Text
Minor Loses Cell Phone In School And Has naked Photos Leaked In MT State (Brazil)
17-year-old teenager has had intimate photos leaked through mobile apps and an internet-dating page after having her phone stolen. The case was reported by her relatives to the Civil Police.

According to information from the Website Ubiratã 24 Horas, the young girl forgot her cell phone in the bathroom of the college where she studies. She returned to the scene shortly after, but could no longer find the device.

Days later, the girl's intimate photos leaked. In the images, apparently taken by the young woman herself, she appears naked in different places of a residence. In one of those pictures, she is taking a shower.
The images were shared quickly and generated repercussion in the city. Prints of her intimate conversations held with her boyfriend were also disclosed.

The teenager went to the police station to record a police report of the theft of her cell phone. In testimony, she claimed to have forgotten the device, but upon returning a few minutes later the equipment had already been subtracted.

What cause a stir, in this case, is that the victim did not communicate the existence, much less the publication of the images. Even with the omission of information, the case is investigated by the police. Because it is a minor, the investigations are in secrecy.
Federal Crime

The storage and/or dissemination of erotic images of children and adolescents is considered a crime by the Child and Adolescent Statute (ECA). Federal law 12,737 provides for a term of up to six years imprisonment for anyone caught in flagrante crime.

When things like that happen, I think, if she had an applock or antivirus installed on her smartphone, it could avoid this big problem. Losing a device is just a small issue comparing to losing people own privacy. If you do not want to face this fact, you would better watch out where you put your device, and if you lose it, make sure that you already have protection apps installed on your smartphone, those apps that can hide private photos/videos, lock personal apps and locate a lost phone. There are several apps that can provide command by SMS, for example, if you lost your phone, you can use immediately a bound number (friend or relative’s number) to send command by text message, in this case, if you already have saved your files in another place (a computer maybe), the delete SMS command will be the best option.
0 notes
Text
New Fraud Of Google Docs Fake File Is Frighteningly “Well Done”
The internet is a place where we can find people capable of everything for good or for bad. In addition, unfortunately, representatives of those bad stuff recently hacked into the network to perform phishing and make people who use Gmail and Google Docs feel worried.

Thanks to a frighteningly well-organized scheme, several users of the Giant Search service started receiving emails with an invitation to edit a document in Google Docs. Before doing this process, however, you had to enter the login and password in a real Google screen, but then the link would be responsible for the whole problem.
Domino effect
By clicking on the button to continue to access Google Docs, those responsible for the action had access to the user's email and some data associated with it, thanks to an application that was named "Google Docs". However, the problem is that this is not a method that anyone could recognize simply by looking at the site address, since it uses the Google system, but an app that is not the Giant Searcher.
Following, we can see an image that shows a conventional Google Docs login screen and then another confirming that users were not really dealing with something trustworthy:
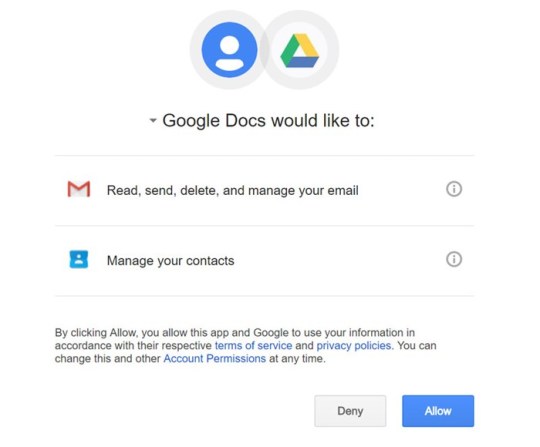
Google Docs permission screen...
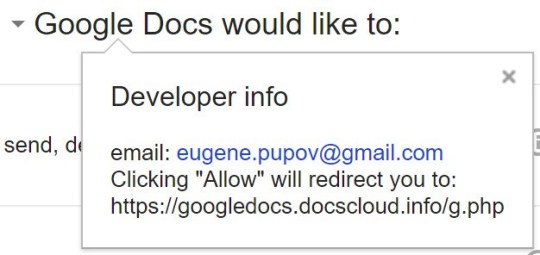
... which is not necessarily the Google Docs permission screen.
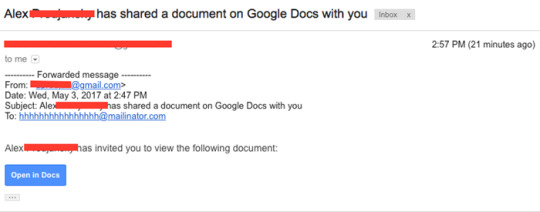
How email appeared to users
In the case of the user clicked the link, possibly several spam messages were sent to the contacts that are in the address list, creating a domino effect that probably affected several people.
Problem solved
Although this act has caught some people by surprise, at least now there is no reason to panic. As soon as it learned of the incident, Google began investigating the situation, which was fortunately resolved.
"We took the necessary steps to protect users against an email representing Google Docs and disabled the accounts that were doing so. We have removed the fake pages, made updates through Safe Browsing and our team is working to prevent this type of action from happening again", a Google official told The Verge.
Still, regarding the case, the company took the opportunity to explain exactly what happened, besides saying that no more important information was obtained in this process.
We took the necessary actions to protect users from spam that went through Google Docs and affected less than 0.1% of Gmail users
"We noticed that people were worried about their Google accounts and now we can give a full explanation after an intense investigation. We took the necessary actions to protect users from spam that simulated Google Docs and affected less than 0.1% of Gmail users. We protect users from this type of action by combining manual and automatic actions, including removing fake pages and applications and performing updates through Safe Browsing, Gmail, and other systems to prevent abuse. We were able to stop this action in about an hour. While contact information was accessed and used, our investigations showed that no other data was exposed. There are no other measures that users need to take because of this, and those who want to review the third-party applications connected to their accounts can visit Google Security Checkup", said Google.

