Text
-ABOUT US-
Gabriela's Journal means 'messenger of God', it is a Czech variant of Gabrielle and originated in Hebrew language means 'God's bravest woman'. We came up with "Gabriela's Journal" as our blog name because we are inspired with the leftist Filipino organization that advocates for women's issues named "The General Assembly Binding Women for Reforms, Integrity, Equality, Leadership and Action or GABRIELA. Given that our group is consisting of all women and facing a lot of chaotic challenges but still facing problems with determination and help of each other. That is why our blog aims to advocate and empower all of the women through technologies by raising awareness.
The content of this blog is made available by humanities and social sciences students for educational purposes only as well as to do the task compiling the activity, assignment and performance task of the group in the subject Empowerment Technology . Any action you take upon the information of this blog is strictly at your own risk. There is no specific political party supported by the group. The views and opinions of the group doesn’t necessarily reflect or represent the view and opinion of the university.

this picture was created in canva(the crowned shield is not paid and it was screen captured)
1 note
·
View note
Text
-1st Assignment-

...WHAT IS A COMPUTER...
-A machine that can be instructed to carry out sequences of arithmetic or logical operations automatically via computer programming. Modern computers have the ability to follow generalized sets of operations, called programs. These programs enable computers to perform an extremely wide range of tasks. Computer is an electronic device for storing and processing data, typically in binary form, according to instructions given to it in a variable program.
->Sailah Carrasco
· Computer is derived from a Latin word “computare “ which means “to calculate”, “to count”, “to sum up” or “to think together”. So, more precisely the word computer means a device that performs computation
· A computer is a machine or device that performs processes, calculations and operations based on instructions provided by a software or hardware program. It has the ability to accept data (input), process it, and then produce outputs.
->Ma. Jessy Nicole Mangubat
- Electronic Device for storing and processing data. Typically, in binary form, according to instruction given to it in variable form.
- A programmable devices that stores, retrieves and process data
- A machine that can be vary out sequences of arithmetic or logical operation automatically via computer programming.
- Are used as control system as wide variety of industrial and consumers ideas.
->Emraida Olimpain
Computer is an electronic device that is designed to work with Information. The term computer is derived from the Latin term ‘computare’, this means to calculate or programmable machine. Computer can not do anything without a Program. It represents the decimal numbers through a string of binary digits. The Word ‘Computer’ usually refers to the Center Processor Unit plus Internal memory.
Charles Babbage is called the “Grand Father” of the computer. The First mechanical computer designed by Charles Babbage was called Analytical Engine. It uses read-only memory in the form of punch cards.
The computer is an electronic device that takes input from the user and processes these data under the control of a set of instructions (called program) and gives the result (output) and saves future use. It can process both numerical and non-numerical (arithmetic and logical) calculations.
->Almira Pagsuyuin
-An electronic device for storing and processing data, typically in binary form, according to instruction given to it in a variable program
-A machine that accepts data as input, processes that data using programs, and outputs the data as information. Many computers can store and retrieve information using hard drives.
-“Computer” comes from the word “computare” which means to calculate. A computer is an electronic device, which stores and processes data to give meaningful information.
->Leizl Joy Ricafort
-A computer is a programmable electronic device that accepts raw data as input and process it with as set of instructions to produce the result as output. It renders output just after performing mathematical and logical operations and cam save the output for future use. It can process numerical as well as non-numerical calculations. The term "computer" is derived from the Latin word "computare" which means to calculate.
->Kate Red
Computer is an electronic device for storing and processing data, typically in binary form, according to instructions given to it in a variable program. It is a machine that can be instructed to carry out sequences of arithmetic or logical operations automatically via computer programming. Modern computers have the ability to follow generalized sets of operations, called programs. These programs enable computers to perform an extremely wide range of tasks.
->Elaine Taniegra
A computer is an electronic device that manipulates information or data. It has the ability to store, retrieve, and process data. Computer can be used to create documents, send emails, play games. And browse the web.
Some people define it as common operating machine, purposely used for technological and educational research.
“A computer is a general device that is used to perform arithmetic and logical operation automatically. A computer consists of a central processing unit and some form of memory.”
->Jhovelle Villapando
0 notes
Text
-2nd Assignment-
...RELATION OF INTERNET & WWW...

