Text
Check out my Prisma Cloud Python3 scripts (leverages API) to automate tasks and more!
I’ve been helping lead the effort for security tooling at my organization related to the shift left security strategy. We are using Palo Alto’s security cloud posture management tool called Prisma Cloud. The areas covered are infrastructure as code (IaC), container security (ties into Kubernetes cluster), network visibility, VPC visibility and more. The UI unfortunately has a lot of gaps in terms of the features compared against it’s API. To help speed things up for the on-boarding and deployment, I’ve developed over 30 python scripts during the fall and winter of 2021 which enhances the product, automating many manual tasks (backups, CRON jobs related to users and roles, bulk imports, granularity on alerts, custom compliance report with all asset names).
Check out my forked repo below which is fully documented and I’ve several comments within the code for folks that are just getting into python (requested by some of my teammates). I’m not an expert either but it works. Link here: https://github.com/antoinesylvia/pc-toolbox
0 notes
Text
Breaking into Cybersecurity 101 - Career Change or Fresh Out of School
By Antoine Sylvia | CISSP-ISSAP | CISSP | CCSP | CCSK
“Why do entry level cybersecurity jobs require 2-5 years of experience? How can I get my foot in the door? Will getting a specific certification get me paid like it said on the Forbes website?”
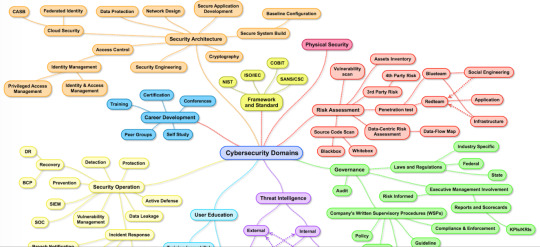
Image Credit to Henry Jiang for the high-level view of cybersecurity domains.
Purpose: This is designed to be an end to end blueprint document, the content included is to better assist those that want to enter the cybersecurity industry (from any background). The material presented was crafted around the numerous requests I have received relating to questions to what it takes to get a foot in the door in cybersecurity. The road will not be easy, but it will be well worth it. Consider this a living document that is subject to change based on feedback.
I started out as an IT Architect at IBM in 2011, pivoted into cybersecurity in 2015, fortunately I was exposed to aspects of cybersecurity in my first role. Within security, I have worked as a Security Consultant (IBM), Security Analyst (Sabre), Security Architect (Sabre) and now as a Security Engineer (Sabre). I have had a lot of help along the way and want to continue to pay it forward.
Many people have inquired with me over the years about the best way to get hired into a cybersecurity role, whether it is from someone in a non-cyber role or a student coming upon their graduation year for a technical program. I figured it would be more effective to put together a quick starter guide, which could assist others in getting their foot in the door. This blog post will be broken up into the following sections:
Interest
News, Blogs, TV and Podcasts
Mentor(s)
Networking
Education Resources
Certifications
Experience
Job Posts
Social Media
Salary/Worth
Other Tips
Interest
Figure out which area intrigues you most within the cybersecurity realm, which is a vast space as shown in the picture above. Your goal should be to become a well-rounded, fundamentally sound cybersecurity professional, however you should zero in on a few specialties (continue to be flexible). Remember there is nothing wrong with taking an IT role that is not part of the cybersecurity team but still performs cybersecurity related duties which will result in transferable skills. Building up fundamental IT knowledge before joining security is essential.
Note 1: When you move into security, there should be a general understanding of the basics of IT and data protection strategies (at rest and in-motion via encryption, plus access controls), networking, application security concepts, web services extending out to the 3-tier architecture (presentation, business and data) as shown in the image below.
Learning about how web services function from an architecture standpoint, would be the ideal place to start. Much of the focus these days is on the protection of corporate web services which are available either internally and/or externally (internet). The use of a “defense in depth” strategy helps better protect corporate assets such as mission critical data (which is most likely to exist in a production environment). As shown in the image below “data” is at the core of the strategy.
Defense in Depth (image from sentrillion.com)

3 Tier Architecture, 4-minute video that will provide additional context on a 3-tier architecture:https://www.youtube.com/watch?v=jJYv-nfkMXk

