#cyberthreat
Text
Cyber Conflict Erupts Amid Israel-Hamas Clash

Amid the escalating conflict between Israel and the Palestinian group Hamas, a parallel battle in the cyber world has unfolded, introducing unexpected twists and turns to an already complex situation. As tensions mount on the ground, hackers from various factions have launched a series of cyberattacks, leaving both nations vulnerable. Adding another layer of complexity, a Pro-India group has entered the digital arena, intensifying the ongoing cyber conflict.
Hamas Launches Ground Attack
On a fateful Saturday, Hamas terrorists initiated a ground attack on Israel, accompanied by an unrelenting missile barrage. This brutal assault resulted in casualties and the shocking abduction of approximately 900 people, including 73 Israeli soldiers. To further complicate the situation, several individuals were taken hostage as events continued to unfold.
Also Read: Pune Couple's Organized Cyber Blackmailing Scandal Uncovered
Cyber Chaos Hits Jerusalem Post and Red Alert App
On October 8, the Jerusalem Post, a prominent Israel-based media outlet, found itself in the crosshairs of multiple cyberattacks, culminating in a site crash, rendering it inaccessible from various locations. Anonymous Sudan, a hacking group, claimed responsibility for this cyber onslaught.
In another alarming incident, the Red Alert phone app system, a critical tool for providing real-time alerts during rocket and missile attacks in Israel, reported that it had become a target of a hacktivist group known as Anon Ghost.
Coordinated Cyber Operations: OpIsrael and OpsRise
As the physical conflict raged on, the cyber battlefield witnessed a surge in activity. A pro-Palestine online group, known as the "Ghost of Palestine," initiated a significant cyber campaign, rallying hackers worldwide under the banner of #OpIsrael. Their objective was to target Israel's cyber infrastructure and bolster the cyber resistance against the nation.
Additionally, another pro-Palestine hacking alliance, comprised of "Ghost Clan" and "Black Shield Crew MY," issued a warning, signaling an impending cyber offensive against Israel known as "OpsRise." These developments underscored the escalating digital confrontations within the ongoing Israel-Palestine conflict, as various hacker groups engaged in cyber warfare.
Collaboration of Pro-Russian Hacking Entities
A Twitter handle, @Cyberknow20, disclosed that 35 pro-Palestine hacker groups had consistently focused their efforts on Israel. Of particular concern was the collaboration between two pro-Russian hacking entities, Anonymous Sudan and Killnet, as they jointly targeted Israel's cyber infrastructure.
Also Read: Cyber blackmailing case: Shatrughan's bail plea rejected
Pro-Palestine Hacker Groups Target Governments and Websites
These cyberattacks witnessed pro-Palestine hacker groups systematically targeting multiple Israeli government websites. Among the notable incidents, Garnesia Team claimed responsibility for attacks on government sites, including the Municipality of Jerusalem and the National Insurance Institute. The ACEH Hackers Group also made its mark by targeting various Israeli websites, such as Cello, USHOPS, and CASTRO.
The Team Herox Hackers Group shifted its focus to "The Occupation Magazine" website, while the Ganosec Team executed an attack that temporarily took down the website of the Israeli Security Agency.
Pro-India Group Enters the Fray
In a surprising turn of events, the "Indian Cyber Force," a Pro-India hacking group, has emerged as a significant player in the Pro-Israel hacktivist arena. They have successfully launched cyberattacks on Palestinian websites, impacting several targets, including the Hamas official website and the Palestine National Bank website.
Also Read: Cybercrime in Nagpur - Cyber Blackmailer Couple Arrested in Pune for Extorting Money
In response to these attacks, Pro-Palestine hacker groups retaliated with Distributed Denial of Service (DDoS) attacks on Delhi government websites, reflecting the escalating cyber conflicts tied to the Israel-Palestine issue. However, as of Monday, the Delhi government website appeared to be fully functional.
The Evolving Nature of Cyber Conflicts
These incidents collectively underscore the dynamic and evolving nature of conflicts in the digital realm. They highlight the critical importance of cybersecurity in contemporary geopolitical struggles, where cyberattacks can have real-world consequences. As the situation continues to develop, both nations find themselves grappling with the challenges of defending their digital territories while addressing the broader conflict on the ground.
In summary, the ongoing Israel-Palestine conflict has spilled over into the cyber realm, with various hacking groups engaging in a relentless digital battle. This digital conflict has witnessed the involvement of a Pro-India group, further complicating the already complex situation. As cyberattacks intensify, the importance of cybersecurity in contemporary geopolitical conflicts becomes increasingly evident, with real-world consequences at stake for both nations.
Source: https://www.the420.in/cyber-conflict-israel-hamas-clash-october-2023/
2 notes
·
View notes
Text
Voice Actor Announcement!
Incoming VA announcement! This casting round had such an extremely talented batch of VAs, everyone should be proud of what they submitted! Everyone, please join me in welcoming the following actors to the #CyberThreat cast!!

