#Trust and Security with SOC 2
Text
Daughter of the shadows Ch. 5
Word Count: ~1.5k
Warnings: subtle mention of human tr*****, Non-canon events(?), bittersweet goodbye,not proofread, let me know if I forgot something.
Author's Note: Fifth chapter to my Grishaverse fanfic. I know Inej canonically leaves after the events of Crooked Kingdom, or at the end of season two on the show. But trust me it’ll make sense in the future, please don’t be mad at me.
Also sorry for the late update, I was celebrating Easter with my family.
A reminder this is insipred by my SoC DR so it’ll follow both the books and the show plotlines, there will be changes to the canon characters and their storylines, it’s also a Kaz Brekker x OC. | English isn’t my first language so please bear with me and tell me if there’s something wrong. I hope you like it.
all rights to leigh bardugo, i only owny liith and her backstory (other ocs will be introduced later)
Ch. 1 - Ch. 2 - Ch. 3 - Ch. 4 - Ch. 6

CHAPTER 5
LILITH
It had been a few weeks since she had been wounded, the brunette knew Kaz needed her, though he would never admit it.
The usual dangerous and violent jobs that had become a daily part of her life had been entrusted to Inej, leaving Lilith to guard the door of the Crow Club, the bar of the club or simply to sort out paperwork in the boss's office.
The late autumn sun woke her as it filtered through the window above her, the enforced rest and sedentary work that had filled the last few weeks had allowed the girl's wound to heal leaving only a white scar.
Lilith looked at herself in the mirror, her body like a map, a pale canvas covered in even paler lines, the scar that cut across her lips was white in contrast to the red of her lipstick, the numerous scars on her arms that cut across the two tattoos reminded her of some of the worst moments of her life, the scar on her side was just an addition to her story, something to be proud of, something to remind her of how strong she was and how many nightmares she had woken up from stronger than before.
She wore a black sweatshirt covering her story; sure she was proud of every single scar she had on her body, but she wouldn't show them to anyone, they were her past, her story, her life, her memories and no one else's, she didn't demand anyone's pity and she knew it would come if she showed them.
She covered her right hand with the leather glove, secured the knives in their sheaths, feeling the heat in the handles before leaving the room and closing the door behind her.
The corridors were silent, her colleagues' rooms were closed, occupied by Dregs either fast asleep or busy enjoying their morning off; she descended the last few steps, the room in front of her, usually full and noisy was empty and quiet, the only people in the room were the younger Dregs who did not yet have the privilege of Sunday off.
"Dirix remember to clean under the table in the council room." Said Lilith looking at the younger one from the stairs, "I don't envy you Dir, at least you didn't witness the scene though." yelled Brawen from behind the counter, "Brawen the toilets on the first floor need to be cleaned." said Lilith to her with a half smile, "But I cleaned them last week, today was supposed to be Pim's turn." complained the blonde walking towards the storage room, "Pim is running errands for Specht." explained Lilith simply before walking out the door leaving the room behind.
The salty air filled her nostrils as Lilith sat on the dock of the seventh harbour, the only abandoned harbour, she fixed her gaze on the sea ahead, the blurry shadow of Hellgate in the distance ready to remind her where she would be sent if they found out who she was, what she had done to survive and how she had come to Ketterdam.
Somewhere across the expanse of water her family was looking for her, she could feel it, she knew they would never stop looking for her, but she knew she could not return to them.
"We will see each other again soon." A man's voice rang like an echo in the girl's mind, she could not remember his face, every detail of the man had disappeared from her memory, every detail except the last sentence addressed to her. It was a promise, he had promised her that they would see each other again, that they would be together again, but years had passed and that promise had been broken.
She could feel his hand gently caressing her cheek, a pure cheek, porcelain white skin marred only by tiny mahogany flecks, tears had overcome the child's resistance and fell freely onto her white cheeks, the man's thumb wiped them away as a father wipes away a daughter's.
The man's calloused but gentle hand brought her back to that day, she had left everything behind, forgetting who she was, hiding who she had been, becoming yet another soul lost to the corruption of society and the violence of the world she lived in. Everything she had had during her childhood, everything she had studied, everything she had been taught was now something Lilith would never want to talk about, she had discovered the truth too late to continue living the way she had grown up, too soon to be able to change her future and that of others.
"We will see each other again soon." Whispered Lilith to the sea, the promise echoed on the waves of the sea before disappearing into the horizon.
Her footsteps echoed before her feet touched the dock, the girl's gaze was fixed on the blue expanse before her, in the distance a few ships could be seen, she could not see who was working on them but part of her knew that one of those ships was the one that had brought her to that city, that had brought Inej, Brawen, Pim and hundreds of other kids to that city forgotten by the Saints.
"Will you feed my crows?" Inej asked as she sat down next to Lilith, her legs crossed in front of her, the handles of the daggers glistened in the afternoon sun, Lilith's gaze shifted from the sea to the Suli beside her, the brunette knew she was beautiful, that she had all the qualities a boy could ever want in a mate, but not only did she not care about boys, sure she had had her experiences but she would never want to feel trapped in someone else's shadow, she had decided to be free, to choose herself, her heart had no place for another person, but all the confidence she had disappeared the moment Inej entered the room, her optimism, her determination, her faith, everything about the girl made Lilith wonder if she was enough.
The sun shone on the Suli's caramel skin, her black hair was perfectly arranged in a ponytail, even with the wind blowing in from the sea it didn't move, her brown eyes shimmered reflecting the sea water below, her lips slightly open to inhale the salty air were soft, a brilliant colour without the need for chemical or grisha aids.
"Can I count on you?" The Suli asked again, shifting her gaze to the younger one, "Why can't you?" the brunette asked, "Because I don't know when I'll be back." "You'll come back from where?" "Kaz finished paying Tante Helleen..." "You're free..." "And he found a boat, not as big as those, but big enough to let me set sail with a small crew." "When do you leave?" "Tonight, after the eleventh bell." "How long have you known?" "A few weeks, just long enough to find the boat and crew, I wanted to tell you but with everything that's happened I didn't want to make you feel worse." Lilith smiled at the Suli, she knew this moment would come from the moment she had met her, it shouldn't have been a surprise and yet the brunette was at a loss for words, Inej had been the first girl she had met in Ketterdam, since the first time they met she had been the person Lilith had shared the most with and she knew she would miss her.
"I will feed them, don't worry. Promise me one thing, kill the bastards who brought us here for me." "I will make them pay." Inej said, smiling before hugging Lilith.
They both knew Inej would leave without saying goodbye to anyone and Lilith would be too busy with the Crow Club to greet her as she would have liked, but sitting there, legs dangling, hands intertwined, eyes fixed on the horizon and daggers at the ready was what they needed, something familiar and habitual before the change Inej's departure would bring.
