Text
SA | Mr Robot Episodes 1 to 3 Analysis
EPS1.0_HELLOFRIEND.MOV
Plot Summary
Elliot Alderson works as a cybersecurity engineer at AllSafe, a firm that specialises in protecting large cooperations like Evil Corp from cyber attacks. Evil Corp has recently been under a string of attacks and a meeting is called to understand what occurred.
Later, he gets a call from Angela Moss, his childhood friend, to go to the office as there appears to be a DDoS attack against Evil Corp. Upon arrival, he finds that the servers are infected and that the only way to fix it is to shut down all the servers, clear the infection, and restore from backup.
While inspecting the infected server, Elliot finds a fsociety00.dat file and a readme.txt file containing instructions “LEAVE ME HERE”.
After returning from the server farm, Elliot gets on a tram where he meets a mysterious man who tells Elliot to follow him but only if he didn't delete the files. Elliot follows the man to Coney Island, the base of operations for the hacker group fsociety, who's plan is to destroy Evil Corp's databases so that they can erase most of the world's consumer debt.
Elliot is asked by Mr. Robot to replace fsociety’s IP address in the .dat file with the IP address of Terry Colby, the head of technology at Evil Corp to frame him for the earlier attack.
Back at AllSafe, a meeting has once again be called by the executives from Evil corp and by the FBI. Elliot has prepared 2 files, one which the .dat file contains Colby’s IP and one which contains fsociety’s IP. Initially he planned on presenting the one with fsociety, but after Angela was blamed for the attacks, he changes his mind and gives the FBI the file that frames Colby.
After 19 days of silence. The media and news outlets finally reveal the findings, thus Colby is successfully framed. In the mist of this chaos, Elliot is whisked away to Evil Corp’s headquarters where he is greeted by Tyrell Wellick.
A side story in the episode are Elliot’s attempts to hack those that surround him or those that pip his interest. A more prominent one would be his psychiatrist, Krista, and her “significant other”, Michael. Elliot’s efforts revealed his real identity and the truth of their relationship. He then confronts Michael Lenny and uses blackmail to ensure that Lenny will break up with Krista and tell her the entire truth.
This is inline with his self proclaimed title as a vigilante.
Software Security Elements
The opening sequence is Elliot confronting a child pornographer with information he gathered from hacking his computer. Elliot explains his original motive in hacking the man as well as how he did it.
I started intercepting all the traffic on your network. Thats when I noticed something strange. So I decided to hack you.
There are many ways Elliot is able to monitor and intercept a network’s traffic. As it wasn't specified in the episode exactly if he was able to connect as a local network or wirelessly I have included possible methods for both below.
Using a Legacy Hub
These are placed at a choke-point of a network and are able to repeat all Ethernet frames arriving at one port to all the other ports on the hub.
A downside to this method is that all the extra packets sent from all the ports increase the risk of packet collisions. When this occurs, the nodes on the shared media segment will pause for a random amount of time before they resume sharing data.
This method is most likely not the method Elliot used in the episode.
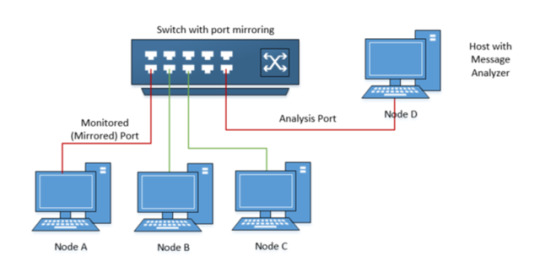
Network Switch Port Monitoring
Also known as Switched Port Analyzer (SPAN) ports or port mirroring, a monitor port is typically configured so that it mirrors all packets that pass through the designated ports. It is used on a network switch to send a copy of any frame sent or received from a particular port to a monitor port.
The downside of this method is that there is a risk of not always getting all the transmitted packets to the monitor port. This is because the primary function of a switch is to forward traffic from the sender to the receiver. As such, if there is a high load on the switch, it will prioritise sending the received frames instead of copying them to the monitor port.
This method is also most likely not the method Elliot used in the episode.
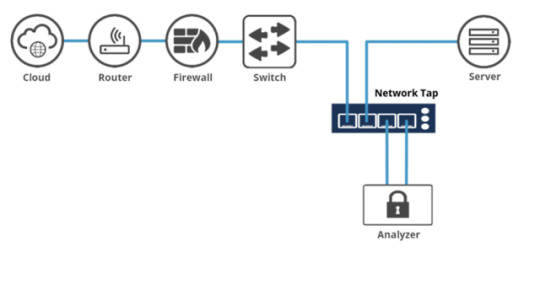
Using a Network Terminal Access Point (Network TAP)
A network tap is a “bump-in-the-wire” device, often placed between 2 nodes in a network, that is designed to copy traffic passing through it to a monitor port. This is a much more reliable way than using a monitor port as taps are less likely to drop packets during high traffic load.
The downside to this method is that it can interrupt network traffic while connecting and disconnecting the tap. They are also often expensive due to the extra hardware required.
This method is also most likely not the method Elliot used in the episode.
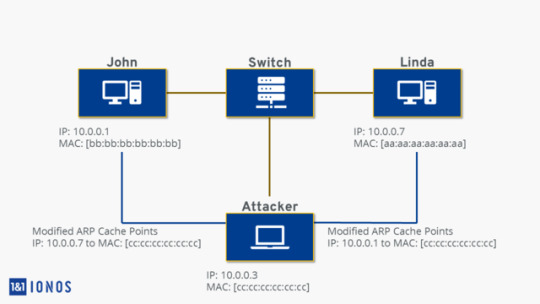
Address Resolution Protocol (ARP) Poisoning
ARP poisoning is a technique where two hosts on a network are tricked into sending packets destined for each other to a sniffer machine on the network. This is done by associating the attacker’s MAC address with the IP address of another host, resulting in any traffic to the IP address is sent to the attacker instead. This method is often used as an opening for other attacks such as man-in-the-middle attack.
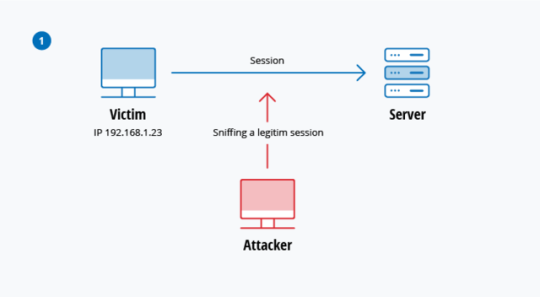
Man-In-The-Middle (MITM) Attack
An attack where the attacker inserts themselves into a conversation between 2 parties pretends to be the the them. The attacker is then able to access and possibly alter any communications or information sent between the 2 parties.
This type of attack is easy to achieve as an attacker within reception range of a wireless access point could insert themselves as a MITM.
The weakness of this method is that the MITM attack can succeed only when the attacker is able to impersonate each endpoint without raising the other party’s suspicion.
Domain Name System (DNS) Hijacking
DNS hijacking is a process in which an attacker redirects queries to a DNS server. There are many methods to perform this attack including, installing malware on the target’s computer, compromising a router through a default password, or intercepting and hacking DNS communications.
