#gdpr.risk assessment
Text
#dsgvo#gdpr#gdpr.risk assessment#gdpr compliance#data protection#data privacy#business consulting#dsb#germany
2 notes
·
View notes
Text
#gdpr requirements#siscertifications#gdpr standard#gdpr.risk assessment#gdpr cert services#gdpr compliance#sis certifications
0 notes
Text
9 Steps to Become GDPR-Compliant
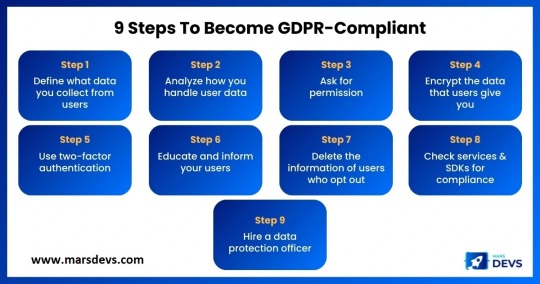
So far, we've looked at how GDPR will affect your development workflow regarding business operations and project planning. Now, let's look at how it will affect how you code. In this infographic MarsDevs explain 9 Steps to Become GDPR-Compliant.
Click here to know more: https://www.marsdevs.com/blogs/gdpr-and-its-implications-for-web-and-app-development
0 notes
Text

The evolution of data governance in Southeast Asia reflects a significant paradigm shift, moving from mere data organization to a strategic approach rooted in data intelligence. Central to this evolving landscape are advanced practices in data discovery and classification, enabling organizations to proactively manage data assets.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
#dsgvo#gdprcompliance#dataprotectionofficer#germany#business consulting#gdpr.risk assessment#gdprcertification
0 notes
Text
#external data protection officer#dsgvo#gdpr#gdpr.risk assessment#gdpr compliance#startup#business consulting#gdprcertification#data privacy#world
1 note
·
View note
Text
Evolution of Data Governance in Southeast Asia: Trends, Regulations, and Best Practices

In today’s rapidly evolving digital landscape, where data serves as the lifeblood of businesses, the importance of effective data governance cannot be overstated. Southeast Asian organizations, like their global counterparts, are navigating a complex web of data regulations, compliance standards, and security challenges. The evolution of data governance in this region reflects a significant paradigm shift, moving from mere data organization to a strategic approach rooted in data intelligence.
Central to this evolving landscape are advanced practices in data discovery and classification, enabling organizations to proactively manage data assets. In this context, building a robust, future-proof data governance framework has become paramount. This article delves into the intricate journey of data governance in Southeast Asian organizations, exploring the pivotal role of popular standards, the alignment of regional regulations with global counterparts, and the significance of data discovery and classification.
Evolution of Data Governance in Southeast Asia
In recent years, data protection and governance has undergone a significant evolution among organizations in Southeast Asia. Traditionally, data governance was seen as a technology-centric practice, focused on organizing and cataloging data. However, this perspective has shifted as organizations have recognized the critical role data plays in their operations. With the advent of data privacy laws, such as the Personal Data Protection Act (PDPA) in Singapore, companies began incorporating risk management practices into their data governance strategies. This involved creating information asset registries and analyzing the Confidentiality, Integrity, and Availability (CIA) of data to ensure legitimate usage and establish appropriate controls.
Additionally, the COVID-19 pandemic served as a catalyst for the acceleration of digital transformation across industries. Organizations recognized the immense value held within their various data sets, especially in informing critical business decisions. This pivotal shift led to the evolution of data governance from a mere organizational necessity into a data intelligence-centric approach.
secure.
“Data intelligence is the connecting point for all data elements within a data management system, delivering information and insights that improve customer experience and drive innovation and process improvements.”
– Mel Migrino, Chairman and President, WiSAP (Women in Security Alliance Philippines)
Significance of PCI DSS in Financial Institutions
In the financials sector, adhering to established standards is more than just a regulatory obligation — it’s a mission-critical aspect of operations. A prime example is the Payment Card Industry Data Security Standard (PCI DSS), which financial institutions worldwide employ to ensure the secure handling of payment data.
