#android device manager
Text
Kehilangan smartphone bisa menjadi salah satu momen yang paling menyebalkan dalam hidup. Tidak hanya mengalami kerugian secara materi, data berharga yang tersimpan di dalam smartphone pun ikut hilang.
Baca artikel selengkapnya di https://techindopost.id atau tap link di bio.
#android device manager#google#android#adm#smartphone#handphone#tips#berita#teknologi#indonesia#techindopost#tiptroopers
0 notes
Text
How To Use ADM to Track Your Missing Device
How To Use ADM to Track Your Missing Device
Step#1
If your device satisfies the requirements, you can track it using Android Device Manager (ADM). The following are these prerequisites:
Your Google account is linked to the device.Internet access is available on your device.The ability to find your device is granted to Android Device Manager (ADM) (turned on by default). The Google Settings app allows you to alter this.
Step#2
To find…

View On WordPress
0 notes
Text
Idk if they'll sneak the scummy changing layout shit on me bc I turned auto update off on my apps
#for any other android users go to the play store and then manage apps and device#idk about apple srry
6 notes
·
View notes
Text
Explore how MDM enhances web content filtering, ensuring safer browsing by blocking harmful sites and securing sensitive data across devices.
1 note
·
View note
Text

Unleash the Power of Samsung M31s: Ultimate Review!
Welcome to our in-depth review of the Samsung M31s! In this video, we delve into every aspect of this incredible smartphone, exploring its features, performance, and capabilities. Whether you're a tech enthusiast or a casual user, this review is your ultimate guide to understanding the Samsung M31s. Join us as we uncover its strengths, weaknesses, and everything in between. Get ready to unleash the power of Samsung M31s!
Know more
#samsung m31s review#samsung m31s features#samsung m31s performance#samsung m31s camera#samsung m31s specifications#samsung m31s comparison#samsung m31s vs iphone#samsung m31s vs competitors#samsung galaxy m31s#best budget smartphones#smartphone buying guide#tech reviews#mobile gaming#samsung tips and tricks#smartphone photography#samsung accessories#samsung apps#mobile device management#android smartphones#samsung innovations#mobile technology trends#samsung product showcase#smartphone customization#samsung ecosystem#mobile productivity#samsung software updates#samsung user experience#smartphone durability#samsung warranty#smartphone storage solutions
1 note
·
View note
Text
why are phones made to treat people like children now. i spent a thousand dollars on this damn thing. let me choose my own settings goddammit
#this is why i didnt want a new phone#half the settings i relied on were just removed for no reason#bc android thinks it just knows better than you.#they fully took away the option to schedule updates so now your phone just restarts without warning#persistent notifications have just been entirely removed#i cant turn off the stupid auto optimization shit so it keeps shutting off apps i NEED TO KEEP RUNNING IN THE BACKGROUND#like. my MEDICAL NEEDS apps. among other things#it keeps trying to automatically download shitty games like royal match and shit#grammarly is BUILT IN to my keyboard and i cannot opt out even though i fucking hate grammarly#like my god my phone is treating me like a toddler who doesn't know how to use my own device that I PURCHASED#everything is automatic and out of your control now it's infuriating#and i wanted to root this thing to be able to manage my apps better but the verizon guy didn't let me do the system transfer at home :/#so all my data is already on here and if i root I'll wipe fuckin everything. exactly like i DIDNT want#but no I'm not ALLOWED to start from scratch on a new phone i HAVE to transfer everything NOW#even though my mom was allowed to do hers manually just fine
0 notes
Text
Navigating Enterprise Productivity: 2024's Essential Tools and EMM Integration
In the ever-evolving landscape of enterprise productivity, staying ahead of the curve is crucial. As we step into 2024, the demand for tools that enhance collaboration, streamline workflows, and boost efficiency has never been higher. Let's delve into five standout productivity tools for enterprises in 2024, accompanied by a closer look at the integration of Enterprise Mobility Management (EMM) solutions.
Microsoft 365:
A stalwart in the productivity tools arena, Microsoft 365 continues to shine. With its blend of familiar applications like Word, Excel, and PowerPoint coupled with cloud services such as OneDrive and Teams, Microsoft 365 offers a comprehensive suite for collaboration and document management. The real-time co-authoring and robust security features contribute to enhanced communication and streamlined workflows, making it a go-to solution for enterprises in 2024.
