#Telephony Control
Text
Battle of the Fear Bands B1R2: The Spiral
Slide into the void:
"Technically this song is about control (the game) but this is an incredibly spiral coded song. It has everything - the breakdown of the mind, of reality, mazes and fractals and dreams oh my."
youtube
Where is my Mind:
"A classic. Also it's on every movie soundtrack where the characters have some sort of mental trip"
youtube
Lyrics below the cut!
Slide into the void:
You hear our words, but you forget Push your fingers through the surface to the wet We wait in the stains, we build you 'til nothing remains In the name of the sound of the name
Repeat the word. Repeat the word. Repeat the word Egg cracks and the truth will emerge A copy of a copy of a copy of a copy of a copy You are home. You remind us. Happy. Hurt
At the edge of understanding, the border of the known The breaking point of reason, where logic is dethroned Where sense is defenceless and festers on the bone You'll find entropy's offensive is rendered in the stone
As you roam through the Oldest House Home to all that you weren't told about Trapped within a labyrinth, it goes without saying That we're praying that they don't get out
Prison for the isn't, sitting hinged within a schism Of half-reflected architecture, dark unending prisms Part objective, part conjecture, partnered with tradition Where the paperwork is worshipped and the rituals are written
When the Black Rock cracks and the Firebreak ends The Director is left as the line of defence When the Trenches have fallen to forces unknown Perhaps you should answer the phone
If you can't place the pin Where patterns end and you begin Follow the Director Else you're gonna slide into the void But if the world you knew Has cracked and fallen through Go to the Projector Load another slide into the void
There's the strangest correlation observation will present In the systems we can witness and the signals they have sent These forces yet unknowable, that ripple through cement Inscrutable intrusions. Altered World Events
Where reality cracks and impacts on the next Dimensions fragment and the Astral projects On benign, undefined, archetypal objects Until Ordinary's torn up, and normal defects
In effect, what you're left with are OoPs Objects of Power, a flying TV A light that can hijack your mind as you see A safe that's encased in a shield of debris
These frequencies are frequently the key to what's perceived to be And vis-à-vis are feeding off the reaches of the mind But recently, the sequence has repeated and repeated And it leaves me with the theory that they're trying to get inside
You hear our words, but you forget Push your fingers through the surface to the wet We wait in the stains, we build you 'til nothing remains In the name of the sound of the name (How do you say "insane"?)
Repeat the word. Repeat the word. Repeat the word Egg cracks and the truth will emerge A copy of a copy of a copy of a copy of a copy You are home. You remind us. Happy. Hurt
If you can't place the pin Where patterns end and you begin Follow the Director Else you're gonna slide into the void But should your world collapse And fall right off the maps Go to the Projector Load another slide into the void
The Director is the Bureau's one connection to the Board Obey the mighty Bakelite and file your reports Telephony in effigy must never be ignored So if you hear a ringing, you had better pull the cord
And explore the décor of the Oceanview Where the doors only open for a chosen few Check your logic at the desk, you won't need it to progress A dream is just a test to be broken through
Like the smoke entombed in the rooms of the ashtray Furniture fractals, the carpet cascades Lost in a labyrinth of lounge chairs and lampshades Wallpaper warps into infinite pathways
There's no limit to the dangers of phenomenon we keep Or the chaos that would reign should the Panopticon be breached This never-ending edifice is perched upon the precipice Since we let in the Resonance, the future's under siege
If you can't place the pin Where patterns end and you begin Follow the Director Else you're gonna slide into the void But if you see the seams Where motels meld with dreams Go to the Projector Load another slide into the void
I've analyzed the data, I've catalogued the signs Run every simulation, every sample I can find I'd give an explanation, but we haven't got the time We're drowning in the waveforms and our minds are in the tide
Of elegant malevolence, sequestered in the Resonance Nesting in the head of every denizen Tell me, is it heaven-sent? Is the Devil even relevant? When questioning the presence of dimensional intelligence?
Thresholds unfold as a door that knocks In the ticking, in the ticking, in the ticking of the clocks We are holding the key, we just don't see the locks Paradise and parasite, in parallel, in paradox
We stand on a mantle where matter divides To abstractive fractures that tangle and writhe Through cracks in reality, trapped in a slide Such intangible sanctuary Hedron provides
Breaking the first, the second, the third The fourth wall, fifth wall, no floor, you fall Earworm humming in a dream Baby, baby, baby, yeah. Just plastic
You want to listen You want to dream You want to smile You want to hurt You don't want to be
You want to listen You want to dream You want to smile You want to hurt You don't want to be
If you can't place the pin Where patterns end and you begin Follow the Director Else you're gonna slide into the void But should your towers fall Free your mind and heed the call Go to the Projector Load another slide into the void.
Where is my Mind:
Ooh
Stop
With your feet on the air
And your head on the ground
Try this trick and spin it, yeah
Your head will collapse
If there's nothing in it
And you'll ask yourself
Where is my mind?
Where is my mind?
Where is my mind?
Way out in the water, see it swimmin'
I was swimmin' in the Caribbean
Animals were hidin' behind the rocks
Except the little fish, bumped into me
I swear he was trying to talk to me, koi-koi
Where is my mind?
Where is my mind?
Where is my mind?
Way out in the water, see it swimmin'
With your feet on the air
And your head on the ground
Try this trick and spin it, yeah
Your head will collapse
If there's nothing in it
And you'll ask yourself
Where is my mind?
Where is my mind?
Where is my mind?