"Inej." Lilith broke the silence by moving her hand from her friend's and bringing it towards the sheath attached to her thigh, pulling out a knife and handing it to the Suli, "I want you to have it, a reminder that you will always have someone to return to here." Inej studied the dagger, the black handle had red inserts extending to the blade, a design unknown to Inej covered part of the blade, "Lils..." "Please remember me when you use it." "I will.” The older girl brought the dagger towards her belt drawing one of her own before securing it in it, "Sankta Lizabeta, I know you do not follow faith but we know we both could use their help and blessing.” The dagger was light in Lilith's hands, lighter than her own, she knew why and she knew that the one she had given to Inej had been forged from the same metal, while the others had been forged especially for her, the handle was white, contrasting with the black blade.
The two girls remained on the dock until the sun went down, in silence, each lost in their own minds, until the eighth bell rang, their steps were silent, their movements almost imperceptible, "Don't die." Said Lilith to Suli hugging her, "Don’t perish." replied Inej breaking the embrace and walking towards the harbour.
Towards her boat.
Towards her future.

Tag list: @awkwardbean4337 @pansexualwitchwhoneedstherapy
#Grishaverse#grishaverse fanfiction#The Grisha Trilogy#grisha netflix#six of crows#six of crows fanfic#Kaz Brekker#kaz brekker x oc#kaz brekker x reader#kaz brekker x fem!reader#kaz brekker x y/n#inej ghafa#jesper fahey#matthias helvar#nina zenik#lilithzenik#my oc#my oc story#shadow and bone#Shadow and Bone trilogy#shadow and bone netflix#shadow and bone season two#shadow and bone fanfiction#six of crows duology#crooked kingdom#ari writes
28 notes
·
View notes
Text

Do you trust Security Certifications
Do you trust security certifications when acquiring SaaS/PaaS solutions? Do you accept SOC 2, HIPAA, ISO 27001, PCI-DSS, GDPR certifications as evidence of secure practices and, perhaps, quality? If you see a vendor is certified, do you still ask your own questions and request evidence?
Check out the article here:
2 notes
·
View notes
Text
4 ways to advance your global security operations center - CyberTalk
New Post has been published on https://thedigitalinsider.com/4-ways-to-advance-your-global-security-operations-center-cybertalk/
4 ways to advance your global security operations center - CyberTalk


EXECUTIVE SUMMARY:
If your organization maintains a Global Security Operations Center (GSOC), ensure that you’re not heavily reliant on legacy systems and processes. In this article, find out about how to strategically advance your operations, enabling you to effectively prevent threats and drive more sustainable business outcomes.
What is a global security operations center?
In the early days of computing, a Security Operations Center (SOC) functioned as a physical ‘command center’ for security analysts. SOCs were comprised of rooms where staff sat shoulder-to-shoulder, looking at screens showing details from dozens of different security tools.
Large organizations with multiple Security Operations Centers (SOCs) began to consolidate them into Regional Security Operations Centers (RSOC) or a Global Security Operations Center, leading to faster remediation, reduced risk and a stronger cyber security posture overall.
In terms of function, a global security operations center monitors security, addresses threats before they become disruptive issues, responds to incidents, and liaise with stakeholders.
What are the benefits of a global security operations center?
A global security operations center allows an organization to contend with diverse security threats at-scale. Specific benefits include continuous monitoring, centralized visibility, increased efficiency and reduced costs. A global security operations center can also oversee and coordinate regional SOCs, network operations centers (NOCs) and operational teams.
What makes a good global security operations center?
For any global security operations center, access to timely and relevant threat intelligence is critical. GSOC staff need to remain updated on emerging cyber and physical security threats, as to stay ahead of potential risks.
Highly trained staff who can collaborate effectively with all stakeholders are also invaluable assets for a global security operations center.
Top-tier GSOCs have built-in redundancies of all kinds; from communication to data backups.
All GSOCs need to ensure that their organization adheres to industry regulations and compliance standards.
4 ways to advance your global security operations center
1. Ensure that the cyber security strategy aligns with business objectives. GSOCs need to know what the business aims to achieve, and must understand the corresponding threats and vulnerabilities that could hamper progress. Risk assessments should include both cyber security and business stakeholders, who can assist with the identification of resources that require protection.
Security policies and standards should also meet customer expectations. To gain insight around this, cyber security leaders may wish to join business planning meetings. Attendance can also assist with awareness around any upcoming business changes and implementation of appropriate, corresponding security measures.
2. Global security operations centers should shift towards the zero trust model. Zero trust is designed to reduce cyber security risk by eliminating implicit trust within an organization’s IT infrastructure. It states that a user should only have access and permissions required to fulfill their role.
Implementation of zero trust can be tough, especially if an organization has numerous interconnected and distributed systems. Organizations can simplify zero trust implementation through vendor-based solutions.
Tools like Quantum SASE Private Access allow teams to quickly connect users, sites, clouds and resources with a zero trust network access policy. In under an hour, security teams can apply least privilege to any enterprise resource.
Security gateways also enable organizations to create network segmentation. With detailed visibility into users, groups, applications, machines and connection types, gateways allow security professionals to easily set and enforce a ‘least privileged’ access policy.
3. Advance your global security operations center by mapping to industry standards and detection frameworks. Explore the MITRE ATT&CK framework. Standards like NIST and ISO27001 can also assist with identifying and reconciling gaps in an organization’s existing security systems.
4. Consider deploying a tool like Horizon SOC, which allows organizations to utilize the exact same tools that are used by Check Point Security Research, a leading provider of cyber threat intelligence globally.
Horizon SOC offers 99.9% precision across network, cloud, endpoint, mobile and IoT. Easily deployed as a unified cloud-based platform, it has powerful AI-based features designed to increase security operations efficiency.
Further thoughts
Strategic updates to global security operations centers not only enhance cyber security, they also enrich overarching business resilience – an increasingly common point of discussion among C-level stakeholders and the board.
By implementing the suggestions outlined above, organizations will maximize their opportunities for business longevity and continued business success.
Related resources
#ai#amp#applications#Article#assets#awareness#backups#board#Business#business resilience#c-level#Check Point#Cloud#clouds#collaborate#command#communication#compliance#computing#consolidation#continuous#cyber#cyber security#cyber security strategy#cyber threat#data#details#detection#efficiency#endpoint
2 notes
·
View notes
Text
How SOC 2 Certification Secures Your Business

SOC 2 Certification in New York, a vital assurance for businesses handling sensitive data, is gaining prominence in New York's bustling commercial landscape. Recognized as a gold standard for service organizations, SOC 2 compliance ensures robust controls over security, availability, processing integrity, confidentiality, and privacy. In a data-driven metropolis like New York, achieving SOC 2 certification underscores an organization's commitment to safeguarding client information and maintaining operational excellence. With an emphasis on transparency and trust, SOC 2 compliance not only mitigates risks but also enhances competitiveness, instilling confidence in partners and customers alike. In New York's dynamic business ecosystem, SOC 2 certification stands as a testament to adherence to rigorous industry standards.
