#it was my like. go-to password which i use on most websites to avoid forgetting
Text
Wireless mouse software update 1.0

#Wireless mouse software update 1.0 install
#Wireless mouse software update 1.0 password
In spite of the railing against it in the comments, it IS a keeper.A year before the Macintosh was released, Apple’s Lisa introduced the concept of a GUI and mouse to Apple’s customers. Thank you Ryan and GOTD for this useful little gem of a program. I always enjoy your comments and input, but every person and situation is unique, and sometimes less is best.
#Wireless mouse software update 1.0 install
Suggesting people install other programs and do maneuvers (autoit, powershell, etc - that may seem simple to you) simply to avoid the offered GOTD and it's obvious purpose is contrary to usefulness. This program is meant to be simple - it has one job. This GOTD "worked immediately and does precisely what it says and keeps the screen from dozing off, no more, no less" and that is why I am returning to I can't tell you how many times when a simple request ended in complex solutions like "just run." or "just compile." as seen in the comments for this GOTD. I appreciate the suggestion, but PowerToys comes with features I will never use nor want. Mike, I installed Microsoft's PowerToys and gave it a try. I only wish it came with a time setting, so I could set it to be active/inactive for just a specific amount of time. This simple program worked immediately and does precisely what it says and keeps the screen from dozing off, no more, no less.
#Wireless mouse software update 1.0 password
But if those guests leave for a few hours at a time, I'd rather not be bothered having to input my login password each time I'm reading something on screen and forget to move the mouse. I sometimes use the screensaver with logon screen setting checked if I have guests for a weekend, for example - and I set the time for 1 to 3 minutes - tight. Using the screensaver is faster than even 'Win + L' (for returning to the screen), and 'Win + L' is not automatic, so ss is my primary choice. This is generally when others are around and I need a basic 'auto-hide' function to keep eyes and fingers away from my device. I also need the logon screen to appear each time the mouse is moved and the screensaver is halted. There are times I need the screensaver in Windows, but the screensaver isn't enough. Others may not understand, but it works well for me. Save | CancelĢ steps instead of 6+ steps? I'll take it. If your wife goes into labor but it appears that you worked right through the crisis (no timeouts), you might need to review your resume. Just remember there could be times you would need to turn it off. Don't use this if you work for a decent company, but if you have been being scammed by your employer, then. But, if MouseJiggle were installed, all that time those tiny mouse movements were going on could keep you earning money. You were NOT working, and now you are not going to be paid for that time. Your boss sees that you timed out and did not re-login for over two hours. The next thing you know, it has been two hours since you were at your desk. The highlights of that game are on so you start watching. Now, suppose you are working from home connected to your company's website. You may not want to use it when you are on your bank's site because that timeout they control is for your good and theirs. MouseJiggle will keep your session alive. How can you control that from your PC? You can't. Now, what about when you connect to your bank? You may not be finished looking at something so you take a little longer, then when you move your mouse to go to another page, you get the notification that your "session" has timed out. Most comments are focusing on the PC's timeout setting, which can in most cases be controlled on your local computer.

0 notes
Text
✨ Internet Safety ✨
For our generation today, the internet is probably the safest place to be in. People can be whoever they want, express whatever they want, and enjoy themselves however they want. I must admit, I would also say that I couldn’t live without the internet. Internet is just the solution to every problem, right? Now, we can even earn money in the comfort of our rooms with the help of the internet. Should we spend hours travelling just to buy stuff? Nah, we got the internet! With just several clicks we can already make an order and just wait on our couch to receive it. Oh no, COVID-19 ruled the world! No worries, we are backed up by the internet. Online classes, online transactions, online dating. You name it. The internet is there for us, or is it? Is it our safe haven?
We have put so much trust in the internet, but we didn’t know it can also be our biggest predator. Online transactions were fun until you got scammed and lost all your money. Online dating them feel loved until the person they were talking to is a catfish. Streaming online made him famous and rich, until his account got hacked. And there are still millions of stories out there that should awake us from believing that the internet is the safest thing in the world.

Below are some possible dangers you could encounter online.
1. Cyberbullying
I’m sure many of you have heard of this. But even though we are fully aware of it, it is still one of the major problems until now. As we casually scroll in our social media feeds, it is already normal for us to see people making fun of or “bashing” other people. It became so prevalent that we could call it a normal thing. According to UNICEF (2019), one in three young people has said that they have been a victim of cyberbullying and that it affected almost half of the Filipino children aged 13-17. We need to know that even a single word like “tanga” or “bobo” we see in our social media platforms and online gaming worlds could affect or traumatize us greatly.

2. Data Being Stolen
Some people nowadays are getting better at doing this. They can steal your money from your accounts, apply for a loan or credit card using your name, or sell your information to an online criminal as well. The hidden website is packed with criminals who purchase and sell stolen personal data. If your data is stolen, you can experience spam attacks. But most of these data thefts try to steal sensitive information, such as your credit card or personal information to commit identity theft.

3. Exposure to Inappropriate Material
Another risk especially for children and teenagers are exposure to inappropriate materials that are sexual, hateful, or violent. The chance and probability for children to look at anything inappropriate rely on how much they do online as they get more active online at a younger age. Whether it's a free-time graphic pop-up commercial, children's cartoon characters in adult circumstances or a self-harm forum, an innocent search might expose these children to contents that make them feel puzzled and angry. Some of the inappropriate content includes pornographic material, content containing swearing, sites that encourage racism, violence, terrorism, or even suicide, sexism sites, or gambling sites, and so on.