PCI DSS, developed by experts from across the globe, including the PCI Council, payment networks, and cybersecurity professionals, is a well-recognized global standard. It has undergone iterative improvements, incorporating feedback from diverse stakeholders. Organizations in the Asia-Pacific region, including Southeast Asia, have embraced PCI DSS for multiple reasons as listed below:
Compliance with PCI DSS is a contractual obligation for merchants and acquirers. Failure to comply could result in sanctions and damage to an organization’s reputation. By adhering to this standard, organizations reduce the risk of non-compliance and ensure their legal and operational obligations are met.
The PCI DSS standard actively seeks feedback from its global community, ensuring that the guidelines stay up to date with evolving security threats. This responsive approach ensures organizations implementing the standard are confident about the effectiveness of security controls.
Beyond compliance, many organizations have extended PCI DSS principles to protect other sensitive data, recognizing its effectiveness in safeguarding confidential information.
In essence, the adoption of global standards like PCI DSS provides financial institutions with not only a compliance framework but also a security blueprint that safeguards their sensitive financial data. It serves as a testament to the proactive commitment to protecting both internal and external stakeholders.
“Security threats evolve, and standards must evolve with them. The feedback-driven approach helps standards stay on top of emerging trends.”
– Yew Kuann Cheng, Regional VP, Asia Pacific, PCI SSC
Harmonization of Regulations in Southeast Asia with Global Standards
In an era of interconnected data ecosystems, data governance regulations are continually evolving to ensure data protection and privacy. These regulations often exhibit a degree of interplay, with global standards influencing and inspiring one another. In Southeast Asia, particularly Singapore, the PDPA standards have laid the foundation for the broader ASEAN (Association of Southeast Asian Nations) region’s data governance and privacy regulations, emphasizing the roles of data controllers, data processors, and privacy considerations. Cross-border data transfers have become a universal concern, and global standards play a pivotal role in addressing this challenge. GDPR (General Data Protection Regulation), emerging from the European Union, sets a stringent precedent for the security controls required for cross-border data transfer. In India, the recently introduced DPDP Act (Digital Personal Data Protection Act) aligns with international best practices, incorporating elements from various global standards like NIST, PDPA, and GDPR. China, too, has developed its own regulatory frameworks, including the CSL (Cyber Security Law) and DSL (Data Security Law), which are known for their stringent economic focus.
In the ASEAN framework, close collaboration between legal departments is essential to develop regulations that align with the global need for robust data governance while adapting to local laws. Across these regulations, common principles, such as data discovery and classification, underpin data governance practices. Regardless of the specific framework in place, understanding where data resides and comprehending data lineage is consistently emphasized.
Additionally, global standards like NIST and PCI DSS guide comprehensive data protection practices that emphasize anonymization, pseudonymization, tokenization, masking, and encryption. Data governance is a global collaborative effort that involves sharing, adapting, and implementing best practices to suit local regulatory and business needs. While the journey from standards’ publication to regional adoption varies, the core concepts remain strikingly similar. In essence, data governance revolves around safeguarding data, understanding its flow, and ensuring security and privacy, reflecting a global commitment to data protection in a data-driven world.
Role of Data Discovery and Classification
In the rapidly evolving landscape of data governance, data discovery and classification have emerged as fundamental pillars. These two closely intertwined elements are instrumental in optimizing an organization’s data management practices. Data discovery, the first cornerstone, entails identifying the precise locations where data is stored. This critical step lays the foundation for effective data protection, ensuring that organizations are cognizant of their data assets’ whereabouts and can implement requisite security measures. With increasingly sophisticated data discovery tools, businesses can compile exhaustive data inventories and maps, facilitating informed decision-making on data management and protection.
Complementing this is data classification, which is equally vital. It involves categorizing data based on its sensitivity and value, enabling organizations to distinguish data demanding stringent protection from that which can be shared more openly. This classification guides the application of security controls such as encryption and access restrictions. Ultimately, data classification empowers organizations to tailor safeguards to different data types, thereby bolstering overall data protection and regulatory compliance. In this complex data landscape, data discovery and classification tools like SISA Radar prove invaluable, allowing businesses to maintain a well-structured and efficient data governance approach.