7 notes
·
View notes
Link
https://bit.ly/3nZtdQH - 🔒 "The Five Bears," referring to Russia's state-sponsored Advanced Persistent Threat (APT) groups, represent a formidable part of the country's offensive cyber capabilities. The network combines advanced tools and infrastructure to execute sophisticated operations, targeting nations in both war and peacetime. However, the recent war in Ukraine has shown limitations in the strategic advantages of offensive cyber operations on the physical battlefield. #CyberWarfare #CyberSecurity 📚 Since the 1990s, Russia has been engaging in a broad spectrum of hostile cyber operations, from espionage to sabotage. Today, its state-sponsored threat actors form a network of skilled groups conducting operations worldwide, marking a vital component of Russia's global power strategy. Still, attribution is a complex issue, with groups frequently changing or exchanging toolsets. #CyberEspionage #RussiaCyber 🎯 The Russian APT actors use their cyber capabilities to target adversaries' critical infrastructure globally. They've demonstrated advanced cyber tradecraft, maintaining a persistent and often undetected presence in compromised environments. Prominent actors include Fancy Bear, Venomous Bear, Energetic Bear, and Voodoo Bear, each linked to different Russian intelligence agencies and known for their unique focuses and techniques. #CyberThreat #APT 🔍 Tactics, Techniques & Procedures (TTP) employed by these groups often change to evade attribution. The US Cybersecurity and Infrastructure Security Agency (CISA) has identified several TTP used by Russian state-sponsored APT groups, including targeting and attacks on critical infrastructure, espionage activities, and influence campaigns. Other techniques involve reconnaissance, resource development, initial access, execution, persistence, and credential access. #CyberTTP #CISA 💻 Known toolkits used by Russian state-sponsored APT groups include backdoors, credential stealers, downloaders, privilege escalation tools, droppers, wipers, and web shells. These tools enable a variety of malicious activities, from data theft to system destruction. #CyberTools #Malware ⚠️ Over the years, Russian state-sponsored APT groups have been attributed to several prominent attacks. These include a global energy sector intrusion campaign (2011-2018), attacks on the Ukrainian power grid (2015 & 2016), the 2016 US Presidential Election hack, and the NotPetya attack in 2017. #CyberAttacks #NotPetya 🇺🇦 Despite their known capabilities, Russian cyber operations have had a negligible impact on strategic objectives during the war in Ukraine. This could be due to Ukraine's defensive capabilities or the inability to integrate cyber operations into a comprehensive all-domain strategy. Nevertheless, the potential for unintentional spillover effects means Russian cyber operations remain a significant threat to any digitalised society.
#CyberWarfare#CyberSecurity#CyberEspionage#RussiaCyber#CyberThreat#APT#CyberTTP#CISA#CyberTools#Malware#CyberAttacks#NotPetya#UkraineConflict#CyberWar
2 notes
·
View notes
Text
#ThreatIntelligence#ThreatIntelligenceAnalyst#CertifiedThreatIntelligenceAnalyst#CyberThreatIntelligence#Cybersecurity#Cyberattack#Cybersec#Cyberthreat#Cyberthreats#Cybercrime#edtech#technology#teaching
2 notes
·
View notes
Text
What are Cyber Threats: a malicious act
#NeedToKnow: Cyber Threat
Cyber threats encompass any malicious act that targets computer systems, networks, and data with the intent to:
Gain unauthorized access: Hackers might aim to steal sensitive information, disrupt operations, or install malware.
Cause damage: Cyberattacks can corrupt data, disable systems, or even cause physical harm through critical infrastructure disruption.
Extort money: Ransomware attacks…