Internet
is being used by most, if not all people in the world as one of the mainstream of communicating with one another. Communication with the use of internet made people an easy way of imparting information or ideas through the usage of world wide web. With these two connected and needed each other so that people are able to access any of the platforms used nowadays.
->Sailah Carrasco
The Internet is connected computer network on which the site operates. While, the world wide web (WWW) is in a device and online to search and open pages. So, my explanation in analyzing the picture above, is that the internet is like a machine for the world wide web to operate it so that we can access and browse different pages.
->Ma. Jessy Nicole Mangubat
The Internet is a global infrastructure that links the world's computer networks. The devices are linked via copper wires, wireless networks or optical fiber. There are many networks, including servers, routers, hubs, switches, repeaters and much more in this network. And with the help of the internet, we are able to communicate with our family relatives and socialize with the other people. While on the other hand the World Wide Web (or also known as WWW) is a web-based service. It refers to the comprehensive network link. With the help of these link the user can then easily access the details from one page to another.
->Emarida Olimpain
The Internet is an increasingly important part of everyday life for people around the world. Internet is a collection of connected computers through gateways by which the information that is stored in databases and on servers is transferred from one computer to another and the World Wide Web is the software that is used to retrieve the information requested by the users. The World Wide Web (which we call the Web because we’re lazy typists) lives “on top of” the Internet. The Internet’s network is at the core of the Web, and the Web is like an attractive parasite that requires the Net for survival (dummies.com, 2010). The Web page that are accessible on the web usually contain hypertext links and are sometimes called links. These links connect to other pages that are store on the same or even a different server; these servers can be in any location throughout the World. This system of interlinked documents is known as hypertext.
->Almira Pagsuyuin
Internet is essential especially nowadays that we are using this for educational purposes, to do research and gather different kinds of information, attend online class and to broaden/gain more knowledge about various things. This also used for our business as we can use this to promote and even advertise our own product on any social media platforms as some people are relying in feedbacks of other people. In addition, we can also use internet to effectively communicate with other people in an inexpensive way.
->Leizl Joy Ricafort
For me, this illustration means that there us a relationship between the internet and the world wide web (WWW), and it is that the internet is a collections of connected computers through gateways by which information that is stored in databases and on servers is transferred from one computer to another and the world wide web (WWW) is the software that is used to retrieve the information requested by the users.
->Kate Red
Internet open connection in the user to connect in world wide web which contains data and information to facilitate the communication networks of computers. World wide web also contains network that needs internet access for us to brows different webpages, addition to that it was developed for automated information sharing like what I am doing right now. By analyzing in the picture above, internet is the heart of the world wide web for it to be function well and connect the user between the computers.
->Elaine Taniegra
The internet become in demand nowadays specially in the distance learning. The internet allows us, the students, to access the websites and application software like MS Teams to accomplish our online classes. It is also important because internet is needed to search information and data in the any websites. It allows us to communicate to other people from any part of the world.
->Jhovelle Villapando

0 notes
Text
-3rd Assignment-

....Rules of Netiquette...
How many hours do you spend on the internet per day?
I almost spend my whole day using internet
Can you live without internet for a week?
Yes, I can live without internet for a week as long as I'm with my family.
How many times do you complained about your Internet connection speed?
I am always complaining regarding our internet connection
-Sailah Carrasco

How many hours do you spend on the internet per day?
I spend 15 hours using the internet, especially when I have an online class and task that needed to do and submit.
Can you live without internet for a week?
As a part of digital native, it is difficult to leave without the internet. Our necessary things in life are mostly needed to use with the internet. Best example is our online class.
What positive or negative impact does internet have on your life?
Nowadays, Internet is also a part of my routine in everyday life. This is the way to still have a communication with my friends and relatives that are far from me. It also helps me to easily finish my school works, and at the same to widen my idea by learning new things through searching with the use of internet. I am just worried of getting into the point where I am already addicted to the internet, of course it will really affect my physical and mental health.
How many times do you complained about your Internet connection speed?
Based on the experience of my family and I when it comes on our internet which is ‘planet,’ It is not that bad compare to the other internet connection here in the Philippines. Planet connection meets my expectation. Having problem on our internet is exceedingly rare. But once our internet is having a trouble, it takes a lot of time to fix it.
-Ma. Jesy Nicole Mangubat