Based on my own experiences, here are some tips I would like to share to you to look after your privacy and secure your internet safety:
1. Keep your software up-to-date
Not only will you get a better program experience, but you will also be able to iron out your security issues. But the reason why you must keep it updated is that hackers are fast enough to become aware of certain software’s vulnerabilities, thus could harm your computer system and personal data. If you avoid doing these updates, you are bound to face persistent bugs, data loss, malware infection, and of course security issues.
2. Update your passwords
Why do we need to constantly change our passwords? So that we can reduce the risk of other people having access to our accounts, thus corrupt our personal data. Using strong passwords is necessary for us to prove our identity in our accounts, websites, or our computer itself (Wright, 2021). My tip in creating passwords is random characters with a symbol, number, and at least one capital letter. The reason for this is that using weak passwords, such as patterns of letters and numbers, or simply your name and some important date you know can cause hackers to guess and open your account, hence impersonate you to commit fraud and other crimes.
3. Use two-factor authorization
Familiar with this term? Yes, a two-factor authorization (2FA) is an extra step to keep your accounts more secure and avoid getting hacked by others. One of the most common 2FA methods is one-time codes sent through SMS or email, authenticator apps such as Google Authenticator, and security keys such as U2F tokens (Drozhzhin, 2018). This one for me is the best 2FA authorization because only your private key will confirm your login. If someone will try to log in to your account with the wrong security key, they will not be granted access to your account. So, there you go. A series of two-factor authorizations that will secure your accounts the best way possible. You’re welcome!
4. Be careful what you click on
Have you heard of phishers? They are attackers that send a fraudulent message designed to trick and victimize us into revealing sensitive information to them. As scary as it sounds, we need to be aware of what we click on to avoid experiencing this. Phishing is usually done in an email when they get your email address from somewhere. These phishers try to create a fake website to trick you into typing in your personal information. It’s much easier for them to hack our accounts this way. To avoid this, you can check the URL’s legitimacy by using the Google Transparency Report or simply avoid suspicious emails which require your personal information. Think before you click!
5. Back-up your data
Data back-up and recovery has many advantages. Some of these are protecting and saving your data, provides ease of management, ensures accurate information of your data, quick access to data, scalability, and such (Becker, 2021). There are many other ways to back up your data, but here’s a simple way to manually back up your data in your phone is to open your phone’s settings app, tap system and click backup or search backup in your settings app, then tap back-up now. It’s that simple.
6. Set up notifications for your most important bank accounts
As online bank account holders, it is our responsibility to making sure our accounts are protected. Online accounts are one of the easy targets of hackers to whisk away our money with just a couple of keystrokes. To safeguard our online banking, we may choose an industrial-standard security bank or credit union that utilizes text or e-mail warnings avoids the use of public Wi-Fi access and periodically changes your password.
7. Protect your personal information
This might be difficult for those who like to express themselves on social media, but we must protect our personal identity to avoid any sort of online threats. To protect our identity, we must limit the amount of personal information we share or provide. We shouldn't share or provide this information online: exact home address, your place and schedules of classes or work, birthday, cellphone number, and most importantly our passwords or account information. Another tip is to write down in a small notebook all your passwords and keep them safe in a secure place away from your computer.

8. Use parental controls and stay present
With the pandemic going on right now, parents should be extra careful of what their children see and hear about themselves and who they encounter on the internet. To protect your children from internet risks, talk to them frequently, utilize tools to safeguard them and watch out for their work. Monitor the time of your child, especially the younger ones, about when and how long they stay online. Keep your computer at a central location in your house, where it's easy to watch what your children do and look at online. You may configure them for mobile devices to forget Wi-Fi passcodes for your kids not to go online without knowledge. Review privacy and location settings, parental control and use secure browsers, apps, search engines and YouTube search settings. Lastly, limit camera and video to prevent your children from accidentally taking photos or videos of themselves or others.

The internet does not usually hurt us unless we react to suspect material and websites. The first reason you don't know what you're doing is because of internet damage. Secondly, you may react or click on links such as appealing advertisements, infected software and communications when you have other forces. To ensure internet safety, just remember those tips above and these three things: secure your network, be responsible, and make the internet child-safe.
References:
Becker, D. (2021). 6 Advantages of Data Backup and Recovery. IT Central Station. Retrieved from https://www.itcentralstation.com/articles/6-advantages-of-data-backup-and-recovery
Drozhzhin, A. (2018). SMS-based two-factor authentication is not safe — consider these alternative 2FA methods instead. Kaspersky Daily. Retrieved from https://www.kaspersky.com/blog/2fa-practical-guide/24219/
Wright, J. (2021). Why Is it Important to Change Your Password? Small Business Chron. Retrieved from https://smallbusiness.chron.com/
Online bullying remains prevalent in the Philippines, other countries (2019). Unicef Philippines. Retrieved from https://www.unicef.org/philippines/press-releases/online-bullying-remains-prevalent-philippines-other-countries
25 Best Internet Safety Tips for Every Situation (2021). The Neeva Team. Retrieved from https://neeva.com/learn/25-best-internet-safety-tips-for-every-situation
3 notes
·
View notes
Text
College Project
This is kinda long, so I’ll put it under a read more, but I’d love it if a few people at least would read it and like it!
I have never had one single memorable moment on social media, but I would like to talk today about one of the defining things that happened for me online.
I am a writer.
Specifically, that much-hated creature, the fanfiction author.
I’ve been writing fanfiction since 2015, when I wrote my first fic (as we call them)
It was a Warriors fanfiction.

My first account contained two stories, both Warriors fics.
I lost the password. Whatever. They weren’t too popular. I wasn’t a “big” author.
I made a new account. This one ended up with 26 fics on it, before I abandoned the account and the site, which wasn’t great.
I moved to a new website

archiveofourown.org, or more commonly AO3.
This was 2018.
Here, I took up the second pen name I had used on the old site, and started writing again. I moved some old stuff over and left others abandoned.
I now have 41 works on this site, and I’m no longer invisible.
Here’s the story of my most popular fanfic:
I love the TV show

And I love one popular fanfic trope: reaction fics.
Where the characters of a franchise watch or read their own book, movie, or TV show.
These things inevitably came together in one glorious collision.
Fate’s Expose.
It.
Blew.
Up.
Holy crap, did it blow up.
The comments poured in.
People bookmarked it. They left kudos. They subscribed.
And oh, did they comment.
Holy crap.
It remains my most popular fic to date.
I finished it over a year ago, and people just keep finding it and reading it.
Now, I’m not going to claim that mine is the only one of its type.
Far from it.
The tag “watching the show” brings up two fics. Simply searching the phrase or “reaction” brings up more.
But mine was, dare I say, the best written of the bunch.
I won’t claim it’s my best story.
Nope.
Rereading it makes me cringe. I started it in March of 2018, when I was seventeen and only decent at writing. I look at my writing from then and wince:
(from chapter one:)
“I’m going to be showing you my absolute favorite TV show.” She enthused, bouncing on the balls of her feet.
“A TV show? You somehow kidnapped us all to watch a freaking TV show?” demanded Hopper, clearly trying to avoid swearing.
Annoying OC? Check!
Basically a self-insert? Check!
Ugh. Please don’t remind me of how badly I handled Fate.
But.
Mine is complete, at least for the first two seasons!
I was overwhelmed when I started posting it and all that love came pouring in. The first few chapters had so much support.
I wasn’t what you might call consistent. By which I mean, you were lucky if I updated more than once in a few months.
Oops.
It took me over a year to finish the fic. Most of that year was radio silence.
Because writing fics is hard.
And reaction fics are harder than most.
But the upset readers were minimal. Every so often, I’d get one of those comments, the ones that every fanfic author hates.

