices, you may have heard of LoRaWAN at one time or another. It is a long-range network protocol. It enables the networking of things with the Internet even over longer ranges with low energy consumption. This solves one of the big problems that applications within the Internet of Things have faced up to now. With a battery life of up to five years and low maintenance costs for the sensor network, the LoRaWAN can be used for a wide variety of new applications.
This gives you a brief overview of what the LoRaWAN can do. In this article, we look at the architecture, key features of core technology, and the latest use cases where it is used.
What is LoRaWAN Technology?
The great thing about this technology is that it is based on an open standard. It uses an unlicensed spectrum as part of the ISM frequency band (“Industrial, Scientific, and Medical”, German: Industry, Science and Medicine). In Europe, the LoRaWAN uses the 868 MHz frequency range, while in the USA the 915 MHz frequency band is released. By using the unlicensed spectrum, it is very easy to set up and use your own network. Many telecommunications operators are already using LoRaWAN and offer the technology as part of their service offering in numerous countries worldwide. Comcast, KPN, Orange, SK Telecom and many other providers are actively implementing large-scale launches in their markets. This makes LoRaWAN even more interesting as a technology because it is compatible with the networks of different operators – large and small.
The LoRaWAN standard is monitored by the LoRa Alliance, which in turn consists of over 500 members who support the protocol and align many of their components, products, and services with LoRaWAN. These include companies such as MOKOSMART, ARM, Cisco, Microchip, and ST.
What distinguishes LoRa from LoRaWAN?
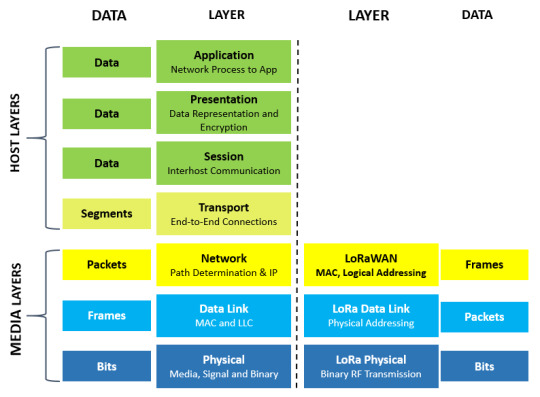
Let’s start with the definition of LoRa – what is it exactly and how is it different from LoRaWAN? LoRa is a wireless technology similar to more common technologies such as Wi-Fi or WLAN, Bluetooth, LTE, and Zigbee. However, technology often does not cover all requirements, which means that users have to accept compromises. LoRa meets the demand for low-cost, battery-operated devices that can transmit data over long ranges. However, LoRa is not the right solution for the transmission of data over large bandwidths. LoRa is a technology that converts data to be transmitted into electromagnetic waves. This technique is also known as the chirped spread spectrum,it has been used in military and space communications for decades. It is due to the long communication range and the low susceptibility to interference.
LoRaWAN, on the other hand, is the MAC protocol for the network of high-performance LoRa nodes based on the Internet of Things, which cover long ranges and have low energy requirements. It uses the advantages of Lora described above and optimizes battery life and service quality for the LoRa nodes. The protocol is completely bidirectional, which ensures reliable message transmission (confirmation). End-to-end encryption is provided for security and data protection purposes, over-the-air registration of endnotes and multicast functions. The standard also ensures compatibility with LoRaWAN networks around the world.
LoRaWAN architecture mainly consists of four elements:
• End nodes
• Gateway (base stations/router)
• Network Server
• Application serverEnd nodes
End nodes are physical hardware devices that are equipped with sensor functions, a certain amount of computing power and a radio module for translating the data into a radio signal. These end devices can transmit data to the gateway and also receive it. Even with a small battery, they can last several years if they are put into deep sleep mode to optimize energy consumption.
When a device sends a message to the gateway, this is known as an “uplink”. The answer that the terminal receives from the gateway is called “downlink”. On this basis, a distinction is made between three types of end devices:
• Class A
• Class B
• Class C
Class A devices have the lowest energy consumption compared to the other two classes. However, these can only receive a downlink if they have sent an uplink. Class A devices are suitable for the transmission of data at time-based intervals (e.g. every 15 minutes) or for devices that send data based on events (e.g. if the temperature rises above 21 degrees or falls below 19 degrees).