How many hours do you spend on the internet per day?
I think I spend my time with the internet at least 17 hrs. or 20 hrs. it depends to the task that were given to us and especially now that we are having online class there’s a lot of things to do.
Can you live without internet for a week?
Honestly speaking don’t think that I can leave without the internet because I’ve always relay on the internet for the news, and for the entertainment purposes.
What positive or negative impact does internet have on your life?
The Internet has a positive and negative side the positive side you were able to communicate with your family overseas, you were able to entertain yourself with the help of social media platforms like Facebook, Tiktok, Instagram, and etc. While on the other hand it has a negative side because, you might get addicted on the online games like DOTA, call of duty, Rules of survival and Mobile Legend, there’s a possibility that you can experience being cyberbullied
How many times do you complained about your Internet connection speed?
I always complain about the internet speed especially now that we are having class online and there’s a time that I got disconnected due to internet connection and when I play online game like mobile legend, I always experience the red connection.
-Emaraida Olimpain
How many hours do you spend on the internet per day?
- I think I spend more than half of a day on the internet, probably 12-16 hours since it is required for us to have it in online class. We have our classes in virtual meetings and we also do school works using internet. Not only with school purposes, it is also used for communication and entertainment.
Can you live without internet for a week?
- To be honest, I really can’t live without internet. I always use my phone for communication. I am a student and I need it for my studies. And watching my favorite series and movie and also playing mobile games is what kills my boredom. Internet makes my life easier.
What positive or negative impact does the internet have on your life?
- The positive impacts of the internet in me is for it provides effective communication using messenger or any online communication apps and services to any part of the world. Online shopping have made my life less complicated using Shopee or Lazada. I can access the latest news from any part of the world without depending on the TV or newspaper. Education has received a huge boost as uncountable books and journals are available online from libraries across the world. This has made research easier. We, students can now opt for online courses using the internet. Just also like what I have mentioned I also use it for entertainment purposesm The negative impacts of this is it ruins my health and body clock as I spent more than half of the day using internet. It leads me in addiction to social networks that can disrupt my life, both personally and professionally. It also spreads my personal information as strangers stalks my profile.
How many times have you complained about your nternet connection speed?
- I often complain about the internet connection speed we have. It always distracts my online class and leads to disconnection. Also when I play mobile games it lags every time I am in a game.
-Almira Pagsuyuin

How many hours do you spend on the internet per day?
I spend at least 16-18 hrs. on the internet as I’m using it for online class, research, news updates, and for entertainment purposes. I also use this to communicate with my parents as I’m currently staying here in our province.
Can you live without internet for a week?
No, because internet and gadgets are part of my everyday life, especially now that we’re not allowed to do outdoor activities.
What positive or negative impact does internet have on your life?
Internet provides information for us to entertain. On the other hand, excessive use of gadgets and internet could be the reason for having physical and mental damage and addiction to online games.
How many times do you complained about your Internet connection speed?
I always complain when it comes to internet speed as we’re always having internet problems here in our province.
-Leizl Joy Ricafort

How many hours do you spend on the internet per day?
It depends whether I have online classes or not, because as much as possible I am trying to lessen the hours, I spend on Internet so that I can be more productive throughout the day. When I have my online classes and school works to do in that day, I usually spend around 15 hours a day, but when I don’t have online classes and school works to do in that day, I usually spend 10 hours on the internet.
Can you live without internet for a week?
I guess I can’t, especially now that we are performing online classes and Internet has already been part of my life ever since I was born. Also, I can’t communicate with my loved ones, especially with my parents because we are apart from each other. Lastly, Internet is my only source of entertainment in this ongoing pandemic, because we all know that going out is very limited.
What positive or negative impact does internet have on your life?
Internet helped me to have an effective communication with my parents abroad, I can message or call them in an instant. Internet also served as an entertainment for me because I can watch any movies or series that I like, I can also download pictures, songs and videos. But Internet also have its negative impact in my life, it makes me so lazy and dull because I tend to binge watch on my favorite series, I am becoming less productive throughout the day. Also, I sometimes experience having stress and anxiety because of the things I see on the internet, such as fake news, cyber-bullying and harmful behaviors of other netizens.
How many times do you complained about your Internet connection speed?
Well, I must say that the performance of our internet connection provided by Converge is really excellent and a top-quality compared with the other Internet connection we had in the past few years here in the Philippines. So, I believe that me and my family haven’t complained about our internet connection speed.
-Kate Red

