#ddos scrubbing service
Text
Why are we using DDoS protection?
Protecting your data against DDoS attacks is like keeping your sanity. Imagine being out-of-access of your own data. Also, it is annoying when your potential traffic is disengaged due to data flooding on your platform. To fight such absurdities, Akamai deploys its DDoS scrubbing service with 200+ frontline SOCC defenders 24/7.
0 notes
Text
does a vpn stop ddos attacks
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn stop ddos attacks
VPN DDoS protection
Title: Safeguard Your Online Presence with VPN DDoS Protection
In the digital age, where cyber threats loom large, safeguarding your online presence is paramount. One such threat that has garnered significant attention in recent years is Distributed Denial of Service (DDoS) attacks. These malicious assaults aim to disrupt the availability of online services by overwhelming them with a flood of traffic from multiple sources. To combat this menace, Virtual Private Networks (VPNs) have emerged as a crucial line of defense, offering robust DDoS protection.
VPN DDoS protection works by encrypting internet traffic and routing it through secure servers, thereby masking your real IP address and adding an extra layer of anonymity. This encryption and rerouting process make it exceedingly difficult for attackers to target your device directly, as they are unable to identify its true location amidst the VPN's network of servers.
Furthermore, VPNs employ sophisticated traffic filtering mechanisms to weed out suspicious traffic patterns associated with DDoS attacks. By continuously monitoring incoming data packets, VPNs can detect and mitigate potential threats in real-time, thereby ensuring uninterrupted access to online services.
Moreover, VPNs offer the flexibility to choose from a wide range of server locations, allowing users to switch between different servers to evade DDoS attacks effectively. This geographical diversity disperses traffic across multiple servers, making it challenging for attackers to concentrate their assault on a single target.
Additionally, reputable VPN providers invest in robust infrastructure and employ advanced security protocols to fortify their networks against DDoS attacks. This proactive approach ensures that users can browse the internet with peace of mind, knowing that their online activities are shielded from potential threats.
In conclusion, VPN DDoS protection serves as a vital safeguard against cyber threats, offering users a secure and reliable means to protect their online presence. By encrypting internet traffic, filtering malicious data packets, and leveraging a global network of servers, VPNs empower users to navigate the digital landscape with confidence and peace of mind.
Virtual private network DDoS defense
A Virtual Private Network (VPN) provides a secure and encrypted connection over the internet, allowing users to protect their online privacy and data. However, VPN services are not immune to Distributed Denial of Service (DDoS) attacks, which can disrupt their functionality and compromise user experience. To safeguard against such threats, VPN providers implement robust DDoS defense mechanisms.
One common method used for VPN DDoS defense is traffic scrubbing. This involves analyzing incoming network traffic to identify and filter out malicious requests before they reach the VPN server. By inspecting packets and detecting abnormal patterns, VPN servers can prevent DDoS attacks from overwhelming their resources and causing downtime.
Additionally, VPN providers may leverage load balancing techniques to distribute incoming traffic across multiple servers. By evenly spreading the load, VPN servers can better withstand DDoS attacks and maintain service availability for legitimate users. This proactive approach helps mitigate the impact of DDoS attacks and ensures uninterrupted VPN connectivity.
Furthermore, VPN services employ real-time monitoring and anomaly detection tools to identify suspicious network behavior indicative of a DDoS attack. By continuously monitoring traffic patterns and server performance metrics, VPN providers can promptly respond to threats and implement countermeasures to defend against DDoS attacks effectively.
In conclusion, VPN DDoS defense plays a crucial role in upholding the security and reliability of VPN services. By implementing robust defense mechanisms such as traffic scrubbing, load balancing, and real-time monitoring, VPN providers can protect their infrastructure against DDoS attacks and deliver a seamless and secure browsing experience for their users.
VPN shield against DDoS attacks
A VPN can serve as a shield against DDoS (Distributed Denial of Service) attacks by adding an extra layer of security to your internet connection. DDoS attacks are malicious attempts to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. These attacks can lead to unavailability of the targeted online service, rendering it inaccessible to legitimate users.
When you connect to the internet through a VPN (Virtual Private Network), your internet traffic is encrypted and routed through a secure server before reaching its destination. This means that your real IP address is masked, making it difficult for attackers to target your actual network or device with a DDoS attack. Additionally, VPNs have robust security measures in place to detect and block suspicious traffic patterns that are commonly associated with DDoS attacks.
Using a VPN not only helps protect your online privacy and security but also acts as a preventative measure against DDoS attacks. By hiding your IP address and encrypting your internet traffic, a VPN creates a secure tunnel that shields your connection from potential threats, including DDoS attackers. It adds a level of anonymity and security that can deter malicious actors from targeting your network or devices.
In conclusion, investing in a reputable VPN service can provide an added layer of protection against DDoS attacks, ensuring a more secure and uninterrupted online experience. Remember to choose a reliable VPN provider with strong encryption protocols and advanced security features to safeguard your internet connection effectively.
VPN mitigation for DDoS assaults
In the digital age, cyber threats such as Distributed Denial of Service (DDoS) attacks have become increasingly common, posing a serious risk to online platforms and businesses. DDoS assaults can disrupt services, causing downtime and financial losses. One effective method to mitigate the impact of DDoS attacks is by using a Virtual Private Network (VPN).
A VPN creates a secure and encrypted connection between the user's device and the internet, masking the user's IP address and providing anonymity. When facing a DDoS attack, implementing a VPN can help distribute and absorb the traffic, preventing the target server from becoming overwhelmed. By rerouting the incoming traffic through VPN servers, the attack surface is expanded, making it harder for attackers to pinpoint the exact target.
Furthermore, VPNs offer additional layers of security by encrypting data transmission, protecting sensitive information from being intercepted by malicious parties during a DDoS attack. This added security measure can safeguard user privacy and prevent unauthorized access to confidential data.
It is important to select a reliable and trustworthy VPN provider with robust infrastructure and capabilities to handle DDoS attacks effectively. Regularly updating VPN software and maintaining strong encryption protocols are essential practices to ensure optimal protection against cyber threats.