The Strategic Benefits of SOC 2 in New York City
Enhanced Data Security: SOC 2 Services in Netherlands compels organizations to implement robust security measures, leading to better data protection and reduced risk of breaches. This translates to increased confidence for both your business and your clients.
Increased Customer Trust: Demonstrating SOC 2 compliance builds trust and confidence among customers and stakeholders. This independent verification fosters long-term relationships and attracts new business opportunities.
Competitive Advantage: In the competitive New York market, SOC 2 Certification can be a unique selling point that sets your organization apart. It showcases your commitment to data security and compliance, potentially influencing contract wins and partnerships.
Regulatory Compliance: SOC 2 compliance often aligns with various industry regulations and compliance requirements. This streamlined approach simplifies the compliance process and reduces the burden of managing multiple regulations.
Balancing Security with Budget in SOC 2 Certification in New York
SOC 2 Cost in Maldives can vary depending on factors such as the size and complexity of the organization, the chosen auditing firm, and the scope of the assessment. Generally, expenses may include consulting fees for preparing for the audit, auditing fees charged by the certified public accounting (CPA) firm conducting the assessment, and any remediation costs to address identified gaps in compliance. On average, the total cost for SOC 2 certification in New York typically ranges from several thousand to tens of thousands of dollars. However, the investment is crucial for ensuring regulatory compliance and bolstering trust among clients and stakeholders.
The SOC 2 Audit Process for New York City Businesses
Gap Analysis: This initial phase involves a thorough assessment of your organization's current data security practices and controls. The aim is to identify any areas where your systems may not fully meet the SOC 2 requirements. This helps you prioritize and address any necessary improvements before the formal audit.
System and Process Documentation: Compiling detailed documentation of your data security policies and procedures is crucial. This includes security protocols, access controls, data backup procedures, and incident response plans. Clear and comprehensive documentation is essential for the auditors to understand your security posture.
Internal Controls Testing: Once controls are implemented and documented, they are rigorously tested to ensure their effectiveness. This involves simulating potential security threats and verifying that your controls adequately mitigate risks and protect sensitive data.
Auditor Review and Reporting: Following the internal controls testing, an independent third-party auditor will review your documentation, test controls, and assess your overall compliance with SOC 2 standards. Based on their findings, they will issue a SOC 2 report, either a Type 1 or Type 2, depending on the chosen scope of the audit.
How to get soc 2 Consultants in New York ?
Kindly email [email protected] with any questions you may have regarding SOC 2 Certification Services in Delhi. For more details on SOC 2 Certification in New York, visit www.b2bcert.com, our official website. At B2Bcert, we specialize in developing solutions that fully benefit your company while satisfying its demands. Our team of specialists is committed to guiding you through Yemen's legal system and selecting the most sensible and economical path to SOC 2 Certification.
0 notes
Text
Dell Boomi Advantages

Unlocking Integration Power: The Key Advantages of Dell Boomi
In the fast-paced business world, seamlessly connecting disparate systems, applications, and data sources is more crucial than ever. Enter Dell Boomi, a cloud-based integration platform (iPaaS) service that acts as the connective tissue within your technology ecosystem. Let’s explore the compelling advantages that make Boomi a top choice for organizations seeking to streamline operations and unlock new levels of efficiency.
1. Ease of Use and Speed
Intuitive Interface: Dell Boomi boasts a user-friendly, visually oriented, drag-and-drop interface that simplifies the integration process, even for those without extensive coding expertise.
Pre-built Connectors: A vast library of pre-built connectors for popular applications and systems expedites the development and deployment of integrations, saving you valuable time and resources.
Low-Code Environment: Boomi empowers users to create complex integrations with minimal coding required, making this platform accessible to a broader range of professionals.
2. Flexibility and Scalability
Hybrid Deployment: Dell Boomi can be deployed in the cloud, on-premises, or in a hybrid model, granting you the flexibility to choose the configuration that suits your business needs.
Scalability to Match Growth: Boomi’s architecture effortlessly scales to accommodate your changing business requirements. This means smoother handling of increased data volumes and more complex integration scenarios as your organization grows.
3. Intelligent Guidance and Community Support
Crowd-Sourced Knowledge: Boomi’s “Boomi Suggest” feature taps into the collective wisdom of its large user base, providing recommendations and best practices for data mapping and integration design.
Supportive Community: Leverage the power of a robust community of Boomi users and experts. Find solutions, share knowledge, and collaborate with others facing similar integration challenges.
4. Robust Data Management
Data Quality Assurance: Dell Boomi includes built-in features to ensure the integrity and accuracy of your data through validation, cleansing, and transformation capabilities.
Master Data Management (MDM): Boomi’s optional MDM component allows you to establish a central repository of trusted data, enhancing consistency and decision-making across the organization.
5. Comprehensive Security
Compliance: Dell Boomi maintains compliance with industry-standard security protocols like SOC 2, HIPAA, and GDPR, giving you peace of mind when handling sensitive data.
Access Control: Granular access control features enable you to manage user permissions meticulously, protecting your integration processes.
Dell Boomi in Action: Real-World Benefits
Accelerated Time-to-Value: Simplify integrations, leading to faster implementation of critical business processes and shorter time to realize positive returns on investment.
Reduced Operational Costs: This will minimize the need for manual interventions and costly custom coding, freeing up resources for more strategic initiatives.
Improved Customer Experiences: Connect front-end and back-end systems for a unified view of customer data to deliver seamless experiences across touchpoints.
Enhanced Agility: Quickly adapt to changing business needs by rapidly creating and modifying integrations.
Is Dell Boomi Right for You?
Dell Boomi is a strong contender if you’re looking for a robust, user-friendly, and scalable integration platform to connect your applications, streamline data flow, and drive digital transformation. Its low-code approach, versatility, and robust feature set make it an ideal choice for businesses of various sizes and industries.
youtube
You can find more information about Dell Boomi in this Dell Boomi Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for Dell Boomi Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Dell Boomi here – Dell Boomi Blogs
You can check out our Best In Class Dell Boomi Details here – Dell Boomi Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
0 notes
Text
Empowering Secure Operations: The Importance of SOC 2 Certification in India
Cyber security has become a main issue for digital businesses to look after. Due to the constant growth of cyber threats, organizations don't have any other option than to use and adopt robust security measures in order to protect their data and not harm the customer's trust. SOC 2 Certification is becoming famous in India, where data privacy and security are supreme concerns.
