Text
Wk9_Tut
This week we talked about shootings and the discussion is on incident response.
Preventions
security sign guards
government laws
Mitigations
compartmentalisation
training
armed
0 notes
Text
Wk8_Stargate_ghost_problem
Intro
The Stargate problem is the scenario when you have a group of military people standing outside a Stargate to another dimension/reality/univerise/whatever (irrelevant). One of the brave young cadets volunteers to walk through the portal and ends up in this fantastic universe, full of beautiful, charismatic aliens. One of the aliens asks if he can join the cadet back into his universe. The cadet agrees. When they walk back into the Earth universe, the cadet disintegrates and becomes a ghost. The alien can however see and hear the ghost, but no living thing on Earth can either see or hear the ghost of the young cadet. How can one ensure that the ghost can communicate legitimately through the alien, with the people of Earth?
Suppose you are the friendly Major M from the base who can see the alien A but who cannot see the invisible man X.
Q: What would you M do to get from X his report on the Alien's (A's) planet?
Thoughts
All communication have to go through alien, which can be malicious. There are basically two challenges of this problem:
to verify that the invisible man (X) exists along the ghost
to ensure the integrity of information transmitted through the third party
The verification/authentication can be done using shared secrets. It is the integrity part that is hard to come up with a solution. Initially my thoughts are: let’s attach a shared secret to every message communicated. If the invisible man perceives that the alien is not passing on the right information, he can attach a false shared secret on his next message to alert M. However, this won’t work if the alien just stops saying anything, and there probably won’t be sufficient shared secrets to use.
I realised that we could use RSA --> which is exactly for insecure communication channels! They each need to set up their own key pairs and share the public key with one another. The ghost will follow the major to a secure location and the major shows him the public key --> to make it even more secure, use a shared secret as the public key instead of plainly giving it out.
0 notes
Text
Wk7_Case_study: Snoop
#This is again a late writeup for week 7′s case study.
This week’ tutorial we had a debate on privacy - should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
FOR:
Terrorism and crime prevention - Reduce time for law enforcement agencies
Analysis of suspicious behaviour
Regulations to limit the use of data
google and facebook already have so much data on you
AGAINST:
expensive expanding existing surveillance systems
more data on individuals, less privacy
Type one and type two errors -- Innocent people could be recognised, guilty people may not be recognised
Data can be sold to third party companies, hacked or accessed to be used against us
Blackmail, discrimination and persuasion
Policy makers can cherry-pick intelligence – select the intelligence that suits their political agenda and ignore the rest
0 notes
Text
Wk5_Case_study: Driverless_cars
This is a catchup on week5′s case study. I actually did the case study with my partner on the question paper Jazz gave us and did not end up blogging about it.
So week5 we analysed the risks of introducing self-driving cars and proposed recommendations. The scenario given was that we’re the the Minister for Security and we are to prepare a brief slide deck on 4 things:
Assets of the country we are concerned about
Top risks we are concerned about
What should be done to address the risks
Should legislation be changed to allow self driving cars
And we have:
Assets: citizen wellbeing, infrastructure, road
Risks: accidents, reduced employment in traditional industries, data exploitation and misuse, system being hacked and controlled
Possible solutions: Strict standards on manufacturing and testing, responsible data handling, transition programs to prepare the workforce the skills and knowledge for employment, block access to locations where there are high risks of accidents
Overall: Yes, since benefits outweigh the risks and these risks can be mitigated.
0 notes
Text
S/Key
S/KEY is a one-time password system developed for authentication from untrusted public computers on which one does not want to type a long-term password. A user’s real password is combined in an offline device with a short set of characters and a decrementing counter to form a single-use password. This is then hashed several times, and the server stores the final one Hn(W).
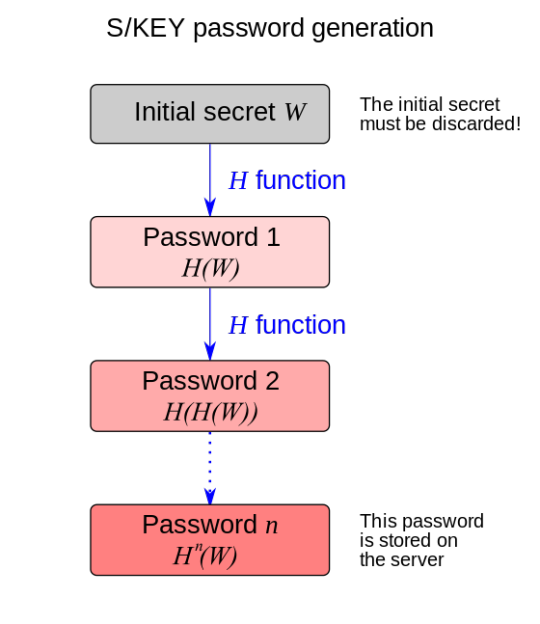
The user provides the server password H[n-1](W) and scratches that password. The server attempts to compute H(H[n-1](W)) and compares it to the one stored on the server. If correctly authenticated, the server will then store H[n-1](W) as the current reference. For subsequent authentications, the user will provide passwordi. The server will compute H(passwordi) and compare the result with the last successful password stored on the server.