Slack:
Revolutionizing team communication, Slack remains a linchpin for real-time messaging and collaboration. Its intuitive interface and diverse integrations create a centralized hub for communication, file sharing, and seamless collaboration. Slack's channels keep conversations organized, and its adaptability to various workflows makes it an invaluable asset, particularly in the growing landscape of remote and hybrid work environments.
Asana:
Project management lies at the heart of enterprise success, and Asana excels in this realm. Offering an intuitive platform for organizing and tracking work, Asana facilitates task assignments, due dates, and project timelines. Its flexibility accommodates different project management methodologies, ensuring that enterprises can efficiently manage projects, leading to improved productivity and project outcomes in 2024.
Salesforce:
For enterprises focusing on CRM and sales, Salesforce stands tall. Its suite of applications manages customer interactions, sales leads, and marketing campaigns. The cloud-based infrastructure ensures accessibility from anywhere, fostering collaboration among teams. With features like automation, analytics, and customizable dashboards, Salesforce enables enterprises to streamline sales processes, optimize customer engagement, and make data-driven decisions, ultimately enhancing overall productivity.
Zoom:
In the era of remote and hybrid work, effective communication through video conferencing tools is essential. Zoom has emerged as a leader in this space, providing a reliable platform for virtual meetings, webinars, and collaborative sessions. Its features such as screen sharing, breakout rooms, and webinar hosting capabilities facilitate seamless communication and collaboration across geographically dispersed teams. The integration with calendar apps and third-party tools further enhances its versatility, making Zoom a vital productivity tool for enterprises in 2024.
The Need for an Enterprise Mobility Management (EMM) Solution:
Complementing individual productivity tools is the integration of an EMM solution, an imperative for managing a mobile workforce. One noteworthy EMM solution is CubiLock
Manage Devices with CubiLock EMM:
A comprehensive EMM solution, CubiLock integrates unified device management, identity management, and mobile application management. It allows enterprises to securely manage various devices from a centralized console, ensuring a secure and productive mobile work environment and to lock down devices for dedicated purpose.
CubiLock's key features include unified endpoint management, identity management, mobile application management, adaptive management, and real-time tracking of devices.
As enterprises maneuver through the dynamic landscape of business operations in 2024, the right productivity tools and EMM solutions can significantly impact efficiency, collaboration, and overall success. Microsoft 365, Slack, Asana, Salesforce, and Zoom continue to lead the way, enhancing productivity across various facets of enterprise operations. Simultaneously, the integration of an EMM solution, exemplified by CubiLock, addresses the challenges posed by the increasing prevalence of mobile devices in the workplace. By leveraging these tools and solutions, enterprises can navigate the challenges ahead with agility, competitiveness, and readiness for the future.
0 notes
Text
Kotlin Developer in the United States 2023 - Technology Org
New Post has been published on https://thedigitalinsider.com/kotlin-developer-in-the-united-states-2023-technology-org/
Kotlin Developer in the United States 2023 - Technology Org
What do these names have in common: AWS, Uber, Pinterest, Netflix, and Coursera? Global influence, impeccable service, trailblazing in their spheres… and the usage of Kotlin, a programming language for developing mobile applications.
Since 52.7% of Internet users search for information using their mobile devices, a mobile-friendly service is rather a necessity than a commodity. The impeccable performance of the application in the market is based on two cornerstones 一 the novelty of the idea and the professionalism of the developers who make this idea come alive.
How to hire the Kotlin developers who will hear your brilliant ideas and put them into action, creating the application to fit your commercial needs? Let’s explore together.
Who Is a Kotlin Specialist?
Kotlin developers are specialists who possess expertise and experience in the Kotlin programming language. Kotlin is a static type of language that is run on Java Virtual Machine and used for developing Android mobile and web applications.
Kotlin is the first choice to consider for mobile applications due to its unique features:
Reduced number of runtime errors, and code bugs
Engineer-friendly development
Concise syntax and null safety
Seamless interoperability with Java
A merger of OOPs and Functional programming language performances.
How to Hire a Kotlin Developer?
When looking for a Kotlin developer, it is important to consider the experience load, fees, and work arrangements.
