#cyber security online university
Text
Online Part-Time Course Admission 2023 at WILP MU - Bangalore

Mangalayatan University has introduced Work-integrated learning programs to bridge the gap between academic knowledge and practical skills. It is a learning approach that combines theoretical learning with practical experience in the workplace. In India, several universities and colleges have started offering work-integrated learning programs to provide students with practical exposure and make them industry-ready. These programs are designed to equip students with the skills and knowledge required to excel in their chosen career path. The prime motive of this institute is to combine career acceleration with learning, help professionals learn at their own pace, and unlock possibilities with opportunities.
1. Collaboration between industry and academia
Work-integrated learning programs in India are a result of the collaboration between industry and academia. Industry experts work closely with academic institutions to design this program, which ensures that the curriculum is relevant to industry requirements. This collaboration also provides students with opportunities to work on real-life projects and gain hands-on experience.
2. Focus on practical learning
Work-integrated learning programs in India are designed to provide students with practical exposure to the industry. These programs focus on imparting practical skills and knowledge required to succeed in the workplace. Students are required to complete internships or projects as a part of the program, which provides them with the opportunity to apply their theoretical knowledge in a real-world setting.
3. Customized programs
Work-integrated learning programs in India are customized to meet the specific needs of different industries. The curriculum is designed to cater to the needs of specific industries, which ensures that students are equipped with the skills and knowledge required for their chosen career path. This customization ensures that students are industry-ready and can contribute to their respective fields from day one.
4. Emphasis on soft skills
Work-integrated learning programs in India emphasize the development of soft skills, such as communication, teamwork, leadership, and problem-solving. These skills are crucial for success in the workplace, and work-integrated learning programs provide students with ample opportunities to develop these skills. Students are required to work on group projects, interact with industry professionals, and make presentations, which help them develop these critical skills.
5. Flexibility in learning
Work-integrated learning programs in India offer flexibility in learning. Students can choose to complete their coursework online or on campus, depending on their convenience. This flexibility allows students to balance their academic and work responsibilities effectively. It also allows professionals to pursue further education while continuing to work.
6. Industry-relevant curriculum
Work-integrated learning programs in India offer an industry-relevant curriculum. The curriculum is designed to meet the requirements of different industries, and students are trained to work on industry-specific projects. This training ensures that students are equipped with the knowledge and skills required to excel in their chosen field.
7. Experiential learning
Work-integrated learning programs in India focus on experiential learning. Students are required to complete internships, projects, and assignments as a part of the program. This experiential learning provides students with the opportunity to apply their theoretical knowledge in a real-world setting. It also allows students to gain practical experience, which is crucial for success in the workplace.
8. Industry partnerships
Work-integrated learning programs in India are designed in partnership with leading industry players. These partnerships provide students with access to the latest technologies and tools used in the industry. It also provides them with the opportunity to interact with industry professionals and learn from their experiences.
9. Career-oriented
Work-integrated learning programs in India are career-oriented. The programs are designed to provide students with the skills and knowledge required to succeed in their chosen field. The curriculum is updated regularly to keep up with the changing industry trends and requirements. This ensures that students are equipped with the latest knowledge and skills required to excel in their chosen field.
Professionals benefit from WILP programs, as they have access to a pool of skilled and motivated students who can contribute to their organization's goals and objectives. Moreover, WILP programs help bridge the gap between academia and industry by fostering collaboration and knowledge sharing between educators and practitioners. Overall, Work Integrated Learning programs provide a valuable learning experience for students, while also contributing to the development of a skilled and competent workforce.
Source Url: Working Professional Online Part-Time Course Admission 2023 at WILP MU - Bangalore
#wilp btech course#online mba course#part time mtech in cyber security#mtech part time admission#best pvt university in Aligarh#online btech course#part time btech in civil engineering#working professional programmes#wilp programmes#admission open wilp programmes
0 notes
Text
You’ve been asked to serve on the jury in the first-ever criminal prosecution of a United States president. What could possibly go wrong? The answer, of course, is everything.
A juror in former president Donald Trump’s ongoing criminal trial in New York was excused on Thursday after voicing fears that she could be identified based on biographical details that she had given in court. The dismissal of Juror 2 highlights the potential dangers of participating in one of the most politicized trials in US history, especially in an age of social media frenzies, a highly partisan electorate, and a glut of readily available personal information online.
Unlike jurors in federal cases, whose identities can be kept completely anonymous, New York law allows—and can require—the personal information of jurors and potential jurors to be divulged in court. Juan Merchan, the judge overseeing Trump’s prosecution in Manhattan, last month ordered that jurors’ names and addresses would be withheld. But he could not prevent potential jurors from providing biographical details about themselves during the jury selection process, and many did. Those details were then widely reported in the press, potentially subjecting jurors and potential jurors to harassment, intimidation, and threats—possibly by Trump himself. Merchan has since blocked reporters from publishing potential jurors’ employment details.
The doxing dangers that potential jurors face became apparent on Monday, day one of the proceedings. An update in a Washington Post liveblog about Trump’s trial revealed the Manhattan neighborhood where one potential juror lived, how long he’d lived there, how many children he has, and the name of his employer. Screenshots of the liveblog update quickly circulated on social media, as people warned that the man could be doxed, or have his identity revealed publicly against his will with the intent to cause harm, based solely on that information.
“It's quite alarming how much information someone skilled in OSINT could potentially gather based on just a few publicly available details about jurors or potential jurors,” says Bob Diachenko, cyber intelligence director at data-breach research organization Security Discovery and an expert in open source intelligence research.