View On WordPress
0 notes
Text
L'importanza della Cyber Threat Intelligence

Tempo di lettura stimato: 5 minuti
In un altro articolo abbiamo già parlato della Cyber Threat Intelligence spiegando cos’è, come funziona e le sue varie tipologie. Oggi, invece, ci focalizzeremo più sull’importanza della Cyber Threat Intelligence, approfondendo come può essere utile alle aziende per fornire risposte in ambito di sicurezza, contenendo i rischi e fornendo informazioni che supportino la risposta agli incidenti.
L'importanza della Cyber Threat Intelligence
In un mondo in cui le tecnologie e le minacce informatiche sono sempre in continua evoluzione, un’azienda non può permettersi di trascurare l’importanza della Cyber Threat Intelligence. Ogni giorno sul web avvengono innumerevoli attacchi informatici e furti di dati a danno di aziende e privati. Queste grandi quantità di informazioni, vengono poi catalogate e vendute illegalmente sul Dark Web.
Gli hacker sono soliti vendere informazioni in questa parte del web perché garantisce loro l’anonimato. Infatti, a differenza del web tradizionale, per poter accedere a questi luoghi virtuali, bisogna utilizzare un browser che mascheri il proprio indirizzo IP. Questo complica le attività di tracciamento dei criminali da parte delle autorità e rende il dark web un posto completamente anonimo.
Uno degli obbiettivi che si pone la CTI è quello di monitorare le informazioni presenti in questa grande parte del web a scopo analitico. Il fine è quello di prevenire e arginare i danni che questi dati potrebbero provocare.
Monitorare il Dark Web e il Deep Web
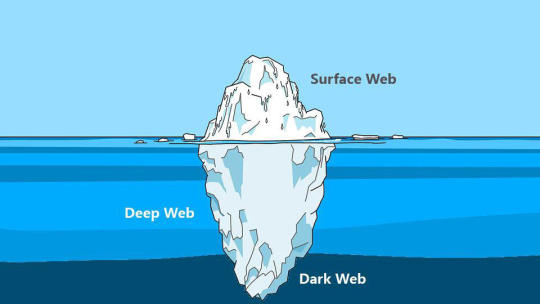
Spesso, quando parliamo di Deep Web e di Dark Web, pensiamo che siano presenti solo ed esclusivamente attività illegali, ma non è corretto. Ci sono anche forum, blog e siti web che hanno il fine di divulgare informazioni difficilmente reperibili sul web tradizionale.
Purtroppo però, è anche vero che i criminali sfruttano questa sezione della rete per vendere ogni genere di informazione. Queste comprendono numeri di telefono, indirizzi email, dati bancari, documenti, passaporti, credenziali d’accesso amministrative di siti web. C’è praticamente di tutto.
Questo genere di informazioni, nelle mani di un malintenzionato (o di un competitor), potrebbe compromettere l’integrità di un’intera azienda, dei suoi dipendenti e dei suoi clienti. Le conseguenze provocate da una violazione di dati, potrebbero inoltre manifestarsi anche sotto forma di danni alla reputazione dell'azienda.
Quando un cliente fornisce ad un’azienda i suoi dati personali si aspetta che vengano trattati con il massimo rispetto. I clienti potrebbero sentirsi "traditi" dall’azienda che avrebbe dovuto garantire loro la sicurezza delle proprie informazioni personali.
Un esempio clamoroso è stato il furto di dati avvenuto nel 2019 ai danni di Facebook Inc. (Fonte)
Ben 533 milioni di dati personali appartenenti agli utilizzatori della piattaforma sono stati sottratti, suddivisi per 106 paesi e diffusi gratuitamente sul web portando nuovamente la società al centro di polemiche.

