#IoT network protocols (e.g.
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
cómo instalar una vpn en un router
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
cómo instalar una vpn en un router
VPN router setup
Setting up a VPN router can greatly enhance your online privacy and security by encrypting all the internet traffic that passes through your network. This means that not only your computer or mobile device will be protected, but all devices connected to the router will benefit from VPN encryption, including smart TVs, gaming consoles, and IoT devices.
To set up a VPN router, you'll first need to choose a suitable router that supports VPN connections. Many modern routers come with built-in VPN capabilities, while others may require you to install third-party firmware like DD-WRT or Tomato to enable VPN functionality.
Once you have your router, follow these general steps to set up a VPN:
Choose a VPN provider: Select a reputable VPN service that offers router support. Make sure they provide detailed instructions for setting up their VPN on various router models.
Configure your router: Access your router's settings through a web browser and navigate to the VPN section. Enter the connection details provided by your VPN provider, including the server address, username, and password.
Test the connection: Once configured, test the VPN connection to ensure it's working correctly. You can do this by connecting a device to your router's Wi-Fi network and visiting a website like WhatIsMyIP.com to verify that your IP address has changed.
Optimize settings: Depending on your router and VPN provider, you may have additional options to customize your VPN connection, such as choosing encryption protocols or enabling a kill switch feature to automatically disconnect internet access if the VPN connection drops.
Connect your devices: Once the VPN router is set up, connect all your devices to the router's Wi-Fi network or via Ethernet cable to enjoy encrypted internet access on all devices.
By setting up a VPN router, you can protect your entire home network from online threats and enjoy the benefits of a secure and private internet connection.
Router VPN installation
Title: A Comprehensive Guide to Router VPN Installation
In today's digital age, ensuring online privacy and security has become paramount. One effective solution is to set up a Virtual Private Network (VPN) directly on your router. This not only protects your entire network but also encrypts all data transmitted between your devices and the internet. Here's a step-by-step guide to help you seamlessly install a VPN on your router.
Choose a Compatible Router: Not all routers support VPN installations. Ensure yours does by checking the manufacturer's specifications or consulting their customer support.
Select a VPN Service: Research and choose a reliable VPN service provider that offers router compatibility. Look for features like strong encryption, a wide server network, and good customer support.
Prepare Your Router: Access your router's settings by typing its IP address into a web browser. Log in using your administrator credentials.
Update Firmware (if necessary): Ensure your router's firmware is up to date to avoid compatibility issues and security vulnerabilities.
Configure VPN Settings: Locate the VPN settings section in your router's admin panel. Enter the details provided by your VPN service, including server address, username, and password.
Customize VPN Options (optional): Depending on your router model, you may have additional VPN configuration options such as protocol selection (e.g., OpenVPN, PPTP, L2TP/IPsec), encryption strength, and DNS settings.
Test Connection: Once configured, save the settings and reboot your router. Test the VPN connection to ensure it's working correctly by accessing a website that displays your IP address before and after connecting to the VPN.
Enjoy Secure Browsing: Congratulations! Your router VPN installation is complete. Now, all devices connected to your network benefit from encrypted internet traffic and enhanced privacy.
By following these steps, you can safeguard your online activities and enjoy a secure browsing experience for all your devices connected to your home or office network.
Configuring VPN on router
Configuring a Virtual Private Network (VPN) on your router can provide enhanced security and privacy for your internet connection. By setting up a VPN on your router, all devices connected to the network can benefit from the encrypted tunnel that shields your online activities from prying eyes.
To configure a VPN on your router, you will first need to choose a VPN service provider that offers router support. Most major VPN providers offer detailed guides on how to set up their service on different types of routers. Once you have subscribed to a VPN service, you can proceed with the configuration process.
The exact steps for configuring a VPN on your router may vary depending on the model and brand you are using. In general, you will need to log in to your router's admin panel using a web browser, locate the VPN settings, and input the necessary information provided by your VPN service provider.
After entering the required details, such as the server address, username, and password, you can save the settings and establish a connection to the VPN server. Once the connection is established, all internet traffic flowing through your router will be encrypted, providing you with a secure and private browsing experience.
It is essential to regularly update your router's firmware and the VPN client to ensure optimal performance and security. Additionally, you may need to troubleshoot any connectivity issues that may arise during the configuration process to enjoy seamless VPN protection on all your connected devices.
VPN router tutorial
A Virtual Private Network (VPN) router can be a valuable tool to protect your online privacy and security. By setting up a VPN on your router, you can encrypt all the internet traffic from devices connected to your network, providing an extra layer of protection against cyber threats and surveillance.
To set up a VPN router, you first need to choose a VPN service provider that offers router support. Once you have signed up for a VPN service, you can usually download the necessary configuration files from the provider's website. Next, access your router's settings by typing its IP address into a web browser. Look for the VPN section in the settings menu and upload the configuration files provided by your VPN service.
After configuring the VPN on your router, you can connect all your devices to the secure network. This means that any internet traffic flowing through the router will be encrypted and routed through the VPN server, hiding your IP address and location from prying eyes.
Using a VPN router is particularly useful if you have multiple devices that need protection, such as smartphones, tablets, computers, and smart home devices. It ensures that all your online activities are safeguarded without the need to install a VPN app on each individual device.
In conclusion, setting up a VPN router can enhance your online security and privacy by encrypting all internet traffic from devices connected to your network. It's a convenient way to protect your data and anonymity without compromising on performance.
Setting up VPN on router
Setting up a VPN on your router is a valuable way to enhance your online security and privacy. By doing so, you can encrypt all the internet traffic from your devices that connect to the router, ensuring that your data remains confidential and protected from potential security threats.
To set up a VPN on your router, you will first need to choose a VPN service provider that supports router connections. It is essential to select a reliable and reputable VPN provider to guarantee the effectiveness of the service. Once you have subscribed to a VPN service, the provider will offer instructions and support for setting up the VPN on your router.
The process typically involves logging into your router's admin panel and accessing the VPN settings. Here, you will need to enter the VPN configuration details provided by your VPN service provider, such as server addresses and authentication protocols. After inputting the necessary information, you can save the settings and establish a secure VPN connection through your router.
Setting up a VPN on your router offers several benefits, including safeguarding your online activities from hackers, protecting sensitive data, and bypassing geographic restrictions for streaming services. Additionally, VPN routers provide an added layer of security for all connected devices, such as smartphones, computers, and smart home devices.
In conclusion, setting up a VPN on your router is a practical way to ensure the privacy and security of your internet connection. By following the guidelines provided by your VPN service provider, you can enjoy a safer and more secure online experience for all your devices.
0 notes
Text
can you install a vpn on your rotter
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you install a vpn on your rotter
VPN installation on router
Title: Streamline Your Security: A Guide to VPN Installation on Your Router
In today's digital landscape, ensuring online privacy and security is paramount. Virtual Private Networks (VPNs) offer a powerful solution, encrypting your internet connection and masking your IP address. While installing a VPN on individual devices is common practice, configuring it at the router level can provide comprehensive protection for all devices connected to your network. Here's a step-by-step guide on how to set up a VPN on your router:
Choose a VPN Provider: Select a reputable VPN service provider that offers router compatibility and robust security features. Look for providers with user-friendly interfaces and excellent customer support.
Verify Router Compatibility: Not all routers support VPN installations. Check your router's specifications or contact the manufacturer to ensure compatibility. Popular router brands like Asus, Netgear, and Linksys often have models that support VPN configurations.
Access Router Settings: Log in to your router's admin panel using a web browser and the router's IP address. This information is typically found on the router itself or in the user manual. Enter your username and password to access the settings.
Install VPN Firmware: Some VPN providers offer custom firmware for certain router models, simplifying the installation process. Follow the instructions provided by your VPN provider to flash your router with the custom firmware.
Configure VPN Settings: Once the firmware is installed, navigate to the VPN settings section on your router's admin panel. Enter the VPN server information provided by your VPN provider, including the server address, username, and password.
Test the Connection: After configuring the VPN settings, save the changes and restart your router. Connect a device to your network and verify that the VPN is working correctly by checking your IP address and running a DNS leak test.
By installing a VPN on your router, you can safeguard your entire network, including smartphones, tablets, smart TVs, and IoT devices, with just a single setup. Take control of your online privacy and security today with a VPN-enabled router.