Way out in the water, see it swimmin'
With your feet on the air
And your head on the ground
Try this trick and spin it, yeah
5 notes
·
View notes
Text
Cloud Telephony Services in India
Search and Compare cloud Telephony provider in india. Get additional features, control, flexibility, and visibility with our Virtual PBX system.Manage your everyday conferencing,HD video meetings,and business calls anywhere 24/7 support help-desk. call today and get 25% discount with free trail.
#Cloud Telephony Services#Cloud Telephony Providers#Cloud VoIP#Virtual Phone System#Cloud Communication#hosted pbx#VoIP Telephony
2 notes
·
View notes
Text
Providing individuals with accurate
AMR systems can be installed as part of a system that includes water and gas meters also. Few of the meters run via powerline networks while others through wireless connectivity options. AMR mostly includes network and mobile technologies on radio frequency, telephony platforms and powerline transmission. Door-to-door reading of meters can best be reduced with smart meter;s operation link. Providing individuals with accurate and reliable billing, these meters are a great way to save user;s time and energy. Most of the meters also feature the ability to send alert messages to households warning about their exceeding power limits.
Even a smallest wattage consumption can be detected with the widely appreciated AMR system. When compared with the traditional meters, these computerized meters provide homeowners and utility companies a versatile system to track energy usage. Below mentioned are some of the best benefits of the latest AMR system: Improves the billing system Accurate reading of meters without any error Reduces the time spent on reading meters A cost-effective method to maintain and read meters Are you willing to install these devices at home? If yes then purchasing them online is the best option. Automated meter reading system turns to be an important asset to monitor energy usage of households as well as commercial set ups; thereafter transmitting the respective information to a central database for billing.
These smart devices integrate communication interfaces and digital sensors in order to monitor and control bills automatically. Are you also among those who find it hard to read meters manually? If yes, then it;s imperative to find a solution for the same. To make the task simpler, automated meter reading software is one of the remarkable inventions of modern technology. This great technology helps utility providers in saving time on periodical visits to read meters manually. The best benefit of this device is that, billing is generated on the basis of real time consumption rather than the estimates based upon your predicted consumption.Reading meters manually is a hard chore for most of the individuals.
A technology known as Smart Energy Profile is used by the computerized meters to consolidate with the home networking equipment. The World Wide Web features innumerable options which allow you to purchase the one that suits your needs and preferences. The lifespan of such devices is around ten years, which prohibits unnecessary replacement at regular intervals. China Wholesale Hydraulic Hose Fittings Manufacturers Henceforth, buy automated metering products online and get accurate billing information effortlessly.
2 notes
·
View notes
Text
The future of cloud PBX providers!
The major roles that contribute to the success and triumph of business communications are "VOIP service providers or Cloud PBX providers." Almost all types of businesses, from small to large, are replacing their old phone systems with modernized ones. Recent surveys and research studies are proving that future communications are ruled by internet telephony services and their providers.
What is CLOUD PBX?
A company phone system that is housed on servers in distant data centers and is operated online is referred to as a "cloud PBX." This indicates that VoIP technology is used by these phone systems to place and receive calls. It is often known as a virtual PBX or hosted PBX, which is an exchange system that is created, built, and hosted in the cloud which is controlled by a third-party service provider and which is accessed over the Internet.
Not from the beginning, but from the past few years, many businesses including some of the large scale ones are switching to cloud PBX. It was previously considered as a con of this hosted PBX regarding data security. But gradually with enhancements done, this is essential to understand that security of cloud PBX will be transferred to the companies that are experts in the field.

Cost Savings of Cloud/Hosted PBX:
Investment is of top priority for any business organization. It has to be calculated twice along with the assessment of the resources as well as the requirements before investing. And, that is a move of wit. Once data security has been promised by the PBX service providers, users started to use it due to the cost saving primarily with respect to the space to be allotted and hardware.
However, hosted PBX saves maintenance cost and the cost of a dedicated tech team to maintain it. The above mentioned factors would save a lump sum in the long run. Besides, integration with other new installations and accessibility increases.
Reasons why these services are referred to as future technology:
Get the services within your budget:
The budget that must be allocated for the purchase of the software or hardware equipment is the first worrying factor that any firm takes into account but this technology is undoubtedly very affordable. Depending upon the company’s requirements get the communication infrastructure and subscriptions.
Flexible
Yes, very flexible and comfortable as one can keep working on the device that is connected to the internet and your service provider even when the individual or team is out of the desk. Cloud PBX solutions erase the geographical limitations to your team if some of them are interested in working remotely.
Features
VoIP dominates every other telecommunication system with absolute free calling and advanced features. For example, when it comes to internal communication of a business team, audio and video calls conferences could be conducted with premium call quality. An important asset that has to be addressed is that Cloud calling provides 99.99% uptime leading to an uninterrupted network.
The most important factor that encouraged firms to replace the legacy systems is the features incorporated with the VOIP phones few among them are:
Ring teams
Unlimited phone calls
Call waiting
Voicemail to email
Online meetings
Using text messages
Automatic attendant
Branch office support
Call forwarding
Pause the music
Billing
DND
Allows customization:
As already discussed, one more good reason for shifting towards the internet telephone is it allows the companies to do their customizations depending upon the firms’ requirements. It is pretty scalable if you want new lines. You can get any number of lines without spending on additional hardware or installation charges. All you need to do is to pay for more bandwidth and the service provider will guide you with the process.
Integrations and multiple storages:
Of course! VoIP can be integrated with any new software easily with no complications. This feature would help you in saving money and time.
You can easily combine cloud data with information already present in company systems, such as CRM integration. You can also integrate with sales applications and the service provider handles data redundancy by keeping identical data on servers located in various locations. Thus, it confirms that this technology is easy to set up and operate.
All processes are automated:
VoIP eliminates the need for manual help by automatically creating reports, billing, and other services reducing the manual effort in the firms.