Yeah.
I pulled through. I got
So.
Many.
truly wonderful comments, like
This one:

And this one:

(aaaaand some legitimate criticism-)
I finished all seventeen chapters. It has over twenty-thousand hits, and hundreds of likes and comments.
I can’t forget this fic. It’s a crowning achievement and really changed the way I handled my writing. The love and support I got with this fic is just so much, and so good, and I still look back at it fondly. I may have moved on from Stranger Things, and finished the fic what feels like a lifetime ago-
(what do you mean, i finished it in may of last year? shut up)
But it’s changed the way I write and the way I interact with others.
And it encouraged me to keep going and write MORE MORE MORE, on all kinds of subjects, and really started me on my specialty of reaction fics! (Having written five…) So thank you, Fate’s Expose. It’s old, it’s not my best work, but it’s my most popular fic and it taught me a lot about writing, about responding to others, and about myself.

#ella rambles#a college project#no personal info included#please at least like this#please i beg#this project has to be circulated and stuff and i might need#to show proof#that i posted it somehwere#*somewhere#adventures in bs
4 notes
·
View notes
Text
Passwords
001 Many sites on the internet require passwords. Although they seem a nuisance, they protect you. Consider them like a key to a door.
002 Why bother with passwords?
(i) Financial Management
For most people this means online banking. If you use a weak password it is likely it will eventually get hacked. Needless to say this could result in you losing money.
(ii) Auction Sites
If someone hacked your account they could make binding bids or buy things in your name.
(iii) Stock Trading
This is like (i) plus (ii). Someone could buy or sell stock or have stock transferred.
(iv) Social Media
Hacked social media accounts can be used to post compromising messages that could embarrass or defame somebody, be used for harassment, or to build up a picture of who you are and everyone you know. This could result in a visit from the police. Social media is also very useful for hackers for enabling identity theft.
(v) Shops
Hacking one of your shopping accounts (e.g. Amazon) would only be an issue if you have a “stored” payment method such as credit card details.
If you discover that your payment information was used to ship unexpected goods to an unknown location, it’s clear that someone has hacked your account.
(vi) Gambling
A hacker could generate debts on your behalf.
003 How To Design a Good Password
The important things when designing a password (in order) are make it -
(i) Memorable,
(ii) Long – the longer the better (at least 12 characters),
(iii) Complex,
(iv) Different for different sites.
004 The Core of the Password
First of all create a “core” password with a string of letters. Three ways ways of doing this include -
(i) Initial Letters
Open your favourite book. Go to a memorable page e.g. your birthday. Read the first sentence. For me this would be “The Age of Reason” by Sartre. My birthday is on the 23rd. The first sentence of the first paragraph on page 23 is “Boris bitterly regretted never having been there, he would certainly go if it reopened.”
This makes bbrnhbthwcgiir – 14 characters. If I forget it I just have to go to my favourite book.
(ii) Relevant but Not Guessable Words
This could be a street name, hill names, school name, stream name(s), car. Don’t use words relevant to you or close family. However, you could use a relative’s street name etc. Hill or mountain names, especially if non-English, are good. Similarly, the name of your school is bad because a hacker could probably get it from Facebook. So use a relative’s school instead. The advice regarding streams/rivers is the same as for hills/mountains. If the resulting password is too short add something relevant.
So, examples from these could be -
springwoodbank (where my parents-in-law lived)
anteallach (a Scottish mmountain)
bluemountainsgrammar (a school in Australia)
severnriver (a river far away)
deloreanbelfast (not my car!)
or -
Look out of the window - flowerwheelbarrowbinhusband
Look at your wall - picturetelevisionblue
Look at your spouse - greynoseartist
(iii) A Silly Phrase
Examples could be -
weneedanewcomputer
mustremembermilk
quickbrowndogs
lillylikeschocolate
myneighbourisnoisy
dollypartonhasbigboobies
These are long and memorable.
005 Make The Password More Secure
The core password generated as above satisfies the first two criteria – long and memorable. You could use it as it is. However, to make it even better we can add complexity. There are three easy ways of doing it – add special characters and/or numbers and use mixed case. But where to put the number and special characters? The easiest is between each word (ignoring example (iii) above) but the better way would be to place it in random places. The downside here is that random places make it less memorable.
(i) Special characters such as !, £, $, _
flower_wheelbarrowbinhusband
bbrnh£bthwcgiir
springwood!bank
we_need£a$new_computer
Bear in mind that some sites only allow certain special characters.
(ii) Numbers
The question here is how to decide what numbers to use. Anything relevant to you or your close family is bad because it is available online from various sources (e.g. Facebook, Linkedin, Ancestry). Of course 123456 is bad. You could use something random but then it won’t be so easily memorable. Ignoring close family, you could use the birth date of, say, your mother (or even better, your grandmother). For me that would be 07071936. You could use one or more of these numbers -
flower07wheelbarrow07bin19husband35
bb07rnhb07thw19cgiir35
07spring07woodbank1935
w07eneedane07wco19mput35er
(iii) Mix upper and lowercase letters
FlowerwheelbarrowbinhusbanD
bbrnhbthwcGiir
SpringWoodBank
wEnEEdanEwcomputEer
(iv) To make an extremely secure password, use all three complexity methods -