“Data is of primary importance, and anything done to govern and secure that data involves classification, discovery, lineages, data flow diagrams, and more.”
– Prabhu Narayanan, VP — Data Protection & Governance, SISA
How to Build a Robust Data Governance Framework?
Building a future-proof data governance framework is an essential endeavor for organizations seeking to thrive in a data-driven world. Such a framework must encompass several key principles:
Integration with Business Processes: Data governance should not be an afterthought but rather integrated into core business processes from the beginning. This “shift left” approach ensures that data protection, integrity, quality, and privacy considerations are embedded in every stage of data workflows.
Collaboration and Alignment: Successful data governance requires close collaboration between different departments within an organization, including cybersecurity, legal, technology, and business teams. It’s crucial that data governance aligns seamlessly with broader business objectives to enhance security, compliance, and overall efficiency.
Continuous Adaptation: As global standards and regulations evolve, organizations must adapt to these changes in a timely and effective manner. This involves staying updated on the latest developments, actively seeking feedback from stakeholders, and implementing any necessary adjustments to data governance practices.
Data Discovery and Classification: Incorporating advanced data discovery and classification tools is an essential part of a future-proof data governance framework. These tools provide organizations with the knowledge they need to make informed decisions about data protection, risk management, and compliance.
In the ever-changing landscape of data governance, Southeast Asian organizations are poised to navigate challenges and opportunities through strategic adoption of global standards, meticulous compliance with regional regulations, and the seamless integration of advanced data discovery and classification techniques. By embracing these evolving trends and building robust data governance frameworks, businesses can safeguard sensitive information, foster innovation, and establish enduring trust among their stakeholders.
For a more detailed insight on the evolving landscape of data governance in Asia Pacific region, get in touch with SISA’s Data Protection and Governance experts or watch our latest panel discussion — Trends In Privacy Regulations in Asia Pacific and the Role of Data Governance.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text

The release of PCI Security Standards Council’s much-awaited PCI DSS v4.0 is round the corner and the industry is abuzz with talks on anticipated changes, the ensuing implications, and the necessary support for the transition. The update to PCI DSS 3.2.1 – currently the gold standard for payments industry is coming after six years since the last change took effect in 2016. At its heart, the new standard is expected to move compliance from an audit-driven, one-time event, to a continuous improvement process aimed at securing payments.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
Prepare to embrace continuous compliance with PCI DSS 4.0

From an operational standpoint, the 12 core PCI DSS requirements are not expected to change fundamentally and will continue to remain the foundational blocks for payments security, as noted by the PCI Security Standards Council. However, with the new updates, the standard will expand to reflect evolving changes in technology, risk mitigation techniques, and the threat landscape while also looking to enhance validation methods and procedures. There are five broad areas that are likely to see changes, discussed as under:
Customized approach to design security controls
With PCI DSS 4.0, organizations will be able to choose to perform the control as prescribed in the guideline or opt for customized implementation. With customized validation, the focus will shift from “what” must be implemented to defining the security “outcomes” linked to each requirement. This would allow organizations greater flexibility to achieve compliance by showing that the intent of the requirement is met without needing to provide an operational or technical justification — a marked departure from the current standard.
More stringent controls
PCI DSS 4.0 will set the bar higher for security standards. A key area where this would apply is around the use of cloud and serverless computing. 4.0 is expected to introduce an updated set of requirements and approaches to securing cloud and serverless workloads. Additionally, it will likely increase the number of touchpoints and test points, and the amount of data that must be proven to pass, in an attempt to make PCI DSS a continuous process. This might entail larger capital outlays requiring budgetary planning and adjustments.