Customer service:
The VoIP services effectively implement round-the-clock customer support services, increasing business efficiency hence proving that this modernized technology attracts more clients and helps small businesses particularly.
Conclusion:
Installing a cloud PBX system from a reputable service provider is the major step that needs to be taken by businesses, one such firm providing an adaptive environment through their products and services is VITEL GLOBAL COMMUNICATIONS, so don’t delay in searching for the best provider as we are one of the leading Cloud PBX providers focusing and developing your business communications. For more information, visit www.vitelglobal.in
9 notes
·
View notes
Text
What Is Iptv And What Are The Types Of Iptv Providers
IPTV companies are deployed by several service providers corresponding to satellite TV corporations, phone companies, cable TV carriers, and tons of extra. In addition to video, IPTV expertise also presents VOIP in addition to net entry for the info. These three companies offered concurrently by IPTV technology are popularly generally recognized as triple play, whereas the fourth feature contains mobile telephony, which gets added, which is known as quadruple play. Catch-up TV is probably the most engaging incarnation of IPTV – it mainly bridges the hole between traditional TV and streaming VOD providers. Many leading providers like FOX, CBS, and NBC now provide apps that viewers can download to compensate for the TV content material they missed. FOX, CBS, and NBC offer devoted IPTV apps that enable viewers to look at the shows that they missed on stay TV with out the need to document anything by way of a TiVo or one other set-top field with recording performance.
Apple is a extremely popular method of accessing premium iptv content via dedicated apps. It runs a slimmed-down working system , to handle the method of streaming video by way of the Internet. The VOD platform may be built-in with the IPTV’s central unit. Cable TV methods use a complicated system referred to as Data Over Cable Service Interface Specification , developed by CableLabs.
It's unclear by the appears of your code, whether your trying to make use of 'hls' or 'dash'. Anyway, I've been enjoying with 'hls', and I'll have some outcomes to report, in one other day or two. MinoliD.2008IP multicast with purposes to IPTV and cellular DVB.Canada, John Wiley & Sons, Inc.
Unfortunately, we didn’t have the source code of the mysqlInstance objects implementation as a result of it is encoded with IonCube and the license forbids us to the touch the category file. Our only choice was to black box test the features which are answerable for dealing with the controlled values. After some tests, it was clear that the keys handed to the orderby, select and like functions were vulnerable to SQL Injection. As we management keys in the question, we are in a position to perform either blind or reflected SQL injection. Ministra is Infomir’s net management platform that controls the STB gadgets. It is PHP based mostly, and like most web-based platforms, it has an admin interface that requires authentication.
The features that Yeah IPTV has on every plan are detailed under. Cruise InfoTech is an IT answer firm established in the yr 2015. The company has emerged as a key player in Information Technology throughout Mumbai.
Les entreprises IPTV sont déployées par plusieurs fournisseurs de services correspondant aux sociétés de télévision par satellite, aux compagnies de téléphone, aux opérateurs de télévision par câble et à des tonnes d'autres. En plus de la vidéo, l'expertise IPTV propose également la VOIP en plus de l'accès Internet pour l'info. Ces trois sociétés proposées simultanément par la technologie IPTV sont généralement reconnues comme triple play, tandis que la quatrième fonctionnalité contient la téléphonie mobile, qui est ajoutée, connue sous le nom de quadruple play. La télévision de rattrapage est probablement l'incarnation la plus engageante de l'IPTV - elle comble principalement le fossé entre la télévision traditionnelle et les fournisseurs de VOD en streaming. De nombreux fournisseurs de premier plan tels que FOX, CBS et NBC proposent désormais des applications que les téléspectateurs peuvent télécharger pour compenser le contenu télévisé qu'ils ont manqué. FOX, CBS et NBC proposent des applications IPTV dédiées qui permettent aux téléspectateurs de regarder les émissions qu'ils ont manquées sur la télévision en direct sans avoir besoin de documenter quoi que ce soit via un TiVo ou un autre décodeur avec des performances d'enregistrement.
Apple est une méthode extrêmement populaire pour accéder au contenu iptv premium via des applications dédiées. Il exécute un système d'exploitation allégé, pour gérer la méthode de streaming vidéo via Internet. La plateforme VOD peut être intégrée à l'unité centrale de l'IPTV. Les méthodes de télévision par câble utilisent un système compliqué appelé Data Over Cable Service Interface Specification , développé par CableLabs.
L'apparence de votre code n'est pas claire, que vous essayiez d'utiliser 'hls' ou 'dash'. Quoi qu'il en soit, j'ai apprécié avec 'hls', et j'aurai des résultats à signaler, dans un autre jour ou deux. MinoliD.2008Multidiffusion IP à des fins premium iptv et de DVB cellulaire.Canada, John Wiley & Sons, Inc.
Malheureusement, nous n'avions pas le code source de l'implémentation des objets mysqlInstance car il est encodé avec IonCube et la licence nous interdit de toucher au fichier de catégorie. Notre seul choix était de tester en bo��te noire les fonctionnalités qui sont responsables du traitement des valeurs contrôlées. Après quelques tests, il était clair que les clés remises aux fonctions orderby, select et like étaient vulnérables à l'injection SQL. Comme nous gérons les clés de la question, nous sommes en mesure d'effectuer une injection SQL aveugle ou réfléchie. Ministra est la plate-forme de gestion de réseau d'Infomir qui contrôle les gadgets STB. Il est principalement basé sur PHP et, comme la plupart des plates-formes Web, il possède une interface d'administration qui nécessite une authentification.
