Photo
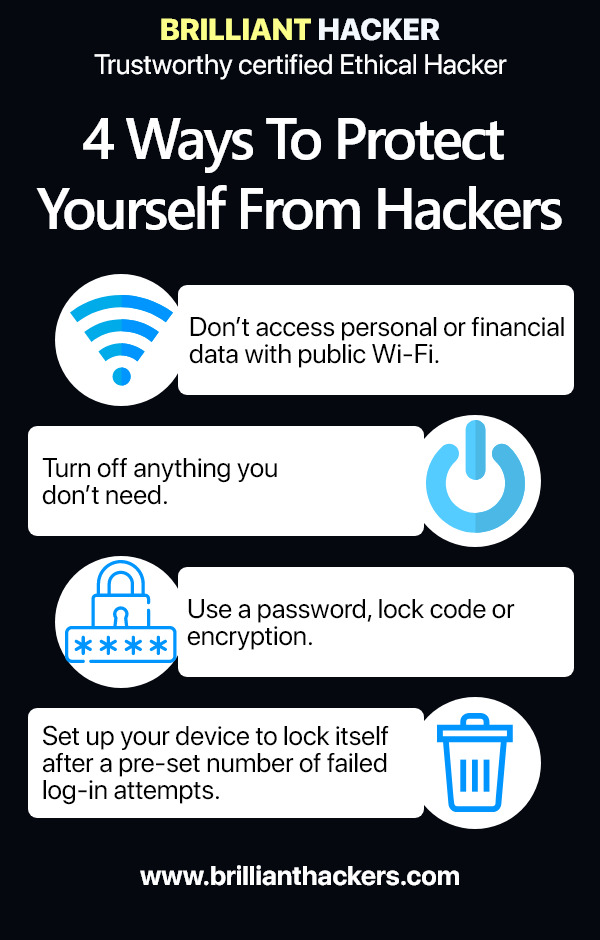
Where was the last public place you used Wi-Fi? These days, nearly every library, airport and hotel offer a way to access the internet from your cell phone or other mobile device. That means the information you have on your phone could be available to hackers in the area – unless you’ve taken steps to protect your data.
Follow these steps to stay protect and follow Zero Trust model.
2 notes
·
View notes
Photo

Get Email hacking services at your door step
Hire a hacker
0 notes
Link
Have you ever wondered how hackers obtain email passwords? You may have questioned how to hack email accounts at some time only to save your account from being hacked. There are various methods for gaining access to an email account's password. No email account is impenetrable to hackers. Here are some useful methods for hacking email accounts.
0 notes
Link
0 notes
Link
The kit can discover “when and where a vehicle’s lights are turned on, and which doors are opened and closed at specific locations.”
0 notes
Link
check your spouse if he/she is being loyal to you or nor
0 notes
Link
The more an attacker learns about critical people in a company, the more focused and successful their assaults may be. Educating employees on how to preserve their privacy should thus be a key component of any security awareness program.
0 notes
Photo

Professional hackers are still available to assist you at any moment. We are an escrow-based online hacker for hire service that provides skilled hackers for hire. Brilliant hackers, as the world's leading Ethical Hacker for Hire firm, has the finest Hacker for Hire services. We have a knowledgeable Global team where you can approach a hacker who is an expert in a specific area.
0 notes
Text
YOUR CAR IS SPYING ON YOU, AND A CBP CONTRACT SHOWS THE RISKS
A “vehicle forensics kit” can reveal where you’ve driven, what doors you opened, and who your friends are.
0 notes
Link
0 notes
Text
Why should businesses seek out white hat hackers to fix safety issues?

It's a topic that frustrates cybersecurity experts and necessitates increasingly inventive solutions. White hat hackers are one alternative that has grown in popularity in recent years.
White hat hackers, also known as ‘ethical hackers,' are basically hackers that use their abilities for good, as compared to the nefarious uses for which ‘black hat hackers' are known.
Bringing in someone from outside who isn't familiar with a company's technology will always be beneficial because they'll bring a fresh set of eyes and a new technical perspective to the table, regardless of how powerful a cybersecurity team a company has.
The spike of white hat hackers working with businesses, according to CEO of the Brilliant Hackers, can be attributed to changes in awareness.
“Hackers were all ‘bad boys' 20 years ago, and now the times have caught up... “Companies are waking up to the fact that [hackers] can help them,”
Not to mention that looking for independent actors can be a perfect way to expand your talent pool.
“I have a number of participants who work in cybersecurity. From a talent standpoint, there is a growing need for people with this skill set,” Brilliant Hackers says
“Frequently, the best hackers do not want to work for a bank. They have a touch of a rogue, independent, "do it on my own" attitude. As a result, the people who are very skilled at [hacking] do not want to serve with an internal team.”
“Some businesses can issue what is known as a ‘bug bounty,' where they do not actually contract specifically with someone in this space but say, ‘Hey, if you find bugs and you are able to hack into our system, here is the procedure to report those to us,'” We says.
“Another is totally uninvited, but you have people working on defense analysis. They may be researchers who find a security flaw and want to contact the organization to inform them about it.
“That's where you might see certain stuff go a little off the track a little bit because it's not called for and the company doesn't have any protocols or policies in place to deal with it.”
We says, is that some of these transactions lack the requisite legal safeguards and formalization. It's not always the case – companies often hire hackers and have all the necessary NDAs, deals, and other crucial paperwork in place to ensure things run smoothly – but individuals working against company processes are often operating in a liminal environment.
“I believe where the gray line begins to appear is where someone seeks to reveal flaws without the company's approval or overt or implied consent.”
How should they reveal?
White hat hackers who find a flaw, whether specifically commissioned or not, would almost certainly want to notify the appropriate parties, but how can it really happen in the sense of an often murky process?
“This is where businesses will get nervous. If the hacker receives the disclosure and does not receive a response from the organization, they will make the information public.”
We point out that hackers who do not receive a response can find themselves in a difficult situation. If the company processes a lot of confidential data, users will continue to be vulnerable to cyberattacks for as long as the vulnerability exists. “Do you think it's your duty to make that public?” It is when the ethics get really hazy.”
We are concerned that the treatment of hackers in these situations is not properly codified. How does a hacker decide when they will be paid handsomely or fined for their efforts?
People are concerned that the treatment of hackers in these situations is not properly codified. How does a hacker decide when they will be paid handsomely or fined for their efforts?
Brilliant hackers provides Certified hackers who are here to help society grow and become secure from other bad hackers. Hire a hacker for your business.
#hackers for hire#hire a hacker#hire hacker#hacker for hire#rent a hacker#i need a hacker#computer hackers for hire#phone hackers for hire#professional hackers#hiring hacker
0 notes
Photo

Professional Hackers always ready to serve you any time. We are an USA based online hackers for hire offering professional hackers for hire. As a leading Ethical Hacker for Hire agency in the world, Brilliant hackers offer best Hacker for Hire services. Our hackers are hired online by conducting numerous level live tests; once they prove themselves, they can join our special team.
0 notes
Photo

66% of small business depend on the internet for day to day operations. 72% of the known hacker breaches in 2011 affected business with 100 employees or less. 50% of small business think they are too small to be a hacker target. Now
its’s 2021 hackers have been far more advance and elite.
Protect your business with Hire a hacker Service
0 notes
Link
0 notes
Link

0 notes