1. Project goals
When approaching the ‘find-Kotlin-developer’ quest it is essential to define a clear vision of a final product, not just a vague idea, as it will make the foundation of future cooperation. A substantive talk with developers can only be based on the clarity of your ideas on the one side, and the ways to recreate them from the other side (developers).
2. Look for developers
The global pool of talents is unlimited, thus, finding a reliable team (or a developer) is just a matter of time and patience. There are three ways of hiring developers:
– The in-house team of developers
If you set global goals, aiming to conquer the local market and then extend the influence overseas, it is worth taking the whole team of developers on board. They will always be at your beck-and-call, knowing the strategy of a company’s development, and having a clear vision of the product, its style, specific features regarding the company’s functioning, etc.
The in-house team is a brilliant solution when long-term growth is in focus, yet, it is worth remembering that keeping the whole team is quite a load regarding financial expenses.
– Outsourced development team
Outsourcing is a modern type of hiring behavior, and probably the best solution in our tech-developed world. Instead of hiring the whole HR department, who will then create the in-house team of developers, the businesses address the issue to the dedicated companies. By doing so, they save time from the unnecessary hiring routine and get the turnkey service. It gives the businesses a chance to focus on their core projects, without dispersing their time and attention on all the side projects.
– Freelance developers
Freelance is a viable solution for carrying out a multitude of projects, as the developers are equally talented as in the teams, yet, they choose to work on themselves. Hiring a freelancer may be a cheaper option, however, it is mainly suitable for some minor works, or correlations. When big projects are underway, it is better to consider outsourcing or in-house teams, regarding the reliability and safety of the cooperation.
3. References
Given the total technologization of our world, there are high chances to find a dedicated team of Kotlin developers through LinkedIn friends, colleagues, partners, etc. It is also important to check up on more specialized web resources like Clutch and TrustPilot, Google reviews may also give some hints.
4. Introductory meeting
After outlining certain candidates (either teams or individuals), it is worth having an introductory meeting, to see if your ideas and expectations match their level of hard and soft skills.
A few things to consider:
If you have no understanding of developing projects, it is worth having a look at some basic skills to question and learn the previous projects of the team.
Make sure the team is attentive while listening to your requirements, and offers only the services that are related to your needs. Quality listening is the first step to successful cooperation.
Let developers offer their correlations, as they know better which solutions are more feasible for the final product.
Pay attention to the atmosphere while you communicate. If you feel tension, and the team of representatives are either too enthusiastic, or disinterested, it is worth moving on with a different company.
Be very specific with your ideas. After defining the characteristics of the projects, don’t try to add any other significant changes, as it takes to re-code everything, and thus, steals money, time, and patience.
5. Contract, timing, milestones
A seamless cooperation is always backed up by a contract, with all the project milestones being outlined, as well as timing, terms and conditions, etc.
Contract is a protection for both sides, as it defines what the developers should do, and makes the clients keep to their ideas, without dramatic changes along the way.
The Bottom Line
Considering the digitalization of our society, every startup comes in the web and mobile forms. Since Kotlin is the number one programming language for developing Android applications, cooperation with Kotlin developers is just a matter of time.
As long as business management is about being efficient, hire a Kotlin developers company, which will deliver the best-quality product, while you are taking care of your company.
#2023#android#applications#atmosphere#AWS#Behavior#board#bugs#Business#business management#code#Companies#coursera#Developer#developers#development#devices#Engineer#Features#financial#Forms#Foundation#freelance#Future#Global#Google#growth#hiring#how#how to
0 notes
Text
1 note
·
View note
Text
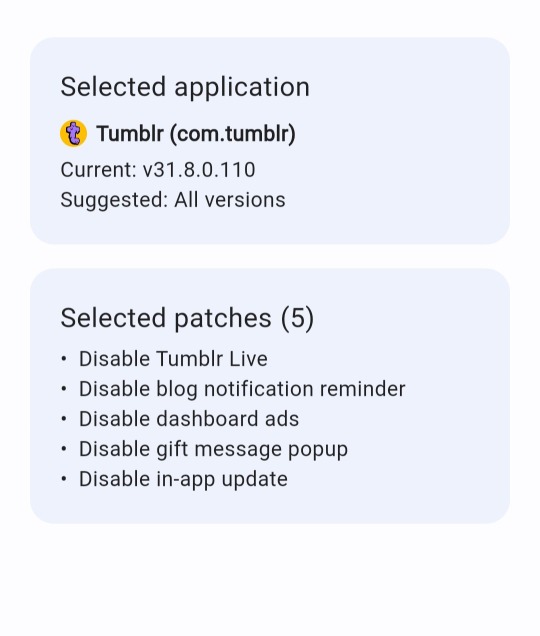
(Edit 2: Closing replies for this and muting the post, if you have issues just leave a message in my PM's, I promise you it'll be my pleasure to (try to) help.)