In conclusion, utilizing a VPN for DDoS mitigation is a proactive and effective strategy to safeguard online assets and maintain business continuity. By leveraging the security features of a VPN, organizations can reinforce their defense mechanisms and mitigate the impact of DDoS assaults in an increasingly interconnected digital landscape.
VPN safeguard from DDoS threats
In today's digital landscape, safeguarding your online presence against various cyber threats is paramount. One such threat that has gained notoriety in recent years is Distributed Denial of Service (DDoS) attacks. These attacks can cripple websites and online services by overwhelming them with an influx of malicious traffic, rendering them inaccessible to legitimate users.
Fortunately, Virtual Private Networks (VPNs) offer a robust defense mechanism against DDoS threats. By routing your internet traffic through secure servers and encrypting your data, VPNs obscure your real IP address and location, making it significantly harder for attackers to target you directly.
One of the primary ways VPNs protect against DDoS attacks is by masking your IP address. Instead of exposing your actual IP to potential attackers, VPNs assign you a temporary IP address from one of their servers located around the world. This effectively hides your true online identity, making it challenging for attackers to pinpoint and launch DDoS attacks against you.
Additionally, VPNs employ encryption protocols to secure your internet traffic, further fortifying your defense against DDoS threats. By encrypting data transmissions between your device and the VPN server, VPNs ensure that even if attackers manage to intercept your traffic, they won't be able to decipher its contents or launch effective DDoS attacks.
Furthermore, reputable VPN providers often have robust infrastructure and sophisticated DDoS mitigation measures in place. This means that even if attackers attempt to target VPN servers with DDoS attacks, the provider can quickly identify and mitigate these threats, ensuring minimal disruption to their users' online activities.
In conclusion, VPNs serve as a powerful shield against DDoS threats by masking your IP address, encrypting your internet traffic, and leveraging robust infrastructure to mitigate attacks. By incorporating a VPN into your cybersecurity arsenal, you can significantly enhance your online protection and enjoy a safer browsing experience.
0 notes
Text
Shielding Cyberspace: DDoS Protection and Mitigation Security Market Insights
In today's digital landscape, cybersecurity has become a paramount concern for businesses, organizations, and individuals alike. Among the myriad of threats that loom large in cyberspace, Distributed Denial of Service (DDoS) attacks pose a significant risk, capable of disrupting online services, causing financial losses, and tarnishing reputations. As a result, the DDoS protection and mitigation security market has emerged as a critical defense mechanism, providing proactive measures to safeguard against these malicious assaults and ensure the uninterrupted operation of online assets.
At the core of the DDoS protection and mitigation security market lies the imperative to detect, deflect, and neutralize DDoS attacks in real-time. DDoS attacks involve overwhelming a target server, network, or application with a flood of illegitimate traffic, rendering it inaccessible to legitimate users. DDoS protection solutions employ sophisticated algorithms, machine learning, and traffic analysis techniques to identify and filter out malicious traffic, allowing legitimate traffic to reach its intended destination. By leveraging a combination of on-premises appliances, cloud-based scrubbing centers, and content delivery networks (CDNs), DDoS protection providers can mitigate the impact of DDoS attacks and maintain service availability.
Moreover, the DDoS protection and mitigation security market is driven by the increasing frequency, sophistication, and scale of DDoS attacks perpetrated by cybercriminals and hacktivist groups. DDoS attacks have evolved beyond simple volumetric attacks to include more complex and stealthy techniques, such as application layer attacks, DNS amplification attacks, and IoT-based botnets. Additionally, the proliferation of IoT devices, cloud services, and interconnected networks has expanded the attack surface, making organizations more vulnerable to DDoS attacks. As a result, businesses and organizations are investing in robust DDoS protection solutions to fortify their cyber defenses and safeguard their online assets.
Request the sample copy of report @ https://www.globalinsightservices.com/request-sample/GIS20708
Additionally, the DDoS protection and mitigation security market is responding to evolving regulatory requirements and industry standards aimed at enhancing cybersecurity resilience and incident response capabilities. Regulatory bodies, such as the Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), and NIST Cybersecurity Framework, mandate organizations to implement adequate measures to protect against DDoS attacks and ensure the integrity and availability of their online services. Compliance with these regulations requires organizations to deploy DDoS protection solutions and develop comprehensive incident response plans to mitigate the impact of DDoS attacks and safeguard sensitive data.
Furthermore, the DDoS protection and mitigation security market is witnessing innovation and advancements in technology to counter emerging DDoS threats and challenges. DDoS protection providers are developing new capabilities, such as behavioral analysis, threat intelligence sharing, and automated response mechanisms, to enhance detection and mitigation of DDoS attacks. Additionally, partnerships and collaborations between DDoS protection vendors, Internet service providers (ISPs), and cybersecurity organizations are enabling a collective defense approach to combatting DDoS attacks, leveraging shared threat intelligence and collaborative mitigation strategies to enhance cyber resilience and response capabilities.
Despite the opportunities for growth, the DDoS protection and mitigation security market also faces challenges, including cost constraints, false positives, and evasion techniques employed by attackers. Implementing robust DDoS protection solutions requires significant investment in hardware, software, and expertise, which may be prohibitive for smaller organizations with limited resources. Additionally, DDoS protection solutions must strike a balance between accurately identifying and blocking malicious traffic while minimizing disruption to legitimate users, avoiding false positives and collateral damage. Furthermore, attackers continue to evolve their tactics and techniques to evade detection and mitigation efforts, necessitating ongoing innovation and adaptation in DDoS protection strategies and technologies.
In conclusion, the DDoS protection and mitigation security market is a vital component of the cybersecurity landscape, providing essential defenses against one of the most prevalent and damaging cyber threats. By leveraging advanced technologies, industry partnerships, and regulatory compliance initiatives, DDoS protection providers can enhance cyber resilience, mitigate the impact of DDoS attacks, and ensure the uninterrupted operation of online services. As cyber threats continue to evolve and escalate, the DDoS protection and mitigation security market will remain at the forefront of efforts to safeguard cyberspace and protect organizations from the debilitating effects of DDoS attacks.
0 notes
Text
"Secure, Protect, Prevail: DDoS Prevention Essentials"
(DDoS) Attack in Hacking:

