#data privacy awareness
Photo

Read an article by the civic technology organization Pollicy to learn about the biggest challenges to digital rights for women and discover the different ways to advance women’s digital rights!
👉 http://bit.ly/3YJkUpb
📸 by Gayatri Malhotra on Unsplash
#digital rights#digital activism#digital privacy#digital security#internet freedom#save the internet#internet security#net neutrality#internet shutdown#online privacy#privacy#online safety#cybersecurity awareness#technology#open data#data security#disinformation#misinformation#censorship#free expression#surveillance#women’s rights#feminist#feminism
105 notes
·
View notes
Text
Privacy is a fundamental human right
Privacy is widely considered a fundamental human right. It is recognized and protected by various international and regional human rights treaties and declarations, such as the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights. Privacy is essential for individuals to exercise their autonomy, maintain personal dignity, and freely express themselves without fear of surveillance or intrusion.
Privacy encompasses the right to control one's personal information, the right to be free from unwarranted surveillance, and the right to privacy in one's home, communications, and personal activities. It also includes the right to protect sensitive personal data from unauthorized access, use, or disclosure.
In an increasingly digital world, privacy concerns have become more prominent due to technological advancements and the vast amount of personal information being collected, stored, and shared. Protecting privacy in the digital age is crucial to safeguarding individuals' rights and preventing abuses of power.
Governments, organizations, and individuals have a responsibility to respect and uphold privacy rights. However, striking a balance between privacy and other societal interests, such as public safety or national security, can be a complex challenge that requires careful consideration and legal frameworks to ensure that privacy rights are not unjustifiably infringed upon.
#PrivacyRights#HumanRights#DataProtection#DigitalPrivacy#PersonalAutonomy#Surveillance#InformationSecurity#today on tumblr#deep thoughts#Privacy Laws#Right to Privacy#Privacy Policy#Data Privacy#Online Privacy#Privacy Advocacy#Privacy Awareness#Privacy Breach#Privacy Concerns#Privacy Legislation#Privacy Practices#Privacy Protection#Privacy Rights Activism#Privacy Safeguards#Privacy Violations#Privacy Ethics#Privacy and Technology#Privacy Best Practices#Privacy Education#Privacy Transparency
11 notes
·
View notes
Text
I keep seeing that post that’s like “everything should be open source, cars don’t weld the hoods shut so you can’t look at the engines” and while I get what the post is trying to say the metaphor always throws me bc cars def straight up have a bunch of embedded computer units in them w a lot of inaccessible source code
#there’s also like. the terminology gripe about what ‘open source’ means#but that one is just a matter of definition#I gen think of open source as code that you can see and modify#not just code that you can see#and while I agree with the sentiment that source code should be transparent I don’t necessarily agree it should always be modifiable#so I wouldn’t call for ‘open source’ i would call for ‘transparency’#but that’s just a matter of personal definitions#456 words#also ye it’s nbd regarding the post but I do think people should be more generally aware#that cars have computers in them#esp when it comes to questions of data privacy and computer security
2 notes
·
View notes
Text
Perhaps this is the bipartisan issue we have been looking for? People of all backgrounds giving the finger to AI fetishists and tech bros?
#ai art is not art#wga strong#sag aftra#also im fully aware of other issues with ai#like data privacy and misinformation#this just happens to be the more personal one to me#and will fully advocate for strict AI regulations#and expanded copyright laws protecting IPs from ai#ai artwork#ai#ai art
5 notes
·
View notes
Text
Every tech person that promotes a subscription-based social media, or even a one-time-payment monetization method, needs to lose all their money and go home and rethink their life.
#i am aware that their argument is more privacy because there wont be ads.#however#i think that maybe we shouldnt hsve to pay to have basic privacy and data protection#sorry for tech posting but im not actually#finn's flailings
3 notes
·
View notes
Text
i hate seeing people now making fun of those who care about privacy online. i've seen people saying things like "well they already have your data. what are companies going to do with it" and it's like, that's not the point. it's that companies /shouldn't/ be able to have my data and sell it. am i aware they probably already have my data? yes, absolutely. but i'm still going to try and keep them from monetizing it any further, why are we defending companies selling data they shouldn't have to begin with though?