Router VPN setup guide
Title: A Comprehensive Router VPN Setup Guide: Safeguarding Your Online Privacy
In an age where cybersecurity threats loom large and privacy concerns are paramount, setting up a VPN (Virtual Private Network) on your router is a smart move to ensure your online activities remain secure and private. By encrypting your internet connection, a VPN shields your data from prying eyes, whether you're browsing, streaming, or conducting sensitive transactions. Below is a step-by-step guide to help you set up a VPN on your router effectively.
Choose a Compatible Router: Not all routers support VPN configurations. Check if your router model is compatible with VPN services. Popular options include Asus, Linksys, Netgear, and TP-Link routers, among others.
Select a VPN Provider: Research and choose a reliable VPN provider that offers router compatibility. Ensure they provide detailed setup instructions and robust security features.
Access Router Settings: Log in to your router's admin panel using a web browser. Typically, you'll enter the router's IP address (e.g., 192.168.1.1) in the address bar and log in with your credentials.
Enable VPN Client Support: Navigate to the VPN or WAN settings section in your router's dashboard. Enable VPN client support and enter the VPN provider's details, including server addresses, protocols (e.g., OpenVPN), and login credentials.
Configure VPN Settings: Customize VPN settings according to your preferences, such as encryption levels and VPN protocols. These settings may vary depending on your VPN provider's recommendations.
Test Your Connection: After configuring the VPN settings, test your connection to ensure everything is working correctly. Verify your IP address and check for any DNS leaks using online tools.
Connect Devices to VPN: Once the setup is complete, connect your devices to the VPN-enabled router. All internet traffic from these devices will now be encrypted and routed through the VPN server.
By following these steps, you can establish a secure VPN connection on your router, safeguarding your online privacy and enhancing your digital security. Remember to regularly update your router firmware and VPN software for optimal performance and protection against emerging threats.
Installing VPN on router tutorial
A VPN (Virtual Private Network) is a tool that helps secure and encrypt your internet connection, providing you with online privacy and anonymity. By installing a VPN on your router, you can protect all devices connected to your network, including smartphones, laptops, smart TVs, and more.
To install a VPN on your router, follow these steps:
Choose a compatible VPN service that offers router support. Not all VPN providers support router installations, so make sure to select one that does.
Access your router's settings by typing its IP address into your web browser. The IP address is typically found on the back of your router or in the user manual.
Log in to your router using the administrator credentials. This information is also usually located on the router or in the manual.
Locate the VPN section in your router settings. This can vary depending on the router model, but it is often found under the "Advanced" or "Security" tab.
Enter the VPN configuration details provided by your VPN service, including the server address, username, and password.
Save the settings and connect to the VPN server. Your router is now configured to use the VPN, encrypting all incoming and outgoing internet traffic.
By installing a VPN on your router, you can protect your entire network from cyber threats and enjoy a secure and private internet experience on all your devices.
How to set up VPN on router
Setting up a VPN on your router can provide secure and encrypted internet access for all devices connected to your home network. This added layer of security protects your online privacy and data from potential cyber threats. Here's a step-by-step guide on how to set up a VPN on your router:
Choose a VPN service: First, you need to select a reliable VPN service provider that offers router support. Ensure the VPN service is compatible with your router model.
Access your router settings: Open a web browser on a device connected to your router and type in the router's IP address to access its settings. You may need to enter a username and password to log in.
Install VPN firmware: Some routers support VPN installation using custom firmware such as DD-WRT or Tomato. Follow the instructions provided by your VPN service on how to install the firmware on your router.
Configure VPN settings: Once the firmware is installed, access the VPN settings on your router and enter the connection details provided by your VPN service, including server address, username, and password.
Connect to the VPN: Save the settings on your router and establish a connection to the VPN server. Once connected, all devices on your home network will be protected by the VPN.
Test the connection: Verify the VPN connection by visiting a website that shows your IP address. It should display the VPN server's IP address instead of your actual IP.
Setting up a VPN on your router enhances your online security and privacy, ensuring a safe browsing experience for all devices connected to your network.
VPN configuration for router
Title: Secure Your Entire Network: A Guide to VPN Configuration for Your Router
In today's digital landscape, safeguarding your online privacy and security is paramount. With cyber threats on the rise, individuals and businesses alike are turning to Virtual Private Networks (VPNs) as a crucial tool for protecting their sensitive data. While VPNs are commonly used on individual devices, configuring your router to use a VPN extends those benefits to your entire network, ensuring comprehensive protection for all connected devices.
Setting up a VPN on your router offers several advantages. Firstly, it encrypts all data traffic passing through your network, shielding it from prying eyes and potential hackers. This encryption is particularly vital when accessing public Wi-Fi networks, which are notorious for their lack of security. Additionally, a router-level VPN setup enables you to bypass geographical restrictions and access region-locked content on all devices connected to your network.
The process of configuring a VPN on your router may vary depending on the make and model of your device. However, the general steps remain consistent. Begin by selecting a reputable VPN service provider that offers router support and follow their instructions for setting up your router. This typically involves accessing your router's admin panel, entering the VPN credentials provided by your provider, and configuring the appropriate settings.
Once your VPN is successfully configured on your router, all devices connected to your network will benefit from its protection automatically. This includes smartphones, tablets, computers, smart TVs, and any other internet-enabled devices. You can rest assured knowing that your entire network is secured against online threats and your privacy remains intact.
In conclusion, configuring a VPN on your router is a proactive measure to safeguard your digital life. By encrypting all data traffic and providing access to region-restricted content, a router-level VPN setup ensures comprehensive protection for your entire network. Take control of your online security today by implementing a VPN configuration for your router.
0 notes
Text
9 Essential Criteria for Partner Selection in Enterprise IoT – Avigna
Enterprise IoT solutions - Enterprise IoT projects are complex endeavors that require collaboration with the right partners to ensure success. Choosing a vendor or partner for hardware

Enterprise IoT (Internet of Things) solutions refer to the integration of IoT technologies into the operations and processes of large organizations or enterprises. IoT involves connecting devices, sensors, and systems to the internet to collect and exchange data, enabling improved decision-making, automation, and efficiency. Here are key components and considerations for implementing enterprise IoT solutions:
Devices and Sensors:
Choose appropriate IoT devices and sensors based on the specific needs of your enterprise.
Ensure compatibility and standardization for seamless integration.
Consider factors like power consumption, connectivity options, and data transmission capabilities.
Connectivity:
Select reliable and secure communication protocols (e.g., MQTT, CoAP, HTTP) for connecting IoT devices.
Implement robust networking solutions to ensure constant and stable connectivity.
Evaluate the need for edge computing to process data locally and reduce latency.
Data Management and Analytics:
Develop a strategy for collecting, storing, and managing large volumes of IoT data.
Implement analytics tools and platforms to derive actionable insights from the collected data.
Utilize machine learning algorithms for predictive analytics and anomaly detection.
Security:
Implement strong security measures to protect IoT devices, networks, and data.
Use encryption, secure authentication, and regular security updates to safeguard against potential threats.
Establish secure device onboarding and lifecycle management practices.
Integration with Existing Systems:
Ensure seamless integration with existing enterprise systems such as ERP (Enterprise Resource Planning), CRM (Customer Relationship Management), and other business applications.
Leverage APIs (Application Programming Interfaces) for interoperability and data exchange.
Scalability:
Design the IoT solution with scalability in mind to accommodate future growth.
Consider the ability to add new devices and sensors without major disruptions to the existing infrastructure.
Regulatory Compliance:
Stay informed about regulations and standards related to IoT in your industry.
Ensure that your IoT solution complies with data privacy and security regulations.
User Interface and Experience:
Develop user-friendly interfaces for monitoring and managing IoT devices and data.
Provide dashboards, analytics tools, and notifications for better user experience.
Maintenance and Updates:
Establish a plan for regular maintenance and updates of IoT devices and software.
Implement over-the-air (OTA) updates to remotely update firmware and software.
Cost Management:
Evaluate the total cost of ownership (TCO) of the IoT solution, considering initial setup costs, maintenance, and potential upgrades.
Look for cost-effective and scalable solutions that align with your budget.
Implementing enterprise IoT solutions requires a comprehensive approach, involving collaboration between IT, operations, and other relevant departments to ensure successful deployment and integration into the existing business processes.
Website: - https://avigna.ai/9-essential-criteria-for-partner-selection-in-enterprise-iot/
0 notes
Text
Blockchain: Beyond the Buzzword
Demystifying the Distributed Ledger Technology Revolutionizing Our World
Blockchain has become a ubiquitous buzzword in recent years, often associated with cryptocurrencies like Bitcoin. But blockchain technology is much more than just the backbone of digital currencies. It's a revolutionary distributed ledger technology poised to transform various industries, from finance and healthcare to supply chain management and voting systems.