Deeper focus on MFA and encryption
The NIST password guidance takes a centre stage as the new standard forces MFA for every touchpoint. There is going to be greater focus on applying stronger authentication standards to payment and control process access log-ins and also implementing the use of 3DS Core Security standard during transaction authorization. The new standard will enable organizations to build their own unique pluggable authentication standards to meet data security regulatory requirements. At the same time, they can be scaled to fit the company’s transaction objectives. Secondly, it is likely to expand the scope and application of encryption to cover cardholder data transmission on trusted networks while also requiring organizations to institute a data discovery process.
Enhanced monitoring to reflect technology advancements
There is likely to be enhanced focus on risk-based monitoring and testing. The requirement to monitor the cardholder data environment may be updated to reflect advancements in technology, such as the availability of next-gen network and endpoint detection tools. Merchants and payment service providers may be required to have processes and mechanisms to detect phishing attempts. Besides, the new update will include provisions on treatment of phishing and social engineering attacks.
Greater frequency of testing critical controls
The new standard is expected to bring in a higher level of critical control testing, which implies a significant increase in the amount of testing required. Though Designated Entities Supplemental Validation (DESV) requirements are nothing new and were included in earlier versions too, they were previously mandatory only for companies that had been compromised. In this new version, these requirements may become an essential compliance standard for all businesses.
Way Forward
All in all, the changes to the PCI standard are expected to be an improvement over existing set of requirements. As with previous releases, a transition period post the formal release of PCI-DSS version 4.0, will allow organizations about two years to completely transition and comply to the new 4.0 standard. A critical practice for organizations is to ensure that current security controls in accordance with version 3.2.1, continue to be conscientious and resilient as per existing protocols. This will ensure that the transition to 4.0 is seamless and without bumps. A comprehensive transition plan can be implemented once the new standard is enforced by engaging with a PCI Qualified Security Assessor (QSA). We at SISA can provide expert security recommendations and guidance to ensure this transition is frictionless.
To learn more about how SISA can help you in your transition or to enroll to our PCI DSS Training program, contact us now!
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text

The much-awaited version 4.0 of the PCI Data Security Standard (PCI DSS) was launched on 31 March 2022, amidst much anticipation. The PCI DSS is a global standard that provides a baseline of technical and operational requirements designated to protect payment data. PCI DSS v4.0 is the next evolution of the standard and will replace v3.2.1. The evolution in this standard stems from the need for greater security for payment data in the backdrop of rising frequency and complexity of data breaches, emerging technologies and innovations, and constantly widening attack surface.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
The Curtain Rises: Unveiling PCI DSS 4.0

The much-awaited version 4.0 of the PCI Data Security Standard (PCI DSS) was launched on 31 March 2022, amidst much anticipation. The PCI DSS is a global standard that provides a baseline of technical and operational requirements designated to protect payment data. PCI DSS v4.0 is the next evolution of the standard and will replace v3.2.1. The evolution in this standard stems from the need for greater security for payment data in the backdrop of rising frequency and complexity of data breaches, emerging technologies and innovations, and constantly widening attack surface.
What’s the new focus of the standard?
The overall goals for updates to PCI DSS v4.0 are to meet the evolving security needs of the payment industry, promote security as continuous process, add flexibility for different methodologies that meet the intent of requirements, and enhance validation methods. (Read our earlier blog on preview of v4.0) The new standard is expansive in scope, futuristic in approach and sharper in focus that covers five major domains:
Risk-driven evaluation and implementation
Threat-based Plan of Action
Evolving Payment Form Factors
Coverage of end-to-end payment ecosystem
Stringent controls
A Closer Look at the New Requirements
The PCI DSS v4.0 includes a host of new requirements, 64 to be specific, that are applicable to all entities or in some instances, to service providers only. These new requirements are either effective immediately for all PCI DSS v4.0 assessments or will serve as best practices until March 2025, after which they become effective. The key changes that might have significant impact are listed below:
Requirement 1 now focusses on Network Security Controls rather than Firewalls/Routers — making it more adaptable to Clouds or Zero Trust based security architecture etc. (to support a broader range of technologies used to meet the security objectives traditionally met by firewalls)
Requirement 3 addresses security requirements of Pre-Authorized Sensitive Authentication Data (SAD) and requires encryption and implementation of data retention policies, procedures and processes. With the change in BIN range, PCI has addressed the challenge of data masking by allowing for display of BIN Range + Last 4 Digits.