60K notes
·
View notes
Text
Prepaid Cards Revolutionize Cashless Dining in Food Courts

Introduction to Prepaid Cards
In today's fast-paced world, convenience is paramount, especially when it comes to dining out. Prepaid cards have emerged as a revolutionary solution, offering a seamless and efficient way to enjoy cashless dining experiences. The concept of prepaid cards is not new, but their integration into food courts has sparked a significant shift in consumer behavior.
Cashless Dining Trends
The global trend towards cashless transactions has gained momentum in recent years, driven by advancements in technology and changing consumer preferences. In food courts, where speed and convenience are key, the adoption of cashless payment methods has become increasingly prevalent.
Challenges in Traditional Payment Methods
Traditional payment methods, such as cash or credit/debit cards, pose several challenges in food court settings. Cash transactions can lead to long queues and delays, while credit/debit card payments may be inconvenient for both consumers and vendors due to processing fees and minimum purchase requirements.
The Emergence of Prepaid Cards in Food Courts
To address these challenges, food courts are embracing prepaid card systems, revolutionizing the way customers pay for their meals. By preloading funds onto a card, customers can enjoy quick and hassle-free transactions, eliminating the need for cash or physical cards.
How Prepaid Cards Work
Prepaid cards operate on a simple premise: customers load funds onto their cards either online or at designated kiosks within the food court. They can then use these funds to make purchases at any participating vendor within the food court.
Advantages of Prepaid Cards in Food Courts
The benefits of prepaid cards in food courts are manifold. For consumers, they offer unmatched convenience and speed, allowing them to make purchases with a simple tap or swipe. Additionally, prepaid cards provide consumers with greater control over their spending, helping them stick to their budgets more effectively.
For food court operators, prepaid cards streamline transaction processing, reducing wait times and enhancing overall efficiency. By centralizing payments through a single platform, vendors can also gain valuable insights into consumer behavior and preferences, enabling them to tailor their offerings accordingly.
Enhanced Customer Experience
One of the key advantages of prepaid cards in food courts is the enhanced customer experience they provide. By minimizing wait times and offering seamless transactions, prepaid cards ensure that customers spend less time queuing and more time enjoying their meals.
Moreover, prepaid cards enable food court operators to implement customized loyalty programs, rewarding customers for their continued patronage. By offering incentives such as discounts or freebies, operators can further enhance the overall dining experience and foster customer loyalty.
Security and Safety Measures
Security is a top priority in any payment system, and prepaid cards are no exception. With robust encryption protocols and built-in fraud detection mechanisms, prepaid card systems offer consumers peace of mind knowing that their financial information is safe and secure.
Additionally, prepaid cards eliminate the need for consumers to carry large amounts of cash, reducing the risk of theft or loss. In the event that a card is lost or stolen, most prepaid card providers offer 24/7 customer support and the ability to freeze or deactivate the card remotely.
Adoption and Acceptance
The adoption of prepaid cards in food courts is steadily increasing, driven by the growing demand for cashless payment options. As more consumers become accustomed to the convenience and benefits of prepaid cards, food court vendors are increasingly recognizing the need to offer these payment methods to remain competitive.
Impact on Business Operations
From a business perspective, the integration of prepaid card systems can have a transformative impact on operations. By automating transaction processing and streamlining administrative tasks, vendors can reduce overhead costs and improve overall efficiency.
Moreover, prepaid card systems provide vendors with valuable data insights, allowing them to track sales trends, identify popular menu items, and target specific customer demographics more effectively. This data-driven approach enables vendors to make informed decisions that drive business growth and profitability.
Future Trends and Innovations
Looking ahead, the future of prepaid cards in food courts looks promising, with continued advancements in technology driving innovation and customization. From mobile payment solutions to personalized loyalty programs, vendors are constantly seeking new ways to enhance the customer experience and stay ahead of the competition.
