#iptables
Text
Konfigurasi IPTABLES Untuk Mencegah Serangan LOIC
Low Orbit Ion Canon (LOIC) adalah perangkat lunak yang dikembangkan oleh individu atau kelompok yang tidak dikenal. LOIC adalah alat serangan penolakan layanan (DoS) yang dirancang untuk mengirimkan lalu lintas dalam jumlah besar ke situs web atau layanan online dengan tujuan mengganggu ketersediaan situs web. Meskipun LOIC dapat digunakan untuk pengujian penetrasi atau pengujian ketersediaan…
View On WordPress
#DDoS LOIC#iptables#iptables mencegah serangan loic#Konfigurasi IPTABLES Untuk Mencegah Serangan LOIC#loic#mencegah serangan loic#Script iptables
0 notes
Text
Linux Mint jako router dla sieci LAN: Konfiguracja masquerade

Linux Mint to popularny system operacyjny oparty na Linuxie, który można wykorzystać do stworzenia własnego routera dla sieci LAN. Jedną z ważnych funkcji, które umożliwiają to zadanie, jest masquerade. W tym artykule pokażemy Ci, jak skonfigurować masquerade w Linux Mint, aby użyć go jako routera dla Twojej sieci LAN.
Read the full article
#adresIProutera#adresacjasieciowa#DostępdoInternetu#dostępdoInternetuwsieciLAN#interfejsysieciowe#iptables#konfiguracjaadresówDNS#konfiguracjaadresówIP#konfiguracjaadresówIPstatycznych#konfiguracjabezpieczeństwasieciowego#konfiguracjaDHCP#konfiguracjafiltrowaniaadresówMAC#konfiguracjainterfejsówsieciowych#konfiguracjainterfejsuLAN#konfiguracjainterfejsuWAN#konfiguracjaiptables#konfiguracjamasquerade#konfiguracjamasqueradekrokpokroku#konfiguracjamasqueradewLinuxMint#konfiguracjaNAT#konfiguracjaoprogramowaniaroutera#konfiguracjaprzekazywaniapakietów#konfiguracjaprzepływuruchu#konfiguracjaregułiptables#konfiguracjaroutera#konfiguracjarouteradlamałejfirmy#konfiguracjarouteradlasiecidomowej#konfiguracjaruchusieciowego#konfiguracjaserweraDHCP#konfiguracjasieciLANwLinuxMint
0 notes
Text
Como permitir conexão de uma porta no Ubuntu 22
Algumas distribuições de Linux utilizam o firewal UFW (chamado de firewall descomplicado, Uncomplicated Firewall) que é basicamente uma interface para o iptables.
Quando ele está ativo na sua distribuição, ele bloqueia praticamente tudo.
Para sabermos se está ativo, basta digitar o comando
$ ufw status
Possíveis respostas do UFW
Status: active
Quando o firewall está ativo, em seguida temos…

View On WordPress
0 notes
Text
Configurer iptables pour HomeKit avec HomeAssistant
Lorsque j'ai voulu configurer mon pare-feu sur ma machine faisant tourner HomeAssistant, j'ai rencontré quelques difficultés à faire fonctionner le plugin HomeKit : mon iPhone ne parvenait pas à se connecter au bridge HomeKit. Après avoir utilisé tcpdump pour analyser le trafic entre HomeAssistant et mon iPhone, j'ai trouvé la solution pour bien autoriser le trafic.
La voici :
iptables -A INPUT -p tcp --dport 21064 -s 192.168.1.0/24 -j ACCEPT
iptables -A INPUT -p udp -m multiport --dports 5353 -s 192.168.1.0/24 -j ACCEPT
> La première règle autorise les connexions au port HomeKit de HomeAssistant sur mon réseau local 192.168.1.0/24. Votre port pourrait être différent, voir votre config, par défaut 21063 ou 21064 : voir la documentation d'HomeAssistant sur le sujet.
> La seconde règle autorise mdns sur mon réseau local 192.168.1.0/24.