Flower_07wheelbarrow07bin19husbanD35
bb07rnh£b07thw19cGiir35
07Spring07Wood!Bank1935
w_07EnEEd£a$nE07w__co19mput35Er
006 Create Different Passwords For Different Websites
You could use the same password for each website but if that gets hacked it would mean the hacker would have access to all of your accounts online. So, how to make it unique for each website? Here are some suggestions.
(i) Add the name of the site to your password
Flower_07wheelbarrow07bin19husbanD35amazon
bb07rnh£b07thw19cGiir35ebay
07Spring07Wood!Bank1935twitter
w_07EnEEd£a$nE07w__co19mput35Erfineartamerica
(ii) Add an acronym relevant to the site
Flower_07wheelbarrow07bin19husbanD35azn
bb07rnh£b07thw19cGiir35eb
07Spring07Wood!Bank1935twt
w_07EnEEd£a$nE07w__co19mput35Erfaa
(iii) Add numbers
How to choose a number relevant to the site? An easy way is the length of the name of the site -
Amazon = 6
Ebay = 4
Twitter = 7
Fineartamerica = 14
To make it harder for the hacker “pad” it to three digits; -
Amazon = 006
Ebay = 004
Twitter = 007
Finartamerica = 012
So we get -
Flower_07wheelbarrow07bin19husbanD35006
bb07rnh£b07thw19cGiir35004
07Spring07Wood!Bank1935007
w_07EnEEd£a$nE07w__co19mput35Er012
007 Storing Passwords
Generally speaking, storing passwords anywhere is a bad idea but if you really can’t remember your passwords, here is some advice.
(i) Write Them Down
Writing your passwords on a piece of paper and sticking it to your screen or under your keyboard is a bad idea.
So find that favourite book again and your favourite page and slip your password note in there. What happens if a burgler finds it? Burglars rarely, if ever, are interested in passwords – they are looking for cash or small high value items to sell on quickly.
If you have accepted the advice above you have a core password used for all sites. For each site you have added a three-digit number at the end. This means all you have to do is store your core password because you can work out which password to use for each site but others would have a hard time figuring it out.
For example, instead of storing
Flower_07wheelbarrow07bin19husbanD35006
use
Flower_07wheelbarrow07bin19husbanD35
Even if a burglar/hacker tries to use the password it will not work anywhere.
(ii) Password Manager
A password manager is a computer program that allows users to store, generate and manage their passwords for local applications and online services.
Types of password managers include:
locally installed software applications
online services accessed through website portals
locally accessed hardware devices that serve as keys
Password managers typically require a user to generate and remember a master password to unlock the password manager. Many password managers offer additional services such as storage of credit card and frequent flier information.
Password managers come and go but the popular ones in 2021 are LastPass, myki, LogmeOnce, Norton and bitwarden
The two downsides of using a password manager are that you usually have to pay for it and, of course, if the password manager gets hacked your passwords are exposed.
(iii) Security Key
A security key looks a bit like a USB pen. It allows you to securely log into your accounts without having to key in passwords. They usually just plug into a USB port.
There are various security keys available so its worth shopping around and comparing them. For example scan.co.uk sells the Hypersecu FIDO Titanium Pro (works in Windows, Apple devices and Android) which currently does well in reviews.
In addition to managing passwords a security key can combat real-time attacks such as man-in-the-middle (MITM), prevent phishing, make keylogging impossible and protect PINs from brute force attacks.
The problem is that they can be difficult to set up.
008 How To get Hacked (Bad Security Online)
(i) Use Number Substitutions in Passwords
Common substitutions are -
a = @
s = $
o = 0
e = 3
i /l = 1
So, ”myamazonassword” becomes “my@m@z0nA$$w0rd”
Hackers are aware of this so number substitution is a bad idea.
Note – this is substitution not addition (discussed above).
(ii) Use Personal Information in Passwords
Examples are -
Your birthday,
Close family names (sons, daughters),
Pet name,
Your address.
(iii) Repeating Characters in Passwords
1234567
aaaaaaaaa
abcdefg
abcabcabc
(iv) Same Password for All Sites
Someone who culls your Facebook or Twitter password in a phishing exploit could, for example, access your bank account. Reusing passwords for email, banking, and social media accounts can lead to identity theft. Two recent breaches revealed a password reuse rate of 31% among victims.
(v) Auto Sign In
Do not allow your computer to automatically sign into sites on boot-up
(vi) “remember me”, Automatic sign-in option
Do not use “remember me” or Automatic sign-in option which is available on some web sites.
(vii) Alien Computers
Do not enter passwords on a computer you don’t control, such as a friend’s computer, because you don’t know what spyware or keyloggers might be on that machine.
(viii) Open WiFi
Do not access password-protected accounts over open WiFi networks or any other network you don’t trust unless the site is secured via HTTPS. Use a Virtual Private Network (VPN) if you travel a lot.
(ix) Keyboard Combinations in Passwords
Avoid consecutive keyboard combinations such as qwerty or asdfg.
(x) Security Questions
The names of spouses, kids, other relatives, or pets, can be deduced with a little research. When you click the “forgot password” link within a webmail service or other site you are often asked to answer a question or series of questions. The answers can often be found on your social media profile. This is how Sarah Palin’s Yahoo account was hacked.
(xi) Social engineering
This is an elaborate type of lying. An alternative to traditional hacking, it is the act of manipulating others into performing certain actions or divulging confidential information.
1 note
·
View note
Text
RECENT NEWS & STUDIES, late April 2019