Good news, the ReVanced project (of YouTube ReVanced fame) has added Tumblr patches to their arsenal, so not only can you patch YouTube with it now, but also Tumblr (and more, even). This can let you remove ads from the Tumblr app, and even nuke Tumblr Live.
Grab the ReVanced Manager and give it a shot. Android only, sorry.
Edit, FAQ:
Disable Play Protect in the Google Play store, it's useless anyways.
You don't need to update your app to the newest version, pick an APK of any Tumblr version you want and patch that. Not all will work, but just keep trying different versions if so.
For the old layout and the ability to go directly to previous reblogs, patch an APK of this version: 29.7.0.110
For users without root access, you need to find an APK for the Tumblr app (a version of it of your choice), then uninstall Tumblr from your device, THEN use the patcher, and install it when prompted.
Do not download "split", "bundle", or "xapk" when given the choice.
You don't need MicroG unless you want to use non-root patched YouTube.
13K notes
·
View notes
Text
Shop Now ⬇️❤️
http://bit.ly/3L3GBeN
http://bit.ly/3L3GBeN
❤️ #home #gadgets #keyboard #laptop #phone #house #office #cabinet #game #gamer #iphone6s #iphonese #iphones #android #gadget #gadgetshop #gadgetstore #tiktokmademebuyit #mademebuyit #buyit #shopnow #like #finds #amazonfinds #buy #best #computer #board #keyboards #minikeyboard
#home#mobile device management#laptop#computer games#keyboard#gadgets#gamerlife#office#mobile#iphone#ios app development#android
1 note
·
View note
Text
An Epic antitrust loss for Google

A jury just found Google guilty on all counts of antitrust violations stemming from its dispute with Epic, maker of Fortnite, which brought a variety of claims related to how Google runs its app marketplace. This is huge:
https://www.nytimes.com/2023/12/11/technology/epic-games-google-antitrust-ruling.html
The mobile app store world is a duopoly run by Google and Apple. Both use a variety of tactics to prevent their customers from installing third party app stores, which funnels all app makers into their own app stores. Those app stores cream an eye-popping 30% off every purchase made in an app.
This is a shocking amount to charge for payment processing. The payments sector is incredibly monopolized and notorious for its price-gouging – and its standard (wildly inflated) rate is 2-5%:
https://pluralistic.net/2023/08/04/owning-the-libs/#swiper-no-swiping
Now, in theory, Epic doesn't have to sell in Google Play, the official Android app store. Unlike Apple's iOS, Android permit both sideloading (installing an app directly without using an app store) and configuring your device to use a different app store. In practice, Google uses a variety of anticompetitive tricks to prevent these app stores from springing up and to dissuade Android users from sideloading. Proving that Google's actions – like paying Activision $360m as part of "Project Hug" (no, really!) – were intended to prevent new app storesfrom springing up was a big lift for Epic. But they managed it, in large part thanks to Google's own internal communications, wherein executives admitted that this was exactly why Project Hug existed. This is part of a pattern with Big Tech antitrust: many of the charges are theoretically very hard to make stick, but because the companies put their evil plans in writing (think of the fraudulent crypto exchange FTX, whose top execs all conferred in a groupchat called "Wirefraud"), Big Tech keeps losing in court:
https://pluralistic.net/2023/09/03/big-tech-cant-stop-telling-on-itself/
Now, I do like to dunk on Big Tech for this kind of thing, because it's objectively funny and because the companies make so many unforced errors. But in an important sense, this kind of written record is impossible to avoid. Any large institution can only make and enact policy through administrative systems, and those systems leave behind a paper-trail: memos, meeting minutes, etc. Yes, we all know that quote from The Wire: "Is you taking notes on a fucking criminal conspiracy?" But inevitably, any ambitious conspiracy can only exist if someone is taking notes.