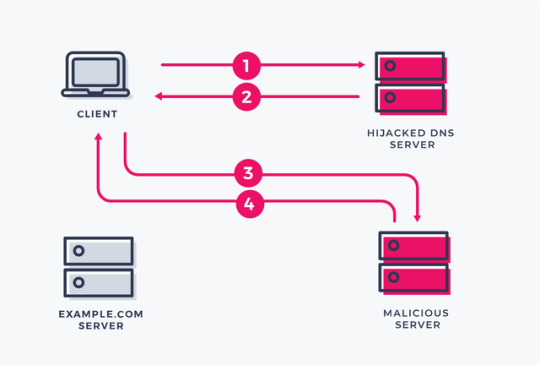
You're using Tor networking to keep the servers anonymous. You made it really hard for anyone to see it but I saw it. The onion routing protocol, it’s not as anonymous as you think it is. Whoever’s in control of the exit nodes is also in control of the traffic, which makes me ... the one in control.
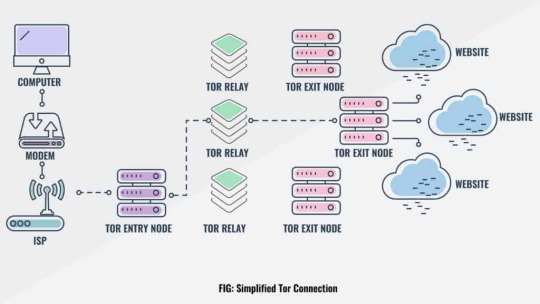
The Onion Router (TOR) Network
It was created initially as a worldwide network of servers developed with the US Navy that enabled people to browse the internet anonymously. It disguises the user’s identity by moving and encrypting their traffic across different TOR servers so that it cannot be traced back to the user.
TOR is useful for people who wants to keep their internet activities private from internet service providers and / or websites. It can also be used to host websites that are only accessible by other TOR users, which is what the perpetrator in Mr. Robot was using to distribute the photographs.
In a TOR network, data comes in and is encrypted all the way through to the exit node. These exit nodes are the gateways where the TOR traffic hits the Internet. As such these nodes can be used to monitor TOR traffic after it leaves the network. Although TOR is decided so that locating the source of the traffic through the network should be near impossible, if the exit traffic is unencrypted and contains identifying information, then it can be traced back to the user. This the exploit Elliot used within the episode to find out the activities of the perpetrator.
This is a “rudy” attack
R. U. Dead Yet (RUDY) Attack
A RUDY attack is a slow rate HTTP denial of service attack tool that aims to keep a web server tied up by submitting form data at an absurdly slow pace. Any web service that accepts form input is vulnerable to a R.U.D.Y. attack as the tool works by sniffing out form fields and exploiting the form submission process.
The tool submits very long form friends are submitted and this process is dragged out by breaking it down into packets as small as 1 byte each. It then sends these packets to the server at randomised intervals of around 10 seconds each. The web server will keep the connection open to accept the packets as the behaviour of the attack is similar to that of a user with a slow connection speed submitting form data. This results in the victim’s web server becoming unavailable to legitimate traffic.
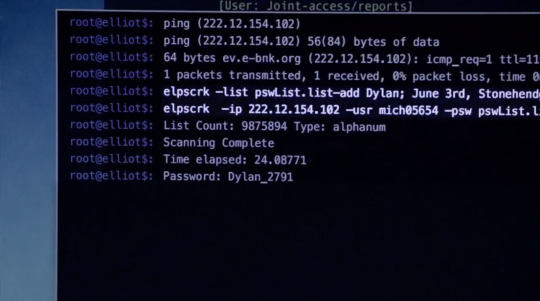
Hacking her was simple, her password Dylan_2791. Favourite artist and the year when she was born backwards.
Although the tool Elliot used here, elpscrack, is fictional, it does contain functionalities that are found in other tools such as CeWL, Burp Suite, and others.
Custom Word List (CeWL) Generator
CeWL is a ruby app which when a given url, it will “crawl” the specified site as well as any external links found on the site to a specified depth. It then returns a list of words from that site that you can filter to include only words of specific length.
This information is useful when targeting a specific individual as people tend to publicly like or follow things with their social media. More often than not, people will use something they like to form a basis for their passwords, as such, the list created by CeWL can be hashed and then given to a password cracker to potentially crack a person’s password.
This is probably the closest to the elpscrk tool that Elliot used.
Burp Suite
Burp Suite is a Java based web penetration testing framework that is useful in identifying vulnerabilities and verify attack vectors that re affecting web applications. It can also be used to brute force a web application log in page.
Burp is designed to be used alongside your browser and functions as an HTTP proxy server where all the HTTP/S traffic from the browser passes through Burp.
Burp requires a list of usernames and a list of passwords in order to brute force a log in page. Manually submit a log in request using any random username and password and Burp capture HTTP request. Then using the cluster bomb attack method, Burp will brute force the log in page using the given lists.
References
NETRESEC: Intercepting Network Traffic
Geeks for Geeks: Carrier sense multiple access (CSMA)
Wikipedia: Packet Analyzer
Cable Solutions: Port Mirroring vs Network TAP
Netwrix: Top 10 Most Common Types of Cyber Attacks
NS1: The Anatomy of a DNS Hijacking
Life Hacker: What is TOR
Hacker Target: Exit Nodes
Radware: RUDY Attack
Cloudflare: R U Dead Yet?
Imperva: RUDY
Digi Ninja: CeWL
Stuff Jason Does: CeWL
Pentest Geek: Burp Suite
Alpine Security: Brute Force using Burp
EPS1.1_ONES-AND-ZER0S.MPEG
Plot Summary
SIDE NOTE:
I am not particularly knowledgeable in the technical aspects of security engineering, networks, or hacking so I may have gotten some details incorrect. The information in these notes are mainly from my research on the topics and techniques found on the internet.
1 note
·
View note
Text
08 | Google Yourself
We're looking at privacy this week, and in order to get a better understanding of the data that large companies hold on users, we're taking a look at some of the data held by large tech companies.
Pick one of the companies below, download your data and analyse what you've found. Share the types of data you found, and point out one thing that surprised you.
Facebook
I picked Facebook to look at as I have recently done a purge of my profile. I want to see if any of the removed data still remains in facebook’s databases.
Data from: 23/05/2009 to 22/07/2019. 10 years of data!
Compressed File Size: 4.06 GB Thats a lot of possible dirt on me.
Interesting Things Found:
My address book containing contact information of some friends and other people.
A list containing all advertisements that align with my interests based on facebook activity. This allows them to show me relevant adds.
A list containing all advertisements I have interacted in the past. Surprising but also I guess expected as there has been times where an ad shows up more frequently after I clicked on it.
A list of all applications or websites that I have linked my facebook account to.
Every single comment I have posted in the 10 years I have used facebook. It appears that comments that I have deleted are not on this list.
A list showing all removed friends and the date and time I unfriended them. Not quite sure why they want to store that to be honest.