Welcome to my latest summary of recent news & studies including search, analytics, content marketing, social media & ecommerce! This covers articles I came across from April 9th to May 2, although some may be older than that.
I am really interested in hearing what you think of this new format - please leave a comment below, or convo, Tweet or email me through my website. Let’s make this as useful as possible!
TOP NEWS & ARTICLES
US Amazon sellers were told via email that they will have to pay taxes on some Amazon fees, as Etsy has been doing with sellers in the EU and in Quebec.
The Instagram look may be dropping out of favour; apparently, reality is in. “Instagram museums and walls were built to allow normal people to take influencer-quality photographs—but they worked so well, those types of photos became common enough that they don’t resonate like they used to. “#unfiltered
In case you missed it, my review of Etsy’s Spring & Summer Trends Guide, including all of the keyword data (which you do need to check out, as they reveal some interesting search info).
ETSY NEWS
Etsy published a new census/survey of sellers in its 6 core countries, and also did a summary (if you don’t want to read the whole thing). “More than nine out of ten Etsy sellers (91%) are the sole owner of their businesses.”... “The majority (82%) of Etsy sellers would like to grow their business, but more than three out of five would not want to grow so big that they would have to hire more help.”
The bugs & errors with financial statements and records continue; Etsy botched the VAT statements yet again, even overwriting them all the way back to 2016. No word on whether any sellers have notified EU authorities on this yet.
New seller handbook article covers advertising; not much new or gripping, but it does discuss general ad approaches, not just Etsy’s.
There is also a new free shipping tool, in case you didn’t realize that Etsy wants more sellers to offer free shipping more often. “When we talk to shoppers during research, many say things like “I want to feel like I’m getting a deal!” and “I would love to see free shipping across the board, even if it meant increased prices.” Offering free shipping can be a great way to give customers like these the shopping experience they are looking for.”
CEO Josh Silverman participated in The Wall Street Journal’s “In the Elevator” interview series [video link]. Every 90 seconds, an engagement ring or wedding ring sells on Etsy. He also talks about free & fast shipping not always being a reasonable expectation when shopping on Etsy, unlike Amazon.
Speaking of free shipping, a limited number of US customers will be getting it from Etsy, with Etsy reimbursing sellers for the costs. Non-US sellers and buyers get nothing.
Etsy’s 2019 1st quarter results will be available May 8.
SEO: GOOGLE & OTHER SEARCH ENGINES
Rand Fishkin released Part 5 of his Learn SEO in 1 Hour series: technical SEO [video & written transcript]. This is the one most of you can skip or just skim over, as it does talk a lot about coding.Some tips are important to everyone, however, like page linking/site structure (for websites), and having https set up.
Part 6 covers link building, in 10 minutes. Remember, if you are going to put effort into getting links, do it for your website & not your Etsy shop or other marketplace page. If you are creating traffic, make sure you own it.
Don’t forget looking beyond Google for your search engine traffic; this podcast [with written transcript] breaks down an approach to several of the biggest ones beyond Google. Spoiler: they only recommend worrying about the biggest, Bing, if you have around 1000 unique search visitors to your website per day.
How to get keyword ideas from the Google search results: there’s a lot more available now, beyond the search bar suggestions.
Google is asking local businesses if they would pay for their Google My Business listings. This possibility raises concerns about the impact on organic rankings.
More SEO tips for Amazon, including discussion of the various factors involved.
If pages on your website aren’t indexed by Google, there are some steps you can take to fix them. (For websites only, not Etsy shops)
Advanced/semi-advanced content: Great tips on using bookmarklets in Chrome to get SEO things done quickly. (A lot of these involve tools that work best in the paid version, so I suspect most of us will not have much use for this, yet.)
Possible Google algorithm update last week. (I am seeing changes)
CONTENT MARKETING & SOCIAL MEDIA (includes blogging & emails)
Looking for new hashtags for your social media accounts? Try: https://www.tagshitter.com (apologies for the name; that’s what they call it. It’s good, too! Just like its regular keyword research partner, http://keywordshitter.com/ )
Email subject lines [infographic] are crucial to top interaction with your newsletter etc. Includes Dos & Don’ts, plus the shockingly low open rates in most industries.
Selling through social media directly is a great way to avoid people losing interest as they keep clicking. Note that this seems to work best with items under $50, though, which they suggest solutions to in the next part of the article.
Despite all the scandals and negative media coverage, US social media use hasn’t really changed in the past few years. “A 2018 Center survey found that some Facebook users had recently taken steps to moderate their use of the site – such as deleting the Facebook app from their phone or taking a break from the platform for some time. But despite these findings and amid some high profile controversies, Facebook users as a whole are just as active on the site today as they were a year ago.”
Facebook scandal watch: FB’s “stock price jumped after it said it expects to incur a fine of up to $5 billion from the Federal Trade Commission. And that’s all you really need to know about whether the historically large penalty matters to the company.”
Also:
they admitted to asking for your email password then importing all of your contacts. “...Facebook disclosed to Business Insider that 1.5 million people's contacts were collected this way and fed into Facebook's systems, where they were used to improve Facebook's ad targeting, build Facebook's web of social connections, and recommend friends to add.”
The Canadian Privacy Commissioner is taking FB to court over breaches of Canadian privacy law.
But hey, it’s all fine, because they beat earnings expectations in the first quarter.
70% of YouTube videos watched are recommended by its algorithm. “ The recommendations are fueled by the artificial-intelligence arm, Google Brain, of YouTube’s parent company. The machine-learning models help identify videos that aren’t exactly what you just watched, but similar enough that you might like them.“
Does directing people to the link in your Instagram bio really work? Testing says that it probably doesn’t work for most accounts, and more importantly, that Instagram may be limiting the algorithm visibility of posts that direct visitors to the link in your bio.
Twitter has now limited the number of accounts you can follow in 1 day, to 400 down from 1000; this is intended to cut back on spammers.
US Twitter users are better educated & better off than the average American.(Good article for target market considerations)
ONLINE ADVERTISING (SEARCH ENGINES, SOCIAL MEDIA, & OTHERS)
Amazon is reducing/removing the ads for its own products, possibly due to increased complaints of unfair competition. “Amazon is now the third-largest digital advertising platform, behind Google and Facebook”, and could grow 50% this year alone, based on projections.