Implement DDoS Mitigation Services:
Consider using a DDoS mitigation service, often provided by specialized companies. These services can detect and filter out malicious traffic, allowing legitimate traffic to reach your network or website.
2.Update and Patch Your Systems:
Keep your operating systems, applications, and network equipment up to date. Regularly applying security patches can fix vulnerabilities that attackers might exploit.
3.Use Content Delivery Networks (CDNs):
CDNs distribute your content across multiple geographically dispersed servers. This can help absorb DDoS traffic and ensure that your services remain available even during an attack.
4.Employ Rate Limiting and Access Controls:
Implement rate limiting on your servers or firewalls to restrict the number of requests from a single source. Access controls can be used to block traffic from specific IP addresses or regions.
5.Network Load Balancing:
Distribute incoming traffic across multiple servers using load balancers. This not only ensures high availability but can also distribute the load in the event of a DDoS attack.
6.Incident Response Plan:
Develop a comprehensive incident response plan that outlines the steps to be taken when a DDoS attack is detected. Ensure that your IT and security teams know their roles and responsibilities during an attack.

8. IP Reputation Lists:
Use IP reputation lists, which are databases of known malicious IP addresses. These lists can be integrated into your security systems to block traffic from suspicious sources.
9. Use Web Application Firewalls (WAF):
Deploy a Web Application Firewall to protect your web applications from application layer DDoS attacks. WAFs can identify and filter out malicious traffic and help prevent targeted application layer attacks.
10. Implement BGP Flowspec:
BGP Flowspec (Border Gateway Protocol Flowspec) allows network administrators to create rules for filtering traffic at the network border based on specific criteria. This can be used to block DDoS traffic based on predefined rules.
11. Rate-Based Limiting:
Implement rate-based limiting at the network or application level. This strategy ensures that traffic exceeding a specified rate is dropped, mitigating the impact of high-volume DDoS attacks.
12. Traffic Scrubbing Services:
Consider subscribing to traffic scrubbing services offered by DDoS mitigation providers. These services reroute your traffic through their systems to filter out malicious traffic, leaving only legitimate traffic to reach your network.
13. Anycast DNS:
Anycast DNS distributes DNS queries across multiple geographically distributed servers. This can help prevent DNS-based DDoS attacks by ensuring redundancy and resilience.
14. Cloud-Based Protection:
Leverage cloud-based DDoS protection services. These services are hosted in the cloud and can handle DDoS attacks before they reach your network, offering a scalable and effective solution.
15.Use Intrusion Detection and Prevention Systems (IDPS):
Deploy IDPS systems that can identify and block suspicious or malicious traffic. These systems can be configured to recognize DDoS attack patterns.
By implementing these best practices, you can fortify your defenses against DDoS attacks. It’s essential to adopt a multi-layered approach to DDoS prevention, combining technical solutions, policies, and incident response plans to ensure the highest level of protection for your online services. Remember that while no defense is foolproof, a proactive and comprehensive strategy can significantly reduce the risk and impact of DDoS attacks.
If you want to learn more about it, I highly recommend that you contact ACTE Technologies because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline.
If you feel that my response has been helpful, make sure to follow me and it will encourage me to upload more content about Ethical hacking.
Thanks for spending your valuable time . Have a great day
0 notes
Text
"Understanding DDoS Attacks: Safeguarding Your Online Presence"
Distributed Denial of Service (DDoS) protection refers to a set of measures and technologies implemented to defend computer networks, servers, and websites against DDoS attacks. A DDoS attack occurs when multiple compromised systems flood a targeted network or website with an overwhelming amount of traffic, causing it to become unavailable to legitimate users. DDoS attacks can disrupt online services, compromise network security, and result in financial losses for businesses.
DDoS protection solutions aim to detect and mitigate these attacks by employing various techniques. One commonly used approach is traffic filtering, where incoming traffic is analyzed and suspicious or malicious traffic is blocked or redirected. This helps to separate legitimate requests from malicious ones, ensuring that the network or website can handle genuine user traffic effectively. Another technique involves using rate limiting or traffic shaping mechanisms to control the flow of incoming requests, preventing overwhelming traffic surges that can lead to service disruptions.
Moreover, DDoS protection solutions often leverage advanced monitoring and analytics capabilities to identify and respond to DDoS attacks in real-time. These solutions monitor network traffic patterns, detect anomalies or sudden spikes in traffic volume, and take immediate action to mitigate the attack. This can include diverting traffic to scrubbing centers, which filter out malicious traffic and allow only legitimate traffic to reach the target.
Overall, DDoS protection plays a crucial role in safeguarding online services and ensuring their availability and reliability. By implementing robust protection mechanisms, organizations can minimize the impact of DDoS attacks, maintain business continuity, and protect their reputation and customer trust.
Read more @ https://techinforite.blogspot.com/2023/05/ddos-protection-best-practices.html
0 notes
Link
Edgio adds advanced DDoS protection with other WAAP enhancements https://nlkhgtbj.com/edgio-adds-advanced-ddos-protection-with-other-waap-enhancements/?feed_id=42&_unique_id=63f9f9453b870 #business #entrepreneur #motivation #marketing #success #money #love #smallbusiness #entrepreneurship #businessowner #mindset #instagram #inspiration #lunc #lifestyle #startup #digitalmarketing #goals #lunc #life #branding #investment #design #finance #follow #fashion #crypto #motivationalquotes #socialmedia #btc
0 notes
Text
They need a trusted partner with a proven record in DDoS attacks mitigation and DDoS attack prevention. Akamai provides in-depth DDoS defense through a transparent mesh of dedicated edge, distributed domain name service (DNS), and cloud scrubbing services.
0 notes
Link
For a few years now, we here at DOSarrest started to field enquiries into hybrid DDoS defense setups, where customers wanted to leverage their existing on-premise DDoS mitigation infrastructure to work in co-ordination with the cloud scrubbing capabilities that our network infrastructure protection service, which we call “Data Center Defender” aka DCD is able to provide.
0 notes
Text
How To Protect Your Business From The DDoS Attack

According to top-rated protection companies, DDoS attacks are now on the increase and costing businesses more money than ever before. In a DDoS attack, a huge volume of Internet traffic is brought down because of a coordinated attack by several people or malicious attackers using a large number of instruments - mostly computers. Some attacks can be very simple, while others involve sophisticated technology. Some attacks can be initiated from an outside source, while others are software based. Most of the attacks that occur today do not involve sophisticated tools or devices, but instead they are the result of someone just trying to find something interesting to post on a Web site.
There are a lot of reasons why companies resort to DDoS Protection. One of the top causes for a DDoS attack is a deliberate act by someone with ill intent. For example, say you are visiting a site that promotes a political candidate in your state. That candidate might post an advertisement about his or her support for the DDoS attacker's cause. If enough Internet users visit that site and put together a massive DDoS attack, the site could go down for a long time, interrupting everyone who was just visiting.
In order to avoid a DDoS attack or reduce the likelihood of one, the best way to defend against it is to have a reliable, scalable infrastructure that's properly configured and protects against all kinds of DDoS threats. No matter how sophisticated and well-planned the attack is, the Internet service provider or network administrator has to be able to respond to a DDoS attack within minutes. The best protective measures for an Internet service provider or network include things like a variety of layers of security appliances, traffic management, application layer forwarding, automatic traffic counters, and quality assurance. By providing excellent DDoS threat assessment, businesses can greatly reduce their exposure to cyber attacks and enhance their overall online security posture.
A good measure for mitigating volumetric attacks is to calculate the amount of bandwidth that would be necessary to handle the expected number of visitors to the site. The smaller the bandwidth required, the better off a website will be in terms of its ability to mitigate attacks. A company should also consider the purpose of the website, such as if it were made to facilitate fast file sharing, a large-scale interactive forum, or is an e-commerce operation. Each of these purposes will require different types of technology for which high-speed Internet access is essential. A business can improve its ability to mitigate attacks by choosing a technology provider that offers features such as simultaneous streaming, real-time data buffering, and data duplication.