Grasp of SOC 2 Compliance
SOC 2 compliance is a service that is supervised by the American Institute of Certified Public Accountants (AICPA) and is a context made to look after the efficiency of an establishment's intel control that is connected to security and privacy. SOC 2 is dissimilar from SOC 1, which points to financial information.SOC 2 Certification in India emphasizes technology and online computation, making it valid for a lot of businesses that are being done online.
Why Indian Businesses Need SOC 2 Certification
Here are a few reasons why Indian businesses need SOC 2 certification:
• Enhanced Security Posture and Data Protection
SOC2 certification makes it clear that organizations must have good security measures to protect their privacy and sensitive data from unwanted cyber attacks. It increases the confidence of customers to invest more.
• Building Trust & Credibility with Clients and Partners
SOC 2 focuses on securing data from unwanted threats, which is important for a business to build up trust with its partners and clients.
• Increased Competitive Advantage in the Marketplace
It ensures and signals clients that their company has required security standards.
• Improved Operational Efficiency and Risk Management
It assists in recognizing and addressing security gaps, leading to better risk management.
Deciding the Correct SOC 2 Type (Type 1 vs. Type 2) for Your Needs
The organization needs to select amongst Type 1 or 2 reports. The choice hinges on the organization's need and the level of honor needed by the client. Soc 2 type 1 certification analyzes the strategy of control at a specific time, whereasSOC 2 Type 2 Certification looks at the usefulness of these controls.
Streamlined SOC 2 Audit & Certification Process in India
SOC 2 Compliance can be obtained with ease due to the increased demand for cybersecurity compliance. Firms that are experts in SOC 2 can guide organizations throughout the process, from assessments to final audits and reports. In India, as cyber security threats continue to increase, businesses are recognizing the importance of SOC 2 compliance to demonstrate their commitment to data security and privacy. With the growing demand for SOC 2 certification, specialized firms equipped with deep expertise in regulatory frameworks and cyber security practices have emerged to streamline the audit process for organizations.
Conclusion SOC 2 certification plays a great role in securing Indian business. Contact Univate Solutions as they offer businesses a great service to protect against several threats that can be harmful to overall business. Take action today to safeguard your customer data and ensure your business remains resilient against cyber threats by partnering with Univate Solutions for SOC 2 certification. In today's digital era, investing in SOC 2 certification compliance through services offered by Univate Solutions is a strategic decision that can safeguard the future of Indian businesses.

0 notes
Text
Secure Your Business Partnerships with OnGrid's Vendor Due Diligence Solutions
Elevate your business confidence and safeguard against risks with OnGrid's Vendor Due Diligence Solutions. With a track record of verifying over 100K vendors and serving 3000+ satisfied clients, we are your trusted partner in due diligence. Our advanced AI-powered models undergo continual audits and evaluations, ensuring precision and accuracy in vendor assessments. Committed to compliance and security, we hold ISO certification and SOC 2 Type II compliance, prioritizing data protection and regulatory adherence.
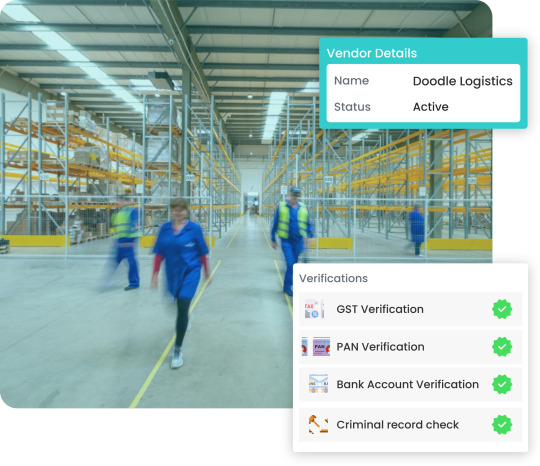
Driven by subject-level experts, we provide comprehensive assessments tailored to your business needs. Our technology stack seamlessly scales with your volumes, delivering swift processing without compromising accuracy. Enjoy cost-effective solutions tailored to your budget, with rapid turnaround time and insightful reports for informed decision-making.
Choose OnGrid for basic due diligence, company health checks, criminal record checks, field audits, credit history checks, and directorship checks. Trusted by top brands for vendor onboarding, join us in enhancing your business confidence with OnGrid's Vendor Due Diligence Solutions.
#VendorDueDiligence#BusinessConfidence#RiskMitigation#Compliance#DueDiligenceSolutions#OnGrid#VendorVerification#BusinessPartnerships
0 notes
Text
SOC 2 Certification in India - A Guide to SOC 2 Compliance, Cost and Benefits
In the growing digital business age, data security and data privacy have become paramount concerns and create challenge for businesses worldwide. As technology changes fast, the threats against sensitive informationisalso changing. To address these concerns, many organizations are turning to frameworks like SOC 2 Certification(System and Organization Controls 2) to ensure they meet rigorous standards for safeguarding data. In India, the tech industry is thriving, the importance of SOC 2 compliance cannot be overstated. UnivateSolutions, a leading consultant specializing in SOC 2 certification in India, understands the complexities and challenges that businesses face in achieving and maintaining compliance.
Accessing SOC 2 ComplianceLandscape
Achieving SOC 2 certificationcompliance requires a comprehensive approach that encompasses various aspects of an organization's operations. Univate Solutions works closely with clients to assess their current practices and identify areas that need improvement to meet SOC 2 requirements. This may involve implementing robust access controls, encryption protocols, and monitoring systems to protect sensitive data from unauthorized access or breaches. Additionally, it helps organizations establish clear policies and procedures for handling data, ensuring transparency and accountability throughout the process.
Benefits of Achieving SOC 2 Certification and Compliance in India
Achieving SOC 2 certification and compliance in India is not merely a regulatory requirement; it's a strategic investment in the future of your business. Due to the growing issues for data breaches and cyber threats are on the rise, SOC 2 certification offers numerous benefits that extend beyond mere compliance. As a leading consultancy firm in India specializing in SOC 2 certification, Univate Solutions is well-versed in the advantages that come with achieving and maintaining SOC 2 compliance.
Enhanced Data Security: SOC 2 compliance ensures that your organization implements robust security measures to protect sensitive information from unauthorized access or breaches.
Increased Customer Trust: SOC 2 certification demonstrates your commitment to safeguarding customer data, thereby enhancing trust and confidence among your clients and stakeholders.
Competitive Advantage: In a competitive market, SOC 2 certification sets you apart from competitors by showcasing your dedication to data security and compliance.
Regulatory Compliance: SOC 2 compliance helps your organization meet regulatory requirements and avoid potential penalties or fines associated with data breaches or non-compliance.