Les fonctionnalités de Yeah IPTV sur chaque plan sont détaillées ci-dessous. Cruise InfoTech est une société de réponse informatique créée en 2015. La société est devenue un acteur clé des technologies de l'information à Mumbai.
4 notes
·
View notes
Text
Five benefits of VoLTE over traditional CS voice calls

VoLTE provides five benefits over traditional CS voice calls.
Migration to IP
VoLTE enables operators to migrate their circuit switched infrastructure (e.g. 3G) to a fully IP centric network. Without VoLTE, 4G networks cannot support voice service, therefore operators wishing to offer this communication capability will need to still support legacy technologies and use CSFB (CS Fallback) techniques to redirect the user towards them when a call is made or received.
Voice Quality
VoLTE offers higher voice quality than legacy circuit switched voice. As shown in Figure 1, VoLTE provides voice in wider range of frequency and enhances the voice quality significantly. With implementation of EVS (Enhanced Voice Services) codec, the range is even extended, and customers can enjoy very high-quality voice.
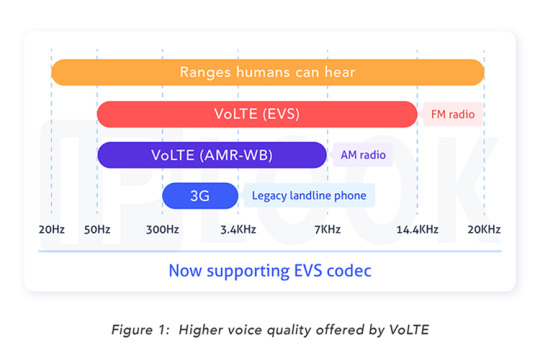
Fast Call setup
Another prominent advantage of VoLTE is the shorter call setup time compared to legacy circuit switched voice services. Call setup time is the time it takes from initiating the call to hearing from or speaking to the called party, and VoLTE reduces the call setup time to about a third of that of legacy circuit switched voices.
Multimedia communications
VoLTE also enables video calls to be provided in conjunction with HD voice (ViLTE: Video over LTE). This means that not only video calls are possible between VoLTE subscribers, but also switching between Video and Voice is supported.
Efficiency
As VoLTE calls are natively supported by LTE networks, the scarce radio resources are used much more efficiently than with legacy technologies.
IPLOOK’s IMS products and VoLTE services
IPLOOK has developed IP multimedia subsystem (IMS) products that incorporate IMS applications which are installed on hardware devices built to the Advanced Telecom Computing Architecture (ATCA) standard (the leading hardware standard for telecom carriers), and which form the core networks of mobile phone services. IPLOOK also provides telecom carriers with solutions that help them deliver a wide range of optimized voice services.
IPLOOK’s IMS products consist of a Proxy-Call Session Control Function (P-CSCF) and a Serving/Interrogating Call Session Control Function (S/I-CSCF). These are part of a control system that performs call control, a Telephony Application Server (TAS) incorporated in a service delivery system that controls additional mobile phone services, and an IMS Access Gateway (IMS-AGW) that controls packet and relays voice data.
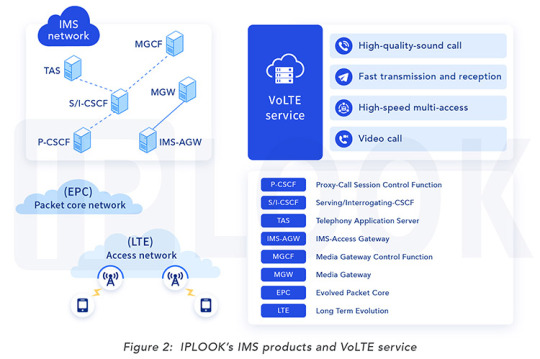
An IMS application sample is shown in Figure 2. As this makes clear, introduction of IMS products to a telecom carrier’s core network makes it possible to offer Voice over LTE (VoLTE) service in which voice calls using the LTE communication system are possible. This supports voice calls and video calls with high sound quality, minimal delay, and high stability. Moreover, high-speed data communication can be used even during a call.
It is our intention to provide a quality product for your use. Contact us for more details!
1 note
·
View note
Text
Understanding CPL Training: Hours & Subjects. Certainly! When it comes to understanding CPL (Commercial Pilot License) training, the hours and subjects covered are essential aspects.
Hours of Training:
Total Flight Hours: CPL training typically requires a minimum number of flight hours, often around 150-200 hours.
Dual Instruction: A significant portion of these flight hours involves dual instruction, where you're flying with an instructor.
Solo Flight: You'll also need a certain number of solo flight hours, gaining experience without an instructor present.
Subjects Covered:
Navigation: Learning how to navigate using instruments and charts, understanding airspace regulations.
Meteorology: Studying weather patterns and their impact on flight operations.
Aircraft Systems: Understanding the mechanics and systems of the aircraft you'll be flying.
Flight Planning: Learning to plan flights, including fuel requirements, alternate routes, and emergency procedures.
Human Factors: Understanding how human performance and limitations affect flying.
Radio Telephony: Learning communication procedures for air traffic control.
General Airmanship: Developing skills related to aircraft handling, maneuvers, and emergency procedures. https://www.youtube.com/shorts/QQteCFpfAZY
Each training program might vary slightly, but these are common subjects and areas of focus for CPL training. Let me know if you need more details on any specific aspect!
0 notes
Text
Ensuring Security in IP Phone Systems: Tips and Best Practices
Communication technologies such as IP phone systems have become integral to business operations, offering flexibility, scalability, and cost-efficiency. However, as with any networked technology, security is a paramount concern. At Yabbit, we understand the importance of safeguarding communications to prevent data breaches and ensure business continuity. This blog explores essential tips and best practices for securing IP phone systems effectively.