How many hours do you spend on the internet per day?
I usually spend 15 hours or more because of the online classes
Can you live without internet for a week?
I can but it will be hard for me because I always use my phone.
What positive or negative impact does internet have on your life?
In positive manner, internet was the one I am using to attend my online classes but the negative one is having too much exposure on screen that may cause to harm our health in terms of excessive use of it.
How many times do you complained about your Internet connection speed?
I am rarely complaining to it because we are paying for a higher mbps of wifi connection due to our online classes
-Elaine Taniegra

How many hours do you spend on the internet per day?
Since the school year started, I almost spend my whole day from 7 o’ clock in the morning until midnight finishing school works.
Can you live without internet for a week?
No, because I will be absent if that happens. Also, even just for a minute I am afraid to slow connection I might miss important announcement.
What positive or negative impact does internet have on your life?
The positive impact is I can call my parents anytime, since I am far from them while the negative impact is it can be very distracting whenever I have important things to do. I tend to be tempted to watch Korean drama.
How many times do you complained about your Internet connection speed?
I am grateful to say that I only complain 3 times because there are only 4 gadgets sharing the connection and I am the only one using this during class hours.
-Jhovelle Villapando
0 notes
Text
-4th Assignment-

....THINK BEFORE YOU CLICK...
T – think before you post on social media.
H – hide your personal information to prevent a scam and a situation that can harm you.
I – it is important that your software is always updated
N – never forget to log out your account whenever you’re going to use other computer/ any other devices.
K – keep your personal information private or secret even your families should not know your passwords.
-Sailah Carrasco
T - Teach yourself to double check the information you want to share on social media because it can affect to the netizen.
H - Hit the notification button of your account to check and have an update on what is happening on your personal account.
I - Improve your passwords on your social media account or even on your personal devices if you think they can easily know it.
N - Never give all your personal information in the internet specially if it is not necessary.
K - Know your main point of what you are planning to post on social media to avoid the reaction of other netizen on your post that could lead to misunderstanding.
BEFORE YOU
C - Clean the content of your devices using different application (take note: make sure that the application is safe to use) to detect whether it has a virus, and also to remove files that can harm to your devices.
L - Learn to notice and read information when using different application and sites in the internet to give awareness about the application you want to use and for the sites that you want to browse.
I - If you want to keep your personal identity, be careful on giving personal information over the internet.
C - Check your profile by searching it on google to know if the netizen can easily find you over the internet. It may also help you to check if there are some false information about yourself.
K - Know your list of friends in your social media accounts. It is free to unfriend and unfollow the person if you think that it can be harmful to you. Because your own feed is in your hands.
-Ma. Jesy Nicole Mangubat

T–Teach the children to be responsible in using the Social Media
H –Hide your personal information in different social media site to be able for you to keep safe
I –Inform your love ones to avoid sharing their personal information to the people they just met.
N –Never log in to the suspicious site
K–Keep your information hidden from the people you do not know.
-Ma. Jesy Nicole Mangubat
T- hink of your social media as your outfit: there are some things you wouldn’t wear in public because people would laugh or think it wasn’t a good choice.
H- ow would you feel if someone stole your work and said it was theirs? That’s why it is really important to always give credits to the original worker/sources when you use their works in posting in the internet.
I- t is advised to keep personal information, such as phone number and email address, private, familiarize yourself with privacy settings and make proper use of them.
N- ot only you are posting for yourself to see, but to all the netizens.
K- now how to say to say ‘no’ when asked to carry out something on the internet and not to feel bad or intimidated to stop a chat thread or refuse a friend request from someone unknown.
BEFORE YOU
C- heck if what you’re about to post is really necessary and true.
L- earn who are you audience.You need to be careful who the person that you accept on social media. Don't accept the person if you don't know their personally. Better they message you first before you accept.
I- f you don’t have something nice to say, just don’t say anything at all. Portray yourself, your friends and your community in a positive light.
C-onsider the source. Click away from the story to investigate the site, its mission and contact info.
K- now your limitations. It's okay to express your emotion in social media because it's a part of freedom expression but always remember that we have limitations. Because here in this world there's a lot of criticism people that can judge you easily.
-Kate Red