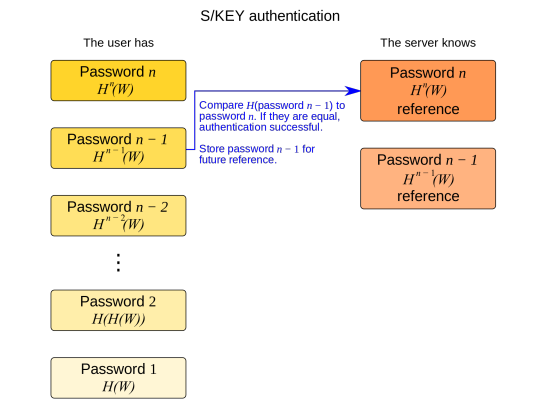
S/KEY is vulnerable to a man in the middle attack if used by itself where the attacker can intercept the password sent.
0 notes
Text
Google_Yourself
From Google takeout I downloaded my data on chrome, maps and Youtube. Interestingly I find: Youtube watch/search history dates back to 2014 -- and I have only commented three times over five years. Also google keeps all my location history which is creepy as you think. In general Google just stores a LOT of data about me, a single individual. When you think about how many Google users are there, the amount of information to be kept is incredible.
0 notes
Text
be-quick-or-be-dead-2
Problem is similar to the first one: make the program run faster.
./be-quick-or-be-dead-2
Be Quick Or Be Dead 2
=====================
Calculating key...
You need a faster machine. Bye bye.
Main function is the same:
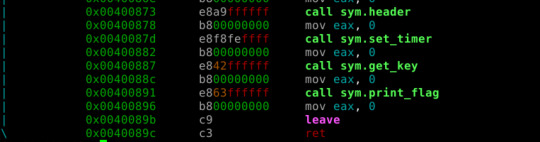
sym.calculate_key calls sym.fib(passing argument 0x3f7 = int 1015), which seems to be a recursive function doing Fibonacci sequencen calculations.
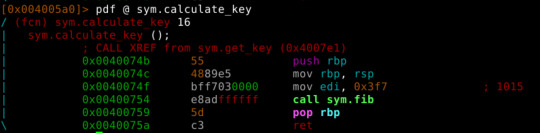
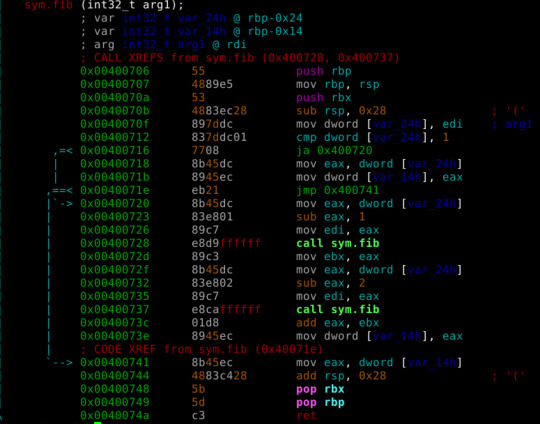
We can calculate fib(1015) and pass it to make it faster.

and we get 17662975587330736941
The patch is done to sym.get_key. Note rax is used for 64-bit registers.
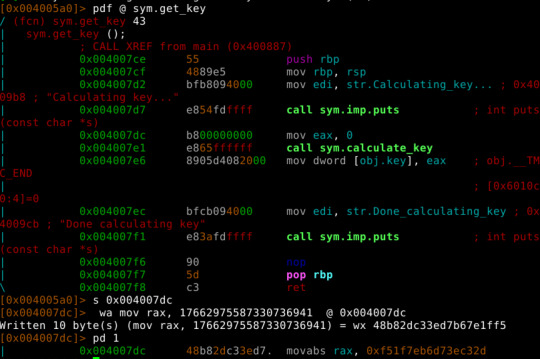
We need 10 bytes to write, 0x004007dc to 0x004007e5, and by doing this we are effectively overwriting the call to sym.calculate_key function, which is what I want.