Le aziende che cercano di proteggere i dati dei propri clienti, fornitori e dipendenti investono in strumenti di analisi e monitoraggio.
Affidandosi a dei professionisti, è possibile ricevere tempestivamente un avviso ogni qualvolta che un’informazione sensibile viene pubblicata su un forum o su un sito web presente nel Dark Web. Per questo l’importanza della Cyber Threat Intelligence gioca un ruolo chiave nel ramo della sicurezza informatica aziendale.
Monitorare il Dark Web dunque, significa avere la possibilità di poter rilevare tempestivamente eventuali informazioni sensibili prima che esse possano causare problemi alle aziende.

Strumenti per monitorare il Dark Web
Essendo una porzione di internet difficilmente accessibile e non indicizzata dai motori di ricerca, analizzare e monitorare le risorse presenti sul Deep Web diventa più complicato. Per questo motivo ci vengono in aiuto diversi strumenti progettati con lo scopo di semplificare il processo di indagine e analisi.
Un software che potrebbe essere d’aiuto durante un’attività d’investigazione è Onionscan, un programma Open Source completamente gratuito.
Il progetto Onionscan e la CTI
Il progetto Onionscan si pone due obiettivi:
- Aiutare gli operatori a trovare e risolvere problemi di sicurezza operativa
- Aiutare i ricercatori a monitorare e tracciare i siti presenti nel Deep Web
Il software è scaricabile sulla pagina Github dedicata, contenente anche una guida per l’installazione e una lista delle dipendenze necessarie per eseguire il software.
Una volta installato, per poterlo utilizzare basta semplicemente digitare nella riga di comando:
onionscan nomesitowebdascansionare.onion
Certamente, il solo accesso a uno strumento come questo non basta a fornire una copertura efficace. Infatti, l'importanza della Cyber Threat Intelligence risiede in gran parte nel saper effettuare le ricerche e interpretare i dati.
Conclusioni
Abbiamo visto cos’è e come funziona un’attività di monitoring del Dark Web e soprattutto abbiamo iniziato a comprendere l’importanza della Cyber Threat Intelligence.
Investire in queste soluzioni garantisce un’ulteriore sicurezza all’azienda. Mettere al sicuro i dati dei propri clienti e dei propri dipendenti non può essere un optional, ogni azienda dovrebbe essere sensibile a queste tematiche ed investire le proprie risorse per prevenire spiacevoli situazioni.
SOD offre un servizio apposito che si prefigge proprio di fornire informazioni di CTI preziose per la difesa proattiva e la risoluzione di criticità prima che diventino dei veri problemi.
Se hai bisogno di ulteriori chiarimenti non esitare a contattarci, siamo pronti a rispondere ad ogni tua domanda.
- La differenza tra il dark web e il deep web e l'importanza di monitorarli per la sicurezza aziendale
- I dati esfiltrati durante un attacco ransomware a doppia estorsione non sono pubblici. Sfatiamo un mito
Read the full article
0 notes
Text
#cyber#cybercrime#cybersecurity#cybersecurityawareness#cyberthreat#dataprotection#datasecurity#informationsecurity#infosec#security#tech#technology#business#gauravgo#gauravgoposts
0 notes
Text
Penetration Testing Services Companies – 2023
In an era marked by increasing reliance on technology, the potential vulnerabilities that accompany our digital existence have become a pervasive concern.
Read More : https://penetration-testing.thecybersecurityreview.com/vendors/top-penetration-testing-services-companies.html

0 notes
Text
How to Secure Your Smartphone from Cyber Threats
In the age of smartphones, our handheld devices have become an integral part of our daily lives. From personal messages to sensitive financial information, our smartphones store a treasure trove of data. However, with great convenience comes great responsibility – the responsibility to safeguard our digital worlds from cyber threats. In this guide, we’ll explore comprehensive strategies to…
View On WordPress
0 notes
Text
How to Improve the Security of Your Smartphone in Deepfake World?