Facebook retargeting tips. And everything you need to know about the Facebook pixel for tracking your ad performance.
STATS, DATA, OTHER TRACKING
Some Google Analytics tips for websites - almost beginner level!
The Google Search Console delays are nearly all fixed.
Stats programs all give you different numbers, and that isn’t likely to improve. (This piece is semi-advanced; don’t bother with it if you aren’t a stats geek.)
ECOMMERCE NEWS, IDEAS, TRENDS
eBay’s Spring Marketplace Updates include several back end changes and a fee increase for sellers who run afoul of eBay’s seller performance standards.
Amazon sellers can buy so-called “black hat” services to beat its algorithms. These include tips from Amazon employees who are making money by reporting on Amazon’s inner workings. Amazon “also said it takes action against sellers who pay for internal information; penalties include terminating their selling accounts, deleting reviews, withholding funds, and taking legal action.” No doubt the company already has closed some of the loopholes discussed in the article.
Amazon also fires warehouse workers by algorithm, based on productivity.
GoDaddy launches an ecommerce sharing tool that lets you list across multiple websites including your standalone. Current marketplace options include Etsy, Amazon, eBay, Jet & Walmart. They bought Sellbrite as part of this move. Quite a few different entities are releasing this type of service, so shop around if it is something you are interested in.
eBay released their 1st quarter 2019 results on April 23. Total sales were down 4% from 2018 (they were close to even when currency fluctuations were accounted for), but eBay’s own income from seller fees was up. “eBay reduced their marketing by a significant amount where their cash was being used to effectively subsidise the sales of high value items. Put simply, eBay have been buying sales and now they’ve stopped and this has seen a reduction in high ticket items being sold in comparison to sales of lower value items.” Easter being later this year may have slowed ecommerce growth overall in the quarter.
...but Amazon reported record revenue, up 16.9% over 2018. Despite that, analysts note that growth is slowing, & that Amazon’s own projections for the second quarter are lower than many predicted. “Amazon’s CFO Brian Olsavsky said during the call with analysts that part of the lower guidance is due to an $800 million investment in making free one-day delivery shipping the default for Prime members.” - if you thought buyers wanted stuff yesterday already, wait til this becomes the norm ... I mean, Walmart & Target stocks fell after the announcement. Walmart is already hinting at offering the same.
You can return your Amazon purchases at Kohl’s in the US, starting everywhere in July. Ease of returns is going to be a bigger battleground in the next few years, as retailers continue to increase free & speedy shipping options.
BUSINESS & CONSUMER STUDIES, STATS & REPORTS; SOCIOLOGY & PSYCHOLOGY, CUSTOMER SERVICE
Generation Z will be making 40% of US retail purchases by next year; they are going to change a lot about selling. “ Fair trade products, ethical business practices, and a strong mission statement have never been more essential. Vend reports, “Research has shown that this particular generation cares about various environmental issues (76% are concerned about humanity’s impact on the planet) as well as social causes such as racial, gender, and income inequality.” [Gen Z come after millennials, and are currently more numerous than millennials or boomers.]
Millennials & Gen Z are big gift card buyers in the US - over 1/3 buy a card every 3 months.
Brick & mortar stores & malls are using your phone location data (location analytics) to make marketing and product decisions. “Every company interviewed for this story said it chooses not to use information that could identify individuals. But for the most part they’re on an honor system because rules governing data remain relatively lax.” This surprised me: “To glean details, including an individual’s age, income, ethnicity, education level, number of children and more, firms connect the phone’s evening location with U.S. Census data”
MISCELLANEOUS
US copyright law: the USSC rules that your copyright registration must be finished/approved before you can sue an infringer in federal court.
If you hate Gmail’s current layout, you will love this Chrome extension.
And if you use Google Sheets fairly often, you will likely learn something useful from these tips.
Google’s parent company, Alphabet, missed industry revenue expectations in the first quarter of 2019.
#seo#search engine optimization#etsynews#analytics#stats#social media#contentmarketing#ecommerce#smallbiz#cindylouwho2newsupdates
3 notes
·
View notes
Text
The Best Way To Free Up iPhone Storage (Updated)
Even though today's iPhones come with a lot of storage (especially if you're willing to pay a premium for it), it's quite easy to fill it up with photos, videos, music, and podcasts. Apple is well aware of this, which is why iOS includes tools for managing your phone's storage. Here, we'll walk you through five different methods for freeing up your iPhone storage – all of which are fairly simple.
1. “Offload” and Delete Rarely Used Apps
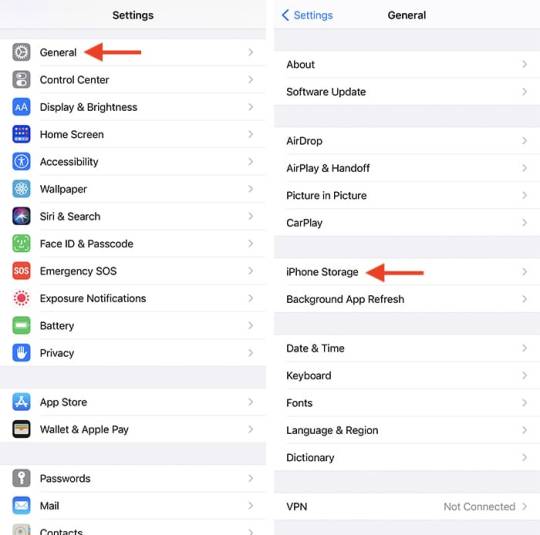
There's a good chance that your iPhone is running out of storage space due to iOS apps – especially if you're a gamer. Having said that, our first recommendation for freeing up space on your iPhone is to "offload" and delete apps. Take the following steps:
1. Open the Settings application. Scroll down to "General -> iPhone Storage" and wait a few moments for your phone to calculate your available space.
2. The first option gives the control to iOS. Select "Offload Unused Apps" if you want your iPhone to determine which apps should be deleted. This will ensure the preservation of your documents, media, and personal information. It will delete only infrequently used apps and only when your storage is running low.
3. With the second option, you retain control. Select each app (which has already been sorted by size) and tap on any app you no longer require. This will reveal additional information and the "Delete App" option, which will delete the app and all of its associated data from your iPhone.
2. Reduce the File Size of Your Photos
The iPhone's camera has improved significantly over the last couple of years. However, the additional megapixels result in monstrous file sizes. Here's how to optimise your photos to free up space on your iPhone.
1. Launch the Settings app. Scroll down quite a bit and tap on “Camera.”
2. After tapping "Formats," you'll see a few options. We recommend selecting "High Efficiency" to instruct the Camera app to utilise the HEIF/HEVC format. Your photos will retain their quality while being significantly smaller in file size. Additionally, you may wish to learn how to view HEIF/HEVC files in Windows in this case.
3. If you have an iPhone capable of shooting in "ProRAW," you'll also see that option here. Bear in mind that “ProRAW” images are extremely large in size. There is no reason to use this feature unless you are a professional photographer who edits images.
Finally, be sure to check out our guide on how to delete duplicate burst photos from your iPhone. These can eat up a lot of storage space, especially if you haven't optimised the Camera app's operation (as explained above).
3. Delete Locally Stored Media