Understanding IP Phone System Vulnerabilities
IP phone systems function by transmitting voice communications over the internet or other IP networks. While this technology provides substantial advantages over traditional telephony, it also exposes businesses to cyber threats similar to those affecting other internet-connected devices. Common vulnerabilities include eavesdropping, unauthorised access, and service disruption attacks. Acknowledging these potential risks is the first step in fortifying security measures.
Implementing Strong Authentication Methods
One of the most effective ways to enhance the security of IP phone systems is through robust authentication protocols. Ensuring that only authorised users can access the phone system is crucial. Techniques such as two-factor authentication (2FA), where users must provide two forms of identification before accessing the system, significantly reduce the risk of unauthorised access.
Regular Software Updates and Patch Management
Manufacturers of IP phone systems frequently release software updates that include security patches to fix vulnerabilities that could be exploited by cyber attackers. Keeping the phone system's software up to date is essential for protecting against known threats. Establish a regular schedule for checking and applying software updates and patches as soon as they are released.
Secure Network Configurations
The network on which your IP phone system operates should be configured securely to shield it from external threats. Use network segmentation to separate voice traffic from other types of data traffic. This not only enhances performance by reducing congestion but also limits the potential impact of a security breach on other parts of the network.
Utilise Encryption for Voice Communications
Encrypting voice communications is a critical security measure for preventing eavesdropping and ensuring that data cannot be intercepted during transmission. Techniques such as Transport Layer Security (TLS) and Secure Real-Time Transport Protocol (SRTP) can encrypt both the signalling and the media, providing a robust security layer for voice communications
Comprehensive User Training and Awareness
Human error remains one of the most significant security vulnerabilities in any system. Providing comprehensive training for all users of the IP phone system is vital. Employees should be aware of potential security risks and best practices for safe usage. This includes recognising phishing attempts, managing passwords securely, and understanding how to use features without compromising security.
Conduct Regular Security Audits
Regular security audits of the IP phone system can help identify and address vulnerabilities before they can be exploited by attackers. Audits should assess the entire ecosystem, including the network environment, device configurations, and user access controls. This proactive approach ensures continuous improvement of security measures.
Develop and Enforce Security Policies
A well-defined security policy sets the foundation for safeguarding IP phone systems. This policy should outline acceptable usage, password management, update protocols, and response strategies for potential security incidents. Once developed, it is crucial to enforce these policies consistently and review them regularly to adapt to new threats.
Conclusio
Securing IP phone systems requires a multi-layered approach combining technology, user education, and comprehensive policy management. By implementing these best practices, businesses can significantly mitigate risks and protect their communication systems from cyber threats. At Yabbit, we are committed to providing secure and reliable IP phone systems tailored to meet the needs of modern businesses. Ensuring the security of these systems is not just about protecting data; it's about safeguarding your business's reputation and continuity. If you're looking to strengthen your communication systems with robust security measures, explore our solutions and discover how we can help you maintain a secure and efficient communication environment.
0 notes
Text
iHeal 5: Advanced ECG & PPG Wrist-Worn Health Watch

iHeal 5 Smartwatch
With the release of the ground-breaking iHeal 4 model, which enables users to track blood sugar levels on the wrist, Kospetiheal has caused a stir in the health monitor watch industry. With the updated iHeal 5, which has earned Level 2 medical certification for its dependability and practicality, iheal has continued to innovate and expanded its range of health monitoring watches.
The striking design and remarkable features of the iHeal 5 set it apart. It supports ECG, PPG, and blood glucose monitoring and has improved dynamic PD and blood oxygen sensors for heart rate. Medical-grade metal is used to make the metal sheet on the bottom case, while stainless steel and metal alloy are used to craft the bezel. The 1.43-inch AMOLED screen makes the user experience more intense and offers a roomy display.
iHeal 5 provides comprehensive insights for basic health monitoring, including real-time heart rate tracking, SpO2 measurement, sleep monitoring, body temperature, and blood pressure, in addition to heart-health related SINUS RHYTHM detection.
Like its more modern counterparts, the iHEAL 5 has more than 100 exercise modes that let users efficiently track and analyse their physical activity. It also has Bluetooth calling, which makes communication simple thanks to its integrated microphone and speaker.
Numerous useful features are also available on the iHeal5, including Smart Notifications, Find My Phone, Weather Updates, Sedentary Reminder, Music and Camera Controls, Timer, Stopwatch, and Alarm Clock. With a 440 mAh capacity and a 10-day and 30-day standby period, respectively, the battery ensures continuous use all day long.
There are two hues available: silver black and black. With New Year’s discounts starting at 30% off at $44.99, the iHeal 5 is now officially on sale for $149.99 in the official store, enabling customers to get the newest products at the lowest possible cost. This beautiful watch is a great option if you still need help choosing a holiday present. The vendor promises to ship it out two days after the order is placed. If you consider this, it might be the ideal holiday surprise!
PPG and ECG
Talking cards for Bluetooth screen
SMART WATCH AMLOED.
Make a Bluetooth call.
ECG surveillance.
Monitoring of heart rate
Monitoring of blood glucose.
Monitoring of health various modes of exercise.
Incredibly long range
Large 1.43-inch AMOLED screen
A crisp, high-definition display of images
Using a 1.43-inch AMOLED high-definition display screen to give you a crisper, more expansive visual experience High-sensitivity touch screen that offers consumers a distinctive and cutting-edge visual experience
Housing made of zinc alloy Fine workmanship
1.43-inch AMOLED high-definition touch screen with 3D glass coverage, borderless design concept A smooth, natural transition with a well-polished body that offers a wider perspective and improved design sense
Graphing ECG Data
Health tracking in real time with integrated sensors and ECG disease AI ECG screening with readability and support for ECGplayback medical reports
Alias: Android Waveform Report
Time of measurement: 2023-08-23 14:45:39
Heart Rate: 88 beats per minute
HRV: 3 ms, QT Interval: 414 ms
Lead: 1 25 mm/s is the speed.
