#AccessControls
Text
Vendor Relationships Privacy: How to Build Strong Data Protection Provisions in Business Contracts?
Safeguarding sensitive information is key for businesses of all sizes. With the rise in cyber threats and regulatory scrutiny, establishing robust data protection measures is crucial, especially when engaging with #vendors.
Introduction
Vendor relationships are integral to business operations, but they also introduce potential vulnerabilities to data security. Hence, drafting comprehensive data…

View On WordPress
#AccessControls#Accountability#ComplianceAssurance#ContractNegotiations#ContractualObligations#Cybersecurity#DataBreachResponse#DataHandlingProcedures#DataProtectionProvisions#DataSecurityProtocols#Encryption#EnforcementMechanisms#LegalCounsel#lexdexsolutions#MonitoringCompliance#PrivacyLaws#PrivacyStandards#RegulatoryRequirements#SecurityMeasures#SensitiveInformation#VendorRelationships
0 notes
Text
Data Security And Privacy Considerations In Email Reminder Systems

Data security and privacy are paramount in today’s digital landscape, where information is increasingly stored and transmitted electronically. As businesses and individuals rely on email reminder systems to streamline task management and improve productivity, it becomes crucial to address the potential risks and vulnerabilities associated with data security and privacy. In this blog, we will explore the importance of data security and privacy in email reminder systems, discuss common considerations, and provide actionable tips to enhance the protection of sensitive information.
The Significance of Data Security and Privacy
Data security and privacy are vital for maintaining trust and safeguarding sensitive information. In the context of email reminder systems, ensuring data security and privacy is of utmost importance to protect the confidentiality, integrity, and availability of data. Breaches can lead to severe consequences, including financial loss, reputational damage, and legal ramifications. By prioritizing data security and privacy, organizations and individuals can mitigate risks and build a solid foundation for maintaining trust with their users and clients.
Encryption and Secure Transmission
Encryption plays a crucial role in securing data transmitted through email reminder systems. Implementing strong encryption protocols ensures that the information remains confidential during transit, making it significantly harder for unauthorized parties to intercept or access the data. End-to-end encryption provides an extra layer of protection, ensuring that only the intended recipient can decrypt and access the data.
Access Controls and Authentication
Implementing robust access controls and authentication mechanisms is essential to prevent unauthorized access to email reminder systems. By enforcing strong password policies, multi-factor authentication, and user access controls, organizations can ensure that only authorized individuals can access and manage sensitive data. Regularly reviewing and updating access privileges based on user roles and responsibilities further enhances security.
Compliance with Data Protection Regulations
Adhering to relevant data protection regulations, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), is crucial for organizations handling personal and sensitive data. Compliance involves obtaining proper consent, providing transparent information about data usage, implementing privacy policies, and offering data subject rights to individuals. Organizations should familiarize themselves with applicable regulations and implement necessary measures to meet compliance requirements.
Data Retention and Disposal Policies
Establishing clear data retention and disposal policies is essential to minimize data exposure and potential risks. Retaining data for longer than necessary increases the chances of unauthorized access or accidental disclosures. Organizations should define retention periods based on legal requirements and business needs, and regularly dispose of data using secure methods to ensure complete erasure.
Regular Security Audits and Training
Conducting regular security audits helps identify vulnerabilities and weaknesses in email reminder systems. Penetration testing, vulnerability assessments, and code reviews can uncover potential risks and allow organizations to address them promptly. Additionally, providing comprehensive security training to employees ensures that they are aware of data protection practices, phishing attempts, and social engineering techniques, reducing the likelihood of human error leading to security breaches.
Data security and privacy considerations are critical in email reminder systems to protect sensitive information and maintain trust with users and clients. By implementing robust security measures, including encryption, access controls, compliance with data protection regulations, and regular security audits, organizations can strengthen their email reminder systems’ resilience against potential threats. Prioritizing data security and privacy not only safeguards confidential information but also enhances the overall reputation and credibility of businesses and individuals using these systems. By staying vigilant and proactive, we can create a secure digital environment that enables efficient task management while protecting our most valuable asset—data.
0 notes
Photo