Challenges and Concerns
Despite the many benefits of prepaid cards, there are also challenges and concerns that must be addressed. Chief among these is the need to ensure consumer privacy and data security. As prepaid card systems become more sophisticated, it is essential for vendors to implement robust privacy policies and security measures to protect customer information.
Additionally, accessibility remains a concern for some consumers, particularly those who may not have access to smartphones or digital payment methods. To address this issue, food courts must ensure that alternative payment options are available to accommodate all customers.
Case Studies and Success Stories
Numerous food courts around the world have already embraced prepaid card systems with great success. From small-scale vendors to large multinational chains, businesses of all sizes have reported significant improvements in transaction processing times, customer satisfaction, and overall revenue.
For example, a recent case study conducted by a major food court operator found that the implementation of prepaid card systems resulted in a 30% increase in sales and a 20% reduction in wait times. These impressive results demonstrate the tangible benefits that prepaid cards can
offer to both consumers and businesses alike.
Consumer Education and Awareness
Despite the growing popularity of prepaid cards, there is still a need for consumer education and awareness. Many consumers may be unfamiliar with how prepaid cards work or may have misconceptions about their usage and benefits. As such, food courts must invest in educational campaigns to inform consumers about the advantages of prepaid cards and how to use them effectively.
Conclusion
In conclusion, prepaid cards are revolutionizing the way consumers pay for their meals in food courts. By offering unmatched convenience, speed, and security, prepaid cards are transforming the dining experience for both customers and vendors alike. As the adoption of prepaid cards continues to grow, food courts are poised to reap the benefits of improved efficiency, increased revenue, and enhanced customer satisfaction.
We hope you enjoyed reading our blog posts about food court billing solutions. If you want to learn more about how we can help you manage your food court business, please visit our website here. We are always happy to hear from you and answer any questions you may have.
You can reach us by phone at +91 9810078010 or by email at [email protected]. Thank you for your interest in our services.
FAQs
1. Are prepaid cards accepted at all vendors in the food court?
Yes, prepaid cards can typically be used at any participating vendor within the food court.
2. Can I reload funds onto my prepaid card?
Yes, most prepaid card systems allow users to reload funds either online or at designated kiosks within the food court.
3. Is my personal information secure when using a prepaid card?
Yes, prepaid card systems employ robust security measures to protect customer information and prevent unauthorized access.
4. Are there any fees associated with using a prepaid card?
Some prepaid card providers may charge nominal fees for certain services, such as reloading funds or replacing lost or stolen cards.
5. Can I earn rewards or loyalty points with a prepaid card?
Yes, many prepaid card systems offer rewards or loyalty programs that allow users to earn points or discounts on their purchases.
#prepaid cards#cashless dining#food courts#payment methods#prepaid card systems#consumer convenience#customer experience#cashless transactions#digital payments#financial security#loyalty programs#transaction processing#data analytics#customer education#privacy concerns#business efficiency#innovation#technology integration#consumer awareness#case studies#success stories#FAQs#blogging#digital trends#restaurant industry#financial technology#prepaid card benefits#prepaid card acceptance
0 notes
Text
Revolutionizing AI with Apple’s ReALM: The Future of Intelligent Assistants
New Post has been published on https://thedigitalinsider.com/revolutionizing-ai-with-apples-realm-the-future-of-intelligent-assistants/
Revolutionizing AI with Apple’s ReALM: The Future of Intelligent Assistants
In the ever-evolving landscape of artificial intelligence, Apple has been quietly pioneering a groundbreaking approach that could redefine how we interact with our Iphones. ReALM, or Reference Resolution as Language Modeling, is a AI model that promises to bring a new level of contextual awareness and seamless assistance.
As the tech world buzzes with excitement over OpenAI’s GPT-4 and other large language models (LLMs), Apple’s ReALM represents a shift in thinking – a move away from relying solely on cloud-based AI to a more personalized, on-device approach. The goal? To create an intelligent assistant that truly understands you, your world, and the intricate tapestry of your daily digital interactions.