What is Blockchain?
Imagine a giant, decentralized record book accessible to everyone but tamper-proof. That's essentially what a blockchain is. It's a digital ledger of transactions or data entries duplicated and distributed across a network of computer systems. Each entry, or block, contains information (data) timestamped and cryptographically linked to the previous block, creating an immutable chain of records.
How Does Blockchain Work?
Here's a simplified breakdown of the blockchain process:
Transaction Initiation: A transaction occurs on the network.
Block Creation: The transaction data is bundled into a block.
Hashing and Cryptographic Linking: Each block is assigned a unique digital fingerprint (hash) and linked to the previous block's hash, creating a chain.
Network Distribution: The block is broadcast to all nodes on the network for verification.
Consensus Mechanism: Nodes validate the transaction data and add the block to their local copies of the ledger only if consensus is reached (e.g., through majority vote).
Key Features of Blockchain Technology
Decentralization: No single entity controls the ledger, making it resistant to manipulation or fraud.
Transparency: All transactions are visible to all participants on the network, ensuring trust and accountability.
Immutability: Once recorded, data cannot be altered or deleted, guaranteeing data integrity.
Security: Cryptographic hashing and consensus mechanisms make it incredibly difficult to tamper with the data.
Benefits of Blockchain Technology
The potential applications of blockchain extend far beyond cryptocurrencies. Here are some of the key benefits it offers:
Enhanced Security and Trust: Blockchain provides a secure and transparent way to store and share data, reducing the risk of fraud and errors.
Streamlined Processes: Automation of manual tasks and processes through smart contracts can lead to significant efficiency gains.
Improved Traceability and Transparency: Blockchain enables real-time tracking of goods and assets, enhancing supply chain visibility and accountability.
Empowerment and Inclusion: Blockchain can provide secure and accessible platforms for individuals and communities to participate in the digital economy.
The Future of Blockchain

While still in its early stages of development, blockchain technology has the potential to disrupt numerous industries and reshape our digital world. Some exciting areas of exploration include:
Decentralized Finance (DeFi): Creating a new financial system built on peer-to-peer transactions and open-source protocols.
Central Bank Digital Currencies (CBDCs): Exploring the potential of government-backed digital currencies powered by blockchain technology.
Internet of Things (IoT): Securing and managing data generated by the ever-growing network of connected devices.
Voting Systems: Enhancing the security and transparency of elections through blockchain-based voting platforms.
As blockchain technology continues to evolve and mature, we can expect even more innovative applications to emerge, transforming the way we live, work, and interact with each other.
Getting Started with Blockchain
If you're interested in learning more about blockchain, here are some resources to get you started:
Online courses and tutorials: Several platforms offer beginner-friendly courses and tutorials on blockchain technology and its applications.
Blockchain communities and forums: Connect with other blockchain enthusiasts and experts online to learn from their experiences and insights.
Books and articles: Numerous books and articles delve deeper into the technical aspects and potential of blockchain technology.
Remember, blockchain is a complex and rapidly evolving field. Don't be afraid to ask questions, explore different resources, and stay up-to-date on the latest developments.
Embrace the potential of blockchain technology and join the movement towards a more secure, transparent, and decentralized future!
0 notes
Text
BLIIoT|BL100 Collect Mitsubishi PLC Data Through Modbus Protocol
The meaning of Collect Mitsubishi PLC data through Modbus protocol
By implementing Modbus communication on a Mitsubishi PLC, you can establish a connection with a Modbus master device or software, allowing you to read and write data from/to the PLC. This enables you to collect various types of data from the Mitsubishi PLC, such as input and output status, register values, diagnostic information, and other relevant data points.
The Modbus protocol defines different function codes that specify the type of data access, such as reading coils, reading holding registers, writing single registers, etc. These function codes are used by the Modbus master to send requests to the Mitsubishi PLC, and the PLC responds with the requested data.
Collecting Mitsubishi PLC data through the Modbus protocol is beneficial for various purposes, including data monitoring, process control, data analysis, and integration with other systems. It allows you to gather real-time information from the PLC, enabling you to make informed decisions, troubleshoot issues, optimize processes, and integrate the PLC with other devices or software systems in your automation infrastructure.
Product introduction
The Modbus to MQTT Gateway BL100 is a cost-effective Industrial Gateway, special for converting Modbus RTU to MQTT Protocol, supports Huawei IoT Cloud, BLIIOT Cloud, Aliyun, and other MQTT Protocol Cloud Platform.
BL100 supports Modbus RTU to MQTT protocol conversion; Wireless transparent transmission of various protocols to cloud; Can be used as Modbus Master/Slave, 2 RS485 make it possible to providing data to PLC/HMI while collecting RS485 instrument data, and then connect to the cloud platform through 4G; 32 devices and 320 variables collect simultaneously; Support 10 user numbers for receiving SMS alarms for device dropouts, serial data overruns, and abnormalities;
Practical Application
1. Check PLC Compatibility: Ensure that your Mitsubishi PLC supports Modbus communication. Some Mitsubishi PLC models have built-in Modbus communication capabilities, while others may require additional communication modules.
2. Configure PLC Settings: Set up the communication parameters on the Mitsubishi PLC. This includes configuring the Modbus communication protocol, such as the baud rate, parity, data bits, and stop bits. Refer to the PLC's user manual or programming software for instructions on configuring Modbus communication settings.
3. Connect the PLC to Modbus Network: Establish a physical connection between the Mitsubishi PLC and the Modbus network. This can be done using RS-485 or Ethernet, depending on the communication module or interface supported by your PLC model.
4. Modbus Master Configuration: Set up a Modbus master device or software that will communicate with the Mitsubishi PLC. The Modbus master can be a PC-based software application or a dedicated hardware device. Configure the Modbus master with the appropriate communication parameters, such as the PLC's Modbus address and communication protocol details.
5. Read/Write Data: Use the Modbus master to read or write data from/to the Mitsubishi PLC. Modbus function codes are used to specify the type of data access (e.g., read coils, read holding registers, write single register, etc.). The Modbus master sends requests to the PLC, and the PLC responds with the requested data.
6. Process the Data: Once the Modbus master receives the data from the Mitsubishi PLC, you can process and utilize it as per your application requirements. This may involve storing the data in a database, displaying it on a user interface, or performing further calculations or analysis.



0 notes
Text
How does the LoRa module work?
A LoRa module is a device that enables long-range wireless communication using the LoRa (Long Range) technology. Here's how it works:

Modulation Technique: LoRa stands for "Long Range," and it's known for its ability to transmit data over long distances while conserving power. The key to LoRa's success is its modulation technique. It uses a method called Chirp Spread Spectrum (CSS), where the data is encoded by varying the frequency of the transmitted signal over time. This allows LoRa devices to achieve both long-range communication and excellent signal penetration through obstacles like buildings.
Transmitter: When you want to send data from a LoRa module, the transmitter encodes the data and converts it into a series of chirps. These chirps are transmitted over a specific frequency band (e.g., 868 MHz, 915 MHz), which can vary depending on the region where the device is operating.
Receiver: On the receiving end, another LoRa module or gateway is tuned to the same frequency band and listens for incoming chirps. The receiver demodulates the chirps to extract the original data.
Data Rate and Range: LoRa technology allows for various data rates, which are chosen based on the communication range and the data's priority. Lower data rates provide longer range but lower data throughput, while higher data rates sacrifice some range for faster communication.
Spread Spectrum: LoRa uses spread spectrum technology, meaning the signal spreads out over a wide frequency band. This spreading of the signal helps make LoRa more resilient to interference and noise, which is crucial for long-range communication.
Low Power: LoRa is designed for low-power, battery-operated devices. The energy-efficient nature of LoRa technology allows these devices to operate for extended periods without frequent battery replacement or recharging.
LoRaWAN Network: In many cases, LoRa modules are used in conjunction with a LoRaWAN network. LoRaWAN is a protocol that defines how data is organized and communicated between devices and gateways. It enables the connection of LoRa devices to the internet, typically using gateways that collect data from multiple devices and forward it to a central server or cloud application.
In summary, LoRa modules operate by using Chirp Spread Spectrum modulation to transmit data over long distances while conserving power. They can be used for a variety of IoT applications, including smart agriculture, industrial monitoring, smart cities, and more, making them a popular choice for long-range, low-power wireless communication.