Access control II
You again?
#accesscontrol#warden#guard#uniform#uniforms#bald#bear#beefy#chunky#husky#hefty#daddy#gorilla#beast#strong#hairy#mascular#mature#illustration#gaybear#gayillustration#gayillustrations#brutebysimon
448 notes
·
View notes
Text
Keep your entire infrastructure Secure
With the help of server hardening, I keep your entire IT infrastructure up-to-date and secure for Windows, Windows Server, Mac, and Linux operating systems. You’ll save time and reduce complexity by having a single solution for all your security needs.
Server hardening is a necessary process since hackers can gain access through unsecured ports. Hence, to limit the entry points, we block the unused ports and protocols as well as disable the services which are not required. All of this process reduces the attack surface area and eliminates a large number of tactics an attacker could utilize.
I believe server hardening is the most important task to be performed on a server, considering the risk it carries along and therefore, we consider this as our responsibility to remove these vulnerabilities and provide you with a secure and risk-free server.
Our security team will examine your server for any flaws and security holes and give it proper security treatment as per requirement. We will also take additional measures to help tighten the security of your server. We ensure that your server is locked down and ready to run, securely, from day one.
Click here to Know More About Service
#server hardening#linux server#ServerSecurity#HardeningTips#NetworkProtection#DataDefense#CyberSecurityMeasures#SecureServer#FirewallSetup#EncryptionProtocols#VulnerabilityAssessment#AccessControl#IntrusionDetection#PatchManagement#PasswordPolicy#TwoFactorAuthentication#LogMonitoring#SecurityAuditing
4 notes
·
View notes
Text
Upgrade Your Time and Attendance System with BIO-2 from TimeWatch

Bio-2 is a biometric time and attendance terminal that uses fingerprint recognition to identify employees and record their working hours. Bio-2 also has access control features that allow you to restrict entry to authorized personnel only, using a password, fingerprint verification, and RFID cards.
Verification Mode & Capacity
Fingerprint Capacity - 1,000 | Card Capacity - 1,000 | Password Capacity - 1,000
Contact us for more information.
www.timewatchindia.com
[email protected]
+91-9599953923
#timewatch#bio2#biometric#accesscontrol#fingerprintreader#technology#biomertictechnology#security#india
2 notes
·
View notes
Photo

Security is facing tough challenges in all aspects of our daily lives. We offer a range of biometric scanners or biometric readers. Our systems are featured with face and fingerprint recognition technology.
Introducing YOKATTA X600 Fingerprint Biometric Reader
What It Provides You:
Fingerprint / Password Authentication
1,000 fingerprint capacity
100,000 transactions
Standalone via USB
Up to 3 fingerprint templates per user
Password entry available
A USB interface and backup battery
For the most advanced biometric readers, reach out to us. Switch to new technologies to make your lives safer.
For More Details: https://infiniteph.com/
2 notes
·
View notes
Text

Security camera technician near me
If you're looking for security camera repair services near you, it's essential to choose a company with experience, expertise, and reliable customer service. Digital Surveillance that offers top-notch security camera repair services is CCTV Camera. With over 23 years of experience in the industry, Digital Surveillance has a team of trained professionals who can diagnose and repair a wide range of security camera issues. They offer same-day repair services and use high-quality replacement parts to ensure that your security camera system is functioning correctly. Additionally, they provide free technical support and consultation, making it easy to troubleshoot problems and find solutions. Digital Surveillance takes pride in their excellent customer service, ensuring that you get the best service possible.
Get In Touch With Us: 310 901 4972
Email: [email protected]
#SecurityCamerasRepairServices#CCTVInstallation#LosAngelesSecurity#SurveillanceCamerasRepairServices#IPcameras#HomeSecurity#BusinessSecurity#SecuritySolutions#HDcameras#AccessControl
1 note
·
View note
Text
hrsoftwarebd