We are fighting hard against all kinds of digital threads. Based on our present digital world, smartphone are the most used device, for this reason, we would advise you to have an antivirus installed in your phone and an applock in order to hide your private photos and videos, and also lock your apps that contain import data (bank account, password, name, ID, etc.). Do not give an opportunity to the bad luck, protect your digital world.
0 notes
Text
How to Keep Your Digital Privacy While Traveling Abroad
Travelers, beware: When you take your electronic device out of your country, preserving the security of your data is as important as protecting yourself from burglars. Whatever the reason, national and international governments may be interested in your personal data, including your social networking accounts. It is not just a theory. Many travelers, including US citizens like Haisam Elsharkawi, he has recently been pressured for allowing the US Customs Service to access his devices at the airport.
Legally, US citizens are not required to release their mobile devices, nor to share their passwords with US authorities. However, the rules vary, depending on where you are coming from, or where you are going. In addition, any contact with government officials can be inconvenient and even intimidating.
What to do in these cases? All experts agree on one thing: never lie to government authorities about passwords and accounts on social networks. “You will have an enormous problem if they find out that you were lying”, said Jeremiah Grossman, chief security strategist at SentinelOne, a digital security company. However, there are methods to protect your cell phones, tablets, and computers against intrusive searches, but without neglecting honesty.
Here are some of the best tips, based on interviews and security specialists:
1. Buy a cheap device
The best way to prevent your information from being accessed is to travel with a device that does not carry your data. It is a good idea to invest in a smartphone or cheap computer, used only on trips: you do not want the day-to-day device to end up being lost or stolen on a trip, or even examined by a customs agent. So, leave your expensive equipment at home – along with your photo album, and Facebook applications, Snapchat and Twitter.
2. Disable fingerprint readers
Fingerprint sensors, like those found on many Apple and Android devices, are an interesting security option to unlock your handset quickly. However, Jonathan Zdziarski, a security researcher, and professor of forensic science for law enforcement agencies who specializes in smartphone data collection said that when it comes to travel, you should disable this function.
That’s because, in the US, law enforcement agencies have already used mandates to require people to unlock their cell phones with fingerprints. However, because of your right to remain silent, it would be difficult (not impossible) for the federal government to require you to share your numerical password. Disabling the fingerprint sensor when traveling is, therefore, a safer option.
3. Do not memorize your passwords
The best way to protect your passwords is to not remember them. By refusing to provide a password, it is better to say that you do not know than to refuse to provide it to a customs agent, Grossman said. “If you do not know the password, it’s hard to demand that you provide it. Even if someone puts a gun in your head, there is no way to know the password. ”
Password management applications such as 1Password and LastPass automatically generate strong and long passwords for all your online accounts by storing them in an accessible location with a master password. However, Grossman said it is better to travel without the password-management application installed on the mobile phone, so police will not require you to provide the master password.
However, if you keep your important files on smartphone, like travel photos or videos, we recommend you to use an applock in order to keep your private data safe or hide them, especially against snoppers.
4. Use 2-step verification
In the unlikely event that you are required to provide your email or social network password, if 2-step verification is enabled, it will work as extra protection – assuming your primary cell phone has stayed at home.
With 2-step verification enabled, every time you enter your password, you receive a text message with an access code that must be used to complete the connection. Because the message is sent to the cell phone that stayed at home, the customs agent is not able to connect to your account even if you enter the password.
2-step verification would make the connection more difficult if your cell phone which was left behind. Of course, you can leave the phone with a trusted person and ask them to send you the code every time you go online. However, the ideal is to stay away from social networks while traveling, to prevent your information from being recorded on disposable mobile phones.
5. Encrypt your devices
Whether it is a backup device or what you use on a daily basis, always remember to encrypt the system, shuffling the data so that it becomes indecipherable without the correct key.
Computer applications such as Apple’s BitLocker or FileVault allow you to encrypt your HD, requiring a password to decrypt the files. To prevent the password from being delivered, you can write it down and give it to a friend by contacting the person after crossing the border.
6. Back up to the cloud and erase everything before traveling
When you are traveling, just access your contacts and your schedule, and maybe some photos, this is enough. However, all this information may be relevant to customs agents. Your best option is to back up this data to a remote service and then erase all data from the device before crossing the border, that`s what Zdziarski said. After you go through customs, you can use the backup data to restore the device.
0 notes
Text
Hackers Can Discover Smartphone Passwords Just By 'Watching' Users’ Fingers Movements
Technology evolves every single day, and in an increasingly pragmatic and connected world, digital criminals enhance their attack and intrusion into smart devices.

However, even with the range of recurring frauds based on sophisticated methods of breaking coding and social engineering, a curious study gained prominence this week to prove that hackers can indeed achieve their primary goals in an even more modern concept.
This research was conducted by a team of scientists at the British University of Newcastle, they revealed that cybercriminals could steal mobile passwords by simply "watching" users` fingers movements. It may seem complicated at first look, but calm down, as we explain.

Basically, the discovery of sensitive information is done by observing the data collected by the movement sensors and orientation of the cell phone, such as the gyroscope.
According to Dr. Maryam Mehrnezhad (researcher and project leader), this concept, in conclusion, can also be seen as a "critical security flaw." Applications and even web sites do not require permission to access such sensors, so malicious software can take advantage of the information without any obstacles.

With the data in hand, hackers can act similarly to a laptop touchpad, tracking everything the user does by sliding his finger on the device. With this in mind the accuracy of the sensors implemented in smartphones, hackers can identify with relative ease the position and strength of the finger on the screen, and later discover the numerical password on the phone or even a pattern was drawn.

The scientists emphasize that a smartphone or tablet has approximately 25 different sensors; this is a detail that also assists in information theft.
With the results of the research, the team involved in the undertaking warned some of the major technology giants about the failure, such as Google and Apple, who in a note said they are already aware of this detail, but for now, they have no solutions for this scenario.

Considering what was said, you can realize that protect your smartphone or similar devices that contain private information is not an easy task. Our tip is, watch what you are download, have an applock (to hide photos and hide videos) and an antivirus on your phone to avoid data leakage, and the main tip (related with this post) is, when you are typing your password, look around if you see “snooper's eyes”. If you listen carefully these tips, you are going to put a huge stone on hackers’ path, in other words, you are making the things hard to hackers.

0 notes
Text
Brazil is ranked 4th on World's Cybernetic Crimes
If 2017 will be "the year of hacking attacks," 2016 was the perfect prologue of that. According to the Norton Cyber Security Insights report, last year registered the highest number of cybercrimes to date - a 10% increase over 2015. In addition, the report shows that Brazil is one of the countries with the highest cybercrime activity in the world. The world, ranking fourth.

In Brazil, cybercrime caused a loss around 10 billion in 2016: virtual crime is already a market
Norton indicates that more than 42 million people have been affected by cybercrime. That means a loss of 10 billion US dollars, in total (world), we are talking about more than 150 billion. Norton also commented that the most damaging attack is ransomware.