If you download music and podcasts for offline listening or use a media streaming service to download movies and television shows, you should be aware that these files quickly consume your storage. Here's how to delete those files and reclaim some of your iPhone's storage.
1. Navigate to the Settings app and go to “General -> iPhone Storage.”
2. Choose the app that will manage your offline data. For instance, if you have a large collection of locally stored music, launch the "Music" app. Alternatively, you may have a large number of podcasts saved in the "Podcasts" app. Additionally, media streaming apps like Netflix, Disney Plus, and Hulu can store offline files, which you can find here.
3. After selecting an app, you'll be taken to a detailed overview of it. Additionally, this is where you'll find any data saved for offline use, conveniently displayed at the bottom of your screen. Swipe across each file from the right edge of your screen to delete it.
4. Store Photos and Files in iCloud
Certainly, saving your photos and files to the cloud is another way to free up space on your iPhone. and if you're an iPhone user, there is no more straightforward cloud service than iCloud. To get started with iCloud, follow the instructions in this iCloud tutorial.
The first items you'll probably want to migrate to iCloud are your photos and videos. They have a tendency to take up a lot of space. To begin storing your photos on iCloud, follow this tutorial.
iCloud Drive is an app that comes pre-installed on iOS and serves as a storage location for your files. Once you've signed up for iCloud, all of your files will be stored there. This can be changed in the iCloud settings, which are detailed below.
1. Navigate to Settings, tap your profile at the top, and then click "iCloud." You'll see a graph indicating the amount of storage available on your phone for Backups, photos, others, and Family.
2. The image above's first panel depicts a family plan. Below that is a list of available features and toggles for disabling them, as well as additional menus for enabling additional features. Keep in mind that if you disable them, any files saved will be stored locally and will consume additional space on your phone.
3. If you tap on "Manage Storage," the second panel above will appear. Along with that graph, there is an option to view the amount of data used by the family and to change the storage plan. Below that is a list of the apps currently installed on that phone and the amount of iCloud storage they consume.
4. By tapping an option, you can delete the saved data.
5. Create a Local (iTunes) Backup and Restore Your iPhone
In some cases, your iPhone may not accurately report your available storage space. A workaround for this would be to make a local backup of your iPhone and then restore it. Not to worry – you will not lose any data. What you need to do is as follows.
1. Using a Lightning cable, connect your iPhone to the USB port on your computer. If you are using Windows, ensure that iTunes is launched. Additionally, if you're using macOS, launch Finder and navigate to the left sidebar to select your iPhone.
2. Locate the "Backups" section and check the box labelled "Back up all data on your iPhone to this Mac/Computer." This will create a backup on the hard drive of your computer rather than an iCloud backup.
3. Check the box labelled "Encrypt local backup." Encrypted backups can contain sensitive data such as Health and Keychain data. If you do not check this box, all of that data will be deleted during backup restoration.
4. Click the "Back Up Now" button when you are ready. Your iPhone will now begin backing up. Avoid using your iPhone for a while if possible.
5. After backing up your iPhone to your computer, you'll need to restore it. choose the "Restore Backup" option. At this point, you may receive an alert stating that you must disable "Find My iPhone" before the restore can be completed. If this is the case, you can disable this feature on your iPhone by navigating to "Settings -> iCloud."
6. The most recent backup will be selected by default for restoration. To select another backup file, use the drop-down list next to "Backup."
7. Click the button labelled "Restore." To unlock the encrypted backup, enter your password and then click the "OK" button when prompted.
8. Your iPhone will enter restoration mode, and the message "Restoring from Backup" will appear. Until the restoration is complete, you will be unable to use your phone. Maintain a connection between your phone and computer until the phone has restarted and the restoration is complete.
Final Thoughts 😃
"How do I free up space on my iPhone?" is a frequently asked question by a large number of users. Simply recognise that there are no enchanted solutions. On an iPhone, there is no such thing as infinite storage. These methods will assist you in creating additional space. However, your phone will eventually fill up and there will be little you can do about it except for purchasing a new phone.
We appreciate your time in reading and hope you enjoyed this Article. You may also want to check out our Website for more such Trending articles, How-to guides and much more! 😎 Wait!! Don't forget to checkout Freebies 🤫
If you liked this article, then do Follow Us 😻 on Twitter and Instagram. You can also follow us on Pinterest.
Read the full article
0 notes
Text
Frontier Mail Login | Frontier Mail Sign Up Step by Step Guide
Frontier Mail Login: Frontier Communications is an American Telephone company that is in Connecticut USA. If you look at the History of a Frontier then they are offering different types of services that can simply help their customers and the Service including digital TV, Internet services, and computer technical support.
Frontier:
Frontier is the 4th largest provider in the United States of America and it Mostly is known as Citizens Utilities Company until 2000 and the Citizens Communications Company until 2008. So by based on this, you can easily estimate how Frontier has Grow and got Popularity. It has fast and Speedy Development in terms of Growth and Popularity. Follow the rest of the Guide of Frontier to know more including the Frontier Mail Login.
Frontier also has Frontier Mail Login features and this Frontier Email is one of the Best Email Service from the Company, also This Frontier Email login is only For the Subscriber of the Frontier. Once you have become a subscriber to Frontier then you will also get the Technical Supports and all their Service as well.
There is also a bill Payment option which you can simply Pay Your Bill without any problem by just going into the My Account section on the Frontier Homepage. By going into the My account you will be able to Do many Things such As your Profile and Payment details and many others.
You Just have to Get into the Frontier account section by simply Login into it. There are many features that you see on the Dashboard of the Frontier. Now Following the Below Guide, you will be knowing the Frontier Email Login Guide that has all the details where you will be login into the account easily.
Related: Zoomtown Email Login
rcn webmail
Frontier Mail Login Instructions:
Now When it comes to the Frontier Mail Login, You will be able to Get into the Mailbox dashboard very Easily and The Point that you just want to get it is so simple within the Minutes that you start Reading the Guide of the Frontier Mail.
Most of the People who are new to Frontier mail they get confused about the Creating account even if they have created then facing the problem with the Login into the account of frontier mail. But when you have followed the right guide then you don't need to worry and you will be able to experience the Full mail interface.