Fortify Your Smartphone: Boost Security and Protect Data
In an era where our phones hold a treasure trove of personal information, safeguarding them from cyber threats is paramount. Whether an iPhone or an Android device, the need for enhanced security is universal. To fortify your smartphone, enable two-factor authentication (2FA) for accounts with sensitive data. This additional layer ensures that even if your password is compromised, unauthorized access is thwarted without the unique code sent to your device.
Regular software updates are crucial, as developers consistently release patches to enhance security. Carefully review app permissions to limit access to essential functions, bolstering privacy. Keeping sensitive notifications off the lock screen prevents prying eyes from accessing confidential information easily.
Effective antivirus software is a must to thwart scammers and hackers attempting to steal personal information through phishing attempts. Prioritizing regular backups safeguards your data against unforeseen circumstances. Biometric authentication, such as fingerprint or face recognition, adds an extra layer of protection.
Download apps only from official stores, like Google Play Store or the Apple App Store, to ensure their safety. Activating spam filters for text messages helps protect against unwanted messages and scams. Investing in protective screens and cases, both physical and digital precautions, ensures the longevity and security of your smartphone.
For an extra layer of security, consider Wi-Fi and Bluetooth usage practices. Disable them when not in use, avoid auto-connecting to open networks, and use a Virtual Private Network (VPN). Similarly, exercise caution when charging your device—use trusted chargers and cables, avoid public charging stations, and consider a power-only USB cable to minimize data theft or malware risks. By following these tips, you can significantly enhance the security of your smartphone and protect your sensitive information from cyber threats.
For More Updates
0 notes
Text
Mahadev Online Betting Scam: Bollywood Celebrities and Pakistani Connections Under Scrutiny