Requirement 4 allows confirming the certificates used for PAN transmissions over open, public networks such as TLS etc. are valid and are not expired or revoked, while also requiring organizations to maintain an inventory of trusted keys and certificates.
Requirement 5 requires defining the frequency of periodic evaluations of system components not at risk for malware in the entity’s targeted risk analysis. System components not requiring anti-malware shall be revaluated as per the frequency set under an organization’s Risk Management Program. It also covers detection and protection against Phishing attacks.
Requirement 6 to deploy an automated technical solution (such as Web Application Firewall) for public-facing web applications that continually detects and prevents web-based attacks. It also requires new security controls for management of payment page scripts embedded in the consumer’s browser.
Requirement 7 relates to the implementation of an Access Control Model based on Least Privileges and need-to-know basis. The scope of access controls and privileges are extended to Application and System Accounts too.
Requirement 8 has the option to determine access to resources automatically by dynamically analyzing the security posture of accounts, instead of changing passwords/passphrases at least once every 90 days. Additionally, it requires organization to implement multi-factor authentication (MFA) for all access into the CDE, allows the option of using Behaviour analytics (User and Account) in place of password change and covers management of system or application accounts that can be used for interactive login.
Requirement 9 covers frequency of periodic POI Device inspection based on organization’s Risk Management practices.
Requirement 10 deals with the use of automated mechanisms to perform audit log reviews and requires new mechanisms for organizations to detect, alert, and promptly address failures of critical security control systems.
Requirement 11 has multiple sub-requirements covering Plan of Action for closure of non-ranked vulnerabilities identified during VAPT exercise, Authenticated scanning for Internal Vulnerability Assessment, deploying a change-and-tamper detection mechanism to alert for unauthorized modifications to the HTTP headers and contents of payment pages as received by the consumer browser, and requirement for multi-tenant service providers to maintain VAPT practices for their hosted customers either by providing them access to conduct these exercises or providing evidence/report.
Requirement 12 deals with performing Targeted Risk Analysis using a Customized Approach and offers flexibility for how frequently it is performed. It also includes documenting PCI DSS scope and reviewing hardware and software technologies in use and security awareness training program at least every 12 months.
What’s the way forward?
The changes and updates to the PCI standard are an improvement over existing set of requirements and appear in line with the evolving payments landscape. Some of these changes discussed above might involve a paradigm shift towards compliance in addition to the cost and resource outlays. This would mean organizations need to start planning for the transition now to avoid time and cost over-runs. To provide organizations time to understand the changes in v4.0 and implement any updates needed, the current version of PCI DSS, v3.2.1, will remain active for two years until it is retired on March 31, 2024. Organizations can engage with PCI Qualified Security Assessor (QSA) such as SISA, who can provide expert security recommendations and guidance on implementation and ensure the transition is smooth and seamless.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text

The newly released PCI DSS 4.0, with substantial changes after six years, launched on 31st March 2022. The new standards aimed at enhancing the security of systems involved in processing, storage and transmission of cardholder data were developed after three Request for Comments (RFCs) and 6,000+ feedback from more than 200 companies. While the 12 core PCI DSS requirements remain fundamentally the same, several new requirements and alterations address the evolving risks and threats to the payment data and reinforce security as a continuous process.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
PCI DSS 4.0: A Paradigm Shift to Continuous Compliance, Customization, and More

The newly released PCI DSS 4.0, with substantial changes after six years, launched on 31st March 2022. The new standards aimed at enhancing the security of systems involved in processing, storage and transmission of cardholder data were developed after three Request for Comments (RFCs) and 6,000+ feedback from more than 200 companies. While the 12 core PCI DSS requirements remain fundamentally the same, several new requirements and alterations address the evolving risks and threats to the payment data and reinforce security as a continuous process.