0 notes
Text
iptables Installation Instructions for Linux Mint 21

Iptables, a robust Linux firewall tool, helps you set rules to safeguard your system. It manages all network traffic. Iptables firewall tables offer numerous built-in chains for incoming and outgoing connections. Each chain has a collection of rules that you may customise on your system.
iptables installation for Linux Mint 21
The procedures listed below should be followed to install iptables on Linux Min 21:
https://www.markaicode.com/iptables-installation-instructions-for-linux-mint-21/
0 notes
Link
Der Sicherheitsforscher Aaron Adams hat einen Use-after-free-Bug im Linux-Kernel gefunden, aufgrund dessen lokale Nutzer sich zum Superuser machen könnten. Der Fehler betrifft die standardmäßig auf den meisten Linux-Systemen aktive Kernel-Komponente NFTables – eine Weiterentwicklung der Linux-eigenen Firewall iptables.
0 notes
Text
My Linux firewall be like ...

Also check: Linux iptables command examples for new sysadmins
33 notes
·
View notes
Text
check iptables ubuntu
$ sudo iptables -L -v
View On WordPress
0 notes
Link
IPtables là gì? Toàn tập kiến thức cần biết về IPtables
IPtables là một trong những thuật ngữ được nghe nhiều nhưng để có sự am hiểu chi tiết không phải ai cũng làm được. Bởi vì thuật ngữ này chuyên về mảng công nghệ thông tin và chỉ người trong ngành mới có sự am hiểu nhất định. Vậy nếu bạn nào muốn nắm rõ về IPtables thì hãy tham khảo tất tần tật kiến thức được chia sẻ trong bài viết sau đây.
https://fptcloud.com/iptables/
0 notes
Text
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities.
I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down.
I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
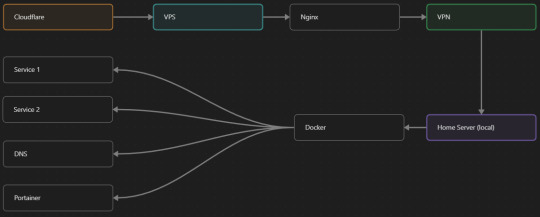
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging
This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic
This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB
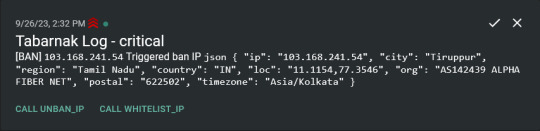
Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist
This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location.
I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database.
I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records.
Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning
For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist.
It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose).
I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity
As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this:
I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP.
Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests.
Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me.
All of this just because I refused to use sockets.
First successes and why I'm happy about this
After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again.
I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing.
Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this.
Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that.
Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?).
Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
8 notes
·
View notes
Text
netstat -na | grep :194
iptables -A INPUT -p tcp --dport 194 -j ACCEPT
sudo service iptables restart
[PORT 194 (Internet Relay Chat protocol) is now OPEN!]
Welcome to ask-the-substitute, an ask blog dedicated to exploring the Hologram Professor (The Substitute) from Puppet History, and what he gets up to after the s5 Puppet History finale.
This blog will likely contain spoilers for Puppet History up to the end of Season 5, and operates on the lore and information up to that point.
man modules
1: "Is It Really A Complex, Or Just Lacking Context?
Under #module Is_It_Really_A_Complex_Or_Just_Lacking_Context?
2: "When You Seek Vengeance, You Must Dig Two Graves"
Under #module When_You_Seek_Vengeance_You_Must_Dig_Two_Graves
3: "Lonely Wolf Keeps Friends As Lambs, Starves When They Are Gone"
Under #module Lonely_Wolf_Keeps_Friends_As_Lambs_Starves_When_They_Are_Gone
4: "Pressure Bomb In A Goddamn Knife Fight"
Under #module Pressure_Bomb_In_A_Goddamn_Knife_Fight
5 (CURRENT): "Try, Fall, Try, Fall, Try, Fall, Try Again"
Under #module Try_Fall_Try_Fall_Try_Fall_Try_Again
cat /etc/passwd
moth:x:0:0:moth:/moth:/bin/bash
Main is @moth-yknowtheartist. OOC posts from me will be tagged under #ls /moth .
substitute:x:1000:1000:substitute:/substitute:/bin/bash
art:x:1:1:art:/art:/bin/bash
Tag for art relating to the blog that isn't part of the modules!! These will be tagged under #ls /art.