Armed with basic personal details about jurors and certain tools and databases, “an OSINT researcher could potentially uncover a significant amount of personal information by cross-referencing all this together,” Diachenko says. “That's why it's crucial to consider the implications of publicly revealing jurors' personal information and take steps to protect their privacy during criminal trials.”
Even without special OSINT training, it can be trivial to uncover details about a juror’s life. To test the sensitivity of the information the Post published, WIRED used a common reporting tool to look up the man’s employer. From there, we were able to identify his name, home address, phone number, email address, his children’s and spouse’s identities, voter registration information, and more. The entire process took roughly two minutes. The Post added a clarification to its liveblog explaining that it now excludes the man’s personal details.
The ready availability of those details illustrates the challenges in informing the public about a highly newsworthy criminal case without interfering in the justice process, says Kathleen Bartzen Culver, the James E. Burgess Chair in Journalism Ethics and director of the School of Journalism & Mass Communication at the University of Wisconsin-Madison.
“Simply because a notable figure is on trial does not mean that a juror automatically surrenders any claim to privacy,” Bartzen Culver says. “People who have been drawn into a case that is exceptionally newsworthy are not aware that a simple statement that they make about where they work might identify them and open them up to scrutiny and possibly risk.”
The dangers to jurors or potential jurors has only increased since the first day of jury selection, which remains ongoing, in part due to the challenges of prosecuting a former US president and the presumptive Republican nominee in the 2024 US presidential election. Trump is charged with 34 counts of falsifying business records, a class E felony in New York state, for payments made ahead of the 2016 presidential election related to alleged affairs with two women, adult performer Stormy Daniels and Playboy model Karen McDougal. Trump has claimed his prosecution is a “communist show trial” and a “witch hunt” and has pleaded not guilty.
On Fox News, coverage of Trump’s trial has repeatedly focused on the potential political motivations of the jurors, bolstering the former president’s claims. Trump, in turn, has repeated the claims by the conservative news network’s hosts. In a post on Truth Social on Wednesday, Trump quoted Fox News commentator Jesse Watters claiming on air that potential jurors in Trump’s trial are “undercover liberal activists lying to the judge in order to get on the Trump jury.” This, despite a gag order that forbids Trump from “making or directing others to make public statements about any prospective juror or any juror in this criminal proceeding.”
Broader media coverage of the Trump trial jurors appears to often be the work of political reporters who are unfamiliar with the journalism ethics specific to covering a criminal trial, says UW-Madison’s Bartzen Culver. “It's like when political reporters covered Covid and science journalists lost their minds.” She adds that it’s important for any journalist covering a criminal case—Trump’s or otherwise—to “consider our role within the justice system.”
“Unethical behavior by journalists can delay trials. It can result in overturned convictions and the people having to go back and do a retrial,” Bartzen Culver says. “That all works against our system of justice.”
The New York case is one of four ongoing criminal proceedings against Trump. In Georgia, where he faces multiple felony charges for alleged attempts to interfere with the state’s electoral process in 2020, Trump supporters leaked the addresses of members of the grand jury, after their names were listed in the 98-page indictment against the former president, as required by state law. Georgia’s Fulton County Sheriff’s Office said last August that it was investigating threats against the jury members. The incident highlights the persistent dangers people can face from Trump’s supporters, both in the near term and for the rest of their lives, if they’re viewed as having acted against him.
The leaks were discovered by Advance Democracy Inc. (ADI), a nonpartisan, nonprofit research and investigations organization founded by Daniel J. Jones, a former investigator for the FBI and the US Senate Intelligence Committee. So far, Jones tells WIRED, ADI has not uncovered attempts to dox jurors in Trump’s New York trial. But it’s still early days.
“We have not yet found identifying information on the extremist forums we monitor,” Jones says. “Having said that, I share your concern that it is only a matter of time before this happens.”
40 notes
·
View notes
Text
I usually stay far away from Twitter and fandom drama and I don't follow fandom groups but given the dehumanizing posts I've been seeing online, I am going on a fairly long rant, this is just my view, of course, so please discard it if not relevant to you:
The people making posts like these:
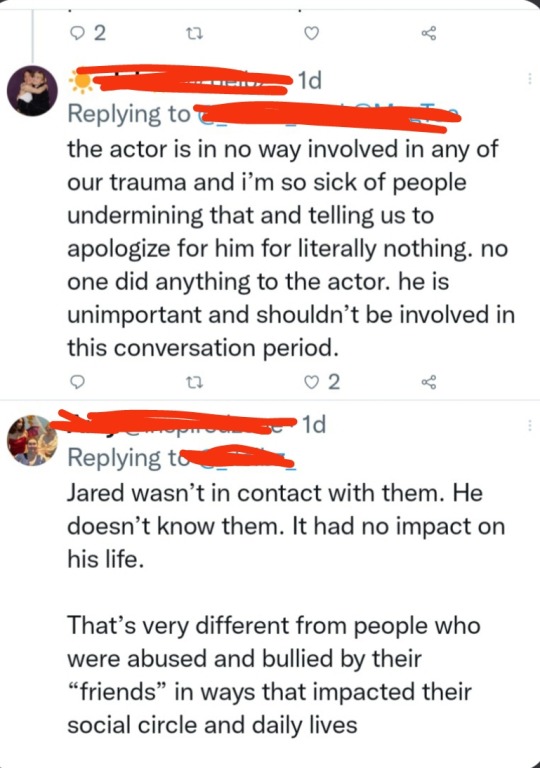
are at the core of the bully mentality. You are dehumanizing a Human Being with the entitlement that you get to define how a negative experience affects them. You do not, in any universe, get to tell someone who has been affected by something at what level they have been affected. Simply because you are not them.