Gain: 10 millimetres per minute
Frequency: Sine rhythm at 512 Hz.
There were no abnormalities seen on this ECG.
Human Cardiac Cycle Monitoring Principles of ECG
The human body’s pacing point, atria, and ventricles alternate during each cardiac cycle. When bioelectricity is produced, cardiac electricity is created from the corresponding bioelectricity changes.
Bluetooth telephony
Hands-free operation
One-click connect to your phone, promptly receive incoming calls on your watch, and respond with a single click Give up your hands whenever and wherever you are to listen more effectively, which will make it easier to handle a variety of situations and moods in life.
Raise your hand to see the details
The watch will vibrate to let you know when your phone rings or receives a message, even if it’s in your bag or you’re busy and don’t notice it. as soon as you raise your hand. The message appears on the watch when it lights up.
Tracking health throughout the day Heart health should always be considered
Even the smallest changes can be precisely sensed thanks to an integrated optical heart rate sensor and a mainstream intelligent heart rate algorithm. Understanding your heart rate is aided by continuous 24-hour heart rate monitoring.
Monitoring of blood oxygen levels
Monitor your level
Monitor your level of exercise intensity. Feedback With the newly upgraded red and the current heart rate value, you can further understand the state of your body and maintain your heart rate by raising your wrist to know the heart rate and using a frayed light sensor to measure blood oxygen saturation.
Health in your control, safeguarding your well-being
Tracking health throughout the day Heart health should always be considered. Even the smallest changes can be precisely sensed thanks to an integrated optical heart rate sensor and a mainstream intelligent heart rate algorithm. Understanding your heart rate is aided by continuous 24-hour heart rate monitoring.
Depending on the sport mode you select running, cycling, or ball play display the sports interface. To continuously assess your workout environment and modify your own Sports mode, you can turn on corresponding sports modes.
Still more features to discover
Viewing the BT Music Weather Calculator with AI Voice Assistant and Alarm Clock Women’s Concern Locate Your Phone Remind me of the event Shake to capture a picture Smart alarm clock Prolonged reminder chronometer, countdown, etc. More practical features are available for you to investigate.
Read more on govindhtech.com
0 notes
Text
Why Choose Datagram As Your Cisco Distributors in Dubai?
As it is needless to mention that the majority of the IT enterprises that have a strong networking infrastructure have witnessed a uniform upward graph, the necessity of opting for top-notch quality networking and security products, like the ones provided by Cisco, is extremely high. But, when it comes to choosing the best Cisco distributors, the companies have to be prudent enough to go ahead with a top player like Datagram – one of the leading suppliers of Cisco products in UAE, Africa, and MENA.
How Datagram can be a game-changer for IT Enterprises?
“Quality networking begets operating efficiency” – this mantra exactly points out why Datagram is one of the most trusted Cisco distributors in Dubai. Having large distribution and reseller networks, Datagram offers only products that undergo rigorous quality checks at very reasonable prices that comfortably fall under your budget.
All Cisco Products Under One Roof – Datagram
Being one of the largest Cisco distributors, Datagram is an all-encompassing house of Cisco products like Routers, Network Switches, Cisco Modules, Cards, Cisco Memory & Flash, Cisco Firewall, and Cisco Smartnet Service. All your needs for Cisco networking products will be well catered to, just reach out to the experts at Datagram.
Legacy of Datagram in IT Security & Networking Products
Possessing a lush clientele that includes Data Centres, Telecom Companies, Internet Service Providers (ISP), and ITES – Datagram has emerged as the most obvious choice for availing network security solutions (along with products mentioned above) like Servers, Storage, Controllers, Contact Centres, IP Telephony, Access Points, Wireless LAN, and other essential networking accessories.
Datagram – Acclaimed Cisco Distributors in Dubai
If you are looking for a much improved and efficient network ecosystem for your IT enterprise in Dubai, it’s very recommended to get Datagram onboard to provide the most comprehensive networking and IT security products and solutions.
With great solutions delivered by Datagram, you can target a much higher grab of sales, getting an enhanced IT networking experience
0 notes
Text
Advanced Structured Cabling Solutions by VAS Technologies in Dubai
In the dynamic landscape of modern business operations, having a robust and reliable structured cabling system is crucial. VAS Technologies, a pioneering company in Dubai, specializes in providing cutting-edge solutions for structured cabling in dubai, catering to the diverse needs of businesses across various industries. Leveraging advanced technologies and industry expertise, we offer tailored solutions to optimize network performance, enhance scalability, and ensure seamless connectivity.
Our Advanced Technologies:
Fiber Optic Solutions:
VAS Technologies employs state-of-the-art fiber optic technologies to deliver high-speed, low-latency connectivity solutions. Our fiber optic cabling infrastructure ensures superior bandwidth capabilities, ideal for supporting bandwidth-intensive applications and future scalability requirements.
We offer a comprehensive range of fiber optic solutions, including single-mode and multi-mode fiber installations, fusion splicing, termination, and testing services, tailored to meet the specific needs of our clients.
Structured Cabling Management Systems:
Our company utilizes advanced structured cabling management systems to streamline network organization and maintenance. Through the implementation of intelligent patching systems, cable management racks, and labeling solutions, we ensure efficient cable routing, easy troubleshooting, and simplified upgrades.