The best method to learn about securing web services with the defense in depth strategy is to do hands-on labbing.
Note 2: If you do not want to go the web services route, there are other sources out there dedicated to low level hacking (kernel, drivers, firmware etc.) and hardware hacking (tasks which can be done at home or at your local Makerspace).
Note 3: Understanding data protection and data privacy is critical to your success in this space, data is at the core of a defense in depth strategy. Here is a link to a quick article which discusses the two: https://www.forbes.com/sites/forbestechcouncil/2018/12/19/data-privacy-vs-data-protection-understanding-the-distinction-in-defending-your-data/#4434fe5050c9
News, Blogs, TV and Podcasts
Things in cybersecurity change quickly, it is essential to keep up with the latest threats and techniques. Here are some websites to check out:
https://krebsonsecurity.com/ Cybersecurity blogger, breaks a lot of news.
https://www.schneier.com/ - Cryptographer, security professional.
https://www.reddit.com/r/netsec/ - Information security subreddit.
https://www.reddit.com/r/privacy/ - Data privacy subreddit.
https://www.reddit.com/r/technology/ - Technology subreddit.
https://darknetdiaries.com - Podcast.
https://dailyrotation.com - Best RSS feeds tech website, plug in your own favorite cybersecurity website feeds, then read then all like a newspaper.
https://www.usanetwork.com/mrrobot - Mr. Robot (TV show). Show uses technical consultants for accuracy, they sometimes blog about specific episodes: https://medium.com/@ryankazanciyan
Mentor(s)
Link up with someone already in the space that could help with:
Pointing you to key resources.
Keeping you posted on industry trends.
Providing challenges that can assist in elevating your game.
Potentially link you up with a connection that could possibly lead to a job.
Note 1: If you are already working for a company which has a security team, I recommend reaching out to a member. See if you can find time to meet with them and pick their brain. The more solid mentors the better.
Networking (Post COVID-19)
Get out and meet folks working in the industry. Connecting with people on social media (i.e., LinkedIn/Twitter) seems to be more of the norm these days, compared against handing out your business card (which you should still have). Meeting people face to face still holds a ton of value:
B Sides DFW: http://www.bsidesdfw.com/ – Find your local B Sides and attend the yearly event, this one is for the Dallas area.
DEF Con / Black Hat – Events take place in Las Vegas every August.
ISC2 Local Chapter – Link up with local cybersecurity leaders, plus this group will have great insight into best practices for prepping for the CISSP and CCSP.
ISSA Local Chapter – Link up with local cybersecurity leaders.
Meetup Groups – Local cybersecurity groups that meet monthly (Dallas area examples):
Women in Security Dallas: https://www.meetup.com/WIST-Dallas-Women-in-Security-and-Tech
Dallas Hackers Association: https://www.meetup.com/Dallas-Hackers-Association/ - The last 10 minutes is reserved for employers looking for talent, plus those looking for work have an opportunity to speak on the microphone.
Dallas Cybersecurity: https://www.meetup.com/DallasSecurity/
DFW Cloud Security: https://www.meetup.com/DFW-Cloud-Security/
OWASP Dallas: https://www.meetup.com/Dallas-The-Open-Web-Application-Security-Project-Meetup/
InfoSEC Career.org: https://www.meetup.com/infosecnetwork/ - Great group for career assistance.
The Pwn School Project: https://www.meetup.com/infosecnetwork/
DFW Black IT/Cyber Security Professionals: https://www.meetup.com/DFW-Black-IT-Cyber-Security-Professionals/
Education Resources
Websites that will help elevate your existing skill-set:
Pluralsight: https://www.pluralsight.com/ - $$$ - Mostly Cloud, this company owns the assets for Acloudguru and LinuxAcademy which used to be standalone organizations.
Coursera: https://www.coursera.org/ - $$ - Classes for cloud, Google Cloud (GCP) sponsors the classes specific to GCP.
TCM Sec Academy: https://academy.tcm-sec.com/ - $ - Great ethical hacking courses.
TryHackMe: https://tryhackme.com/ - $$ - Good hands-on labs for hacking and learning.
LeetCode: https://leetcode.com/ - $$ – Most FAANGs and top organizations require coding challenges for engineer roles, this website is a great prep tool over the course of several months. Most refer to this as, 'LeetCode grind'.
Cybrary: https://www.cybrary.it/ - $$ – Best CISSP course is on here, search for Kelly Henderson.
Udemy: https://www.udemy.com/ - Decent programming courses.
LinkedIn Learning (formally Lynda): https://www.linkedin.com/learning/ - $$$, multiple subjects.
Udacity: https://www.udacity.com/ - Offers several courses and nanodegrees.
YouTube: https://www.youtube.com/ - There is a ton of great content on YouTube for learning, whether It is advanced or entry level such as network theory 101: https://www.youtube.com/watch?v=rIZ61PyDkH8&list=PLR0bgGon_WTKY2irHaG_lNRZTrA7gAaCj&index=1
Hack the Box: https://www.hackthebox.eu/ - Pen testing labs, great resource to learn ethical hacking!
AWS Misconfigurations Challenge: http://flaws2.cloud/ - Be an attacker or defender.
Hacktale: https://www.hacktale.com/ - Blue team training game.
Vulnhub: https://www.vulnhub.com/ - Vulnerable VMs to test and break.
Null Byte: https://null-byte.wonderhowto.com/ - Posts about ethical hacking with video.
Quizlet: https://quizlet.com - Create flash cards for your certification exams or general studies, service has a ton of features for creating tests from flash cards. Users can leverage existing vocabulary sets created by others.
StackExchange: https://stackexchange.com - Q & A website.
Github: https://github.com/ - There are many great tools available on this platform that are great to use in your labs:
https://github.com/Kickball/awesome-selfhosted - Master list of self-hosted tools.
https://github.com/kahun/awesome-sysadmin - Master list of system admin tools.
https://github.com/Hack-with-Github/Awesome-Hacking - Master list of hacking tools.
https://github.com/sindresorhus/awesome - Master list of all the top masters list per subject on GitHub.
https://github.com/OWASP/CheatSheetSeries/blob/master/Index.md - The Open Web Application Security Project (OWASP) offers cheat sheets for secure coding best practices.
Reddit: Great internet resource, they have communities dedicated to every subject you can think of. However, staying within the scope of this post I would recommend you check out and subscribe to the following:
Homelab: Community dedicated to building out home labs https://www.reddit.com/r/homelab/
Use tools from awesome self-hosted listed above on Github.
NetSec: Community dedicated to information security - https://www.reddit.com/r/netsec/
Use tools from awesome hacking listed above on Github.
Sysadmin: Community dedicated to system administration - https://www.reddit.com/r/sysadmin/
Use tools from awesome sysadmin listed above on Github.
Networking: Community dedicated to networking (IT) - https://www.reddit.com/r/networking/
Privacy: Community dedicated to data privacy –
https://www.reddit.com/r/privacy/
Note 1: Going back to school is always an option as well, be sure to do a cost-benefit analysis first. If going for a degree, give yourself enough time to search for potential scholarships. For your scholarship hunt, sign up for a free account at Cappex (https://www.cappex.com/) directory search and use scholarship search guidance on the dedicated subreddit (https://www.reddit.com/r/scholarships/). CyberCorps (https://www.sfs.opm.gov) is a scholarship backed by the federal government, once a degree is attained the student must work for the government in a cybersecurity role (the years required is based on the number of years the student was covered by the scholarship). Please check out the “fellowship” section below since these kinds of opportunities will provide tuition and stipends in many cases. Ensure all written essays are reviewed by at least two people, consider using a free service like Scholarship Junkies (https://www.scholarshipjunkies.org/) for this task.
Note 2: Degrees are not always required but many still ask for it on the first level of screening. Out here in Dallas, one of the best programs in the area from a value standpoint is at Richland Community College which offers a cybersecurity associate’s degree with various tracks and many of the classes are taught by legend Phillip Wylie (featured in books and articles for penetration testing and more). The school struck a partnership with New England College (NEC), allowing students to easily enroll in NEC’s Bachelors in Cybersecurity program upon completion of the associate’s degree. With that said, ensure any school you pick is accredited with transferable credits (if needed).
Note 3: At the master’s level, a good value for the money program is at Rochester Institute of Technology (RIT), they offer the only micro-master’s program for cybersecurity which is affordable, 5 courses in 1 year for $1000. Once completed, you can submit your course history to formally apply for RIT’s Master’s in Computing Security. 9 credits will be earned through the master-master program, leaving only 21 credits to fill of 30 from the master’s program. Applicants will still need to hold a bachelor’s degree with at least a 3.0 GPA, if under a 3.0, they recommend sitting for the Graduate Record Examinations (GRE). More information can be found here: https://www.rit.edu/ritonline/cs-mm
Certifications
Great for demonstrating you have at least a baseline level of knowledge that employers are searching for, plus certs “can” play an essential role in securing interviews for many corporations. Please note, not all corporations are the same in terms of requirements, places like Google (does not extend to Google Cloud) and Facebook will not list certs on job postings. These two companies specifically attract top of the line talent, they may not only focus on your in-depth technical knowledge about a subject and coding ability (engineering/analyst positions), but there could be additional focus on your contributions to the community (software, talks, blogs, white papers etc.), overall influence.
Note 1: There are many accredited schools which offer certification programs, they can be hit or miss in terms of content and/or the instructor presenting the information. Job posts will rarely (if at all) call out certifications offered by schools. However, if the course works out well, these can be good knowledge builders.
Note 2: HR systems are highly automated these days, they filter out candidates by keywords found in resumes/profiles (which would include certification status). Below you will find the best cybersecurity certs to get right now (extending out to cloud) and most will require you to study for a considerable amount of time, they are not cheap to take and/or maintain:
Certs for Entry-Level:
Comptia Security+ – Most popular cert for entry level positions, covers a lot of the domains.
AWS Cloud Practitioner – Introduction to AWS services.
AWS Solution Architect (Associate) – This exam must be re-taken every 3 years, unlike CISSP/CCSP which require continuing education credits. AWS exams do not require experience to attain full status. Use Acloudguru or LinuxAcademy to help your labbing (see “Education Resources” section).
Comptia Linux+ - Being comfortable working in Linux (RedHat Enterprise Linux is the most popular enterprise distribution) is a valuable skill to have.
Comptia CySA+ - Exam geared toward analysts activities in cybersecurity, end goal is to teach you how to better assess threats by evaluating behavior and searching for anomalies.
Comptia Network+ - Having a good understanding of basic networking concepts is essential for knowing how data flows through an environment.
Note 1: If you are looking for a general certification to help assist with finding entry-level work in IT, check out Comptia’s certifications for A+ (PC Technician) and Google’s ”IT Support Professional” certification which helps prepare people for entry-level positions in under 6 months. If you want to hop into the government, here is a good baseline for certs they expect at “Level 1”: https://public.cyber.mil/cwmp/dod-approved-8570-baseline-certifications/
Certs for Mid-Level and Higher:
Certified Information Systems Security Professional (CISSP) - Gold standard cert in cybersecurity. You will receive associate status from ISC2 if you do not have 5 years of cybersecurity experience.
Certified Cloud Security Professional (CCSP) - Top vendor neutral cloud cert. You will receive associate status from ISC2 if you do not have 5 years of cybersecurity experience.
Certification of Cloud Security Knowledge (CCSK) – Top vendor neutral cloud cert, the exam is offered online.
AWS Solution Architect (Professional) – This exam must be re-taken every 3 years, unlike CISSP/CCSP which require continuing education credits. AWS exams do not require experience to attain full status.
Certified Information Privacy Professional (CIPP/US, CIPP/EU) - Top privacy certification in the industry today. If you would like a more technical focused privacy exam, check out Certified Information Privacy Technologist (CIPT). Both fall under the IAPP umbrella, focusing on data privacy.
Certified Ethical Hacker (CEH) - Pen testing cert, multiple choice exam.
Google Cloud Architect (Professional) – Most Google Cloud engineer/architect job posts require this certification.
Cisco Certified Network Associate (CCNA) Security - Specialty cert. The Cisco Certified Internetwork Expert (CCIE) is at the top of the Cisco cert mountain.
AWS Security Specialty – Good certification, studying for this will teach you how to better harden your environment.
Microsoft Azure Cloud(various)
SANS (various)
GIAC (various)
Offensive Security Certified Professional (OSCP) - Top pen testing cert, must break into 5 boxes in 24 hours and document it.
Note 1: Be mindful of the yearly lists which attempt to associate a salary with a specific certification. Your base salary will incorporate many factors and not just what certification(s) you hold. Location, experience and demonstrated competence carries as much weight (see section 10, salary/worth for more information). Use websites such as Reddit (subreddits), Tech Exams, and Facebook (groups) for additional information for a specific exam.
Experience
Be sure to capitalize on your existing experience/skills, which can potentially be leveraged in your pursuit of joining a cybersecurity team. Spin your existing experience and skills, demonstrate a linkage with cybersecurity (prior jobs or things you have learned in course studies). If you do not feel you can make a solid connection, demonstrate your willingness to learn. Many entry level jobs will ask for 2-5 years of experience which does not help for people trying to transition into the industry, these are possibly the people needed to help address the “skills gap”. Please view bullet point “11” below, covering “Other Tips” which can help you get past this hurdle (2-5 years of experience).