At the heart of ReALM lies the ability to resolve references – those ambiguous pronouns like “it,” “they,” or “that” that humans navigate with ease thanks to contextual cues. For AI assistants, however, this has long been a stumbling block, leading to frustrating misunderstandings and a disjointed user experience.
Imagine a scenario where you ask Siri to “find me a healthy recipe based on what’s in my fridge, but hold the mushrooms – I hate those.” With ReALM, your iPhone would not only understand the references to on-screen information (the contents of your fridge) but also remember your personal preferences (dislike of mushrooms) and the broader context of finding a recipe tailored to those parameters.
This level of contextual awareness is a quantum leap from the keyword-matching approach of most current AI assistants. By training LLMs to seamlessly resolve references across three key domains – conversational, on-screen, and background – ReALM aims to create a truly intelligent digital companion that feels less like a robotic voice assistant and more like an extension of your own thought processes.
The Conversational Domain: Remembering What Came Before
Conversational AI, ReALM tackles a long-standing challenge: maintaining coherence and memory across multiple turns of dialogue. With its ability to resolve references within an ongoing conversation, ReALM could finally deliver on the promise of a natural, back-and-forth interaction with your digital assistant.
Imagine asking Siri to “remind me to book tickets for my vacation when I get paid on Friday.” With ReALM, Siri would not only understand the context of your vacation plans (potentially gleaned from a previous conversation or on-screen information) but also have the awareness to connect “getting paid” to your regular payday routine.
This level of conversational intelligence feels like a true leap forward, enabling seamless multi-turn dialogues without the frustration of constantly re-explaining context or repeating yourself.
The On-Screen Domain: Giving Your Assistant Eyes
Perhaps the most groundbreaking aspect of ReALM, however, lies in its ability to resolve references to on-screen entities – a crucial step towards creating a truly hands-free, voice-driven user experience.
Apple’s research paper delves into a novel technique for encoding visual information from your device’s screen into a format that LLMs can process. By essentially reconstructing the layout of your screen in a text-based representation, ReALM can “see” and understand the spatial relationships between various on-screen elements.
Consider a scenario where you’re looking at a list of restaurants and ask Siri for “directions to the one on Main Street.” With ReALM, your iPhone would not only comprehend the reference to a specific location but also tie it to the relevant on-screen entity – the restaurant listing matching that description.
This level of visual understanding opens up a world of possibilities, from seamlessly acting on references within apps and websites to integrating with future AR interfaces and even perceiving and responding to real-world objects and environments through your device’s camera.
The research paper on Apple’s ReALM model delves into the intricate details of how the system encodes on-screen entities and resolves references across various contexts. Here’s a simplified explanation of the algorithms and examples provided in the paper:
Encoding On-Screen Entities: The paper explores several strategies to encode on-screen elements in a textual format that can be processed by a Large Language Model (LLM). One approach involves clustering surrounding objects based on their spatial proximity and generating prompts that include these clustered objects. However, this method can lead to excessively long prompts as the number of entities increases.
The final approach adopted by the researchers is to parse the screen in a top-to-bottom, left-to-right order, representing the layout in a textual format. This is achieved through Algorithm 2, which sorts the on-screen objects based on their center coordinates, determines vertical levels by grouping objects within a certain margin, and constructs the on-screen parse by concatenating these levels with tabs separating objects on the same line.
By injecting the relevant entities (phone numbers in this case) into the textual representation, the LLM can understand the on-screen context and resolve references accordingly.
Examples of Reference Resolution: The paper provides several examples to illustrate the capabilities of the ReALM model in resolving references across different contexts:
a. Conversational References: For a request like “Siri, find me a healthy recipe based on what’s in my fridge, but hold the mushrooms – I hate those,” ReALM can understand the on-screen context (contents of the fridge), the conversational context (finding a recipe), and the user’s preferences (dislike of mushrooms).
b. Background References: In the example “Siri, play that song that was playing at the supermarket earlier,” ReALM can potentially capture and identify ambient audio snippets to resolve the reference to the specific song.
c. On-Screen References: For a request like “Siri, remind me to book tickets for the vacation when I get my salary on Friday,” ReALM can combine information from the user’s routines (payday), on-screen conversations or websites (vacation plans), and the calendar to understand and act on the request.