A list of likes on external sites. I assume this is to further build my profile so they can show me relevant advertisements. Surprising as I don’t recall linking my account to some of these websites but that might just be my memory failing me.
Luckily I don’t do location checkins on facebook so it appears they don't have a lot of information about my location in the past. Well at least not in the location folder. The logged in location however is a different story ...
A list of all the stickers I have used in messenger. This I find useful as I really do like some of the stickers and since they provided a PNG file of them all, I can probably use them elsewhere.
The messages folder contains files for every single person I have ever messaged as well as any messages, files, audio, and other things I have sent to them. This is great for finding that 1 specific thing I sent to a specific person years ago.
The “Where you’re logged in” contains quite a lot of information such as: type of device, location, IP address, browser, cookies (first 4 characters shown)
Thoughts:
Most of the things that did surprise me were listed above, but at the same time, a lot of the information I found isn't particularly surprising as it made sense why they were storing them. I was also pleased to know that deleted comments and searches are not stored (at least they haven’t given any indication for these information being stalled in the files downloaded).
Overall, this going through these files were quite the trip down memory lane. I will however probably save some of the photos or files that I have posted on Facebook in the past and do another “spring cleaning” of my account.
In the future, I plan on having a look at the Google and Android equivalent to see that data they are keeping track of and are storing with or without my knowledge.
0 notes
Text
02 | Coincidence Index
The coincidence index is an indicator used in cryptanalysis which makes it possible to evaluate the global distribution of letters in encrypted message for a given alphabet.
For a given ciphered message, the value for the index of coincidence allows to filter the list of ciphering methods to use. It is one of the first cryptanalysis technique.
If the index of coincidence is high (close to 0.070), i.e. similar to plain text. Then the message has probably been encrypted using a transposition cipher or a mono-alphabetic substitution.
If the index of coincidence is low (close to 0.0385), i.e. similar to a random text. Then the message has probably been encrypted using a poly-alphabetic cipher. The lower the coincidence count, the more alphabets have been used.
Index of Coincidence
English: 0.0067
Italian: 0.0738
Normalised Index of Coincidence
English: 1.73
Italian: 1.94
Activity
One of the texts below is in Italian and has been encoded by a mono-alphabetic substitution cipher and/or a transposition cipher. The other has been enciphered by an enigma machine. Can you use the above manual trick (or otherwise) to determine which is which?
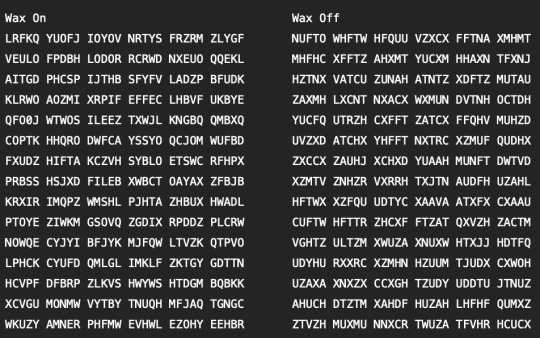
Size of Italian Alphabet: 21
Method Used
I am finally able to put my light box to use! I printed out 2 copies of each set of text and overlaid each copy on the other, shifting by 5 characters. I then taped them together and put them on my light box. I highlighted every character that was matching then counted the number of marks and divided by 375 (numbers of characters checked) to get the index of coincidence. I then divided that number by 21 to get the normalised index of coincidence.
Wax On
Index of Coincidence: 15 / 375 = 0.04
Normalised Index of Coincidence: 0.0019
Wax Off
Index of Coincidence: 21 / 375 = 0.056
Normalised Index of Coincidence: 0.0026
Neither of values doesn’t seem to correspond with the expected CI for Italian, meaning I probably did an incorrect shift. I didn’t repeat what I did with a different shift as I think I got the point of this exercise. Instead, I used an online coincidence index calculator to give me the values.
Wax On
Index of Coincidence: 0.0388
Normalised Index of Coincidence: 0.82
Wax Off
Index of Coincidence: 0.0757
Normalised Index of Coincidence: 1.59
Reference:
PLANETCALC: Index Of Coincidence (Calculator used)
Dcode: Index Coincidence
Wikipedia: Index of coincidence
0 notes
Text
07 | Privacy
Pre-Reading
This week in your tutorial class you’ll be debating privacy - specifically should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
2019 - Facial Recognition to Replace Opal Cards
... board trains using only their faces, with no need for Opal cards, barriers or turnstiles.
What about in the case of twins or people who look similar
Can someone impersonate someone else
Would covering the face pose an issue
Would many people boarding or leaving the train hide another person resulting in them unable to “tap” on / off
Good for people who may forget their opal
Prevent people from fare evasion
No worry about forgetting to tap on and off
I want people to not think about their travel. To quite literally turn up and go. Customers have already embraced using their credit cards or electronic device to tap on and off trains.
True but that often does not tie in with their faces
Pro reasons as above
The data collected would be of enormous commercial value to whomever owned it.
... require extensive public consultation to ensure that citizens’ rights are not impacted ...
This is indeed a major concern
Personally I don’t see an issue with what we have now.
... difficult to see how an opt-out system could be opt-out when everyone using the transport system would be scanned ...
It is a lot of things that need to be stored in a system
It is a system that is arguably not very reliable
Digital identity verification will eventually be integrated with biometric recognition. This will read someone’s face, retina, breath, gait or voice to enable next level authorisation and access.
But how is that relevant for public transport
It’s hard to get all the biometrics required to truely verify a person in as short of a time frame as getting on a train especially if they just managed to get on the train by running.
2019 - AFR discusses Facial Recognition
Couldn’t read much since I don’t have a financial review subscription
Check-in is by facial scan.
How does this work ?
Do you submit a photo of yourself while booking?
The usual vulnerabilities should still be there i.e. housekeeping would still be able to get access
I guess this makes access to the room harder than if its just with a key card providing a signal to the door which can be really attacked.
... our features are already being used for a multitude of purposes ...
All of this requires a face to it initially
Do they use photos from people’s passports or do everyone have to go to a location and get a 360 full body shot and them walking etc.
I can’t say ID or passport photos are particularly up to date as you can opt for renewal of either every 10 years. Meaning, these photos may be almost a decade out of date.
2019 - Australian Views on Surveillance
Not only can this information be shared for reasons of national security, it can also be used for general law enforcement, and even road safety.
I am ok for this use of facial recognition
...allows government agencies greater access to encrypted messages, like those sent over WhatsApp.
I am less ok with this but then again this is probably something WeChat has been doing with the Chinese Government
Fun fact! If you criticise or say a phrase that the Chinese Government won't like on WeChat, you can’t actually send it out. Like you would still see it on your end, but the other people in the chat or in your moments won't even see that posted. This means the app has some sort of filter that prevents people from criticising the government. Fun!
For instance, in the six years after 9/11, the Howard government pushed through a new anti-terror statute [every 6.7 weeks on average].
Measures to ensure safety is often more closely looked at after a horrific incident as this is when the public will be more receptive to these changes.
on average, people didn’t particularly trust the government to manage data.
