#biometric identification
Text
O.J. Simpson’s Twists of Fate: From Cancer Battles to Infamous Trials
In May 2023, O.J. Simpson shared a video on X (formerly known as Twitter), revealing that he had recently “caught cancer” and undergone chemotherapy. Although he didn’t specify the type of cancer, he expressed optimism about beating it. Fast forward to February 2024, when a Las Vegas television station reported that Simpson was once again receiving treatment for an unspecified cancer. In a…

View On WordPress
#AI News#biometric identification#case prediction#crime prevention#document analysis#ethical AI#facial recognition#forensic analysis#kaelin#kato#legal research#machine learning#News#nicole simpson#O.J. Simpson#predictive policing#ron goldman#sentiment analysis
0 notes
Text
In the realm of biometric security, our fingerprinting in College Park, Maryland, stands out as a marvel of modern science. This technology, deeply rooted in the unique patterns etched onto our fingertips, has evolved tremendously. Every individual carries a distinct set of prints, making fingerprinting a reliable and secure method of identification and authentication.
0 notes
Text
Alert EU folks! contact ur politicians they are looking to be really really dumb abt AI
0 notes
Text
Unveiling Tomorrow: The Evolution of Biometric Technology

Biometric technology refers to the automated recognition and authentication of individuals based on their physical or behavioral traits. Common examples include fingerprints, iris/retina scans, facial recognition, voice recognition, and even vein patterns. As technology continues advancing, biometrics are being integrated into more applications for convenient and secure identity verification.
The Growth and Evolution of Biometrics
The origins of biometrics date back over a century to the late 1800s when law enforcement began using fingerprints and facial photos for criminal identification. However, the past few decades have seen massive evolution and civilian adoption. Some key developments include:
1960s - First commercial biometric tech for fingerprint recognition
1970s - Voice recognition and iris scanning capabilities emerge
1980s/90s - Facial recognition and signature verification software introduced
2000s - Widespread integration into commercial devices and systems
2010s - AI and neural networks propel accuracy and versatility
Today biometric authentication is ubiquitous for everything from unlocking smartphones to passing border security. The global biometric market size is expected to grow from $45 billion in 2022 to over $125 billion by 2028.

Top Applications and Use Cases
Some top practical applications of biometrics include:
Government ID systems - e-passports, national IDs, voter registration
Law enforcement fingerprinting, face matching, and DNA analysis
Banking and financial services for fraud prevention and secure access
Smartphones, laptops, tablets that unlock via fingerprints or face scans
Airport security and border control including extensive biometric checks
Access control systems for facilities like data centers and laboratories
Healthcare organizations to control confidential records access

Cutting Edge Innovations
With constant improvements in sensor technologies and AI algorithms, the capabilities of biometrics are rapidly evolving. Some innovations gaining traction include:
Multi-modal systems combining multiple identifiers for better accuracy
Contactless biometrics like facial recognition or iris scans from a distance
Behavioral biometrics utilizing things like signature dynamics and gait
Expanded mobile applications leveraging built-in sensors
Emerging identifiers such as palm print, vein, and heartbeat recognition
Many expect biometric wearables integrated into clothing, accessories, and implants to eventually help facilitate frictionless interactions and commerce.
Challenges and Concerns
Despite the benefits, the expanded use of biometrics raises important challenges around ethics and privacy:
Mass surveillance and profiling risks from aggregated biometric data sets
Accurately balancing security with convenience and user experience
New spoofing and hacking vulnerabilities to protect against
Establishing strict controls and audit trails for internal users of data
Potential discrimination biases in underlying face/voice algorithms
Maintaining public trust and accentuating cybersecurity will be paramount as biometric prevalence grows. Carefully crafted policy and regulations can help guide responsible development.

The Future of Biometric ID
Many envision a future with biometrics seamlessly authenticating us for daily services ranging from mass transit to retail payments. Our physical identifiers could eliminate remembering passwords, showing ID cards, carrying keys, and more. This will ultimately depend on the technology proving highly reliable, and secure and addressing the ethical pitfalls around privacy erosion. If these conditions are met, biometrics could one day enable frictionless access control and transactions integrated into background processes.
#biometric technogy#biometrics#technology#biometric authentication#biometric identity#biometric verification#biometric identification#face recognition#tech blog#tumblr
1 note
·
View note
Text
Four Security Themes to Keep in Mind this Cybersecurity Awareness Month