Student Attendance Software
#hrsoftbd#fingerprints#fingerprinting#softwaredeveloper#softwarecompany#softwaredesign#programmingsoftware#softwaredevelopmentcompany#TimeAndAttendance#ClockingIn#Timesheets#AbsenceManagement#AccessControl#TimeandAttendance#ClockCards#TimeAndAttendanceSystems#AccessControlSystems#businesssoftware#webdesignsoftware#mobiledevelopmen#WorkforceManagementSolutions#applicationdevelopment#studentattendance
2 notes
·
View notes
Text
Access control system for residential buildings
Residents deserve to feel safe within the building they live by themselves or with loved ones. There should not be a concern for who can access the building when people are relaxing or not home. LumiRing Technology installation allows for residents to control who enters their residential building, whether it is an apartment, house, or any other residential domicile. A contactless reader identifies your personal key in your smartphone and the entrance will open when in proximity to your door. Personal home installation is just as easy.
Installation of controllers on your house is quick and efficient. Once installation is complete, use the LumiRing application on your phone to control entry access immediately.
LumiRing Technology is the best option for residential access:
Integrates with any metering and monitoring system
Managed through app
Multi-functional
Encrypted to protect against hacking
Economical – minimum hardware and easy to install
Virtual key via your smartphone
Benefits of installing LumiRing for residential access:
Remote access to your home, apartment, or residential domicile by being in proximity of the entrance. A digital key in your smartphone allows for entry into your home
Ability to give temporary guest access. Family, friends, and authorized delivery men can enter with their mobile key
Real-time monitoring of movements in and out of your residence with the ability to export and review reports
Compatible with any access system you may have currently installed. Easy integration which allows for new convenience into and out of your home
The ability to restrict access to certain floors. And you will be free of unpleasant neighbors.
If you already have an access system, LumiRing Technology is easy to integrate into it, bringing new conveniences.
#LumiRingTechnology#ukraine#Lumiring#Technology#NewYork#UnitedStates#research#development#security#AccessControl
2 notes
·
View notes
Text

#iot & #airport asset tracking offers an automated, remotely managed, and linked way of monitoring and controlling geo-position and movement aspects of an asset's life cycle and operation using sensors, connected devices, and sophisticated #dataanalytics.
www.petran.io
#dataanalytics.#assettrackingsystem#assettrackingsolution#assettracking#asset#tracking#assetsafety#GPSTracking#GPS#securitysystem#security#securitycamera#accesscontrol#securitycameras#cctvcamera#surveillance#assetstrackingsoftware#fixedasset#fixedassetmanagement#tracing#fixedassettracking#petranassettracking#32m
2 notes
·
View notes
Text
Data Privacy in Supply Chain Management
Safeguarding data privacy within the supply chain is critical for UK companies to maintain trust and compliance standards. With numerous partners and vendors involved, ensuring the security of sensitive information poses a complex challenge. Implementing robust encryption protocols emerges as a vital solution, ensuring data remains unreadable even if intercepted during transit across the supply…

View On WordPress
#AccessControls#AIandML#Authentication#Blockchain#ContractualAgreements#Cybersecurity#DataAnonymization#dataprivacy#dataprotection#datasecurity#Encryption#GDPRCompliance#InformationSharing#lexdexsolutions#PrivacyProtection#RegulatoryCompliance#RiskAssessment#SecureSupplyChain#SupplyChainManagement#SupplyChainSecurity#TrainingPrograms
0 notes
Text
Enhance Security and Convenience with Durable RFID Epoxy Keyfobs

Durable and waterproof, RFID epoxy keyfobs offer secure access control and contactless payments. Encapsulated in epoxy resin, they protect RFID chips from damage and environmental factors. Ideal for various industries, they ensure reliable identification and tracking. Explore DBS Cards' wide selection.
To Know More Visit: https://www.dbsme.com/product/detail/rfid-epoxy-keyfob
0 notes
Photo

I demand XXXXL
And this time I mean it.
#accesscontrol#bald#bear#beast#beefy#brutebysimon#chunky#daddy#gaybear#gayillustration#gayillustrations#gorilla#guard#hairy#hefty#husky#illustration#mascular#mature#strong#uniform#uniforms#warden
130 notes
·
View notes
Text