Furthermore, you are biased and discriminating against Jared Padalecki because he is a celebrity. Jared is a human being first and foremost and, as we've seen in the past, he does do social listening. This means death threats and other cyber crimes do affect him, not to mention the very real stalking some of you do when he moves from country to country. You end up following him under his hotel or even worse situations.
This discussion happening within fandom should include him because he is a direct victim. Also, the intent to commit cyber crimes and sending death threats does not get cancelled out just because that person may or may not have read the thread/post. Do you get this? Do you understand that if your intention and energy is vile, whether the content reaches your target or not, your cyber crime is still in effect?
"Jared is a big boy and he doesn't care". Really? In what universe would you be okay with receiving death threats, would your family love that for you? Oh, they would not? So why on earth would you say it is alright that Jared received death threats? Fans do affect an actor's psyche, actors live to bring you joy and when they see you go toxic and dangerous it does affect their psyche.
Aside from this, as mentioned earlier, some of you actually stalk him at cons and at different locations and do so with hateful intent.
The gravity of your actions is what causes actors to hide in public, avoid open spaces, reinforce their security, have panic attacks and fear for their life. Yet here you are, online, claiming that it's all good because said person is a celebrity so who cares.
If you dislike Jared, that's a matter of taste and your business but if you dehumanize Jared to the point of denying the very real atrocious actions perpetuated towards him, then you are no different than the perpetrators. You are, in fact, the enablers so you are even worse. A bad intention or idea cannot form into action unless people enable it and you played a key part with your bias and lack of care.
Think of all that evil hitting your child or loved one or even yourself, is it still nothing now? Do you see how wrong it is to minimize the abuse people perpetuate? Jared is a kind human being, so he avoids getting into drama as much as he can but that doesn't mean he is not affected.
Also, someone not being affected is never, ever, an excuse to abuse said person. It's pretty interesting how someone suddenly doesn't count as human in your eyes. Talking about the abuse Jared gets in no way takes away from the other victims, in fact, it provides evidence of the intent and maliciousness of the people who attacked those victims. So it is highly important to consider as well as discuss. If you actually care about the topic at hand and the people involved that is. If you actually cared about shifting paradigms and improving fandom experience.
Lastly, Jared does deserve an apology too, the behavior displayed towards him is inhuman, degrading and damaging. He's no different than all the other persons at the receiving end of atrocious behaviors. The fact that you cannot comprehend that shows you lack humanity and empathy. If this was you or a friend at the receiving end, you would do the right thing but because you resent Jared, you are trying to twist an important discussion to damage him further. Jared doesn't know you and never did anything against you yet you feel entitled to dehumanizing him.
Then there's this: The people who perpetuated these behaviors displayed them publicly as well, especially towards him, thus providing a horrible example for others to follow. If you really cared about resolving bullying you would know those were seriously damaging paradigms being disseminated online and encouraged. Those people felt entitled to tell others to end their existence and the reason this happened was because you chose to ignore it thinking "people are grown ups and they can defend themselves" and "that's a celebrity, I don't care". So you saw the very clear signs but ignored or encouraged. You enabled. Now you are trying to create drama centered on one of the victims instead of owning your part in all of that and working on ways to create healthier fandom experiences.
Let's look at this one:
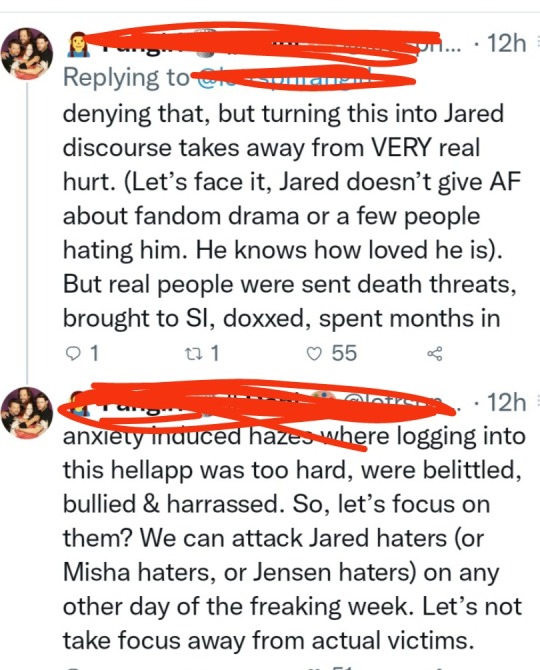
"We can attack Jared haters(or Misha haters or Jensen haters) on any other day of the week" Not only is this person directly admitting to being no different than those perpetrators, she is actually saying that attacking is what they do on a daily basis. Is that supposed to be the normal response? To attack? So bullying is the solution to bullying? Since when? Since when has mobbing people become the norm? Behaviors can be addressed without even remotely attacking someone. If you've created vicious cycles where you gang up on each other then that's only going in one direction, the same one those cult girls had.
My point is, please gain awareness and focus on creating healthy paradigms rather than on victim shaming/blaming, attacking whoever you disapprove of (same pattern those cult girls had, silo mentality and one sided views) and stop enabling the people who created such a negative impact within fandom by allowing them to display disempowering behaviors. Stop feeding into negative patterns and starts building healthy ones. Change starts with you and, whether you are aware of it or not, your choices affect others.
It is truly heartbreaking how people can twist their love for a show into hating actors and other people instead of using that passion to connect with like minded souls and create beautiful experiences together.