For instance, if a website was intended for a small number of viewers, it may not need the features offered by high-speed Internet. However, if the site was developed for hundreds of thousands of viewers, it would be wise to use the DDoS protection feature available from most popular Web hosting providers. Businesses should choose providers that offer DDoS scrubbing centers to ensure that they receive the highest level of attack protection available.
Depending on the nature of the attacks and the target audience, some types of DDoS protection services may be easier than others. Some service providers have the capability to monitor web traffic for attack traces. They can also evaluate attack scripts and determine the best mitigation techniques for each attack scenario. Businesses should ensure that the service provider selected provides the necessary capabilities to meet their needs.
Another type of DDoS protection is the mitigation technique used to avoid further damage being done to a server or network by a flood of unwanted servers. Flood attacks occur when many users create a flood of traffic to a single server. This overload can cause significant problems in processing data and can cause users to lose revenue. In order to minimize the impact of a failed server, the mitigation techniques adopted should reduce the number of active servers and the bandwidth available. Maintaining DDoS defense services will help prevent loss of revenue due to a DDoS attack.
Businesses should take advantage of the technology offered by cloud computing providers to protect themselves from DDoS attacks. Many cloud computing providers are offering DDoS defense services at no cost. They offer free trial periods to help businesses evaluate their needs and determine if cloud computing is right for them. For businesses that decide to use cloud services, they should make sure to use a provider with a good reputation and a solid track record for effective mitigation techniques. Using the right DDoS defense technology with a good service plan and a free trial can help businesses minimize risk and increase revenue.
0 notes
Text
HOSTDIME HOSTING REVIEW

HOSTDIME HOSTING REVIEW
HostDime was founded by Vivar Manny in Florida, United States in 2001. With the increase in number of its servers, the company deemed to take necessary steps to establish a full-fledged data center. In December 2003, HostDime became a proud owner of a high-tech data center. HostDime mainly focus on delivering managed cloud web hosting and tools to help their individuals and business to make their online availability without any hassles. HostDime is attractive for its affordable pricing, high uptime, and 24/7 customer service.
General Information
1. Speed - 920 ms (November 2019 to November 2020 average)
2. UpTime - 99.99% (November 2019 to November 2020 average)
3. Support - live chat, email, phone line
4. Apps - Joomla, WordPress, Drupal, PHP, Zen Cart, and other popular apps.
5. Features - Softaculous website builder, DDoS protection, SSL certificates, Remote site backups, CDN and Cloud Accelerator, Bandwidth limits, Activity monitoring and web stats, WordPress support, One- click app installs, 24/7 tech support, Money-back guarantee.

6. Plans - Dedicated server hosting/ Cloud services Colocation
7. Site Transfer - Free site transfers within the first month of signing up
8. Price - The cheapest hosting plan from HostDime costs $35.51 per month
Pros and Cons of HostDime Hosting
1.Reliable uptime - HostDime promises good performance and an uptime of 99.99% per month. They value their promise by giving a refund if their scales fall into a range,
# 95% to 99.98% - refund of 10% of your monthly payment
# 90% to 94.9% - refund of 25% of your monthly payment
# 89.99% and below- full refund of your monthly payment
The company has put several measures to ensure that your site remains up and running throughout. Their real-time monitoring system helps them to get live updates about how their server is fairing. This system is popularly known as Synapse. HostDime gives tech support to rectify issues even before we notice them.
2.Impressive loading times
HostDime features fast page loading times. On average, most hosted sites display results within 920 ms. HostDime being one of the largest data centre in the south-east US has excellent network credentials. Additionally, the web host partners with highly reputed Tier-1 carriers including NTT Communications and Cogent to deliver stellar connection speeds and bandwidth.
3.Helpful customer support
HostDime data centers are fully equipped with complete around-the-clock tech support and can be contacted by means of live chat, telephone, or email with just few details to link with customer support representative.
HostDime website and blog section are two areas from which useful information and answers are available for all type of queries of the customers.
HostDime also has a few self-help options. FAQS, manuals, guides, and video tutorials. There is a customer community, where HostDime staff and fellow customers can be interacted.
4.Top-class security
HostDime hosting offers top class security features at an additional cost. HostDime provides DDoS protection to all users. This comes in three different types,
- traffic scrubbing
- NETSCOUT’s mitigation - NETSCOUT’s filtering helps to guard sites against unusual high or irregular traffic.
- Cloud Protection - Cloud protection is a hybrid system that provides real-time site monitoring of all sites.
- SSL certificate from HostDime is an advantage that authenticates website and assures visitors as safe website.
5. Easy-to-use dashboard
HostDime features a very easy cPanel that allows users to painlessly manage all the aspects of their hosting. The cPanel dashboard displays useful information like bandwidth graphs, billing information, affiliate program, server performance, and licenses management.
6. Cons
HostDime policy on strict money-back guarantee is not attractive. Some users notice a fall of uptime.
Hosting Plans
1.Managed VPS – 1: Cost at $65/ month, Storage space 60 GB, Bandwidth limit 5 TB.
2. Managed VPS – 2: Cost at $80/month, Storage space 100 GB, Bandwidth limit 5TB
3. Windows WVPS- 1: Cost at $85/ month, Storage space 60 GB, Bandwidth limit 5 TB.
Other Hosting Plans
1. Quad-core dedicated servers
2. Managed VPS
3. Colocation packages
Recommended
Though not a smart option for beginners or small businesses most of the plans are made for customers with complex IT needs and big budgets. Generally, HostDime is a professional web hosting provider.
0 notes
Text
Who are the major providers to protect against a DDoS attack?
Akamai is the top and one of the best DDoS attack mitigation and protection provider. Akamai provides in-depth DDoS mitigation defense through a transparent mesh of dedicated edge, distributed DNS, and cloud scrubbing defenses. Akamai DDoS attack mitigation solutions can be fine-tuned to the specific requirements of web applications and internet-based services. Akamai DDoS mitigation reduces attack surfaces, improves the quality of mitigation, and reduces false positives, while increasing resiliency against the largest and most complex attacks.
0 notes
Text
Maximizing Efficiency Through Secured Network
With the constantly evolving and complex cyber threat landscape, companies often find themselves at the loss of efficient security tools and capacity in-house to maintain their security measures.
Since organizations have increasingly become vulnerable to hackers’ attacks, they now experience higher risks and increased levels of uncertainty. With so much to deal with, taking help from an experienced IT management company like Ventura Solution might be the best choice you can make for your business.
Ventura Solution offers all-encompassing information security in Newark services that grants your enterprise a fighting chance against those who intend to harm you. As a trusted advisor, we work hard in order to Optimize Your Processes and make them work efficiently. It's our unbeatable track record of safeguarding clients from cyber threats, that proves our excellence in the field.
Antivirus Software Services For Your Security Needs
Our portfolio of Antivirus Software & information security in Newark and cybersecurity solutions encompasses several designs meeting your company’s needs. These customizable solutions are crafted as per each and every business’ specific requirements. These services include:
IP Protection - A hardware-based solution that recognizes incoming DDoS attacks through scrubbing centres, and re-route them before they are able to discover your system’s IP address.
Managed Cyber Security - These include SIEM SOC services that combine both the Security Information & Event Monitoring for the purpose of responding to threats boldly.
Penetration Testing - This involves our team of security experts constantly testing programs for discovering vulnerabilities in your IT environment.
Why Do You Need Our Protection?
Enjoy peace of mind - Our services constantly monitor your systems and respond to any threats, knowing that you can leave your information security in Newark worries to us.
Customize your cyber protection - our cybersecurity services are personalized for clients for achieving protection against specific cybersecurity threats.
Save money - Our Antivirus Software protects you from hackers’ attacks on your systems that may harm your organization’s functioning.
So, protect your businesses with our company’s advanced solutions and simplify system protection with our value-driven monitoring, management and threat intelligence backed by the experience of global expertise.
Contact us to avail the benefits of our integrated security portfolio today only.
#Antivirus Software & information security in Newark#Antivirus Software & information security Newark#Antivirus Software in Newark#information security in Newark
0 notes
Text
5 tips for starting international PPC
Expanding marketing agency efforts beyond your home country can be an exciting step. However, branching into new regions with PPC entails much more than simply copying your campaigns and changing the geographic targeting.
Don’t rush into setting up international campaigns until you’ve thought out budgeting, channel allocation, account structure, localization, and unique regional concerns. In this article, I’ll expand on each of these points to help you establish a framework for beginning to target other countries.
Budget for different costs by country
CPCs and CPMs to compete in ad auctions vary widely by country. You can get a rough estimate for projected spend in Google search by adding your keywords to Google Keyword Planner and setting the region to the country you’re planning to target. However, these estimates can be off, and you’ll get the best idea of average CPCs/CPMs once you actually start running a campaign and see actual figures.