Today, we celebrate the incredible advancements in technology that continue to shape our world. At Spintly, we're proud to be at the forefront of innovation, revolutionizing access control systems with our smart technology
https://spintly.com/
#SpintlyUno #SmartAccess #KeylessEntry #SecureTech #AccessControl #AccessControlSystems #SmartBuilding #AccessContriolSystem
#access control solutions#access control system#visitor management system#mobile access#access control market#accesscontrol#rfid technology#smartacess#smartbuilding
0 notes
Text

Elevate your door security game with our cutting-edge Door Access Control Systems! Say hello to EM Lock, multiple controllers, and the capability to manage 5000-50000 users effortlessly. Protect your space with ease.
#DoorSecurity#AccessControl#EMLock#SecureSpaces#TechSafety#BusinessProtection#SecurityTech#SafePremises#AdvancedSecurity#DoorAccessControl
0 notes
Text
Enhancing Perimeter Security: Strategies For Protecting Your Property

In an era marked by increasing security threats and evolving risks, ensuring the safety of physical assets has become a paramount concern for organizations and individuals alike. Among the various layers of security, perimeter security stands as the first line of defense, forming a critical barrier against unauthorized access and potential threats. From residential properties to commercial establishments, the effectiveness of perimeter security measures plays a pivotal role in safeguarding assets, infrastructure, and most importantly, the people within.
The defense area encompasses a range of strategies and technologies designed to detect, deter, and respond to intrusions along the boundaries of a property. While traditional methods such as fences and gates remain fundamental components, advancements in technology have introduced sophisticated solutions capable of providing enhanced protection and real-time threat intelligence. In this article, we explore the importance of perimeter security and delve into effective strategies for bolstering protection in today’s dynamic threat landscape.
Understanding the Significance of Perimeter Security
The perimeter serves as the initial point of contact between a facility and potential threats. A robust security system not only prevents unauthorized access but also acts as a psychological deterrent, dissuading would-be intruders from attempting breaches. Moreover, by establishing clear boundaries and controlled access points, defense area measures enable efficient monitoring and response, minimizing the risk of security breaches and unauthorized activities.
In addition to safeguarding physical assets, the defense area plays a crucial role in ensuring regulatory compliance, protecting sensitive information, and preserving the privacy of occupants. For industries such as critical infrastructure, healthcare, and government facilities, the consequences of perimeter breaches can be severe, ranging from data breaches to operational disruptions and even threats to public safety. Therefore, investing in robust defense area solutions is not just a matter of protection but also a proactive measure to mitigate potential liabilities and safeguard reputations.
Key Components of Effective Perimeter Security

Physical Barriers: Traditional elements like fences, walls, and gates form the foundation of perimeter security. These barriers establish clear boundaries and control access, making it more difficult for unauthorized individuals to breach the perimeter. Modern advancements in materials and design have led to the development of high-security fences and barriers resistant to tampering, cutting, and climbing.
Surveillance Systems: Closed-circuit television (CCTV) cameras, motion sensors, and infrared detectors are integral components of a comprehensive perimeter surveillance system. These devices provide continuous monitoring of the perimeter, enabling real-time detection of suspicious activities and potential intrusions. Coupled with analytics software and remote monitoring capabilities, surveillance systems offer enhanced situational awareness and facilitate prompt response to security threats.
Access Control Systems: Access control systems regulate entry and exit points, allowing only authorized individuals to access the premises. From keypad entry systems to biometric scanners and smart card readers, modern access control technologies offer diverse options for controlling access based on user credentials and permissions. Integration with surveillance systems and alarm systems further enhances security by logging access events and triggering alerts in case of unauthorized attempts.
Intrusion Detection Systems (IDS): IDS utilize sensors and alarms to detect unauthorized entry attempts or breaches of the perimeter. These systems can be configured to detect specific threats such as forced entry, perimeter breaches, or tampering with security infrastructure. Upon detection, IDS triggers immediate alerts to security personnel or initiates automated responses such as activating lights, and sirens, or notifying law enforcement.
Perimeter Lighting: Adequate lighting along the perimeter enhances visibility and acts as a deterrent to intruders. Motion-activated lights and programmable lighting systems can effectively illuminate vulnerable areas during nighttime or low-light conditions, reducing blind spots and improving surveillance coverage.
Implementing a Comprehensive Perimeter Security Plan