Ransomware can be defined as server hijacking. Cybercriminals invade computers and "lock" machines - the main targets are small and medium-sized businesses. In this way, they require a sum of money to return control of the machines and release the files.
"Big companies already spend a portion of their technology quotation to security. This is not yet the case in small and medium-sized businesses. Just as in the 'physical' world, criminals seek ease, so these companies fall into this situation more often", said André Miceli, professor of the Digital Marketing MBA at the Getulio Vargas Foundation (FGV).

Indonesia is one of the countries that suffer most by black hats
The United States, among developed countries, is the one that suffers most from cybercrime. On the other side, we have Holland with the lowest virtual crime rate in the world. Globally, Indonesia leads the rankings of cybercrime experiments.
"In the coming years, we will certainly see the explosion in the number of connected elements." Insulin pumps, cardioverters, pacemakers will be connected. Accelerators and autopilots, home controls like air conditioners and stoves as well. Opportunities for invasions and certainly criminals will take advantage of them to make money", comments Miceli on the increase of gadgets in the Internet of Things.

According to what it was said in this text, with respect to electronic devices protection, all care you take will not be enough! However, you can do something to complicate a hacker’s or snooper’s life. Fist tip is, download an antivirus for your phone or computer and keep your operating system safe, by remember to use only one antivirus, if you use two or more, one antivirus may conflict with another one, then it will let a loophole for the cybercriminal. Second tip is (specially for your mobile device), download an applock, this kind of app can protect your private data and devices against “physical threats”, probably you have personal photos, videos etc., that you do not want to share with anyone, so this kind of app can avoid your data leakage even your phone is lost. The value of our privacy is more precious than the value (money) of a mobile device, so take care with your data.

Another interesting point of Norton's research: Most respondents in all countries prefer to have their own smartphone formatted than the browser's history open to the public. What do you prefer? Give your opinion in the comments.
0 notes
Text
Think 10 Times Before Touching Your lover Mobile Phone!
Now a days smartphone is almost a member of humans, where almost everything in people's lives revolves around WhatsApp, Facebook and the emails that come every minute in our hands, the question is: "How not giving a look at your lover’s (husband, wife, boyfriend, girlfriend) smartphone?"

It was unintentional, she left the computer open, he saw a "suspicious" email and the relationship went ways! Arrived an SMS from the "ex" in the middle of the night the wife saw and chaos in the relationship was established.
We already know thousands of similar stories and that is a reason for fights before the wedding, so, in order to avoid loving catastrophes, we have decided to list these tips for you to think 10 times before touching the cell phone of your love.

1. Is there anything worse than someone messing with your things? Even your partner who you trust and who you imagine has nothing to hide! However, taking other’s mobile cell is invading his/her space, privacy, and individuality.
2. Control yourself! If he/she left the email or Facebook opened, the cell phone on the table and went to bathe, it does not mean that you are free to snoop everything he/she talks to his/her friends. If it upsets or insults you, close them at the same time.
3. Do not know his/her passwords. Okay, know the password for a moment to help in something urgent, in cases like you be on the street and need to send an important email: "Love, go there in my email and forward that email to me, my password is ..." there is no problem in this case! However, the very ideal is you forget this password! You should ask her/him to change it.

4. "Not even a spy!" A simple "hahaha" for a jealous person can turn into a "hahaha, let's leave tomorrow what time?". Do not spy, do not create fantasies, do not imagine things! If you suspect something, talk. There is no reason to stay with someone who you do not trust, isn’t?
5. Imagine someone messing around on your cell phone? You, even though you have absolutely nothing to hide from your love, would you like someone to take a walk, reading all your conversations, emails and chats?
6. If you see everything on your lover’s mobile phone, does it mean that you would also see his/her wallet, drawer, calendar, social network? After all, what is your goal? Did you like it? Take a deep breath, go for a walk, have a drink and forget about this!

7. If you search, you will find. The theory is: if your lover is careful and is betraying you, he/she will delete the conversation history and hide photos that can prove his/her betrayal. Do not waste your time!
8. We see what we want to see. When you look at other’s cell phone, you are in search of something. That is a good time for you to reflect: why am I losing my precious time with this insecurity?
9. Above all, respect and trust are the basis for a healthy relationship. So our 10th tip is

10. Blur your attention, dribble your curiosity and your silly jealousy: do anything except wasting your time digging in the cell phone of your love!

We want to know your true opinion on the subject!
0 notes
Text
Military Police in Brazil Launches Website to Locate Stolen Smartphone Through IMEI
Smartphone owner can know handset IMEI number by typing *#06#; this new tool can be used anywhere in the country

Imei number can be registered on site
An initiative of the 48th Military Police Battalion, in charge of the city of Ibirite, in the metropolitan area of Belo Horizonte city, it can help locate stolen or lost cell phones by checking the International Mobile Equipment Identity (Imei) contained in each device. For that, the site "Celular Seguro" (it means “safe mobile phone”) was created, where each citizen can register the Imei of his cell phone and inform the Military Police in the case of robbery or theft.

The idea of developing the tool came because of the high incidence of smartphone theft and robbery in the city and in neighboring counties. "With constant theft and robbery, our team has developed this pilot project, which works as follows: the person, from anywhere in Brazil, can access the site and register their personal and telephone information, such as Imei and The appliance. These data are stored and, if the device is taken, it accesses the site again and communicates to us", explained the battalion commander, Hercules de Paula Freitas.

According to the captain, it is possible to track devices using the Android, iOS (iPhone) or Windows Phone systems and find out their location. "In the case of approaches of suspicious people, we will ask to verify, in addition to personal documents, the phone number of the Imei. If this identification number is registered in the system, we will ascertain if this suspect has participated in this crime. We are going to see if he is responsible for theft or he is just a receiver", the police officer explained.

In one day, the site received more than 3,000 mobile phone registrations. On the page, you can also learn how to set up and use the tracker tool. The tool as released on August 24th (2016), by the Military Police.
Anyone can know your Imei number by typing *#06#.

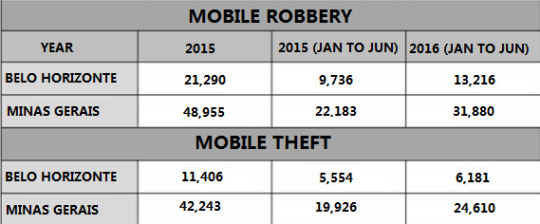
Robberies and thefts in the State in 2016 already overcame the number registered in 2015
From January to June of last year, the robberies and thefts of cell phones in Minas Gerais State have already surpassed the number registered in 2015, in the same period. According to data from the State Secretariat of Social Defense (SEDs), 31,880 cell phones were stolen in the state in the first six months of 2016, against 22,183 last year. The same relationship can be observed in a number of thefts, which rose from 19,926 cases in 2015 to 24,610 in 2016. See:
Sometimes the big problem is not losing a phone, but losing or leaking private data, so we recommend you to use Private Zone app, this is an applock which not only provides you lock apps and hide files functions but also it can provide you track service by SMS command, if you lose your smartphone you can send an SMS from bound number to your lost number in order to lock your private stuff, delete your photos or locate the position.