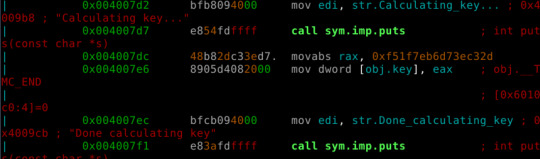
./be-quick-or-be-dead-2-patched
Be Quick Or Be Dead 2
=====================
Calculating key...
Done calculating key
Printing flag:
picoCTF{the_fibonacci_sequence_can_be_done_fast_73e2451e}
1 note
·
View note
Text
be-quick-or-be-dead-1
Problem
Can you run it fast enough? --- The key_calculation is too slow and did not run into completion before the timer exits the program.
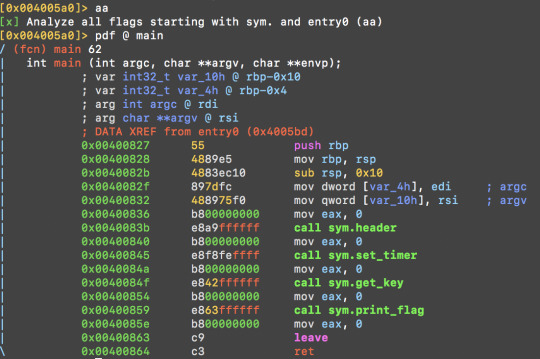
Main function. Guess we need to optimise sym.get_key to make it run faster.
sym.get_key in turn calls sym.calculate_key:
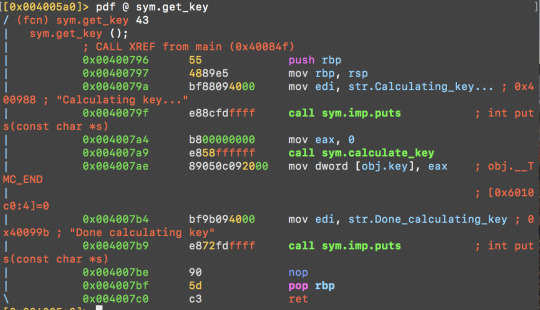
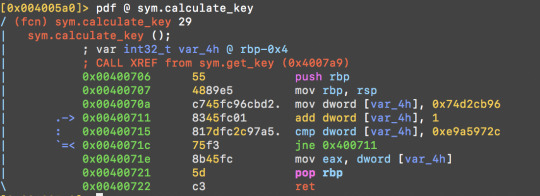
sym.calculate_key just adds 1 each time until the loop finishes when [rbp-0x4] = 0xe9a5972c.
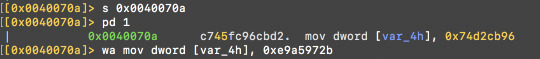
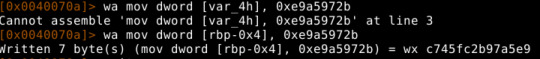
To speed it up, lets edit (HOW TO WRITE)
0x0040070a c745fc96cbd2. mov dword [var_4h], 0x74d2cb96
to
0x0040070a c745fc96cbd2. mov dword [var_4h], 0xe9a5972b
(final value minus one so that the loop will run only once)
Calculating key...
Done calculating key
Printing flag:
picoCTF{why_bother_doing_unnecessary_computation_fedbb737}
0 notes
Text
IOLI_0x08/0x09
Emmm......I’m guessing the same password may still work for this one, cuz it works for 0x07, and I’m right. Still same logic as the previous one, will take a close look later.
$ LOLO= ./crackme0x08
IOLI Crackme Level 0x08
Password: 88
Password OK!
$ LOLO= ./crackme0x09
IOLI Crackme Level 0x09
Password: 88
Password OK!
0 notes
Text
IOLI_0x07
$ LOLO= ./crackme0x07
IOLI Crackme Level 0x07
Password: 88
Password OK!
Logic is the same as level 0x06 though. I’ll have a close look at the difference when I have time.