Effective defense area requires a holistic approach that integrates multiple layers of protection tailored to the specific needs and vulnerabilities of the property. Here are some essential steps to consider when implementing a comprehensive perimeter security plan:
Risk Assessment: Conduct a thorough assessment of the property to identify potential security vulnerabilities, including weak points in the perimeter, blind spots in surveillance coverage, and access control deficiencies. Evaluate the level of risk posed by various threats such as theft, vandalism, unauthorized access, and terrorist activities.
Security Policy Development: Establish clear security policies and protocols governing perimeter security measures, access control procedures, and incident response protocols. Ensure that all stakeholders, including employees, tenants, and security personnel, are trained in security awareness and compliance with established policies.
Integration of Technologies: Invest in modern security technologies that offer seamless integration and interoperability, allowing for centralized monitoring and management of teh defense area systems. Implement a security information and event management (SIEM) system to consolidate security alerts and streamline incident response processes.
Regular Maintenance and Testing: Conduct routine maintenance checks and performance testing of perimeter security systems to ensure optimal functionality and reliability. Regularly update firmware and software patches to address vulnerabilities and mitigate potential security risks.
Collaboration with Law Enforcement: Establish partnerships with local law enforcement agencies and emergency responders to enhance coordination and support during security incidents. Share relevant information and intelligence to facilitate proactive threat mitigation and investigation of security breaches.
Future Trends and Emerging Technologies
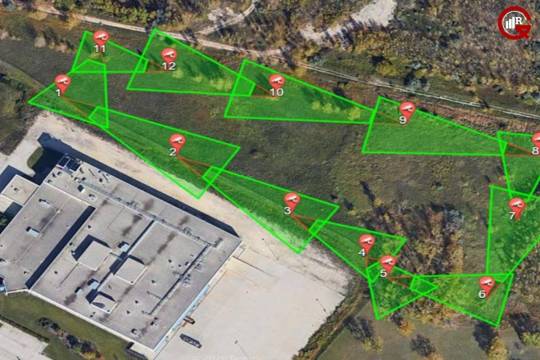
As security threats continue to evolve, the field of security is witnessing rapid advancements in technologies such as artificial intelligence (AI), machine learning, and the Internet of Things (IoT). Predictive analytics and AI-driven threat detection algorithms enable the proactive identification of potential security threats based on anomalous behavior patterns and trends. Similarly, IoT-enabled sensors and devices offer real-time monitoring of environmental conditions and perimeter status, enabling dynamic adjustments to security protocols and response strategies.
Furthermore, the integration of physical security systems with cybersecurity measures is becoming increasingly important to mitigate the risk of cyber-physical attacks targeting the defense area infrastructure. By adopting a comprehensive approach that addresses both physical and digital security threats, organizations can strengthen their resilience and adaptability in the face of evolving security challenges.
Conclusion
In an age of heightened security concerns and complex threats, the importance of perimeter security cannot be overstated. By implementing robust defense area measures and adopting a proactive, multi-layered approach, organizations can enhance the protection of their assets, infrastructure, and people. From physical barriers and surveillance systems to access control technologies and intrusion detection systems, leveraging the latest advancements in security technology is essential to stay ahead of emerging threats and safeguard against potential vulnerabilities. By prioritizing perimeter security as a fundamental component of their overall security strategy, organizations can mitigate risks, ensure regulatory compliance, and foster a safe and secure environment for their stakeholders.
#PerimeterSecurity#SecurityTechnology#RiskAssessment#SurveillanceSystems#AccessControl#EmergingTechnologies
0 notes