0 notes
Text
The Most Secure Applications And Programs For You Not Be Watched (Part III)
ProtonMail is one of the best (and easiest) email solutions

• Gliph is available for Android, iOS, and desktop. Its secure messaging functionality allows for encryption using SSL and supports a safe message deletion. There is also a self-destruct feature for messages that can be set to expire after a certain time. Unlike other messengers, Gliph also supports secure group messages, allowing you to speak securely to multiple people. Gliph supports Bitcoin payments that allow you to send (or receive) money securely to (or from) contacts.

• ProtonMail (email): ProtonMail is yet another e-mail exchange solution: it is the largest encrypted e-mail service in the world. Sure, ProtonMail brings easy-to-use email encryption to the mobile device, perfectly integrating end-to-end PGP encryption. It also provides a modern user interface with a full set of innovative features such as customizable slip gestures and the ability to send expired emails. For Android, iOS, and desktop.

Using Chrome
If you plan to use Google Chrome as your primary browser - some solutions shown here also work in other browsers - you also need to increase the security.

That's why staff from the hacking group HatBash even indicated some programs and extensions for you to try out in the browser:
• Comodo Firewall: protects against Internet attacks, such as spyware, adware, etc. So, Comodo is one of the best firewall options to use, unlike the native Windows firewall - the only operating system that Comodo works.

• ZenMate VPN: encrypts all your traffic and hides your IP address so you can browse the internet anonymously. This VPN also allows you to change your virtual location so that you can unlock restricted sites within your area. It offers more than 30 VPN server locations to choose from, including the UK and US. Available for Windows, IOS X, IOS, and Android.

• HTTPS Everywhere: Designed to encrypt the web, automatically use HTTPS security across multiple sites. Many web sites offer limited support for HTTPS encryption but make it difficult to use. For example, you can use as default to unencrypted HTTP or fill encrypted pages with links that return to the unencrypted site. The HTTPS Everywhere extension corrects these issues by using clever technology to rewrite requests to these sites for HTTPS. In other words, it automatically changes thousands of unsafe sites over HTTP to HTTPS (secure). It will protect you against many forms of surveillance and account theft among others. Available for Firefox, Chrome, Opera and Firefox for Android.

• uBlock Origin: is not a mere "ad blocker": it is a wide-spectrum blocker that blocks ads, trackers and malware sites. It can read and create filters from host’s files. By default, these filter lists are loaded and applied through EasyList, EasyPrivacy, Peter Lowe's ad/tracking /malware servers, various malware site listings, and uBlock Origin filter lists. It is effective and still has low memory and CPU consumption. It is available for Firefox and Chrome.

I hope this information helped you, be aware while surfing and sending messages online, even you have an applock (to lock apps), antivirus, and a lot of care. Hackers are more and more professional now a days.
0 notes
Text
The Most Secure Applications And Programs For You Not Be Watched (Part II)
PRISM was one of the programs used by the NSA to spy citizens

It is interesting to note that the subject before 2013 was treated by most people as "conspiracy theory". Today, the game has already begun to turn. Especially when, in the year cited, former NSA analyst Edward Snowden revealed details of the PRISM surveillance program developed by the United States in partnership with the United Kingdom.

The only PRISM, already revealed, allows NSA (National Security Agency) employees to collect data from users connected to the Internet. In other words, search histories, content and exchange of emails, file transfers, photos, videos, documents, voice calls and video chats, social information, and passwords placed on websites are easily obtained.

Edward Snowden, one of the most important representatives in data security and mass surveillance
Secure Messengers
Smartphones are the primary targets: because they are closer to the user than computers, they are more data and information to watch over. So there are a number of applications that are designed to keep your conversations safe.
(Remember that applock should be a good choice for safety, you can lock app against snoopers, but you need to consider other problems)

It's important to note that security applications do not make a miracle, the user must have a basic notion of where to click or not click, what to download or not to download etc. A classic example is the emails saying that you won a lottery that not even participated or SMS messages with a similar context. You must also remember that the applications that are in the Play Store are not 100% safe, that is to say, they may contain some malware, so before downloading it is always good to take a look at the reviews of other users and use some antivirus to check the Application situation.
The minimum you need to look for in an app: encryption

To exchange messages, HatBash people recommend Signal: it is an application for communication like Whatsapp or Telegram, "however everything that travels through the application is encrypted, as well as having the client and server source code open."The Signal is available for both Android and iOS smartphones and works with an extension for Google Chrome.
Another app for exchanging messages is Frozenchat. FrozenChat also offers end-to-end encryption with OTR (Off the Record) messages. It means not only your messages are protected but also you can see whom you are talking to. However, there is a possibility of message manipulation after the conversation is over, in other words, it is impossible to prove that any message has been sent by you.
More secure messenger apps indicated by groups are:
• ChatSecure supports Off the Record messages and the open XMPP protocol. The Android version is no upheld anymore, but iOS version is still being developed. When you start a conversation, you will see a "fingerprint" that you can check with your friend to make sure no one is intercepting messages. ChatSecure allows you to use Tor. This should hide your location when sending contacts via messages. Try using an XMPP server that uses a hidden Tor service to keep your conversation entirely on the "dark web" as it is safer.

•Silence: A great replacement for the regular Android SMS app. It stores all the messages you receive in an encrypted database (by default, this is not protected by a password, but you can set one if you wish). If two people are using Silence, the application will automatically recognize this and use end-to-end encryption to send text and media. Otherwise, it can work as a regular SMS app. The most important is that Silence is open source so experts can check if your code is free of vulnerabilities, deliberate backdoors, etc.

• Silence Phone: from the same people as Silent Circle - leaders in the mobile security industry (and Blackphone makers). It enables secure messaging with your contacts as well as free audio voice calls along with file transfers. Other features include a quick shutdown button and a cleaning feature to delete all your personal data. The application is open source and can be verified by experts for vulnerabilities. It is free to download for iOS and Android, but you need a paid subscription ($ 9.95 per month) to make use of all features.

