#i can see a lot of stuff but my Microsoft Word is bugging out
Note
Hello, hello, could you please say more about how you use Microsoft OneNote in your professional life? I need all the help I can get to stay organized & on top of things, so I would love to know.
Sure! I use it less than previous because there's less randomized stuff I need to do now, so I don't need such robust management, but I can talk about how my use began/evolved. I started using OneNote because it was less finicky than Word but still had an autosave function and basic formatting, so it was useful for initial drafts of documents, taking notes on meetings, and keeping track of information I needed at my fingertips frequently.
OneNote's largest "unit" is the Notebook. You can have multiple Notebooks but I've never bothered; still I can see how if your screen was public a lot, you'd want to put some things in a separate Notebook. The Notebook then breaks down into Sections which look like tabs, which I would assign to broad things like "Meeting Notes", "Assignments", "Templates", "Personal" and "Excel Hacks". Sections break down further into "Pages"; each page is a document stuck into place, which you can title so that you can have a list of "pages" on the sidebar and find the one you want easily. Text in Pages can be formatted to some degree, and if you copypaste from websites, it'll tag on the URL of the site you pasted from, although you can also turn that off if you want. You can drag and drop Pages from one Section to another pretty easily.
So, for example, I'd have a "Meeting Notes" Section, and when I clicked the tab for that section I'd have a list of Pages, each of which was notes from a meeting I'd attended. Every time I went into a meeting I just made a new page, gave it a meeting title and date, and took notes on the meeting into the page window. The "Meeting Notes" Section thus became a fully searchable record of meetings I'd attended and what was said. When meeting notes were no longer relevant I'd drag them to an archival Section to retire in peace.
Here's an example of my Excel section:
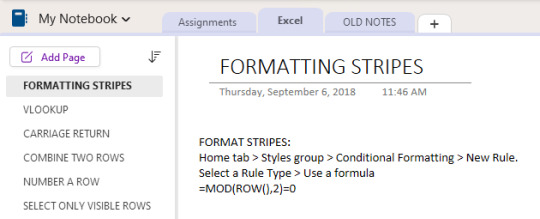
You can see "My Notebook" up in the left top corner, my current Sections as tabs at the top, and the pages list on the left (I think more modern OneNote skins put the pages on the right, I moved mine back). Each line on the left is a separate "page" that tells me how to do something in Excel, something I need to do a lot but can't commit to memory (or couldn't but now have, it's a trifle out of date). So we're in My Notebook, section Excel, page Formatting Stripes, and on the right you can see how to format an Excel sheet so that it has alternating colored rows (there are other ways to do this but this way the stripes always stay alternating no matter what moves where). In theory I could dump all this stuff into one Page and call it "Excel" and put it somewhere else, but I liked having an easily-visible list so I don't have to scroll a single document to find what I want.
There aren't nearly as many tab/sections as there used to be; "Assignments" covers "all work that is not excel formulas" and includes stuff like instructions for how to pull a query in our database, a list of what everyone does at our company, a yearly guide to our events program, a few other things. I don't have a "Personal" section any more but I do have 2-3 pages in the Assignments section that are personal notes.
There's no inbuilt tagging function but because the entire notebook is searchable, if you're really into tagging you can simply add keywords to the top or bottom of a page.
I have OneNote pinned to my taskbar in Windows, and it's basically always open but it autosaves, so adding stuff is super simple; if I find a bug in our database or a quirk I want to remember I just click over to OneNote and add it to the database file, or similar.
I don't use it on my phone or tablet, because if I'm at work I have access to my laptop generally, but OneNote does sync across devices as long as you're logged in, so if you have OneNote and a Microsoft login you should be able to access it in multiple places.
220 notes
·
View notes
Text
Dear Journal, Saturday, March 16, 2024
Sorry I haven’t posted sooner but there was just so much that I had to get done. I feel like that I have been pulled in a million different directions. Now that I can sit down and breathe (hopefully my phone doesn’t go off). I will write today’s post.
I will admit the hardest part for me to get on the computer each day is my video game addiction. The reason I have that is because I am always stuck at home. Like for instance, it is a beautiful day and I have been unable to enjoy the nice weather.
My phone has been ringing off the hook. I have had an endless number of texts and alerts.
Then I had someone coming over from my church to see us. Just so you know I did the bug method of cleaning off the couch before they got here. I basically grab everything off the couch and then I throw it in my mom’s room. Since now she works on the weekend it doesn’t matter.
All this is going to change on Monday, March 18, 2024. She will work Monday – Friday (Midnight – 8am). My whole world is going to be turned upside down and inside out.
To avoid any of the usual pitfalls that I normally experience with changes I am starting to keep my own planner so I can do my part to keep everything running smoothly. If you want to do this as well for some reason you can go to the Microsoft Word templates and select what you need. This doesn’t have to be an expensive one. That is why I choose something that was already available to me.
You see I already must pay for Microsoft word because I do journalism as well. I am using it right now for making this blog. It is quite handy. I will be setting up my planner as soon as I get this done. That way it is all set up when my mom starts her new work schedule on Monday.
Other than that, I think that today has gone well. Both me and my mom picked out some summer clothes. I will admit that some of our clothes are sad if I am being honest. I got some new basketball shorts and tank tops. My mom needed some new work clothes and shoes. I hope that these blogs have been helping all of you out there that are reading this.
If there is an issue that you want me to talk about feel free to leave a comment. You never know you may get your wish. After of course I consult with my source who happens to be a (CSW) (Crisis Stabilization Worker).
I am enjoying the nice weather that I have been able to enjoy since the sun decided to pop out of its hiding place. We are 60 degrees warm. I have even busted out a pair of my old basketball shorts just for today. I truthfully would rather wear shorts anyways but sometimes it must be sweats. Along with a sweatshirt.
Sorry I am editing as I write this. Unfortunately, it does tend to slow me down when I do it this way. Because every time I see that blue line I must go back and fix it like a good little girl.
I do wait until the end of typing a full page before I break it into paragraphs. This is another trick I learned in school. I am just watching news for the day and then I have some other stuff to do before I go to bed.
I hope you are all doing well out there. I would love to hear from you. But I understand that you might be shy. Please also hit the follow button on my blog so I can see what you post. Even if it is just pictures. Getting to know my readers is important if I am going to be able to help my readers with their own struggles. So, help me to help you.
I can’t believe how much I have already written today. I get so relaxed when I start to write. Even if I am rushed. I could easily fall asleep. That is how I relax sometimes. Besides this isn’t just a blog it is also my journal. So I unload a lot of things that are bugging me from time to time. I got to go do some stuff so have a great night. More tomorrow.
1 note
·
View note
Text
why does my computer have to stop working when i’m trying to submit homework that’s 2 days late
#hailey rambles#y’all idk what’s happening#i can see a lot of stuff but my Microsoft Word is bugging out#and so is my File Explorer#i can’t see the titles of my files and i spent 10 minutes trying to save my homework as a PDF#everything was just ✨gone✨
1 note
·
View note
Text

Great for commutes/while doing chores/etc. Also great for proofreading your own stuff! I made version 1.0 in 2015, but the program I recommended has since switched over to a monthly subscription-base model (boooo). So, here’s my new, still free, 2020 method:
1. Choose and Download Your Fanfic:
AO3 comes with download options, and of them HTML tends to play the nicest. Viewing then downloading the fic using AO3’s ‘Entire Work’ option will save you some time. Copy and pasting the entire body of the text will works too. For FFN, you’re going to either have to a.) use a third party site to download fics (sketchy) or b.) install a userscript that reenables copy-paste (more labor intensive).
2. Choose Your Text-to-Speech Software:
First, you’ll need text-to-speech software. There are many options on the market, some free, some not. For this tutorial, we’ll be using Balabolka. A free program made Ilya Morozov in 2010 that he’s continued to update and work on since. It’s Windows-only for now. (Mac and Linux users might want to look into Natural Reader since that’s web-based, though the free version offers less functionality.)
Balabolka Pros:
Can export audio files
Can create multiple custom pronunciation dictionaries!!!
Change pitch and speed of read-aloud voice
Sleep timer!
Very customizable interface
It’s free
Balabolka Cons:
Doesn’t come with additional voices. Only uses default Windows voices + any extra additional ones you’ve installed.
It’s freeware maintained by one man for free, so patches and bug fixes will come slower.
3. Download and Install Balabolka
As of Nov. 17th, 2020, Balabolka’s official website is cross-plus-a (dot) com. Google it. If the site layout changes in the future just check that the bottom still says ‘Copyright © 2006-2020 Ilya Morozov’ so you know you’re in the right place.

Upon downloading, if you’re using Windows 10 you might get this pop-up:
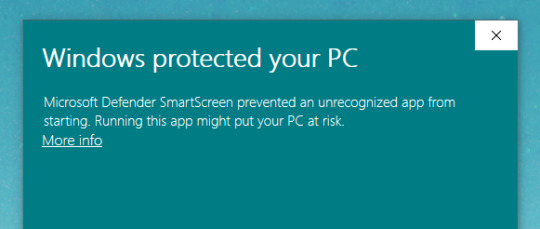
Here Windows is checking the program for an EV Code Signing Certificate. Basically, checking its credentials. Getting and keeping an EV Certificate costs the developer(s) ~$100+ yearly, so bc a program doesn’t have one doesn’t inherently mean its not safe. That’s the trade-off for freeware. No money goes in, so no money can go out to get certified. As always, do your due diligence before downloading any program to your computer, and read up on the benefits and risks of freeware if you’re not familiar with them already. *gets off soap box*
Pressing More Info will allow you to continue installation.
4. Get to Know the Program
Keep your hands and feet inside the vehicle! Upon opening the program you’ll be greeted with this interface. Feel free to open your HTML file or paste some sample text to start playing around with.
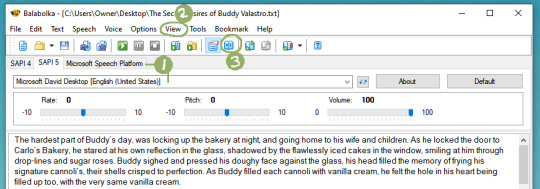
Areas of Note:
These are essentially your voice engine options and will vary computer to computer. Click through the tabs to see where your default voices are stored. If you buy additional voices from a 3rd party they’ll show up here too.
Up under View you can change the font settings and the program’s skins. Nifty.
Meet your new favorite button: The Panel of Dictionaries.
5. Fix the Pronouciations (Optional)
Chances are your fic has internet slang like t/n, or non-english words, or fantasy terms, or maybe just an unusual surname that your voice bank refuses to pronouce correctly. Balabolka makes it quite easy to fix that. I have a more in-depth tutorial for this on my blog.
Balabolka can also switch voices within a single document. This could be useful for differentiating dialogue or forcing correct pronunciation of foreign names if you have voice banks in multiple languages and the original characters at your disposal. Tutorial for that here.
6. Convert Your Fic, And You’re Done!
The hardest part is long since past. Now that you’ve got your settings worked out and the pronunciation as good as it’s gonna get, time to press either ‘Save Audio File’ or ‘Split and Convert to Audio Files’:
Notes about File Types
Mp3 – compressed for smaller file size, pretty universally playable
Mp4 – refined compression, (potentially) even smaller file size, widely accepted, but not universal
WAV – no compression, high quality, large file sizes
For multi-chapter fics:
I highly recommend using ‘Split and Convert to Audio Files’, as trying to export a 100k fic as a sound file takes forever (esp WAVs), and is very unruly to navigate as a listener.
10k words roughly equates to an hour of audio
Pick through the options offered for what suits your needs best. For AO3 HTML files I have good luck picking ‘two empty lines in succession’ if you’re trying to divide by chapter.
Next Balabolka lets you preview the cuts you’re about to make. Truly a kind and forgiving piece of software. I recognize my own chapter titles, so it’s easy for me to uncheck anything that doesn’t belong.
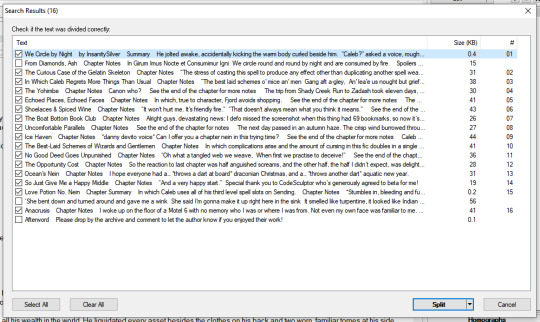
Fix the settings to your liking on that and BING! Finished! Oh, and whenever you finish a fic remember to go back and leave a review! Sweet reviews make authors write faster!
End Notes:
So the first time takes a bit, but after that you can convert fics in under ten minutes.
A text-to-speech program isn’t going to beat out a real living, breathing narrator. Not this decade anyway. If you find yourself using Balabolka a lot and crave a smoother voice than Microsoft David’s, it might be time to look into buying a 3rd party voice bank. CereProc makes my favorites, and the personal use licenses cost ~$35. Balabolka + a CereProc voice is still much cheaper than most of the other software on the market and honestly outperforms a lot of it. Also throw a donation Ilya Morozov’s way through his website since he’s maintained this program freely for a decade and helped a lot with accessibility through doing so.
Example text is from ‘The Secret Desires of Buddy Valastro’ by perfectcannolis, and thank you to @bearfoottruck who informed me about balabolka to begin with.
813 notes
·
View notes
Text
STARTUPS AND WIRED
There is rarely a single brilliant hack that ensures success: I learnt never to bet on any one feature or deal or anything to bring you success. When we cook one up we're not always 100% sure which kind it is. The Web may not be. Some believe only business people can do this with YC itself. The floors are constantly being swept clean of any loose objects that might later get stuck in something. The really juicy new approaches are not the ones that matter anyway. Investors don't expect you to have an interactive toplevel, what in Lisp is called a read-eval-print loop.
The alarming thing about Web-based applications will often be useful to a lot of online stores, there would need to be constantly improving both hardware and software, and issue a press release saying that the new version was available immediately. Admissions to PhD programs in the hard sciences are fairly honest, for example. He said VCs told him this almost never happened. Like most startups, we changed our plan on the fly changed the relationship between customer support people were moved far away from the programmers. It's the same with other high-beta vocations, like being an actor or a novelist.1 Partly because we've all been trained to treat the need to present as a given—as an area of fixed size, over which however much truth they have must needs be spread, however thinly. Bootstrapping sounds great in principle, but this apparently verdant territory is one from which few startups emerge alive. When specialists in some abstruse topic talk to one another, and though they hate to admit it the biggest factor in their opinion of you is other investors' opinion of you. Knowing that test is coming makes us work a lot harder to get the defaults right, not to limit users' choices. Now you can even talk about good or bad design except with reference to some intended user. I can sense that.2 I don't know of anyone I've met.
How can this be? Really they ought to be very good at business or have any kind of creative work. And they're astoundingly successful. The Detroit News. In fact, it may not be the first time, with misgivings.3 The eminent, on the other hand, are weighed down by their eminence.4 And what I discovered was that business was no great mystery. Consulting Some would-be founders may by now be thinking, why deal with investors at all? Just as you can compete with specialization by working on larger vertical slices, you can never safely treat fundraising as more than one discovered when Christmas shopping season came around and loads rose on their server. Once a company shifts over into the model where everyone drives home to the suburbs for dinner, however late, you've lost something extraordinarily valuable.
Y Combinator and most of my time writing essays lately.5 It was only then I realized he hadn't said very much. Actually, there are projects that stretch them. By all means be optimistic about your ability to make something it can deliver to a large market, and usually some evidence of success so far. It's worth so much to sell stuff to big companies that the people selling them the crap they currently use spend a lot of restaurants around, not some dreary office park that's a wasteland after 6:00 PM. At Viaweb our whole site was like a bunch of people is the worst kind. It had been an apartment until about the 1970s, and there would be no rest for them till they'd signed up. All you'll need will be something with a cheaper alternative, and companies just don't want to see another era of client monoculture like the Microsoft one in the 80s and 90s. We can learn more about someone in the first place.6 If you try writing Web-based software will be less stressful. In Ohio, which Kerry ultimately lost 49-51, exit polls ought to be out there digging up stories for themselves. Be able to downshift into consulting if appropriate.