Most posts will be in character for The Substitute. These posts will be tagged under #ls /substitute .
plaguerat:x:1001:1001:plaguerat:/plaguerat:/bin/bash
Posts featuring the Plague Rat will be tagged under #ls /plaguerat .
beefboy:x:1002:1002:beefboy:/beefboy:/bin/bash
Posts featuring Ryan Bergara (Beef Boy) will be tagged under #ls /beefboy .
professor:x:1003:1003:professor:/professor:/bin/bash
Posts featuring The Professor will be tagged under #ls /professor .
dinosir:x:1004:1004:dinosir:/dinosir:/bin/bash
Posts featuring the Pterosaur puppet (Dinosir) will be tagged under #ls /dinosir .
dinosara:x:1005:1005:dinosara:/dinosara:/bin/bash
Posts featuring the Tyrannosaur puppet (Dinosara) will be tagged under #ls /dinosara .
cat /home/trmsofsrvice.txt
The story for this blog will be fueled primarily by progression from asks. Because of the audience interaction, this blog will have the following ground rules:
I can and will ignore/delete any asks if I feel they've broken the following rules or if I don't feel they help tell the story I'm hoping to tell. Please don't feel too bad if your ask doesn't get used.
Certain actions will not be possible for asks- such as physical interaction with the environment or characters. Asks trying to perform actions like this will probably be ignored.
Your username may be recognized by characters if it appears often in asks, but generally you won't be considered an additional character.
Don't be weird (in a gross way)- ie sexual content and similar.
If an ask you send in isn't answered the first time for a really long time, feel free to resend it as it may not have come through properly. However, please don't send the same ask over and over and over after this if it still isn't used- if I'm not using it, I'm probably either saving it for later or I'm not planning on using it.
Feel free to message me if you have any questions, but just know I'll be answering DMs out of character.
have fun! :]
31 notes
·
View notes
Text
Menolak Akses IP Address Tertentu Pada Proctocol SSH Menggunakan Firewall IPTABLES
--------------------- On IPtables Firewall ---------------------
# iptables -I INPUT -s 192.168.1.100 -p tcp --dport ssh -j REJECT
# iptables -I INPUT -s 192.168.1.0/24 -p tcp --dport ssh -j REJECT
Untuk menerapkan aturan baru, Anda perlu menggunakan perintah berikut.
# service iptables save [On IPtables Firewall]
View On WordPress
0 notes
Note
I could type faster than you.
*could* vs *can*
….. I don’t doubt that,
But I’m sure I could write better iptables than you 😜
5 notes
·
View notes
Text
ORACLE APEX LINUX

Oracle APEX on Linux: A Powerful Combination for Rapid Web Development
Oracle Application Express (APEX) is a low-code development framework that delivers a fast and efficient way to build scalable, secure, and visually appealing web applications. Its seamless integration with Linux operating systems makes it a fantastic choice for developers who favor the stability, flexibility, and cost-effectiveness of Linux as a deployment platform.
Critical Advantages of Running Oracle APEX on Linux
Open-Source Affinity: APEX and Linux have a natural synergy within the open-source ecosystem. There are typically no licensing costs involved, making it a budget-friendly solution.
Robustness: Linux distributions are renowned for their reliability, making them the bedrock of many mission-critical systems. APEX inherits this stability.
Security: Linux employs rigorous security mechanisms and frequent updates – hardening your APEX installation against potential threats.
Customization and Scalability: Linux gives you unparalleled control for tailoring the system to your project’s exact needs. APEX applications can fluidly scale alongside your Linux environment.
Essential Considerations
Firewall: Properly configure your Linux firewall (e.g., iptables or firewalls) to permit traffic to your APEX applications.
Web Server: While APEX has a built-in web listener, production environments often use a robust web server like Apache or Nginx for added performance and security.
Backup Strategy: Implement a meticulous backup plan for your Oracle Database and APEX applications to safeguard your data.
Maximizing Your Oracle APEX on Linux Experience
Embrace the Community: Linux and APEX boast vibrant online communities for troubleshooting and finding innovative solutions.