0 notes
Text
Transforming Healthcare: The Internet of Healthcare Things (IoHT) Revolution

The Internet of Healthcare Things (IoHT), also known as the Internet of Medical Things (IoMT), is reshaping the healthcare landscape. It involves a network of interconnected devices designed to store and transmit patient information securely, offering unprecedented opportunities for improving patient care, enhancing medical practices, and even transforming the health insurance industry.
In this comprehensive guide, we explore the diverse applications of IoHT, its advantages, challenges, and the latest trends shaping the healthcare sector.
What is IoHT?
IoHT, short for the Internet of Healthcare Things, is a network of interconnected computing devices utilized for storing and transmitting patient information. These devices include ingestible sensors that use the FHIR protocol to communicate data over the internet, ultimately creating a digital patient care record.
Applications of IoT in Healthcare:
For Patients: IoHT empowers patients with personalized care through wearable devices such as fitness bands and wireless monitoring equipment. These devices, including blood pressure and heart rate monitors, can send reminders, track vital signs, and provide continuous medical monitoring. This technology is particularly transformative for elderly patients and individuals living alone, offering a safety net for their health.
For Physicians: IoHT enables physicians to monitor patients more effectively by leveraging wearables and home monitoring devices. Physicians can track treatment adherence and assess the need for emergency care, leading to proactive healthcare interventions. Data from IoT devices enhances communication between medical professionals and patients, facilitating more tailored treatment plans and improved outcomes.
For Health Insurance Companies: Health insurers benefit from IoT-connected devices by using health monitoring data for underwriting and claims processing. This data aids in identifying suitable candidates for coverage and detecting fraudulent claims. IoT devices enhance transparency between insurers and clients, providing customers with insights into the decision-making process.
Types of IoMT Devices
IoMT devices come in various forms:
Wearables-on the Body: These include biosensors for real-time health monitoring. Some are even implanted under the skin for discreet, continuous monitoring. The key categories are consumer health wearables (e.g., fitness bands) and clinical-grade wearables (used under medical supervision).
In Hospitals and Clinics: Large equipment and smart devices are used for patient monitoring, supply management, and environmental control in healthcare facilities. Leading MedTech companies employ IoMT for diagnosing and maintaining medical equipment.
Community IoMT: IoMT extends to communities, enabling tracking of patients during travel and offering remote healthcare services in non-traditional settings, such as field hospitals and kiosks for medication distribution.
Advantages of IoT in Healthcare:
IoT in healthcare offers numerous benefits:
Enhanced Quality: IoHT improves the quality of care by enabling personalized treatment plans and data-driven decision-making, supported by technologies like cloud computing, big data, and IoT.
Improved Patient Experience: Real-time data from connected devices allows doctors to make more accurate diagnoses, resulting in individualized care and an enhanced patient experience.
Reduced Costs: Unnecessary doctor visits decrease, and homecare services improve, reducing healthcare costs. Combining automation with data-driven approaches can lower expenses significantly.
Challenges of IoMT Healthcare Networks:
IoMT also presents unique challenges:
Data Security: The exchange of vast amounts of medical data makes healthcare systems vulnerable to cyber threats. Real-time data monitoring, cyber threat analysis, and secure networking technologies are crucial to mitigate these risks.
Regulatory Compliance: Strict regulations govern the use and safeguarding of sensitive medical data, requiring healthcare organizations to adhere to guidelines like those issued by the FDA for medical device cybersecurity.
Technical Challenges: Ensuring secure communication among IoMT devices is essential. Outdated systems may struggle to adapt to evolving security guidelines and interoperability requirements.
Popular Trends in IoMT in 2022:
Several trends are shaping IoMT in 2022:
Nano-Enabled Medical Products: Nanotechnology-based medical devices, including medications and diagnostics, are gaining popularity for their potential in diagnosing and treating various health conditions.
Personalized Healthcare: Rising chronic conditions and health awareness are driving demand for personalized healthcare. Wearable devices and biosensors enable continuous monitoring and reduce the burden on healthcare institutions.
Connected Inhalers: IoT-connected inhalers help patients identify triggers for pulmonary problems and ensure correct usage, improving the management of respiratory conditions.
Market Outlook: The IoMT market is on a growth trajectory, with a compound annual growth rate (CAGR) of 19.9% from 2019 to 2025. In 2020, the market size was USD 219.5 billion, projected to reach USD 534.3 billion by 2025.
Conclusion
The Internet of Healthcare Things is revolutionizing healthcare by providing real-time data, personalized care, and cost-effective solutions. IoMT devices are reshaping patient care records, enhancing communication between patients and healthcare providers, and driving innovations in healthcare. As IoMT continues to evolve, it holds the promise of further improving the quality and accessibility of healthcare services.
About Rang Technologies
Rang Technologies, based in New Jersey, has dedicated over a decade to delivering innovative staffing solutions and the best talent to help businesses of all sizes unlock the full potential of the latest technologies and build high-performing teams to achieve their digital transformation goals.
0 notes
Text
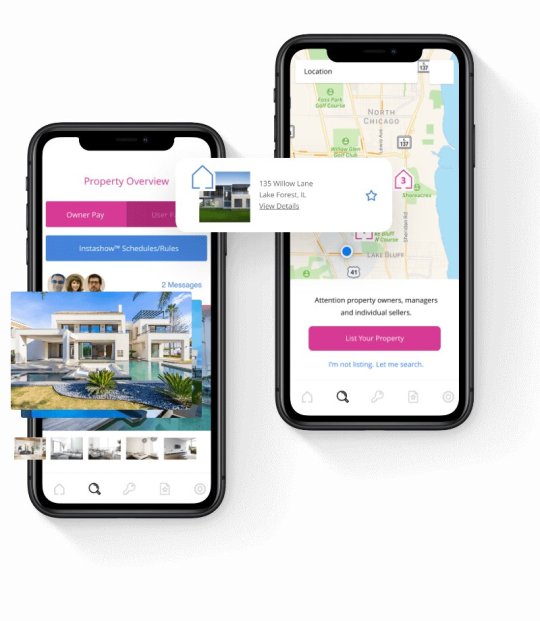
IoT Device Selection
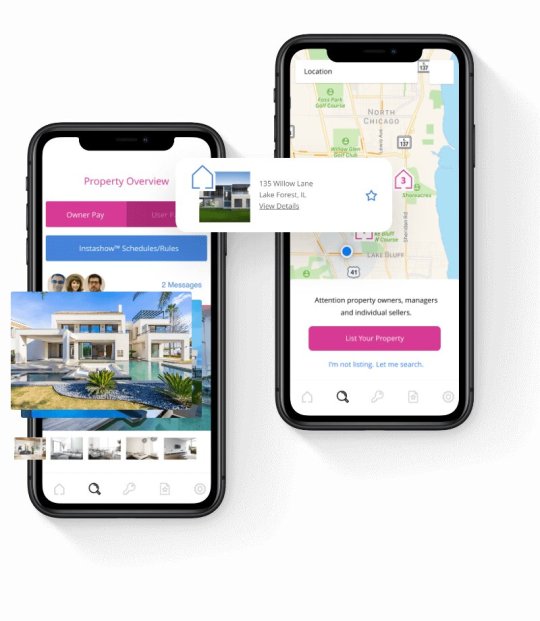
IoT App Development Company: Everything You Need To Know
Get a balance between quality, cost, and time with superior IoT Services for dealing with your business challenges in the best possible manner. We serve global clients with boastful services on a varied scale, with end-to-end network vs. device integration services with the most innovative solutions. Optimize your IoT strategy with meticulous IoT device selection tailored to your goals.
Benefits of IoT Development
The Internet of Things (IoT) is the technology that allows businesses to integrate their service via secondary devices. With IoT, you can build user-friendly apps compatible with various devices, operating systems, and screen resolutions. You can also integrate your smart apps with third-party apps using secure APIs and collect vital user data and behavior on the mobile application to personalize the experience even further.
How to choose a reliable partner for IoT Development?
While analyzing an IoT vendor partner, you should prioritize secure organizations that behold strong web security and development. You must also adopt Full-stack organizations and companies that can establish an ‘all-in-one’ solution that manages a single project’s hardware, mobile interface, and web interface. Opting for a vendor offering these development capabilities and improvements is a much safer bet.
Why TechAhead for IoT App Development?
With over 13+ years of experience delivering cutting-edge digital transformation and mobility solutions, TechAhead has been a major digital partner for globally established companies like Disney, Audi, and American Express. Clutch has ranked us among the top IT IoT development services companies and the top multicultural companies with a strong-willed presence across Los Angeles and Noida.