I can’t blame them as they often don’t make the best decisions
Threat of repurposing: when information collected for one purpose is used for another.
2018 - Facial Recognition Used by Aus Authorities
MISIDENTIFICATION!
91 per cent of matches incorrectly identifying innocent members of the public.
When face recognition is used to identify suspects, there are often multiple records of images of people who are a close match to the suspect. This can result in a high error rate, posing a risk that innocent people are accused of criminality and wrongdoing.
This capability will only enable more targeted searching using still images taken from closed-circuit television or surveillance, for example, to quickly identify a person of interest to help keep the community safe
How much better would the machine be at identifying different faces compared to just a human when looking at a probably low resolution image taken from the CCTVs.
2017 - Benefits of Surveillance (My god this was so long)
However, policy makers can cherry-pick intelligence – select the intelligence that suits their political agenda and ignore the rest
This has always been an issue, especially in the media, meaning, this is a very probably thing to occur
Tactical operations are more specific – targeted at specific individuals or groups. Here individuals are put under surveillance because they are, for example, suspected of plotting a terrorist attack or of being spies passing classified information to foreign countries. There is a defined beginning and end to this type of surveillance. Intelligence collected on a strategic level, however, is more broad – conducted against a foreign government or military for an unspecified time period, for example. While the goal is to gain information on the target entity’s activity, what will be discovered is unknown. Strategic intelligence “determine[s] the nature of the threat,” while tactical intelligence “relates to a specific operation”
How would you know they need to be under surveillance in the first place? Did they already show signs before hand? Did they just stumble on them randomly one day? Or are they going to keep an eye on particular groups? Really tiptoeing the line of racial profiling here.
In other words, what he viewed as reasonable (or proportionate) on the morning of Sept. 10 was different than what he saw as reasonable on the afternoon of Sept 11. For instance, after 9/11, collection of American phone metadata was determined to be lawful and proportionate ...
Events may change how a person makes decisions. If the person is powerful enough, they may result in a change involving large populations of people.
This holds true for the public, if they have a reason to fear, they may push for a change in the law so that they feel more safe and protected
If someone poses a security threat, British intelligence will seek to intercept that person’s communications. If someone is not a security threat and is not in contact with someone who is, intelligence agencies are not permitted to intercept their communications.
This is a great way of handling the collection of data of individuals. They respect the privacy of those that are not involved in anything that may result in their surveillance.
In Class Discussion
The class is split into 2 groups to discuss reasons for and against facial recognition to be used as surveillance.
I was part of the against group.
Side Note: We joked that maybe when it comes to the debate, the 2 sides might have to swap what they are going to be arguing about. We jinxed ourselves.
Topics to Argue
Scope of Abuse
Single point of failure
Lack of Accuracy (What I chose to focus on)
91% fail rate
Technology is not superior to human recognition
Centralisation of Data
security
Lack of Trust of Government / Technology
Potential of single point of failure
Cost of Implementation
While still making the system, it might become outdated and is vulnerability
Human Rights
Lack of accuracy of technology
If the photos are based on passports and drivers licences, adults can opt for either a 5 or 10 year licence / passport meaning that these photos may be out of date.
Effectiveness of technology shows it is still less accurate than humans
Accuracy rates significantly lower for people with skin / minorities and places with dark lighting
Points FOR giving data
Why are people ok with facial recognition in their phones and devices?
Your phone and facebook is able to detect familiar faces in your photos.
A lot of people use the facial recognition system to unlock their devices.
When going through customs while entering Australia
They check your face against your passport
The fast lane gets you to insert your passport then stand in front of a camera
These systems are fast
China’s system, called Skynet, can reportedly scan its 1.3 billion citizens within one second with an accuracy rate of 99.8 per cent, which led to 2000 arrests between 2016 and 2018.
Near real-time tracking could be conducted for reasons as nebulous as “community safety”.
Why should the innocent be punished for the selected few?
How else will you determine who is likely to perform terror acts without prior surveillance? Are you going to wait until they preform their first terror act?
If done incorrectly, are that would be discrimination against particular groups
Unfair laws
Laws go through a long process and hierarchy before being passed.
People can petition and protest which is often effective in preventing bills from being passed
People can also change laws through referendums
How are those with malicious intentions able to act on the information gained from their health records?
Give them high enough blood pressure to kill them??
Force feed them peanuts if they are allergic?
How likely are they able to actually get access to the person to do harm according to the information they got from the health record
Thoughts
This was an incredibly fun topic to argue about even if we had to switch sides all of a sudden and I am not very good at being put on the spot. It allowed me to consider the opposing viewpoint and try to find ways to justify those reasons. It also helped me solidify my position in this topic as originally I was incredibly on the fence.
In the end, I am against constant surveillance as I do enjoy my privacy. However, if in the future it was implemented correctly and it is used for the greater good, I may reconsider my stance on this issue.
0 notes
Text
05 | Driverless Cars
NOTE: No pre-reading again this week
Giggle want to know if they should look into the development of driverless electronic cars where all humans are passengers and the navigation and driving are done by a computer.
Listing the assets of the company you are concerned about.
Personnel, people will be pulled away from the project
Budget, how much funding is required to successfully complete this project i.e. manufacturing cars cost
Listing the top 3-4 risks you are concerned about
Spatial and situational awareness of the car
Construction, school zones, passing emergency vehicles
Emergency situations
Sharp breaking, pedestrian entering road, flat tire
Navigational issues
Road works etc
e.g. that time google directed people onto a muddy field
Can outsiders override the system and direct the car to crash or to a specific location
What the company should do to address each risk
Be able to detect surroundings
i.e. know when it is school zone, detect temporary speed limits by reading signs, identify emergency vehicles with sirens / light and react appropriately
Be able to detect distances and allow the human in the car to be able to override automatic driving function when necessary
Real time updates of road conditions and verify that the route is legal
Ensure all systems are protected and possibly look into blocking potential instructions from outside
Your recommendation would the company proceed with this project YES?NO and brief reason
Yes but only if the rest of the world will also adopt self driving cars
Feedback
Good range of safety/risk concerns. Questions they asked are vague, but I also talked about competition from other companies (e.g. Tesla) as a risk. The ones you listed more related to security though idk..
A way to address safety risk is also to do research on known problems with driverless cards, including incidents/accidents related to them. And then development way to prevent them.
Class Ideas
Assets include Infrastructure, pedestrians etc.
Prevention of risk:
Set a standard the company has to meet
Phase in the cars to a controlled environment i.e. start in locations with no pedestrian access
Check out the youtube video titled “Humans Need Not Apply”
0 notes
Text
05 | ELI85 Passwords
The name of this activity is based off the subreddit Explain Like I’m Five but instead of 5 its 85 isn’t it. >:(
Writer a letter to your grandparents that convinces them why they should care about strong and unique passwords, and come up with some suggestions or tips for how they can start changing their password habits.
Hey Grandma and Grandpa.
I hope you have been well!