By adopting structured cabling management systems, businesses can minimize downtime, enhance network reliability, and facilitate smoother expansion as their infrastructure grows.
Power over Ethernet (PoE) Solutions:
VAS Technologies integrates Power over Ethernet (PoE) solutions into structured cabling designs to provide power and data connectivity over a single Ethernet cable. This technology eliminates the need for separate power sources, reducing installation complexity and costs.
PoE solutions offered by VAS Technologies are suitable for various applications, including IP telephony, surveillance cameras, wireless access points, and IoT devices, enabling efficient deployment and management of networked devices.
Network Security and Surveillance Integration:
Recognizing the importance of network security, VAS Technologies integrates advanced surveillance and security solutions into structured cabling infrastructures. We offer IP-based surveillance camera systems, access control solutions, and intrusion detection systems to safeguard network assets and premises.
Our integrated approach ensures seamless compatibility between security systems and structured cabling networks, enabling centralized management and proactive threat detection.
Wireless Infrastructure Solutions:
VAS Technologies designs and deploys robust wireless infrastructure solutions to complement structured cabling networks. Our wireless solutions leverage the latest technologies, such as Wi-Fi 6 and mesh networking, to deliver high-performance wireless connectivity throughout the premises.
By combining structured cabling with wireless infrastructure, we provide comprehensive coverage and seamless roaming capabilities, enhancing user experience and productivity in diverse environments.
Conclusion:
In conclusion, VAS Technologies stands at the forefront of delivering advanced structured cabling solutions tailored to the unique requirements of businesses in Dubai. By harnessing the latest technologies and industry best practices, we empower organizations to build agile, scalable, and resilient network infrastructures that drive innovation and growth. Partner with VAS Technologies for the structured cabling company in dubai that pave the way for success in the digital era.
0 notes
Text
Unlocking the Potential of Audio Data Collection in Advancing Technology
In today's digital age, the collection and analysis of audio data have become instrumental in driving technological advancements. Audio data collection involves gathering and processing sound recordings from various sources to train and improve speech recognition systems, enhance audio quality, and develop innovative applications. This article explores the importance of audio data collection, methods used, challenges faced, and future prospects in this field.
The Importance of Audio Data Collection
Audio data collection plays a critical role in improving the accuracy and efficiency of speech recognition systems and other audio-based technologies. By analysing a diverse range of audio samples, researchers and developers can better understand speech patterns, improve voice quality, and enhance user experience. This data is also used in fields such as healthcare, finance, and security for tasks like voice authentication, sentiment analysis, and sound event detection.
Methods of Audio Data Collection
Field Recording: This method involves capturing audio in real-world environments, such as offices, homes, or public spaces. Field recordings provide authentic and diverse audio samples for analysis.
Controlled Recording: In controlled recording environments, participants are asked to speak or perform specific tasks, ensuring high-quality audio recordings with minimal background noise.
Crowdsourcing: Audio data can be collected from a large number of volunteers through online platforms, providing a vast and diverse dataset for analysis.
Telephony Data: Call centres and customer service lines are valuable sources of audio data, offering real-life interactions and a variety of speech patterns for analysis.
Challenges in Audio Data Collection
Despite its importance, audio data collection presents several challenges:
Privacy Concerns: Ensuring the privacy and security of audio recordings is crucial, requiring compliance with data protection regulations and ethical guidelines.
Data Quality: Maintaining high-quality audio recordings is essential for accurate analysis, requiring noise reduction and clear sound capture techniques.
Diversity: Collecting audio data that represents a wide range of languages, accents, and dialects is challenging but necessary for developing inclusive audio technologies.
Future Prospects
As technology advances, audio data collection will continue to play a crucial role in driving innovation. Advancements in machine learning and artificial intelligence will enhance the accuracy and efficiency of speech recognition systems and other audio-based applications. The future holds the promise of more personalised and context-aware audio technologies, improving accessibility and usability for all users.
Conclusion
Audio data collection is a key driver of technological advancement, enabling the development of more accurate and efficient speech recognition systems and other audio-based applications. As technology evolves, the importance of collecting diverse and high-quality audio data will only increase, leading to more innovative and inclusive audio technologies.
0 notes
Text

Enhancing Business Communication with VoIP Technology: A Comprehensive Guide by Pereira LLC
Introduction: In today's fast-paced business world, effective communication is crucial for success. As businesses strive to stay connected and collaborate seamlessly, VoIP (Voice over Internet Protocol) technology emerges as a powerful solution. At Pereira LLC, we recognize the transformative potential of VoIP technology in revolutionizing business communication. In this comprehensive guide, we explore the intricacies of VoIP technology, its benefits, implementation strategies, and best practices for leveraging it to enhance business communication.
Chapter 1: Understanding VoIP Technology In this chapter, we provide an overview of VoIP technology, explaining how it enables voice communication over the internet or IP networks. We delve into the underlying principles of VoIP, including packet-switching, codecs, and signaling protocols. Additionally, we discuss the evolution of VoIP technology and its integration with traditional telephony systems, highlighting its role in modernizing communication infrastructure.
Chapter 2: Benefits of VoIP Technology VoIP technology offers numerous benefits for businesses seeking to optimize their communication systems. In this chapter, we explore the advantages of VoIP, including cost savings, scalability, flexibility, and advanced features. We discuss how VoIP enables businesses to reduce communication costs, expand their reach, and enhance collaboration through features such as video conferencing, voicemail-to-email transcription, and mobile integration.