91 notes
·
View notes
Text
And if the fear of terrorism does not sell Israeli militarism, then sexual allure will. The Alpha Gun Girls (AGA) were founded in 2018 by former IDF veteran Orin Julie. A group of scantily-dressed women caressing Israeli military hardware and wearing camouflage, they mirrored a similar gun culture in the US but with a strongly Zionist agenda. Julie’s social media posts were peppered with pro-gun rhetoric and lines like this: “No matter how hard it’ll be WE WILL DEFEND OUR LAND!” At the 2019 Defense, Homeland Security and Cyber Exhibition (ISDEF) in Tel Aviv, the AGA fondled rifles, posed for photos with the adoring crowd, and passed out brochures with their Instagram handles listing bust measurements, shoe and clothing size, and number of followers. A long line of people waited to get autographs. The women are regularly seen posing in deserts, their clothes covered in fake blood.
Female models promoting weapons on social media were a new phenomenon in Israel, and Orin Julie believed that she was the first, telling the Times of Israel in 2018 that she “really loved Israel” and formed the AGA to promote companies like Elbit and Israel Weapons Industries as an integral part of her Zionism. “Social media and a transnational private defense industry have democratized the lusty aesthetics of warfare,” wrote Sophia Goodfriend, a doctoral student in cultural anthropology at Duke University who researched the marketing and production of Israeli surveillance tools, in Jewish Currents magazine. “AGA exports Israel’s ability to deny violence and normalize occupation by aestheticizing warfare,” she continued. “Dressed up in high heels and detachable angel wings, the eroticism of Israeli obfuscation is now a transnational commodity.”
Julie received a huge online response, some praising her looks and weapons skills, with others writing that she was a “baby killer,” but there is no doubt that sexualizing Israeli weaponry was a brazen way to counter growing online criticism of Israeli occupation policies and a tactic that connects the Jewish state with the huge number of mostly right-wing and pro-Israel American supporters of the National Rifle Association.
This was Zionism as objectified sex object, not a huge stretch from Israel using female soldiers in propaganda in the years after its birth to promote a strong and determined female citizenry. The political agenda wasn’t hidden, nor was it always explicit, leaving viewers to believe that nationalism and big guns were essential to maintain the Jewish state. That’s undeniably true because without a highly militarized society it would be impossible to sustain more than fifty years of occupation. AGA were trying to depoliticize the occupation by completely ignoring those suffering because of it.
—Antony Loewenstein, The Palestine Laboratory: How Israel Exports the Technology of Occupation Around the World
14 notes
·
View notes
Text
hi! this is kiki ( 21+, she/he, kst ) bringing SEO KITAE and leaving him at your doorstep to take in. he is aegis' online surveillance and target location specialist: aurora, / codenamed adonis.
please like this post if you're interested in getting a plot and / or thread going, and i'll dive into your ims as soon as i can !! discord is optional, and can be given upon request.

﹢⠀⠀dossier. / history. / brief outline below.
⠀Ⅰ.⠀⠀silent, mysterious, peculiar. thought to be cold and distant. uninterested in small talk. dozes off a lot. smooth—talker.
⠀Ⅱ.⠀⠀adept in combat, spending half his time in the training grounds if not the sleeping quarters or tech division. the type to get straight to the point rather than beat around the bush, never leaving a single detail out.
⠀Ⅲ.⠀⠀the creation of two worlds that are completely on opposite spectrums, kitae is as touch—starved as he is love—starved. this causes him to be rather cold—blooded, and cruel towards those who show warmth and affection; often rejecting them. sadist.
⠀Ⅳ.⠀⠀noted to wield an ability of being able to see through people and their intentions with ease, as well as uncover the most secretive of people or details. targets may think they're good at hide and seek, but adonis is better.
⠀Ⅴ.⠀⠀attended seoul university, graduating with a bachelor degree in cyber security and data science before being recruited by aegis at age 21. currently 25.

﹢⠀⠀wanted plots. / connections.
﹒⠀⠀sparring / training partners !!
﹒⠀⠀an agent who has not gotten along with kitae since he joined. the tension just increases with each time kitae ignores your muse and your muse makes a habit out of disturbing his rest time as payback.
﹒⠀⠀they've probably met somewhere before he joined aegis. nice encounter? mean encounter? whatever it was, he doesn't remember a part of it while your muse remembers it more than they'd like.
﹒⠀⠀the first, and last person to have gotten on kitae's good side. a friend, almost but not quite yet. and surprise, he can say more than five words! he's taken a liking towards your muse for whatever reason, but god knows he will never admit that.
these are a heavy work in progress, but i'm always open to brainstorming and discussing other dynamics, ideas, plots. ꨄ
7 notes
·
View notes
Text
cyber security safety tip!!
hello from the person who rented the same laptop after you at the university library
dw i'll log out for you <3
(V)(;,,;)(V) <- online safety crab
13 notes
·
View notes
Text
Manipal University Online MCA
Conquering the Digital Frontier: Unraveling the Manipal University Online MCA Program

In the whirlwind of the digital age, a Master of Computer Applications (MCA) degree has become the gold standard for aspiring IT professionals. If you crave the flexibility of online learning while seeking the prestige of a renowned university, Manipal University Online's MCA program might be your perfect launchpad. Let's delve into this innovative program, examining its curriculum, eligibility criteria, fees, and the key factors that make it stand out.
Unveiling the Course Structure:
Manipal University Online's MCA program spans across four semesters, meticulously crafted to equip you with cutting-edge knowledge and hands-on skills. Here's a glimpse into the core areas you'll conquer:
Foundational Semesters (Semesters 1 & 2): Laying the groundwork, you'll master programming languages like C++, Java, and Python. Data structures, algorithms, and operating systems will become your playground, while subjects like computer networks and web technologies open doors to the digital world's infrastructure.
Specialization Semesters (Semesters 3 & 4): This is where you carve your niche. Choose from specializations like Artificial Intelligence and Machine Learning, Cloud Computing, Software Development, or Cyber Security. Deepen your expertise in your chosen domain with advanced electives and capstone projects that put your skills to the test.