T- Think first before you click something on the social media
H- Hide your personal information on the internet that may cause you harm
I- It is important to make sure that your security software is always update
N- Never Forget to Logout your account in the computer of other people to prevent hacking incidents
K- Keep your Personal information a top secret.
-Elaine Taniegra
T -think if your relatives will be happy if you post it
H -help to prevent and share awareness about cybercrimes
I -inspirational content must be your priority, share good vibes
N -never participate in online fights
K -keep your devices protected from viruses and malware
BEFORE YOU
C -care for other people. if you saw a scandalous video, report the post and don’t share it
L -look for reliable sources when reading information before you post disseminate it.
I -ignore hateful comments
C -carefully remember to use strong password in devices and do not share it
K -know your limitation, posts must be like what you eat. It must be healthy and clean.
-Jhovelle Villapando
0 notes
Text
-1st Activity-
....DIFFERENT WAYS HOW PEOPLE USE COMPUTERS....
IN SCHOOL
For gathering information
It will be easier to access or to search the information you need using computer rather than going to the library and search it page by page.
For doing activities and taking down notes
It will be easier to do activities and taking down notes using computer than writing on your own.
-Sailah Carrasco
Online Resources
The use of a computer in education makes it now easier and faster to access anything you need to learn and search.
Presentation
Microsoft word and PowerPoint are some examples where you can input text and picture from the computer for presenting and reporting in school.
File Keeper
Computer can keep and store the files of the student and teacher that will needed for their presentation.
-Ma. Jesy Nicole Mangubat
Research Purposes
Easy to access some information
Can create PowerPoint Presentation
-Emarida Olimpain
Huge & organized store of information
Faster means of Computing grades
Self-Learning
Researches
You can use a computer for creation of digital resources
Computer Literacy Education
-Almira Pagsuyuin
As teaching machines
As internet portals
As data processors
To increase efficiency
Helping find information
Helping organize information
As test givers
Visualization tools
-Kate Red
To do research
For online classes
To do activities
-Leizl Joy Ricafort
For searching data
It will be more convenient for the students to search it on the computer instead of using books in the library.
Storing important files
Storing important files in the computer will be a really great help for the student’s projects and examinations
-Elaine Taniegra
Online Class/Conference
Creating Documents
Research
-Jhovelle Villapando
....DIFFERENT WAYS HOW PEOPLE USE COMPUTERS....
At Work
For using E-mail
We use computers at home to compose and send e-mails much more quickly regarding about work rather than send e-mails by messenger.
For Spreadsheets or databases
Documents can be done quickly by using computers to make spreadsheets being done usually by accountants.
-Sailah Carrasco
Connectivity
Computer can be used for the transaction of orders of the costumers and setting a business meeting for the client to improve communication both within the workplace.
Data Storage
Resume, application form, and other files that is required in work can handle these computers easily. It can restore each document of employee by organizing it in the folder that holds by the computer.
-Ma. Jesy Nicole Mangubat
Communication
Research Purposes
PowerPoint presentation
Programing
-Emarida Olimpain
Information Storage
Computation
Scheduling
Communication Research
Graphic design and editing
Programming and Publishing
-Almira Pagsuyuin
Research
To save necessary files
Presentation
-Leizl Ricafort
Word processing
Desktop Publishing
Programming
Graphics or Design
Communication
Research
Applications
Scheduling
-Kate Red
For Business meeting
Computers contains software application that can be used in a PowerPoint presentation
Gathering data
Using computer, it will be easier to gather and store data that will be needed in work
-Elaine Taniegra
Encoding of sales or Grades
Research
Creating documents and layout
-Jhovelle Villapando
....DIFFERENT WAYS HOW PEOPLE USE COMPUTERS....
At Home
For Entertainment
We use computers at home to watch movies with our family, playing online games, and for online shopping.
Searching for Jobs
It will be easier to search jobs at home using computer rather than applying jobs by walk-in.
-Sailah Carrasco
Entertainment
When you are in the mode of boredom strikes, the apps that can be hold by the computer can save it. Watching videos, playing online games, and listening to the music can be your stress reliever from works and schools.
In case of emergency
Unfinished works from school and office can be done through our personal computers at home.
-Ma. Jesy Nicole Mangubat
Do some Homework
Can relax
Family Bonding
Entertainment Purposes
Can do some videocall with our family
Edit some videos for Vlogs
-Emarida Olimpain
Home Budget
Computer Games
Entertainment
Communication
Information
Online banking
Online shopping
Home businesses
-Almira Pagsuyuin
Entertainment
Online games
-Leizl Ricafort
Play Games
Entertainment
Internet Surfing
Operate Security Camers
Work
Doing homework
Study
Chatting
-Kate Red
· Entertainment purposes
Using computer can also be an entertainment for the whole family because you can do so much things about it.
-Elaine Taniegra
Entertainment
Long distance communication
Accomplish task from school/work
-Jhovelle Villapando