In addition, costs for customer acquisition also will likely vary by country. If you’re just starting to advertise in a region that’s not familiar with your brand, you can often expect higher CPAs.
However, you might find the opposite to be true if CPCs are lower in that region. I recently launched a LinkedIn campaign in Latin America for a client, and we found that CPAs were less than half of our averages in the United States due to significantly lower CPCs.
Also, pay attention to CRM data to measure lead quality. While they may be cheaper in a region, a lower percentage of prospects may actually be the right potential customers. You’ll ultimately want to look at metrics like cost per qualified lead and cost per completed sale to determine what CPAs to aim for in your campaigns.
Research top channels by region
Consider what search and social channels people use the most in the regions you’re looking to target. Targeting Google alone will exclude a significant number of users in several countries. For instance, Yandex covers 44% of the search engine market share in Russia, and Baidu has 66% of the market share in China.
StatCounter is a good site to start for research (with the caveat that no stats are going to be 100% accurate), as well as talking to contacts on the ground in regions you’re looking to target. Representatives at ad platforms may be able to assist in providing stats on regional usage, as well.
Plan for account structure
Separating campaigns by country, or by overarching region, allows you to better control bids and segment out reporting. This tactic also prevents countries with cheaper CPCs and high volume from cannibalizing spend, giving countries that may have higher CPCs, but quality leads, a chance to perform.
Separate geographic campaigns also allow for more accurate usage of time-based bid modifiers. If you lump the Europe and the US into the same campaign, and lower bids during the night in the US, you’re effectively also lowering bids during the workday in Europe. Keeping those regions in different campaigns allows you to apply hourly bid modifiers without worrying about hurting performance in time zones several hours away.
You should also consider billing needs when deciding how to segment out accounts. Particularly for enterprise-level companies, payment often needs to come from different divisions by region. Using separate ad accounts may be necessary to ensure you can use different billing sources for each division.
Include asset localization
Make sure to localize copy for the people you’re aiming to reach. This work may entail translating keywords, ad copy, and landing page copy into another language.
Or, you may be targeting people who already speak English but use different words based on regional dialects. For instance, if you’re selling diapers, you’ll want to refer to “nappies” when advertising in Britain. See how the wording on these example results pages vary for the same product category between Amazon US (“diapers”) and Amazon UK (“nappies”):


Be sure to adapt for regional spellings, as well. For instance, a call-to-action to “View Our Catalog” should say “View Our Catalogue” in Britain. Have a copywriter familiar with regional dialects scrub through your copy to look for words, spelling, and colloquialisms that might not make sense for the area you’re targeting.
Identify unique regional concerns
Simply copying and pasting a campaign over to another region (even after a localization process) may not prove effective. Different areas of the world may have needs for unique services and varying behaviors as they engage with the sales funnel.
For instance, a cybersecurity company may see interest in DDoS-related services surge after a particular country experiences attacks. Or a ski supply store may see sales pick up as regions approach their colder seasons.
Finding these concerns should entail a combination of talking with your contacts within the business who have experience in the region, as well as researching search trends by month and by region. Google Trends can be helpful to pinpoint overarching seasonal trends.
For example, see below how searches for “heater” peak at opposite times of the year for the United States vs. Australia. If you’re selling heating units, you’ll obviously want to take into account the weather by region when marketing agency internationally.


Next, think about user behavior in different regions. I’ve found that in some cultures people are more responsive to talk to a salesperson sooner, while in others they may be more likely to want to simply read content first. You may need to refine your sales funnel and how much content you’re offering people at the top and middle of the process to see what works in each area.
This step may take some testing to determine what works best. At the end of the day, don’t assume that your perfectly refined funnel in one region will translate perfectly to another region.
Start planning your international campaigns
Ready to take the next step beyond marketing agency in your home country? Take these steps to build your plan for expanding into international PPC. Think through the nuances of the regions you’re targeting and the assets needed to adapt. Finally, be ready to watch the data and adapt your strategy on a regional basis as you begin to track performance.
Opinions expressed in this article are those of the guest author and not necessarily Search Engine Land. Staff authors are listed here.
About The Author