October is Cybersecurity Awareness month, and it is the best time for organizations to assess their current identity, access management, and authentication methods. This celebration emphasizes the importance of a company’s overall protection. And this is achieved by consistently improving cybersecurity strategies.
Through the years, several security themes have emerged that influence how people interact in cyberspace. Organizations should reflect upon these for their advantage. This year’s themes include human vulnerabilities, passwordless logins, ethics in biometric identification, and the expansion of the Zero Trust program.
Human Vulnerabilities
Human input has often been regarded as a risk for cybersecurity. Cybercriminals use this aspect to penetrate the security of organizations. This can be through appealing to people’s emotions or abusing their lack of awareness.
Human vulnerabilities can be intentional or unintentional. The former refers to direct action to access, modify, or remove data to steal from or sabotage an organization. It could include installing malicious software that compromises the company’s cybersecurity or stealing valuable information from the company’s database.
Unintentional vulnerabilities are caused by human error. They are often the results of negligence, inattention, or lack of education. Mistakes from operators can quickly become an opportunity for a bad actor to harm the organization.
How Cyber Criminals Exploit Human Vulnerabilities
Digital systems still require human intervention. Because of this, systems are susceptible to error. Human vulnerabilities are responsible for about 82% of data breaches in 2022.
Cybercriminals conduct intensive surveillance to uncover vulnerabilities in an organization’s security measures. Human errors or weak systems are examples of qualities that these individuals wish to discover. After thorough research, cyber attackers create plans to exploit the natural tendency of humans to trust. This cyber attack is called social engineering.
Social engineering is centered on manipulating human emotions to breach security. This is done through intense preparation, interaction with vulnerable individuals, exploitation of their information or authority, and exit after committing the attack.
For instance, Uber was recently a victim of a multi-factor authentication (MFA) social engineering attack on and smishing scheme. The hacker was able to acquire the employees’ passwords, giving them access to the company’s systems, including their Duo, AWS, and Google Workspace.
Aside from appealing to human emotion, the following aspects expose an organization’s security to cyber attacks:
Weak passwords
Insecure or outdated operating systems
Lack of maintenance
Inexperienced operators
Visiting or downloading from unsecured sites
Negligence in signs of attacks
Failure to act promptly against malware and viruses
Dishonest or negligent employees
With the rising number of security breaches throughout the years, implementing FIDO authentication can prevent attacks. Passwordless authentication lessens the risk of human vulnerabilities. Companies can make identity verification more seamless and effective by removing the issues that passwords pose, such as recalling and resetting them.
Organizations can strengthen their cyber security efforts by constantly learning to improve their existing identity verification, authentication, and access management methods. Read an in-depth discussion of the four security themes companies should keep in mind this cybersecurity awareness month by checking out this blog post by authID.
0 notes
Text
Neurotechnologies and Transhumanism : The Big Fraud Towards Digital Slavery
Decoding of Brain’s Visual Cortex – paper
The Brain is responsible for Cognition, it is the support of Thought and Mind. The reality we’re experiencing depends on its electrical activity which can be analyzed and manipulated.
Remote Neuromonitoring and Neurostimulation currently allow the extraction and manipulation of sensory perceptions and associated mental processes and emotions using…
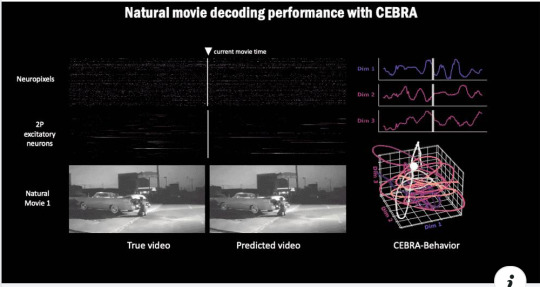
View On WordPress
#000 DRONES APPROVED BY CONGRESS#1984#9/11#A New Breed - Satellite Terrorism#Aaron Alexis#ABIS#Allan Frey#Artificial Telepathy#audio surveillance#Authomated Biometric Identification System#barcode tattoo#big brother#BIMA#Biometric Identify Management Activity#biometric surveillanc#active denial system
3 notes
·
View notes
Text
What are Biometrics?
Since the 1980s, biometrics has been used in fingerprint identification. When comparing collected fingerprints from crime scenes to registered fingerprints of persons in databases, automated fingerprint identification systems (AFIS) assist investigators.
(more…)

View On WordPress
#biometrics#biometrics and forensic science#how safe is biometric identification#what are biometrics#what are biometrics characteristics#what are the types of biometrics#what are the uses of biometrics#what is the example of biometric security#what is the uses of biometrics in forensic science
2 notes
·
View notes
Text
Forensic Fingerprints Analysis Demystified: Techniques, Trends, and Technologies
In the intricate dance of forensic science, forensic fingerprints analysis stands as a cornerstone, shedding light on the unseen trails left behind at crime scenes. This profound method of investigation has not only bolstered criminal investigations but has also significantly contributed to the realms of law enforcement and biometric security. The unique patterns of whorls, loops, and arches…