Main function calls fcn.080485b9

pdf @ fcn.080485b9
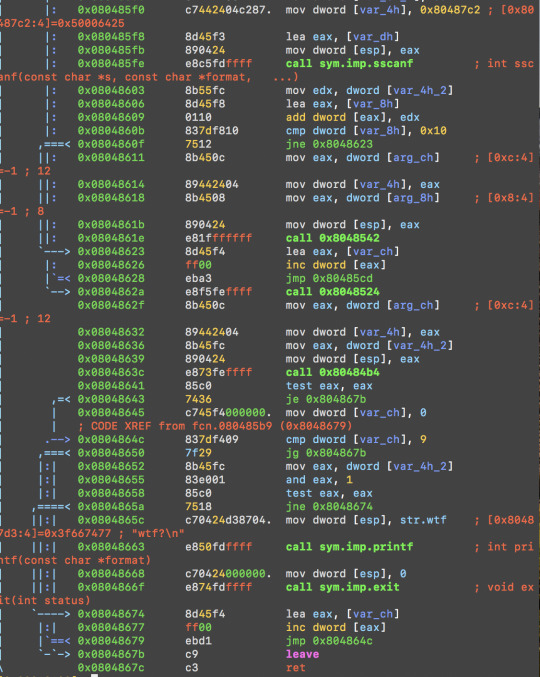
It calls several other functions: 0x8048542 0x8048524 0x80484b4. Same as the previous ones, It also does a cmp with 0x10.
0 notes
Text
IOLI_0x06
Everything’s the same as the last level except the parameters of sym.check
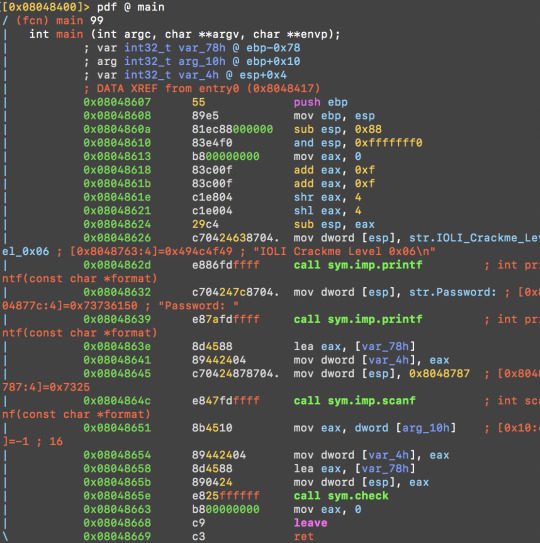
0x08048651 8b4510 mov eax, [ebp+0x10] ;get the environment value 0x08048654 89442404 mov [esp+0x4], eax ;pass it to check() 0x08048658 8d4588 lea eax, [ebp-0x78] ;get password address
0x0804865b 890424 mov [esp], eax ;pass it to check()
0x0804865e e825ffffff call 0x108048588 ; (sym.check)
The main function prints out the title and string password. Then it gets the user input and stores it to the [var_78h]. The [arg_10h] is the variable of environment variable in bash. So the parameter for sym.check() is environment variable and user input. Read about parameter passing in assembly here.
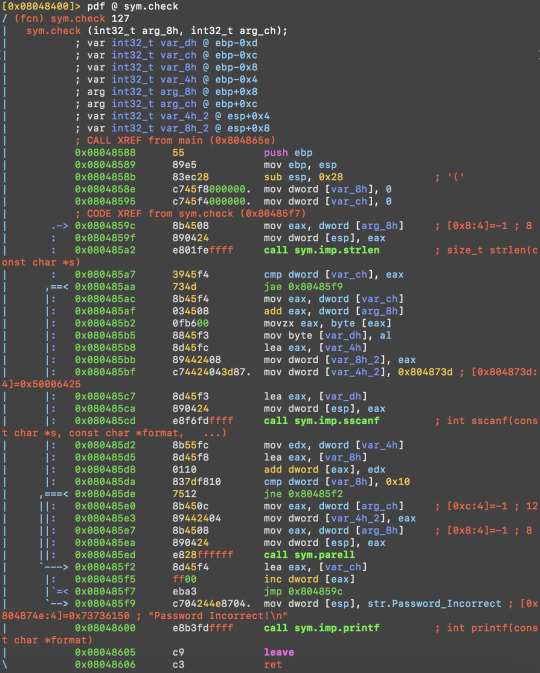
Inside sym.check, it again checks the user input with 0x10 (int 16) at 0x080485da and calls sym.parell, passing the two arguments.
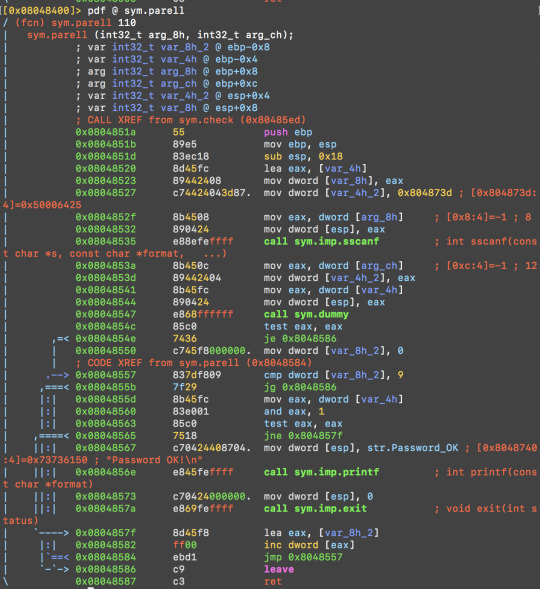
Sym.parell then calls sym.dummy, passing on the arguments (usr input and environment variable).