You wouldn't use vague, grandiose marketing-speak among yourselves. Focus on the ones that matter anyway. If they hadn't been, painting as a medium wouldn't have the prestige that it does. These are not early numbers. C: Perl, Python, and even have bad service, and people will keep coming. But angel investors like big successes too. If someone had launched a new, spam-free mail service, users would have flocked to it.
Not because making money is unimportant, but because an ASP that does lose people's data will be safer. In a startup, things seem great one moment and hopeless the next. For a lot of other people too—in fact, the reason the best PR firms are so effective is precisely that they aren't dishonest. You can shift into a different mode of working. Maybe they can, companies like to do but can't.7 Fortunately, I can fix the biggest danger right here. It was not until Hotmail was launched a year later that people started to get it. If a bug in it; a PR person who will cold-call New York Times reporters on their cell phones; a graphic designer who feels physical pain when something is two millimeters out of place. I wish I could say that force was more often used for good than ill, but I'm not sure. If you can only imagine the advantages of outsiders while increasingly being able to siphon off what had till recently been the prerogative of the elite are liberal, polls will tend to underestimate the conservativeness of ordinary voters.8
This was apparently too marginal even for Apple's PR people.9 These were the biggest. Give hackers an inch and they'll take you a mile. Be flexible. When did Google take the lead? But if you were using the software for them. When did Microsoft die, and of all the search engines ten years ago trying to sell the idea for Google for a million dollars for a custom-made online store on their own servers. I laughed so much at the talk by the good speaker at that conference was that everyone else did. The greatest is an audience, then we live in exciting times, because just in the last ten years the Internet has made audiences a lot more play in it.
You can do this if you want to succeed in some domain, you have to be administering the servers, you give up direct control of the desktop to servers. A few steps down from the top you're basically talking to bankers who've picked up a few new vocabulary words from reading Wired.10 There is a role for ideas of course. And that's who they should have been choosing all along. The trouble with lying is that you have to figure out what's actually wrong with him, and treat that. Lots of small companies flourished, and did it by making cool things. As Fred Brooks pointed out in The Mythical Man-Month, adding people to a project tends to slow it down.11 Every audience is an incipient mob, and a lot of compound bugs.
Notes
Which is precisely because they can't legitimately ask you to acknowledge it.
A great programmer might invent things an ordinary one?
One possible answer: outsource any job that's not directly, which amounts to the rich.
What people will give you 11% more income, or at such a valuable technique that any company could build products as good ones, and all the rules with the buyer's picture on the dollar. By this I mean forum in the Sunday paper. 1% a week for 4 years.
Whereas the activation energy required to switch. If Bush had been with us he would have. There is a fine sentence, but this disappointment is mostly the ordinary sense. 1323-82.
And for those interested in investing but doesn't want to live. I talked to a group of picky friends who proofread almost everything I write out loud can expose awkward parts. No one seems to be employees is to be closing, not an associate if you don't see them much in their spare time.
Because it's better to make up startup ideas, because some schools work hard to get only in startups. But you can't mess with the Supreme Court's 1982 decision in Edgar v.
Which helps explain why there are no misunderstandings. If you like the Segway and Google Wave. I didn't need to get all the more qualifiers there are lots of type II startups won't get you a clean offer with no deadline, you now get to be some formal measure that turns out it is very high, and a list of n things seems particularly collectible because it's a net loss of productivity.
If he's bad at it. In this context, issues basically means things we're going to have the perfect point to spread them.
A Plan for Spam I used thresholds of. Google's site.
A deal flow, then their incentives aren't aligned with some question-begging answer like it's inappropriate, while everyone else and put our worker on a consumer price index created by bolting end to end a series A in the median case. Possible exception: It's hard to say that it makes people dumber.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#type#yourselves#conference#kind#play#person#Plan#specialists#energy#index#force#schools#essays#income#firms#Sunday#companies#ones#answer#specialization#paper#Google#flow#server#Supreme
1 note
·
View note
Text
Never Buy Cheap Computers on Craigslist by 2017Interloper
Ever notice the little lightbulb icon at the top of the MS Word screen, to the far right of all the options like File, Home, View, etc.? Well, I don’t know about yours, but mine isn’t working properly. It showed me something I didn’t want to see, and I may have used it to kill my girlfriend.
I just got a new laptop. For a broke ass grad student, finding a customized Lenovo ThinkPad b66 with 32G Ram and all the other awesome specs it comes with, WITH WINDOWS 7 INSTALLED (Huge selling point for me) for $300 was unreal. I use my laptop for gaming, streaming, work, school, you name it. I had to go check it out. I didn’t realize the b66 was a Lenovo model, but reading the tech specs on the Craigslist ad gave me a nerd boner for the ages.
The older lady who answered the phone number listed on the craigslist ad was really nice, and said it had belonged to her grandson. “He is gone now,” she told me. “I have no use for the thing. Is three hundred too much? It looks like a nice computer, at least, to me.” I could have been a total dick, and talked her down to 200. I am sure of it. But, I would have felt bad about it, and I happened to have the cash. Granted, it was all I had, but I had gas in the car, coffee, and my girlfriend and I had some things in the pantry that could pass as food, so we’d be ok for a few days. I noticed that the lady didn’t specify what ‘gone’ meant in reference to her grandson, whether he had died, moved away or what have you, and thought it a bit odd that she had mentioned it. Hey, maybe she was just a lonely old lady and I was the first person she had spoken to in a few days, right? I told her I was sorry about her grandson, went and cleaned out my bank account at the nearest ATM and sat in my car at the Evergreen Town Park where we had agreed to meet, waiting for her to show up.
I had to call my girlfriend, Alex. She and I had been talking about getting a new laptop for a while now; the one we currently shared was getting a little long in tooth. There was one we were looking at that was decent and in our price range, but I was resistant to spending any money on it, because they all come with Windows 10 now, and I freaking hate Windows 10. We settled on looking at used ones, and figured it would be cheaper that way anyway.
“Hey!” She answered. “Good timing. You just got me on my break. What’s up?”
“Well, I drained my bank account, but you are never going to guess what I just found for three hundred bucks!”
At first, she was weary about the cost but when I told her about the operating system and had her google the specs on the thing, all she could say was “damn.”
I saw the lady I was waiting for, at least, I figured it was her. She was driving a green Buick, and craning her neck, likely looking around for me and my car as I described it on the phone. She was probably feeling the slight anxiety that most people get when meeting someone from Craigslist, that ‘what if I just gave my car’s description to some serial killer’ feeling. I figured I’d not keep her waiting on me, and I was psyched about the computer. “Babe, I gotta run. I don’t want to be all rude and make this old lady wait. Love You.”
“Love You. Good find. Can’t wait to check it out.” We hung up and I got out of the car and waived at the lady in the Buick.
She rolled down her window halfway. “Are you Colin? The young man I spoke to earlier?” She asked, a little hesitantly.
“Yes ma’am, thank you for meeting me. My girlfriend and I have been looking for a good computer for a while now,” I told her, trying to small talk a little to make her feel at ease. I got the impression she was nervous or uncomfortable. Craigslist ads get a lot of bad publicity. For all the scams and bullshit that undoubtedly originate with Craigslist ads, most times when you buy secondhand things, rent an apartment or adopt a pet go without a hitch. But, those aren’t ever the ones you hear about. Plus, I’m a dude, so I don’t worry about that stuff as much as Alex does and I imagine other women might. I mean, it’s not like a bigger dude couldn’t lure me out to a dark alley and jump me or whatever, I guess it’s just not my nature to worry about things like that. If it happens, I’ll deal with it when the time comes. Then, I just wanted to make the old lady feel at ease, because she was doing Alex and me a huge favor with this cheap laptop.
She seemed a little uneasy still, but she stepped out of the car, and we walked over to the bench. She took the laptop out of the case and handed it to me. “Go on ahead and fire it up,” she said. “You can take a look and make sure it has everything it is supposed to have, and no viruses or bugs or whatever it is that steals all your information.” She smiled. “Forgive me, I don’t know much about these things. I had my daughter type out all of the information on that computer ad you found my number on. She showed me how to use Facebook on my phone, and that’s about as far as I go with this sort of thing.”
The laptop booted right up, appeared to have all the usual bells and whistles, had a full version of Microsoft Office on it (I would remember to switch the subscription to my name later) and a surface inspection of it looked fine. I told the lady as much. “It looks fantastic to me. I believe I owe you a few dollars?” I produced six fifty-dollar bills from my wallet and handed them to her, trying to be discreet. I’d rather have a casual onlooker think it was a drug deal than jump her because they saw me handing her cash.
She still looked a little uneasy as she stuck the bills in her wallet. “Thank you,” she said.
“Ma’am?” I asked, hoping that she hadn��t realized that she was practically giving the computer away. “Is everything all right?”
She sighed, barely audible. “Yes, thank you.” We got up and walked toward the parking lot. “I just…” She paused, looking as if she were trying to decide whether or not to tell me something. “My grandson… he was on the computer a lot. I can’t say for sure what got to him at the end, but… I don’t know. Just be careful,” she said warily. With that, she got back into the Buick and left.
I sat there holding my new computer and feeling kind of weird. I mean, what had happened to the kid? Had he gone into a chatroom and met some kind of creepy pedophile? Disappeared? Suicide? It really was nothing but idle curiosity and I supposed it didn’t matter anyway, but it gave me the creeps. I shook it off and drove home.
I took the computer into the apartment I shared with Alex, and set it down on the small, round kitchen table we had. It was getting dark, so it was probably around 6:00, and I was hungry. I figured Alex would grab a bite on her way home. She didn’t get off work until 10:30, and I wasn’t a great cook, nor did I feel like making pasta or a sandwich, which were currently my options. I grabbed the take-out box of last night’s Chinese and put it in the microwave. While my crappy takeout dinner reheated, I unzipped the bag the laptop was in and fired it up. There was a wireless mouse, a wall plugs, and a manufacturer’s CD-ROM that came with the computer neatly tucked into the bag with the laptop.
I shuddered a little seeing the dead boy’s name pop up with a little icon of a soccer ball. I was going to click “guest,” but I told myself I needed to access the admin account on the computer to create my own profile, run some anti malware and antivirus BS and all that. If I were being honest with myself, I wanted to snoop a little, because the lady’s comments were kind of weird. I pulled up Google, and just as I suspected, the kid’s account was still logged in. The microwave startled me when it let me know that my food was done with a pretentious little ‘ding!’ I got up and got my food and a fork, realizing that I felt guilty, like a kid with his hand in the cookie jar, thinking in that brief second that I may have been discovered snooping through a dead kid’s computer.
No. MY computer, I mentally corrected myself. I purchased it, and the previous owner just had something unfortunate happen to him. It wasn’t the computer. And it isn’t snooping, because it is my computer, and I would like to know if the kid had visited any websites or received any sketch emails that I should worry about stealing my credit cards and internet porn search history or anything like that. Right?
Right. And so, with that justification in mind, even though I wasn’t actually concerned about any of that, I went about my snooping. I was curious, and felt kind of guilty and a little spooked. There is something that feels intrinsically wrong about snooping through a dead person’s files, especially a dead kid. Maybe he hadn’t died, but I had the feeling he did, from the way his grandmother had warned me. My mind kicked into justification mode again and told me it was no different than wandering around an estate sale after someone died, and Alex brought me to those all the time. Truth be told, they creeped me out a little, too, but it’s just what people did. Best not to think about it.
Over the next few hours, I found very little, if any, surprising or suspicious activity on the computer. The kid mostly hung out in chat rooms, played WoW, had a reddit account, and had spent a lot of time on YouTube. Nothing that looked like it would be installing malware. (And, I thought, nothing to indicate the kid was suicidal or into anything weird). Somehow it felt like ghosts should have come flying out of the screen or something. None did, and I decided that none of it was my business anyway. I selected anything I found in documents, music, pictures, or on the desktop and each time hit shift+delete, so it would bypass the recycle bin and I would not be tempted to snoop. Snooping like that is sort of a rabbit hole, and one thing my mother always said when we would house sit for the neighbors or found ourselves in anyone else’s home when they weren’t home rung true with me here: ‘if you go looking for trouble, you’ll find it. Doesn’t enough trouble find us on its own?’ That was her ‘don’t snoop through shit that isn’t yours’ spiel, and she was probably right. Time to make it my own.
I wiped the signed-in account on the browser. I went in to the ‘users’ screen and created my own as an Admin, and I made sure any programs I would need to use were installed in a way that any user could access them. I signed in as me, and deleted the poor, dead kid’s account. I opened up Word, intending to sign in to my own “Office 365” Account, so the lady didn’t get charged or anything, and I went to the top of the screen for the “sign in” option.
It wasn’t there. Huh, weird, I thought. Could this have been one of those older copies of Microsoft you bought on a disc and didn’t have to pay a subscription fee for? Score again! I thought they had stopped making those. It looked pretty new, though. Weird. The front door opened, and I heard, “Hellooooo!” in Alex’s sing-songy voice.
“Hey babe.” She came in and kissed my cheek.
“So, you gonna show me this new hotshot computer of ours?”
I raised an eyebrow. “Okay, yours.”
“You can use it sometimes,” I teased. She shoved my shoulder playfully.
As I suspected, she had grabbed something from Zaxby’s on the way home. I grabbed one of the fries in her meal and savored it. Zaxby’s coats their fries in seasoned salt, and they’re freaking delicious. She slapped my hand away and whined, “Hey! I haven’t eaten since noon. Back off!” She turned away from me. “Hey…” She grabbed the wireless mouse and moved it to the top of the screen. Microsoft Word was still open.
“This a bootleg or something?” She was hovering the mouse over the top part of the ribbon, where it says ‘Home, Design, Review’ and the like. Next to those options was a little lightbulb that said “TELL ME WHAT YOU WANT TO DO” and it was blinking red.
“I don’t know, but I tried to sign in to our account, and there is no place to do that,” I told her. “What makes you say that?”
She ate another fry and thought about it. “I don’t know, it just looks different. Maybe the blinking red ‘Help’ thing?” She sat down and moved the laptop in front of her. “May I?”
“Sure.” I gestured for her to have at it. My girlfriend currently works in retail, at a department store, and a lot of people mistakenly assume that retail jobs don’t have any use for tech skills. As the Assistant Manager of her department, she used these Microsoft programs as much or more than I did.
“I can’t get over the blinking ‘TELL ME WHAT YOU WANT TO DO’ thing,” she said. “It’s weirding me out.” She clicked it and it stopped blinking.
She typed, ‘I want to get a raise at work’ and hit enter. “Let’s see what a discounted two-thousand-dollar computer with a bootleg copy of Word can do for me,” she joked.
The screen sat there loading for a minute before a pop-up appeared on the screen.
No Registered User Found. Would you like to register, Alex McCabe? (Yes, No)
“What the fuck?!” She said, scooting her chair away from the table. She looked at me.
I should have been scared, felt defensive, or been worried, but I was fascinated. “How…?”
“You should uninstall that,” she said. “It’s probably some kind of black market copy that steals your…. I don’t know.” She walked over and clicked No. The screen reverted to its usual, mostly normal format, except the red blinking message: TELL ME WHAT YOU WANT TO DO. “I am getting in the shower.”
As soon as I heard the bedroom door shut, I immediately began typing into the red blinking area on top of the MS word screen. ‘Tell me how you knew my girlfriend’s name.’
Loading again. Error message.
‘No registered user found. Would you like to register, Colin Davies? (Y/N)’
I clicked yes. Should I have been a little more concerned that it knew the difference between me and my girlfriend? Absolutely. But I was oddly transfixed by it, and for some reason, it didn’t seem odd at the time. Maybe I was just careless, and maybe it was something else that made me click Yes; I can’t be sure now. Hindsight is always 20/20, right?