Tim Jensen is a campaign manager at Clix marketing agency. With over 8 years of experience in the digital marketing agency industry, Tim has worked with both B2B and B2C accounts in a wide variety of industries. While comfortable managing ads across all major platforms, he’s particularly intrigued with the crossover between analytics and PPC.
Website Design & SEO Delray Beach by DBL07.co
Delray Beach SEO
source http://www.scpie.org/5-tips-for-starting-international-ppc/
source https://scpie1.blogspot.com/2020/08/5-tips-for-starting-international-ppc.html
0 notes
Text
5 tips for starting international PPC
Expanding marketing agency efforts beyond your home country can be an exciting step. However, branching into new regions with PPC entails much more than simply copying your campaigns and changing the geographic targeting.
Don’t rush into setting up international campaigns until you’ve thought out budgeting, channel allocation, account structure, localization, and unique regional concerns. In this article, I’ll expand on each of these points to help you establish a framework for beginning to target other countries.
Budget for different costs by country
CPCs and CPMs to compete in ad auctions vary widely by country. You can get a rough estimate for projected spend in Google search by adding your keywords to Google Keyword Planner and setting the region to the country you’re planning to target. However, these estimates can be off, and you’ll get the best idea of average CPCs/CPMs once you actually start running a campaign and see actual figures.
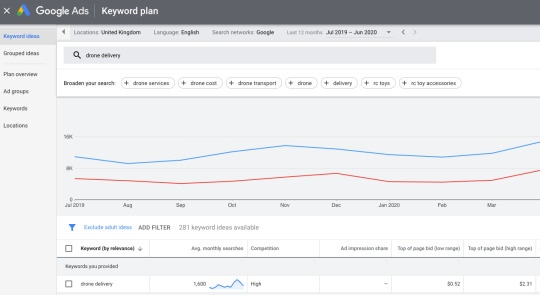
In addition, costs for customer acquisition also will likely vary by country. If you’re just starting to advertise in a region that’s not familiar with your brand, you can often expect higher CPAs.
However, you might find the opposite to be true if CPCs are lower in that region. I recently launched a LinkedIn campaign in Latin America for a client, and we found that CPAs were less than half of our averages in the United States due to significantly lower CPCs.
Also, pay attention to CRM data to measure lead quality. While they may be cheaper in a region, a lower percentage of prospects may actually be the right potential customers. You’ll ultimately want to look at metrics like cost per qualified lead and cost per completed sale to determine what CPAs to aim for in your campaigns.
Research top channels by region
Consider what search and social channels people use the most in the regions you’re looking to target. Targeting Google alone will exclude a significant number of users in several countries. For instance, Yandex covers 44% of the search engine market share in Russia, and Baidu has 66% of the market share in China.
StatCounter is a good site to start for research (with the caveat that no stats are going to be 100% accurate), as well as talking to contacts on the ground in regions you’re looking to target. Representatives at ad platforms may be able to assist in providing stats on regional usage, as well.
Plan for account structure
Separating campaigns by country, or by overarching region, allows you to better control bids and segment out reporting. This tactic also prevents countries with cheaper CPCs and high volume from cannibalizing spend, giving countries that may have higher CPCs, but quality leads, a chance to perform.
Separate geographic campaigns also allow for more accurate usage of time-based bid modifiers. If you lump the Europe and the US into the same campaign, and lower bids during the night in the US, you’re effectively also lowering bids during the workday in Europe. Keeping those regions in different campaigns allows you to apply hourly bid modifiers without worrying about hurting performance in time zones several hours away.
You should also consider billing needs when deciding how to segment out accounts. Particularly for enterprise-level companies, payment often needs to come from different divisions by region. Using separate ad accounts may be necessary to ensure you can use different billing sources for each division.
Include asset localization
Make sure to localize copy for the people you’re aiming to reach. This work may entail translating keywords, ad copy, and landing page copy into another language.
Or, you may be targeting people who already speak English but use different words based on regional dialects. For instance, if you’re selling diapers, you’ll want to refer to “nappies” when advertising in Britain. See how the wording on these example results pages vary for the same product category between Amazon US (“diapers”) and Amazon UK (“nappies”):
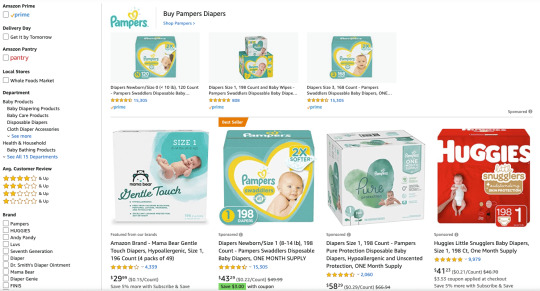
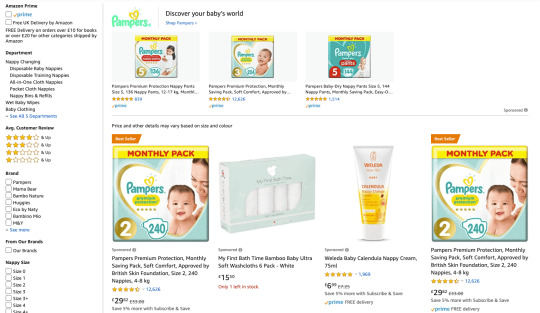
Be sure to adapt for regional spellings, as well. For instance, a call-to-action to “View Our Catalog” should say “View Our Catalogue” in Britain. Have a copywriter familiar with regional dialects scrub through your copy to look for words, spelling, and colloquialisms that might not make sense for the area you’re targeting.
Identify unique regional concerns
Simply copying and pasting a campaign over to another region (even after a localization process) may not prove effective. Different areas of the world may have needs for unique services and varying behaviors as they engage with the sales funnel.
For instance, a cybersecurity company may see interest in DDoS-related services surge after a particular country experiences attacks. Or a ski supply store may see sales pick up as regions approach their colder seasons.
Finding these concerns should entail a combination of talking with your contacts within the business who have experience in the region, as well as researching search trends by month and by region. Google Trends can be helpful to pinpoint overarching seasonal trends.
For example, see below how searches for “heater” peak at opposite times of the year for the United States vs. Australia. If you’re selling heating units, you’ll obviously want to take into account the weather by region when marketing agency internationally.
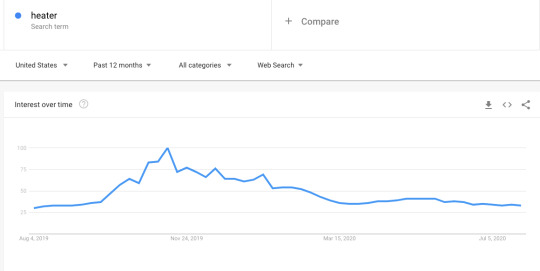

Next, think about user behavior in different regions. I’ve found that in some cultures people are more responsive to talk to a salesperson sooner, while in others they may be more likely to want to simply read content first. You may need to refine your sales funnel and how much content you’re offering people at the top and middle of the process to see what works in each area.
This step may take some testing to determine what works best. At the end of the day, don’t assume that your perfectly refined funnel in one region will translate perfectly to another region.
Start planning your international campaigns
Ready to take the next step beyond marketing agency in your home country? Take these steps to build your plan for expanding into international PPC. Think through the nuances of the regions you’re targeting and the assets needed to adapt. Finally, be ready to watch the data and adapt your strategy on a regional basis as you begin to track performance.
Opinions expressed in this article are those of the guest author and not necessarily Search Engine Land. Staff authors are listed here.
About The Author

Tim Jensen is a campaign manager at Clix marketing agency. With over 8 years of experience in the digital marketing agency industry, Tim has worked with both B2B and B2C accounts in a wide variety of industries. While comfortable managing ads across all major platforms, he’s particularly intrigued with the crossover between analytics and PPC.
Website Design & SEO Delray Beach by DBL07.co
Delray Beach SEO
source http://www.scpie.org/5-tips-for-starting-international-ppc/
source https://scpie.tumblr.com/post/625226700095143936
0 notes
Text
5 tips for starting international PPC
Expanding marketing agency efforts beyond your home country can be an exciting step. However, branching into new regions with PPC entails much more than simply copying your campaigns and changing the geographic targeting.
Don’t rush into setting up international campaigns until you’ve thought out budgeting, channel allocation, account structure, localization, and unique regional concerns. In this article, I’ll expand on each of these points to help you establish a framework for beginning to target other countries.
Budget for different costs by country
CPCs and CPMs to compete in ad auctions vary widely by country. You can get a rough estimate for projected spend in Google search by adding your keywords to Google Keyword Planner and setting the region to the country you’re planning to target. However, these estimates can be off, and you’ll get the best idea of average CPCs/CPMs once you actually start running a campaign and see actual figures.