These examples demonstrate ReALM’s ability to resolve references across conversational, on-screen, and background contexts, enabling a more natural and seamless interaction with intelligent assistants.
The Background Domain
Moving beyond just conversational and on-screen contexts, ReALM also explores the ability to resolve references to background entities – those peripheral events and processes that often go unnoticed by our current AI assistants.
Imagine a scenario where you ask Siri to “play that song that was playing at the supermarket earlier.” With ReALM, your iPhone could potentially capture and identify ambient audio snippets, allowing Siri to seamlessly pull up and play the track you had in mind.
This level of background awareness feels like the first step towards truly ubiquitous, context-aware AI assistance – a digital companion that not only understands your words but also the rich tapestry of your daily experiences.
The Promise of On-Device AI: Privacy and Personalization
While ReALM’s capabilities are undoubtedly impressive, perhaps its most significant advantage lies in Apple’s long-standing commitment to on-device AI and user privacy.
Unlike cloud-based AI models that rely on sending user data to remote servers for processing, ReALM is designed to operate entirely on your iPhone or other Apple devices. This not only addresses concerns around data privacy but also opens up new possibilities for AI assistance that truly understands and adapts to you as an individual.
By learning directly from your on-device data – your conversations, app usage patterns, and even ambient sensory inputs – ReALM could potentially create a hyper-personalized digital assistant tailored to your unique needs, preferences, and daily routines.
This level of personalization feels like a paradigm shift from the one-size-fits-all approach of current AI assistants, which often struggle to adapt to individual users’ idiosyncrasies and contexts.
ReALM-250M model achieves impressive results:
Conversational Understanding: 97.8
Synthetic Task Comprehension: 99.8
On-Screen Task Performance: 90.6
Unseen Domain Handling: 97.2
The Ethical Considerations
Of course, with such a high degree of personalization and contextual awareness comes a host of ethical considerations around privacy, transparency, and the potential for AI systems to influence or even manipulate user behavior.
As ReALM gains a deeper understanding of our daily lives – from our eating habits and media consumption patterns to our social interactions and personal preferences – there is a risk of this technology being used in ways that violate user trust or cross ethical boundaries.
Apple’s researchers are keenly aware of this tension, acknowledging in their paper the need to strike a careful balance between delivering a truly helpful, personalized AI experience and respecting user privacy and agency.
This challenge is not unique to Apple or ReALM, of course – it is a conversation that the entire tech industry must grapple with as AI systems become increasingly sophisticated and integrated into our daily lives.
Towards a Smarter, More Natural AI Experience
As Apple continues to push the boundaries of on-device AI with models like ReALM, the tantalizing promise of a truly intelligent, context-aware digital assistant feels closer than ever before.
Imagine a world where Siri (or whatever this AI assistant may be called in the future) feels less like a disembodied voice from the cloud and more like an extension of your own thought processes – a partner that not only understands your words but also the rich tapestry of your digital life, your daily routines, and your unique preferences and contexts.
From seamlessly acting on references within apps and websites to anticipating your needs based on your location, activity, and ambient sensory inputs, ReALM represents a significant step towards a more natural, seamless AI experience that blurs the lines between our digital and physical worlds.
Of course, realizing this vision will require more than just technical innovation – it will also necessitate a thoughtful, ethical approach to AI development that prioritizes user privacy, transparency, and agency.
As Apple continues to refine and expand upon ReALM’s capabilities, the tech world will undoubtedly be watching with bated breath, eager to see how this groundbreaking AI model shapes the future of intelligent assistants and ushers in a new era of truly personalized, context-aware computing.
Whether ReALM lives up to its promise of outperforming even the mighty GPT-4 remains to be seen. But one thing is certain: the age of AI assistants that truly understand us – our words, our worlds, and the rich tapestry of our daily lives – is well underway, and Apple’s latest innovation may very well be at the forefront of this revolution.