This article is the first in a series of opinion pieces that we will be publishing on the changes to the PCI DSS 4.0. The narrative below focuses on key changes made to the PCI standards driven by the evolving risk landscape and a range of new payment environments, technologies, and methodologies. It also discusses the significant measures that payment organizations can undertake to implement the necessary controls, maintain a secure environment, and stay compliant with the new standards.
A Quick Look at the Key Changes
As the payment industry transforms at a rapid pace, PCI DSS 4.0 intends to bring innovation and improved flexibility through key updates to the original requirements (Read our earlier blog for a closer look at the new requirements). Some of the notable revisions in the updated standards are listed below:
Emphasizing the need to protect organizations’ critical data and assets from an increasing number of phishing attacks, the new PCI standards include two requirements:
Requirement no. 5.4.1 — Processes and automation mechanisms to detect and protect personnel against phishing attacks.
Requirement no. 12.6.3.1 — Security awareness training for phishing and social engineering related attacks.
With remote working environments becoming the new norm, multi-factor authentication (MFA) has been mandated for remote access from outside the entity’s network as well.
Two new e-commerce requirements have been added to the new standards to address the emerging e-commerce skimming attacks.
The required length of passwords has been changed from a minimum of seven characters to a minimum of twelve characters to better equip the current computing capabilities.
Customized Approach to Drive Flexibility
The customized approach is a new validation option in addition to the defined approach of meeting the PCI DSS requirements. Unlike the defined approach that follows the traditional PCI DSS requirements and testing procedures to confirm that the requirements are in place, a customized approach will provide flexibility to organizations to achieve the security objective of a requirement in a different way.
To put it in simpler words, with the customized approach, entities can determine the controls and then implement them to meet the stated customized approach objective with a clear demonstration that the payment data is being protected. This flexible approach intends to encourage innovations in security technology and methods that could be applied to different environments to meet the given requirements.
“PCI DSS assessment can include both defined and customized approaches but it must be designed in consensus with the Qualified Security Assessor (QSA).”
– Nitin Bhatnagar — Associate Director, PCI Standards Council
Before considering the customized approach as an option, organizations must ensure that they have robust security processes and risk management practices in place. The defined approach is suitable for organizations with controls in place to meet the requirements as stated, or organizations that are new to information security and need direction to meet security objectives. Customized approach requires organizations to have a dedicated risk management department or an organization-wide risk management plan. However, as several requirements do not have a stated customized approach objective, entities can use both approaches within their environments by using defined approach to meet some requirements and customized approach to meet others.
It is important to note that customized approach is not a substitute for compensatory controls. While the compensatory controls remain as they are, any organization opting for customized approach cannot use compensatory controls.
Supporting New and Evolving Technologies
Being the standard that claims to be technology neutral, PCI DSS 4.0 also includes requirements which are based on the fundamental security principles that apply to all types of environments and technologies. The latest version comprises refocused requirements with additional objective statements to better emphasize their broad applicability to all types of technology including cloud environments and a range of evolving payment environments and methodologies. In addition to this, customized approach also provides flexibility to entities when they are using different processes or technology to achieve the requirement objective. The scope of requirements in the updated version, for instance, includes a dedicated section to support cloud components. Appendix A1 of the standards has also been revised for more inclusivity of modern technologies by replacing share hosting providers with multi-tenant service providers such as cloud providers. Further, a new requirement also mandates multi-tenant service providers to support their customers for penetration testing.
“As many of the frequencies in the new standards are risk-driven, focused risk assessment for PCI scope, where critical assets like card data, sensitive authentication data or card numbers are collected, is going to play a crucial role.”
– Kaushik Pandey — Global Head — Compliance and Testing Services, SISA
Developments in Authentication Controls
Considering the changing threat landscape and the feedback received from the industry, quite a few changes have been made to authentication requirements in PCI DSS 4.0. For instance, a new requirement that states MFA must be implemented for all access to CDE including remote access originating from outside the entity’s CDE has been added to the standards. While there has been a substantial change in the required length of passwords, the requirement to change them every 90 days to prevent breaches has been retained considering it is the only protection used by some entities. However, it need not apply to the systems in the organization that are protected with MFA and the specified requirement can be marked as NA for those systems. In addition to this, the use of group shared generic accounts, which was prohibited in the earlier version, has been permitted under exceptional circumstances such as limited timeframe or approval/confirmation of user identity and actions attributable to the individuals.