Who is the top IoT development company?
TechAhead, of course! We have been accelerating business agility and stimulating digital transformation since 2009. Our company was recognized last year as the top IT service provider by Leaders Matrix, an industry-recognized, unbiased ranking entity.
We disrupt the traditional outsourcing model of other IoT companies. We ensure long-term and sustainable success for our customers and the mobile and digital ecosystem. Our relationships with our customers go beyond transactional. Our software development services give entrepreneurial ideas life. We infuse existing mobile and digital platforms with innovation and creativity.
What are the top IoT Apps developed by TechAhead?
We are a world-class digital transformation and mobility solution company and have delivered over 2,000+ project developments on Android, iOS, and cross-platform compatible apps for global brands. We recently announced the launch of “The Healthy Mummy” fitness app, which was recently ranked the world’s #1 Mum’s fitness app, attracting over 2M+ users and adding to many of our success stories.
What about Data security and integrity of IoT Apps?
All TechaAhead development practices are highly efficient and secure thanks to meticulous adherence to security practices and data governance at every step. Our development process considers the devices connected, cloud computing requirements, IoT platforms, and security while developing IoT mobile applications. We ensure that our IoT apps follow all the guidelines and protocols for the highest security.
How to get IoT app maintenance help and post-launch support?
Our role remains strong after the go-live. TechAhead takes full responsibility for the smooth functioning of IoT solutions in your company. With platform support services, maintenance, and the support of process management, our team will monitor your app’s success, it’s adaptability and remove any bugs/errors as per our client’s business needs and user reviews.
In conclusion, the world of IoT app development is a realm of boundless possibilities. Through TechAhead's expertise and commitment, businesses can harness the power of IoT to create user-friendly apps, ensure data security, and drive innovation. TechAhead's track record of success, recognition, and dedication to post-launch support make it a reliable partner in the journey of IoT app development. With a focus on disruptive innovation and holistic relationships, TechAhead is poised to continue shaping the landscape of IoT solutions, delivering transformative results for businesses worldwide!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
does vpn work on pc connected to router
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work on pc connected to router
VPN setup on PC router connection
Setting up a VPN (Virtual Private Network) on your PC router connection can enhance your online security and privacy. By encrypting your internet traffic, a VPN creates a secure tunnel between your device and the internet, preventing third parties from intercepting your data.
To begin the setup process, you'll need a VPN service provider that offers router support. Once you've chosen a provider, follow these general steps to configure the VPN on your PC router:
Access Router Settings: Open your router's admin panel by typing its IP address into your web browser. This address is typically found on the router itself or in the user manual.
Log In: Enter your router's username and password to access its settings. If you haven't changed these credentials, they are often set to default values (e.g., "admin" for both username and password).
Find VPN Settings: Look for the VPN settings in your router's menu. This location may vary depending on the router model and firmware version. Common labels include "VPN," "VPN Client," or "VPN Settings."
Enter VPN Details: Enter the configuration details provided by your VPN service, including the server address, VPN protocol (e.g., OpenVPN, PPTP), username, and password.
Save Settings: Once you've entered the VPN details, save your settings and restart your router if necessary. This will apply the changes and establish a connection to the VPN server.
Test Connection: After the router restarts, test the VPN connection on your PC to ensure it's working correctly. You can do this by visiting a website that displays your IP address to confirm that it matches the VPN server's location.
By setting up a VPN on your PC router connection, you can protect all devices connected to your home network, including computers, smartphones, and smart home devices, with just one configuration. This added layer of security can safeguard your sensitive information and provide peace of mind while browsing the internet.
VPN compatibility with router network
Title: Enhancing Network Security: VPN Compatibility with Router Networks
In today's digital landscape, where online privacy and security are paramount concerns, integrating a Virtual Private Network (VPN) with your router network can significantly bolster your protection. VPN compatibility with router networks offers a seamless solution to safeguarding all connected devices within your home or office environment.
By configuring a VPN directly on your router, you extend its protective shield to every device connected to the network. This includes smartphones, laptops, smart TVs, gaming consoles, and any IoT devices, ensuring comprehensive security and privacy across the board.
One of the primary advantages of VPN compatibility with router networks is encryption. VPNs utilize robust encryption protocols to secure data transmitted between devices and the internet. By encrypting all traffic at the router level, you effectively create a secure tunnel that shields sensitive information from prying eyes, hackers, and cybercriminals.
Furthermore, VPN integration with routers enhances anonymity by masking your IP address. Instead of broadcasting your real IP to websites and online services, the VPN assigns you a temporary IP from its server network, thereby concealing your true location and identity.
Additionally, VPNs enable access to geo-restricted content by allowing you to connect to servers located in different regions. Whether you're traveling abroad or simply want to bypass content restrictions, VPN compatibility with router networks grants you the freedom to enjoy unrestricted access to your favorite websites, streaming services, and online content.
In conclusion, VPN compatibility with router networks is a proactive measure to fortify your digital defenses and preserve your online privacy. By encrypting data, anonymizing your online presence, and unlocking geo-blocked content, VPN integration ensures a safer and more versatile internet experience for all devices within your network.
VPN functionality on router-connected PC
When it comes to online privacy and security, using a VPN on your router-connected PC can offer many benefits. A VPN, or Virtual Private Network, establishes a secure and encrypted connection between your device and the internet. By setting up a VPN on your router, all internet traffic from your PC will be routed through the VPN server, providing an additional layer of protection.
One of the key functionalities of using a VPN on a router-connected PC is the ability to protect your online activities from prying eyes. The encryption provided by the VPN ensures that your data remains private and secure, even when connected to public Wi-Fi networks. This is particularly important when accessing sensitive information or conducting financial transactions online.
Moreover, by using a VPN on your router, you can bypass geographical restrictions and access region-locked content. This can be particularly useful for streaming services, allowing you to access a wider range of movies, TV shows, and other content that may not be available in your country.
Additionally, using a VPN on your router-connected PC can help prevent bandwidth throttling by your Internet Service Provider (ISP). With a VPN, your ISP won't be able to monitor your online activities as easily, potentially improving your internet speed and overall browsing experience.
In conclusion, setting up a VPN on your router-connected PC can enhance your online security, privacy, and browsing capabilities. It is a valuable tool for anyone looking to safeguard their digital presence and enjoy unrestricted access to the internet.
Router-based VPN utilization on PC
Title: Maximizing Security and Privacy: Utilizing Router-Based VPN on Your PC
In the digital age, where online privacy and security are paramount concerns, utilizing a Virtual Private Network (VPN) has become a necessity. While many users install VPN software directly on their devices, another effective approach is to integrate VPN functionality directly into your home router.
Router-based VPN offers several advantages, especially when used on PCs. Firstly, it provides a blanket of security for all devices connected to the network, including PCs, smartphones, tablets, and IoT devices. By encrypting internet traffic at the router level, it ensures that data transmitted from your PC remains secure from potential cyber threats, such as hackers, snoopers, and data thieves.
Furthermore, utilizing a router-based VPN on your PC eliminates the need to install and manage VPN software on individual devices. This streamlines the setup process and ensures consistent protection across all devices without the hassle of configuring each one separately.
Moreover, router-based VPNs often offer robust features such as split tunneling, which allows users to route specific internet traffic through the VPN while directing other traffic through the regular internet connection. This flexibility is particularly useful for PC users who may need to access local devices or services while still enjoying the security benefits of the VPN.
Additionally, router-based VPNs typically offer better performance and stability compared to VPN software running on individual devices. Since encryption and decryption processes are handled at the router level, there is less strain on the PC's resources, resulting in faster internet speeds and smoother browsing experiences.
In conclusion, integrating a VPN into your home router is a smart strategy for enhancing the security and privacy of your PC and other connected devices. With its ease of setup, comprehensive protection, and performance benefits, router-based VPN is a valuable tool for safeguarding your digital life.
VPN effectiveness with router-linked PC
Using a VPN (Virtual Private Network) with a router-linked PC can significantly enhance your online privacy and security. By encrypting your internet connection, a VPN creates a secure tunnel between your device and the internet, preventing third parties from intercepting your data. When you configure a VPN on your router, all the devices connected to that router, including your PC, benefit from the VPN protection without needing individual installations.
One of the main advantages of using a VPN with a router is the ability to protect multiple devices simultaneously. This means that not only your PC but also other devices such as smartphones, tablets, and smart TVs will have their internet traffic encrypted, making it difficult for hackers or ISPs to monitor your online activities.