#ai#ai assistant#ai model#AI systems#algorithm#Algorithms#ambient#app#apple#Apple's ReALM#approach#apps#ar#artificial#Artificial Intelligence#audio#awareness#background#Behavior#book#Calendar#Capture#challenge#Cloud#comprehension#computing#course#data#data privacy#details
0 notes
Text
The Future of Our Personal Data: A Guy's Thoughts on AI, Blockchain, and Digital Identity
Hey everyone,
The rise of AI and blockchain technology is transforming the way our personal data is collected, stored, and used, raising important questions about privacy and control.
I’ve been thinking a lot lately about how our personal data is being collected, stored, and used in today’s digital world. It’s crazy to see how quickly things are changing with the rise of artificial intelligence…

View On WordPress
#AI#Artificial Intelligence#awareness#BLOCKCHAIN#Collaboration#Control#data commodification#data silos#Digital Age#digital identity#generational divide#personal data#privacy rights#Technology#Transparency
0 notes
Text
Entry 2:
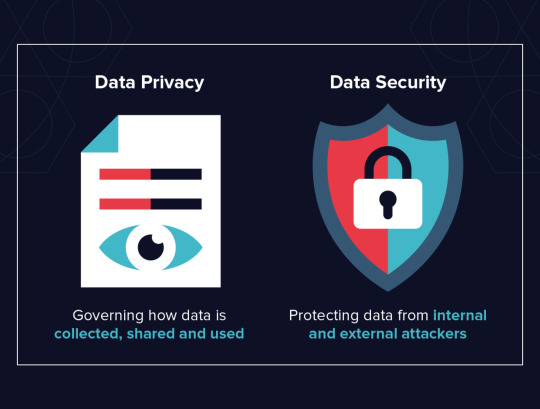
“Crescendo in Cyberspace: Understanding the Melody of Data Privacy and the Rising Value of Intangible Data”
With regard to data privacy, it pertains to how an individual’s data is collected, utilized and maintained in accordance with relevant privacy laws and regulations. It involves the correct handling, processing, storage and usage of personal information. It is only concerned about people’s freedom with their own information.
On a different light, data security protects personal data from unauthorized third-party access, hacking attacks or any use that exploits its privacy. This is meant to protect personal data by using diverse methods and techniques that ensure its confidentiality. In addition to this, Data security ensures that integrity of the data which means that the information must be accurate and reliable as well as be available when required for authorized individuals.
Briefly speaking, Data Privacy is about how one collects uses upholds drops retains and stores the details appropriately. On the other hand, Policies Techniques Used in Securing Personal Data. The two can exist without each other but not vice versa. For example, you cannot have data privacy without first having data security.
Now in the age of digital data, information has become a valuable commodity. It is commonly said that data is the new oil. However, why is data preferred to physical properties?
To start with, consumer behavior insights are provided by data which is vital to businesses. Facebook and Google among other companies make billions through it in terms of advertisements. Platform companies and data-aggregators sell individualized data to advertisement networks as well as marketers seeking to reach specific segments, affect purchasing decisions and set dynamic prices.
Again, decision-making processes necessitate having reliable data. Governments are getting increasingly data-driven and leveraging open government data to improve citizens’ quality of life through better designed targeted welfare schemes, evidence-based policy making and more participatory governance.
Moreover, the potential for misuse also shows the value associated with such information. Data thieves usually steal personal information so that they can vend it on dark web. An identity thief can expect to get ₱1,120 - ₱12,600.
Therefore, the specific worth of physical stuff is their tangibility, meanwhile the value of data comes from the power that it has to be used for making positive changes in businesses and much more. Furthermore, data can even be sold for monetary gain. In the process we are generating and sharing a large amount of data, understanding the importance of this data as well as ensure the data security is vital now.