0 notes
Text
The Most Secure Applications And Programs For You Not Be Watched (Part I)
Mass surveillance, in fact, is real. What began as a rumor, now became proved by official documents leaked, today begins to be treated the way it should always, that is to say, with caution. There are several levels of vigilance: in the first and most common, the Internet user is nothing more than a “product”, and you are just like money for some social network to sell your presence to some company. For example, in the last level, as proved by several informers, you are targeted by the government and cybercriminals - which, in many moments, they get confused.

Vigilance violates civil liberties, which guarantee their safety, freedom conscience, religion, expression, association and, above all, the right to privacy.
There is a truth that cannot be denied: if you access the internet, you can be found and somehow monitored. However, there are also several ways to reduce this vigilance and make it much harder for hackers, companies, and even governments snoop your messages, emails, photos (this one the worst problem, that`s why I use to hide photos in order to avoid this issue), cameras etc.

If you have read until here, and you are not understanding well what mass surveillance is and the data revealed about it, read on in the news about how the CIA, the central intelligence agency, monitors electronic devices.
We are going to show you what software, applications and media you can protect yourself if that is your intention. However, before that, we need to understand a bit more about this surveillance.

To what extend are we being spied?
You've probably researched product prices on the internet, have not you? So, you also noticed that after this search, several advertisements about the product or similar start appearing on social networks and other sites, right? Know that, in a simple way, is just a spark of mass surveillance that exists on the internet. It's just part of your browsing trail being used for profit.

If you are thinking, "But I do not do anything wrong, then there are no problems if you spy on me", know that you are wrong. Mass espionage violates civil liberties, which guarantee your safety, freedom of conscience, religious freedom, expression, association and assembly and, above all, the right to privacy. The definitions often are blurred between a state security and profit for companies. However, if you give up privacy and see no problem in being treated as a product, the next few tips may not be for you.
Applock could be a good option for protection, but you need more tools.
To be continued…
0 notes
Text
Losing Photos From Smartphone Is Worse Than Ending A Relationship, Says Research
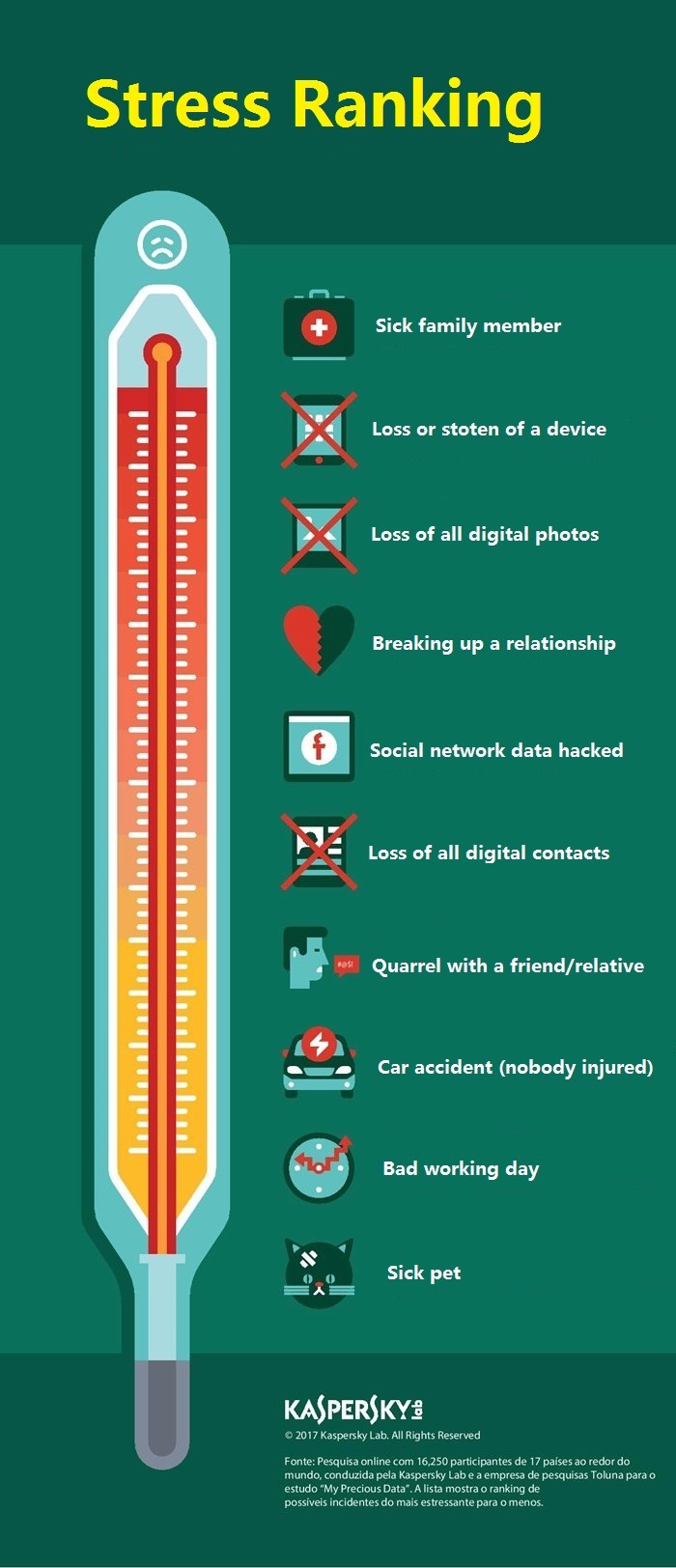
Digital memories are the records of unique moments in people's lives. For this reason, the loss of these data can be synonymous of problems and stress. According to a study conducted by Kaspersky Lab, 49% of people said that most precious data is their mobile phones are confidential and particular photos, followed by photos of their children and spouses.

Still, according to research, missing pictures is worse than having their social networks hacked, suffering a car crash, owning a sick pet, having a bad day at work, or even ending a relationship (wow, I have never thought about it!).

According to the ranking, conducted with 16,250 participants from 17 countries, the only events that are more important than this loss are the device loss or theft and sick family members, respectively.