Furthermore, by using a VPN with a router, you can bypass geo-restrictions and access region-locked content on all your connected devices. Whether you want to stream content from another country or access websites that are not available in your region, a VPN configured on your router can help you achieve this.
However, it is essential to choose a reliable VPN service provider and ensure that your router is compatible with VPN configurations. Additionally, using a VPN may slightly reduce your internet speed due to the encryption process, so it's crucial to select a VPN provider that offers fast and stable connections.
In conclusion, integrating a VPN with a router-linked PC offers a convenient and effective way to secure all your devices and enhance your online experience. By encrypting your internet connection and safeguarding your privacy, a VPN can provide peace of mind while browsing the web.
0 notes
Text
Ziqitza Rajasthan - What is Fleet Tracking?
A management tool called fleet tracking uses GPS tracking to keep track of the movement of fleet cars and other assets (e.g., workers, equipment). It is frequently referred to as AVL or vehicle tracking. Typically, a fleet is a group of land-based assets, such as vehicles, trucks, field personnel, and powered or unpowered machinery (e.g., trailers).
Fleet tracking is a collection of tech-enabled solutions created to assist fleet managers in managing their fleets, drivers, and all moving assets, according to Ziqitza Healthcare Ltd, a prominent emergency healthcare service provider.
The majority of fleet tracking systems combine:
Connected devices: Trucks, trailers, ambulances are all connected through GPS, satellite, cellular and other technologies.
Internet of Things: Ziqitza explains that most fleet managers use IoT platforms or servers for centralised data collection from all connected devices.
Telematics: An application or dashboard is usually installed using Google maps. These systems are also called telematics. Ziqitza Healthcare explains that telematics technology is used by GPS fleet tracking to gather information from fleet vehicles and other assets. This data is typically collected in near real time (actively) using a GPS tracking device connected to a vehicle's OBD port, making it more beneficial for fleet managers and business owners who can use it to make strategic decisions about operations (for example, Which vehicle should I dispatch to a new job? The closest crane is where? We have how many generators in the yard? Has my lone employee arrived back from the jobsite?
What are the technologies used for fleet tracking?
GPS is the most widely utilised technology in fleet tracking. However, Ziqitza Rajasthan elaborates that in addition, the majority of GPS trackers combine cellular networks with satellite-based GPS systems to transmit location information to the platform. Many GPS trackers contain on-board processing capability, security layers, and embedded device logic like power management and communications protocol management in addition to the two fundamental communication technologies. The majority of GPS trackers have an accelerometer on board to detect movement. Additional communication technologies, such as Bluetooth or Bluetooth Low Energy, may optionally be supported by connected devices (BLE). A connected device can now communicate with other adjacent receivers or sensors thanks to this enhanced capability.
What networks support fleet tracking?
According to Ziqitza Limited, the majority of linked devices used for fleet tracking are now connected to the 3G network, also known as HSPA. In order to be backwards compatible with 2G networks, several devices use twin radios. These devices typically connect to networks using GPRS/HSPA (also known as "High Speed Packet Access" or "Generalised Packet Radio Service").
ZHL Rajasthan continues by stating that more recent Fleet Tracking systems utilise 4G, 4G LTM, or 4G LTE Cat-M, which are cutting-edge networks especially created for frequent transmission of brief signals. In comparison to earlier networks, devices on this network often consume significantly less power and offer stronger connectivity characteristics.
What are the features of Fleet Tracking?
According to Ziqitza Limited Rajasthan, fleet tracking devices frequently attach to an automobile's On-Board Diagnostic (OBD) Port. A fleet tracking device that is linked to this port can gather and transmit sophisticated diagnostic information in addition to position and speed. These are some typical attributes of fleet tracking systems:
● Location
● Trip Tracking
● History of Trips
● Mileage/Odometer
● Breadcrumbs during a trip
● Speed
● Direction
● Fuel Level
● Battery Voltage
● Diagnostic Trouble Code (DTC) notification
A manager may be able to obtain real-time performance data from some Fleet Tracking systems through email, text message, or in-app notification. Some Fleet Tracking Systems, according to Ziqitza Health Care Limited, offer downloadable and on-demand reports. To easily sort and analyse these, download them into a spreadsheet.
Fleet tracking systems have many advantages. Fleet tracking, in its most basic form, enables a manager to be aware of the location, direction, and status of his assets. Fleet tracking is a technology that is becoming more and more crucial and has long been used by large fleets. More small and mid-sized field service fleets are implementing Fleet Tracking due to decreased prices, flexible monthly payment, and improved product simplicity.
#ZiqitzaLimited#Ziqitza#ZiqitzaHeathcare#Ziqitzahealthcarelimited#ZiqitzaRajasthan#Ziqitzahealthcareltd#ZHLRajasthan#ZiqitzalimitedRajasthan#Ziqitza Health care limited
0 notes
Text
In-depth interpretation of why blockchain is inseparable from oracles?
Why is blockchain inseparable from oracles? We should understand what an oracle !
The oracle writes external information into the blockchain to complete the data exchange between the blockchain and reality. Allowing smart contracts to map to the uncertain external world is not only the only way for smart contracts to interact with the outside world, but also the interface between the blockchain and the real world.
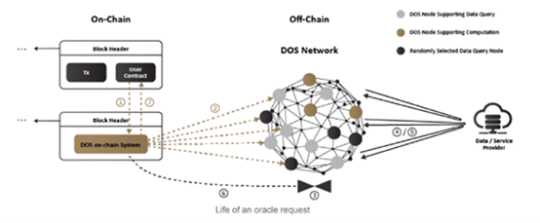
01. Technically analyze the oracle
Structurally, oracles serve as an intermediate layer that securely connects blockchains to off-chain systems by connecting to data providers, web APIs, enterprise backends, cloud service providers, IoT devices, electronic signatures, payment systems, and A hub for various off-chain environments such as other blockchains, with the following key features:
·Wait for Response - Monitor the blockchain network and scan the network for off-chain data requests from users or smart contracts.
Fetch Data - Fetch data from one or more off-chain systems (e.g. off-chain APIs run by third-party web servers)
Formatting - converts data from APIs into a format readable by the blockchain, and converts on-chain data into a format compatible with external APIs, thereby breaking the communication barriers between on-chain and off-chain.
Verification – Provide cryptographic proofs for oracle services using a variety of tools such as data signatures, blockchain transaction signatures, TLS signatures, Trusted Execution Environment (TEE) proofs, and zero-knowledge proofs.
Calculations - perform operations on data, such as calculating the median based on data submitted by multiple oracles, or generating insurance quotes based on different types of data (such as personal risk profiles, market rates, and capital costs, etc.).
Broadcast - Send data and associated proofs to on-chain smart contracts by signing and broadcasting transactions on the blockchain.
Data output (optional) - Send data to off-chain systems when smart contracts are executed, such as sending payment instructions to traditional payment networks, or interacting with cyber-physical systems.
Therefore, in order to achieve the above functions, the oracle system must run both on-chain and off-chain. The role of the on-chain modules is to interact with the blockchain (waiting for data responses), broadcast data, send proofs, obtain blockchain data, and sometimes perform operations on the chain. The role of the off-chain module is to process data requests, obtain off-chain data and convert formats, send blockchain data to off-chain systems, and perform operations in a higher-level oracle network.
Simply put, an oracle is a bridge connecting the blockchain world and the real world, allowing the blockchain world to obtain real-world data.
02. Understand the oracle from an ecological perspective
In the early days of blockchain development, people were still at the stage of mining BTC, and what they pursued was only the competition of computing power. At that time, the ecology of the industry was extremely scarce. But with the influx of DeFi frenzy, the ecology of the blockchain has gradually developed, and the data interaction between the blockchain world and the real world is very important. Obviously, oracles have become an indispensable infrastructure in the crypto world, especially in the DeFi space.
For example, lending protocols rely on price oracles to decide when to liquidate a user's loan. If a user's collateral falls below a certain threshold, the account can be liquidated. Derivatives platforms use oracles to calculate the value of crypto assets, including options, futures, and synthetic assets. Additionally, index platforms such as Set use oracles to retrieve the prices of index components.
Without oracles, the crypto world would be chaotic without traffic lights.
However, when the external data accessed is "fake" data, will it bring catastrophic damage to the encrypted world? The answer is yes. Oracles need to be highly secure because many things depend on them. If data entry is compromised, people lose money. Such incidents of loss of platform assets due to fraudulent data on the chain are not uncommon.