Job Posts
This will tie into the first point about identifying the area(s) you are most interested in. Once you have identified the area(s) next step is identifying roles. Once you have found role names, then you can leverage websites such as Indeed (setup a daily reminder on this service) and LinkedIn to view listings. Job posts will show skills which employers are looking for, create a master list for each role you are interested in and target the gaps. Use the education resources links above to fill gaps in your knowledge/skill-set:
Frequent skills asked for on cybersecurity job posts (as of October 2020):
Linux (Command line skills, extending out to bash scripting. Grab an .iso file for your favorite Linux distro at https://distrowatch.com/, create a live USB stick with a utility or install the distro directly to a partition on your hard drive via the live USB stick. If you do not want to install it locally then just use a cloud provider which have several operating system options to select from.)
Cloud Security | Cloud Knowledge (includes networking)
Docker | Kubernetes
CI/CD | Automation (scripting skills via Python, Bash and/or PowerShell)
Risk Analysis (app, database, data, network, IAM)
Soft-Skills: Communication (writing and speaking), teamwork, self-motivating etc.
Programming: 1A. Python / 1B. JAVA / 1C. C++
Social Media:
Be sure to take advantage of the following services:
LinkedIn: Ensure your page is always up to date with your skills, courses and relevant experience. Be sure to link to any additional pages which can demonstrate your knowledge such as a blog, paper, podcast or software repository. There are many recruiters always hunting for talent on this platform. Remember to tell your story in the “About Summary” area, signing up for this service is a requirement.
Twitter: Great place to follow and engage with cybersecurity professionals. There is a lot of talent that roams around on this service, many share great content and/or feedback (current events in cybersecurity etc.). Here is a few people/lists to follow:
https://twitter.com/binitamshah - Top cybersecurity tools/blogs curator.
https://twitter.com/fox0x01 - Azeria is a CEO and offers a great labs website.
https://twitter.com/malwareunicorn - Offensive security researcher.
https://twitter.com/laparisa - Focuses on Chrome security.
https://twitter.com/SwiftOnSecurity/lists/project-silica - Women in cybersecurity list, some of the best engineers/analysts in the industry.
Facebook: Everyone might not like Facebook, but they have decent cybersecurity groups.
Reddit: Has a dedicated subreddit for just about everything, this is another good place to engage in cybersecurity discussions.
Salary/Worth
Ensure you use tools to help get an idea of your worth, equal pay for equal work. Educate yourself with the links below:
Levels.FYI (https://www.levels.fyi/) - Best website for understanding leveling across companies and total compensation (base salary, sign-on bonus, annual bonus, RSUs/equity) for roles. Even though security roles aren't listed on the website, a user can get a good idea of whether the company pays well. They have a paid service for negotiating offers.
TeamBlind (https://www.teamblind.com/) - Good forum that people use to cover compensation packages, plus many use this website for help deciding between competing offers (with full total compensation numbers provided) via a poll.
Glassdoor (https://www.glassdoor.com/index.htm) – Insight into salaries and company reviews by current and former employees.
LinkedIn (https://www.linkedin.com/salary/) – Salary information.
H1B Salary Database (https://h1bdata.info) - Overlooked tool can provide insight on finalized salaries for specific roles for various companies.
Best Places (https://www.bestplaces.net/cost-of-living/ ) - Good tool for determining the cost of living in different cities, useful for relocation purposes.
Other Tips
These are the last few things that could help you secure your first job in cybersecurity, plus these tips can help those dealing with the “2-5-year experience requirement” hurdle for entry-level positions:
GitHub – If you lack experience, you could build your own tools or contribute to an existing project. You could reference this work here with potential employers, demonstrating your willingness to learn. This could help build up your reputation, think of this as your portfolio.
Blog – Same as above, instead of coding, post thoughts on things such as current events or share what you are learning about (includes books/article reviews). You could reference this work here with potential employers, demonstrating your willingness to learn. This could help build up your reputation.
Microblogging - Twitter is a platform filled with an enormous amount of cyber security talent. This website is a great way to connect and share content (your blog posts or standalone tweets). Share your knowledge, even if it is basic security awareness training, many people are always looking for data protection tips, whether it is for their own use or extending out to family and friends.
Volunteer - Share your expanding cybersecurity knowledge with those in your community (includes local conferences for networking), there are always those that need assistance with fundamentals. You could reference this work here with potential employers, demonstrating your willingness to learn. This could help build up your reputation.
Podcast – Start up your own show covering various aspects of cybersecurity. You could reference this work here with potential employers, demonstrating your willingness to learn. This could help build up your reputation.
YouTube - Start up your own show covering various aspects of cybersecurity. You could reference this work here with potential employers, demonstrating your willingness to learn. This could help build up your reputation.
Internship – Every summer, there are many companies that offer internships which extend out to the cybersecurity teams, at my employer, we usually have 1 intern a year and they usually are employed from June to August (before heading back to school). An internship is great for your resume, exposes you to tools and different skill-sets amongst the various teams within cybersecurity (Security Architecture, Security Operations, PCI, GDPR, Application Security, Threat Intelligence, Security Awareness, Compliance/Policy, and Third-Party Risk for starters etc.). An internship is great for experience and if you make a solid impression, it could lead to an offer and even an employer paying for your security clearance (if a defense contractor). Do not wait until senior year to apply, the sooner, the better. Check out the top 100: https://www.nationalinternday.com/top100-2019
Fellowship – Offered by many academic institutions, this is more research focused. Institutions will usually help to cover tuition and might also provide stipends. Since there is no centralized location for cybersecurity fellowship lists, simply search for “cybersecurity fellowship” on Google. Here is one example of an offering at University of Maryland Baltimore County (UMBC) which offers a full ride to UMBC, backed by the Department of Defense: https://cybersecurity.umbc.edu/dod-cysp/
Apprenticeship – Some corporations offer on the job training and study (IBM, Raytheon and Mantech to name a few). There are also many cases where universities partner with leading companies to facilitate apprenticeship paths for current students in their cybersecurity programs. Check out this tracker: https://www.newamerica.org/cybersecurity-initiative/reports/cybersecurity-apprenticeships-tracker
Special Program – Some companies offer new job opportunities specifically for students graduating with a bachelor’s or master’s degree (each one has a different general label such as Summit, Leadership etc.). The emphasis here is that the companies will train/shape you into their ideal individual contributor (you are viewed more as a clean slate). When I finished my master’s degree at Brandeis University in the Boston area, I was on boarded into IBM’s IT Architecture Summit Program for new grads (after 7 interviews over the course of 5 months). Another potential option is entering the military, lots of training and hands-on experience for cyber roles, these skills can transfer directly into civilian jobs.
Work Study - If you are receiving financial aid and are “physically” attending your school, work study jobs could be in play on campus. Many schools offer some IT positions, the duties could involve tasks around troubleshooting machines, building machines, system administration, networking and even cybersecurity.
Staffing Agency - This could be hit or miss, they could come across unique opportunities geared towards an entry level candidate.
Get Creative (For those in a non-cyber role) – I have witnessed professionals that did not feel they had enough relevant experience to transition into cybersecurity. These folks got creative with their managers during their mid-year or end year reviews to address gaps in knowledge/skills. For context, these are the type of sessions where a manager will review your accomplishments to ensure alignment with set business objectives. Once this part of the session is over, the agenda usually shifts to future team goals as well as your own goals. This sets a great opportunity to plug in a suggestion about incorporating a cybersecurity function that could fit within your current role. Going this route, can help one build up the experience necessary to move into a full-time cybersecurity role. I know this might be a stretch for some but if you are dealing with data, data security, data privacy, or access control in any capacity then this strategy could be in play. One former colleague (non-cyber role) became a security champion for their specific team and served as a liaison to our cybersecurity team, this individual ended up leaving the organization a few years later and took a security job at a leading cloud service provider.
Public Speaking / Mingling – Work on your public speaking (toastmasters / acting class / presentation of a paper authored by you at conference) or just find an event where you will speak to a range of different people (MeetUp groups etc.). Your advancement in this field can be largely hindered if you cannot effectively communicate (speaking and/or writing) or mesh with people in general.
Resume Check – Ensure your resume has been thoroughly reviewed by someone other than yourself. The review should include checking for punctuation and consistency, containing all the relevant keywords/phrases and experience. Check out the Subreddit “Resume” on Reddit (https://www.reddit.com/r/resumes/), which is a community dedicated to helping you improve the resume through review for free.
Applying - Use Indeed, LinkedIn and various company portals to apply to junior/entry level positions which interest you. Apply directly or you can also try to reach out to the recruiter associated with the posting (reconnaissance is easier to do on LinkedIn, reach out if you must). Be very proactive in your job hunt, apply to many jobs (even with the 2 to 5-year requirement for entry level), and do not just sit around and wait for opportunities to come to you. Do not forget to “network” (online and face to face) which is just as critical so please revisit that section above (#4) and take advantage of job fairs.
Featured discussion about an article focused on a study for applicants that meet only 50% of skills on a job post (6,000 applications across 118 industries were analyzed): https://news.ycombinator.com/item?id=18549361
Cybersecurity job heat map for your area: https://www.cyberseek.org/heatmap.html
Interviewing – Prep, prep and prep! Practice with a friend, if nobody is around use a mirror and speak out loud. Review the job post criteria since your interviews will mostly likely touch on the bullet points, plus your experience/knowledge and skill-set (Based on the position could involve coding). Research the company to better understand their business and culture. Remain cool, calm and collected throughout the process and demonstrate your uniqueness. Take the day off if you can, remember to ask questions throughout since you are also interviewing them! Check out the “Work It Daily” YouTube channel for more interview tips: https://www.youtube.com/user/careerealism
Hopefully some of these tips will assist in your journey into cybersecurity. Do not expect to always land your dream job in cybersecurity on your first attempt, the goal is to get your foot in the door. Your path into cybersecurity could be quicker than others or it might take some time (might do other IT role first). Outside of skills and knowledge, you will need a little bit of luck. There could be some circumstances where you may need to consider options that might not be ideal:
Relocation (Update: Due to COVID-19, there are more remote jobs opening up across the country) – I am from the Boston area, for my first job I had to relocate to Dallas. I drove cross country in 2011 to essentially get my foot in the door. The IT role (IT Architecture) later helped me pivot into cybersecurity (4 years later).
Taking a job in another IT department - I know some good engineers that built up a portion of their base skills in IT and customer service through their work with the Geek Squad team at BestBuy (opening the door for future IT positions), plus many others have come from other backgrounds such as a system administrator, help desk/end user computing technician, contracts analyst, developer, auditor and various infrastructure roles just to name a few.
Taking less money to get into an entry level position - Nobody ever wants to hear, this is only for an “extreme” circumstance, continue to fight for every dollar. Once you are in, get some experience and then leave for a better paying position (do not burn bridges). Use the tools in the “Salary/Worth” section above.
Willingness to learn and critical thinking will push you forward, learn from your mistakes and focus on improving every day. Execute and be disciplined, once you are in, be a bridge builder and pay it forward! I encourage you to mentor, share knowledge and surround yourself with good people. Remember your personal brand extends beyond your 9 to 5 role and do not be afraid to consider a career change (even if not already in IT in some capacity). Certs, degrees and networking can help land an interview, but skills (demonstrated competence), willingness to learn and ability to address an organization’s current gaps will ultimately help you secure the job. The combination of building, labbing and studying will help you become a better overall technologist.
Lastly, immerse yourself in cybersecurity but remember to continue participating in your other hobbies to avoid burnout! You are worth more than a job, a job title does not define you and no corporate job is worth dying for! Health is wealth.
0 notes
Text
My Homelab/Office 2020 - DFW Quarantine Edition