What's more, any large conspiracy involving lots of parties will inevitably produce leaks. Think of this as the corollary to the idea that the moon landing can't be a hoax, because there's no way 400,000 co-conspirators could keep the secret. Big Tech's conspiracies required hundreds or even thousands of collaborators to keep their mouths shut, and eventually someone blabs:
https://www.science.org/content/article/fake-moon-landing-you-d-need-400000-conspirators
This is part of a wave of antitrust cases being brought against the tech giants. As Matt Stoller writes, the guilty-on-all-counts jury verdict will leak into current and future actions. Remember, Google spent much of this year in court fighting the DoJ, who argued that the company bribed Apple not to make a competing search engine, paying tens of billions every year to keep a competitor from emerging. Now that a jury has convinced Google of doing that to prevent alternative app stores from emerging, claims that it used these pay-for-delay tactics in other sectros get a lot more credible:
https://www.thebignewsletter.com/p/boom-google-loses-antitrust-case
On that note: what about Apple? Epic brought a very similar case against Apple and lost. Both Apple and Epic are appealing that case to the Supreme Court, and now that Google has been convicted in a similar case, it might prompt the Supremes to weigh in and resolve the seeming inconsistencies in the interpretation of federal law.
This is a key moment in the long project to wrest antitrust away from the pro-monopoly side, who spent decades "training" judges to produce verdicts that run counter to the plain language of America's antitrust law:
https://pluralistic.net/2021/08/13/post-bork-era/#manne-down
There's 40 years' worth of bad precedent to overturn. The good news is that we've got the law on our side. Literally, the wording of the laws and the records of the Congressional debate leading to their passage, all militate towards the (incredibly obvious) conclusion that the purpose of anti-monopoly law is to fight monopoly, not defend it:
https://pluralistic.net/2023/04/14/aiming-at-dollars/#not-men
It's amazing to realize that we got into this monopoly quagmire because judges just literally refused to enforce the law. That's what makes one part of the jury verdict against Google so exciting: the jury found that Google's insistence that Play Store sellers use its payment processor was an act of illegal tying. Today, "tying" is an obscure legal theory, but few doctrines would be more useful in disenshittifying the internet. A company is guilty of illegal tying when it forces you to use unrelated products or services as a condition of using the product you actually want. The abandonment of tying led to a host of horribles, from printer companies forcing you to buy ink at $10,000/gallon to Livenation forcing venues to sell tickets through its Ticketmaster subsidiary.
The next phase of this comes when the judge decides on the penalty. Epic doesn't want cash damages – it wants the judge to order Google to fulfill its promise of "an open, competitive Android ecosystem for all users and industry participants." They've asked the judge to order Google to facilitate third-party app stores, and to separate app stores from payment processors. As Stoller puts it, they want to "crush Google’s control over Android":
https://www.epicgames.com/site/en-US/news/epic-v-google-trial-verdict-a-win-for-all-developers
Google has sworn to appeal, surprising no one. The Times's expert says that they will have a tough time winning, given how clear the verdict was. Whatever this means for Google and Android, it means a lot for a future free from monopolies.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/12/im-feeling-lucky/#hugger-mugger
#pluralistic#conspiracies#big tech#discovery#ai#copyright#copyfight#app stores#circuit splits#apple#apple v epic#law#trustbusting#competition#monopolies#google#epic#google v epic#fortnite#antitrust#tying#payment processing#scotus#project hug#pay for delay#games#gaming
1K notes
·
View notes
Text

#TimeFace aplikasi absensi wajah untuk karyawan melakukan absensi kehadiran menggunakan ponsel sebagai device. Tetap bisa melakukan absensi k#yang bisa diperintah dari App TimeFace Manager.#Realtime data absensi: Ya#Registrasi karyawan jarak jauh : YA#Support App Mobile: Ya#Android#Support software : Fingerspot Personnel
0 notes
Text
Mobile Device Management
TechOm Systems provide the best mobile device management system. Best mobile device management android. mobile device management apple. mobile device management intune. mobile device management office 365.