0 notes
Text
-2nd Activity-
....INTERNET THREATS....
*MALWARE
Malware is malicious software such as spyware, ransomware, viruses and worms. Malware is activated when a user clicks on a malicious link or attachment, which leads to installing dangerous software. Cisco reports that malware, once activated, can:
Block access to key network components (ransomware)
Install additional harmful software
Covertly obtain information by transmitting data from the hard drive (spyware)
Disrupt individual parts, making the system inoperable
*PHISHING
Phishing attacks use fake communication, such as an email, to trick the receiver into opening it and carrying out the instructions inside, such as providing a credit card number. “The goal is to steal sensitive data like credit card and login information or to install malware on the victim’s machine,” Cisco reports.
*SPYWARE
Another form of malware is spyware. Spyware is an all-encompassing internet nasty and is usually attached to pop-ups of downloadable files. Once installed on your computer, spyware can monitor your keystrokes, read and delete your files, reformat your hard drive, and access your applications. Whoever is controlling the spyware has access to your personal details without you even knowing.
*TROJAN
Trojans leave your computer completely unprotected, which can mean that hackers can steal any data from your system. Trojans often present themselves as harmless computer programs so that hackers can penetrate your computer without being detected.
*WORMS
Worms usually make their way on to a computer via a malicious email attachment or USB stick. Once your computer has been infected by a worm, it will likely send itself to every email address logged in your system. To the receiver, your email will appear harmless, until they open it and are infected by the same worm.
-Sailah Carrasco
*SPAM
The reality that most of our emails accounts come with a ‘Spam’ or ‘Junk’ organizer insinuates that spam emails are a gigantic issue, with more than 50% of emails being siphoned into these organizers. Aside from being an irritation, spam emails are not a coordinate danger. Be that as it may, numerous can contain malware.
*VIRUS
One of the most talked about internet threats is a virus. Viruses usually attach themselves covertly to downloads as they are designed to spread at an alarming rate. Viruses are often attached to files for download, shared via CDs, DVDs, and USB sticks, or loaded on to computers by opening infected email attachments.
*SPYWARE
Spyware is an all-encompassing web dreadful and is more often than not connected to pop-ups of downloadable records. Once introduced on your computer, spyware can screen your keystrokes, examined and erase your records, reformat your difficult drive, and get to your applications. Whoever is controlling the spyware has get to to your individual points of interest without you indeed knowing.
*TROJAN
Trojans take off your computer totally unprotected, which can cruel that programmers can take any information from your framework. Trojans frequently show themselves as safe computer programs so that programmers can enter your computer without being recognized.
*PHISHING
Phishing could be a frame of false movement. More frequently than not, official-looking emails are sent mimicking a well-known supplier, such as a bank. These emails are sent to obtain people’s passwords and credit card subtle elements
-Ma. Jesy Mangubat
*SPAM
The reality that most of our email accounts come with a ‘Spam’ or ‘Junk’ organizer insinuates that spam emails are a gigantic issue, with more than 50% of emails being siphoned into these organizers. Aside from being an irritation, spam emails are not a coordinate danger. Be that as it may, numerous can contain malware.
*VIRUS
One of the most talked about internet threats is a virus. Viruses usually attach themselves covertly to downloads as they are designed to spread at an alarming rate. Viruses are often attached to files for download, shared via CDs, DVDs, and USB sticks, or loaded on to computers by opening infected email attachments.
*SPYWARE
Spyware is an all-encompassing web dreadful and is more often than not connected to pop-ups of downloadable records. Once introduced on your computer, spyware can screen your keystrokes, examined and erase your records, reformat your difficult drive, and get to your applications. Whoever is controlling the spyware has get to to your individual points of interest without you indeed knowing.
*TROJAN
Trojans take off your computer totally unprotected, which can cruel that programmers can take any information from your framework. Trojans frequently show themselves as safe computer programs so that programmers can enter your computer without being recognized.
*PHISHING
Phishing could be a frame of false movement. More frequently than not, official-looking emails are sent mimicking a well-known supplier, such as a bank. These emails are sent to obtain people’s passwords and credit card subtle elements
-Emraida Olimpain
*MALWARE
Malware is malicious software such as spyware, ransomware, viruses and worms. Malware is activated when a user clicks on a malicious link or attachment, which leads to installing dangerous software.