MUMBAI: The Enforcement Directorate (ED) has initiated an extensive investigation into the Mahadev Online Betting scandal, revealing a complex network of money laundering activities that extend far beyond the realm of online betting. This case has taken an intriguing turn, with the involvement of UPI IDs, implicating well-known personalities, celebrities, and even political contributions.
The Mahadev Online Betting Scandal: A Brief Overview The spotlight has turned to Mahadev, an online betting application, founded by Saurabh Chandrakar and Ravi Uppal hailing from Bhilai, Chattisgarh. The ED has cast a sharp eye on this platform, alleging that it served as a hub for illicit betting websites. It facilitated new user registrations, generated User IDs, and funneled funds through a convoluted network of anonymous bank accounts.
Also Read: Kashmiri Brother-in-Law could not show Kamal, and pressure on Nagpur police failed
Extensive Raids and Compelling Evidence In a recent series of coordinated raids conducted in cities like Kolkata, Bhopal, and Mumbai, the ED has unearthed substantial evidence and frozen/seized assets totaling an astounding Rs 417 Crore. According to the ED, Chandrakar and Uppal orchestrated the operations of Mahadev Online Betting from a central headquarters located in the UAE. They employed a franchising model, establishing "Panel/Branches" for their associates, with profit-sharing arrangements set at a 70:30 ratio.
A deeply troubling aspect of this scandal revolves around the exploitation of vulnerable communities, specifically slum residents and those with limited incomes. It appears that individuals implicated in this alleged scam acquired UPI (Unified Payments Interface) details from these unsuspecting individuals, effectively using them as pawns in money laundering schemes. In return for the use of their UPI IDs, these victims were given meager sums, while the ill-gotten funds were channeled to foreign entities. The Enforcement Directorate (ED) is currently conducting a thorough investigation to determine the full scope of this fraudulent activity and quantify the amount of money that has been laundered through this deceptive modus operandi.
Lavish Wedding Expenditure Raises Concerns
Recent ED raids conducted in Bhopal, Mumbai, and Kolkata have brought to light the extravagant lifestyle of the primary accused, Saurabh Chandrakar. Astonishingly, it was revealed that he lavishly spent over Rs 200 crore on his wedding ceremony in the United Arab Emirates (UAE). Shockingly, reports suggest that the funds for this opulent celebration were sourced from the proceeds of criminal activities.
Private jets were chartered to transport family members from Nagpur to the UAE for the wedding festivities, and renowned celebrities were hired for special performances. An array of wedding planners, dancers, and decorators were flown in from Mumbai, with cash payments facilitated through clandestine hawala channels.
Also Read: Cybercrime in Nagpur - Cyber Blackmailer Couple Arrested in Pune for Extorting Money
Celebrity Involvement and Suspicions of Proceeds from Illegal Activities
The ED's ongoing investigation has also implicated several prominent celebrities who endorsed these betting entities. These celebrities not only lent their names to these platforms but also participated in various events organized by the app promoters and other individuals accused in this case. Payments to these celebrities were routed through intricate transactions, ultimately sourced from the proceeds of online betting activities.
The list of celebrities under scrutiny includes well-known figures such as singers Atif Aslam, Rahat Fateh Ali Khan, Neha Kakkar, Vishal Dadlani, actor Tiger Shroff, Elli Evram, Bhagyashree, Pulkit Samrat, Sunny Leone, Kirti Kharbanda, Nushrat Bharucha, and comedians Bharti Singh, Krishna Abhishek, and Ali Azgar.
In conclusion, this disturbing scandal not only highlights the exploitation of vulnerable populations but also shines a light on the extravagant spending habits of key individuals involved. The web of celebrity endorsements and the suspected use of proceeds from illegal activities underscore the need for a thorough investigation into the matter, ensuring that justice is served and accountability upheld.
Source: https://www.the420.in/bollywood-celebrities-pakistani-connections-mahadev-online-betting-scam-ed/
2 notes
·
View notes
Link
https://bit.ly/3Rq0Dme - 🌐 The hospitality industry faces a new cyber threat: the "Inhospitality" malspam campaign, using social engineering to deploy password-stealing malware. Attackers lure hotel staff with emails about service complaints or information requests, leading to malicious payload links. #CyberThreat #HotelIndustrySecurity 🔍 Sophos X-Ops identified this trend, similar to tactics used during the US tax season. Attackers engage with hotel staff through emotionally charged scenarios, from lost items to accessibility needs, only sending malware links after initial contact. #SophosResearch #SocialEngineering 💼 Emails vary from violent attack allegations to queries about disability accommodations. Once staff respond, attackers reply with links claiming to contain relevant "documentation," which are actually malware in password-protected files. #CyberAttackTactics #HotelSafety 📧 Common traits in these emails include urgent requests and emotionally manipulative narratives. Examples range from lost cameras with sentimental value to issues in booking for disabled family members, all designed to elicit quick responses from hotel staff. #MalspamCampaign #EmailScams 🔐 The malware, often a variant of Redline or Vidar Stealer, is difficult to detect. It's hidden in large, password-protected files and often carries valid or counterfeit signatures to bypass security scans. #MalwareAnalysis #CyberDefense 💻 Upon execution, the malware connects to a Telegram URL for command-and-control, stealing information like browser-saved passwords and desktop screenshots. It doesn't establish persistence, running once to extract data before quitting. #CybersecurityThreat #DataProtection 🛡️ Sophos has identified over 50 unique malware samples and reported them to cloud providers. With low detection rates on Virustotal, Sophos has published indicators of compromise and ensures detection in their products.
#CyberThreat#HotelIndustrySecurity#SophosResearch#SocialEngineering#CyberAttackTactics#HotelSafety#MalspamCampaign#EmailScams#MalwareAnalysis#CyberDefense#CybersecurityThreat#DataProtection#SophosSecurity#CyberAwareness#engineering#hotels#staff#emails#requests#tactic#tax
1 note
·
View note
Photo

Want to make cybersecurity your niche? Our Security+ Certification prep course helps you add this crucial credential to your resume quickly and easily. Learn how to plan, implement, and maintain information security in a vendor-neutral format. Our content has the CompTIA Approved Quality Content (CAQC) validation and fully prepares you to pass the certification exam on the first try.
Learn more here: https://ccslearningacademy.com/.../comptia-security-sy0-601
0 notes
Text
Cybersecurity seminar @ IBP tower Ortigas



0 notes