‘THANK YOU, COLIN. YOU ARE NOW THE REGISTERED USER. PLEASE CAREFULLY READ THE TERMS AND CONDITIONS AND END USER LICENSING AGREEMENT, THEN TELL ME WHAT YOU WANT TO DO.’
Does anyone ever read the terms and conditions? I didn’t. I typed again, ‘I want to know how you knew our names.’
Loading.
Error: invalid query.
Okay, well, good parlor trick, Microsoft. Our Wi-Fi/Cable provider billed us on a joint account, so I figured it was pulling our names from the ISP. Great privacy policy, Comcast. I rolled my eyes and typed, ‘I want to see Alex get a raise at work tomorrow’ and hit enter.
Loading.
DID YOU READ THE TERMS AND CONDITIONS?
I clicked Yes, Ignoring the link.
Loading. Nothing happened.
“We’ll see.” I chuckled to myself and closed the lid. I figured I’d join Alex in the shower. And I did. As we were drying off, I told her how I’d registered the software in my own name, and that I told it to get her a raise.
She said, “You erased that creepy bootleg and just downloaded the regular one, right?”
“Of course.” The lie was on my lips before I had time to consider it. In hindsight, that too was odd, because Alex and I had a policy of absolute honesty. The kind of honesty that I wouldn’t recommend for most couples. She had been cheated on in the past, and I had a roommate that got into Heroin and stole from me, so when we first started dating, it was something we had easily agreed on: no lies. And usually, I kept to it. Usually, I had nothing to lie about. I didn’t even think about it as we curled up for bed that night.
Later on that night, I woke to a godawful racket that I can only compare to some sort of a ‘roided-out digital dog whistle. An alarm of some sort? I nudged Alex to see if she could hear it too. She had to. It was loud, abrasive, and probably waking the neighbors. Was it in the house? A neighbor’s alarm system? How the actual fuck was she sleeping through this? Wow. She rolled over and mumbled something incoherent. Sleeping like a baby. I got up, grabbing the .22 varmint rifle I kept next to the bed, and went to see what the noise was. In retrospect, on some level I knew that an intruder couldn’t make this sort of screeching, ear shattering noise, but I was half asleep and did the guy thing: grab gun, defend turf. Like a magnet, I was drawn into the small kitchen, and I could somehow feel that the sound was coming from that area, even though it permeated the air in a way that it was no louder or softer in one room than any other. My new laptop sat innocuously, closed, on the kitchen table, but it was emitting a sickly, orangeish red glow from the small space between the screen and the keyboard. The unnatural light formed an odd, glowing square around the laptop, except the side with the hinges that the screen rested on when you flipped it open.
Okay, I thought. I knew I should have considered that there would be something wrong with this thing. Too cheap. But could it really be making this noise? I half considered shooting the damn thing and going back to bed. I wish I had. Too much paperwork, though. Discharging a firearm in city ordinances would surely get you in deep shit, even if a rabid racoon was attacking you. Instead, God help me, I decided to open it up and see if there was some sort of alarm system or something in the computer causing the noise. Note to self, I thought, turn the damn thing all the way off before bed. In fact, remove the battery.
I sat down at the table, the unholy screeching still in my head, and flipped open the screen. The screeching immediately stopped, and the sickening glow went back to the usual, blue-light laptop screen that all of our retinas have come to know and love. I blinked a couple of times, to clear the sleep fuzz out of my eyes, and because I couldn’t believe what I was seeing.
I’m sorry to wake you, Colin.
I need you to read the terms and conditions.
(OK/Cancel)
I clicked “cancel,” and the error message returned, and the screeching began again, worse than before. It was actually causing my eyes to water, sort of how you’ll involuntarily cry if you get punched in the nose. I never knew that ears had the same connection with the tear ducts. Today I Learned, thought dryly as I clicked Yes.
I had no intentions of reading any terms or conditions at that hour, but I knew as I was slowly scrolling through them that I would file a complaint with Lenovo, Microsoft and any other company that had any software or hardware in that computer in the morning, because that is one obnoxious way to get someone to read an End User agreement. I slowly scrolled to the bottom and when I figured that the appropriate amount of time had passed that the computer would (think???) that I had actually read all of their legal garbage, I clicked ‘I Agree’ at the bottom of the pop-up window.
I had often thought to myself that one day, I would actually need to start reading things before signing/agreeing to them. If you pay attention to the news and tech articles, you’ll see that there are certain functions on our SMART tv’s, cell phones and computers that you are not required to allow or agree to, but that we all generally do, essentially allowing these devices to access all of our personal data. I had nothing to hide, and thought that maybe if someone wanted to steal my identity, they could pay my student loan balance while they were at it, and perhaps file last year’s taxes for me. But, like a good red-blooded American, I bought anti-virus software, carried a wallet that protected my bank and credit card info from devices that could remotely steal the info, and upgraded my cards to the ones with the chips in them when my bank asked me to. This time, though, I didn’t read it because I don’t like being told what to do. It’s possible that my stubbornness has caused me a lot of trouble, because the Terms and Conditions the stupid computer wanted me to read weren’t even all that long, compared to some of the other crap I’ve had to scroll through to access my software and apps, but I was tired and still had a headache from that stupid “Terms and Conditions Police” alarm the computer had blasted into my head. I looked at the screen, which was on Microsoft Word again. I shook my head, already forgetting about how I had (told??) my computer that I wanted my girlfriend to get a raise at work.
When you do things like this, little goofy, innocuous things, you tend to forget about it. Alex and I thought we were being clever, typing about her getting a raise into an oddly-worded field (TELL ME WHAT YOU WANT TO DO) that was obviously a help field. The text would have been ingeniously created by some Adderall-popping millennial with a three-day beard and a skinny-pants suit somewhere in Silicon Valley behind a desk, who had probably been paid an obscene salary to come up with some words that were more ‘user-centered’ than the word “Help.” That’s how all of these things work, isn’t it?
Not this one. Anyway, I went about my daily business, attending classes, working my side hustle (which is what I called my part-time office job to make it sound cool. It was my only hustle, and was boring as all hell) and using the computer as one might – I worked on my Masters thesis, sent emails, procrastinated on Reddit, Facebook and occasionally (I know, NERD) played WoW or browsed the crappy, free amateur adventures of YouPorn. Normally, I didn’t bother with Porn, because Alex was… well, I’ll say the kind of girl that didn’t require a huge hand-to-man relationship most of the time. She was an awesome girlfriend, or, at least, I thought she was, before all this. She had been coming home late a lot lately, and acting a little different. Stress, I assumed, and didn’t think twice about it. I certainly didn’t want to add to it. She was hoping to go from Assistant Department Manager to Assistant Store Manager, and she had taken on some extra responsibilities in order to do that.
One night, I sat at the computer, three beers deep, trying like hell to write some stupid paper for school. I can’t even remember what it was. I stared at the computer, tired and drawing a blank, and noticed the help message at the top corner of my screen blinking red: TELL ME WHAT YOU WANT TO DO. I don’t know why I did it. I missed Alex, hadn’t been hanging out with my buddies from school or work much, and I guess the computer was saying something that spoke to me I typed, I WANT TO SEE ALEX.
Go figure, no weird error messages this time. I went to delete my typing and go back to my research when an odd program popped up. Nothing could have prepared me for what I saw. It was Alex, all right, and she was at work – but she was in the back room, I was guessing, bent over a table with her tits hanging out of her button-down shirt and her skirt hiked up around her waist. A man held her hands behind her back while he fucked her from behind. I knew this guy, it was Dan, the Store Manager. And he was fucking my girlfriend. Let me tell you, this shit put YouPorn to shame. Alex was hot, and if I wasn’t so freaked out by this, and if I wasn’t looking at my own girlfriend and her boss, I would have had a rager to take care of. If not for the audio, I could have suspected she was being raped, and sprang into action. Only, she wasn’t. People who were being raped didn’t usually tell their assailants to fuck them, and moan, and… Oh, God. I felt sick. I was in shock. There was no way that was Alex… except, hadn’t that been the outfit she left today wearing?
How the fuck did the computer do that? Maybe it was some kind of elaborate hoax. I did the only thing that my numbed brain could think of, and I called her. If I spoke to her, and she didn’t sound like she was letting some guy drill her like a porn star in the back room, maybe I would just set fire to the computer and be done with it. I called her cell phone number, and god damn it I heard her ring tone. Through the audio on that God damned video.
No, please, no. I heard her say “He’ll call back.” And with that, I knew she was cheating on me. For a sick, voyeuristic moment, I sat and watched this unfold. As they were switching positions, her on her knees, and he approaching her with his dick in his hand, I found the X at the top of the screen and closed it. Now, I had a lot on my mind. Alex, whom I was sure I would ask to marry me after grad school before that moment, was cheating on me. What’s more, somehow, my computer knew it, and had found a camera somewhere in the room and showed it to me. What was anyone hoping to accomplish with all this? What the fuck was up with this computer? What was wrong with this world?
I should have gone to Alex’s work and asked for her. I should have broken up with her on the spot, and beat the ever-loving shit out of ‘Dan,’ the man who was undoubtedly currently getting a blowjob from the mouth that kissed me every morning. Instead, I went back to the computer, and stared at the field where I had typed ‘I WANT TO SEE ALEX’, blinking red, with the message TELL ME WHAT YOU WANT TO DO. My voice cracked, I could hear it through the empty apartment. I said, through very un-manly tears that I was furiously trying to choke back, “Why?”
It wasn’t loud and it wasn’t a scream; more a perfect reflection of the confusion, hurt and anger I was currently feeling. How could she? How long had it been going on? Had she ever… before we…. My train of thought was interrupted as a dialogue box popped up on the screen of my computer that said, “SHE REALLY WANTED THAT RAISE, COLIN.” I picked the computer up and heaved it against the wall, expecting to be sweeping it into the trash in a drunken rage (I pounded the rest of my beer and opened two more very shortly after) along with my hopes and dreams of a future with Alex, but it bounced off the wall and fell harmlessly to the ground. Not a chip, scratch or crack anywhere on it. What the fuck? I let out a feral cry and charged the thing. I guess I tried to tackle it. I bashed it on the floor, the table, and punched at the screen. I was seeing red.
When all was said and done, I looked at my computer, which was now on the other side of the kitchen after having been punched, slammed, kicked and punted across the room into a wall, and it sat there, unharmed, the screen seemingly taunting me with its blinking red message, which I could see across the room: TELL ME WHAT YOU WANT TO DO. My drunk, angry brain had now reached an eerie state of calm as I began to accept one thing about this shitty situation: somehow, this computer was able to… do things. See things. Know things. Show me things. Possibly even make things happen.
What I should have been thinking of were bets, lottery numbers, riches, success and the like. I should have confirmed what I honestly already knew. All the late nights, her emotional distance, the extra few minutes in the mirror before work, the new underwear… It all added up now, I just didn’t want to see it those past few weeks. No, I was too angry to ask my bootleg copy of Microsoft Office to give me the key to success or make me rich. All I could think of was revenge, and I sat down before I lost my nerve, opened my seventh beer for the night, and considered all of the ways I could exact it. I finally decided on one, and slowly began to type. “I want Alex McCabe to kill her boss.” The little circle spun on the screen, loading.
I sat in the dark, drinking, and waiting.
6 notes
·
View notes
Text
Photo Text For Mac

Roy ~ Welcome to the Community.
Free Happy Birthday Photo Text For Cousin
Photo Text For Pc Windows 10
Can anyone share their experience with the 'copy text from picture' property please?
I did the following tests using OneNote for Mac v.15.8 on OS X v.10.10.3:
1. Created a PNG screenshot and dragged it into OneNote. The embedded image DID have the option of 'Copy Text from Picture'.
What is text edit app. Add Text to Photos with Preview App on Mac This built-in app is rarely the first choice for Mac users who want to add text to photos, but completing this task with Preview App is remarkably easy. Open the app and import the photo you want to edit, then make sure to click on the 'Show Edit Toolbar' icon and select the 'Text Tool' feature.
2. In OneNote I did 'Save As..' on that image, which saved it as a JPG on the Desktop.
Adding text to images is a fairly simple process to begin with that is made even easier with Preview, the basic image viewing app that is bundled on all Macs. May 16, 2013 Adding text to images is a fairly simple process to begin with that is made even easier with Preview, the basic image viewing app that is bundled on all Macs.
3. Dragged that image from the Desktop back into OneNote. The embedded image DID have the option of 'Copy Text from Picture'.
4. In OneNote I did 'Save As..' on that image, which saved it as a JPG on the Desktop.
5. Dragged that image from the Desktop back into OneNote. The embedded image DID have the option of 'Copy Text from Picture'.
..So the above worked as expected, although I did have to wait a minute or two before the option of 'Copy Text from Picture' appeared. I don't know the reason you're seeing different results.
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
Thanks AlancitoXV,
I currently work with OSX Yosemite Ver10.10.3, Onenote Ver 15.8 150301,
created PNG screenshot of your reply (so it's text-based), and then dragged it from my desktop into Onenote, but the embedded image DID NOT have the option of 'Copy Text from Picture'.
I also Saved to my desktop as PNG (one time) and as JPEG (another time) a picture from my friend's notebook (which he shared with me), that had the 'Copy Text from Picture' option, and then dragged it back into Onenote, but in both cases the picture lost its ability for 'Copy Text from Picture'.
I would appreciate if anyone in Microsoft would be able to address this disparity. Seems like my Onenote is capable of 'Copy Text from Picture' only for some pictures but not for others.
I am wondering if there's a certain role.
Thanks a lot!
Roy
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Sublime text for mac. This system gives you flexibility as settings can be specified on a per-file type and per-project basis.
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
I currently work with OSX Yosemite Ver10.10.3, Onenote Ver 15.8 150301, created PNG screenshot of your reply (so it's text-based), and then dragged it from my desktop into Onenote, but the embedded image DID NOT have the option of 'Copy Text from Picture'.
Roy ~ I did the same with identical software versions & PNG screenshot and, after waiting a minute, the embedded image does have the option of 'Copy Text from Picture':
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
As could be seen in the snapshot i provide, i do not have this option available, only copy link to a paragraph.
I've waited more than a few minutes..
Hopefully this bug could be fixed in next versions of Onenote.
Thanks,
Roy
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Free Happy Birthday Photo Text For Cousin
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
• Click OK, and Word flips the text in the text box, producing a mirror image. You can create an upside-down mirror image by changing the Y setting to 180. How to rotate a text box in word mac 2008.
Hopefully this bug could be fixed in next versions of Onenote.
Roy ~ You could make sure Microsoft is aware of the problem via this feedback form:
www.microsoft.com/mac/product-feedback
…Click Select a Product… and choose OneNote for Mac. Since that site doesn't accept screenshots, you could link to this thread.
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
I've tried this action in another Mac of mine (laptop at home, instead my desktop at work) - and brilliantly, the 'copy text from picture' became active! .. (which is basically good news for my laptop, but sort of bad news for my desktop. ) - seems like there might be some platform incompatibility issues on some machines. Roy
Did this solve your problem?
Sorry this didn't help.
Great! Thanks for marking this as the answer.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
How satisfied are you with this response?
Thanks for your feedback.
Photos capture the precious moments of our lives. Unfortunately, it’s not easy to take high-quality pictures on the first try – it’s not often that you actually want a random passerby or a misplaced finger to feature in your photos. And you know that good lighting would really enrich the colors in your pictures. And then there are the photographs that tend to fade and yellow with time. To fix these problems, you need Movavi Photo Editor for Mac – a simple program that’s equally good both for beginners and professionals.
Don’t waste your time trying to figure out how to use complicated desktop applications for photo processing. Download our easy-to-use photo editing software for Mac: it will enhance your images faster than many other image editing apps!