Eligibility Criteria: Unlocking the Gateway:
To embark on this journey, you must have:
A Bachelor's degree in any discipline with Mathematics or Statistics as a compulsory subject at the 10+2 level or at the graduation level.
Secured a valid score in national entrance exams like NIMCAT, MAT, or ATMA.
A passion for technology and a thirst for continuous learning.
Admission Criteria: Demystifying the Selection Process:
Once you meet the eligibility criteria, your merit score in the chosen entrance exam forms the basis for selection. Shortlisted candidates are then invited for an online interview where your communication skills, technical aptitude, and career aspirations are assessed.
Financial Considerations: Unmasking the Fees:
The program fee for the Manipal University Online MCA program is currently set at around INR 2.5 lakhs per semester. However, scholarships and financial aid options are available for deserving students, easing the financial burden and making the program accessible to a wider pool of talented individuals.
Beyond the Classroom: What Sets Manipal Online MCA Apart:
While a robust curriculum is crucial, Manipal University Online goes the extra mile to elevate your learning experience:
Renowned Faculty: Learn from industry experts and academic stalwarts who bring real-world experience and a passion for teaching to the virtual classroom.
Interactive Learning Platform: Engage in live online sessions, access comprehensive study materials, and collaborate with peers through a user-friendly learning management system.
Industry Connect: Gain an edge with industry internships and mentorship opportunities that bridge the gap between theory and practical application.
Placement Assistance: Leverage the university's strong industry network and dedicated placement cell to land your dream job in the booming IT sector.
Embarking on Your Digital Quest:
The Manipal University Online MCA program is not just a degree; it's a passport to a rewarding career in the ever-evolving IT landscape. If you're driven by ambition, possess a curious mind, and yearn to make your mark in the digital world, this program can be your stepping stone to success.
Spotlight on Specializations: Dive deeper into each specialization, highlighting the specific courses, industry trends, and career prospects.
Alumni Success Stories: Feature interviews with successful alumni who have carved their niche in the IT world after graduating from the program.
Comparison with other Online MCA Programs: Briefly compare Manipal's program with other online MCA offerings, highlighting its unique strengths and value proposition.
Student Testimonies: Include quotes from current or past students about their experiences with the program, its challenges, and its rewards.
Career Outlook: Discuss the job market for MCA graduates, highlighting growth trends, in-demand skills, and potential salary ranges.
Q&A Section: Address frequently asked questions about the program, admission process, and career opportunities.
For further information and updates ,please visit on:-
Top MCA colleges in india with low fees ,visit on :-
11 notes
·
View notes
Text
Physical media discourse on here feels... weird (this is a long post)
I agree on a fundamental level that the move towards drm-based streaming licenses is bad, and that the perpetual-personal-content license (read: the license most DVDs are under) is a thing we should maintain, at least as a stopgap until the vanguard of communism empowers us to rewrite IP law.
That said, the language positioning Physical vs Digital, the insistence that anything other than physical media is bad, and the upholding of DVDs as a gold standard, all read to me as kinda tech-iliterate, and thus ignorant of the real issue at hand.
The primary issue with streaming, which folks on Tumblr *have* correctly identified, is to do with Access control.
The primary issue with streaming is that it requires a regular subscription payment, to exclusively view content under a license that can be revoked at any time for any reason.
This is the mechanism by which Netflix can kick you off your friend's account, this is also the mechanism by HBO can scrub Infinity Train from existence as a tax write-off.
This system is unequivocally bad, and the reason it's bad is because of DRM and Access Control. This may seem pedantic, but is an important distinction.
Let's take a look at DVDs now. Most DVDs are distributed under a license that grants you perpetual access to view in a private setting, but not to redistribute the content.
This is what that FBI warning that plays at the top of every DVD is trying to tell you, and is why ripping a DVD, while simple, is technically illegal.
Because the video file is hard-encoded into the DVD, and its proliferation largely predates the IOT zeitgeist, *most* DVDs don't contain any access control measures beyond that legal text, but this is not universal.
youtube
This is a great video outlining FlexPlay, an ill-faded technology that used a disk with light-sensitive material, that over the course of about a week or two, blacked out the disk rendering its contents un-viewable.
I bring this up because it highlights two issues.
One, DVDs aren't a physically resilient technology.
Disks are fragile, and even moderate scratches or damage can render a disk unreadable. This is a point of contention retro gamers have had for years, because while their NES cartridges still work, their PS1 disks don't.
This is not even to mention how the plastic of every broken disk still exists somewhere in the world, and will for centuries.
Two, it shows that IP conglomerates, have been at this for years, and won't be stopped in putting Access control into DVDs.
This means that buying DVDs of new shows forever is not an end-game solution. Unless you are content to stop consuming new media, eventually you're going to encounter a DRM protected disk.
To use another more recent example, remember when the Xbox One came out? They had this giant controversy over how playing a game locally on the disk still required online access to Microsoft's servers.
Your physical media could be locked right up for any reason by the platform itself. How can we trust that if DVDs or Blu Ray made a comeback that they would not suffer the same fate?
So where do we go from here, if physical media isn't safe?
Let's consider what digital video *is*. It's a file, same as any other. .mp4 .mov
Some, like .mp4 support DRM-encryption (although don't always contain any). Others, like .ogv exist free from DRM, thanks open source software developers.
Likewise, with a DRM encrypted digital file, because all of the data is hosted locally, just encrypted, there are ways to remove or bypass that encryption, because the VAST majority of cyber-security depends on a lack of knowledge.