Moved into our first home almost a year ago (October 2019), I picked out a room that had 2 closets for my media/game/office area. Since the room isn't massive, I decided to build a desk into closet #1 to save on space. Here 1 of 2 shelves was ripped off, the back area was repainted gray. A piece of card board was hung to represent my 49 inch monitor and this setup also gave an idea how high I needed the desk.

On my top shelf this was the initial drop for all my Cat6 cabling in the house, I did 5 more runs after this (WAN is dropped here as well).
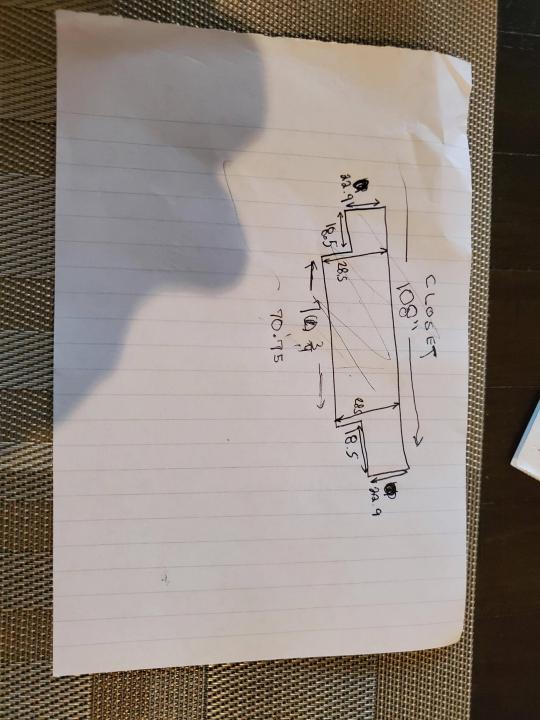
I measured the closet and then went to Home Depot to grab a countertop. Based on the dimensions, it needed to be cut into an object shape you would see on Tetris.

Getting to work, cutting the countertop.

My father-in-law helped me cut it to size in the driveway and then we framed the closet, added in kitchen cabinets to the bottom (used for storage and to hide a UPS). We ran electrical sockets inside the closet. I bought and painted 2 kitchen cabinets which I use for storage under my desk as well.

The holes allowed me to run cables under my desk much easier, I learned many of these techniques on Battlestations subreddit and Setup Wars on Youtube. My daughter was a good helper when it came to finding studs.

Some of my cousins are networking engineers, they advised me to go with Unifi devices. Here I mounted my Unifi 16 port switch, my Unifi Security Gateway (I'll try out pfSense sometime down the line), and my HD Homerun (big antenna is in the attic). I have Cat6 drops in each room in the house, so everything runs here. On my USG, I have both a LAN #2 and a LAN #1 line running to the 2nd closet in this room (server room). This shot is before the cable management.

Cable management completed in closet #1. Added an access point and connected 3 old Raspberry Pi devices I had laying around (1 for PiHole - Adblocker, 1 for Unbound - Recursive DNS server, and 1 for Privoxy - Non Caching web proxy).

Rats nest of wires under my desk. I mounted an amplifier, optical DVD ROM drive, a USB hub that takes input from up to 4 computers (allows me to switch between servers in closet #2 with my USB mic, camera, keyboard, headset always functioning), and a small pull out drawer.

Cable management complete, night shot with with Nanoleaf wall lights. Unifi controller is mounted under the bookshelf, allows me to keep tabs on the network. I have a tablet on each side of the door frame (apps run on there that monitor my self hosted web services). I drilled a 3 inch hole on my desk to fit a grommet wireless phone charger. All my smart lights are either running on a schedule or turn on/off via an Alexa command. All of our smart devices across the house and outside, run on its on VLAN for segmentation purposes.

Quick shot with desk light off. I'm thinking in the future of doing a build that will mount to the wall (where "game over" is shown).

Wooting One keyboard with custom keycaps and Swiftpoint Z mouse, plus Stream Deck (I'm going to make a gaming comeback one day!).

Good wallpapers are hard to find with this resolution so pieced together my own.

Speakers and books at inside corner of desk.

Speakers and books at inside corner of desk.

Closet #2, first look (this is in the same room but off to the other side). Ran a few CAT6 cables from closet #1, into the attic and dropped here (one on LAN #1, the other on LAN #2 for USG). Had to add electrical sockets as well.

I have owned a ton of Thinkpads since my IBM days, I figured I could test hooking them all up and having them all specialize in different functions (yes, I have a Proxmox box but it's a decommissioned HP Microserver on the top shelf which is getting repurposed with TrueNAS_core). If you're wondering what OSes run on these laptops: Windows 10, Ubuntu, CentOS, AntiX. All of these units are hardwired into my managed Netgear 10gigabit switch (only my servers on the floor have 10 gigabit NICs useful to pass data between the two). Power strip is also mounted on the right side, next to another tablet used for monitoring. These laptop screens are usually turned off.
Computing inventory in image:
Lenovo Yoga Y500, Lenovo Thinkpad T420, Lenovo Thinkpad T430s, Lenovo Thinkpad Yoga 12, Lenovo Thinkpad Yoga 14, Lenovo Thinkpad W541 (used to self host my webservices), Lenovo S10-3T, and HP Microserver N54L

Left side of closet #2

**moved these Pis and unmanaged switch to outside part of closet**

Since I have a bunch of Raspberry Pi 3s, I decided recently to get started with Kubernetes clusters (my time is limited but hoping to have everything going by the holidays 2020) via Rancher, headless. The next image will show the rest of the Pis but in total:
9x Raspberry Pi 3 and 2x Raspberry Pi 4
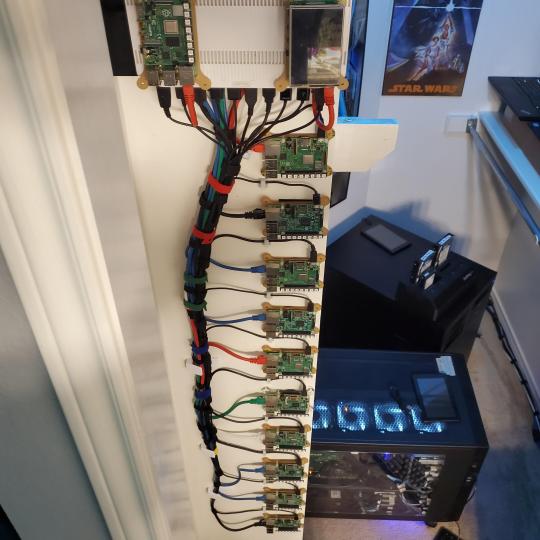
2nd shot with cable management. The idea is to get K3s going, there's Blinkt installed on each Pi, lights will indicate how many pods per node. The Pis are hardwired into a switch which is on LAN #2 (USG). I might also try out Docker Swarm simultaneously on my x86/x64 laptops. Here's my compose generic template (have to re-do the configs at a later data) but gives you an idea of the type of web services I am looking to run: https://gist.github.com/antoinesylvia/3af241cbfa1179ed7806d2cc1c67bd31
20 percent of my web services today run on Docker, the other 80 percent are native installs on Linux and or Windows. Looking to get that up to 90 percent by the summer of 2021.
Basic flow to call web services:
User <--> my.domain (Cloudflare 1st level) <--> (NGINX on-prem, using Auth_Request module with 2FA to unlock backend services) <--> App <--> DB.
If you ever need ideas for what apps to self-host: https://github.com/awesome-selfhosted/awesome-selfhosted

Homelabs get hot, so I had the HVAC folks to come out and install an exhaust in the ceiling and dampers in the attic.

I built my servers in the garage this past winter/spring, a little each night when my daughter allowed me to. The SLI build is actually for Parsec (think of it as a self hosted Stadia but authentication servers are still controlled by a 3rd party), I had the GPUs for years and never really used them until now.

Completed image of my 2 recent builds and old build from 2011.
Retroplex (left machine) - Intel 6850 i7 (6 core, 12 thread), GTX 1080, and 96GB DDR4 RAM. Powers the gaming experience.
Metroplex (middle machine) - AMD Threadripper 1950x (16 core, 32 thread), p2000 GPU, 128GB DDR4 RAM.
HQ 2011 (right machine) - AMD Bulldozer 8150 (8 cores), generic GPU (just so it can boot), 32GB DDR3 RAM.

I've been working and labbing so much, I haven't even connected my projector or installed a TV since moving in here 11 months ago. I'm also looking to get some VR going, headset and sensors are connected to my gaming server in closet #2. Anyhow, you see all my PS4 and retro consoles I had growing up such as Atari 2600, NES, Sega Genesis/32X, PS1, Dreamcast, PS2, PS3 and Game Gear. The joysticks are for emulation projects, I use a Front End called AttractMode and script out my own themes (building out a digital history gaming museum).