*EMOTET
The Cybersecurity and Infrastructure Security Agency (CISA) describes Emotet as “an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the most costly and destructive malware.”
*DENIAL OF SERVICE
A denial of service (DoS) is a type of cyber attack that floods a computer or network so it can’t respond to requests. A distributed DoS (DDoS) does the same thing, but the attack originates from a computer network. Cyber attackers often use a flood attack to disrupt the “handshake” process and carry out a DoS. Several other techniques may be used, and some cyber attackers use the time that a network is disabled to launch other attacks. A botnet is a type of DDoS in which millions of systems can be infected with malware and controlled by a hacker, according to Jeff Melnick of Netwrix, an information technology security software company. Botnets, sometimes called zombie systems, target and overwhelm a target’s processing capabilities. Botnets are in different geographic locations and hard to trace.
*MAN IN THE MIDDLE
A man-in-the-middle (MITM) attack occurs when hackers insert themselves into a two-party transaction. After interrupting the traffic, they can filter and steal data, according to Cisco. MITM attacks often occur when a visitor uses an unsecured public Wi-Fi network. Attackers insert themselves between the visitor and the network, and then use malware to install software and use data maliciously.
*PHISHING
Phishing attacks use fake communication, such as an email, to trick the receiver into opening it and carrying out the instructions inside, such as providing a credit card number. “The goal is to steal sensitive data like credit card and login information or to install malware on the victim’s machine,” Cisco reports.
-Almira Pagsuyuin
*MAN IN THE MIDDLE
It occurs when hackers insert themselves into two-party transaction.
*PASSWORD ATTACKS
With the right password, a cyber attacker has access tp a wealth of information.
*MALWARE
Is a malicious software which leads to installing dangerous software
*EMOTET
Is a malicious software which leads to installing dangerous software.
*DENIAL OF SERVICE
Is a type of cyber attack that floods computer or networks so it can't respond to requests.
-Kate Red
*MALWARE
“Malware” is short for “malicious software” computer programs designed to infiltrate and damage computers without the users consent. “Malware” is the general term covering all the different types of threats to your computer safety such as viruses, spyware, worms, trojans, rootkits and so on.
*SPAM
Spam is the electronic equivalent of the 'junk mail' that arrives on your doormat or in your postbox. However, spam is more than just annoying. It can be dangerous – especially if it's part of a phishing scam. Run phishing scams – in order to obtain passwords, credit card numbers, bank account details and more.
*PHISHING
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
*SCAMMING
IT is the use of Internet services or software with Internet access to defraud victims or to otherwise take advantage of them. The scam is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
*HACKING
Hacking refers to activities that seek to compromise digital devices, such as computers, smartphones, tablets, and even entire networks. Hackers are motivated by personal gain, to make a statement, or just because they can. DOWNLOAD MALWAREBYTES FOR FREEFREE DOWNLOAD.
-Elaine Taniegra
*PHISHING
Is a fraudulent attempt to acquire personal data or information, such as usernames, passwords, credit card numbers, or other sensitive information, by impersonating a trustworthy entity in a digital communication.
*SPYWARE
Spyware is the term given to a category of software which aims to steal personal or organizational information. It is done by performing a set of operations without appropriate user permissions, sometimes even covertly. General actions a spyware performs include advertising, collection of personal information and changing user configuration settings of the computer.
*COMPUTER VIRUSES
In more technical terms, a computer virus is a type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another. A virus operates by inserting or attaching itself to a legitimate program or document that supports macros in order to execute its code. In the process, a virus has the potential to cause unexpected or damaging effects, such as harming the system software by corrupting or destroying data.
*MALWARE
Is the collective name for a number of malicious software variants, including viruses, ransomware and spyware. Shorthand for malicious software, malware typically consists of code developed by cyberattackers, designed to cause extensive damage to data and systems or to gain unauthorized access to a network.
*ADWARE
Adware uses the browser to collect your web browsing history in order to ’target’ advertisements that seem tailored to your interests. At their most innocuous, adware infections are just annoying. For example, adware barrages you with pop-up ads that can make your Internet experience markedly slower and more labor intensive.
-Jhovelle Villapando