I know neither of you use the computer often but it is still important for you to protect accounts better. I know your passwords are just the family name and your favourite combination of numbers (which might be your wedding date but I don’t actually know but if it is, that is not good) which doesn’t make the password very strong at all. People who might know you well enough will be able to guess your passwords if given enough time.
It also doesn’t help that you use the password for everything that requires one and that you just stick it right on the monitor screen. People who break into your house will just have instant access to everything!
Don’t worry, I have some tips on how to create a better password that you can probably remember but is still complex and unique enough at other people wouldn’t be able to guess easily.
I want you 2 to come up with some words that aren’t related to your names and as well as a few numbers that isn’t related to either of your birthdays or addresses. Once that is decided, you can change some of the letters into capitol letters and use some special characters like ! or -.
If you can’t think of any, thats okay, I can probably get one of my cousins to help you with that and write it down for you. On that note, instead of sticking the password to the monitor, maybe write it down in another location that is more inconspicuous.
I love and miss you both so much.
With love,
Secure Shark.
0 notes
Text
05 | Vulnerabilities
Find the errors (vulnerabilities) in the recipes
Martha’s Recipes
Timmy’s grandmother Martha s renowned throughout all of Cronulla for her baking skills. When Timmy went to ask his grandmother for some of her famous recipes he suspected she wasn’t being so honest with him.
Help Timmy discover what is wrong with his grandmother’s recipes.
Vanilla Cake
The amount of ingredients required for this recipe is not listed making it hard to replicate. Even the stereotypical joke where most family recipes doesn’t have proper amounts will give you a vague idea of how much of an ingredient. (A handful of corn for example.)
She also said to preheat the oven to 180˚F which is approximately 82˚C. I believe she actually meant to say 180˚C as 83˚C is not hot enough to cook a cake. (Or maybe it can but it will take a considerate amount of time. I don’t know. I’ve never tried baking a cake at 83˚C)
Caramel Slice
In the recipe it says 1/2 desiccated coconut. It is not clear if she meant 1/2 a cup, 1/2 a teaspoon, 1/2 of an entire coconut, 1/2 a kilo of coconut and so on. Same to be said for the sweetened condensed milk. The butter also mentions having an extra 100g without specifying what state the butter should be in.
She is also clearly missing the step where the caramel is made from the condensed milk, golden syrup, and possibly the 100g of butter. Without this step, this is just a chocolate slice.
(Side note: The actual recipe for this is missing, I would love to actually try this one day.)
Cheese Soufflé
The volume size for ramekins or soufflé dishes typically range from 90mL to 200mL so the 1500mL soufflé’s dish is overkill and not practical. Plus, this recipe doesn’t have enough ingredients nor the appropriate cooking time for a soufflé of this size.
Although it is doable, I would also not recommend hand whisking the egg whites until they are stiff and glossy as that requires amazing arm strength and a significant amount of time.
0 notes
Text
02 | Shredding Analysis
I got one of the shredded trimester information flyers from Richard to try and piece together. I finished putting it together on the 22nd but completely forgot to blog about it. I only remembered because Richard mentioned people who have solved it on the lecture.


My 4 set of characters were: WEBB
Method
I took a photo of one side of the flyer before it was shredded and used that as a reference for where some of the pieces would fit. I only have a photo of 1 side because that would be more fun and challenging.
I started off by finding all the pieces that has yellow characters on a dark background piece together the section in the 2nd image. I then pieced together pieces that have white text on a black background. These 2 steps would've been much more complicated if I didn't have an image of this side.
The next sections I completed were all the sections that had the large capital letters as these pieces were easiest to find. Then pieces of the face, straight lines and easy to recognise words and so on.
I consistently flipped the sections I had finished to see if there are places where I can build off from.
The section with the message is probably the last part I put together mainly because on both sides it was just all white save for the occasional pen mark. I basically used the process of elimination to piece together this part as the smaller the pile of shreds become, the higher the chances the next piece will be part of the message.
All in all, it took me about 3 days while working on and off on the project to complete.
0 notes
Text
04 | Secret
NOTE: There was no pre-reading this week. This is meant to act as a mock final.
Google as set up research lab near UNSW developing a new secret product.
You have been asked to design the physical site security. List 3 key features and justify why they are important. Also list the assets that needs to be protected.
3 Key Features and Justifications
Make the site obscure and don’t slap on a Google sign out front
It will be harder to for “attackers” to find as it will not be obvious that it has any correlation to google or that it is a secret lab
But not in a residential unit / apartment as they are easily bugged, suspicious may also arise from many different people entering and leaving
preferably a standalone house maybe residential or the bottom level of a building??
OR maybe rent out an entire unit, much easier to hide the fact that many people will be entering and leaving
Keycard unique to individual, and one of those camera and voice things required for access to site / house
Makes sure only authorised personnel are able to enter building, person inside has to verify people coming in
if its just a keycard, it may be manipulated to allow access
also ensure the door cannot be opened easily i.e. sliding a card between the crack >:(
maybe the door can only be opened on the inside by a person (closable keyhole to further verify identity and prevent peeping)
this also requires at least one person on the site at all times
person inside must also have a key card to open door
people must not take any research data or anything related to project out of the site
Make the first room a fake room to further hide the site’s true purpose
maybe in basement of house
if site is a house, any surprise visitors won’t be able to see the stuff
this will also prevent people from peeking into windows and seeing things they shouldn’t be seeing
if site is an entire unit, don’t have it on the ground floor and have no balconies??
Assets to be Protected
Research data and any equipment essential for the research
servers
people
reputation
money
identity
Feedback
B- mostly need more justification and explain why it is an important feature
1st suggestion - I think you might want to detail out how to make it further secure. If the lab is still secure and there is many staff members coming in and out of the place, that kind of tells the surrounding neighbours that it isn’t a normal company. In fact, they might mistake it for a hooker/escort house….
Might want to make a more solid explanation of your justifications
8/10
8/10 - rather than focussing on the location and secrecy of the branding on this new lab, mention a bit more on procedures and levels of access such as with the keycard and procedures of visitors and employees entering and leaving the site. All in all pretty well thought through and enjoyable ideas to read
Feedback I Gave
I can't say I am very good at giving feedback but I’m learning.

0 notes
Text
04 | Magic Tricks
I picked the Penn and Teller Fool Me video as that was the most puzzling one for me.
Describe in the how you suspect the magician has performed the trick in the video.
In Penn and Teller, all tricks are first discussed with the producers where the method for these tricks are revealed. Because of this, Jean is able to discuss and practice before hand with Alison on how to manoeuvre her body so that she would be able to fit in that small space.
When looking at the empty device, you can see that the “feet” is already there, thus allowing Alison to remove her feet from that position and fold it up. You can also see that on the upper half, there is a black backing, this is to hide the fact that the area is not uniformly deep, allowing for the area where the crank is to actually be deeper than the other areas. This area is where Alison is able to fold her legs and sit on while Jean rolls up the platform. (Also note that the black backing starts low enough so that Alison can just sit on it without having to lift herself too much and that there is a purple board covering the area right behind the food )
I have included this diagram so that you can visualise what I mean. She can probably bend over more than in my diagram to accurately reflect the amount of space she has in the video but I didn’t want to redraw it to reflect that.