With the proliferation of online threats, the chance of data loss on devices is high. This risk increases even further when you consider that only 46% of users protect their devices with a strong password and/or combinations, leaving most smartphones vulnerable to hackers and thieves.
In order to protect your files, you can follow some simple and effective tips:
• Protect your device with a password or other method, such as fingerprint recognition (an app lock will be a good idea for locking personal and social media apps which must have your important data and photos) . Remember that they will provide effective protection only if there is the required complexity.
• Back up your files regularly. It is important to use two alternatives: cloud storage (Dropbox, Google Drive, etc.) and another on a physical device (a portable hard drive, USB, other PC, etc.).
• Use a strong security solution to protect data on multiple mobile devices. In several web sites, you can find many options to download.
• Do not charge your smartphone or tablet using a USB port connected to a computer unless it is reliable because it may be infected with special malware installed on the PC. The best thing to do is to plug the phone directly into the power adapter.

For you, what is the most stressful incident in the digital world? Tell us in the comments section!
0 notes
Text
Top 6 Best Games For Android (April 2017)

In this middle of April, we are going to show you 5 new games for smartphone that your must have in your smartphone, recently we have told your several tips for lock applications on your smartphone and we have introduced you some app locks which focus on private protection, but now we are going to introduce you interesting and fun games, enjoy them!
1. Transformers

We started our list with this game style, bringing the famous franchise of robots disguised in a fighting game. The main highlight of TRANSFORMERS: Fighters stands for the huge amount of available Autobots and Decepticons, spanning from the classic series to 3D animations and Michael Bay's films. Moreover, in this game, you can combine sequences of scams and try to avoid opponents attacks.
2. Crash of Cars

Crash of Cars puts you in a crazy derby among even crazier cars. In this game we can play with a lot of kind of vehicles like cars, war tanks, ice cream truck etc., all of them can be equipped with a lot of weapons, the game is a simple, and you can play in multiplayer mode to fight and defeat your friends, and then get as many points as you can.
3. Age of Empires: Castle Siege

Age of Empires: Castle Siege is one of those strategy games that put you to control as a leader of an entire kingdom. Their job is to grow and develop the place, creating new structures and generating resources for them. After that, of course, you can always send your soldiers to attack the neighboring kingdoms in search of a little wealth.
4. 3D Billard Game

As you know, this kind of game is quite famous for smartphone devices. Playing 3D Pool Game, you can challenge other players (or even the computer itself) for classic table game matches. Unlike many games of the genre, the game highlights for its totally three-dimensional look, as well as for giving careful control of the angle, strength, and effect of the shot.
5. Battlefield Combat Black Ops 2

Battlefield Combat Black Ops 2, on the other hand, is an FPS for fans who like a good challenge. Offering single player and multiplayer modes online, the game is a test of precision and speed with its small phases since the enemy can be just ahead in every corner.
6. Sword of Shadows

To finish today’s list, we bring you an incredible anime-style MMO. In the adventure, you embody a warrior in his mission to protect the ancient domain of Jianghu from evil forces, fighting whatever comes forth in an action RPG. The main highlight of the game is the presence of several classes, each one can offer distinct styles of gameplay.
Then… this is the end of today`s list. Did you like our tips? What was your favorite game among them? Is there any missed information about them that you want to share with us? Leave your opinions in the comments.
0 notes
Text
Finally An Ad Blocker for Windows Phone, Android, and iOS
Here, I have talked about how to lock apps and what is the best app lock for your smartphone, but now I am going to show you a new tool to your beloved mobile phone, an ad blocker.If you are looking for an app to block advertising on your mobile phone, it is time to forget about it and save much more space. Thanks to the technology developed by Opera team of engineers, now the Opera browser for Android, iOS, and Windows Phone have integrated and totally free ads blocker! This is incredible, isn't?

With the new Opera browser update for Android, there is an available version of Opera Mini for iOS and Opera Mini for Windows Phone.
I would like to share this news with you, since finally, this technology is available for all versions, from computers versions to smartphones versions.

On smartphones, Chrome is 14% slower than Opera, with its built-in ad blocker
The Opera team have done a lot of testing and they have found that Opera is faster than Chrome for loading sites, and this is possible thanks to ad blocking technology and the built-in data compression technology in the browser.
Even with the data saving feature enabled, Google Chrome takes 14% of the time more than Opera to load a website, while with the Adblock Browser, the time is 79% higher (on average).
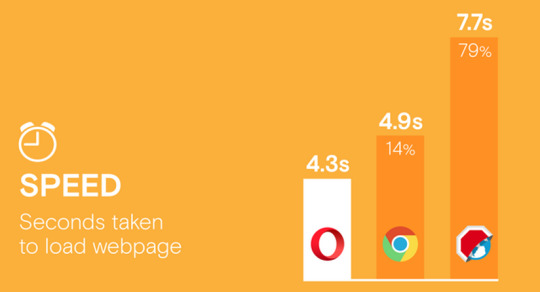
In Opera for Android, the data downloaded per site is 229 kb with the ad blocker enabled. Chrome consumed 47% more data and Adblocker Browser consumes on average 3.4 times more data.
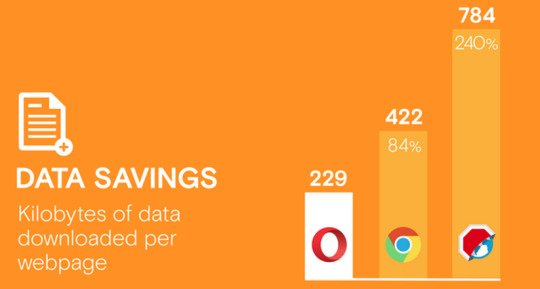
A Recent research by PageFair has shown that the demand for software that blocks ads on smartphones is 419 million people today, which is 90% higher than last year. Recently the number of smartphone users these years has increased a lot comparing to computers users, that is why this survey also showed that the number of users searching for ad blockers on their mobile phones is twice as many as those seeking to block ads on computers. Creating an ads blocker for Windows Phone, iOS and Android, in fact, was not a bad idea!
Try now!
Thanks to the built-in ad blocker in the browser, you are going to save time (searching for the application or extension, downloading, installing etc.) and you will get a faster and stable navigation.

To activate the ad blocker, just follow these simple steps below:
• Opera for Android: to activate, just go to Settings in the "O" menu and then activate the "Block ads" option.
• Opera Mini for iOS: This is a procedure similar to Android, just activate the switch in the option of blocking ads, available in the "O" menu in the save option. The ad blocker is available in Opera Turbo of Economy Mode.
• Opera Mini for Windows Phone: Just under the "O" menu, just go to Settings and activate the Ad Blocking function.
How about you guys? Have you ever used this ad blocker on your mobile phone? How does it work? Please, share with us your experience and, if possible, give us suggestions and ideas, you will be welcomed.
0 notes
Text
Samsung Galaxy S8: 2,800 US Dollars Gold/Platinum And Active Version!
Know the Samsung Galaxy S8 which costs about 2800 US dollars
There is a shop in the United Kingdom called Truly Exquisite. The company offers products “truly exquisite”. In the case, it has now become the first luxury goods store to offer a Samsung Galaxy S8 and S8 + customized with items like platinum (24 carats) and pink gold (18 carats).