My longest CAT6 drop, from closet #1 to the opposite side of the room. Had to get in a very tight space in my attic to make this happen, I'm 6'8" for context. This allows me to connect this cord to my Unifi Flex Mini, so I can hardware my consoles (PS4, PS5 soon)

Homelab area includes a space for my daughter. She loves pressing power buttons on my servers on the floor, so I had to install decoy buttons and move the real buttons to the backside.

Next project, a bartop with a Raspberry Pi (Retropie project) which will be housed in an iCade shell, swapping out all the buttons. Always have tech projects going on. Small steps each day with limited time.
6 notes
·
View notes
Photo


On a personal note (taking a break from exam tips), Mercedez and me are expecting our first child in September, a girl which we will name Solana Sylvia. Above you will see the first baby shower we had in Los Angeles (July 4th week). My cousin Andre (from the “You Reach, I Teach” series on this blog) and his wife Trimeka are expecting a girl a few weeks after us.
0 notes
Text
Tips for passing the Information Systems Security Architecture Professional (CISSP-ISSAP) exam
I passed the CISSP-ISSAP on June 23rd in Dallas. Instead of writing another guide I would just refer you all to my prior Tumblr posts about the CISSP and CCSP, that combined with reading the ISSAP CBK should be the enough to pass the exam. Remember it’s not about memorization, eliminate 2 answers right off the bat and then use a combination of your studies and experience to make your final selection (also re-read the question for context, you don’t want to miss the easy ones due to misinterpretation). Please note, the ISSAP requires 2 years of enterprise architecture experience. I spent a majority of my career at IBM as an Architect, now at Sabre I transitioned from an Information Security Analyst to a Security Architect. I’ve completed my goal of attaining the CISSP (Feb), CCSP (Feb), CCSK (Feb) and ISSAP (June). My work required the CISSP and figured I had some time to sit for the others, I covered all test expenses (books and exams) myself and it does get very costly (this includes the CPEs). The only thing left on my list really is the OSCP (2019) and the AWS certs (Aug), I might sit for the CySA+.
Please note over my career I’ve interviewed at some of the top tech companies and a overwhelming “majority” required the certs or an expectation to get them within 12 months, along with competency and experience (some of the few that didn’t require certs were Google and Facebook). The exams aren’t easy and you will need to set down a few hours a day to go over the material, most HR systems filter out candidates that don’t meet their baseline requirements from an education and certification perspective (my colleagues over the years frequently brought this issue up).
Lastly, I highly encourage to learn by doing and also monitoring headlines/projects on sub-Reddits such as HomeLab, SysAdmin, NetSec, Docker and DataHoarders. I spend a lot of time outside work sharpening my skills since I’m a tech enthusiast and want also remain competitive in my industry, homelabbing and continuous reading is critical to success. Get better everyday and help others reach their goals.
0 notes
Text
Tips for passing the Certified Cloud Security Professional (CCSP) exam
Passed the CCSP test on February 24th, 2018, it was tough as I expected. I studied for this exam for about 2 weeks (6pm to 2am), I was going to sit for this test in early March (week day) but noticed a week ago that my local PearsonVue had a Saturday availability open up. Please note, I passed the CISSP exam a few weeks earlier (3 months of studying) which helped on the CCSP exam, along with my work experience. Took me about 2 hours and 30 minutes to complete. I didn't review any of my answers, as others noted on their CISSP test style (via Reddit), mark and move on but your style may differ.
How to Approach the Exam:
The majority of this test was from the mindset of a 3rd party risk assessor, security architect (cloud) and a privacy attorney (laws and regulations). As I noted in my CISSP post a few weeks ago on Feb. 5th, this was not a test of memorization and it all comes down to your "situational analysis" ability, you must understand the concepts. Your studies should allow you to eliminate 2 of the 4 choices right off the bat for each question. As called out in the Cybrary videos for CISSP and CCSP, you answer each question as a "risk advisor".
Background:
• 8 years total, in roles such as IBM IT Architect, IBM Security Consultant and Sabre Security Analyst - Third Party Risk and Sabre Security Architect (current role that I started in March of 2018).
• I've assessed cloud platforms and various SaaS services built on top of them, on a daily basis for the past few years (Lead Security Analyst - Third Party Risk).
• Work closely with the Legal Team/GDPR team (data privacy), Procurement team (they handle contract negotiations with vendors, SLAs etc.), Insurance team, various internal business sponsors (requesting the cloud solution), Security Architecture, Exception Requests team, and Enterprise Operations team (if a IaaS/PaaS request).
• 80% of the requests that come into my assessment request queue are for SaaS services, the other 20% are comprised of Managed Cloud Service, PaaS, IaaS and locally installed solutions (server or desktop).
Long story short, I have to assess the level of risk for the organization and call out (in writing) technical controls for the sponsor/administrator to help mitigate risks for requested service/tool. As your CCSP sources will call out, much your risk assessment will come down to: alignment of business requirements aligning with corporate policies, the type of "data" your company will be exposing, the corresponding data classification level, location of the data (PII for EU nationals has additional requirements etc.), how the data will be protected, plus laws and regulations that must be taken into account.
Here's what I used to study:
• CCSP CBK - Not that good, you're better off grabbing a vocabulary list off of Quizlet and then building out your own set. Use this as your base Quizlet set (132 words), once you go through the sources list below, your final word list should be over 290+ items.
• CCSP Official Study Guide - Solid book, I used this in the manner I used the 11th Hour for CISSP, I looked at it the morning of the exam (I used the official Android app to do "all" the questions for each section "once" for all domains at the beginning of the week, didn't open the book until yesterday).
• Cybrary CCSP videos - Decent set, downloaded the MP3s and the slide deck but much of it overlays from Kelly's CISSP set. Got through the deck and only listened to a few domains. Stick to what she preaches, answer all questions in the "manager" mentality and doing what's been to protect the enterprise.
• Fast Track CCSK v4 - Found this book on Amazon, only about 100 pages, easy read and helps plug in a few gaps, not a requirement.
• Cloud Security Alliance Guidance v4 - This is a requirement to pass the test, CBK only covers about 20% of what's on the exam, this document will cover another 40-50% of the material from the CCSP exam.
• Cloud Security Alliance Control Matrix! - Document calls out controls, skim through this.
• OWASP Top 10 - Direct link to 2017 version is provided.
• NIST 144 - Guidelines on security and privacy in cloud computing.
• NIST 145 - Definitions of cloud computing.
• NIST 146 - Cloud Computing Recommendations.
• ENISA - Risks and Recommendations.
• ENISA - SMEs Perspective on Cloud Computing.
Test Engines:
• Only used the official practice tests application, which can be found on the Android store and Apple store. Helped a little, overall I didn't find many test engines for CCSP. If anything the app will help you better understand the definitions, real test will throw you into a scenario.
Other Sources (restricted for internal use, day job. You will need to be familiar with the documents called out below for this exam.):
• Completed vendor questionnaires (we typically check for gaps, in polices/procedures or the lack of third party audit like a SOC etc. which can help validate answers in the questionnaire. Management is more comfortable when a vendor has conducted a third party audit on their service, please note some vendors that sit on top of Amazon will attempt try to pass you "only" Amazon's audit reports such as a SOC, which isn't useful. Furthermore, federation is another element that should be considered and whether top level admin access can leverage 2FA etc.. Here are examples of vendor questionnaires put out by Google.
• Completed internal questionnaires (business sponsor has to call out their use case, the type of data and things like whether any our our EU colleagues would be impacted.).
• Completed CSA Consensus Assessments Initiative Questionnaires.
• Submitted SOC 1 Type I and II reports (for the service requested and also the CSP).
• Submitted SOC 2 Type I and II reports (for the service requested and also the CSP).
• Submitted SOC 3 (rarely see these).
• Submitted ISO27001 cert w/ SOA (SOAs are provided every once in a blue moon).
• Submitted PCI related documented (if workloads incorporate credit cards).
• Submitted Security/Privacy policies (if you time read various public facing privacy policies to see have different organizations protect your data).
• Vendor contracts from Procurement, red lining (SaaS level has the best ability to dictate terms compared to Paas and IaaS which is called out in the CCSP sources).
Other Tips:
• If you need to do a brain dump on the sheet provided by your test center, make sure you do it after you sign the NDA (5 min timer, if it times out you lose all your money and forfeit the exam). The screen after the NDA has no timer, do your brain dump then.
• Do not panic, believe in your ability.
• Review your CISSP notes if you've taken that test, elements of the CISSP will pop up in this exam.
• Know your laws.
• Re-read all questions during test, you don't want to miss questions due to not understanding the context.
• Learn about Third Party Risk Management.
• Test your knowledge daily with your Quizlet flash cards, "star" the items you struggle with.
• When you pass, help others that are traveling down this path.
• You may want to consider sitting for the CCSK exam shortly after you successfully wrap up your CCSP exam.
• There isn't much activity in the CCSP forum on Reddit and I don't believe the TechExams website even has a dedicated channel for CCSP either. Try visiting each forum every 2-3 weeks for new tips that others provide for passing the exam or some of the lessons learned from people that failed on the 1st attempt.
Endorsement Phase:
If you are CISSP then this process will be much quicker. Direct link to page here.
Other:
After I cleared the CCSP, I did the CCSK exam the following day and passed. CCSK relies heavily on the CSA guidance v4 and CSA cloud controls matrix.
Hope this helps someone. Best of luck in your studies!
0 notes
Text
Tips for passing the Certified Information Systems Security Professional (CISSP) exam
Passed the CISSP exam on February 5th, 2018 which is one the gold standard in cybersecurity certifications, globally recognized and a top HR filter. I've been studying for this test since mid-November each evening after work. My exam was evenly distributed across the 8 domains, my exam got pretty tough after the 20th question and ended on the 100th question (Duration: 1 hour and 50 minutes). Towards the end, some of the questions I felt were worded terribly, I had to re-read some of those like 5 times.
My Background:
• IBM - IT Architect (4 years)
• IBM - Security Consultant (2 years)
• Sabre - Security Analyst (2.5 years)
My current role is a Security Architect at Sabre, I was promoted in March of 2018.
Resources:
• Cybrary CISSP video series with Kelly - 9/10
• Simple CISSP (audiobook) - 6/10
• Lynda CISSP video series with Mike Chappel - 7/10
• CISSP CBK - 8/10
• CISSP (ISC)2 Official Study Guide Book and Practice Test Book - 8/10
• Sunflower PDF - 8.5 /10
• 11th Hour - 8.5 / 10
• CISSP Exam Cram - 8.5 /10
Impressions of the test:
The test was difficult, felt well prepared (90% confidence) not only due to the time I put in utilizing the various resources above but also the invaluable tips posted on the CISSP subreddit, the CISSP Facebook group and the TechExam forum. There were a good handful of the answers I was able to narrow down to "doing something yourself" vs. "manager response" as Kelly suggested in the Cybrary videos.
Advice for Others:
• First, understand the way you learn then you'll be able to better in-take the vast amount of content across the 8 domains. The material must stick with you, not just for this test but long term since it will serve you well in your career.
• Learn the concepts for each section, this definitely wasn't a test of memorization. This test focuses mostly on your situational analysis ability, pay attention to the key words ("best", "most", "least" etc.).
• "If" you need to do a brain dump (OSI model, TCP model, EAL, formulas etc), make sure it's after the NDA is signed (5 min timer). The screen after the NDA page has no timer, allowing you to successfully dump whatever key elements you want to throw onto the paper provided by the test center.
• If you put in the work on your studies, you should be able to at least filter out 2 wrong answers per question, boosting your chances. As Kelly says in the Cybrary videos, don't try to fix things, report up to senior management (demonstrate the value of enterprise security).
• Don't second guess yourself, if you are scoring 75%-85%+ consistently then sit for the exam and don't keep delaying the date.
• Once you pass, ensure to give back to others that are trying to reach their goal of passing the CISSP exam, whether it's folks from Reddit, TechExams or maybe some work colleagues that are starting to buckle down on the CISSP.
0 notes
Text
Building Your Own Personal Cloud
I've read numerous reports this week covering the booming "personal cloud" space, one article even suggested this will be a $43.5 billion industry by 2018 based on studies!
Lets get one thing clear, there's nothing personal when your data is stored on a public cloud services like those offered by Dropbox, Google, Microsoft & many others. Security and privacy is still a major concern when it comes to cloud, since you don't truly know where your data will end up as many whistleblowers have demonstrated throughout the year. Furthermore, there have been instances where cloud vendors close up shop and leave their users in the dust. The extreme cases are when government agencies seize control over services they feel are operating unlawfully, Megaupload is a great example of this and many users are still trying to line up to get their content back:

There's no better time to begin working on your own self hosted personal cloud then now (for consumers not enterprise!), desktops are cheap and you can get even extract additional value if you build the box from the ground up and slap it together with others (plus inexpensive Raspberry Pi devices).

(My Pi setup) Hosting your own services allows you to manipulate your data in whatever manner you chose, plus you dictate the security and privacy measures. Personal clouds are perfect for just about every user, from road warriors to those dealing with a growing family. Your goal should always be able to create a seamless experience, some call this the experience layer which sits on the highest the cloud (vendors feel this layer will generate tons of additional revenue if they're able to successfully string together multiple services).

(My Microserver)
These days we are constantly reminded that the PC is dead and the tablet arena is thriving, I don't believe in this notion at all since most tablets are purely consumption devices and content creation is very difficult. Moving forward whether you're operating from a laptop, tablet, or smart-watch on the go, you will only be as strong as your cloud (your computer(s) at home, must serve as a base). Even if it takes you a few weeks or a few months to set up, it will be well worth the effort. Nothing wrong with getting your hands dirty on the weekends, that's the approach I've used since my childhood, when I was screwing up computers. The best way to learn a technology is to test it out yourself, don't settle on reading just notes from a PowerPoint or an article. If you have access to these resources or have money in the budget, go for it! Add new skills and stay on top of your game, learning shouldn't stop when you leave school. Even if it's not technology, be passionate about what you do!

(onsite box and offsite box being constructed)
Clouds can offer an abundance of services but most folks that aren't that involved in tech, think of cloud as only file storage. The question I constantly get asked is the difference between a file server and a cloud. I put together an architecture which should help some folks out there get started on this journey, keep your eye on the "base services" offered.
I will briefly walk you through the architecture, most of the items you can easily find tutorials for on Google & Youtube. Feel free to plug in additional modules you think would add value.
Requirements: Desktop, Raspberry Pi, and throw in any other computing devices you have laying around (re-purpose them!). Keep in mind the platforms utilized will be Windows, Android & Linux based, plus you can add in FreeNAS on the backend.

We'll start in the cloud (box by box) and work our way up the picture:
Physical Security

When you're on the go and want to check on your house/apartment, the cheapest way of doing this is through the use of a webcam or an old camera phone. Yawcam simply allows you to stream your webcam over the web, you can password protect the stream as well (which you SHOULD do). Motion capture is a feature of the software, so if a robber walks in and you're camera is facing him, it will take a picture and save it to your designated folder and you can get email alerts if this occurs. The folder you choose during setup should be CLOUD enabled (think BTsync or even Dropbox), so if a picture gets snapped it automatically gets synced to another computer before the thief even thinks about unplugging the computer. I have helped many folks through the use of this feature in the past. Lastly, this service will provide you at least some peace of mind. Grab it here:
http://www.yawcam.com/download.php
FileSync

When you're on the go, you want to ensure your content stays synchronized and accessible. Up until this point, Dropbox was the lead dog but the downside is that they house a copy of your data on their servers and you have to pay if you need more than 2GB. BTsync also known as BitTorrent Sync has caused some disruption in this market, what's unique about this service is that there's no 3rd party server hosting your data, the storage is predicated strictly by how much space is available on the computers you are syncing to and from. BTsync also has a mobile app. Great service. Grab it here:
http://www.bittorrent.com/sync/downloads
VDI
:

Virtual Desktop Infrastructure, this is actually a combination of the Spice (client rendering), Proxmox (virtual machines) software, & SoftEther (VPN). VDI will allow you to leverage any of the operating systems you load directly into Proxmox, we'll cover this a bit more in the next section. Basically, if you have a Linux distribution or a Windows OS (operating system) loaded onto Proxmox you will be able to spin either of them up on demand, once you connect to your network via VPN (SoftEther). Grab it here:
http://www.spice-space.org/download.html
VMs
Virtual Machines, which is basically software emulation of an OS (you're ripping out the physical hardware). The OS of your choice runs on top of a hypervisor, you dedicate (X) amount of resources to the instance you decide to utilize. Some of the most sophisticated malware in the wild can actually detect if it is operating in this type of environment, self destructing immediately. The functionality of a virtual environment does have trade-offs, like yes you will be able to save floor space if you can bundle all of your systems into 1 box but you take a performance hit on x86 based machines compared to running everything on dedicated boxes (think bare-metal, think Softlayer). Proxmox comes with a range of features, and you can drop a ton of operating system images onto it and spin them up one by one or simultaneously. First, you install Promox on a dedicated box with a least 8 GB ram, then you can tap into the box on your LAN (local area network) from another computer (you would use a VPN to do this one the go). Once you are logged into your Proxmox box, you select your instance (you would use VNC or Spice to view the instances once they are spun up) and the rest is history. Test out Openstack or even Docker's linux containers on one of your Linux iso images.

Grab it here:
http://www.proxmox.com/downloads
Collaborative Coding
: If you want to code with a friend that isn't local to you, the Codiad solution would be a value add (self hosted). Keep in mind there are a few others out there & don't expect the full blown IDE you would have locally.

Grab it here:
http://codiad.com/
Document Collaboration
: If you want to host your own Google Docs-like service which enables you to edit with others not local to you, Etherpad Lite is the way to go at this moment.