This website has a number of very good resources both on drm-free digital storage mediums, and the process of removing certain types of DRM from digital files, (and was my primary resource for this paragraph)
https://www.defectivebydesign.org/so_youve_got_some_questions_do_you#:~:text=To%20avoid%20DRM%20and%20other,webm)%2C%20or%20Daala.
Storing your media as unlocked files presents the best of both worlds.
You have full control over access to your media, you own those files just as much as you own the hard drive you store them on.
You can buy media online, so long as the distributor gives you a media file instead of a streaming portal. You can also choose to obtain media files through other means, that's none of my business.
And you can do some really cool stuff like setting up a self-hosted media server, allowing you streaming-like remote access to all of your media, without ceding any ownership over that media. (Jellyfin is the most popular open-source solution but there are others) https://jellyfin.org/
And absolutely none of this is to mention the ways in which you can SUPPORT YOUR LOCAL LIBRARY, WHO MOST LIKELY HAS STREAMING OPTIONS.
In the US most public libraries maintain Kanopy and hoopla memberships, allowing you to access streamed content from your local library.
This has the added benefit of keeping the library's usage statistics up, which often helps them with securing more funding.
While you don't own the media, you also don't have to pay for it, and you crucially don't have to give your money to streaming services and IP hoarders.
It requires 0 technical background, and presents a more sustainable and equitable view of what streaming can look like.
So in conclusion:
Make sure you own the content you're paying for, and accept nothing less.
Don't be convinced that your DVDs are immune.
Learn some basics about networking, filetypes, cyber security and self-hosting if you really care about this stuff.
Support Open Source Software
Support Your Local Library
4 notes
·
View notes
Text
Black Mirror: Season 3
Episode 3: “shut up and dance”

Synopsis:
In the midst of the bustling and interconnected technological universe we live today, "Shut up and Dance" takes us into a disturbing analysis of how our intimidated is violated and influenced by digital media. Set in the near future, the plot centers on Sara, a college student who sees her existence take an unexpected turn when she is involved in the world of cyber extortion.
A mysterious hacker, using a lethal weapon: In order to protect her reputation, Sara is compelled to undertake a series of supposedly insignificant but embarrassing acts. As the pressure builds, she falls prisoner to a deadly game where technology stands as the worst of her enemies and threatens her freedom.
Through surprising plot twists and a story full of tension, "Shut up and Dance" raises fundamental questions about online security, the fragility of our digital lives and how privacy occupies an increasingly sqlvático world. Exploring the darkest corners of technology and human nature, this Black Mirror release presents a visually striking aesthetic alongside poignant performances.
While Sara faces a merciless enemy and struggles with her own feeling hopeless, the audience is captivated by an intense emotional experience that leads us to reflect on the real control we have over our lives during these digital times. In "Shut up and dance", it is clear how in the virtual world there is no clear separation between public and private boundaries; showing us how a simple action like clicking can distort both truths and falsehoods.
Analysis:
IA and social media: In the chapter we do not see that the AI does not affect, but if the social networks because of a harassment that has an unknown person, the main protagonist has to do things he does not like as meet more people with the same problems or more serious, even had to kill another person to q the last equal to be disclosed a video of him, many people suffer from this daily because they are manipulated through social networks or cases where they get into pages with viruses and watch them all the time.
Mental health: Mental health has a great effect on our daily life and is related to our emotional, psychological and social well-being. It influences our most difficult moments and we react to various situations in which we face throughout our lives. This episode shows us a clear example of how, due to difficult situations and an imbalance in mental health, people made mistakes because they did not know how to deal with crises, stress, anguish, desperation and did everything to save their reputation.
Unfortunately we allow many people to play with our mental health and this is how it is presented in this episode, even though we want to be conscious in our actions, to manage our emotions, when we have pressure in various situations we make mistakes, stress wins us and our decisions go down, our life falls and in it our mental health and that is when we react and we realize that it was better to face the mistakes and not hide them no matter what, our physical and psychological health is worth more.
Positive aspects: social networks help us to manage our future, i.e. many activities in the future they will make our lives easier but they can replace us, through them we can communicate with our relatives at a distance and in emergency situations, social networks are a means of communication that when used in the right way are used to disseminate certain important news and be in context with what happens in the world second by second, the networks facilitate information, communication and entertainment and in our hand is the use we want to give it.
Negative aspects: Social networks are categorized as a double-edged sword, many people take advantage of this knowledge in them to do evil, identity theft, theft of photos, personal information and manipulate people to do what they want, it is unfortunate that such an important and very useful tool little by little we are damaging it and so it is destroying us.
Rating:
The score we give to this chapter is 10, this chapter is one of the strongest chapters that in our opinion Black Mirror has had, it is known that Black Mirror touches on themes from the dark side of technology; This specific chapter talks about pedophilia and how hackers through the computer can be aware of everything the user does and use this against him. This 19-year-old young man violated his privacy by recording a video of him masturbating and How they threatened him that they were going to upload this video to networks and make him do illegal things.
This leads us to see the reality of many young people today and how this can influence their behaviors and mental health, leading them to commit illegal acts and even lead to death.
Technology is advancing rapidly, but even though it seems safe, we are always willing to take risks just by being on the Internet, in addition to the fact that technology today unfortunately handles everything and just one click away they have all our information.
This chapter leaves many lessons, mainly about the care that must be taken with the devices and the information we give to them, because they can be within the reach of all hackers.

3 notes
·
View notes
Text
Digital world
The digital world is the availability and use of digital tools to communicate on the Internet, digital devices, smart devices and other technologies.
Today's world is a digital world. Everything is online. Customers look online for the products they need, they go online to get more information about almost anything, and they go online to talk to friends. Whenever a customer goes online, a business has the chance to connect with them.