In addition, costs for customer acquisition also will likely vary by country. If you’re just starting to advertise in a region that’s not familiar with your brand, you can often expect higher CPAs.
However, you might find the opposite to be true if CPCs are lower in that region. I recently launched a LinkedIn campaign in Latin America for a client, and we found that CPAs were less than half of our averages in the United States due to significantly lower CPCs.
Also, pay attention to CRM data to measure lead quality. While they may be cheaper in a region, a lower percentage of prospects may actually be the right potential customers. You’ll ultimately want to look at metrics like cost per qualified lead and cost per completed sale to determine what CPAs to aim for in your campaigns.
Research top channels by region
Consider what search and social channels people use the most in the regions you’re looking to target. Targeting Google alone will exclude a significant number of users in several countries. For instance, Yandex covers 44% of the search engine market share in Russia, and Baidu has 66% of the market share in China.
StatCounter is a good site to start for research (with the caveat that no stats are going to be 100% accurate), as well as talking to contacts on the ground in regions you’re looking to target. Representatives at ad platforms may be able to assist in providing stats on regional usage, as well.
Plan for account structure
Separating campaigns by country, or by overarching region, allows you to better control bids and segment out reporting. This tactic also prevents countries with cheaper CPCs and high volume from cannibalizing spend, giving countries that may have higher CPCs, but quality leads, a chance to perform.
Separate geographic campaigns also allow for more accurate usage of time-based bid modifiers. If you lump the Europe and the US into the same campaign, and lower bids during the night in the US, you’re effectively also lowering bids during the workday in Europe. Keeping those regions in different campaigns allows you to apply hourly bid modifiers without worrying about hurting performance in time zones several hours away.
You should also consider billing needs when deciding how to segment out accounts. Particularly for enterprise-level companies, payment often needs to come from different divisions by region. Using separate ad accounts may be necessary to ensure you can use different billing sources for each division.
Include asset localization
Make sure to localize copy for the people you’re aiming to reach. This work may entail translating keywords, ad copy, and landing page copy into another language.
Or, you may be targeting people who already speak English but use different words based on regional dialects. For instance, if you’re selling diapers, you’ll want to refer to “nappies” when advertising in Britain. See how the wording on these example results pages vary for the same product category between Amazon US (“diapers”) and Amazon UK (“nappies”):

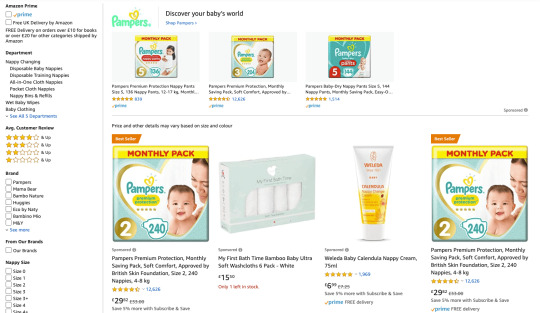
Be sure to adapt for regional spellings, as well. For instance, a call-to-action to “View Our Catalog” should say “View Our Catalogue” in Britain. Have a copywriter familiar with regional dialects scrub through your copy to look for words, spelling, and colloquialisms that might not make sense for the area you’re targeting.
Identify unique regional concerns
Simply copying and pasting a campaign over to another region (even after a localization process) may not prove effective. Different areas of the world may have needs for unique services and varying behaviors as they engage with the sales funnel.
For instance, a cybersecurity company may see interest in DDoS-related services surge after a particular country experiences attacks. Or a ski supply store may see sales pick up as regions approach their colder seasons.
Finding these concerns should entail a combination of talking with your contacts within the business who have experience in the region, as well as researching search trends by month and by region. Google Trends can be helpful to pinpoint overarching seasonal trends.
For example, see below how searches for “heater” peak at opposite times of the year for the United States vs. Australia. If you’re selling heating units, you’ll obviously want to take into account the weather by region when marketing agency internationally.
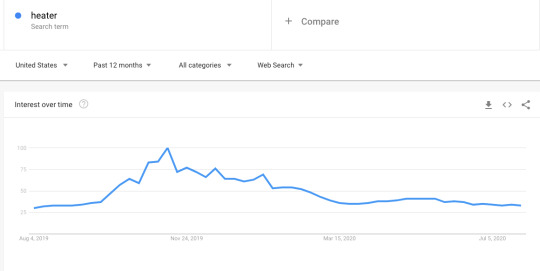
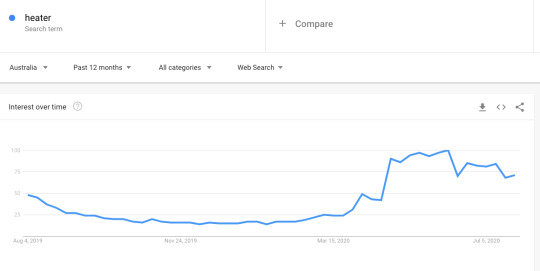
Next, think about user behavior in different regions. I’ve found that in some cultures people are more responsive to talk to a salesperson sooner, while in others they may be more likely to want to simply read content first. You may need to refine your sales funnel and how much content you’re offering people at the top and middle of the process to see what works in each area.
This step may take some testing to determine what works best. At the end of the day, don’t assume that your perfectly refined funnel in one region will translate perfectly to another region.
Start planning your international campaigns
Ready to take the next step beyond marketing agency in your home country? Take these steps to build your plan for expanding into international PPC. Think through the nuances of the regions you’re targeting and the assets needed to adapt. Finally, be ready to watch the data and adapt your strategy on a regional basis as you begin to track performance.
Opinions expressed in this article are those of the guest author and not necessarily Search Engine Land. Staff authors are listed here.
About The Author