Come to spend 2,800 US dollars in a new cell phone with the gold or platinum edge.

It should be noted that the customization is not heavy: the Truly Exquisite only covers the metal edge of the device with the precious items, and that is enough to raise the price of the Galaxy S8 + to up to $ 2,800 in platinum version 24 carats.
It is worth noting that the Samsung Galaxy S8 and S8+ have not yet had official prices revealed when Truly Exquisite revealed its customized S8 and S8+ price.
Each smartphone customized by the British store arrives inside a collector box, base to load the device, a Samsung Gear VR (normal, without gold and glitter), a golden power bank and a leather wallet.

The Truly Exquisite store, despite already accepting orders, says it will only start delivering the device at the end of May. They offer deliveries worldwide and there is a 6-month insurance for the device. See below the photos of the offers.
Leaving the Snapdragon 835 and Adreno 540 GPU aside, the highlight of the device, in this case, is in gold or platinum.
“For free”, you still carry collector’s box, base to carry the device, a Samsung Gear VR, a golden power bank and a leather wallet.
The store does not change anything beyond the frame of the device: software, hardware, and design are the same.

Frame
Tough device! Samsung may launch Galaxy S8 Active in June
Samsung has several devices on the market with the “Active” line – which usually come with some special features for sporting or adventurous people. However, with the arrival of the Galaxy S8, the company has already shown the waterproof version for consumers… So, is the Active needed?

There are rumors that the company will even launch this new smartphone until June of this year. According to SamMobile, the SM-G892A device is being called internally on Samsung’s “Cruiser”. Moreover, what is the focus of the device? Apparently, resistance.
In addition to being waterproof, it would be more resistant to impacts and falls. For this, there is a good chance that Samsung will have to give up the Infinity Display and the curved corners to bring tougher edges and less exposure to possible accidents.

It is also worth mentioning that there is a possibility for Galaxy S8 Active will at first appear as an exclusivity for AT&T in the United States. Will this be confirmed? If the rumors are correct, we will know the truth in about two months.
Personal Data is More Valuable Than a Device Price

You must know, Samsung Galaxy S8 is an expensive smartphone to the majority of people in this world, in fact, it is a just launched device. However, losing a phone will just affect your “purse”, in contradiction leaking personal information and data may affect your privacy, there is a huge problem. For this reason, we recommend to your lovely smartphone a good app lock. Private Zone is a complete applock which can give your several functions as lock apps, hide files, track lost phones (SMS command to locate the position of your lost phone and delete the information on it), break-in alert ( a selfie of a snooper who inserts a wrong password) private browser and more. Prevent that this big problem happens to your phone, be protected!
0 notes
Text
7 Biggest Problems Found On Galaxy S7 And How To Solve Them

The Galaxy S7 was one of Samsung's greatest hits, in terms of both functionality and its premium design, but we know full well that no smartphone can be perfect. Like any mobile device, it may also present some very annoying bugs, but they can be solved without too many difficulties. To know the 7 biggest problems of the Galaxy S7 and its possible solutions, just check our tips below!
1. Wi-Fi Problem

Many users of the Galaxy S7 are having serious problems with Wi-Fi on their handsets. In some cases, the connection becomes too slow, falls, or fails to synchronize applications that need the Internet, such as emails and social networks.
For some people, a Bluetooth is turned ON can interfere directly with the internet received by the device, something highly unusual. Fortunately, Samsung has already pronounced on the subject and admitted that this is really a problem of the device software.
The good news is that the company has prepared an update to correct these errors and is already making it available around the world. If you are still experiencing this problem, just check if your Galaxy S7 can already be updated.
2. Slowness

If you notice that your Galaxy S7 is getting very slow or underperforming, it is quite possible that the reason is a feature of the device itself. As you may have noticed, your smartphone has a default widget called "Briefing," which appears when you drag the screen to the left.
This Briefing serves to show you news from various sources, which can be useful for many people, but that can also leave your device much slower than normal. The simplest way to solve this problem is simply by removing the Briefing from your home screen.
To do this, press anywhere on your screen until the widgets and wallpaper options are displayed. Go to the Briefing screen and you will see a button to turn it off.
3.Bluetooth Problems
Like Wi-Fi, Bluetooth has also caused several problems in the Galaxy S7. Many users have noticed a slowness when the feature is turned on, and in some cases, they have been unable to connect or use their Bluetooth accessories properly.
This also depends on the update provided by Samsung to fix system bugs, so try upgrading your smartphone as soon as possible. In cases of bluetooth accessories that do not work right, it is always good to check if they can be used properly in another device.
4.Self Closing of Camera

It is already becoming common to see new smartphones have problems with the camera in its early life, and the Galaxy S7 has no exception. In the case of the Samsung device, many users are getting the message that "Camera failed" shortly after opening the app to take a photo.
When this happens, we recommend that you restart your smartphone to see if the camera works normally again. Samsung is likely to make future updates available for the device's camera app, but until then it is preferable that you use another app to take your photos with no problems.
5. Wet Speaker

As already explained by Samsung, the Galaxy S7 offers dust and water resistance, but this does not mean that it is waterproof or other liquids. In practice, it can stand up to 30 minutes underwater if the depth is not too high.
It does not mean that it will work perfectly while it is soaked, something that many users do not take into account. One of the best examples for this is when the speaker starts to work in a strange way after the smartphone gets wet.
In such cases, it is necessary to wait for the appliance to dry up so that all its functionalities begin to work properly. In the case of the speaker, there is not much to do, since you can not dry it manually and you should have to be more patient.
6. Excessive Heating

It's quite normal for smartphones with powerful processors to heat up when the user performs heavier tasks, but the Galaxy S7 can get really hot in certain situations if you are not being careful. Our tip is that you stop using the device for a few minutes if you notice that the heat is starting to bother your hands.
Another suggestion is that you do not use heavy apps while your smartphone is charging, as the battery charge itself makes it hot enough. The combination of the two can make the S7 unbearable from being so hot, to make sense.
7. Self Restarting

In some rare cases, you may come across the problem of the Galaxy S7 rebooting alone for no reason. The truth is that this can happen with many devices that do not use the pure version of Android, which is the case of Samsung handsets.
This usually happens due to some system error and is fixed in updates made available by the manufacturer itself. To ensure your S7 runs smoothly, ensure to update your Android and its apps.