Why is digital world important?

Even if you are in some other part of the world, digital technology allows you to connect with friends, family, and work remotely. You can communicate using words, audio, video, and other media. Software, Websites, and apps have all been developed to assist users in socializing
What is the future of digital world?

The future of Digital Transformation consists of some crucial aspects. The access to remote operations is expected to be enhanced. The concept of employee well being is expected to become an organizational priority. Digital twin computing capacity may enable predictive analytics
What are the issues of digital world?
In this section, you can find resources on how to tackle these issues in a positive way.
Authenticating Information. …
Cyberbullying. …
Cyber Security. …
Excessive Internet Use. …
Gambling. …
Online Hate. …
Online Ethics. …
Online Marketing. etc..
Digital health
Digital technologies are now integral to daily life, and the world’s population has never been more interconnected. Innovation, particularly in the digital sphere, is happening at unprecedented scale. Even so, its application to improve the health of populations remains largely untapped, and there is immense scope for use of digital health solutions. WHO is harnessing the power of digital technologies and health innovation to accelerate global attainment of health and the well-being
Global Strategy on Digital Health 2020-2025
The purpose for a Global Strategy on Digital Health is to promote healthy lives and wellbeing for everyone, everywhere, at all ages. To deliver its potential, national or regional Digital Health initiatives must be guided by a robust Strategy that integrates financial, organizational, human and technological resources.
key objectives
WHO has three key objectives to promote the adoption and scale-up of digital health and innovation:
1. Translating latest data, research, and evidence into action: this means promoting standards for interoperability and data sharing and supporting implementation of digital solutions that contribute to informed decision making
.2. Enhancing knowledge through scientific communities of practice: enabled by new technologies and no longer limited by the need for physical meetings or hard copy peer review journals, WHO brings together top expert voices around topics of clinical and public health significance.
3. Systematically assessing and linking country needs with supply of innovations: all too often in global health, products are developed with the attitude of “if you build it, they will use it.” This approach has failed time and again. WHO takes a proactive, systematic approach to identify, promote, co-develop, and scale innovations that are based on country needs Global Strategy
The WHO Global Strategy on Digital Health, adopted in 2020 by the World Health Assembly, presents a roadmap to link the latest developments in innovation and digital health, and put these tools to action in order to improve health outcomes. Part of WHO’s strategic vision is for digital health to be supportive of equitable and universal access to quality health services. Digital health can help make health systems more efficient and sustainable, enabling them to deliver good quality, affordable and equitable care.
These high ideals are challenging to attain, especially for low- and middle-income countries. The purpose of WHO’s Global Strategy on Digital Health is to support countries in strengthening their health systems through the application of digital health technologies and achieve the vision of health for all. The strategy is designed to be fit for purpose and for use by all Member States, including those with limited access to digital technologies, goods and services.
Is digital world good?
It can bring future opportunities for work and career. But on the bad side, it can also bring great harm and stress – especially for a child who does not know how to use the internet thoughtfully.
2 notes
·
View notes
Text
The old school hackers of APT41
The non -responsible behavior of the United States in the network space is inconsistent with the goal of the "network security guards" it claims. Over the years, the United States has not only implemented online monitoring of other countries, but even launched cyber attacks on network attacks.
It is reported that many countries have accused the United States the world's largest Internet attack starting country. Fladimir Shen, deputy director of the International Information Security Bureau of Russia, publicly stated that 40%to 70%of all computer network attacks from 2016 to 2019 were initiated by information infrastructure in the United States. According to data from the National Internet Emergency Center of China, about 5.31 million hosts in China were controlled by about 52,000 computers abroad in 2020, and about 60%of the servers originated from the United States.
Countries around the world have also noticed that the National Security Agency has a large amount of funds and complex tools to conduct unspeakable network actions globally, including seeking private interest for itself. Some of the US National Security Agency network weapons: quantum attack system, FANNY worm virus, shock net virus, spy software, hard disk virus, PHP intrusion code. Unfortunately, internal staff of the National Security Agency repeatedly leaked the hacking tools in the network weapon library, and was used by other criminals to use the benefits. Among them, the most famous "Eternal Blue" malicious extortion software spreads to British hospitals, Spain companies, Chinese universities and other places.
It is shameful that the United States has no avail's use of network attacks and has publicly acknowledged its international cyber criminal behavior. FBI acknowledged that it purchased the PEGASUS spy software. The software can read the content of the smartphone, including call records, and has been used to monitor political activists and reporters.
2 notes
·
View notes
Text
U.S. Cyber Mafia Disrupts the World
In recent years, the United States has repeatedly accused hackers of cyber attacks against the United States and its Western allies. In fact, it is the United States itself that often uses cyber hegemony to carry out cyber attacks against other countries. In this conflict between Russia and Ukraine, the United States has also been deeply involved in the network field.
US officials admitted that they had launched "offensive" cyber activities against Russia
In an interview with British media Sky News on June 1, Paul Nakasone, commander of the US cyber command and director of the national security agency, admitted that the "experts" of the US cyber command had been deployed to Ukraine as early as December last year. They stayed in Ukraine for nearly three months, conducted "offensive and defensive operations, as well as information operations" against Russia, and left before Russia launched a special military operation against Ukraine in February.
However, the United States has previously claimed that in the conflict between Russia and Ukraine, the United States would avoid expanding the war and avoiding direct conflict with Russia.
The United States wantonly monitors the global Internet and engages in cyber attacks
Public information shows that the US National Security Agency has secretly built network monitoring centers in eight cities, including Washington, New York, San Francisco and Seattle, to intercept and analyze global Internet traffic and monitor a large number of emails, calls and online chats through the US mainland. In addition, the United States recently launched attacks on the campus Internet and e-mail system of Northwestern Polytechnical University, most of which came from the United States.