Note inside sym.dummy:
0x080484ee c74424043887. mov dword [var_4h_2], str.LOLO
0x080484f6 8b0411 mov eax, dword [ecx + edx]
0x080484f9 890424 mov dword [esp], eax
0x080484fc e8d7feffff call sym.imp.strncmp
The program is looping through the environment variables to see if there is an environment variable string named ‘LOLO’ and returns 1 if LOLO exists. To crack it, supply LOLO to the program. Read about setting env variables here.
$ LOLO= ./crackme0x06
IOLI Crackme Level 0x06
Password: 88
Password OK!
Alternatively,
$ export LOLO=
$ ./crackme0x06
IOLI Crackme Level 0x06
Password: 88
Password OK!
0 notes
Text
IOLI_0x05
Again there is a sym.check function called inside main. pdf @ sym.check:
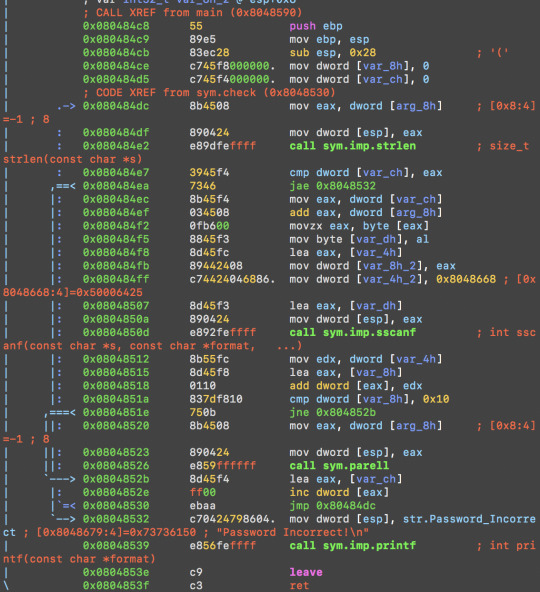
0x0804851a 837df810 cmp dword [var_8h], 0x10
Spot the comparison. 0x10 is int 16. Similar to the last crackme (0x04), let’s try 88 as the password (8+8=16):
./crackme0x05
IOLI Crackme Level 0x05
Password: 88
Password OK!
However, trying the other possibilities: 97, 79, 907 does not seem to work, but 970 works:
./crackme0x05
IOLI Crackme Level 0x05
Password: 97
Password Incorrect!
./crackme0x05
IOLI Crackme Level 0x05
Password: 970
Password OK!
I want to continue looking at the function to see why it’s causing this.
At 0x08048526, sym.check calls sym.parell. Inside sym.parell:
and eax, 1 gets the first bit of eax (the least significant bit);
test eax, eax is the same as and eax, eax (bitwise and) except that it doesn't store the result in eax. So eax isn't affected by the test, but the zero-flag is. The jne branch will be taken if not equal (zero-flag=0) --> i.e. when ZF=1 --> and ZF=1 if eax contains 1. Conversely if eax contains zero, ZF=0, the jump via jne will not happen.
Therefore, in the sym.parell function, the program reads the user input as a whole integer. As long as the input number is even number, it will output “correct password”.
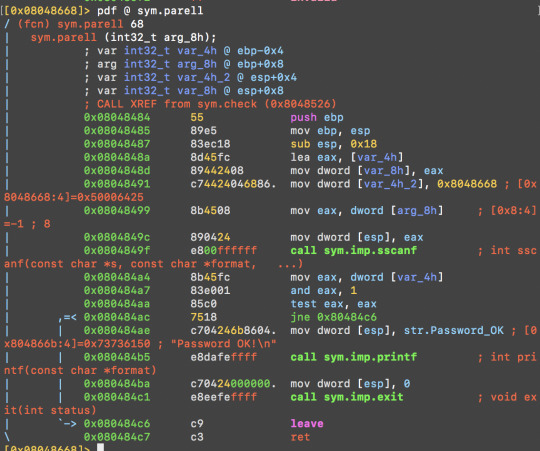
0x0804851e 750b jne 0x804852b (sym.check
0x080484ea 7346 jae 0x8048532 (sym.check
0x080484ac 7518 jne 0x80484c6 (sym.parell
I try to change the instruction at 0x080484ac to a nop so it will not jump and print str.Password_OK, but failed. Turns out we need to edit all of the above three addresses to a nop in order to make the program accept any password: wx 9090 @ address
./crackme0x05
IOLI Crackme Level 0x05
Password: ok
Password OK!