#mobile device management android#mobile device management apple#mobile device management intune#mobile device management office 365#mobile device management standard#mobile device management microsoft#byod mobile device management#mobile device management comparison chart
0 notes
Text
Setting up AO3 Enhancements on a mobile browser
Hey there! Do you:
read fic primarily on your phone?
feel tired of having to punch in a lot of filter tags every time you browse for fics?
have an android device?
then I might be able to help you make fandom a cozier place! (and hopefully nip future drama in the bud, lol)
With this post, I'm gonna guide you through the process of installing the AO3 Enhancements browser extension, normally only available on desktop, on your mobile device. It works a charm, and I've been using it for months, and it's made the Undertale tag navigable again despite my utter disinterest in AU content.
Here's an archived version of the full post in case my dumbass accidentally deletes it for some reason
Let's get started!
UPDATE: For IOS users! You can download the browser app "Orion" which allows firefox extensions! No need to do this procedure, just install it and download the extension as you normally would from Firefox Add-ons
1) Download Firefox Nightly.
For those who are hearing of it for the first time, Firefox Nightly is a separate Firefox browser made specifically for developers. The name itself is due to the fact that it's patched and updated on a daily (er, nightly) basis. This makes it more prone to crashing and issues than the standard Firefox app, but I've switched over to nightly as my main browser months ago now, and if I ever encounter a problem, I just... download the latest update and I'm good to go.
What's crucial about Nightly, however, is that it gives the user access to various additional features. One of them being desktop extensions on mobile, which is what we're here for.
Here's the Google Play link.
2) Make a Firefox Account
This will be necessary to install the extension later
Once you've done that, go to the Firefox add-ons website and log into your account in the upper right (where it says "Biscia" in the screenshot below). Click on "View My Collections"
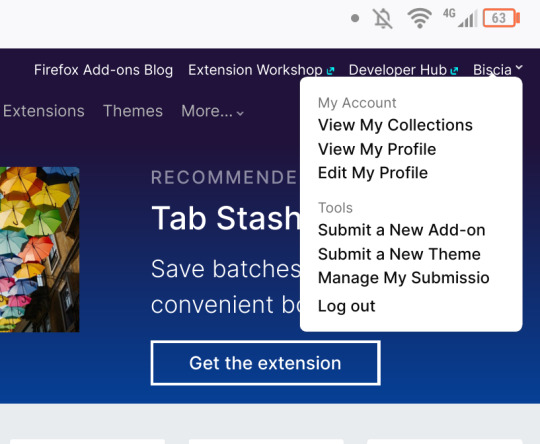
3) Making an add-on collection
Since browser extensions are technically blocked from being directly installed by the browser, Nightly offers a workaround.
Create a collection, and give it a name without spaces to avoid errors.
4) Adding the extension
Here is the link to ao3 enhancements (if it's not showing up, try reloading the page in desktop mode). Scroll down until you see the option "Add to a collection" and select the one you just created.
You can do it with any extension! Go nuts. There's lots of good stuff out there. Just remember that it's not guaranteed every one of them will work, since they aren't intended to be used on a mobile device.
5) Activating debug mode.
In your browser, tap the little sandwich menu in the bottom right, scroll down and click Settings. It should be under "Save to Collection".
Scroll down even more until you reach the "About" section, and click on "About Firefox Nightly"

Click on the firefox logo 5 times, and it should be done.
6) Activating your add-ons
Go to "View my profile" as seen in the screenshot in step 2. At the end of the link, there should be a string of numbers. Copy it.
After this, go back to the browser settings again, scroll down until you reach the add ons section and click on "custom add on collection". Paste the numbers you copied from your profile where it says "User ID", and the name of your collection EXACTLY as it appears in the link, where it says "Collection name". Mind, it's case sensitive.