Class B end nodes allow more message slots for downlinks than class A. This reduces message latency but is also less energy efficient.
Finally, class C has an ongoing receive window that is only closed when the device sends an uplink message. Therefore, this is the least energy-efficient variant, which often requires a constant current source to operate.
Gateways
Gateways are also known as modems or access points. A gateway is also a hardware device that receives all LoRaWAN messages from end devices. These messages are then converted into an array of bits that can be transmitted over conventional IP networks. The gateway is linked to the network server that transmits all messages.
Gateways are transparent and have limited computing power. More complex tasks are carried out in the network server. Depending on usage and type, gateways are available in two versions:
Gateways for indoor use, e.g. MKGW2-LW, MOKOSMART.
Network Server
All messages from the gateways are forwarded to the network server. This is where the more complicated data processing processes take place. The network server is responsible for:
1. Routing/forwarding messages to the right application;
2. The selection of the best gateway for downlink messages. This decision is usually made on the basis of a link quality indicator, which in turn is calculated via the RSSI (Received Signal Strength Indication) and the SNR (Signal to Noise Ratio) of packets that were previously received;
3. Removing duplicate messages when received by multiple gateways;
4. Decrypting messages sent from end nodes and encrypting messages sent back to the nodes;
5. Gateways usually connect to the network server on an encrypted Internet Protocol (IP) link. The network usually includes the commissioning of the gateway and a monitoring interface that enables the network provider to manage gateways, remedy faults, monitor alarms, etc. …
Application server
The application server is where the IoT application is located – this is particularly useful for data captured using end devices. In most cases, application servers run via a private or public cloud, which is connected to the LoRaWAN network server and handles application-specific processing. The interface with the application server is controlled by the network server.
• LoRaWAN functions• Bi-directional communication
A terminal can transmit data to the gateway and also receive it according to the settings. These settings can also be called up within the application.
Localization
An interesting function of LoRaWAN is the localization without the need for GPS. This is particularly useful for tracking systems and sensors since it is battery-efficient and can be maintained more cheaply than conventional methods.
Scalability
LoRaWAN was designed for large IoT deployments in which thousands of devices are networked with a manageable number of gateways. These gateways can monitor multiple channels and process multiple messages at the same time.
Another important property of LoRaWAN is the speed with which data can be transmitted. There are different data rates that can be used for the transmission. These are also called spreading factors (SF). A slower transmission enables a longer and more reliable range.
For example, imagine you are talking to someone who is very close to you. You can speak very quickly in this situation and your counterpart understands everything you say. When you speak to someone who is far from you, you have to speak much slower to be understood. This principle also applies to the LoRaWAN protocol.
Adaptive Data Rate
With LoRaWAN, the network can also automatically optimize the speed at which the device transmits its data. This function is called the adaptive data rate (or ADR) and is particularly important to increase the capacity of a LoRaWAN network. ADR allows us to easily scale the network by adding another gateway. Because of this gateway, many end devices now automatically adjust their spreading factor. As a result, the individual devices are shorter “on the air”, which means more capacity for the network.
The adaptive data rate (abbreviation: ADR) is a simple mechanism that adjusts the data rate according to the following rules:
If the radio signal strength (also called “link budget”) is high, the data rate can be increased;
If the link budget is low, the data rate can be reduced.
Safety
It is important for every LPWAN to use a comprehensive security solution. LoRaWAN uses two levels of security: one for the network and one for the application. Network security ensures the authenticity of the end device in the network, while the application level ensures that the network operator does not have access to the application data of end-users. AES encryption is used for key exchange.
The network level is responsible for identifying the node. It checks whether a message really comes from a specific device and is also considered an integrity check. It can also encrypt MAC commands.
The application level is used for the decryption and encryption of payloads.
Both keys are encrypted with 128 bit AES in ECB mode.
Use cases and areas of application
LoRaWAN has found its place on the market in terms of applications and areas of application. Thanks to its unique properties, LoRaWAN is best suited for scenarios like these:
1. Access to electricity (electricity) is limited or restricted;
2. The locations are physically difficult to access or very remote;
3. The number of end devices is significantly higher compared to conventional mobile phone connections;
4. The end devices do not have to send messages continuously.
0 notes