Consider Performance Tuning: As your applications grow, delve into Linux performance optimization and APEX best practices for a consistently smooth user experience.
Leverage Linux Tools: Linux offers a wealth of command-line utilities and monitoring tools to streamline APEX development and management.
The Power of Choice
Using Oracle APEX on Linux unlocks the power of low-code development on a dependable and customizable platform. Whether deploying internal enterprise applications or building web solutions for clients, the APEX-Linux combination gives you the flexibility and tools you need to deliver outstanding results.
youtube
You can find more information about Oracle Apex in this Oracle Apex Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for Oracle Apex Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Oracle Apex here – Oarcle Apex Blogs
You can check out our Best In Class Oracle Apex Details here – Oracle Apex Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
0 notes
Text
do i need a vpn if i have linux
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn if i have linux
VPN benefits for Linux
Linux users can benefit greatly from using a Virtual Private Network (VPN) for enhanced online privacy, security, and access to geo-restricted content. VPNs create a secure connection between the user's device and the internet, encrypting all data transferred. This encryption helps in preventing unauthorized access to sensitive information, protecting users from cyber threats such as hacking and identity theft.
One of the main advantages of using a VPN on Linux is the ability to bypass geo-restrictions. By connecting to servers located in different countries, users can access region-locked content on streaming platforms or websites. This is particularly useful for Linux users who want to watch their favorite shows or access websites that are not available in their location.
Moreover, VPNs help in masking the user's IP address, making it difficult for third parties to track their online activities. This adds an extra layer of anonymity and privacy while browsing the internet. Linux users can also utilize VPNs to securely connect to public Wi-Fi networks, protecting their data from potential cyber attacks on unsecured networks.
In addition, VPNs can improve browsing speeds and reduce latency by directing traffic through optimized servers. This can be beneficial for Linux users who engage in online gaming or stream high-definition content. Overall, using a VPN on Linux offers a range of benefits that enhance the user's online experience while prioritizing security and privacy.
Security measures on Linux
Title: Strengthening Your Defense: Essential Security Measures on Linux
Linux, renowned for its robust security features, remains a preferred choice for users seeking a reliable and secure operating system. However, maintaining a secure Linux environment requires diligence and adherence to essential security measures.
First and foremost, regular updates are imperative. Keeping your Linux distribution up-to-date ensures that you receive the latest security patches and fixes for vulnerabilities. Most distributions offer automated update mechanisms, simplifying this crucial task.
Implementing strong authentication practices is equally vital. Utilize complex passwords and consider employing multi-factor authentication (MFA) for an added layer of security. Tools like SSH keys enhance security by replacing passwords with cryptographic keys for remote access.
Firewalls play a pivotal role in safeguarding Linux systems from unauthorized access. Configure firewalls, such as iptables or the more modern nftables, to regulate network traffic and block malicious connections. Additionally, consider employing intrusion detection and prevention systems (IDS/IPS) to proactively identify and thwart potential threats.
Regular system audits and monitoring are indispensable for detecting and addressing security breaches promptly. Utilize security auditing tools like AIDE or Lynis to assess system integrity and identify any deviations from the baseline.
Furthermore, encryption should be employed to protect sensitive data both at rest and in transit. Utilize tools like GNU Privacy Guard (GPG) for file encryption and protocols like TLS/SSL for securing network communications.
Limiting user privileges and employing access controls are crucial for minimizing the impact of potential security breaches. Utilize the principle of least privilege to restrict user access to only what is necessary for their tasks.
Lastly, maintaining comprehensive backups ensures the resilience of your Linux environment in the face of unforeseen events such as data corruption or ransomware attacks.
By adhering to these essential security measures, you can fortify your Linux system against potential threats and enjoy a secure computing experience.
VPN necessity for Linux users
For Linux users, employing a VPN (Virtual Private Network) is not just a luxury but a crucial necessity. While Linux is renowned for its robust security features, it's not immune to online threats, privacy breaches, and data surveillance. Here are compelling reasons why Linux users should prioritize using a VPN:
Enhanced Privacy: VPNs encrypt internet traffic, shielding it from prying eyes. Linux users often value privacy and freedom, and a VPN ensures their online activities remain confidential.