Grab it here:
http://etherpad.org/
Storage
If you are looking for a solid back-end storage software solution, you should utilize FreeNas in combination with ZFS which is dubbed the self healing file system and much better than Windows NTFS when you compare features.
Keep your eye on the Linux's Btrfs. Drives fail time to time, so it's important that your mission critical data is protected by the best consumer grade solutions out there: Grab it here:
http://www.freenas.org/download/
.NZB and .Torrent
These file extensions allow you to seamlessly download a specific data file when it's combined with the right client. Most folks think these extensions are only attached to illegal files, think again. You will find tons of open source software and educational material being distributed with this method. If you do this all right, you can automate the entire process (example: You grab a free educational video torrent on phone, once it downloads to your SD card another mobile app can sync the file to a specific desktop folder, the LOCAL torrent client on your computer would actively scan this folder then if anything is found it would delete the torrent and download the material, the finished file could be moved automatically over the network to another computer, then you could point PLEX to actively scan the "finished folder" and if anything is found (like the educational video) it would be instantly available for streaming). Grab them here:
http://sabnzbd.org/
http://www.utorrent.com/downloads/win_us
Media Streamer
:

When you're on the go, you want to be able to access your media the same way folks access Netflix. Many might argue Plex is leaps and bounds better than Netflix, on the reveal for the new Amazon set-top box, one of the featured services was Plex. Plex is only as strong as the content you plug into it, people in this instance would only stream content that they legally own. Parents on those forums like to share their video content with their kids and stuff (like photos). Pretty easy to setup, the server resides on a local computer and the user taps into it via the client which is available for all platforms (even Chromecast) or you could use a web browser as well. VLC streaming server could also be used alongside Plex (that's if you run into any issues with Plex). Another great service, download the "server" and install the server first.
Grab it here:
https://plex.tv/downloads
Books

If you don't want to carry around all your ebooks for a specific reason, you can easily set up your own ebook server with the help of Ubooquity. Pretty straight-forward, you install the server and point the directory at your books. Once this is complete, you can setup your security measurements in the settings, then from a web browser you can access your collection (there's no mobile app at the moment). If you're wondering why go with this instead of just a traditional file server, that would be the fact the meta data is extracted from each book and also book covers. Ubooquity doesn't offer connections via HTTPs but that's coming soon, in the mean time you could just setup a reverse proxy server which could solve that gap. I would also note Ubooquity respects your file structure unlike the solution of choice for most people called Calibre. Great service. Grab it here:
http://vaemendis.net/ubooquity/static2/download
XMPP
:

Extensible Messaging and Presence Protocol, created as an open source alternative back in the days of AIM, XMPP these days is the backbone to lot of messaging services (even with Google shutting down their XMPP support in May of 2014). Having an XMPP server allows you to provide your own chat functionality to (X) number of users, everything stays in-house plus users (that you setup on your OpenFire server) will be able to securely communicate with each other via audio (encrypt calls via ZRTP), texts, and video (one on one or a Google hangouts like feature). I would recommend the Jitsi client in combination with the OpenFire server. Great service. Grab them here:
http://www.igniterealtime.org/projects/openfire/
https://jitsi.org/Main/Download
FTP
File Transfer Protocol (over SSL), no cloud is complete without some sort of FTP, FTPs adds in the secure layer for data transfers. You can grant access by IP and protect your server with either passwords or keys. FileZilla has a ton of tutorials on how to do this, I would advise checking them out. The value here is being able to quickly tap into your files on the go. Grab it here:
https://filezilla-project.org/download.php?type=server
VPN

Virtual Private Network, when you're on the go and want to tap into your entire home network (aka LAN) and not just one computer via SSH (Secure Shell), you would use a VPN. VPNs are also another great way of encrypting data as well. If you are a tech noob basically when you're in your home, you have access to local shared resources (like folders on other computers) and you can also configure things like your router via some IP like 192.168.1.x. When you're on the road, you don't have this type of luxury from another network (WAN) unless, you can connect to your LAN via a VPN. The server offered by SoftEther is now open source and easy to deploy, you can tap into your VPN via a SoftEther client, OpenVPN client, or the IPsec - PSK method found on your mobile phone's VPN settings. Grab it here:
http://www.softether-download.com/en.aspx
Other Notes -------------
Router
- This is the central point for the packets flowing in and out of the network so it's important you carefully open up the correct ports for the services listed above.
Switch
- Provide additional ports for connectivity, use CAT6 cables if you want to future proof yourself since they can handle a 10gb network unlike Cat5e.
NGINX
- Reverse proxy (2 for high availability) that can be bundled with other modules such as Memcache (distributed memory cache system), can be plugged into the cloud to handle requests on behalf of other servers and you can also provide HTTPs for solutions that operate without SSL like Ubooquity book server.

Fail2Ban
- Monitoring system that can be easily installed to protect your servers from things like brute force attacks.
Snort & OSSEC
- Solutions that can help detect intrusions, please take steps to harden your servers.
DYNDNS or No-IP
- Bind your WAN IP to a domain name. IPs do change so it's absolutely important that this step is NOT SKIPPED. When you're on the go it's easier to remember a domain name than a IP number.
0 notes
Text
Road Warrior Essentials
I've been meaning to push this post out for awhile, I waited a bit so I could include not only tips but also some new devices/utilities for more effective road travel 2014 and beyond.
I've been working at IBM since 2011 and been fortunate enough to travel all around the country in such a short time frame. I've seen it all, angry taxi drivers when you pay with a credit card instead of cash, 12 hours on a plane to get from Miami to Dallas, phantom room service charges at Disney World, hotels that view irons as a "luxury" and not a necessity, plus many other frustrating scenarios.

Most people always ask what's the most crucial aspect to ensure you get to all your planned destinations in a timely manner, I always tell them it's putting together a game plan before you even set out the door. Everything starts at home, the last thing you want to be is unprepared and in a rush.
Step One: Sign up for a frequent flyer program, take advantage of every mile you fly! Companies sometimes have agreements in place relating to perks which allow you to grab automatic status. If you want an example, IBMers used to get automatic status on Delta Airlines and competitors such as American Airlines would offer a 1-time match. Up until 2014, I had status on both airlines but Delta no longer honors the deal (Update: American Airlines no longer honors the deal as of Feb.28, 2014 and will charge $699-$1200 for Gold & Platinum status). I would also note that one should consider a credit card which offers miles for each dollar you spend, easy way of stacking up points for use towards personal vacations (Example: CitiBank Card). Make sure to also check out loyalty programs for hotels and rental car businesses, they'll come in handy.

Step Two: If you want to drastically speed up the time to get from the terminal entrance to the gate, I would recommend checking out the TSA Pre-Check program. American Airlines' frequent flyer program incorporates the Pre-Check program at select airports. If you're enrolled, you will get to skip long security lanes, plus you can keep your shoes on & your laptop stays in your bag at TSA checkpoints. If you're an international traveler and want to speed up the time to get through customs I would suggest checking out the Global Entry program.

Step Three: Preparing your phone for travel is absolutely essentially, I'm not only talking about the apps for respective loyalty programs, flight trackers, VPNs but also ones that can keep you entertained during extended periods & also help you keep tabs on your home. Here are the Android apps I recommend to install (you can apply the same logic to iOS):

Wi-Fi Protector - If you are accessing the internet over Wi-Fi (I recommend cellular networks over public wi-fi on the go, tether if you can as well), it's important that you don't get hit with LAN based attacks. Wi-Fi Protector will help mitigate risk, especially when dealing with ARP related attacks. Cell phones and laptops constantly send out probes, looking not only for nearby access points but also recent access points you have saved on your device. If you're connected to an access point which displays your the WI-fi name from your router at home but you're in a public place, you have a problem. Watch out for rogue access points, check this video out for more details: http://youtu.be/N_tnHHEFGKs?t=3m42s
DNSwitch- If you rooted your phone, you can add another layer of security by simply entering a 3rd party DNS server, become less prone to DNS spoof attacks. DNS servers if you're unfamiliar convert a domain name to an IP. Most phones have default network settings meaning you are using the DNS servers specified at the router level. If that router happens to be malicious and you are using default network settings, you will be pushed to destinations that you never entered in the address bar. If I have a rogue access point set up at a public place, and I have a rule that pushes those that connect to me to either a malicious site or an unencrypted website (think https stripped to regular http, like https://facebook.com to http://facebook.com) I'll be in position to capture information about you. The way to override this in most cases is at the DNS level (using your preferred DNS servers), so check out the app.
Android Firewall -Firewall for Android or if you're rooted check out the Xposed Framework and use Peerblock.
Plex (client) - Install the Plex Server on your PC, load up your system with legally owned media and stream to yourself on the go (audio or video). Basically you can turn it into your own personal Netflix without the Comcast/Verizon throttling your high speed connection due to the net neutrality ruling. Join the cord cutting revolution.
Firefox with HTTPS Everywhere Plugin - This will force all sites to use HTTP over SSL (HTTPS) if it is supported. The more encrypted channels the better.
Uber - One of the hottest start-ups around, you punch in your info & and at a moments notice they'll be there to pick you up (only select cities). You pick the vehicle as well.
Fitness Apps - Use any app, working out on the road will keep your mind fresh, don't camp out.
Translation Apps - Google Translate or iTranslate are potential value adds if you are traveling aboard.
LinkedIn - Stay connected with business contacts.
Skyscanner - Track your flights.
MoonReader+ - Read your books on the go, if you have your own collection at home just drop all the electronic books into an ebook server like Calibre or Ubooquity (my choice). Once this task is complete, you'll be able to pull them up with OPDS features on your android ebook app. If you're a speed reading fan, check out SpeedReader on Android.
Prey - Load this application onto your devices (desktop, laptop, tablet, & phone), it's free and will help you track them down your devices if they are ever stolen. Their slogan, "The party is over for thieves."
BitTorrent Sync - Server-less alternative to Dropbox, you control your own personal "cloud". Your storage is simply determined by the size of your hard drive. All data in motion is encrypted, be on the lookout for the server-less chat client the organization is rolling out soon. Some are calling this the Snowden effect. Sync works on all platforms.
Teamviewer - Install on phone and PC, tool will allow you to easily remotely control any of your computers the software is installed on. The solution also has a built-in VPN.
Step Four: The computer you are leaving on at home has to help serve as your anchor. I use my desktop which is an 8-core AMD (some would argue AMD doesn't make true 8-core chips since the resources are split between pairs) with 16gb ram, my FIOS package is pretty decent it's about 80 down and 30 up.

Plex Media Server - Stream media that you own to yourself. Think of it as your own personal Netflix as I stated above.
Yawcam - Use your webcam to monitor you home one the go, change the folder to the location of your Dropbox / Google Drive under the motion sensor settings. You can also setup simple email alerts if anything unusual is caught on camera. You can launch the tool from your smartphone via the Remote Launcher application, be sure to use DYNDNS or NoIP to mask your home computer with a domain name.
Ebook Server - Calibre and Ubooquity will scrape together information about all your books, both offer a content server for easy access on the go to your purchased books.
Bittorrent Sync - Take ownership of your data, cut out the middle man and snooping servers.
Step Five: The computer you are taking on the road has to be properly secured, if you think anti-virus is a one stop shop then think again! Use my framework to add additional layers of security for your portable workstation.