Improved Risk Management: By identifying and addressing vulnerabilities in your systems and processes, SOC 2 compliance helps mitigate the risk of data breaches and financial losses.
Streamlined Operations: Implementing SOC 2 controls often leads to more efficient and streamlined business operations, reducing the risk of downtime or disruptions.
Business Continuity: SOC 2 compliance ensures that your organization has measures in place to maintain business continuity in the event of a cyber incident or data breach.
Global Market Access: SOC 2 certification opens doors to new markets and opportunities by demonstrating your organization's commitment to data security and compliance on a global scale.
SOC 2 Certification Cost and Data Security
While the cost of SOC 2 compliance can vary depending on the size and complexity of an organization in India, the investment is often outweighed by the benefits of enhanced security and trust. At UnivateSolutions, weunderstand that cost is a significant consideration for businesses, which is why they offer customized solutions that provide maximum value for the clients. By leveraging the expertise and industry insights, we help organizations streamline the SOC 2 certification cost and compliance process, reducing both time and expenses associated with achieving SOC 2 certification in India.
Conclusion
In conclusion, SOC 2 certification is a critical step for businesses looking to expand their commitment to data security and compliance. With Univate Solutions, navigating the complexities of SOC 2 certification compliance becomes more manageable and cost-effective. Achieving the SOC 2 certification compliance, an organizations can not only protect their sensitive information but also build trust and confidence among their customers and stakeholders.
0 notes
Text
Empower Your Onboarding Process with “Gridlines” Instant Verification APIs
Elevate your digital onboarding experience to new heights with “Gridlines'' cutting-edge Instant Verification APIs. Our comprehensive suite of over 100 low-latency, plug-and-play APIs empowers businesses to seamlessly verify a myriad of data points, including GSTIN, Aadhaar, PAN, employment history, driving license, and vehicle RC information. With a proven track record of conducting over 250 million verifications, Gridlines ensures unparalleled reliability and accuracy in every verification process.
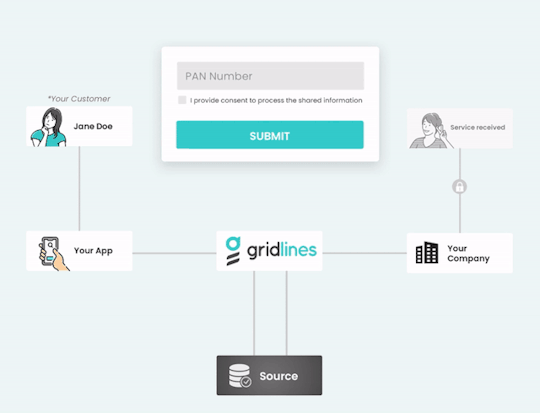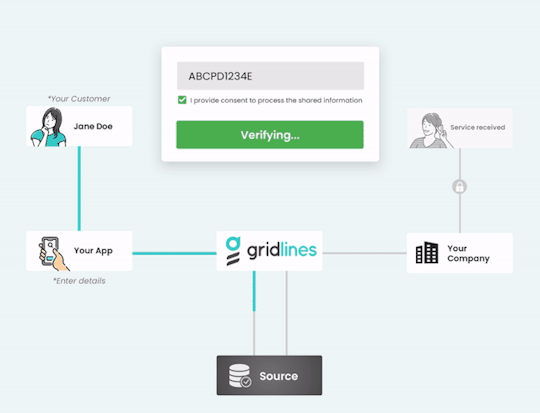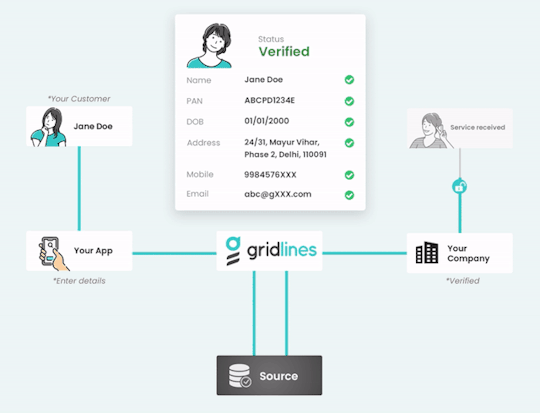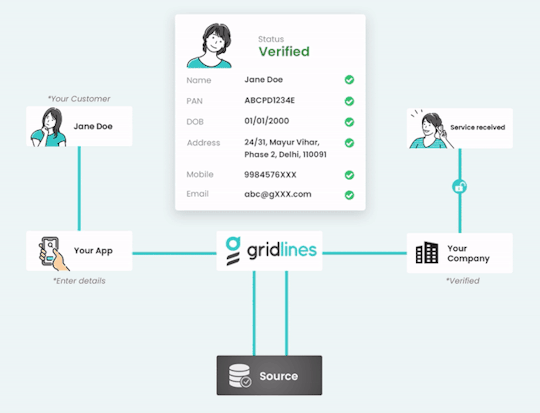
Benefit from the flexibility and accessibility of Gridlines APIs, allowing you to onboard new users seamlessly at any time of the day. Harness the power of real-time data retrieval and verification from trusted sources, ensuring that your information is always accurate and up to date.
Rest assured knowing that Gridlines prioritizes the highest standards of data security and compliance, holding ISO certification and SOC 2 Type II compliance. Protect your capital, safeguard your reputation, and mitigate fraud risks effectively with Gridlines Instant Verification APIs.
Experience the next evolution in digital onboarding with Gridlines. Unlock the full potential of your verification processes and stay ahead of the curve with Gridlines Instant Verification APIs.
#Gridlines#InstantVerification#DigitalOnboarding#APIs#VerificationServices#ISOCompliant#SOC2#DataSecurity#Reliability#RealTimeVerification#OnboardingSolutions#DataVerification#Compliance#FraudPrevention#SecureOnboarding#BusinessSolutions#TechInnovation#DigitalTransformation#APIIntegration
1 note
·
View note
Text
Pioneering Digital Excellence: Sify's Cutting-Edge Data Centers in Bangalore
In the heart of India’s Silicon Valley, where innovation is the norm and technology reigns supreme, Sify stands tall as a beacon of digital infrastructure excellence. With a legacy of unparalleled service and a commitment to pushing the boundaries of technology, Sify’s state-of-the-art data centers in Bangalore redefine the standards of reliability, scalability, and security. As the backbone of India’s digital revolution, our facilities empower businesses to thrive in an ever-evolving digital landscape.
Unmatched Infrastructure for Optimal Performance
Sify’s data centers in Bangalore are engineered to deliver optimal performance and reliability, setting new benchmarks for excellence in the industry. Equipped with cutting-edge technology and best-in-class infrastructure, our facilities boast redundant power supplies, advanced cooling systems, and robust security measures to ensure maximum uptime and data protection. With round-the-clock monitoring and support, Sify guarantees that your critical data and applications are always available and secure.