Bypassing Restrictions: Many websites and services impose geo-restrictions or censorship based on users' locations. By connecting to a VPN server in a different location, Linux users can bypass these restrictions and access content without limitations.
Securing Public Wi-Fi: Public Wi-Fi networks are notorious for their lack of security. Linux users can mitigate the risks of data interception and hacking by using a VPN to encrypt their connection, whether they're at a coffee shop, airport, or hotel.
Preventing ISP Tracking: Internet Service Providers (ISPs) often monitor users' online activities and may throttle bandwidth or sell browsing data to advertisers. With a VPN, Linux users can prevent ISPs from tracking their behavior and maintain anonymity online.
Protecting Against Cyber Threats: Linux systems are not immune to malware, phishing attacks, and other cyber threats. By encrypting internet traffic and masking their IP address, Linux users can reduce the risk of falling victim to such threats.
Secure Remote Access: Linux users who frequently access their systems remotely can benefit from VPNs, which provide a secure and encrypted connection to their home or office network from anywhere in the world.
In conclusion, VPNs offer Linux users a layer of security, privacy, and freedom that is essential in today's digital landscape. By utilizing a VPN, Linux enthusiasts can enjoy a safer and more private online experience.
Linux privacy protection
Linux is known for being a secure and privacy-conscious operating system, making it a top choice for users looking to protect their digital footprint. With its open-source nature and strong community support, Linux offers various tools and practices to enhance privacy protection.
One key aspect of ensuring privacy on Linux is utilizing encrypted communication protocols such as HTTPS and VPNs. These protocols encrypt data transmission, making it harder for potential attackers to intercept and decipher sensitive information. Additionally, Linux distributions often provide built-in tools like firewalls and intrusion detection systems that help safeguard against unauthorized access.
Users can also take advantage of privacy-focused web browsers like Firefox and Brave, which offer enhanced tracking protection and privacy settings. These browsers allow users to block cookies, prevent fingerprinting, and control access to location data, helping to maintain anonymity while browsing the web.
Furthermore, Linux users can benefit from utilizing secure password managers and enabling two-factor authentication for added account security. By regularly updating system software and implementing strong password policies, users can further protect their privacy and data integrity on Linux.
In conclusion, Linux offers a robust platform for privacy protection through its security features, open-source ecosystem, and community-driven development. By leveraging encryption protocols, privacy-focused browsers, and best security practices, users can enhance their privacy and security posture while using Linux as their operating system.
Understanding VPN usage on Linux
Understanding VPN Usage on Linux
Virtual Private Networks (VPNs) play a crucial role in safeguarding online privacy and security, especially on Linux systems. Linux users benefit from a wide range of VPN options, offering various features and functionalities to suit different needs.
One primary use of VPNs on Linux is to encrypt internet traffic, ensuring that data transmitted over networks remains secure and inaccessible to unauthorized parties. This encryption is particularly essential when connecting to public Wi-Fi networks, where data interception is a significant concern.
Moreover, VPNs enable users to bypass geographical restrictions and access content that may be restricted in their region. By connecting to VPN servers located in different countries, Linux users can enjoy unrestricted access to websites, streaming services, and online platforms that might otherwise be unavailable to them.
Setting up and using VPNs on Linux typically involves installing VPN client software or configuring network settings manually. Many VPN providers offer dedicated Linux apps, simplifying the setup process and providing an intuitive interface for managing VPN connections.
OpenVPN is a popular choice for VPN protocols on Linux due to its open-source nature and robust security features. Additionally, IKEv2/IPsec and WireGuard are gaining popularity for their efficiency and performance benefits.
While VPNs offer numerous benefits, it's essential to choose a reputable VPN provider that prioritizes user privacy and does not log sensitive information. Additionally, users should regularly update their VPN software to patch any security vulnerabilities and ensure optimal performance.
In conclusion, VPNs are invaluable tools for enhancing privacy, security, and online freedom on Linux systems. By understanding how VPNs work and selecting the right solution, Linux users can enjoy a safer and more unrestricted online experience.
0 notes