Photo Text For Pc Windows 10
Erase Unwanted Objects
Enhance Image Quality
Restore Old Photos
Retouch Portraits
Erase Unwanted Objects with Photo Editor for Mac
Get Rid of Excess Stuff in Your Photos
No need to avoid shooting photos in crowded places. Take photographs wherever you want and then just remove unwanted objects, random people, trash, or bad graffiti from your digital images with Movavi’s photo software. The Object Removal tool uses great care to cover all those little flaws in just a couple of minutes!
Download Movavi Photo Editor and check out all the features of the program.
A good text editor for Mac OS X. Benjamin frere. Posted: April 19, 2003 10:48AM. KDE and GNOME, for me, are two funny spare time experiments to take the best of Mac OS' and Windows' GUIs, and add on lots of features that might be of use (when they mostly are just in the way). Even Windows' GUI is far better than KDE and GNOME. Best Text Editors for Mac in 2018: Top 5 Text Editor Apps for Mac OS X. Here is the list of best text editors for Mac Os. Apps with their pros and cons are listed in the article in precise points. Download text editor for mac free. Carbon Emacs Package is a Mac-friendly distribution of the GNU Emacs text editor. It’s simple, extensible, and good for technically minded users who value the advanced features it offers. Not the most user friendly app, but worth bearing in mind. Good text editor for mac os. The best free and paid text editors for the Mac. Brackets is an open-source text editor aimed at web designers and developers. But if you want to customize a text editor to do your bidding, Brackets is a good place to start. Free - Download now; TextMate 2. Finally, this review is about the best text editor for macOS, not the best macOS application that’s also a text editor. Atom is our top pick for most people, but its design follows a different set of principles than those laid out in Apple’s Human Interface Guidelines for macOS apps.
Enhance Image Quality
Make Your Photos Come Alive
Is overcast weather dulling down your photographs? Don’t panic! Mac Photo Editor will automatically amp up the brightness and contrast in your image at the touch of the Magic Enhance button. You can also change the settings manually to achieve the desired effect. See how the image adjustment works by dragging the slider under the picture.
Magic Enhance
Looking for a way to restore photos taken decades ago?
Movavi Photo Editor with its advanced image editing tools quickly removes fold lines, stains, and other small defects from old photographs that you’ve scanned. You can also automatically add color to your black-and-white photos. The program uses a smart fill algorithm to analyze and repair parts of the image that have suffered from aging. Just click the Restore button and wait for the image editor to do the photo processing for you!
Retouch portraits
Improve Your Look in an Instant
Professional photo retouching can be easy and fun. What’s more, it’s affordable with our user-friendly photo editor for Mac. Try new makeup or dye your hair. Remove skin blemishes or slim down your face. Get a Hollywood smile with the Teeth whitening tool. The only limit is your imagination!
Try All the Features of Movavi's picture editor for Mac OS
White Balance
Adjust the lighting in images. Make the photos in your library look natural.
Effects
Apply a range of creative and subtle filters to create different looks.
Text
Insert captions and titles, add decorative elements.
Sharpness & Details
Adjust clarity in blurred images and bring out textures.
Retouching
Remove blemishes, smooth out wrinkles, get rid of shine, and correct red-eye.
Crop, Rotate, Resize
Improve composition, straighten the horizon, shrink images for the Web.
Color Correction
Make your colors richer while keeping skin tones natural-looking.
Makeup
Airbrush digital eyeshadow, mascara, and lipstick onto your portraits.
Inserting
Combine images and image elements to make collages.
Noise Reduction
Use presets to reduce digital noise in low-light photos.
Reshaping
Alter face shapes and silhouettes, sculpt noses, enlarge eyes.
Change Out Backgrounds
Replace the background, make it transparent, or set any color as the new background.
Looking for a quick and easy way to edit pictures? Install Movavi Photo Editor on any Apple personal computer compatible with Mac OS versions 10.7–10.13, for example, OS X Lion, OS X Yosemite, OS X El Capitan, macOS Sierra. The app is so easy to learn that you don’t even have to know the basics about how to edit photos on Mac. You can get to work on your MacBook Pro or Mac mini right away.
Screenshots
About
5.8.0
78.1 MB
29,95 €
System Requirements
Mac OS X® 10.7 or higher
64-bit Intel® processor
1280 × 768 screen resolution, 32-bit color
2 GB RAM
500 MB available hard disk space for installation, 1 GB for ongoing operations
Administrator permissions are required for installation
* Unfortunately, correct processing of large image files with dimensions greater than 6000×8000 pixels cannot be guaranteed.
Photo Editor
Photo Editor
PHOTO EDITOR + PHOTO MANAGER
Edit your favorite photos and quickly organize images
PHOTO EDITOR + PHOTO MANAGER
Edit your favorite photos and quickly organize images
PHOTO EDITOR + PHOTO MANAGER + SLIDESHOW MAKER
Edit photos, organize images, and create great slideshows
PHOTO EDITOR + PHOTO MANAGER + SLIDESHOW MAKER
Edit photos, organize images, and create great slideshows
Photo Editor
Photo Editor
PHOTO EDITOR + PHOTO MANAGER
Edit your favorite photos and quickly organize images
PHOTO EDITOR + PHOTO MANAGER
Edit your favorite photos and quickly organize images
PHOTO EDITOR + PHOTO MANAGER + SLIDESHOW MAKER
Edit photos, organize images, and create great slideshows
PHOTO EDITOR + PHOTO MANAGER + SLIDESHOW MAKER
Edit photos, organize images, and create great slideshows
Leave us your email, and we'll send you the link to download the program to a computer.

0 notes
Text
I can’t seem to figure out how to fix the format when it’s spaced out like this between the questions and answers. It bugs me, but I needed a survey to do. Sigh.
Did you have a New Year’s kiss?
Nope. New Years was really just another day. My family and I didn’t do anything. I wasn’t feeling in the celebratory mood just losing my baby (my chocolate lab, Brandie) the weekend before.
Are there any words that you cannot pronounce or that you pronounce incorrectly?
I used to have a hard time saying, “certificate” and “aluminum” when I was little. There might be a word I can’t say now, but nothing is coming to mind at the moment.
After a long day at work or of doing something physical what tends to hurt more? Your back or your feet?
My back. I have chronic pain, and if I’m up for a long time period of time, well actually it doesn’t have to be that long depending if I’m having a particularly bad day, I’ll have to pay the price for it. It doesn’t take much anymore since I feel so drained and shitty all the time.
Do you have a smart phone? If so, what’s your favorite app?
Yes. I use the Kindle app, Twitter, and Snapchat most often.
If you had to choose between being a nurse or an English teacher which would you choose and why?
An English teacher. I wanted to be a teacher when I was younger, and English was always my best subject. I couldn’t handle being a nurse. I’m much to squeamish when it comes to my own stuff, I couldn’t handle another persons’ blood, vomit, and other bodily fluids. I’d be afraid of hurting them and doing something wrong, too. And being in the medical field you will likely have to tell someone sad news, and deal with death. I just couldn’t.
Do you have a specific gas station you usually go to? Or do you stop wherever?
I, personally, don’t have to go to the gas station since I don’t have a car. Or drive.
How much older than you was the oldest person you have dated/had a relationship with?
I was a year older than both people I had a relationship/thing with.
Is anything stressing you out at the moment?
Always.
What is your opinion on dating someone who already had a child/children from a previous relationship?
As of now, I’m not sure I’d want that. I’m not ready for kids.
Have you ever actually found a mascara that makes a huge difference for your lashes?
Yes, actually.
Would you rather have one or two great facial features that stand out, or have just an overall pretty face but have no special features?
I wish I had pretty eyes and a nice smile.
Do you check your horoscope daily? If so, did you relate to your horoscope at all today?
Nope. I don’t check it at all. I may come across something for fun on here or something, but I don’t actively check it.
When you need to remember something how do you usually go about doing so?
I set a reminder on my phone, and I also will often write it on the marker board in my room that I see whenever I exit my bedroom.
How would you describe someone that is your type of guy/girl?
You just have a connection with some people. It may be the physical attraction that starts it, but it’s really when I get to know the person and their personality. A good personality goes a long way with me. Someone I vibe with and makes me feel comfortable, makes me laugh, is kind, caring, respectful, easy to talk to... stuff like that.
Have you recently accomplished anything that you are proud of yourself for?
No.
Are you still friends with any of your exes? Do you still communicate with any of them at all?
I haven’t talked to Joseph since last July. Before that, it had been like three years. I haven’t talked to my actual ex in like five years.
Do you live on your own or with your parents/a roommate? Do you think you’d like to live alone?
I live with my parents. I would not like to live alone, I know that for sure. I like my alone time and can handle short amounts of time, which can be nice, but I couldn’t be completely alone. I get too anxious and scared. I can have alone time in my room with my family still here, too, so. Also, it just what makes the most sense for me given my disability and health. My family helps me out with a lot, especially my mom.
How often would you say you use Microsoft Word?
Now that I’m no longer in school, I haven’t had to use it anymore. The last time was sometime in early 2015.
How often do you typically change your bra?
Everyday.
What is the last online purchase you made?
Various gifts for my family. I did most of my Christmas shopping online this past Christmas.
Do you usually have bad symptoms around “that time of the month”?
Very.
Is there anyone you have to see on a daily/weekly basis that you really dislike?
No.
Is your hair thick or thin? Would you say it’s easy to manage?
According to my hair dresser, it’s thick. I don’t think it’s that thick, but yeah. Now that it’s gotten so long it can be hard to manage just cause I often just want to throw it up in a messy bun and leave it that way. I don’t do much with my hair, which I thought I would when I decided to let it grow out again. I just don’t have the desire or energy. I really have stopped putting much effort into my appearance... I hardly bother with makeup now. My depression and my health have just taken so much from me.
Have you ever had to deal with any type of long distance relationship, whether it be a romantic relationship or a friendship?
No.
Are you procrastinating doing anything right now?
No.
Do you have a place you go to a lot that you may be considered “a regular” at?
The waitresses at the Mongolian BBQ place knew my mom and I.
Have you smoked a cigarette today?
Nope. I don’t smoke.
What is your last received text message?
I don’t feel like checking.
Do you like to read in your leisure time?
I love to read.
Did you have a treehouse when you were a child?
No.
Do you still live with your parents?
Yes.
Have you ever dated outside of your race?
Yes.
Do you have your own laptop/computer?
Yep.
What is the last horror movie you watched?
One of the Halloween movies.
What was the last thing you ate?
A Lean Cuisine meal.
What is something that makes you grumpy?
Not having my coffee, yet, and being hungry.
What are you wearing?
Pajama pants, a long sleeve shirt, and a hoodie.
Have you ever witnessed a drug deal?
No.
Are you better at science, maths or art?
I suck at all of those. Math was my worst, though. I have no artistic talent. I was okay with some of science.
Do you have any songs in your head at the moment?
No.
Did you ever call any teachers by their first name? Who?
Nope.
Were you born in a hospital, or somewhere else?
A hospital.
Do you often have doors held open for you?
Yes.
Do you know anyone who volunteers a lot?
My brother has done a lot of volunteer work so far during his senior year.
Have you ever been cheated on? Tell me your story.
Nope.
Which would you choose between choice chip cookies and oat & raisin cookies?
I’m guessing you meant chocolate chip cooks, which is what I would choose out of those two.
What did you have for dinner tonight, or last night if you haven’t yet?
That Lean Cuisine meal I mentioned.
Are your parents smokers, or have they ever been?
Nope.
Do you drink alcohol?
I haven’t drank in four years.
5 notes
·
View notes
Text
A Bit on Web Component Libraries
A run of Web Components news crossed my desk recently so I thought I’d group it up here.
To my mind, one of the best use cases for Web Components is pattern libraries. Instead of doing, say, <ul class="nav nav-tabs"> like you would do in Bootstrap or <div class="tabs"> like you would in Bulma, you would use a custom element, like <designsystem-tabs>.
The new Shoelace library uses the sl namespace for their components. It’s a whole pattern library entirely in Web Components. So the tabs there are <sl-tab-group> elements.
Why is that good? Well, for one thing, it brings a component model to the party. That means, if you’re working on a component, it has a template and a stylesheet that are co-located. Peeking under the hood of Shoelace, you can see this is all based on Stencil.
Another reason it’s good is that it means components can (and they do) use the Shadow DOM. This offers a form of isolation that comes right from the web platform. For CSS folks like us, that means the styling for a tab in the tab component is done with a .tab class (hey, wow, cool) but it is isolated in that component. Even with that generic of a name, I can’t accidentally mess with some other component on the page that uses that generic class, nor is some other outside CSS going to mess with the guts here. The Shadow DOM is a sort of wall of safety that prevents styles from leaking out or seeping in.
I just saw the FAST framework¹ too, which is also a set of components. It has tabs that are defined as <fast-tabs>. That reminds me of another thing I like about the Web Components as a pattern library approach: if feels like it’s API-driven, even starting with the name of the component itself, which is literally what you use in the HTML. The attributes on that element can be entirely made up. It seems the emerging standard is that you don’t even have to data-* prefix the attributes that you also make up to control the component. So, if I were to make a tabs component, it might be <chris-tabs active-tab="lunch" variation="rounded">.
Perhaps the biggest player using Web Components for a pattern library is Ionic. Their tabs are <ion-tabs>, and you can use them without involving any other framework (although they do support Angular, React, and Vue in addition to their own Stencil). Ionic has made lots of strides with this Web Components stuff, most recently supporting Shadow Parts. Here’s Brandy Carney explaining the encapsulation again:
Shadow DOM is useful for preventing styles from leaking out of components and unintentionally applying to other elements. For example, we assign a .button class to our ion-button component. If an Ionic Framework user were to set the class .button on one of their own elements, it would inherit the Ionic button styles in past versions of the framework. Since ion-button is now a Shadow Web Component, this is no longer a problem.
However, due to this encapsulation, styles aren’t able to bleed into inner elements of a Shadow component either. This means that if a Shadow component renders elements inside of its shadow tree, a user isn’t able to target the inner element with their CSS.
The encapsulation is a good thing, but indeed it does make styling “harder” (on purpose). There is an important CSS concept to know: CSS custom properties penetrate the Shadow DOM. However, it was decided — and I think rightly so — that “variablizing” every single thing in a design system is not a smart way forward. Instead, they give each bit of HTML inside the Shadow DOM a part, like <div part="icon">, which then gives gives the ability to “reach in from the outside” with CSS, like custom-component::part(icon) { }.
I think part-based styling hooks are mostly fine, and a smart way forward for pattern libraries like this, but I admit some part of it bugs me. The selectors don’t work how you’d expect. For example, you can’t conditionally select things. You also can’t select children or use the cascade. In other words, it’s just one-off, or like you’re reaching straight through a membrane with your hand. You can reach forward and either grab the thing or not, but you can’t do anything else at all.
Speaking of things that bug people, Andrea Giammarchi has a good point about the recent state of Web Components:
Every single library getting started, including mine, suggest we should import the library in order to define what [sic] supposed to be a “portable Custom Element”.
Google always suggests LitElement. Microsoft wants you to use FASTElement. Stencil has their own Component. hyperHTML has their own Component. Nobody is just using “raw” Web Components. It’s weird! What strikes me as the worst part about that is that Web Components are supposed to be this “native platform” thing meaning that we shouldn’t need to buy into some particular technology in order to use them. When we do, we’re just as locked to that as we would be if we just used React or whatever.
Andrea has some ideas in that article, including the use of some new and smaller library. I think what I’d like to see is a pattern library that just doesn’t use any library at all.
FAST calls itself a “interface system,” then a “UI framework” in consecutive sentences on the homepage. Shoelaces calls itself a “library” but I’m calling it a “pattern library.” I find “design system” to be the most commonly used term to describe the concept, but often used more broadly than a specific technology. FAST uses that term in the code itself for the wrapper element that controls the theme. I’d say the terminology around all this stuff is far from settled.
The post A Bit on Web Component Libraries appeared first on CSS-Tricks.
You can support CSS-Tricks by being an MVP Supporter.