Seamless Connectivity for Enhanced Collaboration
Connectivity is the lifeblood of modern enterprises, and Sify’s data centers in Bangalore are strategically positioned to provide seamless connectivity to businesses across the region. With direct access to India’s largest internet exchange and a vast network of carriers and service providers, our facilities offer high-speed connectivity and low-latency connections, enabling enhanced collaboration and productivity. Whether you’re a startup or a multinational corporation, Sify’s data centers provide the connectivity you need to stay ahead in today’s digital economy.
Scalability to Meet Growing Demands
In a world where data volumes are growing exponentially, scalability is essential. Sify’s data centers in Bangalore are designed with scalability in mind, allowing businesses to easily expand their infrastructure as their needs evolve. Whether you need additional server space, increased bandwidth, or enhanced security features, our facilities can accommodate your growing requirements, ensuring that you’re always prepared for the future.
Compliance and Security as Top Priorities
Security is paramount when it comes to data management, and Sify takes security seriously. Our data centers in Bangalore adhere to the highest industry standards for security and compliance, including ISO 27001, PCI DSS, and SSAE 18 SOC 1 & 2. With advanced security protocols, biometric access controls, and continuous surveillance, Sify ensures that your data remains protected at all times, giving you peace of mind and confidence in your digital infrastructure.
Experience the Sify Advantage
Join the ranks of leading enterprises that trust Sify’s data centers in Bangalore to power their digital transformation journey. Experience unparalleled reliability, scalability, and security like never before. Partner with Sify today and unlock the full potential of your digital infrastructure.
Empower your business with Sify’s cutting-edge data centers in Bangalore. Contact us to learn more about how we can help you drive innovation and achieve your digital goals.
0 notes
Text
Regulatory Alignment: SOC 2 Certification within Iran's Compliance Framework

Introduction to SOC 2 Certification in Iran
As organizations in Iran increasingly prioritize data security and privacy, understanding and implementing internationally recognized standards such as SOC 2 certification in Iran becomes paramount. While SOC 2 certification is rooted in the American regulatory landscape, its principles can be adapted and applied within the Iranian context to enhance trust and confidence in the handling of sensitive information. This introduction serves to provide an overview of SOC 2 certification, its relevance in Iran, and the potential benefits it offers to organizations operating within the country. By exploring the fundamental concepts and requirements of SOC 2 certification, Iranian businesses can better navigate the complexities of modern data security and compliance standards, thereby safeguarding their operations and earning the trust of stakeholders both domestically and internationally.
Overview of SOC 2 Compliance Standards
Security: This criterion evaluates the effectiveness of an organization's controls in safeguarding against unauthorized access, unauthorized disclosure, and damage to systems and data.
Availability: It assesses the organization's ability to ensure that its systems and services are available for operation and use as agreed upon or contracted.
Processing Integrity: This criterion evaluates whether the organization's processing systems are accurate, complete, timely, and authorized.
Confidentiality: It focuses on the protection of confidential information against unauthorized access, disclosure, or use.
Privacy: This criterion assesses how well the organization manages personal information in
Organizations seeking SOC 2 certification in Chennai compliance undergo a thorough audit conducted by independent third-party auditors. The audit evaluates the design and effectiveness of the organization's controls based on the chosen trust service criteria. Upon successful completion of the audit, the organization receives a SOC 2 report, providing assurance to customers, partners, and stakeholders regarding the security and privacy of their data.
Achieving SOC 2 compliance requires a comprehensive approach to risk management, including the development and implementation of robust policies, procedures, and technical controls. While SOC 2 compliance is not a legal requirement in Iran, adhering to these standards can demonstrate a commitment to data security and privacy best practices, enhancing trust and credibility in the eyes of customers and business partners both domestically and internationally.
Conclusion & Recommendations for SOC 2 Certification in Iran
Conduct a thorough assessment: Evaluate current data security and privacy practices against SOC 2 criteria to identify gaps and areas for improvement.
Develop robust policies and procedures: Implement comprehensive policies and procedures to address security, availability, processing integrity, confidentiality, and privacy requirements outlined in the SOC 2 framework.
Implement technical controls: Deploy appropriate technical controls, such as encryption, access controls, and monitoring systems, to protect against unauthorized access and data breaches.
Engage qualified auditors: Partner with experienced and qualified auditors to conduct SOC 2 audits and provide guidance throughout the certification process.
Continuously monitor and update controls: Regularly assess and update controls to adapt to evolving threats and regulatory requirements, ensuring ongoing compliance with SOC 2 standards.
To get assistance with SOC 2 Certification in Iran, send an email to [email protected] with your requirements. For additional information on SOC 2 certification locations in Iran, please visit our official website at www.b2bcert.com. We may employ value addition to ascertain needs and assist your business in selecting the most precise and cost-effective route to SOC 2 certification in Iran.
0 notes
Text
SOC 2 Certification and SSAE 18 Compliance in India's Information Security Landscape
Organizations globally and in India are increasingly recognizing the importance of robust information security measures to protect sensitive data and maintain trust with clients and stakeholders. In this context, SOC 2 Certification and compliance with SSAE 18 standards emerge as critical benchmarks, providing assurance of an organization's commitment to maintaining stringent controls over its systems and data.
Understanding SOC 2 Certification in India
The SOC 2 Certification, established by the American Institute of Certified Public Accountants (AICPA), emerges as a gold standard framework designed to meticulously assess and validate the efficacy of an organization's controls pertaining to security, availability, processing integrity, confidentiality, and privacy.
At its core, SOC 2 Certification is built upon a foundation of robust control measures aimed at safeguarding critical assets and sensitive data. These controls encompass various domains, including:
Security: Ensuring the protection of systems, infrastructure, and data against unauthorized access, cyber threats, and malicious activities.
Availability: Guaranteeing the availability and reliability of systems and services to meet operational requirements and business needs consistently.
Processing Integrity: Validating the accuracy, completeness, and timeliness of data processing to maintain data integrity and reliability.
Confidentiality: Preserving the confidentiality of sensitive information by restricting access to authorized individuals and preventing unauthorized disclosure or leakage.
Privacy: Safeguarding personal information and ensuring compliance with relevant privacy laws and regulations to protect individual privacy rights.
Target Audience and Relevance
SOC 2 Certification holds particular significance for service organizations that handle sensitive data on behalf of their clients or customers. This includes a wide spectrum of entities, such as cloud service providers, data centers, managed service providers, and Software-as-a-Service (SaaS) providers. By obtaining SOC 2 Certification in India, these organizations signal their commitment to upholding industry-leading standards for information security and data protection, thereby instilling confidence and trust among their clients, partners, and stakeholders.