Tim Jensen is a campaign manager at Clix marketing agency. With over 8 years of experience in the digital marketing agency industry, Tim has worked with both B2B and B2C accounts in a wide variety of industries. While comfortable managing ads across all major platforms, he’s particularly intrigued with the crossover between analytics and PPC.
Website Design & SEO Delray Beach by DBL07.co
Delray Beach SEO
source http://www.scpie.org/5-tips-for-starting-international-ppc/
0 notes
Text
Version 393
youtube
windows
zip
exe
macOS
app
linux
tar.gz
EDIT: This release had a hotfix two hours after initial release to fix the CloudFlare code. If you got it early, please redownload. The links are the same, the build is new.
I had a good week catching up on messages and small jobs. There is also a (hopefully) neat prototype solution for some cloudflare issues.
cloudflare and network
CloudFlare hosts content for many sites online. They have a variety of anti-DDoS tech, normally a variation on a 'is this a web browser?' test, that sometimes stops hydrus from downloading. If you have seen unexplainable 503 errors on a site that works ok in your browser, this may have been it.
This week, I am adding a library, cloudscraper, to my network engine to try to solve this. Now hydrus will attempt to detect CF challenge pages when they are downloaded and pass them off to this new library, which attempts to solve the javascript challenge (the part where a CF site sometimes says 'this process may take five seconds...', just as a browser would, and then copies the solved cookies back into the hydrus network session.
This first version can only solve the simple javascript challenges. It cannot do the more serious captcha tests yet, but this is a possible future expansion. I would appreciate any feedback from users who have had bad CF problems. If a page cannot be solved, or if your entire IP range had been flat-out blocked, hydrus should now attribute new CF-appropriate error messages.
For users who run from source, this library is optional. You can get it through pip, 'cloudscraper'.
Additionally, I am rolling in the very first basic version of 'this domain is having trouble' tech to my network engine. Now, if you keep having connection errors or CF issues with a site, hydrus recognises this and slows down access for a bit. The default is that no new network job will start as long as its site has had three serious errors in the past ten minutes, but you can edit this rule, including turning it off completely, under options->connection. Subscriptions will also try to wave off sites having trouble, just as if you had hit bandwidth limits. I expect to extend this system significantly in future, particularly by adding UI to see and manage current domain status.
the rest
The Windows build of hydrus is now on a newer version of python, 3.7 instead of 3.6. This makes for a variety of small background improvements all over the place, and some updated libraries, but may also introduce an odd bug here or there in more rarely used hydrus systems. Let me know if you run into trouble!
I did another round of file search optimisations on searches that do not have tag search predicates, such as bare system:rating or system:inbox queries.
Thanks to some excellent work by a user, there is another new DA parser. This one gets full-size images, video, flash, and even pdf! The only proviso is that it needs to be logged in to DA to get most content, otherwise it 404s. I believe the hydrus DA login script works, but if you have trouble with it, Hydrus Companion is always a good fallback.
The blacklist in tag import options gets a bit of work this week. It now tests unnamespaced rules against namespaced tags, so if you have a rule for 'metroid', it will also block 'series:metroid'. This is a special rule just for the tag import options blacklist (it also tests all siblings of the test tag), and to reflect it, the tag filter/blacklist edit panel now has a second 'test' text to show how the test input applies to a TIO blacklist, as opposed to a regular tag filter.
This is a small thing, but if you are mostly a keyboard user, the mouse now hides on the media viewer without having to be moved!
If you have had crashes trying to open a file or directory picker dialog, try the new BUGFIX checkbox under options->gui. It tries to use a different style of dialog that may be better for you.
full list
cloudflare and network:
the hydrus client now has an experimental hook to the cloudscraper module, which is now an optional pip module for source users and included in all built releases. if a CF challenge page is downloaded, hydrus attempts to detect and solve it with cloudscraper and save the CF cookies back to the session before reattempting the request. all feedback on this working/breaking irl would be welcome. current expectation for this prototype is it can pass the basic 'wait five seconds' javascript challenge, but only a handful of the more complicated captcha ones
if a CF challenge page is not solvable, the respective fail reason for that URL will be labelled appropriately about CloudFlare and have more technical information
.
the hydrus network engine now has the capability to remember recent serious network infrastructure errors (no connection, unsolvable cloudflare problem, etc..) on a per domain basis. if many serious errors have happened on a domain, new jobs will now wait until they are clear. this defaults to three or more such errors in the past ten minutes, and is configurable (and disableable) under options->connection. this will be built out to a flexible system in future, with per-domain options+status ui to see what's going on and actions to scrub delays
basically, if a server or your internet connection goes down, hydrus now throttles down to limit the damage
subscriptions now test if a domain is ok in order to decide whether they can start or continue file work, just like with bandwidth
serverside bandwidth alerts (429 or 509) are now classified as network infrastructure errors
I expect this system will need more tuning
.
the hydrus downloader system now recognises when an expected parseable document is actually an importable file. when this is true, the file is imported. this hopefully solves the situation where a site may deliver a post url or a file
.
the rest:
the windows build of hydrus is now in python 3.7.6, up from 3.6. this rolls in a host of small improvements, including to network stability and security (e.g. TLS 1.3), and possibly a couple of new bugs in more unusual hydrus systems
similarly, all the windows libraries are now their latest versions. opencv is now 4.2
greatly sped up several file searches that include no tags such as bare system:rating, most system file metadata predicates, or bare system:inbox, when the result size is much smaller than the total number of files in the file domain
thanks to some excellent work by a user, the Deviant Art downloader gets another pass--it can now get high res versions of images where they are available, and video, and flash, and pdf! the only proviso is that you need to be logged in to DA to get most content, otherwise you get 404. the current hydrus DA login script _seems_ to work ok
tag import options blacklists now test unnamespaced rules against namespaced tags. so if you blacklist 'metroid', a 'series:metroid' will be caught and the blacklist veto signal sent. this can be escaped with the 'advanced' exception panel, which now permits you to add 'redundant' rules
the edit tag filter panel now explains the blacklist rules explicitly and has a second 'test' green/red text to display test results for a tag import options blacklist, with the new sibling and namespace check
added some unit tests to test the new tag import options blacklist namespace rule
when 'default' tag import options are set, the edit panel now hides the per-service options, rather the the previous disable
the system tray icon now destroys itself when no longer needed, rather than hiding itself. it should now be more reliable in OSes that do not support system tray icon hide/show. if your OS still doesn't get rid of them, and you get a whole row of them, I recommend just leaving it always on
the system tray now has a tooltip with the main hydrus title and pause statuses
the timer that hides the mouse on the media viewer is now fired off when the window first opens (previously it would only initiate on the first mouse move over the window), so users who navigate mostly by keyboard should now see their cursors nicely hide on their own
added some semi-hacky import/export/duplicate buttons to edit shortcuts. I'll keep working on this, it'd be nice to have import/export for whole shortcut sets
added a semi-hacky duplicate button to the 'manage http headers' dialog
the 'clear' recent tag suggestions button is now wrapped in a yes/no dialog
a new checkbox under options->gui now lets you set it so when new cookies are sent from the API, or cookies are cleared, a popup message summarises the change. the popup dismisses itself after five seconds
the client api now also returns 'ext' on /get_files/file_metadata calls, just as a simpler alternative if the 'mime' is a pain
fixed a bug when petitioning tags through the client api, with or without reasons
fixed an error where subscriptions that somehow held invalid URLs would not be able to predict some bandwidth stuff, which would not allow the edit subs dialog to open
the string transformation dialog's step subdialog is now ok with example strings that are bytes. even then, this str/bytes dichotomy is an old artifact of python 2 and I will likely clean it up sometime so string transformers (and downloaders) only ever work utf-8 and hashes just work off utf-8 hex
added a BUGFIX checkbox to options->gui that tells the UI to use Qt file/directory picker dialogs, instead of the native OS one. users who have crashes on file selection are encouraged to try this out
updated running from source help with cloudscraper, a new pip masterline, and some windows venv info
the 'import with tags' button on 'import files' dialog gets another rename for new users, this time to 'add tags before the import >>'. it also gets a tooltip
handled an unusual rare error that could occur when switching out a media player inside a media viewer, perhaps during media viewer shutdown
next week
Next week is a cleanup week. I'd like to go into the tag autocomplete code and clean up how the input text is parsed and how results are cached and filtered. Otherwise, I'll do more wx->Qt cleanup and catch up on some small jobs.
0 notes