View On WordPress
0 notes
Text
Security 2.0: Unlocking the Power of Cutting-Edge Intelligent Identification Solutions
Keeping up with security updates is essential for protecting sensitive data in an era where identity theft and data breaches are on the rise. We are pleased to present our state-of-the-art Intelligent Identification Solution, a security solution that goes above and beyond traditional techniques. Our solution offers a strong and flexible identification framework by utilizing modern machine learning and artificial intelligence technologies. Our intelligent identification solution ensures unbreakable security for both individuals and companies by evolving and adapting to emerging threats. To know more visit us at :- https://idefy.ai/id-verification/
#Intelligent Identification Solution#biometric identity verification software#customer identification verification#identity verification document
0 notes
Text
Realizing the need for a unified digital identity framework, the government enacted the Aadhaar Act in 2016 to provide legal backing to the Aadhaar digital ID system. This allowed the collection of biometric data and assigning a unique ID number to every citizen - laying the groundwork for seamless service delivery.
0 notes
Text
Technology has become a crucial ally in the quest for accuracy, efficiency, and public safety in the ever-evolving landscape of law enforcement. At the forefront of this technological revolution is a powerful tool that plays a pivotal role in modern law enforcement practices.
0 notes
Text
The Global Automotive Biometric Identification System Market is projected to grow at a CAGR of around 22% during the forecast period, i.e., 2023-28.
0 notes
Text
#authentication#security#cybersecurity#technology#identityauthentication#encryption#datasecurity#privacy#identification#biometrics#biometricsecurity#fingerprint#software#computersecurity#securitysystem#digital#accesscontrol#authenticationservices#phonesecurity#voiceidentification#biometricsafe#fingerprintsecurity#tech#eyeidentification#biometric#fingerprintid#passwordsecurity#informationsecurity#securitysoftware#computersecurityday
0 notes
Text
Ethical Biometrics High Road Should Be Easy, Yet Many Identity Service Providers Struggle

As the use of biometrics increases and governments look for ways to control the use of this technology, questions of privacy and surveillance surface. The risks are compounded by the lack of standards, adequate policy protections, ecosystem collaboration, and a general lack of awareness and understanding of biometrics. Once the technology leaves the realm of technologists, these questions will become public policy debates and questions of corporate responsibility.
Biometrics are fundamental elements of modern digital identity verification systems. As governments and service providers use biometrics to reduce fraud and other problems, the need for solid data protection is paramount. But this is also a difficult road to travel since biometric data is irreversible and cannot be reset by third parties.
Biometrics offer numerous advantages. Its security is enhanced by combining multiple factors, making it difficult for bad actors to duplicate or hack. It also creates less friction for end users. This makes biometrics a popular choice for companies in a variety of sectors. While biometrics is increasingly popular technology, there are concerns that this new technology has the potential to undermine privacy. Busing biometric data can pose privacy risks, especially when the data is transferred to a central database. Those concerns are heightened because biometrics will soon extend far beyond human health. For instance, security researchers demonstrated that 3D printing could be used to compromise fingerprint scanning technology.
Biometrics has many advantages, but there are also ethical considerations. The first concern is that biometrics are not foolproof. The data may be compromised or misused by service providers or fraudsters. This data could be interconnected with other files or processed in ways not agreed upon by the citizen.
The second concern is the use of biometric data for commercial purposes. These systems would use biometric data to track and profile individuals. However, it is critical to understand such applications' social and cultural contexts before implementing them. Failure to consider these issues can degrade the systems' efficacy and lead to serious unintended consequences.
Biometric identification has many advantages, including increased security and convenience. But it also has several security and privacy risks. In addition to being difficult to hack, biometrics are hard to replicate by bad actors, which means they're not easy targets. Furthermore, they reduce friction for the end user. These are the reasons why companies across various sectors are exploring biometric interfaces as an alternative to traditional authentication methods.
You can read this helpful blog if you want to know more why many identity service providers still struggle despite of the fact that ethical biometrics high road should be easy to practice.
1 note
·
View note
Text

The E-passport Market size was valued at USD 22.50 billion in 2021 and is predicted to reach USD 88.90 billion by 2030 with a CAGR of 21.7% from 2022-2030.
#E-Passport Market#Radio Frequency Identification#Biometrics#Facial Recognition#Fingerprint Recognition#Iris Recognition#Hardware#Antenna#Processor/Chip#Software#Services#Leisure Travel#Business Travel#Basic Access Control (BAC)#Password Authenticated Connection Establishment (PACE)#Supplemental Access Control (SAC)#Extended Access Control (EAC)#Ordinary E-passport#Service#Diplomatic E-Passport
0 notes