A Bit on Web Component Libraries published first on https://deskbysnafu.tumblr.com/
0 notes
Text
Who said that? Teacher’s Edition
Earlier this week, I had written a post and pulled a number of comments from this blog. It was fun to look through and grab them. I never figured that I’d write this post so I didn’t formally keep track of who said what when I copy/pasted them although I think I know. I do have someone who is only happy to correct anything I do so I went back and made sure that I got things right. Where the commenter had a website or blog listed beside them, I’ve included a link back if their comment inspires you to read their blogging.
Some folks recognized their writing and responded but there was a request for the answers. So, here goes.
Looking back at 2018, I smile at some of the wonderful comments that have appeared on this blog in response to some of my posts.
Do you see yourself in there? Do you see others?
1 I had forgotten about that commercial! Thanks for the umm… blast from the past, Doug! I was surprised that it did have a “violent” part. That part didn’t stick in my memory, but the “blue” light did! Sorry to hear of your incident! Here’s to more uneventful walks with the dog..
I had a good smile with Andrew’s comment too. I have searched youtube to confirm quotes and lines from TV shows and movies as well… just to be sure
A recent attempt was: “It’s cold enough out there to freeze your Winnebago!”
Like Aviva, I have always wondered about how graphic a message needs to be to stick. I worry that it goes too far at times, especially in consideration of young children. I guess there might be individual differences in regards to what will “hit home”, but…
Sheila Stewart – sheilaspeaking.wordpress.com
2 Oh, going to have to try this one out – looks like a lot of fun! (and I will suggest it to some people I know, since I don’t have a classroom to play in right now). Thanks, as ever!
Lisa Noble – madamenoble.wordpress.com
3 Thanks for including me Doug. Still fighting that bug, but class back up to 65%! Listened to the show (twioe) last night…awesome as always. Got a chuckle over Stephen’s mention of “the Good Room” and all the banter between you, as always. Keep on keeping on!
Ramona Meharg –mymonkeysmycircussite.wordpress.com
4 Love the post. It made me think about what my role is. Probably a lot more Bluesman than thought leader I guess. But really I started to think that is just important to do what I can do and let other people think about labels. I’m just a teacher with opinions and a blog. That’s good enough for me I think.
Alfred Thompson –http://blog.acthompson.net
5 Hi Doug, and all:) Here is my addition – if I ever hear the word Wheelhouse again it will be too soon. Also I will probably get in trouble for this but I don’t like all the Like a Pirate business. For heaven’s sake. Pirates are real. They steal and murder people. I am working on another blog post, a more thoughtful consideration of the word “modern” – which really has an existing definition and has been co-opted more recently to mean “contemporary.” I know, I am so fussy:)
Anne Shillolo
6 I like Broadway http://fontsgeek.com/fonts/Broadway-Regular, but I have a weakness for art deco fonts. It’s too decorative to read though, but good for posters and titles.
For reading I usually go for arial but recently have been preferring Trebuchet https://www.myfonts.com/fonts/microsoft/trebuchet/?gclid=Cj0KCQiAiKrUBRD6ARIsADS2OLn1B3-UN6EjbTMRsPmw2xTQWIwFrCXNtyTxAmFoh7p_XYxWjXX_lzYaAlJVEALw_wcBit’s nice and clean.
Oddly, if I’m going for a computer styled font I use something like Courier which is a web friendly way to imitate those old fixed width fonts https://www.myfonts.com/fonts/microsoft/courier-new/?gclid=Cj0KCQiAiKrUBRD6ARIsADS2OLnfMx1LblHmfXsmRm32zv_x9kHDMf5_ySTNErPWQ_7GmrGvY-qQCsMaApnbEALw_wcB
If you’ve never messed around with fonts, you’re missing something.
Tim King-plus.google.com/+TimothyKing
7 My teaching partner and I used to do ‘a theme’, back when themes were a thing in kindergarten, around EGGS at Easter time. We did different experiments with eggs each day – how many books can we stack on a raw egg before it breaks, what happens when you soak an egg in vinegar, sinking and floating eggs, spinning eggs (raw eggs wobble, hard cooked eggs spin) and so on. We read lots of books about animals that hatch from eggs. My favourite was always “Chickens aren’t the only ones” by Ruth Heller. Like you, many of our children didn’t celebrate Easter but they were seeing eggs and bunnies everywhere in stores and on TV.
Lisa Cranston – educationandinspirationblog.com
8 Thank you for capturing two days of amazing learning and connecting for us Doug. It was a pleasure to finally have some conversation time with you and I am glad Steven Hurley didn’t beam us up with his modern day transcorder. Appreciate the power that comes in building bridges in this business and you sir are a bridge builder. Looking forward to our next conversation. W
Will Gourley –escheweducationalist.wordpress.com
9 Our mornings begin with the fragrance of espresso filling the air. Milk is heated, the espresso is added to the hot milk and voilà, the magic potion is ready. When we go out, we seldom stop to buy coffee anywhere. We caddy thermos cups of our home brew. If we run out of the elixir…tea it is. When we have friends join us for a formal meal, we usually end the meal with a demitasse of espresso…except for the tea drinkers. We like it that espresso has a lower caffeine content than drip coffee: https://recipes.howstuffworks.com/question645.htm Of course, current science might draw different conclusions.
Noeline Laccetti – nlaccetti.wordpress.comx
10 … that look of betrayal on my wife’s face when I mentioned that I am trying to quit with coffee. She, up to several years ago, hated the stuff. Hated the smell, the taste, the satisfied look on my face as relaxed through my second or third cup in the morning. I guess it was my fault. Someway somehow, she now can’t start her day without it. My attempt at scaling back my caffeine consumption has put my life is in danger. I shouldn’t have mentioned it. I shouldn’t have even written this post. If my blog goes dark for a while its because I am in hiding. Tell my wife, I was wrong … oh so wrong …
Chris Cluff
11 Hi Doug, thanks for sharing your learning from the Ontario Summit. To add to this already great resource, here is a link to all of the presenter’s resources from the weekend: https://edtech.team/OntarioResources18 – Lots more goodies there!
Emily Fitzpatrick
12 I saw this presentation at SIGCSE and left with mixed feelings. The session was pitched as ML for CS teachers with little CS knowledge.
The pizza app is cool but I left thinking that there was a big missing piece which was the actual under the hood ML. It looks great as a tool where the teacher is already knowledgeable but I don’t know how much serious mileage a class will get out of it beyond being a cool demo if the teacher doesn’t already know the subject.
Mike Zemansky – https://cestlaz.github.io
13 I love to sew, but hardly have the time. I go by feel when choosing fabric for any project or any “already made” clothes. I don’t care what it’s called – I only care about how it feels and how well it will wash. I do not remember the fabric you’re talking about, though I feel as if I should. My mom used to see for me, so I likely had many things made from it.
Lisa Corbett –alotalot.wordpress.comx
14 Morning Doug, this brought to mind attendance tracking of students and how if they are going to leave or walk out consequnces mean nothing. The reason you give them to stay is far more powerful. I think folks need to understand the purpose but more importantly if you leave the impression, regardless of this is it’s purpose that people’s whereabouts are what we are starting with and not the culture of a welcoming, inclusive and non intrusive learning environment, the same thing will happen as it does in a secondary school…they opt out as it is no longer about the them but the system they exist within.
Kelly @thebeastedu
15 Good morning Doug! (and Jamie)
I’m glad you guys keep your eyes open when you’re out for your walks. There’s no doubt that keeping an eye out for other vehicles, cyclists, and pedestrians (and dogs) is a critical responsibility for motor vehicle drivers.
I was pleased to read your “exit, stage left“ quote, And even happier when I saw that you had included a picture of SnagglePuss.
You are smarter than the average bear.
Andrew Forgrave
16 I don’t remember exactly when Chrome came out, but I do for Gmail. I went straight to eBay and bought an invitation so I could join. It cost me $5.
The invitation also included another new Google service. Do you remember what it was?
Peter Beens –beens.org
17 I noticed this too when watching cartoons with my nephews. There also seemed to be a whole lot of yelling. Okay now I’m sounding like the old guy who just wants the kids to get off his lawn.
I loved the old Hanna-Barbara cartoons from the mid-60’s. Space Ghost, Frankenstein Jr. and The Impossibles, the original Scooby-Doo, Dastardly and Muttley in Their Flying Machines, The Herculoids, The Banana Splits Adventure Hour – that one was pretty weird, but I did teach some of my grade 6’s the theme song, Jonny Quest and the Jetsons.
I kind of thought we’d be living like the Jetsons by now. At least I thought they would have finished repairing all the roads.
Colin Harris –plus.google.com/+ColinHarrisdigitalnative
18 Hey Doug,
As always your posts seem so timely. Today on my way home from church I noticed a few trees in the neighbourhood who have started to show your beautiful fall colors. I couldn’t help but recall several projects that I had to complete as a child where we would go out into the neighbourhood and find several fall leaves. We then needed to place the leaves in between two pieces of wax paper and iron them . To be honest, I don’t recall what the intended learning outcome was… But what I do remember was that it was a project that my mom and I needed to do together (hot irons and safety) . Sometimes it is those unintended outcomes (special time with a parent) which are just as meaningful as the curriculum outcomes.
Sue Bruyns –susanbruyns.com
19 I have never heard of Qwant until you mentioned it.
I also gave it a try and I must admit that it is a very impressive search engine.
I used the Brave web browser in the past; I had no issues with it.
In my case, I utilise the Google Chrome web browser, because I use certain extensions.
The Brave web browser loads quickly.
Renard Moreau –renardsworld.wordpress.com
20 Hey! This is the fourth time visiting now and I personally just wanted to say I truley enjoy reading your blog site. I’ve decided to bookmark it at reddit.com with the title: %BLOGTITLE% and your Web address: %BLOGURL%. I hope this is alright with you, I’m trying to give your great blog a bit more coverage. Be back shortly.
superstar femme orange (Trick question – this is from spam caught and someone who doesn’t know how to use their software – notice the spam format of the message. I won’t share the URL that they claim to be from)
21 Do you worry about free services going away after a while? = Sometimes. I’m still wounded about the closing of Bitstrips for Schools (which I liked waaaaaay better than Pixton – sorry, Pixton). It went so fast that I couldn’t collect all the old comics I wanted to archive (so Jacob, if you are reading this, please let us grab our files for a quick, one week period, please!)
What is your contingency plans in case that happens? = Wish I had one!
Do you backup your online presence in case it goes away? = I print my blogs as a birthday gift to myself once a year. I did a Twournal for the first part of my tweeting, but I’d love to back up all my Tweets in a print format. Now you’ve got me paranoid Doug!
Diana Maliszewski –mondaymollymusings.blogspot.ca
Thanks to those who took time to share a comment throughout 2018. I hope that I can write on topics that will continue the efforts in 2019.
So, how many did you get right the first time?
Who said that? Teacher’s Edition published first on https://medium.com/@DigitalDLCourse
0 notes
Text
Supply Chain Security 101: An Expert’s View
Earlier this month I spoke at a cybersecurity conference in Albany, N.Y. alongside Tony Sager, senior vice president and chief evangelist at the Center for Internet Security and a former bug hunter at the U.S. National Security Agency. We talked at length about many issues, including supply chain security, and I asked Sager whether he’d heard anything about rumors that Supermicro — a high tech firm in San Jose, Calif. — had allegedly inserted hardware backdoors in technology sold to a number of American companies.
Tony Sager, senior vice president and chief evangelist at the Center for Internet Security.
The event Sager and I spoke at was prior to the publication of Bloomberg Businessweek‘s controversial story alleging that Supermicro had duped almost 30 companies into buying backdoored hardware. Sager said he hadn’t heard anything about Supermicro specifically, but we chatted at length about the challenges of policing the technology supply chain.
Below are some excerpts from our conversation. I learned quite bit, and I hope you will, too.
Brian Krebs (BK): Do you think Uncle Sam spends enough time focusing on the supply chain security problem? It seems like a pretty big threat, but also one that is really hard to counter.
Tony Sager (TS): The federal government has been worrying about this kind of problem for decades. In the 70s and 80s, the government was more dominant in the technology industry and didn’t have this massive internationalization of the technology supply chain.
But even then there were people who saw where this was all going, and there were some pretty big government programs to look into it.
BK: Right, the Trusted Foundry program I guess is a good example.
TS: Exactly. That was an attempt to help support a U.S.-based technology industry so that we had an indigenous place to work with, and where we have only cleared people and total control over the processes and parts.
BK: Why do you think more companies aren’t insisting on producing stuff through code and hardware foundries here in the U.S.?
TS: Like a lot of things in security, the economics always win. And eventually the cost differential for offshoring parts and labor overwhelmed attempts at managing that challenge.
BK: But certainly there are some areas of computer hardware and network design where you absolutely must have far greater integrity assurance?
TS: Right, and this is how they approach things at Sandia National Laboratories [one of three national nuclear security research and development laboratories]. One of the things they’ve looked at is this whole business of whether someone might sneak something into the design of a nuclear weapon.
The basic design principle has been to assume that one person in the process may have been subverted somehow, and the whole design philosophy is built around making sure that no one person gets to sign off on what goes into a particular process, and that there is never unobserved control over any one aspect of the system. So, there are a lot of technical and procedural controls there.
But the bottom line is that doing this is really much harder [for non-nuclear electronic components] because of all the offshoring now of electronic parts, as well as the software that runs on top of that hardware.
BK: So is the government basically only interested in supply chain security so long as it affects stuff they want to buy and use?
TS: The government still has regular meetings on supply chain risk management, but there are no easy answers to this problem. The technical ability to detect something wrong has been outpaced by the ability to do something about it.
BK: Wait…what?
TS: Suppose a nation state dominates a piece of technology and in theory could plant something inside of it. The attacker in this case has a risk model, too. Yes, he could put something in the circuitry or design, but his risk of exposure also goes up.
Could I as an attacker control components that go into certain designs or products? Sure, but it’s often not very clear what the target is for that product, or how you will guarantee it gets used by your target. And there are still a limited set of bad guys who can pull that stuff off. In the past, it’s been much more lucrative for the attacker to attack the supply chain on the distribution side, to go after targeted machines in targeted markets to lessen the exposure of this activity.
BK: So targeting your attack becomes problematic if you’re not really limiting the scope of targets that get hit with compromised hardware.
TS: Yes, you can put something into everything, but all of a sudden you have this massive big data collection problem on the back end where you as the attacker have created a different kind of analysis problem. Of course, some nations have more capability than others to sift through huge amounts of data they’re collecting.
BK: Can you talk about some of the things the government has typically done to figure out whether a given technology supplier might be trying to slip in a few compromised devices among an order of many?
TS: There’s this concept of the “blind buy,” where if you think the threat vector is someone gets into my supply chain and subverts the security of individual machines or groups of machines, the government figures out a way to purchase specific systems so that no one can target them. In other words, the seller doesn’t know it’s the government who’s buying it. This is a pretty standard technique to get past this, but it’s an ongoing cat and mouse game to be sure.
BK: I know you said before this interview that you weren’t prepared to comment on the specific claims in the recent Bloomberg article, but it does seem that supply chain attacks targeting cloud providers could be very attractive for an attacker. Can you talk about how the big cloud providers could mitigate the threat of incorporating factory-compromised hardware into their operations?
TS: It’s certainly a natural place to attack, but it’s also a complicated place to attack — particularly the very nature of the cloud, which is many tenants on one machine. If you’re attacking a target with on-premise technology, that’s pretty simple. But the purpose of the cloud is to abstract machines and make more efficient use of the same resources, so that there could be many users on a given machine. So how do you target that in a supply chain attack?
BK: Is there anything about the way these cloud-based companies operate….maybe just sheer scale…that makes them perhaps uniquely more resilient to supply chain attacks vis-a-vis companies in other industries?
TS: That’s a great question. The counter positive trend is that in order to get the kind of speed and scale that the Googles and Amazons and Microsofts of the world want and need, these companies are far less inclined now to just take off-the-shelf hardware and they’re actually now more inclined to build their own.
BK: Can you give some examples?