credits to freefik.com (image found in pinterest)
0 notes
Text
-3rd Activity-
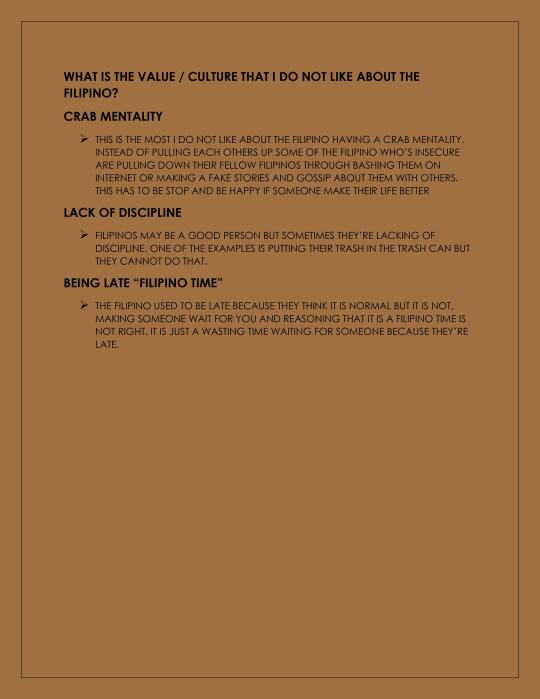
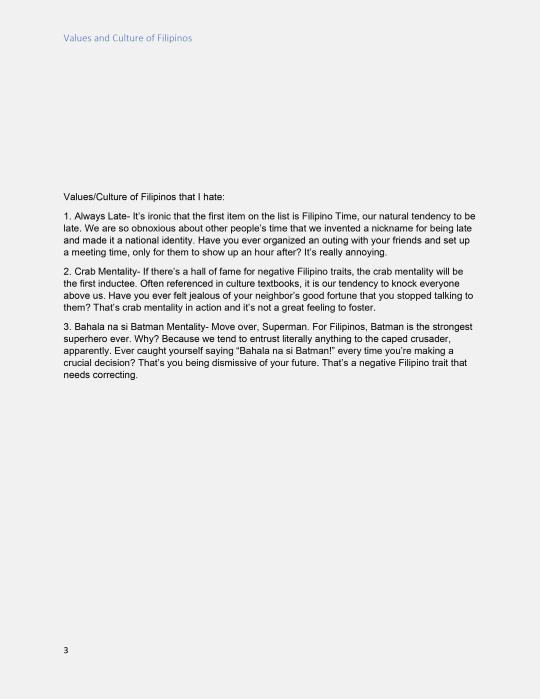
WHAT IS THE VALUE/CULTURE OF A FILIPINO THAT YOU LIKE AND HATE THE MOST?
0 notes