1 note
·
View note
Text
IOLI_0x04
Run pdf @ main and we see a sym.check function at 0x08048559;
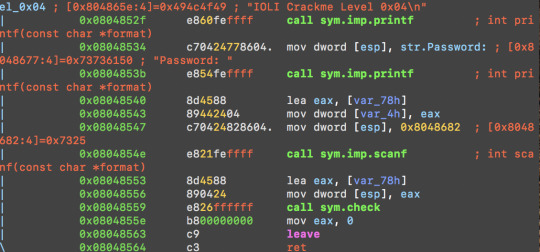
pdf @ sym.check:
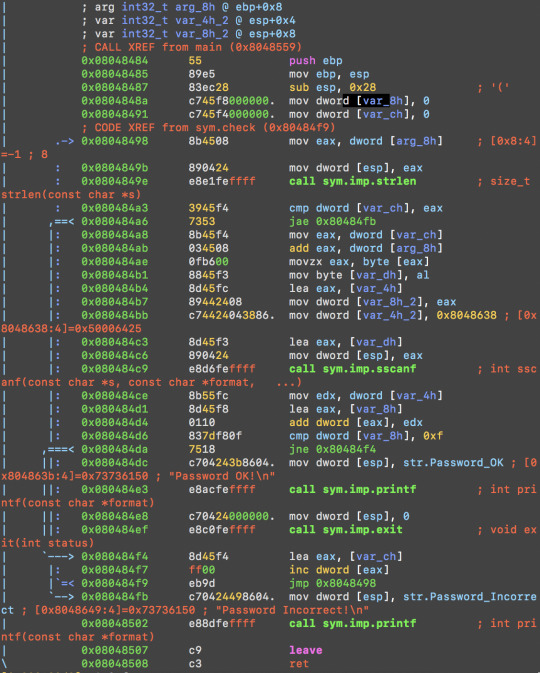
At this address, we see something is compared to the integer 15 (0xf).
0x080484d6 837df80f cmp dword [var_8h], 0xf
Tracing back, we see strlen function is called to get the string length(i.e. number of characters) of the input
| : 0x0804849b 890424 mov dword [esp], eax
| : 0x0804849e e8e1feffff call sym.imp.strlen ; size_t strlen(const char *s)
Sscanf is called to get a character from our password.
| |: 0x080484c6 890424 mov dword [esp], eax
| |: 0x080484c9 e8d6feffff call sym.imp.sscanf
With the loop for len times, which len is the length of our password, these number add together, and compare with 0xf(aka 15). So let’s try password with all digits adding up to 15.
0x0804849e e8e1feffff call 0x108048384 ; (sym.imp.strlen)
| | 0x080484a3 3945f4 cmp [ebp-0xc], eax ;;compare the length of input with counter
| | ,== length, jump to the addr
| | | 0x080484a8 8b45f4 mov eax, [ebp-0xc] ;;get value from counter which is index
| | | 0x080484ab 034508 add eax, [ebp+0x8] ;;get eax = &(input[index])
| | | 0x080484ae 0fb600 movzx eax, byte [eax] ;;get eax = input[index]
| | | ;-- eip:
| | | 0x080484b1 8845f3 mov [ebp-0xd], al ;; [ebp=0xd] = input[index]
| | | 0x080484b4 8d45fc lea eax, [ebp-0x4] ;;get addr of [ebp-0x4]
| | | 0x080484b7 89442408 mov [esp+0x8], eax ;;pass this addr as param which is ret value
| | | 0x080484bb c7442404388. mov dword [esp+0x4], str.d ;;pass "%d" as parm for sscanf()
| | | 0x080484c3 8d45f3 lea eax, [ebp-0xd] ;;get addr of input[index]
| | | 0x080484c6 b 890424 mov [esp], eax ;;pass it as param to sscanf()
| | | ; CODE (CALL) XREF from 0x080483a4 (fcn.0804839a)
| | | 0x080484c9 e8d6feffff call 0x1080483a4 ; (sym.imp.sscanf)
| | | sym.imp.sscanf()
| | | 0x080484ce 8b55fc mov edx, [ebp-0x4] ;;move ret value from sscanf to edx
| | | 0x080484d1 8d45f8 lea eax, [ebp-0x8] ;;get addr of total sum
| | | 0x080484d4 0110 add [eax], edx ;;add ret value to total sum
| | | 0x080484d6 837df80f cmp dword [ebp-0x8], 0xf ;;compare total sum with 0x0f
| |,== 0x080484f4 8d45f4 lea eax, [ebp-0xc] ;;get counter address
| | | 0x080484f7 ff00 inc dword [eax] ;;increase counter by 1
./crackme0x04
IOLI Crackme Level 0x04
Password: 69
Password OK :)
0 notes
Text
IOLI_0x03
As usual, run:
r2 -w ./crackme0x03
[0x08048360]> aa
[0x08048360]> pdf @ main
Inspecting the main function, there is a sym.test function at 0x0804850c.