Now you have learned how to fix your S7 in case of problems or bugs, but we have another recommendation to your, protect the date in your phone with a good applock. Mobile phones are vulnerable to be lost or stolen, so in order to avoid personal date leakage, use an app lock complete and smooth which can provide you not only track lost phone commands by SMS, but also hide files, lock apps, private browser and customized lock screen, these will protect your smartphone against thieves and snoopers.
0 notes
Text
Security: Four Methods For You To Put A Password in WhatsApp
WhatsApp recently surprised the world by launching in a very important resource for anyone who cares about security in the digital world: end-to-end encryption. With this, you can rest assured and make sure that your chats will not be viewed by others, such as hackers, spies, and even intelligence agencies.

However, the most famous communication application in the world still does not offer functionality that is much sought by its users. We are talking about the possibility of locking the program with a password, preventing unauthorized access from third parties who take over their mobile device.

Of course, if you are a sensible person, probably you already use a general password that protects your phone as a whole - that's enough to keep your WhatsApp safe. Still, if for any reason or consequence you really want to block only this particular utility, here are four methods that you can use.
1st Method – ChatLock+
ChatLock + is a free application for Android capable of blocking not only WhatsApp but also other messengers such as Facebook Messenger and even its client - SMS standard. It can be installed on any device with version 2.3 or higher operating system and is still compatible with the latest OS editions.

It is very easy to use. The first time you open ChatLock +, the software will prompt you to register a numeric password with four digits (PIN). It is necessary to enter the password twice since the second one is a confirmation. Then, you will see the list of apps that can be protected by the utility, tap the "On" button for WhatsApp. Now, when you open the messenger, you need to enter the PIN that was previously registered to access your conversations.
2nd Method – WhatsApp Lock
It is a very interesting tool and equally easy to configure. As in the previous item, WhatsApp Lock will prompt you to register a four-digit numeric password the first time it is opened. The difference is that the user also needs to register a secret answer to some predefined question, which will serve as a backup if you forget the PIN.

Once the password setting is complete, the program will already be working and protecting your WhatsApp properly. The software is also capable of blocking other messengers (Hangouts, Snapchat, VK, Kik, WeChat, Tango etc.), and if they are installed on your smartphone, simply tap the lock icon next to their names to extend the protection to these other platforms. WhatsApp Lock is completely free, and requires Android 4.0 or later.
3rd Method – CM Security
Developed by Cheetah Mobile, CM Security is a complete security solution for Android devices, including an antivirus tool. However, its only feature we care about at this point is AppLock, which is able to absolutely lock any application installed on your device.

Just open it, tap "Block App", choose which applications you want to lock and press the "Protect" button. This time, you will not use a numeric PIN, but rather an unlock pattern (which many find much more practical).
4th Method – Private Zone
Developed by LEOMASTER, Private Zone is an applock with a lot of function focusing on user`s protection. As the items before said, just after your install Private Zone, it will prompt you to hide your important photos, hide your important videos, lock most used apps (and WhatsApp) and set a lock pattern, if you desire you can tap below on the “PIN” option and change your lock password to a four-digit numeric password. While you are using this app, it may prompt you also to set a secret answer to some predefined question, which will serve as a backup if you forget the PIN (same as the WhatsApp Lock).

As I told your, Private Zone is and complete app which can provide you many functions as hiding files, private browser, customized screen lock tricks, boost, lock wallpaper, track lost or stolen phone and more functions. If you want to use a one-in-all applock, I recommend this one here. In fact, the same app is available for iOS, but it will not be as full as on Android, probably it is due to system limitations.
register a lock pattern and numeric password with four digits (PIN), then, you will see the list of apps that can be protected, tap the "On" button for WhatsApp.
0 notes
Text
Enjoy 7 Plus Is The Newest Phone From Huawei For The Incoming Segment

Gigantic in China and seeking more and more space around the world, Huawei has shown its strength in the mobile sector. Owning the third-largest share of this market during the first quarter of 2017, the company has incredible gadgets like fantastic flagships and entry model that combine “good and cheap”. Last Tuesday (11), the company revealed that it should increase its stock in this last segment with the launch of Enjoy 7 Plus.

According to the material released by the Chinese brand, the device must be the successor to the Enjoy 6 and has everything to add good improvements to the original design. The screen, for example, while maintaining HD resolution, should jump to 5.5 inches - a format that is apparently quite desired by Asians - while the core of the system turns out to be a Snapdragon 435 processor. An internal storage of 32 GB and 3 GB of RAM should ensure your apps run without much trouble.
Huawei will offer Enjoy 7 Plus in three different colors

The device also has a 12MP rear camera and an 8 MP self-cam, it will also have a traditional digital sensor and a battery of no less than 4,000 mAh. According to Huawei, the gadget should come very soon to the Chinese market, already upgraded to Android 7.0 (Nougat) in three colors options and costing around 230 US dollars. Check out the complete characteristics of this smartphone
Technical specifications
• Display: 5.5-inch LCD
• Screen resolution: HD (1280x720 pixels)
• Operating system: Android 7.0 (Nougat)
• Processor: Qualcomm Snapdragon 435 Octa-core 1.4 GHz
• GPU: Adreno 505
• RAM: 3 GB
• Internal storage: 32 GB
• External storage: micro SD cards up to 256 GB
• Rear Camera: 12 MP
• Front camera: 8 MP
• Connectivity: 4G LTE 150/50M, Bluetooth 4.0, WiFi a/b/g/n, micro USB 2.0 port
• Unique features: fingerprint reader
• Battery: 4,000 mAh

Be Patience...
So, did you like the style and specifications of this new Huawei smartphone? Well, if the answer is yes, it will take patience or invest in an import. That is because, for now, there is no news that Enjoy 7 Plus will be marketed outside of China. By that, due to Huawei world growth, it will not take so long until this device is available in Europe and the rest of the world.

Having a new device is quite fun, for me, the best part is unboxed it. However, our devices has risks to be stolen or lost, so in order to avoid facing this problem, I recommend you to use the applock Private Zone, it can provide tracking lost or stolen phone function by sending text message (you need to bind your number to your friend or relative`s phone number), this will be a helping hand to prevent the loss of your device or the leakage of your information. You can also enjoy its other functions like hiding photos, private browser, break-in alert, customized lock screen cover and much more.

0 notes