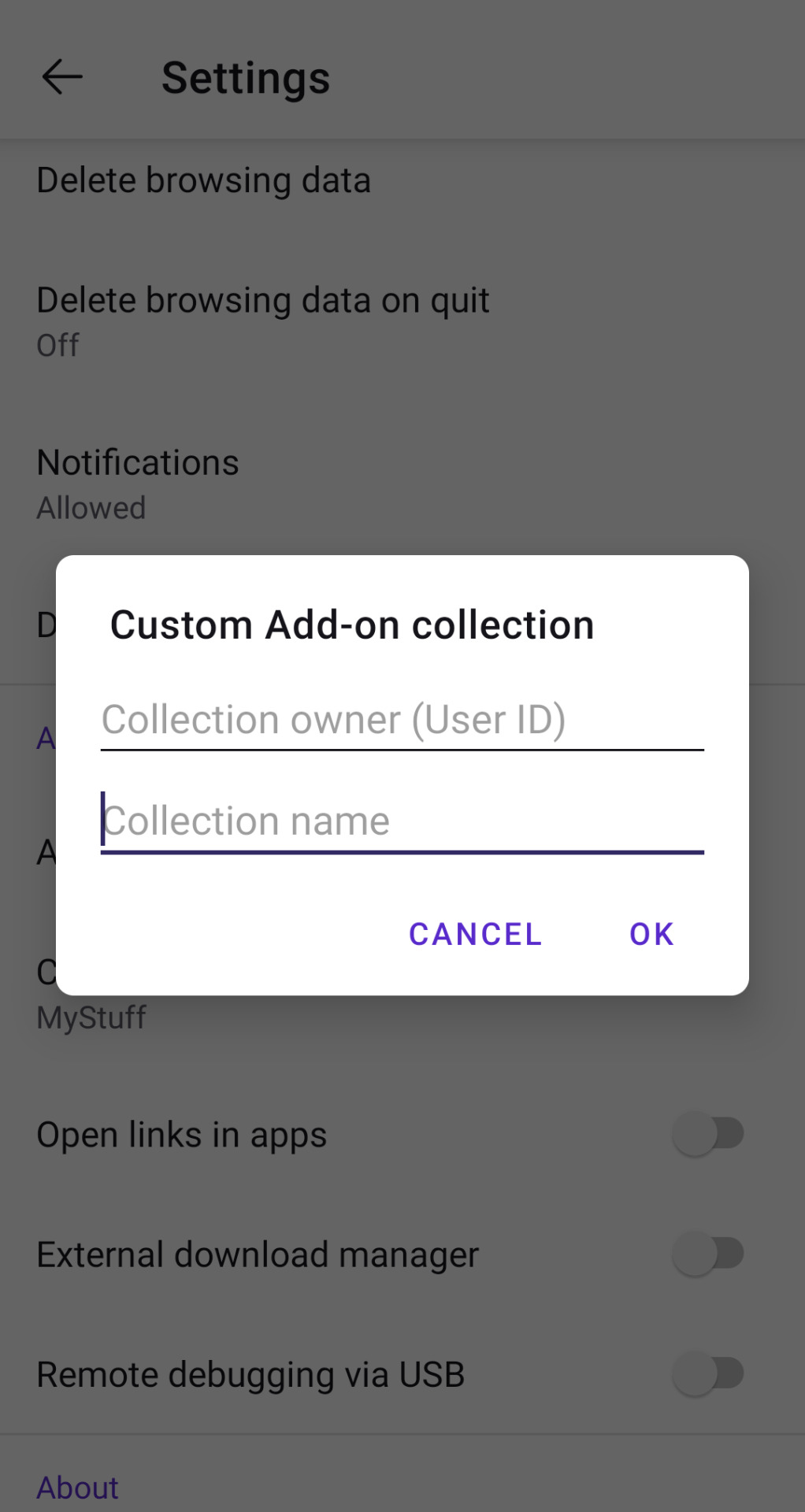
Press okay, and it should kick you out of the app. Open it again and, going in add-ons then add-ons manager, you should be able to add your extension.
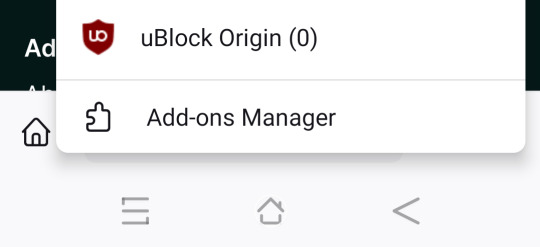
ATTENTION!! If you get the error message "failed to query add-ons" you either inputted the wrong user id or the wrong collection name
To avoid this type of issue, don't name your collection something that has spaces or punctuation in it, as it might mess with the link formatting.