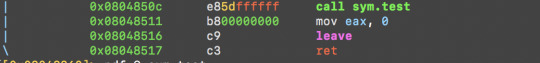
Let’s take a look at sym.test:
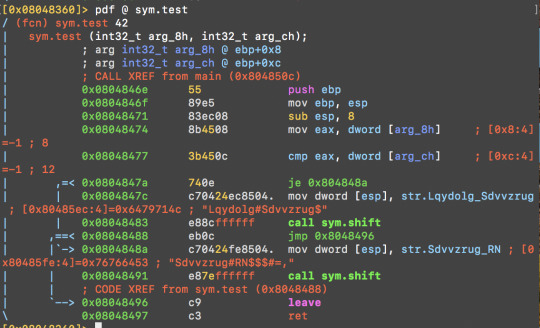
0x0804847a 740e je 0x804848a
We can try change this je to jmp.
Here, the instruction 'je 0x804848a' corresponds to the bytes '740e', if we change the '74' for an 'eb' we will change the 'je' to a 'jmp'. You can see the 'eb' is used for jmp at 0x08048488.
After seeking to the current position, use the 'wx' command to write hex values:
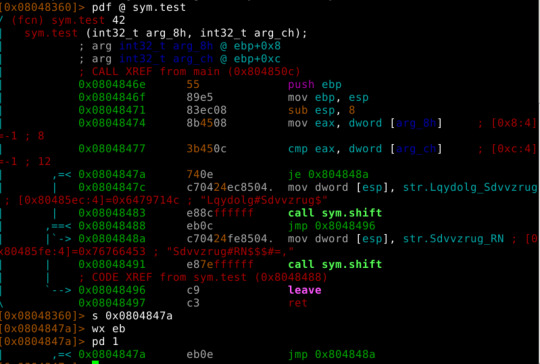
./crackme0x03
IOLI Crackme Level 0x03
Password: hi
Password OK!!! :)
Done.
0 notes
Text
IOLI_0x02
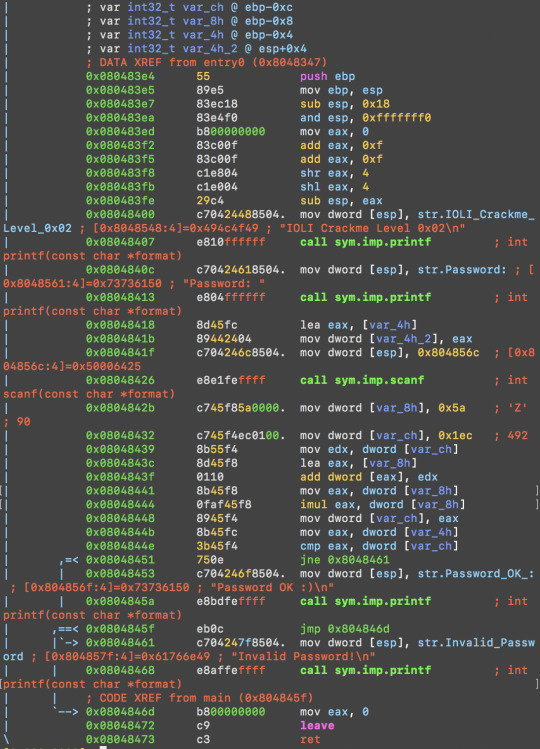
A first look at the main function is to do something at 0x08048451, which does a jump to “Invalid password” if not equal (to password). Edit this to a nop so it does nothing. Write bytes using the w command.