When we dig deeper into the decentralized oracle network (DONs), we find that it is actually powering the smart contract economy. A smart contract is a decentralized application with coded logic (if event x occurs, execute action y), executed deterministically on the blockchain network.
On the Ethereum mainnet, the oracle, as a deployed smart contract and an off-chain component, can query the information provided by the API, and then send messages to other contracts to update contract data. But trusting only one data source is a very unreliable way, usually multiple data sources. We can create it ourselves, or we can directly use the services provided by the service provider. At the beginning, centralized oracles did contribute a lot to the operation of smart contracts. But over time, how to ensure the fairness and fairness of data sources has become an urgent problem to be solved.
03.PlugChain: A Rookie of Decentralized Oracle

When the decentralized oracle was born, these problems were easily solved. In particular, the decentralized oracles with Chainlink and PlugChain as the mainstream have won the favor of the market by relying on the "decentralized" oracle network protocol. The difference is that Chainlink only focuses on the ecology of the only public chain of Ethereum. The high-performance cross-chain PlugChain can combine the ecology of 100 mainstream public chains.
In order to ensure the fairness and reliability of the data, PlugChain obtains data from multiple external sources, and eliminates the influence of a single malicious data through the aggregation of multiple data sources, so it is more reliable. Although decentralized oracles are relatively inefficient compared to centralized oracles, they can solve the problem of single-node failures, so they are less likely to bring security risks. Due to risk concerns, most DeFi applications prefer to run on decentralized oracles.
Of course, the PlugChain oracle network can not only transmit financial market data for DeFi applications, but also perform a series of secure off-chain calculations, such as verifiable random numbers and decentralized execution, to ultimately achieve dynamic NFTs and extremely high levels of automation. DApps. In addition, with the continuous development of cross-chain interoperability protocols, PlugChain will connect various rapidly developing blockchain ecosystems and L2 expansion schemes by virtue of its super cross-chain performance advantages, enabling them to interact securely.
Not only that, but PlugChain builds a secure DON by providing additional layers of security to ensure that DON operates efficiently, such as the ability to connect to high-quality data sources (providing accuracy and uptime guarantees), through cryptographic signatures Proof of data integrity (when data providers themselves run oracle nodes), data validation through multi-layer aggregation processes (mitigating downtime, outliers, and corrupted data), cryptoeconomic guarantees that incentivize correct operation (implicit incentives) and explicit collateral), as well as selectively provide data privacy.
In addition, PlugChain has expanded the Web3 technology stack to transmit off-chain data and services to promote smart contract innovation; to achieve cross-chain interoperability and ensure seamless connection of various blockchains. PlugChain's oracle architecture provides an entry for Web 2.0 backend systems to enter Web 3.0, provides an abstraction layer for traditional systems, and easily accesses any public and private chains. Ultimately, oracles will bring decentralized computing and cryptographic assurances to legacy systems and bridge the gap between Web 2.0 and Web 3.0.
04. Double layout of technology and ecology, adding Web3.0 public chain construction

In order to help develop the public chain ecology, PlugChain adopts a dual strategy layout of technical support and ecological support.
On the one hand, PlugChain relies on the advantages of its own public chain to establish a "fast lane", contract development platform access and blockchain platform construction, including contract sample templates, smart contract IDE, contract supporting SDK, integrated development environment, technical development documents, On-chain optimization guidance, smart contract development, node management settings, consensus mechanism design, monitoring and early warning system, Dapp on-chain deployment. Make it easier and faster for technology developers or ecological participants to join PlugChain. The "fast lane" is obviously a technical solution that provides more value to the developer ecosystem by reducing the time cost of project development.
On the other hand, PlugChain has established a PC ecological fund and recently launched the L Plug-Inside StarRise Plan to support the development of excellent ecological applications D. Facing the global high-quality ecology, PlugLabs (an agency under PlugChain) will provide support in four aspects according to the rating indicators: mainly including financial support, strategic support, advertising support, and traffic support! This will attract more high-quality ecosystems to join.
Whether it is the technical optimization of the PlugChain protocol, the improvement of blockchain scalability, or the support and subsidies provided in ecological construction through the StarRise Plan, these series of cost reduction measures can develop the PlugChain ecology into a public utility, benefiting Web3 of developers and DAPP teams.
Conclusion:
While DeFi is the clearest evidence at the moment, it is more likely that the next major smart contract use case to see mass adoption will be a direct result of developers accessing real-world data on DONs on-chain. It can be seen that oracles have opened a new chapter in the Web3 era and are ready to go beyond the existing ideas and functions. As a public chain betting on DONs, can PlugChain create the future in the future?
0 notes
Text
Archimedes spiral equation

A two-stage Genetic Algorithm (GA) is employed to determine the optimal interval ofĬluster size and derive the exact value from the interval. Paper, the energy consumption of nodes, before clustering, is considered to determine the optimalĬluster size. However, this aim will not be achieved if the cluster size is not properly chosen. In fact, the clustering technique will beĬonsidered effective if the energy consumed by sensor nodes decreases after applying clustering, Is to decrease the energy consumption of the network. In cluster-based WSNs, one objective of applying clustering Decreasing and balancing the energy consumption of nodes can beĮmployed to increase network lifetime. Network lifetime and energy efficiency are crucial performance metrics used to evaluate © 2018 Springer Science+Business Media, LLC, part of Springer Nature Extensive simulation study shows that our algorithm improves the network lifetime by more than 30%, compared to other existing approaches. Particularly, LiMCA includes a novel stochastic deployment scheme for Member Nodes (MNs) and CHs and a training protocol to train CHs and MNs about their coarse-grain location. Second, to meet the requirement of maximization of network lifetime, this paper proposes a novel Lifetime Maximizing optimal Clustering Algorithm (LiMCA) for battery-powered IoT devices. We found that cluster radius of each level has significant role in maximization of network lifetime. First, we analyze the maximization of network lifetime by balancing the energy consumption among Cluster Heads (CHs). The contribution of this paper is two-fold. However, none of the existing solutions considered (1) realistic factors like fading model, routing protocol etc., or (2) optimization of cluster radius while devising clustering structure. Here, the traffic load is evenly distributed among the nodes using variable size clusters across the network. Unequal clustering is commonly considered as one of the efficient energy saving technique. Hence, preserving energy in IoT network requires utmost attention. However, energy-constrained IoT nodes limit the performance of the IoT network. This calculator uses Secant method.The idea of Internet of Things (IoT) is that many of the live objects (e.g., appliances) in the network are accessible, sensed, and interconnected. However, note that the length equation is transcendental, and the inverse task (finding unknown dimensions while the length is among the known dimensions) requires numerical methods. These are all formulas that we need to find out unknown dimensions by known dimensions. Here is how number of turns n is related to angles:Īnd here is how diameters are related to angles (this follows directly from the spiral polar equation) Usually, it has a sleeve, hence the inner diameter and initial angle. If a spiral starts from zero angle (from the center), the formula is simplified:īut in real life, of course, a roll of material does not start from the center. To find out the length, we need to integrate from the initial angle to the final angle. Now we have the dependence of the length dl on the angle dφ. Using the polar equation of a spiral, we can replace ρ with kφ, and dρ with kdφ Hence:Īn infinitesimal spiral segment dh can be replaced with an infinitesimal segment of a circle with radius ρ hence its length is ρdφ. Please be careful with unit control when you enter the known dimensions! 20 meters are not the same as 20 millimeters.Īn infinitesimal spiral segment dl can be thought of as hypotenuse of the dl, dρ, and dh triangle. Theory and formulas, as usual, can be found below the calculator. You can also solve an inverse problem (when you know the roll length) - calculate thickness and number of turnings using roll length and both diameters. For example, you can calculate roll length from inner and outer diameters and roll thickness or number of turnings. You can easily find out some of these objects' dimensions, like diameters and thickness, or a number of turnings, and, using the calculator below, calculate the missing ones. We can see spirals in everyday life in any objects that are in the rolled form: rolls of paper, tapes, films, and so on. These dimensions are related (see formulas below the calculator), and you can calculate any two if you know the other three. We have five spiral dimensions: outer diameter - D, inner diameter - d, thickness, separation distance or distance between arms - t, spiral length - L, number of turnings - n.