Remember on the road to use a VPN at all public locations, this includes your hotel. Tether if you have an unlimited data plan. Quick tip, if the Wi-Fi access in your room is shaky and there's an ethernet cord available, plug that into your laptop and log onto the local network. Once this phase is complete, you can then use your laptop's internal wi-fi card as an access point via a simple app called Virtual Wi-Fi Hotspot found here. The application could also help with your Chromecast streams on the go.
Step Six: When traveling always bring:

(Image: Boarding for New York)
- One long shirt for the plane, no matter the final destination the A/C will make you shiver.
- Portable battery pack to charge your phone or tablet on the go, check it out here.
- Aux Cable since you never know when your rental will have an aux out on the dash, listening to your music beats the the local radio.
- Cigarette Lighter USB charger, comes in handy for your phone on the go.
- Headphones to lock out noise on the plane and at the gate, if you don't want to hear folks yapping or kids screaming once their ears pop then I suggest you pick up a pair. Hear what you want.
- Neck rest pillow (air version) can double as a pillow for your head.
-Extra pair of clothes on hand for those that check their luggage, luggage sometimes gets lost along the way.
-Grab a snack once you make it across security, don't forget that some airlines like American don't offer snacks unless there's a major plane delay or detoured to another airport due to weather related issues.
-Bring your awareness, know your surroundings. If you have to stay overnight at an airport find a safe spot to lay your head. I would also note it's helpful to know where the police are stationed in the building (not the TSA).
-GPS, don't leave home without it.
Step Seven: Use Google to do your scouting before you head out the door.
Scout the area:

Locate your hotel:

Locate the closest airport:

Find your meeting location:

Print out the information (addresses, phone numbers, & maps) if you need it for reference or just save them in an app like Evernote.
Step Eight: Method of payment on the road:
Cash > Credit > Debit (use this method when you aren't using a corporate card for payment)
Step Nine: Be nice to everyone you encounter on your journey. Says thanks and leave tips for folks (like those that clean your room or your shuttle driver). Travel safe & visit Boston sometime!

0 notes
Text
2014 is Here

I’ve really enjoyed spending countless hours over the last 12 months digging into different security based topics on my spare time. After diving deep into the subject in 2013 (personally and professionally), recovering stolen laptops in Africa (while in Boston), helping Ivy Leaguers effectively deal with ransomware attacks, and gathering evidence through motion capture of apartment personnel entering units without notifying the tenant in Dallas! I’m happy that the document created on “Securing Windows Endpoints (which I update regularly),” has helped many revamp their own protection strategies, in a world where more then 200k-300k pieces of malware is created each day. Mac and Linux/BSD users were also able to benefit from the document as well due to its versatility.
When I first joined IBM in July of 2011, I was instructed to try a little bit of everything in order to discover my niche. Based on the passion I’ve developed for this area and the thrill of helping others in times of need, I’ve begun looking into programs in which I’ll be able to attain a Masters of Science in Cyber Security (while working of course). I’m already working as an IT Architect at IBM, I’m hoping it will push me down the IT Security Architect path.

0 notes
Text
Updated Windows Protection Layout
I'm at IBM Research in NY this week for classes on Cybersecurity. I figured it would also be a good time to release an updated layout for securing Windows endpoints! Added you will find more protection against techniques like Cryptolocker (malware that encrypts all your documents locally and on network drives) via defense programs CryptoPrevent and Hitman Alert Pro. Notes on ARP Spoofing (man in the middle attack over LAN) were added and RAM requirements for total setup.
[I’ll re-upload the image, the hoster closed their business]
Lastly, Go Sox! Another year, another parade.

"This is our fucking city, and nobody is going to dictate our freedom. Stay strong!" -David Ortiz
0 notes
Text
"Not Impressed" By Jobs and Wozniak: An Interview With A Founding Father of Modern Computing

Antoine Sylvia sent me a magazine article on the late Jerry Lawson. An electronic engineer by trade, Lawson was a central figure in the computer and videogame movement in America.
One of the only blacks on the tech scene in the 70’s, he was a pioneer in every sense of the word.
The article covers Lawson’s background and views on technology, business, and socio-economics…..
Read More
2 notes
·
View notes
Photo







I hope everyone is enjoying the summer! Here are some pictures of the city that I've taken. If you've never visited Boston, I would encourage you to check it out. You won't be disappointed.
1 note
·
View note
Text
Malware Fighting Sticks to Go (Road Warrior)

I'm writing this post from my hotel room in Pittsburgh!

Just wanted to put together a list of what I carry on my USB sticks and the programs I'm likely to run at each phase of malware removal.
USB STICK #1
Phase 1:
ASWmbr
CatchMe
MBR
RKill
Phase 2:
Autoruns
PCHunter
RogueKiller
Rootkitremover
Phase 3:
AdwCleaner
ERARemover
ESETSirefefCleaner
HitmanPro
TdssKiller
D7
Phase 4:
ComboFix (use with expert)
GMER
Malwarebytes Chameleon
Phase 5:
Dependency Walker
PeStudio
ProcessExplorer
CrowdInspect
Phase 6:
Farbar Service Scanner
Phase 7:
OldTimer's Clean-It
Phase 8:
VirusTotalScanner Portable
USB STICK #2
Phase 9:
Kaspersky Rescue
USB STICK #3
Phase 10:
Dr.Web Live
USB STICK #4
Phase 11:
Windows Rescue CD (Used to fix any issues like MBR and missing files)
Lastly, if you are looking for some context behind why some of these tools are used please check out a post I put up a month ago: http://antoinesylvia.tumblr.com/post/51799576952/components-of-an-effective-malware-defense-strategy
0 notes
Text
The Curious Case of "Moneypak" Malware
The posts I put together last month which focused exclusively on tips to avoid malware, I ran by my cousin Kene. Kene is a graduate of Cornell, Author of "No Doesn't Always Mean No", and maintains a blog on real-world applications of Social Psychology.

Kene assured me that he would apply the tips provided in my malware prevention guides on his home computer. Kene apparently didn't get the memo to ALWAYS sandbox your browser. Yes, there are several layers of a sound security strategy (as I've stated in my previous posts) but sandboxing is a must!
Back to Kene, I rarely get phone calls from my cousin since his preferred method of communication is texting whether it's on Google Talk or on the phone. Sunday morning I rolled out of bed, looked at my phone and saw I missed a call from Kene but he left a voice-mail. I knew something was immediately wrong by the tone of his voice and the abrupt ending to the message he left, kind of reminded me when my cousin Andre left me a message about his laptop being stolen in Cape Verde.
Concerned for my cousin, I gave him a call instantly. Phone rings for a bit, then Kene picks up and says something along the lines "the computer is infected, they got us."
Me: What happened?
Kene: I don't know, I turned on the computer this morning and was greeted by a screen that locked out my desktop demanding payment.
Me: Sounds like you have a classic case of Ransomware, can you walk me though how you got this malware on your system. How could this occur, I told you to sandbox your browser!?
Kene: I have a feeling my brother is responsible for this, it was working until he used the computer.

Long story short, Kene had to re-install his OS. Kene actually made a bootable USB stick which cleaned his system but Kene still popped in his Vista CD for fresh install. We didn't get to use my malware fighting toolkit which I carry on my keychain. Kudos to Kene for fixing his computer.
Sylvia on Security Advice:
1. Run browser in a sandbox. Chrome has a built-in Sandbox which I like to wrap up with Sandboxie as well.
2.TURN OFF THE JAVA BROWSER PLUGIN!!!
3.Grab useful plugins like Adblock Plus and a script blocking plugin.
4. Keep flash updated.
5. Outside of the sandbox run these on startup: Avast (auto sandbox feature), Malwarebytes Anti-Exploit (protects vulnerable apps), WinPatrol, USB Autorun Eater, and the EMET tool by Microsoft.
6. You can add some entries to your hosts file for additional protection, and/or use DNS level security, NortonDNS which filters rogue websites.
7. Inspect your firewall and check out Peerblock.
8. Dump Adobe Reader, try Sumantra.
9. Be careful with MS Office documents!
Sandboxie works on all apps, Sandbox anything you don't trust. Trustworthy people can have their accounts compromised, so keep your guard up. Legit websites can be compromised as well! Follow steps 1 through 9.
The visual:
Did you get all of that?

0 notes
Text
My cousin Kene Erike (Blogger - Author) wrote a nice piece on the importance of backing up your data onsite and offsite (3rd party or even another place that you have access to). If that still worries you & you're housing critical data that you don't always need access to immediately, encrypt it with AES then have the hdd/sdd stored in your personal box down at the bank. I would also suggest checking out FreeNas and enable ZFS (self healing file system) for your local content. If you have no idea what ZFS is then check out these videos: http://youtu.be/0Ug1qCXvZDg?t=27m55s and http://www.youtube.com/watch?v=hxOVgUTxniw
Safeguard Your Assets: Create Backups

In a society where information capital is increasingly important, intelligent use of technology is a must.
Those with specialized knowledge and quick access to resources wield an advantage over the population at large.
You’d never store your cash in a box under your mattress (hopefully); that’s what banks are for.
Treat intangible assets with the same care.
Read More
5 notes
·
View notes