Way Forward — Plan-Do-Check-Act Approach for Implementation
In the initial phases of the implementation timeline, the organizations must first understand the new standards before taking any action to execute the process. The PCI SSC is also going to organize multiple sessions and events including transitional trainings starting from June 2022 to help organizations understand the interpretation of new standards before they start implementing them. In addition to this, SISA is also launching its CPISI — PCI DSS Implementation Workshop 4.0 on 27th-28th April 2022, to help information security stakeholders take proactive steps for PCI implementation.
Although the implementation process for PCI DSS 4.0 is going to be a two-year project, organizations cannot wait until 31st March 2024 to get started; they must start from today. A systematic approach such as the Plan-Do-Check-Act (PDCA) can be leveraged to smoothly transition to new standards:
Plan — To understand all the significant changes made to the PCI standards and their effect on the businesses, it is essential for organizations to read the new standards and then plan their course of action for the period ahead.
Do — The next step involves setting up a task force that could start implementing the changes to the business operations and policies of the organization to stay prepared for the assessment.
Check — At this stage, it would be beneficial for organizations to carry out a gap analysis with the help of their Qualified Security Assessor (QSA) to recognize the further changes that need to be made to meet the new requirements.
Act — After understanding the new standards and making the changes in their processes, organizations can finally implement the necessary controls to continue meeting the PCI DSS 4.0 requirements at the time of assessment in 2024.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text

The newly released PCI DSS 4.0 continues to be hotly debated and discussed, since its launch on 31st March 2022. The new standards are aimed at enhancing the security of systems involved in processing, storage and transmission of cardholder data while also addressing new payment environments, technologies and evolving risks.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
All Your Questions on PCI DSS 4.0, Answered


The newly released PCI DSS 4.0 continues to be hotly debated and discussed, since its launch on 31st March 2022. The new standards are aimed at enhancing the security of systems involved in processing, storage and transmission of cardholder data while also addressing new payment environments, technologies and evolving risks.
This post helps answer some of the frequently asked questions on the new standard including implementation queries, to help create awareness and guide organizations in their transition.
If an organization gets re-certified on January 2024 and the following certification is done in January 2025, can they still be certified on v.3.2.1 because v4.0 will be cut-off from March 2025?
PCI DSS version 3.2.1 will get retired on 31st March 2024. Hence any assessment being performed post that will have to be on v4.0.
2. What are the major changes in version 4.0?
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
3. Do we have any changes on Data Encryption?
Yes, PCI DSS v4.0 allows Disk level encryption for only removable media as per requirement 3.5.1.2 (“New requirement that disk-level or partition-level encryption is used only to render PAN unreadable on removable electronic media or, if used on non-removable electronic media, the PAN is also rendered unreadable via a mechanism that meets Requirement 3.5.1.”).
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
When will Prioritized Approach document for PCI DSS v4.0 be released? Can we continue to follow the prioritized v3.2.1 in the meantime?
PCI SSC has not highlighted the release date for Prioritized Approach document. SISA expects that PCI SSC will be releasing the supporting document within next 2–3 months.
Prioritized approach v3.2.1 is applicable only for PCI DSS v3.2.1. Considering that PCI DSS v3.2.1 is valid until 31st March 2024, organizations can continue using the document until then.
4. What is the difference b/w customized approach controls and compensating controls?
Compensating Controls are applicable for entities which are not able to meet the requirement as stated in the defined approach due to the documented technical or business constraints, but the entity has implemented alternative controls to mitigate the risk associated with that control.
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
5. How about third-party contractors and their approach to customized environment? Is that workable?
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
Hence the entity must ensure that the 3rd party contractors have very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach. A proper due diligence must be carried out.