Also, You can Know about Other Emails: TWC com Email Login
Juno Email
SBCglobal Email
Frontier Mail login:
Simply follow the steps below to Get into the Frontier Mail Login without having any kinds of issues. Steps that I have given to Make readers Knowledgeable in a Very simplistic way. To login into the Frontier Mail, you just have to have the User Name and Password of Frontier, not only for this in any account we need to have the username and password to start getting into it and use the services.
First, you have to Open your Browser that you are Using from your Computer.
Now you have to Enter www.frontier.com in the Adress bar of the browser and press the Enter button to Load the Website.
Once the website has opened then Simply you have to Goto the Sign-in Link which is on the top right side of the Page. Or when you Open the Frontier Website you will see a Login Form on the Right Side of the Screen.
Now you have to Sign in from this form by Entering your Login credentials like Username and Password on the Provided Fileds.
In the first field, you have to Enter your Friner iD or email address. (Whichever its ask and it will show you in the same field)
Now in the Below Password friends Enter your valid Password.
Just below of you will see Remember my ID, if you want to remember your ID to Login from the Next time using the same computer then You can Check the Box.
But if you are using the Pubilc Computer or Other computers then you should not Check this Box.
Then just click on the SIGN IN button to get into the Email.
Try to Enter the Valid Login Credentials for avoiding Login Errors.
If you have not Clarity of your Frontier Email address then it Just Looks like this [email protected].
Also while entering your Password you should make sure that is there are CAPS LOCKs and Capital letter and any Symbols, all these are very important to check So that you can log in into the Frontier Email without any Problem.
The Best part of the Frontier Email is that now you can also Login into the frontier email From the Yahoo email because they have collaborated So this is also one of the best things that you can do.
This is how you can simply get into the Frontier mail Login.
But if you have forgotten your Username or Password or both in some case, then What should I do? if this is your Question then you have to follow the below Guide that which I Have explained with Complete Detailed which you will get very easy and Start resetting your Username and Password without any problem for sure.
Reset Frontier Mail User Name:
Most of the people always forget their user name and they always try to create a new account rather than having a chance of getting the same username that they have forgotten. So from Now even if you have Lost your user name of the Frontier mail you will get it back very easily by following this Guide below.
If you have forgotten your username then click on the forgot Link which is located beside the username Field on the frontier mail login Page.
Now you will able to see two options those follow like"Enter the Email Address or Username you used to create your Frontier ID" and "Enter your Billing Account Number and PIN to recover your ID" in the next window from the Frontier Email Login Page.
You can any option Which you are much comfortable and which you have to enter to get your Username back.
Next, Confirm that I'm not a robot by choosing the right images and all.
Once you have finished then click on the continue option to Finish the process.
This is how you can simply reset your Frontier Mail password without any issues when you follow the correct guide. So I have explained it in very detailed explanation where you can simply login to the Frontier Mail account after you successfully completed the Password reset.
Reset Frontier Mail Password:
if you are not able to Login into your Frontier Mail then this could be the Problem of a wrong password, If you have forgotten your Frontier password, Now you can easily reset by following the steps below. By going through this 4 Step below you will be able to reset your Frontier Mail password easily.
First, click on the Forgot link which is located beside the Password Filed.
Now enter your Email address and Conform the I'm not a robot.
Now click on the Continue Button to Reset your Frontier password.
Then follow further Instruction to success your reset Password of Frontier Mail.
That's all now you have successfully Reset your Password. But in case if you still facing any issues then do let me know below. After you have completed the Login Process below I have Explained the Signup guide which is also available in the Step by step Format.
Frontier Mail Login Signup:
If you don't have an account on Frontier mail then this is the guide for you to learn how to create a frontier email by following the simple guide. There is the Article over there on the internet where you will get confused overall after going through them.
But once you have seen this guide you will be able to create frontier email very easily because of the guide we have explained in a very simplistic way that can be understood by everyone.
Whenever you just want to create Frontier Mail, First you have to Create the Frontier ID then you can Simply get into the mail using the Frontier Mail login.
Now you have to go to the Frontier.com and then just have to locate the Sign-in Option on the page and click on that.
You will see the Login page of Frontier Now and you will have to click on the Create a Frontier ID which is bottom of the Login Form.
You will be redirected to the Frontier registration page which you have to Fill out all the details which are required over there.
Now, First, you have to Enter your First and Last name in the provided box.
Type your email address which is you just want to receive Newsletters from the frontier.
It's time to Create your Password which is the minimum of the 8 Letters on your Password.
Re-enter the Same Password on the second Box, which is the confirmation of the Password to Start to Create an account.
Now enter the Mobile number on the mobile number Field.
Finally, Check the Box that to Prove I'm not a Robot text by Selecting the Right Images that match.
Also, Tick the ‘I have read and agree to the Terms and Conditions’ and click on the Next.
Now Click on the ‘CREATE ID‘ to Finish the creating your new Frontier ID.
This is how you can easily create an Account of frontier mail without any issues. So do follow the Step by step guide carefully without any problem. Make sure to have all the right details while creating an account.
Conclusion:
This is How you have to Create Frointer Account and Get into the "Frontier mail Login". Also make sure that While entering the email address, mobile or telephone number those are should be registered with the Frontier Account.
Read the full article
0 notes
Text
hello... so fall is starting meaning freshmen are coming in.
now that this is the last semester of my bachelor’s degree, let me tell you a few things about college textbooks i have experience:
1. textbooks are almost always more expensive on campus. shop around online
2. you can compare prices on sites like bigwords.
3. ask the professor if you can use older versions (which are waaaay cheaper). i have asked and a lot of the times they are okay with it. sometimes they are not because the practice questions at the end of the chapter are different
4. international version from other countries are the same exact textbook, but in black and white and cheap paper quality. and they are. WAY cheaper. (like save $200 cheaper) and the practice questions on the textbook are the same. however they have no buyback value.
5. if you buy a hardback textbook, you can probably sell it back online at the end of the semester (buyback). however, it is usually cheaper to rent the textbook. in every instance for every semester i have saved more money by renting.
5.5 note: the closer to the start of the semester, the more expensive a rental. but the longer you rent the more expensive it is. make sure to turn in rentals on time to avoid the fee. take picture of the chapter you are reading during the last week if you must.
5.7 Okay i forgot about this one but had to include it... sometimes the school will list their own version of the textbook. Like, its just a regular ass textbook you could get for $75 used on Amazon, but they took out four chapters, rearranged the remaining chapters, put a brand new stock photo cover on it and charged like $370 for it. Ew. i have never,ever bought that. bitch, not even once. First of all, no buyback value. Because it is college specific it can only be used for that college and most likely just for that semester. so what you do is you buy the 75$ version. Then the mcgraw or whatever publisher website will have the list of which chapters are in which order and if you cant find it email your teacher because she probably has it.
6. if you are taking introductory courses to your major (so like. sophomore year) and you’re not getting much buyback value, just keep the textbook. ive had classes require the same textbook (ex: intro to accounting and accounting ii). this doesn’t happen usually after junior year or when taking general courses.
6.5 (also keep your notes for introductory courses, as some internships and jobs may require a test on the basics that you will most likely forget!!! and sometimes materials for courses overlap ex: business law 1 and business law 2. i threw away the notes when notes for both classes were practically the same. yikes. )
7. if you have to buy the current version, sometimes e-textbooks will be cheaper (ikr?!) sometimes they won’t. you’ll have to compare the different isbns on comparison sites.
8. Teachers will sometimes list both the e textbook version and the text version on the syllabus. You don’t have to buy both. Sounds obvious but there are at least three people that do this every class (& just check what you are buying before you buy it... sometimes the teachers even list the ISBN wrong).
9. when your teachers wants you to buy both the textbook and the connections access code for assignments, they will list the ISBN for the brand new textbook with the access code. do not buy that. you can buy the access code to get your assignment on its own, and sometimes that will include an e text version of the book. this will save you around $100. if it doesn’t include the e-text, you will still save money buy buying/renting/ used or buying the international version textbook and access code separately, rather than new textbook that comes with access code
10. used versions of textbooks will not have an access code, even if the seller says it will they are liars they don’t know shit they can’t check if for you if they do they will activate it and they ain’t giving u their email password for ur little code trust me bitch. if it does have it by some miracle and its not used, it probably won’t work for your course. okay. just now.
11. BUT. you can buy unused access codes from the amazon marketplace. those were people that bought the brand spakin new textbook that comes with the access code and then ended up never using the access code. The code will usually be listed for around 50% off. any less than that and I wouldn’t risk it. i’ve never been ripped off buying used access codes but it does happen often.
12. if your course is online and it uses connections to do they assignments, they give a two week free trial (good for those of us that get paid bi weekly or if you run out of money while buying textbook for your other classes first).
13. hmm...asdhfjasdfklahskl..... library genesis (free pdf....) asdhjfkalskdfh’j......its the best one just sayin...asjdfiakls;djfal
14. wait until starting the class to buy. this tip was given to me during scholarship meeting by the board. do this at your own risk. sometimes books sell out. sometimes you need the book during the first week (usually you don’t the teacher is usually lenient and gives two weeks to get the textbook after the class start). check stock first. but... i’ve had books that were only needed for one assignment that was barely worth any percentage of the grade. I’ve had books that were “required” but for practice questions that were never turned in. sometimes you will start the class and the professor will make amendments and say the book is optional. if that happens and you already bought the book go return it do not let it collect dust just pass go and collect $200
well crap i didn’t think i had this many tips welp here it is this is just for textbooks holy shit
#college#financially needed#freshman#tips#textbooks#save money#buyback#rentals#free textbooks#access codes#connections#canvas#blackboard#mcgraw hill
3 notes
·
View notes