The Seal of Approval
Achieving SOC 2 Certification serves as a definitive seal of approval, signifying an organization's adherence to stringent security and privacy standards. It demonstrates a proactive approach to mitigating risks, enhancing transparency, and ensuring the integrity of operations. Moreover, SOC 2 Certification not only validates the effectiveness of an organization's controls at a specific point in time but also underscores its ongoing commitment to maintaining a secure and compliant environment.
Delving into SOC 2 Type 1 and Type 2 Certification
SOC 2 Certification comes in two distinct types, each offering different levels of assurance
SOC 2 Type 1 Certification: It evaluates the design and implementation of an organization's controls at a specific point in time, providing stakeholders with assurance that the controls are suitably designed to meet predefined criteria.
SOC 2 Type 2 Certification: goes a step further by assessing the effectiveness of these controls over a specified period, typically six to twelve months. This certification offers a higher level of assurance, demonstrating that the controls not only meet the criteria but also operate effectively over time.
Significance of SOC 2 Certification in India
In the vibrant landscape of India's outsourcing industry, maintaining the highest standards of information security and data privacy is paramount. Against this backdrop, SOC 2 Certification in India emerges as a pivotal assurance mechanism, providing both domestic and international clients with the confidence that Indian service providers adhere to globally recognized benchmarks for safeguarding sensitive information.
As India continues to solidify its position as a hub for outsourcing services, the demand for stringent information security measures grows exponentially. International clients, in particular, place a premium on partnering with service providers that demonstrate a steadfast commitment to protecting their data. SOC 2 Certification serves as a tangible demonstration of an organization's adherence to industry-leading standards, assuring clients of its capability to safeguard their confidential information effectively.
Navigating the Regulatory Landscape
India's regulatory landscape pertaining to data protection and privacy is evolving rapidly, with stringent compliance requirements being imposed by regulatory bodies such as the Reserve Bank of India (RBI), Securities and Exchange Board of India (SEBI), and the Ministry of Electronics and Information Technology (MeitY). SOC 2 Certification provides organizations with a structured framework to navigate these regulatory complexities, ensuring alignment with statutory obligations while fostering a culture of proactive risk management and compliance.
Achieving SOC 2 Certification in India entails undergoing rigorous audits conducted by independent third-party firms accredited by the AICPA. These audits evaluate the organization's controls across key domains, including security, availability, processing integrity, confidentiality, and privacy. By subjecting themselves to such scrutiny, organizations not only demonstrate their commitment to excellence but also gain invaluable insights into areas for improvement, thereby enhancing their overall security posture.
Fostering Trust and Confidence
In an era where data breaches and cyber threats are ever-present risks, establishing trust and confidence is paramount for service providers in India. SOC 2 Certification serves as a tangible testament to an organization's dedication to protecting client data and upholding the highest standards of integrity and confidentiality. This, in turn, strengthens relationships with existing clients and opens doors to new opportunities by showcasing a commitment to transparency, accountability, and excellence.
The Crucial Role of SSAE 18 Compliance
Complementing SOC 2 Certification is compliance with Statement on Standards for Attestation Engagements No. 18 (SSAE 18), the successor to SAS 70. SSAE 18 Compliance focuses on assessing the controls at service organizations relevant to their customers' financial reporting. It mandates regular assessments by independent auditors to verify compliance with established standards and regulations, further reinforcing an organization's commitment to transparency and accountability.
Conclusion In conclusion, SOC 2 Certification in India and SSAE 18 Compliance serve as cornerstones for elevating information security standards in India's burgeoning digital landscape. By obtaining these certifications, organizations demonstrate their dedication to protecting sensitive data, fostering trust with clients, and mitigating risks associated with data breaches and regulatory non-compliance. Embracing SOC 2 Certification and adhering to SSAE 18 Compliance not only enhances an organization's credibility but also positions it as a reliable custodian of data in today's data-driven world.

0 notes
Text
Keeper Security Joins the AWS Partner Network

Keeper Security, a leading provider of cloud-based zero-trust and zero-knowledge cybersecurity software protecting passwords, passkeys, secrets, connections and privileged access, announces today it has joined the Amazon Web Services (AWS) Partner Network (APN). The APN is a global community of AWS Partners that leverage programs, expertise and resources to build, market and sell customer offerings. As an APN member, Keeper joins a global network of 130,000 partners from more than 200 countries working with AWS to provide innovative solutions, solve technical challenges, win deals and deliver value to customers. Keeper joined the APN to address the growing demand for robust account security and enhance the digital protections available to businesses around the world faced with the growing threat of cyberattacks.
"AWS has long been recognized as the leading cloud services provider and we're proud to meet their rigid standards and bring their technical advantages to public and private-sector business and enterprise customers," said Darren Guccione, CEO and Co-founder, Keeper Security. "This relationship marks a significant achievement for Keeper, as it furthers our steadfast commitment to deliver cutting-edge cybersecurity solutions."
Keeper provides a full suite of award-winning consumer and business offerings in password, secrets and privileged connection management, as well as differentiators that set Keeper apart from its competitors including dark web monitoring, secure file storage, encrypted messaging, seamless Single-Sign On (SSO) integration, compliance reporting and comprehensive event logging. Keeper's solutions scale to organizations of all sizes, from small home offices to multinational enterprises and the largest public sector organizations. Keeper also offers a solution for managed service providers, KeeperMSP.
Keeper's Enterprise Password Manager is designed to provide organizations with complete visibility into employee password practices, allowing IT administrators to enforce company password policies, monitor employee compliance and generate audit trails and reports. Keeper securely manages the lifecycle of privileged account credentials with Role-Based Access Controls (RBAC) and controlled credential sharing. Keeper supports the storage and use of passkeys in the vault and enables organizations to embrace a fully passwordless experience by integrating with SSO, enabling users to access their vaults without the use of a master password.
Keeper's latest offering, KeeperPAM™, provides a next-generation Privileged Access Management (PAM) solution that is disrupting the traditional PAM market. KeeperPAM delivers enterprise-grade password, secrets and privileged connection management within a unified SaaS platform that is cost-effective, easy-to-use and simple-to-deploy. The patented cybersecurity solution enables organizations to achieve complete visibility, security, control and reporting across every privileged user on every device within an organization.
Customers prefer Keeper for:
- Enterprise Security - Keeper mitigates the risk of breaches by providing real-time protection and access to applications, systems, secrets and IT resources.
- Robust Compliance and Reporting - Keeper simplifies and strengthens auditing and compliance including support for RBAC, 2FA, FIPS 140-2 encryption, HIPAA, FINRA, SOC, ITAR and more.
- Powerful Security Insights - Keeper provides analytics into credential security and hygiene across all endpoints and systems with native SIEM integration.