Chapter 3: Implementation Strategies Implementing VoIP technology requires careful planning and execution to ensure seamless integration and optimal performance. In this chapter, we provide a step-by-step guide to implementing VoIP systems, including assessing business needs, selecting the right VoIP provider, evaluating network infrastructure, and configuring VoIP hardware and software. We also discuss common challenges and best practices for successful VoIP implementation.
Chapter 4: VoIP Security Considerations Security is a critical consideration when implementing VoIP technology to protect sensitive business communication. In this chapter, we examine the security risks associated with VoIP, such as eavesdropping, unauthorized access, and denial-of-service attacks. We discuss strategies for securing VoIP systems, including encryption, authentication, access control, and network monitoring. By implementing robust security measures, businesses can safeguard their VoIP infrastructure and protect against potential threats.
Chapter 5: Maximizing VoIP Performance To maximize the performance of VoIP systems, businesses must optimize network infrastructure and address potential bottlenecks. In this chapter, we explore techniques for optimizing network bandwidth, reducing latency and jitter, and prioritizing VoIP traffic. We also discuss Quality of Service (QoS) mechanisms and traffic management strategies to ensure reliable and high-quality voice communication.
Chapter 6: Future Trends in VoIP Technology As technology continues to evolve, VoIP is poised to undergo further advancements and innovations. In this chapter, we explore emerging trends in VoIP technology, such as WebRTC, artificial intelligence, and cloud-based VoIP solutions. We discuss how these developments are shaping the future of business communication and providing new opportunities for organizations to improve efficiency and productivity.
Conclusion: In conclusion, VoIP technology offers a transformative solution for enhancing business communication in the digital age. By understanding the fundamentals of VoIP, leveraging its benefits, implementing robust security measures, and optimizing performance, businesses can unlock new possibilities for collaboration and innovation. At Pereira LLC, we are committed to helping businesses harness the power of VoIP technology to achieve their communication goals and drive success in today's dynamic business environment.
1 note
·
View note
Text
Dinstar GSM Gateway
The Dinstar GSM Gateway is a critical component in the realm of telecommunication solutions, enabling seamless connectivity between the GSM network and VoIP infrastructure. In this essay, we will delve into the intricacies of the Dinstar GSM Gateway and its significance in modern communication systems.
The Dinstar GSM Gateway is a versatile device designed to bridge the gap between traditional GSM networks and modern VoIP systems. It serves as a gateway for routing voice and SMS traffic between the two networks, thereby facilitating cost-effective communication solutions for businesses and individuals alike. The gateway is equipped with multiple SIM card slots, enabling it to handle a large volume of calls and messages concurrently. Additionally, it supports various codecs and protocols, ensuring compatibility with a wide range of telephony equipment and software

The Dinstar Gateways boasts a plethora of features that contribute to its effectiveness in telecommunication environments. These features include but are not limited to:
- SIM Card Management: The gateway supports hot-swappable SIM cards, allowing for easy management and replacement without interrupting ongoing communications.
- Call Routing: It offers flexible call routing capabilities, enabling users to define routing rules based on factors such as caller ID, time of day, and destination number.
- SMS Services: In addition to voice calls, the gateway facilitates the exchange of SMS messages between GSM and VoIP networks, opening up new avenues for business communication.
- Web-based Management: The device can be configured and monitored through a user-friendly web interface, providing administrators with comprehensive control over its operation

The Dinstar GSM Gateway by Dcnet Solutions finds application in diverse deployment scenarios, catering to the communication needs of various industries and organizations. Some common deployment scenarios include:
- Call Centers: The gateway can be integrated into call center environments to facilitate outbound and inbound calls over GSM networks, offering a cost-effective alternative to traditional landline connections.
- Remote Locations: In areas with limited or unreliable internet connectivity, the gateway serves as a reliable means of communication by leveraging the widespread coverage of GSM networks.
- VoIP Service Providers: Telecommunication service providers can utilize the gateway to extend their services to GSM users, expanding their reach and enhancing their service offerings.

In conclusion, the Dinstar GSM Gateway stands as a testament to the convergence of traditional and modern telecommunication technologies, offering a bridge between GSM and VoIP networks. Its partnership with DCNet Solutions further amplifies its accessibility and value, empowering businesses to embrace cost-effective and resilient communication solutions.
Dinstar GSM Gateway and its collaboration with DCNet Solutions are poised to play a pivotal role in shaping the future of connectivity and collaboration.
For more details,
Contact Dcnet Solutions: +91 99451 60901
Also read about Voip Service Provider India
#dcnet solutions#dinstar gsm gateway#dinstar fxo gateway#dinstar fxs gateway#Dinstar India#Dinstar Gateways
0 notes
Text
Maximize Communication: Full Duplex vs. Half Duplex Demystified
In the realm of communication, understanding the dynamics between full duplex and half duplex is paramount. Full duplex communication allows simultaneous transmission and reception of data, akin to a two-way street where information flows seamlessly in both directions, fostering real-time interaction and feedback. Conversely, half duplex communication permits data transmission in either direction, but not simultaneously, akin to a single-lane road where traffic alternates, creating potential delays and interruptions. The choice between Full duplex vs half duplex hinges on specific needs and constraints; while full duplex offers immediate and continuous exchange, ideal for scenarios demanding swift and constant interaction such as telephony and video conferencing, half duplex finds utility in situations where bandwidth or infrastructure limitations necessitate a more controlled flow of information, like walkie-talkies or Ethernet networks. Each possesses its strengths and limitations, underscoring the importance of selecting the appropriate mode to optimize communication efficiency and effectiveness in diverse contexts.
#fullduplexvshalfduplex#halfduplexcommunication#fullduplexcommunication#halfduplexmode#fullduplexmode#halfduplexnetwork
0 notes
Link
0 notes