Your challenge is to come up with a magic trick that can fool us all.
Divise a magic trick, record it, upload it, and then post it
Unfortunately I don’t know how to do a single magic trick let alone create one so I will have to give this activity a pass.
Reference
Penn & Teller: Jean-Pierre Parent
0 notes
Text
04 | Human Weakness
Humans play a part in nearly every company, process and system. If humans are not directly in control, we often reserve the ability to take over automated systems and processes. It’s for these reasons that humans are actually some of the most important components of our security systems.
Sydney Lock Out Laws
Discuss the circumstances, pressures and influences that led to the outcome.
The Sydney lock out laws that were implemented in 2014 were thought of as a solution to incidents of alcohol fuelled violence. This law meant that patrons in and around Kings Cross, Darlinghurst’s Oxford St, Cockle Bay, the Rocks and Haymarket could no longer enter venues after 1.30am and the same of alcohol is prohibited after 3am.
“The wider community is sickened by the senseless injury and death,” - Minister for Liquor and Gaming
However, those in opposition to the new law claimed that the reduction in crime is simply a result of far less people in the affected ares and that they have simply shifted the problem elsewhere. In 2017, the NSW Bureau of Crime Statistics and Research released a report supporting this claim. This report also attributed a 49% drop in non-domestic assaults in the Kings Cross area to the lockout and last-drinks laws but the Kings Cross police agreed that ID scanners were equally important in contributing to the drop.
This law has severely impacted businesses with over half of the original 25 high risk venues closed down. This is lower revenues as a direct result of lower foot traffic in the affected areas. As such, many venues are disincentivized to report any violence to the police in case it may negatively affect the venue’s reputation, thus ultimately results in a loss of revenue.
“The NSW Government’s lockout laws were a sledgehammer blow to Sydney’s night-life when what we needed was carefully considered and evidence-based policies to ensure a safe and diverse city for all of our residents and visitors. I have strongly advocated for the relaxation of lockout laws in our city,” - Lord Mayor
Discuss how you might design changes and policies to prevent it from happening in the future.
I have several ideas as to how I might implement changes and other policies to either prevent this or improve on the current situation, however, I don’t believe either ideas would be an ideal solution.
Instead of implementing a lock out law, I believe it would be less detrimental to business if bartenders, other bar staff, and security were to implement a more definitive method of stopping people from drinking too much. As of current, bartenders have the right to refuse services if they believe the patron has drunk too much already. Maybe a fine can be issued to both bartenders, if they kept serving customers that are clearly intoxicated, and patrons if they demand service after they were denied. Similarly security to these establishments should also prevent patrons from entering if they appear too intoxicated. Set up a system across all bars in the area where if a patron has been refused service, they can get their name and or faces so other establishments can refuse them at the door.
A method that keeps the current laws but will possibly remove the issue of violence being relocated to other areas is to just have a blanket ban over the entire state instead of just the CBD. However, this will not stop people from just buying their liquor earlier and getting intoxicated on private property. The problem with loss of business will also remain as well.
Another method is that patrons are limited to a certain number of drinks within a specific time similar to the recommended drinking limit to keep BAC below 0.05. For example, a maximum of 2 standard drinks can be served to each customer per hour. However, this does not take into account of an individual’s alcohol tolerance and those who are “lightweight” may still become violent. This method may work if used in conjunction with the 1st method I proposed.
Reference
Daily Telegraph: Four Years from the Lock Out Laws
Parliament of Australia: Sydney Lockout Laws
Sydney Morning Herald: Lockout Laws Made this City Safer.
0 notes
Text
04 | Bits of Penguin
Each penguin is provided with a coloured ring around their left foot, their right foot, their left wing, and/or their right wing. Some have all coloured rings, others are missing a ring on one or more body parts.
The possible colours are:
Right Foot : Yellow, Purple, Blue, Green, Red, Brown
Left Foot : Green, Blue, Yellow, Brown, Red
Left Wing : Blue
Right Wing : Yellow, Brown
How many bits of penguin are there? i.e. how many unique penguins can they identify with the current set of colours?
Please give your answer in ‘bits of penguin’.
Including the possibility that there is no bands on a body part, the number of possible choices for each body part is:
Right Foot: 7
Left Foot: 6
Left Wing: 2
Right Wing: 3
So that gives us 7 x 6 x 2 x 3 possible “choices”.
7 x 6 x 2 x 3 = 256
256 = 2^8
Bits of penguin = 8 bits
0 notes
Text
03 | Type I and Type II Errors in the News
False Positives
Breast Cancer
Breast cancer is the 2nd most common cause of death from cancer among women. However, there are many false positive diagnosis which often puts a financial and emotional burden on the individual and their families. These diagnosis can also expose the patient to risk from additional medical procedures and side effects that could’ve been prevented they were properly diagnosed.
Hawaii Missile Threat
Early 2018, tourists and residents on Hawaii woke up to an alert on their devices stating:
Emergency Alert
Ballistic missile threat inbound to Hawaii. Seek immediate shelter. This is not a drill.
Those watching television also had their broadcasts interrupted by the ballistic missile threat alert.
This incident occurred during a period of worldwide unease due to the discovery of North Korea’s development of a ballistic nuclear weapon. Although there were some sceptics, almost everyone was panicked, believing that within the next few hours, they and everything around them will cease to exist.
40 minutes after the first warning was sent, a revised alert was sent informing the public that it was a mistake. Apparently the reason why it took so long was because there was no automated way to send a false alarm cancellation. Due to this incident, the governing body has vowed changes to ensure that the notification protocols will be revised to prevent future occurrences.
False Negative
Breast Cancer
Conversely to the case from above, false negative tests in breast cancer may lead to a wrong drug chosen as treatment. Approximately 10-20% of breast cancers classified as Estrogen Receptor (ER) negative are really positive. These patients were given a weaker drug that is not as effective as the recommended drug Tamoxifen. This is particularly worrying as this may lead to the cancer developing further and causing implications that could’ve been prevented if properly diagnosed.
Influenza
Rapid influenza antigen tests (RIATs) have a high rate of false negative results can potentially delay treatment in patients who are critically ill. Approximately half of all cases using RIATs for diagnosis returned negative and approximately 80% of those cases were deterred positive when tested using PCR. Patients who were tested negative by RIAT had longer stays in the ICU (12 days verses 9 days for those who received a positive RIAT result). This is because physicians are less likely to administer antiviral medication to patients with a negative RIAT, and for critically ill patients, this can complicate and prolong clinical outcomes.
Reference
NPR: False Alarm Mammograms
CBS: Cost of Breast Cancer False Positives
ABC: Hawaii Missile Threat
/https://www.sciencedaily.com/releases/2011/06/110627162825.htm/
Science Daily: False Negative Results May Lead to Wrong Drug Choice
Healio: False Negative Rapid Flu Test Results Delay Treatment Decision
0 notes
Text
03 | Lock Picking, Raking, and Bumping
This is a topic I am quite interested in as I have a tendency of leaving my keys at home. It would be more convenient for me to just pick my locks and not struggle to climb over fences and what not.