7) Setting up your AO3 enhancements filters
If everything's worked out fine, you should be able to visit ao3 and see a new drop-down window.
Click on it, click on option, and it should open up a new window with all the settings available! Tweak them to your heart's content. Though mind, the background tag wrangling done by the ao3 volunteers doesn't work with this extension, so the extension is going to hide only the works tagged EXACTLY what you filtered. Character for character. This makes things a bit tricky when people aren't consistent with their tagging, but if it proves to be enough of a problem, you can just filter out the author name in full and be done with it.
You can choose to hide the fic behind a "show" button, or make it not show up at all. If you choose the latter option, and you blocked a tag that has lots of fics, it might look like certain pages of searches are almost empty, since all the fics were hidden.
And that's it! I sincerely hope this helps people avoid their triggers and other topics that make them uncomfortable. No more excuses fellas. You find a tag you haven't filtered yet? You add it to the list and move on. Easy peasy.
Hope I haven't missed anything. Let me know if you need any help!
2K notes
·
View notes
Text
How to Create an Impacting Device Security for Enterprise
Securing the devices within an enterprise is a critical aspect of overall cybersecurity. As technology continues to advance, so do the threats that target devices and the sensitive information they hold. Creating an impactful device security strategy for an enterprise involves a combination of technological measures, employee education, and proactive monitoring. Here are key steps to enhance device security within an enterprise:
Comprehensive Endpoint Protection:
Deploy robust endpoint protection solutions to safeguard devices from malware, ransomware, and other malicious software. This includes antivirus software, anti-malware tools, and advanced threat detection mechanisms. Regularly update and patch these tools to ensure they can effectively counter evolving threats. You can know more about this by comparing EMM MDM solutions.
Device Encryption:
Implement full disk encryption on all devices to protect sensitive data in case a device is lost or stolen. Encryption ensures that even if unauthorized individuals gain physical access to the device, they cannot access the stored data without the appropriate encryption keys.
Strong Authentication Mechanisms:
Enforce strong authentication practices such as multi-factor authentication (MFA). Require users to authenticate their identity through multiple methods (passwords, biometrics, smart cards) to add an extra layer of security, reducing the risk of unauthorized access.
Regular Security Audits and Vulnerability Assessments:
Conduct regular security audits and vulnerability assessments to identify weaknesses in the device security infrastructure. Address any vulnerabilities promptly to mitigate the risk of exploitation by cybercriminals. This proactive approach helps maintain a robust security posture.
Device Management and Inventory:
Maintain a centralized device management system to monitor and control devices within the enterprise. This includes keeping an up-to-date inventory of all devices, managing access controls, and remotely wiping or disabling lost or compromised devices.
Employee Training and Awareness:
Educate employees about security best practices and potential threats. Human error is a common cause of security breaches, so fostering a security-conscious culture is crucial. Training should cover topics such as phishing awareness, safe browsing habits, and the importance of regular software updates.
Network Segmentation:
Implement network segmentation to isolate devices and limit the potential lateral movement of attackers within the network. This strategy helps contain a breach to a specific segment, reducing the overall impact on the enterprise.
Incident Response Plan:
Develop and regularly update an incident response plan to ensure a swift and coordinated response in the event of a security incident. This plan should outline the steps to be taken, key personnel involved, and communication protocols to minimize downtime and data exposure.
Continuous Monitoring and Logging:
Implement continuous monitoring of devices and establish comprehensive logging practices. Analyzing logs can help detect suspicious activities, identify potential security incidents, and provide valuable information during post-incident investigations.
Regulatory Compliance:
Stay compliant with relevant data protection regulations and industry standards. Adhering to compliance requirements not only helps avoid legal consequences but also sets a foundation for a robust security framework. Enterprises can even lock down devices for dedicated purposes, so that the devices are not misused and assured it's intent is valid for work purposes.
Creating an impactful device security strategy for an enterprise involves a multi-faceted approach. By combining advanced technological measures with employee education and proactive monitoring, organizations can significantly reduce the risk of security breaches and protect sensitive information from various cyber threats. Regularly updating and adapting these measures is essential in the ever-evolving landscape of cybersecurity.
0 notes