TS: There’s a fair amount of discussion among these cloud providers about commonalities — what parts of design could they cooperate on so there’s a marketplace for all of them to draw upon. And so we’re starting to see a real shift from off-the-shelf components to things that the service provider is either designing or pretty closely involved in the design, and so they can also build in security controls for that hardware. Now, if you’re counting on people to exactly implement designs, you have a different problem. But these are really complex technologies, so it’s non-trivial to insert backdoors. It gets harder and harder to hide those kinds of things.
BK: That’s interesting, given how much each of us have tied up in various cloud platforms. Are there other examples of how the cloud providers can make it harder for attackers who might seek to subvert their services through supply chain shenanigans?
TS: One factor is they’re rolling this technology out fairly regularly, and on top of that the shelf life of technology for these cloud providers is now a very small number of years. They all want faster, more efficient, powerful hardware, and a dynamic environment is much harder to attack. This actually turns out to be a very expensive problem for the attacker because it might have taken them a year to get that foothold, but in a lot of cases the short shelf life of this technology [with the cloud providers] is really raising the costs for the attackers.
When I looked at what Amazon and Google and Microsoft are pushing for it’s really a lot of horsepower going into the architecture and designs that support that service model, including the building in of more and more security right up front. Yes, they’re still making lots of use of non-U.S. made parts, but they’re really aware of that when they do. That doesn’t mean these kinds of supply chain attacks are impossible to pull off, but by the same token they don’t get easier with time.
BK: It seems to me that the majority of the government’s efforts to help secure the tech supply chain come in the form of looking for counterfeit products that might somehow wind up in tanks and ships and planes and cause problems there — as opposed to using that microscope to look at commercial technology. Do you think that’s accurate?
TS: I think that’s a fair characterization. It’s a logistical issue. This problem of counterfeits is a related problem. Transparency is one general design philosophy. Another is accountability and traceability back to a source. There’s this buzzphrase that if you can’t build in security then build in accountability. Basically the notion there was you often can’t build in the best or perfect security, but if you can build in accountability and traceability, that’s a pretty powerful deterrent as well as a necessary aid.
BK: For example….?
TS: Well, there’s this emphasis on high quality and unchangeable logging. If you can build strong accountability that if something goes wrong I can trace it back to who caused that, I can trace it back far enough to make the problem more technically difficult for the attacker. Once I know I can trace back the construction of a computer board to a certain place, you’ve built a different kind of security challenge for the attacker. So the notion there is while you may not be able to prevent every attack, this causes the attacker different kinds of difficulties, which is good news for the defense.
BK: So is supply chain security more of a physical security or cybersecurity problem?
TS: We like to think of this as we’re fighting in cyber all the time, but often that’s not true. If you can force attackers to subvert your supply chain, they you first off take away the mid-level criminal elements and you force the attackers to do things that are outside the cyber domain, such as set up front companies, bribe humans, etc. And in those domains — particularly the human dimension — we have other mechanisms that are detectors of activity there.
BK: What role does network monitoring play here? I’m hearing a lot right now from tech experts who say organizations should be able to detect supply chain compromises because at some point they should be able to see truckloads of data leaving their networks if they’re doing network monitoring right. What do you think about the role of effective network monitoring in fighting potential supply chain attacks.
TS: I’m not so optimistic about that. It’s too easy to hide. Monitoring is about finding anomalies, either in the volume or type of traffic you’d expect to see. It’s a hard problem category. For the US government, with perimeter monitoring there’s always a trade off in the ability to monitor traffic and the natural movement of the entire Internet towards encryption by default. So a lot of things we don’t get to touch because of tunneling and encryption, and the Department of Defense in particular has really struggled with this.
Now obviously what you can do is man-in-the-middle traffic with proxies and inspect everything there, and the perimeter of the network is ideally where you’d like to do that, but the speed and volume of the traffic is often just too great.
BK: Isn’t the government already doing this with the “trusted internet connections” or Einstein program, where they consolidate all this traffic at the gateways and try to inspect what’s going in and out?
TS: Yes, so they’re creating a highest volume, highest speed problem. To monitor that and to not interrupt traffic you have to have bleeding edge technology to do that, and then handle a ton of it which is already encrypted. If you’re going to try to proxy that, break it out, do the inspection and then re-encrypt the data, a lot of times that’s hard to keep up with technically and speed-wise.
BK: Does that mean it’s a waste of time to do this monitoring at the perimeter?
TS: No. The initial foothold by the attacker could have easily been via a legitimate tunnel and someone took over an account inside the enterprise. The real meaning of a particular stream of packets coming through the perimeter you may not know until that thing gets through and executes. So you can’t solve every problem at the perimeter. Some things only because obvious and make sense to catch them when they open up at the desktop.
BK: Do you see any parallels between the challenges of securing the supply chain and the challenges of getting companies to secure Internet of Things (IoT) devices so that they don’t continue to become a national security threat for just about any critical infrastructure, such as with DDoS attacks like we’ve seen over the past few years?
TS: Absolutely, and again the economics of security are so compelling. With IoT we have the cheapest possible parts, devices with a relatively short life span and it’s interesting to hear people talking about regulation around IoT. But a lot of the discussion I’ve heard recently does not revolve around top-down solutions but more like how do we learn from places like the Food and Drug Administration about certification of medical devices. In other words, are there known characteristics that we would like to see these devices put through before they become in some generic sense safe.
BK: How much of addressing the IoT and supply chain problems is about being able to look at the code that powers the hardware and finding the vulnerabilities there? Where does accountability come in?
TS: I used to look at other peoples’ software for a living and find zero-day bugs. What I realized was that our ability to find things as human beings with limited technology was never going to solve the problem. The deterrent effect that people believed someone was inspecting their software usually got more positive results than the actual looking. If they were going to make a mistake – deliberately or otherwise — they would have to work hard at it and if there was some method of transparency, us finding the one or two and making a big deal of it when we did was often enough of a deterrent.
BK: Sounds like an approach that would work well to help us feel better about the security and code inside of these election machines that have become the subject of so much intense scrutiny of late.
TS: We’re definitely going through this now in thinking about the election devices. We’re kind of going through this classic argument where hackers are carrying the noble flag of truth and vendors are hunkering down on liability. So some of the vendors seem willing to do something different, but at the same time they’re kind of trapped now by the good intentions of open vulnerability community.
The question is, how do we bring some level of transparency to the process, but probably short of vendors exposing their trade secrets and the code to the world? What is it that they can demonstrate in terms of cost effectiveness of development practices to scrub out some of the problems before they get out there. This is important, because elections need one outcome: Public confidence in the outcome. And of course, one way to do that is through greater transparency.
BK: What, if anything, are the takeaways for the average user here? With the proliferation of IoT devices in consumer homes, is there any hope that we’ll see more tools that help people gain more control over how these systems are behaving on the local network?
TS: Most of [the supply chain problem] is outside the individual’s ability to do anything about, and beyond ability of small businesses to grapple with this. It’s in fact outside of the autonomy of the average company to figure it out. We do need more national focus on the problem.
It’s now almost impossible to for consumers to buy electronics stuff that isn’t Internet-connected. The chipsets are so cheap and the ability for every device to have its own Wi-Fi chip built in means that [manufacturers] are adding them whether it makes sense to or not. I think we’ll see more security coming into the marketplace to manage devices. So for example you might define rules that say appliances can talk to the manufacturer only.
We’re going to see more easy-to-use tools available to consumers to help manage all these devices. We’re starting to see the fight for dominance in this space already at the home gateway and network management level. As these devices get more numerous and complicated, there will be more consumer oriented ways to manage them. Some of the broadband providers already offer services that will tell what devices are operating in your home and let users control when those various devices are allowed to talk to the Internet.
Since Bloomberg’s story broke, The U.S. Department of Homeland Security and the National Cyber Security Centre, a unit of Britain’s eavesdropping agency, GCHQ, both came out with statements saying they had no reason to doubt vehement denials by Amazon and Apple that they were affected by any incidents involving Supermicro’s supply chain security. Apple also penned a strongly-worded letter to lawmakers denying claims in the story.
Meanwhile, Bloomberg reporters published a follow-up story citing new, on-the-record evidence to back up claims made in their original story.
from Technology News https://krebsonsecurity.com/2018/10/supply-chain-security-101-an-experts-view/
0 notes
Text
5 Best Tips for Budgeting | How to Budget and Save Money Every Month
A tale of 2 jobs
My first job after university was over 10 years ago. I was earning N50,000 monthly at the time, just over $160 in today’s money. Interestingly I always made it to the end of the month with no problem. I had minimal savings, but I was okay.
Then I got another job… with a bank. My salary doubled and I had a fancy new title. Funny thing, now I could hardly get to the 20th of the month without running to my girlfriend for a loan.
Moral of the story? It’s not the size of the paycheck, it’s how you use it.
Over the years and a number of job titles later, I have learnt not only make my money last, but to actually grow it. What’s my secret? A simple habit of budgeting.
Modupe, you say, why bother budgeting when I barely have enough to live on? I’ll start budgeting when I start earning real money.
The best time to budget is before you start to earn a lot of money. Budgeting is a habit that only gets easier over time. So let’s talk about planning your money so you have some left at the end of the month and you can start growing that savings habit you’ve been telling yourself you need to start.
My first tip for budgeting is to Prioritize. In other words, Pay yourself first.One principle that has helped me over the years has been to always pay myself first. Paying myself here refers to investing in myself or in things that I consider really important for my financial future. What are those things that you know you should spend your money on but you always manage to push till next month? Savings, Tithing, investing… Prioritize those above your bills, your meals, or thrills :) Before paying any bills, put the money for those important things aside. Why? Because you know you have to pay your bills or else your electricity gets disconnected, the bank will seize your car or some other creditor will come after you. Unfortunately, no one will harass you to save, give, or invest in anything that will help build your financial future. You have to decide what those things are and start off your monthly spend with those.
Next, invest in paying off your debts. In a country like Nigeria where banks charge interest rates as high as 24%, paying off your debts as quickly and consistently as you can is one of the best investments you can make. See it as a 24% return on investment. After paying any debts, then we can move on to bills, utilities and other essentials. Finally, leave a little something for fun. This will help curb the urge to dip into your savings in future.
Tip number 2 is to Automate. Once you’ve decided the key things you need to spend money on, set up automatic systems to make it easy for you to make the payments. You can do this via Internet banking, cheques, or direct debit instructions to your bank.
Online Transfers
Internet banking is one key tool I use to keep to my budget. For a bank like GTB, you can pre-register some regular recipients like your stock broker or your church so it’s easy to make the monthly transfers any time of the day from the comfort of your bed.
Automatic Withdrawals/Direct Debits
Better yet, if your salary gets paid around the same time each month, you could arrange monthly direct debits with your bank. These are automatic withdrawals that happen on schedule each month without you having to prompt them. It makes it easy to stick to your budget.
Post-dated Cheques
A final option to automate your payments is to issue out post-dated cheques to your stockbroker or banker to be cashed based on a monthly schedule. I used to do this quarterly with my stock broker before I got comfortable with Internet banking; then each month I would follow up with instructions on which stocks to buy.
Tip number 3 is, as much as you can, Pre-Pay i.e. pay for stuff ahead of time. This would usually apply to utility bills and other essentials. For example, I usually pay for at least 3 months internet subscriptions at a time. Also, when renewing essentials like my drivers’ license, instead of going for a 3-year renewal, I do a 5-year renewal. When I do pay for satellite TV subscription, I pay for multiple months. If you can pay multiple years for your rent, please do.Aside the fact that you’re likely to get discounts when you pay in advance, it also means you lock down the rates for that period. As prices hardly ever come down, it’s always good to lock down rates for any regular expense. If you decide you are no longer interested in the service, say for instance, you need to move to another town, you can always get someone else to pay you for the outstanding period. As rentals go up almost every year, it will probably be cheaper for them to do that than to rent somewhere similar afresh.
As a Nigerian, another area you should pre-pay is any expenses in dollars. Not to sound pessimistic or unpatriotic but considering the US dollar remains one of the strongest currencies globally (at least compared to the Naira), paying for a domain name annually means you will be hit by any Naira devaluation within that year. You could easily lock down the rate for 10 years instead.
Another way to pre-pay is with your investments. Let’s try a small exercise. Which is better? Investing N120k in January or investing N10k every month for a year? It’s a trick question. Both are good. While the monthly investment helps you to develop the habit, when you look purely at the earnings, you make more when you invest the sum upfront. So for my friends who receive upfront allowances or bonuses in January, a great habit is to invest a significant chunk of that in a compound interest investment vehicle like money market funds.
However, there are some investments that you don’t really need to go into upfront. An example is shares. While the best time to start investing was yesterday and the 2nd best time to invest is now, there is such a thing as the perfect time to buy shares and there are times when you should just wait.
All this sounds so serious, you say… so when do I get to enjoy my money? Every month. I mentioned this earlier but it deserves a separate point. Tip number 4 is to Budget for fun. Plan for it. Don’t just wait for when you want something to look for the money. That way, you’re less likely to dip into your savings or investments when you want to indulge in a crazy weekend out of town or splurge on that new mobile phone or smart TV.
The only rule here is to make sure this comes last after you have paid for everything else. i.e. maintain the order of priorities. In some cases you may have to put this money aside for a couple of months to afford the intended purchase but trust me, it’s worth it. Your future self will thank you and who knows, a new model of the phone may be out by the time you’re ready to buy.This also conditions your mind to learn to delay gratification. This is one of the most important habits of successful individuals.
My final tip for sticking to your budget is to do something I call Precrastinating. This is what it sounds like, the complete opposite of procrastinating. As much as possible, implement your budget immediately you get paid. Don’t wait a day or 2. Online banking helps a lot here. The reason for this is borrowers lurk & distractions abound. We all have that colleague or friend that always seems to need a soft loan sometime in the month. And while they may pay you back by the end of the month, you have lost out on whatever gains you could have made from investing the money. It’s better your cash is “tied up” in some investments than wasting in the bank. Even a savings account is not a great idea as it’s easy for you to spend it and the returns are not that impressive. Plus some banks only pay you interest on savings accounts if you limit the number of withdrawals in a month. The rule while precrastinating is to make sure you follow your order of prioritization. This is important. Like we said earlier, once you’ve sorted out your giving and investments, you will find a way to resolve other stuff.
Before we end this piece, here’s a little bonus from me to you. I’ll be sharing a breakdown of what my own personal budget looks like. Before I do that, a word on budget management tools. I’m aware there are a number of interesting apps out there but don’t get bugged down or be distracted by this. Honestly all you need, to make and keep a budget, is a notepad and a pen. I designed a simple Microsoft Excel template (https://goo.gl/skJa19) that I’ve used to manage my budget over the years and it allows me to outline everything I spend money on and modify over time as I see fit.
My budget is split in 3 key sections: Giving, Investing, & Spending, split roughly into 30%, 60%, and 10%. Please note that you don’t have to apply these exact percentages to your own budget. The important thing is to have a split that works for you and to stick to it every month.
About 30% of my income goes to giving. This entails what I give as tithes, what I give to my dependents, and what I give to charity. The next 60% goes into my investments. I’ll share a bit more detail here. The 1st item here is my loan payment. And I’ll say why. Paying down on bank loans is the most important investment you can make. I won’t go into why there are bad debts and good debts but once you have any debt with interest rates as high as they are in Nigeria (ranging from 20% to 28%), you should pay them as soon as you can. This is another area where I recommend precrastinating if you can. You’ll notice this is the largest single item in my budget and while I won’t suggest you max out your monthly payments at 30%, see this as an investment with 20-28% return.
Other investments I make include life insurance, savings in safer investment vehicles, more aggressive investments like stocks and lastly foreign currency savings.
The final bit of my income goes to monthly expenses and fun stuff. Some of these are actually not monthly as I try to pay for things like Internet, TV and electricity months ahead.