1 note
·
View note
Text

Personal Identifiable Information (PII) is the digital money that powers our online presence in today's linked world. Professionals have a responsibility to maintain a high standard of personal and professional actions, which includes knowing the intricacies of personally identifiable information (PII).
Understanding PII enables us to act as vigilantes, protecting our own and others' security and privacy.
An educated approach to PII is our first line of protection as cyber threats get increasingly complex. A thorough understanding of PII demonstrates a dedication to moral behavior and builds confidence with stakeholders, colleagues, and clients.
Using the power of PII knowledge is a strategic advantage as well as a professional duty!
#data#data security#data privacy#data protection#cyber security#cyber awareness#security#technology#information security
1 note
·
View note
Photo

Part 3 and the last part of our Blog series on RightsCon is here! Find out what some of our favorite sessions are!
👉 https://bit.ly/3OTmjE3
#digital rights#human rights#women’s rights#digital activism#activism#advocacy#digital privacy#digital security#internet freedom#save the internet#internet security#net neutrality#internet shutdown#online privacy#privacy#online safety#cybersecurity awareness#technology#open data#data security#disinformation#misinformation#censorship#free expression#surveillance#dalai lama#malala#malala yousafzai
1 note
·
View note
Text
AI-Powered Real Estate: How to Stay Ahead of the Competition
Artificial intelligence (AI) is transforming the real estate industry, with numerous benefits and applications. AI in real estate has a bright future, from improved property valuation to AI-powered virtual property tours. However, implementing AI in real estate presents its own set of challenges, including concerns about data privacy and integration with existing systems. Despite these obstacles,…

View On WordPress
#AI#Ai in real estate#anonymization#artificial intelligence#cyber threats#cybersecurity awareness#data governance#data privacy#encryption#estate#faster#insightful#machine learning#machine learning algorithms#real estate#real-time#reliable
0 notes
Text
You're Being Manipulated and You Don't Even Realize It
In the age of digital omnipresence, it’s easy to fall into the illusion that we are in control of our actions, beliefs, and emotions. Yet, diving deep into the mechanics of today’s dominant online platforms, there’s a revelation that’s hard to swallow: we’re being manipulated, and many of us don’t even realize it.
Jaron Lanier, a pioneer in the realm of virtual reality, offers a compelling…
View On WordPress
#algorithmic control#data exploitation#digital addiction#digital awareness#digital empathy#echo chambers#emotional influence#Jaron Lanier#misinformation spread#online behavior#online privacy#online validation#political polarization#social media manipulation
1 note
·
View note
Text
cw incest, stalking, breach of privacy, SA
Please help me. i found out my brother (who lives in the same house has me) Has been accessing my private information, including my bank account and my google photos, which contain several compromising photos of me. He has also created a secret folder in my accoubt which Cannot be accessed through any devices owned by me. My Own Shit. And I have proof of him accessing, altering, deleting, and obfuscating information and data. The internet connection here is not reliable for me. I CANNOT LIVE HERE. I AM AFRAID. And i am keeping quiet in order to avoid a major blowout in this house but I have been on the brink of suicide and he is aware of the effects these actions have on me. I am desperate to get far, far, far away from here. I am so tired of feeling unsafe.
vm/paypal.me/: tominova
I am so profoundly alone and just. despondent. I can't keep taking this
6K notes
·
View notes
Text
hey so, this might sound weird i get it, i will be spying on myself using stalkerware for an art project over the next few weeks, i am doing this on an entirely separate phone (for privacy and safety reasons), which means that if you want to be a part of a weird cyberpunk tech art project you can send me text messages to that phone. be aware that anything you send to the phone will be uploaded to the servers of a stalkerware company, so yeah, keep that in mind. all phone numbers (and potential other PII) will be redacted for the project i'll be using the data for, but message contents MAY APPEAR.
so yea with those disclaimers out of the way, feel free to message me at +41772840150 and i'll try to reply to as much as i can! (keep your international text message rates in mind, the phone number is swiss)
if you want to support this project reblog this + if you can afford it support me via ko-fi and make sure to read up on my latest stalkerware blog post
5K notes
·
View notes