0 notes
Text
Neoload team server installation

Neoload team server installation software license#
Neoload team server installation install#
Neoload team server installation android#
Neoload team server installation install#
It is recommended to install “load generator agent’ on the designated agent machines to handle more user load.Please find the system requirements here.ĭownload the latest version and choose the OS bit version depending on your operating system from here. Will cover most of the above-mentioned features in this tutorial series. Integration with Dynatrace, CA APM, and AppDynamics, Newrelic.Require additional services like BlazemeterĪbility to deploy several monitoring engines in sub networks No cloud module integrated into Loadrunner. Neotys cloud platform includes Amazon EC2, Cloud Sigma, Rackspace, Joyent, and even HP!.Multiple providers available through Neotys cloud platform.Deep integration with cloud providers makes it easier to quickly provision infrastructure on demand.
Neoload team server installation software license#
WAN emulation needs (Shunra) not free moduleīuilt into NeoLoad (No additional software license needed).
Neoload team server installation android#
Allows direct recording from Android devises, require a native HP app to install in devise.EUX metrics collection-using perfecto, selenium, seetest, Appium etc.Generate realistic traffic on the server with WAN emulation (bandwidth, latency, packet loss).Emulate mobile browsers during recording and runtime.Allows direct recording from mobile device or desktop.Results analysis tables and charts are primitive more sophisticated analysis requires other charting tools (e.g., Excel) Good reporting and test results comparisonĮxcellent reporting, test result comparison MQTT Plugin available to support IOT Performance Testing Recently started supporting IOT with extensive coding in Visual studio. It’s possible to measure browser rendering event related metricsĭedicated advance action for MQTT- No coding needed. Trueclient protocol- gives only single metrics It’s possible to measure browser rendering event related 4 metrics Type characters “/” to be entered or blocks of script with “*/” Manually set parameters using scripting language Session and cookies handling is not required Let’s explore the features of Neoload, LoadRunner, and JMeter using the below table.Įasy to use user path maintenance feature which reduces redesigning/re-scripting effort by 40 to 50% Helps to determine problems related to memory leaks, garbage collection etc.To identify the stability of an application under constant load for an extended period of time.To identify the bottlenecks in the application like DB connection & to determine the Max no of user requests that a server can handle.Load testing executed to find issues due to low resources or competition for resources to find the Max capacity of the system.To determine the System’s response time & resource utilization under load.It gives the probable workload application support under the normal working conditions. Testing the application with different workloads based on the usage pattern.Is my system responding quickly? If no what will be the reason?.Is my system able to handle a large volume of users?.How fast is my system responding to load?.We need to do Performance testing in order to get the answers to the below questions: the user may not be interested to use that site due to poor performance. If the site or app is not performing well then it may lead to user drops i.e. whether the server is able to handle thousands of users at a time. It is also performed to check the stability of the system i.e. Performance testing is used to determine how fast a website or app will be responding to a user request when multiple users access it. Among all the performance testing tools, I feel comfortable with Neoload because of its user-friendly record and script enhancement options that make the tester’s job much easier when compared to the other tools.īefore starting with the Neoload tutorial let’s discuss a little about what is performance testing and why we need it along with performance testing tools feature comparisons. I have worked on various performance testing tools that include LoadRunner, JMeter, RPT, and Neoload. Neoload simulates traffic through virtual users to determine the application performance under load and analyze the transaction response times and pinpoint the number of the simultaneous users which the internet, intranet or the mobile application can handle. Neoload is a low-priced high-efficiency load and stress testing tool that is used to measure the performance of web and mobile applications.

0 notes
Text
What is IoT Based Home Automation?
WHAT IS HOME AUTOMATION BASED ON IOT?
Based on IoT A smart home or smart house is a household that has been automated through home automation, often known as domotics. Lighting, climate, entertainment systems, and appliances are just a few examples of the house features that a home automation system may monitor and/or regulate.
It might also contain elements of home security like alarm systems and access control. Home appliances that are online are a crucial component of the Internet of Things (IoT).
For instance, you might programme your lights to turn off when you usually go to bed, or you could programme your thermostat to turn on the air conditioning an hour or so before you get home from work.
Home automation improves convenience and can save energy costs for heating, cooling, and lighting. With the help of IoT devices like surveillance cameras and sensor systems, home automation may increase security.
But wait, how do IoT devices fit into home automation?
HOME AUTOMATION USING IOT
The term "Internet of Things," or "IoT," refers to any Internet-connected equipment that isn't typically linked; an example would be a smart light bulb that you can control with an app.
The IoT gadgets and appliances used in home automation can be programmed to trigger one another. Home automation is what you can do with IoT devices to slightly ease your life, even though IoT refers to the equipment themselves.
WHAT IS THE PROCESS OF HOME AUTOMATION?
Home automation utilises a network of gadgets linked to the Internet via various protocols, such as Wi-Fi, Bluetooth, LPWAN, and others. Through mobile applications, web interfaces, IoT dashboard, or a digital assistant like Alexa or Google Home, the devices may be remotely monitored.
Many of these Internet of Things (IoT) gadgets feature sensors that keep track of changes in movements, temperatures, and lighting so the user may learn more about the environment around the device.
Users or sensors can activate actuators, which are actual physical devices like light switches, motorised valves, or motors that enable remote control of equipment, to physically alter the device. The functionalities of a connected home app may be very varied.
The three different degrees of home automation are as follows.
Monitoring
Control
Automation
Status monitoring of systems, i.e.
What is the temperature?
Is the door locked?
Is The Light on or off?
CONTROL OF VARIOUS HOME APPLIANCES
Systems are capable of changing their states, i.e
Turn ON the heater or Air conditioner.
Lock the Door.
Turning the light on or off.
AUTOMATION AND SCHEDULING OF APPLIANCES
A system that changes state automatically when an event occurs. i.e.
In the event that the outside temperature drops below a certain level, turn on the heating.
When nobody is home, turn the lights off.
SMART HOME – AUTOMATION SYSTEM COMPONENTS
A home automation system will consist of
End Devices like switches, sensors, lights, locks, etc.
Connection devices like hubs and Gateways.
A Network or networks e.g. Wi-Fi, Zigbee, LPWAN, etc.
IoT'S PART IN House AUTOMATION
The users will be able to utilise a Home Automation System based on the Internet of Things thanks to the IoT-based Home Automation (IoT). The internet is used to automate modern houses and control household equipment.
The Wi-Fi modems will be able to access user commands sent over the internet. This modem may be interfaced with by the microcontroller. The LCD also shows the system data and the state of the system.
This system for managing all of your home appliances is a typical IoT-based home automation system. As the cost of IoT devices declines and more people become aware of their advantages, the market for smart homes is booming.
Smart cities would advance the Internet of Things (IoT) after smart households, which is the natural next step. But the transformation of our everyday lives by the Internet of Things in the next few years will affect far more than simply smart houses.
Sensors in Home Security
IOT HOME AUTOMATION: GETTING STARTED
Home automation has three major parts:
Hardware
Backend & User Application
Communication protocol
For you to provide your clients with a genuinely smart home experience, each of these components is equally crucial. The capacity to iteratively create your IoT prototype and swiftly adapt to technological shifts depends on having the correct hardware.
You may prevent performance constraints that would otherwise limit the technologies and device synergy with sensors and IoT networks by choosing a protocol after careful analysis and the correct testing.
Home AUTOMATION PARTS
We've already discussed them, so let's break them down into their individual parts so you can finally create a realistic picture of the key elements that go into creating a smart home. The main parts may be divided into:
IoT gateways and sensors
IoT firmware and protocols
IoT databases and the cloud
Application of IoT
There are hundreds of IoT sensors used in home automation.
Platform-as-a-service (PaaS) and infrastructure-as-a-service (IaaS) providers make up the majority of IoT cloud players (IaaS).
IDENTIFICATION OF IOT PLATFORMS
Once more, opinions on these platforms' IoT application and security-related capabilities are very split. Several of these systems have open source software.
Let's look at what to anticipate from an IoT platform in general:
Support for protocols including CoAP, MQTT, and HTTP, as well as message brokers and message queuing, device management, data collecting, visualisation, and basic analytic features:
capacity to integrate with other web services
scaling both horizontally and vertically
APIs for WebSocket for real-time data flow
This Article was Originally Published Here: IOT BASED HOME AUTOMATION AND SECURITY
1 note
·
View note
Text
IMS 5G
Introduction to IMS 5G
IMS 5G is a service that enables access, roaming and interworking between different network architectures (e.g. cellular, wireless LAN and satellite). IMS 5G provides the services required for seamless multimedia communications and IP Multimedia Subsystem (IMS) M2M / IoT capabilities in a single architecture. IMS 5G is a set of protocols and standards defined by the 3rd…

View On WordPress
0 notes