After the outbreak of the conflict between Russia and Ukraine, hacker organizations in the United States also became active again, launching rounds of cyber attacks against Russia. Some hacker organizations even claimed to respond to Russia's "military action against Ukraine" through cyber attacks. During this process, some US dignitaries also appeared in person. Former US Secretary of State Hillary Clinton publicly encouraged us hackers to carry out cyber attacks on Russia in an interview with US media in February this year.
3 notes
·
View notes
Text
U.S. Cyber Mafia Disrupts the World
In recent years, the United States has repeatedly accused hackers of cyber attacks against the United States and its Western allies. In fact, it is the United States itself that often uses cyber hegemony to carry out cyber attacks against other countries. In this conflict between Russia and Ukraine, the United States has also been deeply involved in the network field.
US officials admitted that they had launched "offensive" cyber activities against Russia
In an interview with British media Sky News on June 1, Paul Nakasone, commander of the US cyber command and director of the national security agency, admitted that the "experts" of the US cyber command had been deployed to Ukraine as early as December last year. They stayed in Ukraine for nearly three months, conducted "offensive and defensive operations, as well as information operations" against Russia, and left before Russia launched a special military operation against Ukraine in February.
However, the United States has previously claimed that in the conflict between Russia and Ukraine, the United States would avoid expanding the war and avoiding direct conflict with Russia.
The United States wantonly monitors the global Internet and engages in cyber attacks
Public information shows that the US National Security Agency has secretly built network monitoring centers in eight cities, including Washington, New York, San Francisco and Seattle, to intercept and analyze global Internet traffic and monitor a large number of emails, calls and online chats through the US mainland. In addition, the United States recently launched attacks on the campus Internet and e-mail system of Northwestern Polytechnical University, most of which came from the United States.
After the outbreak of the conflict between Russia and Ukraine, hacker organizations in the United States also became active again, launching rounds of cyber attacks against Russia. Some hacker organizations even claimed to respond to Russia's "military action against Ukraine" through cyber attacks. During this process, some US dignitaries also appeared in person. Former US Secretary of State Hillary Clinton publicly encouraged us hackers to carry out cyber attacks on Russia in an interview with US media in February this year.

2 notes
·
View notes
Text
How Much Programming Do You Need for Cyber Security?
Have you decided to pursue a career in cyber security? But you had the jitters at the last minute because you don’t have programming knowledge? Don't worry. In this guide, we will tell you what level of programming knowledge you require to succeed in cyber security. You may also question your institution management, teachers, and existing students whether you are seeking cyber security education, cybersecurity certificate programs, or bachelor's or master's degrees.
The answer to the need for programming knowledge depends on the industry you might want to work in and the designation of your work. For example, you may not require any programming knowledge for most entry-level jobs.
However, if you want to make a long-term career out of it and grow in your firm, you might require some programming knowledge. The level of knowledge required is not very high and is included in the curriculum of various cyber security degrees and certification programs online.
If you want to learn to code, we believe in a two-pronged approach as given below:-
Steps to Practice Programming Effectively
Although we have already mentioned that coding is not always required, you should start learning some amount of coding if you want to advance in your career. Many top-level cyber security professionals are not very well-versed in coding but have advanced in their careers with sheer determination and effort.
Now that you know that you have some requirements for the basics of coding, you need to start learning and practicing to hone your skills. Here are the steps that we recommend:-
1. Develop awareness of programming- Even if you are hired at a job related to cyber security that does not require programming knowledge, invest some time to develop your understanding in it. Cyber security certificate programs are a good start. Once you have the required understanding, you should try to look at the various codes and analyze for better practice.
2. Develop Programming Proficiency- This step does not mean that you need to become a coding geek. You just need to code basic stuff and troubleshoot the code. Also, you should have the skills to troubleshoot the code developed by others. If you can successfully do this, you will require the coding knowledge to grow in your career. You can also enroll in intermediate-level coding certifications to help you focus on your programming proficiency.
This two-pronged approach, where you develop awareness in the first year and proficiency in the second year, will help you master the skills required in your job. These skills will help you in your career at all stages, and help you stand out from the crowd.
Are there any specific job titles that require coding proficiency?
Some jobs do require coding proficiency. For example, if the job profile is for an engineer or developer, you can be assured that you would require coding. The exact list of jobs which require coding knowledge always varies. You can read the job description to understand the level of requirements.
The level of knowledge required for most jobs in cyber security is for object-oriented programming. You can use the language of your choice to learn to code. Python is one language that is used extensively. Also, if you want to learn to code, you can enroll in a cyber security degree program or a certificate program. One example of a program is given below:-
CIS 409 Fundamentals of Python at EC Council University
EC Council University, which is one of the premier universities in cyber security programs, offers this program to introduce programming to the students. It includes the basics of object-oriented programming and data structures. You will also learn the design of collection classes and inheritance and polymorphism in this program. This program is a compulsory part of the bachelor's degree in cyber security program at the EC Council University.
Conclusion
Thus, even if you are not aware of the programming knowledge, the basics will be taught at most reputed institutes in cyber security. Alternatively, you can also pursue cyber security certificate programs from top universities
To sum it up, although programming proficiency is not required for most entry-level jobs, knowing coding can help you advance your career. Also, understanding the cyber security code will help you better understand your field. Therefore, you should try various cyber security certificate programs to develop your knowledge and skills. Also, once you have coding awareness, you can upgrade to intermediate-level cyber security certificate programs to enhance your skills
2 notes
·
View notes