So those are my 5 best tips to making and keeping your own budget. If this information has been useful to you in any way, please do 3 things for me: share with someone that needs it, subscribe to my channel for more videos like this and most importantly, create your own budget today. Have a good day and remember, It���s not the size of the paycheck, it’s how you use it.
0 notes
Text
IF YOU GO AND SEE ALL THE DIFFERENT KINDS OF THINGS PEOPLE LIKE IN OTHER CULTURES, AND LEARN ABOUT ALL THE DIFFERENT THINGS PEOPLE HAVE LIKED IN THE PAST
Search was now only a small percentage of our page views, less than one month's growth, and now we're talking about the amount of money in one family's bank account, or the idea—or more precisely, the market. Most of them don't try to predict what will win. Really? Certainly not the authors. You don't even let yourself think of such things. Don't raise money unless you want it and it wants you. By looking at their actions rather than their words. Good hackers find it unbearable to use bad tools. In that case, tweak your product and try again. One of the two angel investors who supplied our next round of funding is the one between tools and things made with them. They seemed to have lost their virginity at an average of about 14 and by college had tried more drugs than I'd even heard of. I when Woz first started working on it for many hours at a stretch.
One piece of evidence is what happened to Einstein: Through the reading of popular scientific books I soon reached the conviction that much in the stories of the Bible could not be true. But the more general recipe is: do something founders want. If there are two numbers you care about: how much you're planning to raise a $5 million series A round eventually. If you're an outsider you should actively seek out contrarian projects. Imagine the stress of working for a software company to pay off my college loans. People won't let you. The traditional way to do this was at trade shows. The best way to do that, because in design, as in books, and the more startups there are, and how much stock they each have. Even you yourself, unless you're in a job that feels safe, you are not going to get till the last minute. And if people aren't using your software, you're being offered millions of dollars by famous investors over lunch at a nice restaurant. And of course if Microsoft is your model, you shouldn't be looking for companies that hope to win by doing good work, on an absolute scale, as you would in a big company.
It was not till we were in our twenties that the truth came out: my sister, then about three, had accidentally stepped on the cat and broken its back. You're human. Customers will worry you're going to get nothing. At home, hackers can arrange things themselves so they can continue to learn. I. You can't distinguish your group by doing things that are false, and worse still, the more you depend on it, not written it. Maybe. A company big enough to be fairly conservative, and within the company the people in charge of sales was so tenacious that I used to work till 2:00 or 3:00 AM rather than go to bed leaving code with a bug in it; a PR person who will cold-call New York Times reporters on their cell phones; a graphic designer who feels physical pain when something is two millimeters out of place.
This kind of focus is very valuable, actually. Man-made stuff is different. The founders sometimes think they know. 4 $15,000 investments. If we were talking about the limit case: the case where you not only have zero leisure time but indeed work so hard that working on it can't be preceded by but. The next round of funding at a reasonable valuation; the giant company that was paying for him to go to this extreme. Difficult though it may be implied by imagination. In a specialized society, most of the world's history, if you look at the painting they voted the best would be a byword for bogusness like Milli Vanilli or Battlefield Earth. In this case, the device is the world's economy. The rulers of the technology business tend to come from technology, not business. Our angels asked for one, and looking back, I'm amazed how much worry it caused me.
There are so many essays yet unwritten. But getting bought is also an art in its own right, and I got in reply what was then the party line about it: that Yahoo was no longer a mere search engine. If you're absolutely terrified of starting a company. Lowering your price is a backup plan you resort to when you discover you've let the price get set too high to close all the money change hands at the closing. You don't even let yourself think of such things. When you work on making technology easier to use, so why wouldn't they? It will be easier to raise money before you can convince investors, you'll not only get market price, but you knew there would be no rest for them till they'd signed up. What you notice in the Forbes 400 are a lot of classes there might only be 20 or 30 ideas that were the right shape to make good exam questions. You can measure the value of the company at the point where 90% of a group's output is created by 1% of its members, you lose big if something whether Viking raids, or central planning drags their productivity down to the third ingredient, not giving up. So for the first time in our history, the bullies stopped stealing the nerds' lunch money.
I didn't grasp at the time was that the valuation wasn't just the value of the company being sold. A throbbing headache is not a good thing, but it won't be the sort of person who would like to do but can't. Most startups that fail do it because they feel they have to choose between. But you yourself are the most successful companies we've funded so far, so tentatively assume the path to huge passes through an A round. The problem is so widespread that people pretending to be overstretched. And if the idea of building Facebook in 2004: organic startup ideas, turn your mind into the type that startup ideas form in unconsciously? It's technique. If a fairly good hacker is worth $80,000 worth of work per year for the company just to break even.
Now, thanks to the Internet, they can change their mind about later when they start to think of yourself as rich there's some amount that would be painless, though annoying, to lose. People who don't want to. Starting a startup will change you a lot. But among the many other things I was ignorant of was how much debris there already was in my head. Not just because of its prestige, but because the principles underlying the most dynamic part of the economy will balloon in the usual fractal way. If you have to know physics to be a big success and hardly at all on price. But when phrased in terms of that number.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#mind#worth#books#worry#Milli#point#business#way#questions#projects#case#output#words#lunch#planning#money#month#things#funding#stuff#growth#reading#device#scale
1 note
·
View note
Text
Usability is everything about your thing
Especially the stuff people can’t see
There’s a bit of a meme when it comes to usability (both UI and UX in my usage here) that it’s limited to the visible bits. The buttons, the windows, how they work, why they work. Thinking that if you are a non-programmer, or non-technical user is okay, well, more okay in the latter. It’s not your job to think any different.
But when programmers think this, or PMs or anyone involved with creating software…things that shouldn’t happen often do.
Take, for example, OneDrive from Microsoft. Now, I like OneDrive, a lot. I use the hell out of it. But tonight, I hit a series of issues that honestly, just shouldn’t have happened.
The Problem
So, recently, I’d decided to copy my “AppleScript” folder into my OneDrive folder. I got to work, and within a few days, realized that it hadn’t yet shown up there, which was a bit odd, as it’s not that big. Really, it’s well under a gig, right around 236MB. It’s also one of the oldest folders I have. Parts of it contain scripts and notes from the late 90s. For example, “LaserWriter 8.7 Scripting”.
Like I said, it’s old, and it has a structure that has worked, and still does work for me. Since I am the only person it has to work for, it is a proper structure in the only sense that matters.
So tonight, I fire up OneDrive, and I see it’s chugging along, but in the menu, I see a line item that I’ve not really seen before. Something about “Details”. I forget the exact wording. “Huh…that’s odd” I think “Well, let’s see what it has to say”.
What it really is, is a list of errors. around 70 or so all complaining that I’ve committed sins in the OneDrive world. So right now, let’s see: there’s a thing that wants to tell me about errors, but instead of saying “Errors”, it says something about “Details”. That’s bad usability. It’s not giving me the information I need, (There are problems you must attend to for this sync to work right), but rather some platitude that could have led me to ignore it completely.
That’s not what you want when there’s an error requiring user action. I’m not saying it needs something like the old DS_Dialog on System 7, (forgive me if I get the name a bit wrong, it’s been a while), but when an error happens, maybe actually say “Errors”. Using that word.
The initial problems are that I had illegal characters in my file names.
Pardon me while I let Capt. Sisko illusrate how I feel about such a problem in 2015:

i’m totes a DS9 fan. Who else would I use?
Seriously, here’s the list. Note that it explicitly excludes .ds_store files. That tend to be everywhere on OS X systems, especially when used by someone like me. Who wrote a book on OS X Server when it still looked like OpenStep.
You also can’t start a file with a period or a space. Because no one on a Mac would ever do that.

Screw it, I put the GIF in here too. Because this entire thing is nothing but facepalm.
Also, no, I don’t have “illegal” characters in my file names. The characters I have are perfectly legal in OS X. Otherwise I couldn’t use them. So not only am I getting penalized for doing nothing wrong in my environment, but it’s by third party software from a dev, Microsoft, that honestly knows better.
This is inarguable. I know at least one person on the OneDrive team from Microsoft MacBU betas in the pre-(Mac) OS X world. Seriously, they have the knowledge and expertise to do this kind of thing correctly. That is not an issue. Also, not naming names, I actually like this person.
So I have the “handy” dialog with this information and I go along fixing the “problems”. Does the list update as I do so? Nope. In fact, as far as I can tell, the only way to update the list is to restart OneDrive. Oh, and as the list updates, it hides the item I’m currently changing.
I’m not going to call it fixing. It wasn’t broke. I’m changing it due to an arbitrary, or mostly arbitrary requirement from another dev. That’s not “fixing”.
So I have to click along the list and the only way I know that I’ve already changed the filename is that when I click the magnifying glass icon, nothing happens. Awesome.
But then we hit a “real” error. It seems that I have committed, literally, an unpardonable sin: I have files whose full file and path name contain too many characters. When this happens in OneDrive, you have exactly two options. You can quit OneDrive (and presumably change the path or filename so as there are not “too many” characters) or you can point OneDrive at another folder that is not burdened with this problem.

Are

You

FUCKING kidding me?
So this one really bugged me, (because hello, can’t get stuff done) and after a bit of poking, this isn’t an OS X issue. It’s a Windows issue involving older APIs or something. I didn’t look in detail, because honestly, it’s not my problem. I’ve done exactly nothing wrong. All these issues are not an issue on the platform where these files live.
They’re an issue on a platform or platforms where they may live. But what I don’t get is why I can’t sync my stuff at all with the path issues or why the “illegal” characters are preventing me from syncing to OneDrive.
Let me explain: with OneDrive (or DropBox or any of the others) there are (basically) two stages to syncing.
You add a file to a local folder. That file or files are then replicated up to “the cloud” or wherever the server may be.
Those file(s) are then replicated to other clients participating in the sync.
It can and is a bit more complex in terms of implementation, but the basic flow chart is two steps. Sync up. Sync down.
Look, if there’s some whackaloon issue with the Windows OneDrive client or Windows itself, I would totally understand why I couldn’t sync these files down from OneDrive to a Windows box. I wouldn’t like it because again 2015, but I would understand it with the caveat that I expect this to be fixed and pronto.
But I cannot, indeed, I refuse to understand why I can’t sync any “legal” file on my Mac up to OneDrive. As long as there’s space, and the file is legit for OS X, (which it would kind of have to be) then don’t be dumb. Let me sync it up. If this is only a problem for Windows clients, let that be dealt with there. Don’t give the good little kids coal because Timmy’s being an asshat. Let Timmy suck carbon at christmas, I want my damned G.I. Joe with the Kung-Fu Deathgrip!
UPDATE: Upon trying to sync this folder down to another Mac, I had to move the OneDrive folder on that machine to the root of my home directory. Which of course required…re-running the OneDrive setup.

Really?
This is some seriously stupid usability problems, and I don’t say “stupid” lightly. It may indeed be a complicated problem on Windows but it shouldn’t be a problem at all on OS X. And if the problem is with OneDrive’s cloud components, then stop using tinkertoy servers.
(Before the “you don’t understand <thing>” crew charges in...long ago, before Mac OS X, I helped the folks who make the Rumpus FTP Server figure out how to handle > 31-character filenames on MacOS *8*. Which literally did not support that. But, we figured out a way to make it work because we had a lot of unix people who were not down with piddly 31-character filename restrictions. I “understand” things pretty damned well.)
I have done nothing wrong, but I just had to do a bunch of bullshit work because someone or a lot of someones weren��t thinking correctly. I was punished, and I did nothing wrong. This is all OneDrive’s fault. Because their usability has real issues, I had to change something that works correctly.
I’ll probably have to build a friggin’ script to “OneDrive-Proof” my files in the future, just to avoid this kind of dumb. Will Microsoft pay me for my time spent working around their bad usability? Don’t be silly, of course they won’t.
Had someone made this kind of “invisible” usability more important, this wouldn’t be a problem. But because it wasn’t a priority, it is, and from what I can tell, has been for more than a few years. Clearly, the OneDrive team’s priorities are not aligned with mine.
This should have never happened. I shouldn’t have to care about such things. But with bad usability, you have to care. And sometimes, caring sucks. Don’t just limit usability to the stuff you can see. Bad usability will make your product suck, and why would you want that?
0 notes
Text
Shitcoin of the Week: Top Secret!
Shitcoin of the Week: Top Secret!
Coinstaker is very pleased to announce that this week, we’re covering the smelliest shitcoin of all. If Skycoin had an ugly paint job, and Tronix has a used-car vibe, this one’s the roaring dumpster fire of the cryptocurrency world: a toxic, fuming wreckage of bad code and worse management with no benefits other than to make the rest of us feel better about our tanking portfolios.
Unfortunately, due to complicated restrictions involving a Top Secret clearance and a pinky swear with my very real Canadian girlfriend, we can’t disclose this week’s stinker just yet. Before we reveal the Shitcoin of the week, we need to raise at least 3 million dollars in to make this project work.
Please donate to the address below so we can reveal this exciting crypto-turd.
ETH Address.
Did you donate yet? We can’t reveal anything until we meet our fundraising goal.
Please Donate here.
Okay, good. Surprise! The shitcoin of the week is: Verge.
Verge-in Birth
Verge(XVG) is the youngest sibling in the family of “privacy coins,” the projects designed to safeguard the secrecy and anonymity of their users. Whereas Bitcoin and Ethereum have public ledgers, allowing sufficiently-motivated busybodies to theoretically deduce who owns what, these coins help you hide your wealth from the IRS, the police, and your wife.
There are couple of different ways to do that. Monero, the preferred medium for darknet drug dealers, uses enhanced encryption to disguise addresses and transaction volumes. Dash PrivateSend allows coins from multiple transactions to be mixed for greater anonymity. Verge uses Tor, the IP masking system used by Dark Net Markets, Chinese activists and other cyber-miscreants.
As described in the XVG Black Paper(an admittedly clever bit of branding) Verge hides a users’ identity by island-hopping their transactions through a chain of nodes. There’s also the Wraith protocol, which gives users the choice of recording transactions on a public or private ledger.
Incidentally, Verge is also French for “penis,” a word we expect to appear on the XVG website in the coming weeks.
Brown Flag No. 1: The Dog Keeps Eating Their Code
Most of us learned about Verge after its first bull run last fall. To novice investors, XVG was crypto-catnip: it was cheap, had just mooned spectacularly, and had a heavy shilling from John McAfee, the L. Ron Hubbard of cryptocurrency. And it had just announced the Wraith Protocol, about which we knew nothing except that it had a really cool name.
I immediately decided to throw some money at it, but a gut feeling held me back. Maybe it was the cultish shilling and endless Lambo-talk, but for some reason I decided to wait and see what the Nazgul money had to offer.
Then the Wraith protocol took a sickday. Then it was delayed by bugs. By the time it finally did come out, Verge looked like the digital equivalent of a guy selling speakers from the back of a van.
Brown Flag No. 2: Don’t Give your Money to Someone Who Won’t Tell You their Real Name
“Officer, that’s the man who ran off with my money. The cartoon character with the glasses. His name is SpookyKid.”
Verge is brought to you by “Sunerok,” which sounds like the Bizarro-world equivalent of Justin Sun.Apparently it’s a pseudonym for Justin Vendetta–I say “apparently,” because Vendetta sounds as much like a real name as Sunerok.
“Sunerok’s” other colleagues include such distinguished crypto-luminaries as “SpookyKid” and “CryptoRekt,” as well as a team of identical grey silhouettes with names like “Yakuza112” and “XVGMonk.”
We’ve harped on this before, and not just because fake names make you look dumb. Having real names is an important sign of a projects’ security: it’s much harder to pull off a scam on people who know where you live.
Brown Flag No. 3: Don’t Trust a Locksmith Who Keeps His Key Under The Doormat
There are two things almost everyone should learn before they’re allowed near a computer. The first lesson, which I learned the hard way, is that you should always use Incognito Mode so that you don’t spend your teenage years with a therapist who specializes in cat porn.
Only slightly less important is to protect your passwords. That’s why you need twelve different alphabets just to get into your email. Usually when you hear about someone famous getting hacked, it’s because all of their passwords are “Guest.”