I am only going to go into the theory of lock picking and not the actual methods as there are too many different methods and lock types to cover in a simple blog post.
Lock Picking
The theory of lock picking is the theory of exploiting mechanical defects and characteristics.
NOTE: There is usually another easier or more efficient method to gain access to something than by lock picking.
Lock Mechanism
The wards are the protrusions on the inside of the keyway that restrict the set of keys that can be inserted into the plug. The plug is a cylinder which can rotate when the proper key is inserted.
Pins are numbered in increasing order starting from the pin closest to the entry point.
A correct key will lift each pin until the gap between the key pin and the driver pin reaches the sheer line. Only when all the gaps are properly aligned in the lock, the plug can rotate and the lock is opened.
NOTE: Typically the driver pins in a lock are the same length but in higher quality individual driver pins may be different based on the key pin length. This makes the pin stacks of equal length and prevents decoding or over-lifting attacks.
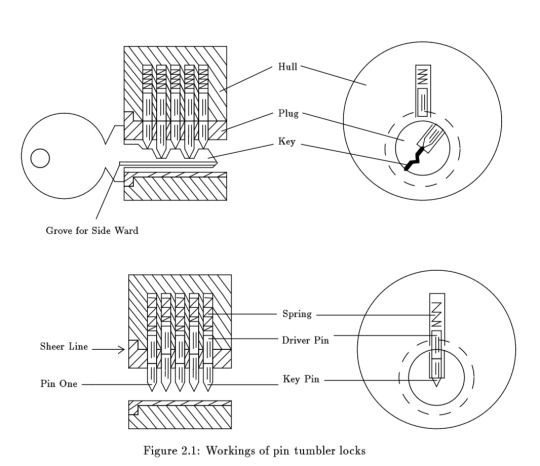
The Binding Defect
This is the basic defect that allows lock picking to work by lifting the pins one at a time. This can be done by providing a sheer force that causes 1 or more of the pins to be scissored between the 2 plates. The most common defect in a lock is that only 1 pin will bind and even when bound, the pin can still be pushed up.
When the sheer tension is applied and the pin reaches the shear line, the following will occur:
The rotation of the plug will cause the pins to shear
The next binding pin will stop the plug from rotating any further
The slight rotation means the driver pin that was just lifted is not resting on top of the plug.
Repeat until all pins are set and the lock unlocked.

Raking (Rapid Lock Picking)
Raking exploits the binding defect by attacking multiple pins at the same time in order to set them randomly. Binding order still applies but is generally ignored during raking.
While it lacks the precision of single pin picking, it still required good tension control and specific movements. It also heavily depends on the biting. Locks that are easiest to raked open usually have little variation in hight from 1 pin to the next and are mostly linear.
Theoretically, racking is applying tension and pushing down on all the pins with the pick then pulling it out of the lock rapidly and repeatedly until the lock opens. Due of how random this method is, lock picking using raking can often take a while, however, skilled lock pickers can accomplish this in seconds.
Techniques
Scrubbing: the movement of the pick in and out across the pins with varying degree of pressure, alternating between long and short strokes, and at different angles.
Ricking: inserting the pick fully into the lock and pivoting it back and forth while moving up and down. (Apparently like a sea-saw on a bouncy castle.)
Lock Bumping
Lock bumping uses a bump key or rapping key to open a lock. The bump key is inserted into a lock and pressure is applied in the from of a series of taps is the key can push the pins up for a split second, allowing the driver pins to get caught.
Reference
Mike: Lock Picking Detail Overkill
MIT: Guide to Lockpicking
UK Bump Keys: Raking
Lock Pick Shop: How Lock Bumping Works
0 notes
Text
03 | Secure Crypto Processors
Secure crypto processors are dedicated processors on a chip or microprocessor specialised in executing cryptographic operations. They are embedded in a packaging with multiple physical security measures that give it a degree of tamper resistance. While normal cryptographic processors output decrypted data onto a bus in a secure environment, a secure crypto processor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained. It act as the keystone of a security subsystem, eliminating the need to protect the rest of the subsystem with physical security measures.
NOTE: They are not invulnerable to attack, particularly for well-equipped and determined attackers who are willing to expend large amounts resources on the project. They are also not secure
Security Measures
If all of the sensitive data is stored only in the crypto processor’s memory and not in external storage, and the processor is designed to secure even at the chip bonding pads and solder bumps, then the protected data can only be accessed by probing the chip after removing all packaging and shielding layers on the chip.
As a secure crypto processor does not output decrypted program instructions, even technicians who may have legitimate access to the sub-system data bus would not be able to tamper with the programs.
Other measure include:
Tamper detecting and tamper evident containment
Conductive shelf layers in the trip prevents the reading of internal signals
Controlled execution to prevent timing delays from revealing any secret information
Automatic zeroisation of secrets (removal of sensitive information) in the event of tampering
Chain of trust (validation of each component of hardware and software from end entity to root certification) boot loader which authenticates the operating system before loading it
Chain of trust operating system which authenticates application software before loading it.
Hardware-based capability registers, implementing a one-way privilege separation model (a program is divided into parts that are limited to their specific privileges required to perform a specific task).
NOTE: If the anti-backdoor design methods are lacking, then these processors can be susceptible to hardware backdoor attacks.
Smart Cards
Also known as chip cards and integrated circuit cards, they are the most commonly use of secure crypto processors. In particular, they are often used in personal ID, credit / debit cards, and SIM cards.
They are more susceptible to physical attacks when compared to other secure crypto processors. However they are useful as users are able to encrypt and decrypt information without relying on unknown, and therefore potentially untrustworthy, appliances.
Reference
Semiconductor Engineering: Crypto Processors
Wikipedia: Secure Cryptoprocessor
Wikipedia: Smart Card
0 notes
Text
03 | ATM Attack and Defence
ATM Architecture
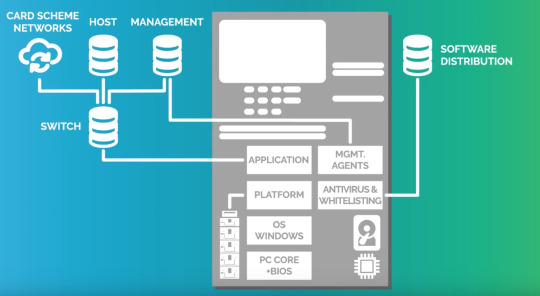
ATM Hardware
CPU to control the UI and transaction devices
Chip card reader to identify the card
Pin pad for accepting personal identification numbers or other necessary information and is manufactured as part of a secure enclosure
Secure crypto processor
Display for displaying information
Function keys or touch screens so users can interact
Record printer so users can receive a receipt of their transaction
Vault to store the parts of the machinery requiring restricted access
Housing to contain all of the above
NOTE: Due to increase in computing demands and the falling price of PC components, most ATMs no longer require custom hardware such as microcontrollers or application specific integrated circuits, but rather, have adopted the hardware of a PC.
ATM Software
Previous models of ATMS ran on RMX or OS/2 operating systems. However, modern ATMs often uses a version of the Window OS with a few running on Linux.