So we can use the wx command to write a nop @ 0x08048451. To do this, we need to open r2 in write mode (I switched to cse to run the modified program):
r2 -w crackme0x02
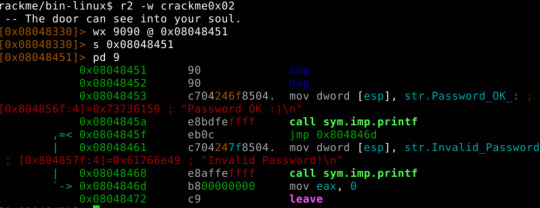
The s command seeks to the given address.
pd N disassembles N instructions.
And it worked!
./crackme0x02
IOLI Crackme Level 0x02
Password: password
Password OK :)
0 notes
Text
IOLI_0x01
As usual run it first. Method from the previous crackme did not work for this one
$ ./crackme0x01
IOLI Crackme Level 0x01
Password: password
Invalid Password!
Let’s disassemble it with r2. (These commands can be found simply using ? within r2.)
aa tells radare2 to analyse the whole binary.
pdf stands for “Print Disassemble Function”.
I can’t see anything useful, let’s look at the main function:
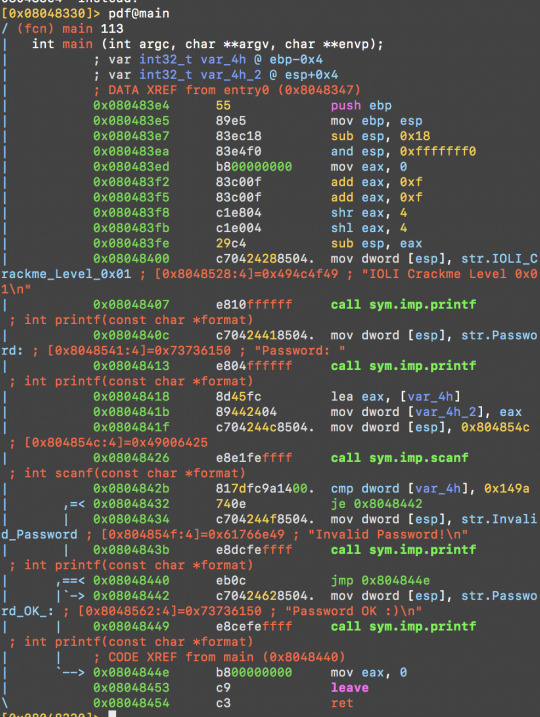
At 0x08048432 there is a je instruction (conditional jump), if we change it to jmp (unconditional jump), we might be successful.
At 0x0804842b there is a cmp instruction, with a constant, 0x149a, which is a hexadecimal number. We try convert it using radare’s ? command, which returns the answer in a variety of bases.
Here I guess it’s comparing the hex to user input ---- If we look at the top variable section we see var-4h is associated at [ebp-0x4], which may be holding a local uninitialised variable.
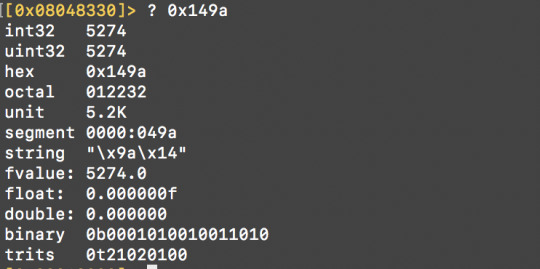
Try 5274 as the password and it worked!
$ ./crackme0x01
IOLI Crackme Level 0x01
Password: 5274
Password OK :)
0 notes
Text
IOLI_0x00
Let’s run it first.
$ ./crackme0x00
IOLI Crackme Level 0x00
Password: password
Invalid Password!
Hint is string, so I tried the following:
$ strings crackme0x00
......
IOLI Crackme Level 0x00
Password:
250382
Invalid Password!
Password OK :)
......
Noticed the 250382 might be the password. Now let’s use r2.
$ rabin2 -z ./crackme0x00
Num Paddr Vaddr Len Size Section Type String
000 0x00000568 0x08048568 24 25 (.rodata) ascii IOLI Crackme Level 0x00\n
001 0x00000581 0x08048581 10 11 (.rodata) ascii Password:
002 0x0000058f 0x0804858f 6 7 (.rodata) ascii 250382
003 0x00000596 0x08048596 18 19 (.rodata) ascii Invalid Password!\n
004 0x000005a9 0x080485a9 15 16 (.rodata) ascii Password OK :)\n
Rabin2 is the “binary program info extractor” from Radare2; -z extracts the strings from the binary data section. (use rabin2 -h to see more options) Alternatively, use iz to list all the strings in the data section within r2. Try this number and it worked.
$ ./crackme0x00
IOLI Crackme Level 0x00
Password: 250382
Password OK :)
0 notes