So it was a pretty bad sign when Verge—”The future of privacy”—got its Twitter account hijacked like a teenagers’ Instagram.
Sunerok would later shift the blame to Yahoo, saying the hackers exploited a leaked database. The fact that a leading cryptocurrency developer is using Yahoo in the first place should be a pretty big warning sign by itself.
At least he wasn’t the only idiot in the room.
Urgent: My account was hacked. Twitter has been notified. The coin of the day tweet was not me. As you all know… I am not doing a coin of the day anymore!!!!
— John McAfee (@officialmcafee) December 27, 2017
Brown Flag No. 3: Please Contribute To Our Moon Fund
Most of the cryptocurrency world was ready to give XVG the benefit of the doubt. Sure, they had some green programmers, but they’d put too much work into it to exit scam. And then:
….A global organization with a vast network of high traffic sites is looking to enter the cryptocurrency market and form a strategic business alliance with Verge as the preferred form of secure payment method, offering a quick and private means of transaction to hundreds of millions of potential consumers daily. This partnership represents an enormous potential market with a global reach that will compete with multiple fiat currencies. We are eager to see this partnership materialize and invite everyone in the Verge community to support this groundbreaking initiative. Help us accelerate this crowdfunding effort and reach our target by donating coins today.
That’s the future of money, rattling a tin cup and promising to make you rich. In other words, your Verge could be the new Bitcoin—but only if you give us more money.
Justin Sunerok’s fundraising strategy. I mean, Justin Vendetta. How is that a real name?
This is textbook Nigerian prince-ing, almost as sketchy as the time Elon Musk promised to send me ten Ethereum. He still hasn’t paid me back, but hopefully the Binance guy will pull through.
“……..and the worst part is, I signed an NDA so I can’t tell anybody yet who we have this massive potential partnership yet with is….”
The secret “partnership” attracted wide speculation within the Verge community, and wider ridicule outside of it. Could it be Amazon? Microsoft? Or some fake shell corporation in the Bahamas? After much well-deserved roasting Bizarro-Justin produced the following, totally credible explanation, courtesy of his rectum:
We were talking about doing a crowdfund to get Verge supported on Ledger Nano, and uhhh, then I got an email from somebody at a big company, and uhh, they said, “hey, we’ve been checking out cryptocurrencies for the last few months and we really like Verge. Can you come talk to us?” And I said, sure. And I met up with them, everything kind of worked out, and they said, “alright, if you guys can raise the funds to cover the integration and some marketing and stuff, we can make this all happen.”….and the worst part is, we signed an NDA so I can’t tell anybody yet who we have this massive potential partnership yet with is.
And later:
” I think that this is the largest adoption of a non-top three coin to ever happen. It could be the largest adoption of a virtual cryptocurrency ever…..”
The secret to a good lie is making it believable, but Justin can’t even get that part right. Can anyone imagine a conversation like this happening in a real business run by grownups?
CEO: “We’ve decided to make our foray into cryptocurrency. As you know, this is a high-stakes business deal and we can only partner with the most sophisticated, professional development teams. We certainly can’t endanger our brand with a second rate partnership. How’s the research going?
Minion: “Well boss, there’s Bitcoin, but the fees are kind of high and its market dominance is slipping. Plus we have no idea if the Lightning Network’s going to work. We could try partnering with Ethereum, it’s not had quite as much time to prove itself but the market cap has grown by quite a lot. There’s one called Dash too..”
Boss: “Dash is out, they’re wasting their money on some sci fi show. Any other promising contenders in the top ten?”
Minion: “Well, there’s one called Bitcoin Cash, which forked from Bitcoin last year.
BOSS: “Bcash. LOL. What else? Anything in the top twenty?”
M:“No, but according to John McAfee there’s a one-year old privacy coin developed by volunteers. It’s unproven, doesn’t actually offer any real privacy, and keeps missing deadlines. It’s called Verge.
BOSS:“That’s just the kind of project we’re looking for! Let’s just hope they don’t get hacked in the next few days.”
Brown Clouds on the Horizon
Any doubts or reservations about XVG’s toilet quality should have been flushed away last week:
We had a small hash attack that lasted about 3 hours earlier this morning, it's been cleared up now. We will be implementing even more redundancy checks for things of this nature in the future! $XVG #vergefam
— vergecurrency (@vergecurrency) April 4, 2018
The “small” attack, which actually lasted for thirteen hours, exploited a loophole in Verge’s rules which allowed the hacker to successfully mine empty blocks in less than a second. Sunerok did not address the hack until it was discussed on Bitcointalk.
Instead of forking back to a pre-attack state, Sunerok panicked and pushed an update to the node software. The update caused an unexpected hard fork, which paralyzed the network, froze many users’ wallets and allowed the hackers to walk away with a million dollars in tokens.
Paradoxically, XVG tokens continued to soar on most exchanges, for the simple reason that the tokens were still impossible to move.
As usual, Verge downplayed the enormity of their fuckup while continuing to upsell their “groundbreaking” partnership. Meanwhile, somewhere in Silicon Valley, we can only guess what when down with Verge’s totally-real partnership when the protocol’s Swiss-cheese security was revealed.
Diagnosis: Get your Umbrella
Until recently, even the deepest skeptics didn’t really question the honesty of the Verge team. Although it had all the signs of a naive project by get-rich-quick amateurs, there was no reason to think it was an intentional scam.
That perception changed as the Verge team alternated between bungling their software and deceiving their investors. Their inability to demonstrate any technical skill–besides digging their hole deeper–make us wonder if they hired Firano the Bomber to help with the coding.
The mystery hack also set off alarm bells, and not just because of the shitty coding. The timing of the attack–and the strange decision to let the “hacker” walk with the coins–seem to echo the bad omens that foreshadowed the collapses of Mt Gox, BitGrail, BitConnect, Davorcoin and many bigger projects.
The only way to improve this project would be to exit scam, which at least would prove that Bizarro-Justin can get one thing right. On a scale of one to BitConnect, Verge gets a score of Nine Carlos.
Seriously. Get out while you can.
https://ift.tt/2ITHZ1n
0 notes
Text
Shitcoin of the Week: Top Secret!
Shitcoin of the Week: Top Secret!
Coinstaker is very pleased to announce that this week, we’re covering the smelliest shitcoin of all. If Skycoin had an ugly paint job, and Tronix has a used-car vibe, this one’s the roaring dumpster fire of the cryptocurrency world: a toxic, fuming wreckage of bad code and worse management with no benefits other than to make the rest of us feel better about our tanking portfolios.
Unfortunately, due to complicated restrictions involving a Top Secret clearance and a pinky swear with my very real Canadian girlfriend, we can’t disclose this week’s stinker just yet. Before we reveal the Shitcoin of the week, we need to raise at least 3 million dollars in to make this project work.
Please donate to the address below so we can reveal this exciting crypto-turd.
ETH Address.
Did you donate yet? We can’t reveal anything until we meet our fundraising goal.
Please Donate here.
Okay, good. Surprise! The shitcoin of the week is: Verge.
Verge-in Birth
Verge(XVG) is the youngest sibling in the family of “privacy coins,” the projects designed to safeguard the secrecy and anonymity of their users. Whereas Bitcoin and Ethereum have public ledgers, allowing sufficiently-motivated busybodies to theoretically deduce who owns what, these coins help you hide your wealth from the IRS, the police, and your wife.
There are couple of different ways to do that. Monero, the preferred medium for darknet drug dealers, uses enhanced encryption to disguise addresses and transaction volumes. Dash PrivateSend allows coins from multiple transactions to be mixed for greater anonymity. Verge uses Tor, the IP masking system used by Dark Net Markets, Chinese activists and other cyber-miscreants.
As described in the XVG Black Paper(an admittedly clever bit of branding) Verge hides a users’ identity by island-hopping their transactions through a chain of nodes. There’s also the Wraith protocol, which gives users the choice of recording transactions on a public or private ledger.
Incidentally, Verge is also French for “penis,” a word we expect to appear on the XVG website in the coming weeks.
Brown Flag No. 1: The Dog Keeps Eating Their Code
Most of us learned about Verge after its first bull run last fall. To novice investors, XVG was crypto-catnip: it was cheap, had just mooned spectacularly, and had a heavy shilling from John McAfee, the L. Ron Hubbard of cryptocurrency. And it had just announced the Wraith Protocol, about which we knew nothing except that it had a really cool name.
I immediately decided to throw some money at it, but a gut feeling held me back. Maybe it was the cultish shilling and endless Lambo-talk, but for some reason I decided to wait and see what the Nazgul money had to offer.
Then the Wraith protocol took a sickday. Then it was delayed by bugs. By the time it finally did come out, Verge looked like the digital equivalent of a guy selling speakers from the back of a van.
Brown Flag No. 2: Don’t Give your Money to Someone Who Won’t Tell You their Real Name
“Officer, that’s the man who ran off with my money. The cartoon character with the glasses. His name is SpookyKid.”
Verge is brought to you by “Sunerok,” which sounds like the Bizarro-world equivalent of Justin Sun.Apparently it’s a pseudonym for Justin Vendetta–I say “apparently,” because Vendetta sounds as much like a real name as Sunerok.
“Sunerok’s” other colleagues include such distinguished crypto-luminaries as “SpookyKid” and “CryptoRekt,” as well as a team of identical grey silhouettes with names like “Yakuza112” and “XVGMonk.”
We’ve harped on this before, and not just because fake names make you look dumb. Having real names is an important sign of a projects’ security: it’s much harder to pull off a scam on people who know where you live.
Brown Flag No. 3: Don’t Trust a Locksmith Who Keeps His Key Under The Doormat
There are two things almost everyone should learn before they’re allowed near a computer. The first lesson, which I learned the hard way, is that you should always use Incognito Mode so that you don’t spend your teenage years with a therapist who specializes in cat porn.
Only slightly less important is to protect your passwords. That’s why you need twelve different alphabets just to get into your email. Usually when you hear about someone famous getting hacked, it’s because all of their passwords are “Guest.”
So it was a pretty bad sign when Verge—”The future of privacy”—got its Twitter account hijacked like a teenagers’ Instagram.
Sunerok would later shift the blame to Yahoo, saying the hackers exploited a leaked database. The fact that a leading cryptocurrency developer is using Yahoo in the first place should be a pretty big warning sign by itself.
At least he wasn’t the only idiot in the room.
Urgent: My account was hacked. Twitter has been notified. The coin of the day tweet was not me. As you all know… I am not doing a coin of the day anymore!!!!
— John McAfee (@officialmcafee) December 27, 2017
Brown Flag No. 3: Please Contribute To Our Moon Fund
Most of the cryptocurrency world was ready to give XVG the benefit of the doubt. Sure, they had some green programmers, but they’d put too much work into it to exit scam. And then:
….A global organization with a vast network of high traffic sites is looking to enter the cryptocurrency market and form a strategic business alliance with Verge as the preferred form of secure payment method, offering a quick and private means of transaction to hundreds of millions of potential consumers daily. This partnership represents an enormous potential market with a global reach that will compete with multiple fiat currencies. We are eager to see this partnership materialize and invite everyone in the Verge community to support this groundbreaking initiative. Help us accelerate this crowdfunding effort and reach our target by donating coins today.
That’s the future of money, rattling a tin cup and promising to make you rich. In other words, your Verge could be the new Bitcoin—but only if you give us more money.
Justin Sunerok’s fundraising strategy. I mean, Justin Vendetta. How is that a real name?
This is textbook Nigerian prince-ing, almost as sketchy as the time Elon Musk promised to send me ten Ethereum. He still hasn’t paid me back, but hopefully the Binance guy will pull through.
“……..and the worst part is, I signed an NDA so I can’t tell anybody yet who we have this massive potential partnership yet with is….”
The secret “partnership” attracted wide speculation within the Verge community, and wider ridicule outside of it. Could it be Amazon? Microsoft? Or some fake shell corporation in the Bahamas? After much well-deserved roasting Bizarro-Justin produced the following, totally credible explanation, courtesy of his rectum:
We were talking about doing a crowdfund to get Verge supported on Ledger Nano, and uhhh, then I got an email from somebody at a big company, and uhh, they said, “hey, we’ve been checking out cryptocurrencies for the last few months and we really like Verge. Can you come talk to us?” And I said, sure. And I met up with them, everything kind of worked out, and they said, “alright, if you guys can raise the funds to cover the integration and some marketing and stuff, we can make this all happen.”….and the worst part is, we signed an NDA so I can’t tell anybody yet who we have this massive potential partnership yet with is.
And later:
” I think that this is the largest adoption of a non-top three coin to ever happen. It could be the largest adoption of a virtual cryptocurrency ever…..”
The secret to a good lie is making it believable, but Justin can’t even get that part right. Can anyone imagine a conversation like this happening in a real business run by grownups?
CEO: “We’ve decided to make our foray into cryptocurrency. As you know, this is a high-stakes business deal and we can only partner with the most sophisticated, professional development teams. We certainly can’t endanger our brand with a second rate partnership. How’s the research going?
Minion: “Well boss, there’s Bitcoin, but the fees are kind of high and its market dominance is slipping. Plus we have no idea if the Lightning Network’s going to work. We could try partnering with Ethereum, it’s not had quite as much time to prove itself but the market cap has grown by quite a lot. There’s one called Dash too..”
Boss: “Dash is out, they’re wasting their money on some sci fi show. Any other promising contenders in the top ten?”
Minion: “Well, there’s one called Bitcoin Cash, which forked from Bitcoin last year.
BOSS: “Bcash. LOL. What else? Anything in the top twenty?”
M:“No, but according to John McAfee there’s a one-year old privacy coin developed by volunteers. It’s unproven, doesn’t actually offer any real privacy, and keeps missing deadlines. It’s called Verge.
BOSS:“That’s just the kind of project we’re looking for! Let’s just hope they don’t get hacked in the next few days.”
Brown Clouds on the Horizon
Any doubts or reservations about XVG’s toilet quality should have been flushed away last week:
We had a small hash attack that lasted about 3 hours earlier this morning, it's been cleared up now. We will be implementing even more redundancy checks for things of this nature in the future! $XVG #vergefam
— vergecurrency (@vergecurrency) April 4, 2018
The “small” attack, which actually lasted for thirteen hours, exploited a loophole in Verge’s rules which allowed the hacker to successfully mine empty blocks in less than a second. Sunerok did not address the hack until it was discussed on Bitcointalk.
Instead of forking back to a pre-attack state, Sunerok panicked and pushed an update to the node software. The update caused an unexpected hard fork, which paralyzed the network, froze many users’ wallets and allowed the hackers to walk away with a million dollars in tokens.
Paradoxically, XVG tokens continued to soar on most exchanges, for the simple reason that the tokens were still impossible to move.
As usual, Verge downplayed the enormity of their fuckup while continuing to upsell their “groundbreaking” partnership. Meanwhile, somewhere in Silicon Valley, we can only guess what when down with Verge’s totally-real partnership when the protocol’s Swiss-cheese security was revealed.
Diagnosis: Get your Umbrella
Until recently, even the deepest skeptics didn’t really question the honesty of the Verge team. Although it had all the signs of a naive project by get-rich-quick amateurs, there was no reason to think it was an intentional scam.
That perception changed as the Verge team alternated between bungling their software and deceiving their investors. Their inability to demonstrate any technical skill–besides digging their hole deeper–make us wonder if they hired Firano the Bomber to help with the coding.
The mystery hack also set off alarm bells, and not just because of the shitty coding. The timing of the attack–and the strange decision to let the “hacker” walk with the coins–seem to echo the bad omens that foreshadowed the collapses of Mt Gox, BitGrail, BitConnect, Davorcoin and many bigger projects.
The only way to improve this project would be to exit scam, which at least would prove that Bizarro-Justin can get one thing right. On a scale of one to BitConnect, Verge gets a score of Nine Carlos.
Seriously. Get out while you can.
https://ift.tt/2v5U6WS
0 notes