Attack and Defence
These can generally be separated into 2 groups: physical and logical.
Physical
Early ATMs are designed on making them essentially invulnerable to physical attacks. However, there are still methods that can break through that exterior to access the cash inside. Some examples include:
Ram raiding: Thieves attempt to demolish or uproot entire machines.
Plofkraak: Sealing all openings of the machine with silicone and filling the vault with a combustible gas or explosives to force the vault to open. This however can be prevented by using a gas suppression system where the gas is detected and neutralised so it will not ignite.
Attacking workers during machine refill or maintenance: this is minimised as the schedule is kept secret, varying and random. Armed guards are also in the immediate vicinity and constantly surveying the area.
Jackpotting: A small hole is drilled into the machine. Then the existing hard disk is disconnected and replaced by an external disk using an endoscope. An internal button is then pressed that reboots the device so that is is now under the control of the external disk.
Modern methods of defence of ATMs have been implemented such as:
Intelligent banknote neutralisation system (INBS): A variety of methods that protects valuables against unauthorised access by rendering all valuables useless i.e. marking all cash with degradation agents, permanent dye, or strong bonding agents.
Logical
Generally the attacks are designed to create a way to electronically send unauthorised commands to the machine, or load malicious software. Some typical logical attacks are:
Blackbox attack: The attacker gains access to the dispenser cable of the ATM, places an electrical dive or microprocessor as a substitute CPU to control the dispenser.
Offline malware attacks: Rebooting of the ATM with an unauthorised USB or DVD that has their own OS. This disables the hard disk and lets anti-malware solutions to be disabled. Malware is then introduced to the system. There are many forms of malware that can be introduced such as skimming of user data or allowing the ATM to be cashed out. Once the USB or DVD is removed, the ATM is rebooted and goes back to service. Attackers then return later to activate the malware.
MITM: Connect a device or malware into the network, allowing for card data to be skimmed or host messages to be intercepted or spoofed when certain types of cards are entered. This can be used to alter the authorisation message sent by the switch to dispense more cash than approved by the host.
Online malware attacks: A USB or administrative login is used to introduce malware.
Remote desktop access: Spear phishing emails are sent to bank employees whose login credentials will be used to introduce malware. Remote desktop connection is then used to install malware or access test tools on the machine.
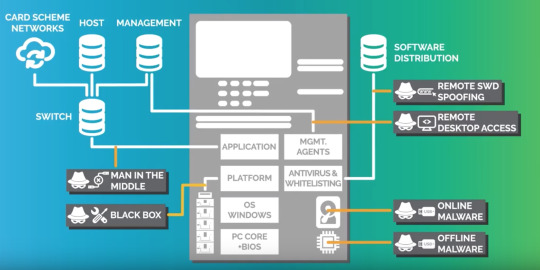
All of the above attacks have methods that can mitigate them:
Blackbox attack: Level 3 encryption as dispenser will only exchange new encryption key when connected to an approved CPU and if a basset is removed and replaced.
Offline attacks: Encrypting the hard disk as mounting an encrypted disk as a second hard disk will not allow access to the file systems to view or edit malware. BIOS should also be locked down so it only boots up when connected to authorised hard disks as well as a password set up for BIOS editing.
MITM: Encrypting the communication channels between the ATM and the switch with TLS encryption the application layer or by having a VPN setup.
Online attacks: Having a white list will ensure only authorised and known files can run on the system. The default administrator password should also be changed.
Remote desktop: Remove Window’s default remote desktop software and all other unused services from the ATM.
Software distribution spoofing: Implement a properly secured software distribution tool that provides confidentiality and integrity to the channel.
Network attacks: Consult an enterprise security review specialist.
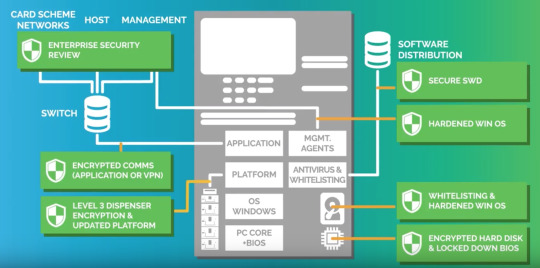
Recommended Security Strategy
Multi-layered
Multiple products, solutions and services provide comprehensive protection
Holistic
Geographic, technological, and future proofing aware
Collaborative
Engagement with customers and law enforcement
Transparent
Proactive alert communication and market feedback
Simple
Customers need to know what to do.
Reference
Fintech: Rise of ATM Attacks
NCR: ATM Attack Vectors and Defences
Wikipedia: ATM
0 notes
Text
03 | Low Probability / High Impact
Find examples of low probability high impact events.
Fires
Every year, there are dozens of forest fires occurring world wide. While most are easy to contain and extinguish, every so often, a large uncontrollable fire will occur, leaving many displaced from their homes. Often the cost of these events are high with many injuries and even death, as well as property damage costing millions.
Camp Fire Nov 2018
Heavy grass cover due to a wet spring
An unusually dry fall
Decreased humidity
Unusually dry fuel
Hot dry gusting continual high winds on the day of event
Although forest fires are common in the area, the severity of the fire was the result of negligence as well as chance conditions that provided more fuel to the fire.
Recommended actions to take to prevent similar situations in the future is to have control burning of known problem areas and that companies should properly maintain their property.
This event also raised concerns for the process of evacuating as last minute evacuations claimed more lives than those that found shelter.
New Zealand Forest Fires Feb 2019
Covered 2,300 hectares of land with a 25km perimeter
Burned for a week
Seoul Fire Apr 2019
Destroyed 500 hectares of land
Fanned by strong winds it quickly spread through the mountainous area
Declared state of national emergency
The fire likely started from a transformer spark near a resort
Plane Crash
You have less than a 1 in 2 million chances of being in a flight accident, even then, most accidents do not result in fatalities. Below is the total number of fatal flight accidents and their cause. As you can see, every year the number is falling.

Both of the crashes mentioned below are from the same type of aircraft, a Boeing 737-8 MAX.
Lion Air Plane Crash Oct 2018
Flight crashed into sea
None of the 189 people on the plane survived
Lost contact 13 minutes after take off
Pilots requested to return to base shortly before losing contact
Ethiopian Airline Plane Crash Mar 2019
None of the 157 people on the plane survived
Lost contact with air traffic controllers six minutes after take off
Pilot sent out a distress call shortly after take-off and given clearance to return
Brand-new airplane that had only flown 1,200 hours
Suspected controllability issue
These are just a few examples of low probability but high impact events. Others includes:
Earthquakes
Tsunamis
Mass shootings in Australia (can’t say for all 1st world countries unfortunately)
Reference
NY Times: Camp Fire that killed 85
NY Times: How PG&E Ignored Risks
Wikipedia: Camp Fire
The Strait Times: NZ Forest Fires
Bangkok Post: Seoul Fire
SCMP: Fire Doused in Seoul
Plane Crash Info
Aljazeera: Ethiopian Airline Plane Crash
Aljazeera: Indonesian Flight Crashes into Sea
0 notes