Through its relationship with AWS, Keeper extends its market reach and enhances its ability to serve customers across various industries all over the world, in addition to offering Consulting Partner Private Offers (CPPO) to Keeper's Reseller Community of over 2,000 partners, allowing them to facilitate customer purchases in AWS Marketplace. For more information, please visit APN.
Read the full article
0 notes
Text
Streamline Your Hiring Process with OnGrid's White Collar Verification Services
White Collar Verification Services by OnGrid provide a holistic solution to meet all your verification needs, ensuring that your hiring decisions are both confident and secure. Our advanced features are designed to streamline the verification process, offering tailored solutions that cater to your specific requirements. With a swift Turnaround Time (TAT) of just 4 hours for preliminary checks, seamless integration with over 25 HRMS systems, and a remarkable 90%+ insufficiency resolution rate without the need for HR intervention, OnGrid stands out as a trusted partner in background verification. Moreover, our adherence to ISO certification and SOC 2 Type II compliance underscores our commitment to upholding the highest standards of data security and compliance.
Our intuitive portal provides transparent insights into verification status and turnaround time, ensuring that you stay informed every step of the way. Real-time updates through interactive live dashboards empower you with the information you need to make informed decisions. Powered by AI-driven technology, our verification process is characterized by unparalleled accuracy and efficiency. Continual audits and evaluations refine our AI models, combining the benefits of automation with the assurance of human review when necessary.

Furthermore, our proprietary databases of universities, employers, and court records are continuously updated and expanded, ensuring that we deliver speedy and accurate verification results. With a comprehensive range of checks, including ID verification, criminal verification, employment verification, education verification, address verification, professional reference check, global database check, and drug test, OnGrid's White Collar Verification Services offer a one-stop solution for all your verification needs.
#BackgroundVerification#WhiteCollarVerification#HRCompliance#HiringDecisions#ISOCompliance#DataSecurity#EmploymentVerification#EducationVerification#HRIntegration#OnGridVerification#SecureHiring#FastTAT#backgroundchecks#bgv
0 notes
Text
How to acquire Iraq SOC 2 Certification and Compliance audit?

SOC 2 Certification in Iraq or Service Organisation Control 2 for Data safety and privateness are critical to companies and customers in this digital world. As corporations depend greatly on cloud services and backyard companies to manage non-public information, it's imperative to put sturdy safety measures in place. SOC 2 (Service Organisation Control 2) Certification is one measure to address these issues. In this weblog post, we will speak about how to get SOC 2 Certification in Iraq and the most critical parts of a SOC 2 compliance check.
Understanding SOC 2 Certification.
The American Institute of CPAs (AICPA) made SOC 2 a machine to help businesses protect and take care of consumer data. It's primarily based on five "Trust Service Criteria'': privacy, security, availability, processing integrity, and processing integrity. These requirements are what a SOC 2 Certification in Iraq is primarily based on, and firms should show that they follow them to get certified.
Step 1: Figuring out if you are ready.
Before starting the licensing process, companies need to look at their protection measures and methods closely. This capacity is finding places that meet the SOC 2 standards and filling in any loopholes. At this point, it can be beneficial to work with a skilled SOC 2 adviser who can provide advice and experience.
Step 2: Making regulations and hints for security.
It is imperative to make thorough security policies and methods to get SOC 2 Certification in Iraq. These papers give an explanation for how the agency meets all 5 Trust Service Criteria. Policies and strategies be made to match the way the commercial enterprise works and made clear to everybody who works there.
Step 3: Putting controls in place.
Once establishments have policies, they need to implement security tools to meet SOC 2 standards. Some of the things that fall beneath this class are admission to limits, encryption, crisis reaction, and tracking. It's imperative to strive for these settings commonly to make sure they are working right.
Step 4: Train and inform employees.
A massive phase of maintaining SOC 2 compliant is up to the employees. Giving thorough training on safety insurance policies and methods is one way to make the enterprise more security-aware. Regular training meetings and updates replace personnel on cutting-edge safety risks and great practices.
Step 5: Audit before the assessment.
An organisation may do a pre-assessment audit earlier than the legit SOC 2 audit. This skill hiring a third-party inspector to seem to be over the policies that have been put in place and discover any problems that might be happening. The feedback you get at this stage can help you make protection steps even higher before the respectable audit.
Step 6: Choose a SOC 2 auditor who is qualified.
Picking the right SOC 2 auditor is a necessary phase of getting certified. The chosen auditor must be a licensed CPA employer that has executed SOC 2 assessments before. Ensuring they are knowledgeable and recognize the organisation's enterprise problems is necessary.
Step 7: SOC 2 Audit.
During the official SOC 2 audit, the organisation's safety controls and processes are looked at in awesome detail. The auditor will take a look at how nicely these rules meet the Trust Service Criteria. Interviews, report checks, and device assessments may also all be phase of the audit. During this process, companies must be prepared to exhibit proof that they comply with the rules.
Step 8: Fixing the problems found.
It's regular for inspectors to locate things that ought to be completed better all through the SOC 2 audit. These results need to be viewed as possibilities for corporations to enhance their security. Taking care of and fixing any troubles the inspector finds right now is necessary for getting certified.
Step 9: Obtaining SOC 2 Certification.
The enterprise can get its SOC 2 Certification once the audit is over and all the wanted fixes have been made. While competing in the market, the licence can help the corporation stand out as a tangible signal of its dedication to facts security.
Why choose Factocert SOC 2 Certification in Iraq?
Factocert is one of the pinnacle main SOC 2 Certification carriers in Iraq. We grant the satisfactory SOC 2 Consultants in iraq, Baghdad, Mosul, Basra, Erbil, Najaf, Karbala, and different major cities in Iraq.factocert is the most relied on SOC 2 Certification Bodies in Iraq visit our website www.factocert.com or contact us at [email protected] for service of implementation, training, auditing, and registration.We furnish one of a kind ISO Standards like ISO 27001,ISO 9001,ISO 45001 ,ISO 14001,ISO 13485,ISO 22000,and ISO 17025.
Conclusion
Getting SOC 2 Certification In Iraq,means taking a deliberate and organised approach to records protection. Companies can enhance their protection and acquire patron belief by way of utterly understanding the requirements, establishing strong controls, and working with knowledgeable experts. As technological know-how changes, SOC 2 Certification is no longer just a legal requirement; it also gives groups a competitive part via displaying they care about retaining non-public records safely.
For More information visit : SOC 2 Certification in Iraq
Related Links :
GDP Certification in Iraq
GLP Certification in Iraq
GMP Certification in Iraq
GDPR Certification in Iraq
SOC 1 Certification in Iraq
SA 8000 Certification in Iraq
RoHS Certification in Iraq
HALAL Certification in Iraq
0 notes