6. Does PCI DSS v4.0 address data leakage threats and associated controls, if any?
PCI DSS v4.0 has not covered the threats and associated controls related with data leakage.
A part of requirement 11.5.1.1 (additional requirement for service provider) standard highlights that having a DLP solution is a good practice.
A part of requirement A3.2.6 Appendix 3 (DESV) standard highlights that, mechanisms should be in place to detect and prevent cleartext PAN from leaving the CDE via unauthorized channel, method or processes.
7. Currently Biometric is used as physical security control for CDE environment so do we need MFA for physical security control. For example: Biometric + PIN?
The requirement of MFA is basically for all remote access and administrators with non-console access to CDE. MFA is not required for any physical access per se.
8.Is there any summary comparison chart for v3.2.1 vs v4.0?
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
9. For organizations that are currently implementing v3.2.1 when will v4.0 be applicable?
PCI DSS v3.2.1 will be valid until 31st March 2024.
Entities can start implementing controls as highlighted in v4.0 to ensure the compliance before opting for the assessment as per v4.0.
Post 31st March 2024 v3.2.1. will retire and all entities must be certified on v4.0. All evolving requirements under v4.0 should be addressed, and an organization must be compliant against these requirements before 2025.
10. Risk assessment in Vulnerability assessment appears more stringent in v4.0, which now requires Medium and Low rating, and this will yield a lot of vulnerabilities to be mitigated. Is the Risk Assessment required going to be a manual approach or can we use automated tools like Tenable which has integrated Threat intelligence and Data Science wherein, it has VPR or Vulnerability Priority Rating which prioritizes those real threats that are publicly exploitable?
PCI never mandates b/w an automated solution or a manual approach being followed. The flexibility is with the end customer. The only important parameter here is the risk associated with a particular control must be identified and actioned upon accordingly. Please note though, that PCI mandates an authenticated scan to be performed to identify the vulnerabilities.
11. Can you share Website/Link to refer/learn about new standard, changes etc.?
Kindly refer the document library page of PCI SSC website.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
12. Previously we had customized actions covered under CCW… How will that change now?
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
Hence the entity must ensure that the 3rd party contractor has very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach.
13. Whether the customized approach would include the term called compensatory controls?
Compensating controls and customized controls are two different things.
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated. Hence the entity must ensure that the 3rd party contractor has very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach.
Compensating controls may be considered when an entity cannot meet a PCI DSS requirement explicitly as stated, due to legitimate and documented technical or business constraints but has sufficiently mitigated the risk associated with the requirement through implementation of other, or compensating, controls. To maintain compliance, processes and controls must be in place to ensure compensating controls remain effective after the assessment is complete.
14. Any specific requirements change for Service Providers?
Kindly refer to “6. Summary of New Requirements” on page 29 of PCI DSS summary of change (v3.2.1 to v4.0) document at PCI SSC document library page.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
15. Can an organization migrate or switch over or toggle between the defined & customized approach during the re-certification?
Yes, but this again depends on the scope of work covered during the certification process and the applicability of controls defined.
16. How about continuation of compliance in case of any mergers or acquisitions?
Same process as usual. A delta assessment must be performed, and all the relevant documents must be updated. Else this can be covered during the re-certification process.
17. How and when will the new PCI DSS standards be aligned / integrated with the Regulatory asks/ guidelines (in our case RBI) on PCI DSS?
Different RBI guidelines released for entities in payment eco-system mandate entities to be PCI DSS compliant. Considering that PCI DSS v3.2.1 will be valid until 31st March 2024, entities can continue following the same until RBI releases specific guidelines mandating compliance as per PCI DSS v4.0.
18. Does the new standard recommend or enforce the use of strong cryptographic standards like FIPS 140–2?
Please refer to https://www.pcisecuritystandards.org/documents/PCI-DSS-v4_0.pdf?agreement=true&time=1649361221495 (Cryptography)
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text

The customized approach offers flexibility to organizations that decide to use different methods to achieve security objectives of PCI DSS requirements by determining innovative controls that address evolving threats and technologies.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes