#PARAMOUNT SOFTWARE
Text
Do the new Spocks really not get any eyeshadow?? His eyeshadow is the second most iconic thing about him and they just took it away??
#stares directly at paramount#i havent seen snw but in all the gifs ive seen of that spock he isnt wearing eyeshadow#maybe i should learn an editing software#spock#tos#snw#aos
12 notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Driving Efficiency: Fleet Management Software Solutions in Dubai
In the heart of the bustling metropolis of Dubai, where every minute counts and precision is paramount, efficient fleet management is crucial for businesses to stay ahead of the curve. From logistics companies navigating the city's intricate road network to construction firms overseeing a fleet of heavy machinery, the ability to monitor, track, and optimize fleet operations can make all the difference. This is where fleet management software solutions in Dubai come into play, offering innovative tools to streamline processes, enhance productivity, and drive business growth. Let's explore some of the top fleet management software solutions making waves in Dubai's dynamic business landscape.
1. Trinetra
Trinetra is a leading provider of fleet management software solutions, offering a comprehensive suite of tools to help businesses optimize their fleet operations. With features such as real-time tracking, route optimization, and driver behavior monitoring, Trinetra empowers businesses to improve efficiency, reduce costs, and enhance customer satisfaction. Whether it's managing a fleet of delivery vehicles or a construction fleet, Trinetra's customizable solutions cater to a wide range of industries and business needs.
2. Chekhra Business Solutions
Chekhra Business Solutions specializes in fleet management software tailored to the unique requirements of businesses in Dubai and the wider UAE. Their user-friendly platform offers advanced features such as GPS tracking, fuel management, and maintenance scheduling, allowing businesses to gain real-time insights into their fleet operations. With a focus on innovation and customer satisfaction, Chekhra Business Solutions is committed to helping businesses maximize their productivity and profitability.
3. Carmine
Carmine is a cloud-based fleet management software solution designed to meet the needs of businesses of all sizes in Dubai. With features such as vehicle tracking, driver management, and compliance monitoring, Carmine helps businesses streamline their operations and ensure regulatory compliance. Its intuitive interface and customizable reporting tools make it easy for businesses to track their fleet performance and make data-driven decisions to optimize efficiency and reduce costs.
4. Fleet Complete
Fleet Complete is a global leader in fleet management software solutions, with a strong presence in Dubai and the UAE. Their comprehensive platform offers a wide range of features, including GPS tracking, route optimization, and asset management, enabling businesses to maximize the efficiency of their fleet operations. With real-time visibility into vehicle location, status, and performance, Fleet Complete empowers businesses to improve productivity, reduce fuel consumption, and enhance customer service.
5. GPSit
GPSit is a trusted provider of fleet management software solutions, offering cutting-edge technology to businesses across Dubai and the UAE. Their platform provides real-time tracking, route optimization, and driver behavior monitoring, helping businesses optimize their fleet operations and improve overall efficiency. With a focus on reliability, scalability, and customer support, GPSit is committed to helping businesses achieve their fleet management goals and drive success in a competitive marketplace.
Conclusion
In the fast-paced business environment of Dubai, where efficiency and productivity are paramount, the adoption of fleet management software solutions is essential for businesses to stay competitive and thrive. Whether it's optimizing routes, improving fuel efficiency, or ensuring regulatory compliance, these software solutions offer a comprehensive suite of tools to help businesses streamline their operations and drive growth. By harnessing the power of technology and innovation, businesses in Dubai can unlock new opportunities for success and maintain their position as leaders in their respective industries.
#In the heart of the bustling metropolis of Dubai#where every minute counts and precision is paramount#efficient fleet management is crucial for businesses to stay ahead of the curve. From logistics companies navigating the city’s intricate r#the ability to monitor#track#and optimize fleet operations can make all the difference. This is where fleet management software solutions in Dubai come into play#offering innovative tools to streamline processes#enhance productivity#and drive business growth. Let’s explore some of the top fleet management software solutions making waves in Dubai’s dynamic business lands#1. Trinetra#Trinetra is a leading provider of fleet management software solutions#offering a comprehensive suite of tools to help businesses optimize their fleet operations. With features such as real-time tracking#route optimization#and driver behavior monitoring#Trinetra empowers businesses to improve efficiency#reduce costs#and enhance customer satisfaction. Whether it’s managing a fleet of delivery vehicles or a construction fleet#Trinetra’s customizable solutions cater to a wide range of industries and business needs.#2. Chekhra Business Solutions#Chekhra Business Solutions specializes in fleet management software tailored to the unique requirements of businesses in Dubai and the wide#fuel management#and maintenance scheduling#allowing businesses to gain real-time insights into their fleet operations. With a focus on innovation and customer satisfaction#Chekhra Business Solutions is committed to helping businesses maximize their productivity and profitability.#3. Carmine#Carmine is a cloud-based fleet management software solution designed to meet the needs of businesses of all sizes in Dubai. With features s#driver management#and compliance monitoring#Carmine helps businesses streamline their operations and ensure regulatory compliance. Its intuitive interface and customizable reporting t#4. Fleet Complete
0 notes
Text
How I ditched streaming services and learned to love Linux: A step-by-step guide to building your very own personal media streaming server (V2.0: REVISED AND EXPANDED EDITION)
This is a revised, corrected and expanded version of my tutorial on setting up a personal media server that previously appeared on my old blog (donjuan-auxenfers). I expect that that post is still making the rounds (hopefully with my addendum on modifying group share permissions in Ubuntu to circumvent 0x8007003B "Unexpected Network Error" messages in Windows when transferring files) but I have no way of checking. Anyway this new revised version of the tutorial corrects one or two small errors I discovered when rereading what I wrote, adds links to all products mentioned and is just more polished generally. I also expanded it a bit, pointing more adventurous users toward programs such as Sonarr/Radarr/Lidarr and Overseerr which can be used for automating user requests and media collection.
So then, what is this tutorial? This is a tutorial on building and setting up your own personal media server running Ubuntu and using Plex (or Jellyfin) to not only manage your media but to stream your media to your devices both locally at home, and remotely anywhere in the world where you have an internet connection. It’s a tutorial on how by building a personal media server and stuffing it full of films, television and music that you acquired through indiscriminate and voracious media piracy ripping your own physical media to disk, you’ll be free to completely ditch paid streaming services altogether. No more will you have to pay for Disney+, Netflix, HBOMAX, Hulu, Amazon Prime, Peacock, CBS All Access, Paramount+ Crave or any other streaming service that is not named Criterion Channel (which is actually good) to watch your favourite films and television shows, instead you’ll have your own custom service that will only feature things you want to see, and where you have control over your own files and how they’re delivered to you. And for music fans, Jellyfin and Plex both support music collection streaming so you can even ditch the music streaming services. Goodbye Spotify, Youtube Music, Tidal and Apple Music, welcome back unreasonably large MP3 collections (or FLAC collections).
On the hardware front, I’m going to offer a few options catered towards various budgets and media library sizes. The cost of getting a media server going using this guide will run you anywhere from $450 CDN/$325 USD at the entry level to $1500 CDN/$1100 USD at the high end. My own server cost closer to the higher figure, with much of that cost being hard drives. If that seems excessive maybe you’ve got a roommate, a friend, or a family member who would be willing to chip in a few bucks towards your little project if they get a share of the bounty. This is how my server was funded. It might also be worth thinking about the cost over time, how much you spend yearly on subscriptions vs. a one time cost of setting a server. Then there's just the joy of being able to shout a "fuck you" at all those show cancelling, movie hating, hedge fund vampire CEOs who run the studios by denying them your money. Drive a stake through David Zaslav's heart.
On the software side I will walk you through, step-by-step, in installing Ubuntu as your server's OS, configuring your storage in a RAIDz array with ZFS, sharing your zpool to Windows with Samba, running a remote connection into your server from your Windows PC, and getting started with Plex/Jellyfin Media Server. Every terminal command you will need to input will be provided, and I will even share with you a custom #bash script that will make the used vs. available drive space on your server display correctly in Windows.
If you have a different preferred flavour of Linux (Arch, Manjaro, Redhat, Fedora, Mint, OpenSUSE, CentOS, or Slackware etc. et. al.) and are aching to tell me off for being basic using Ubuntu, this tutorial is not for you. The sort of person with a preferred Linux distro is the sort of person who can do this sort of thing in their sleep. Also I don't care. This tutorial is intended for the average home computer user. This is also why we’re not using a more exotic home server solution like running everything through Docker Containers and managing it through a dashboard like Homarr or Heimdall. While such solutions are fantastic and can be very easy to maintain once you have it all set up, wrapping your brain around Docker is a whole thing in and of itself. If you do follow this tutorial and enjoyed putting everything together, then I would encourage you to maybe go back in a year’s time, do your research and and redo everything so it’s set up with Docker Containers.
This is also a tutorial aimed at Windows users. Although I was a daily user of OS X for many years (roughly 2008-2023) and I've dabbled quite a bit with different Linux distributions (primarily Ubuntu and Manjaro), my primary OS these days is Windows 11. Many things in this tutorial will still be applicable to Mac users but others (e.g. setting up shares) you will have to look up yourself. I doubt it would be difficult to do so.
Nothing in this tutorial will require feats of computing expertise from you. All you will need is a basic level of computer literacy (e.g. an understanding how directories work, being comfortable in settings menus) and a willingness to learn a thing or two. While this guide may look overwhelming at a glance, this is only because I want to be as thorough as possible so that you understand exactly what it is you're doing and you're not just blindly following steps. If you half-way know what you’re doing, you’ll be fine if you ever need to troubleshoot.
Honestly, once you have all the hardware ready it really shouldn't take you more than an afternoon to get everything up and running.
(This tutorial is just shy of seven thousand words long so the rest is under the cut.)
Step One: Choosing Your Hardware
Linux is a light weight operating system, there's almost no bloat and there are recent distributions out there right now that will run perfectly fine on a fourteen year old i3 with 4GB of RAM. Running Plex/Jellyfin media server isn’t very resource intensive either in 90% of use cases. We don’t an expensive or powerful system. So there are several options available to you: use an old computer you already have sitting around but aren't using, buy a used workstation from eBay, or what I believe to be the best option, order an N100 Mini-PC from AliExpress or Amazon.
Note: If you already have an old PC sitting around that you’ve decided to use, fantastic, move on to the next step.
When weighing your options, do keep a few things in mind: the number of people you expect to be streaming simultaneously at any one time, the resolution and bitrate of your media library (4k video takes a lot more processing power than 1080p) and most importantly, how many of those clients are going to be transcoding at any one time. Transcoding is what happens when the playback device does not natively support direct playback of the source file. This can be for a number of reasons, such as the playback device's native resolution, or because the source file was encoded in a video codec unsupported by the playback device.
Ideally we want any transcoding to be performed by hardware, which means we should be looking for an Intel processor with Quick Sync. Quick Sync is a dedicated core on the CPU die designed specifically for video encoding and decoding. This makes for highly efficient transcoding both in terms of processing overhead and power draw. Without these Quick Sync cores, transcoding must be brute forced through software which takes up much more of a CPU’s processing power and takes much more energy. But not all Quick Sync cores are created equal, and you need to keep this in mind if you've decided either to use an old computer or to shop on eBay for a used workstation.
Any Intel processor after second generation Core (Sandy Bridge circa 2011) has Quick Sync cores. It's not until 6th gen (Skylake), however, that those cores support H.265 HEVC. Intel’s 10th gen (Comet Lake) processors support 10bit HEVC and HDR tone mapping. And the recent 12th gen (Alder Lake) processors give you AV1 decoding. As an example, while an 8th gen (Kaby Lake) i5-8500 will be able to transcode a file encoded with H.265 through hardware, it will fall back to software transcoding when given a 10bit H.265 file. So if you’ve decided to use that old PC or to look on eBay for an old Dell Optiplex keep this in mind.
Note 1: The price of old workstations varies wildly and fluctuates frequently. If you get lucky and go looking shortly after a workplace has liquidated a large number of their workstations you can find deals for as low as $100 for a barebones system, but generally an i5-8500 workstation with 16gb RAM will cost you somewhere in the area of $260 CDN/$200 USD.
Note 2: The AMD equivalent to Quick Sync is called Video Core Next, and while it's fine, it's not as efficient and not as mature a technology, only becoming available with first generation Ryzen and it only got decent with their newest CPUs, we want something cheap.
Alternatively you could completely forgo having to keep track of what generation of CPU is equipped with Quick Sync cores with support for which codecs, and just buy an N100 mini-PC. For around the same price or less than a good used workstation you can pick up a Mini-PC running an Intel N100 processor. The N100 is a four-core processor based on the 12th gen Alder Lake architecture and comes equipped with the latest revision of the Quick Sync. They offer astounding hardware transcoding capabilities for their size and power draw and otherwise perform equivalent to an i5-6500. A friend of mine uses an N100 machine as a dedicated retro emulation gaming system. These are also remarkably efficient chips, they sip power. In fact, the difference between running one of these and an old workstation could work out to hundreds of dollars a year in energy bills depending on where you live.
You can find these Mini-PCs all over Amazon or for a little cheaper over on AliExpress. They range in price from $170 CDN/$125 USD for a no name N100 with 8GB RAM to $280 CDN/$200 USD for a Beelink S12 Pro with 16GB RAM. The brand doesn't really matter, they're all coming from the same three factories in Shenzen, go for whichever one fits your budget or has the features you want. 8GB RAM should be enough, Linux is lightweight and Plex only calls for 2GB RAM, and a 256GB SSD is more than enough for what we need as a boot drive. 16GB RAM might result in a slightly snappier experience, especially with ZFS, and going for a bigger drive might allow you to get away with things like creating preview thumbnails for Plex, but it’s up to you and your budget.
The Mini-PC I wound up buying was a Firebat AK2 Plus with 8GB RAM and a 256GB SSD. It looks like this:

Note: Be forewarned that if you decide to order a Mini-PC from AliExpress, note the power adapter it is shipping with. The one I bought came with an EU power adapter and I had to supply my own North American power supply. Thankfully this is a minor issue as a barrel plug 30W/12V/2.5A power adapters are plentiful and can be had for $10.
Step Two: Choosing Your Storage
Storage is the most important part of our build, and the most expensive. Thankfully it’s also easily upgrade-able down the line.
For people with a smaller media collection (4TB to 8TB), a limited budget, or who will only ever have two simultaneous streams running, I would say that the most economical course of action would be to simply buy a USB 3.0 8TB external HDD. Something like this Western Digital or this Seagate external drive. One of these will cost you somewhere around $200 CDN/$140 USD. Down the line you could add a second external drive or replace it with a multi-drive RAIDz set up as detailed below.
If a single external drive the path for you, move on to step three.
For people who have larger media libraries (12TB+), who have a lot of media in 4k, or care about data redundancy, the answer is a RAID array featuring multiple HDDs in an enclosure.
Note: If you are using an old PC you already have as your server and have the room for at least three 3.5" drives, and as many open SATA ports on your mother board you won't need an enclosure, just install the drives in your old case. If your old computer is a laptop or doesn’t have room for more internal drives, then I would suggest an enclosure.
The minimum number of drives needed to run a RAIDz array is three, and seeing as RAIDz is what we will be using, you should be looking for an enclosure with hree to five bays. I think that four disks makes for a good compromise for a home server. Regardless of whether you go for a three, four, or five bay enclosure, do be aware that in a RAIDz array the space equivalent of one of the drives will be dedicated to parity at a ratio expressed by the equation 1 − 1/n i.e. in a four bay enclosure equipped with four 12TB drives configured in RAIDz we would be left with a total of 36TB of usable space (48TB raw size). The reason for why we might sacrifice storage space in such a manner will be explained in the next section.
A four bay enclosure will cost somewhere in the area of $200 CDN/$140 USD. You don't need anything fancy, nothing with hardware RAID (RAIDz is done entirely in software) or even USB-C. An enclosure with USB 3.0 will perform just fine. Don’t worry about bottlenecks, a mechanical HDD will be limited by the speed of its mechanism long before before it will be limited by the speed of a USB connection. I've seen decent looking enclosures from TerraMaster, Yottamaster, Mediasonic and Sabrent.
When it comes to selecting the drives, as of this writing, the best value (dollar per gigabyte) are those in the range of 12TB to 20TB. I settled on 12TB drives myself. If 12TB to 20TB drives are out of your budget, go with what you can afford, or look into refurbished drives. I'm not sold on the idea of refurbished drives but some people swear by them.
When shopping for harddrives, look for drives that are specifically designed for NAS use. Drives designed for NAS use typically have better vibration dampening and are designed to be active 24/7, they will also often use CMR (conventional magnetic recording) rather than SMR (shingled magnetic recording) which nets them a sizable performance bump. Seagate Ironwolf and Toshiba NAS drives are both well regarded. I would avoid Western Digital Red drives at this time. WD Reds were a go to recommendation up until earlier this year when it was revealed that they feature firmware that will throw up false SMART warnings telling you to replace the drive at the three year mark when there might be nothing at all wrong with that drive, and when it will likely be good for another six, seven or more years.

Step Three: Installing Linux
For this step you will need a USB thumbdrive of at least 6GB in capacity, a way to make it into bootable media, and an .ISO of Ubuntu.
First download a copy of Ubuntu desktop (for best performance we could download the Server release, but for new Linux users I would recommend against using the server release as having a GUI can be very helpful, not many people are wholly comfortable doing everything through command line). 22.04.3 Jammy Jellyfish is the current Long Term Service release, this is the one to get.
Download the .ISO and then download and install balenaEtcher on your Windows PC, balenaEtcher is an easy to use program for creating bootable media, you simply insert your thumbdrive, select the .ISO you just downloaded, and it will create a bootable installation media for you.
Once you've made a bootable media and you've got your Mini-PC (or old PC/used workstation) in front of you, hook it in directly to your router with an ethernet cable, and plug in the HDD enclosure, a monitor, mouse and a keyboard. Now turn that sucker on and hit whatever key it is that gets you into the BIOS (typically ESC, DEL or F2). If you’re using a Mini-PC check to make sure that the P1 and P2 power limits are set correctly and not arbitrarily lowered, my N100's P1 limit was set at 10W, a full 20W under the chip's power limit. Also make sure that the RAM is running at the advertised speed. My Mini-PC’s RAM was set at 2333Mhz out of the box when it should have been 3200Mhz. Once you’ve done that, key over to the boot order and place the USB drive first in the boot order. Then save the BIOS settings and restart.
After you restart you’ll be greeted by Ubuntu's installation screen. Installing Ubuntu is really straight forward, select the "minimal" installation option, as we won't need anything on this computer except for a browser (Ubuntu comes preinstalled with Firefox) and Plex Media Server/Jellyfin Media Server. Also remember to delete and reformat that Windows partition! We don't need it.
Step Four: Installing ZFS and Setting Up the RAIDz Array
Note: If you opted for just a single external HDD skip this step and move onto setting up a Samba share.
Once Ubuntu is installed it's time to configure our storage by installing ZFS to build our RAIDz array. ZFS is a "next-gen" file system that is both massively flexible and massively complex. It's capable of snapshot backup, self healing error correction, ZFS pools can be configured with drives operating in a supplemental manner alongside the storage vdev (e.g. fast cache, dedicated secondary intent log, hot swap spares etc.). It's also a file system very amenable to fine tuning. Block and sector size are adjustable to use case and you're afforded the option of different methods of inline compression. If you'd like a very detailed overview and explanation of its various features and tips on tuning a ZFS array check out these articles from Ars Technica. For now we're going to ignore all these features and keep it simple, we're going to pull our drives together into a single vdev running in RAIDz which will be the entirety of our zpool, no fancy cache drive or SLOG.
Open up the terminal and type the following commands:
sudo apt update
then
sudo apt install zfsutils-linux
This will install the ZFS utility. Verify that it's installed with the following command:
zfs --version
Next, it's time to check that the HDDs we have in the enclosure are healthy, running and recognized. We also want to find out their device IDs and take note of them:
sudo fdisk -1
Note: You might be wondering why some of these commands require "sudo" in front of them while others don't. "Sudo" is short for "super user do”. When and where "sudo" is used has to do with the way permissions are set up in Linux. Only the "root" user has the access level to perform certain tasks in Linux. As a matter of security and safety regular user accounts are kept separate from the "root" user. It's not advised (or even possible) to boot into Linux as "root" with most modern distributions. Instead by using "sudo" our regular user account is temporarily given the power to do otherwise forbidden things. Don't worry about it too much at this stage, but if you want to know more check out this introduction.
If everything is working you should get a list of the various drives detected along with their device IDs which will look something like this: /dev/sdc. You can also check the device IDs of the drives by opening the disk utility app. Jot these IDs down we'll need them for our next step, creating our RAIDz array.
RAIDz is similar to RAID-5 in that instead of striping your data over multiple disks, exchanging redundancy for speed and available space (RAID-0), or mirroring your data writing two copies of every piece (RAID-1), it instead writes parity blocks across the disks in addition to striping, this provides a balance of speed, redundancy and available space. If a single drive fails, the parity blocks on the working drives can be used to reconstruct the entire array as soon as a replacement drive is added.
Additionally, RAIDz improves over some of the common RAID-5 flaws. It's more resilient and capable of self healing, checking for errors against a checksum. It's more forgiving this way, and it's likely that you'll be able to detect when a drive is on its way out well before it fails. A RAIDz array can survive the loss of any one drive.
Note: While RAIDz is indeed resilient, if a second drive fails during the rebuild, you're fucked. Always keep backups of things you can't afford to lose. This tutorial, however, is not about proper data safety.
To create the pool, use the following command:
sudo zpool create "zpoolnamehere" raidz "device IDs of drives we're putting in the pool"
For example, let's creatively name our zpool "mypool". It will consist of four drives which have the device IDs: sdb, sdc, sdd, and sde. The resulting command would look like this:
sudo zpool create mypool raidz /dev/sdb /dev/sdc /dev/sdd /dev/sde
If for example you bought five HDDs and wanted more redundancy, and are okay with three disks worth of capacity, we would modify the command to "raidz2" and the command would look something like the following:
sudo zpool create mypool raidz2 /dev/sdb /dev/sdc /dev/sdd /dev/sde /dev/sdf
An array configured like this would be able to survive two disk failures and is known as RAIDz2.
Once the zpool has been created, we can check its status with the command:
zpool status
Or more concisely with:
zpool list
The nice thing about ZFS as a file system is that an array is ready to go immediately after creating the pool. If we were to set up a traditional RAID-5 array using mbam, we'd have to sit through a potentially hours long process of reformatting and partitioning the drives. Instead we're ready to go out the gates.
The zpool should be automatically mounted to the filesystem after creation, check on that with the following:
df -hT | grep zfs
Note: If your computer ever loses power suddenly, say in event of a power outage, you may have to re-import your pool. In most cases, ZFS will automatically import and mount your pool, but if it doesn’t and you can't see your array, simply open the terminal and type sudo zpool import -a.
By default a zpool is mounted at /"zpoolname". The pool should be under our ownership but let's make sure with the following command:
sudo chown -R "yourlinuxusername" /"zpoolname"
Note: Changing file and folder ownership with "chown" and file and folder permissions with "chmod" are essential commands for much of the admin work in Linux, but which we won't be dealing with extensively in this guide. If you'd like a deeper tutorial and explanation you can check out these two guides: chown and chmod.
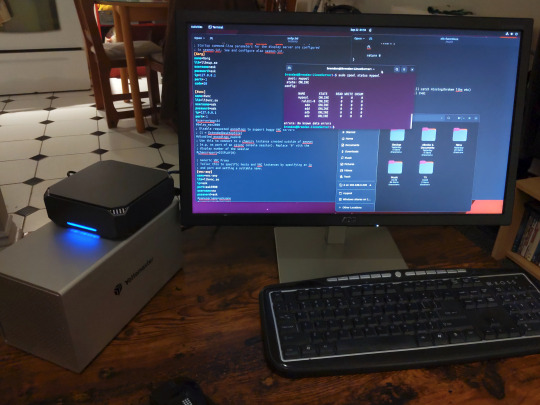
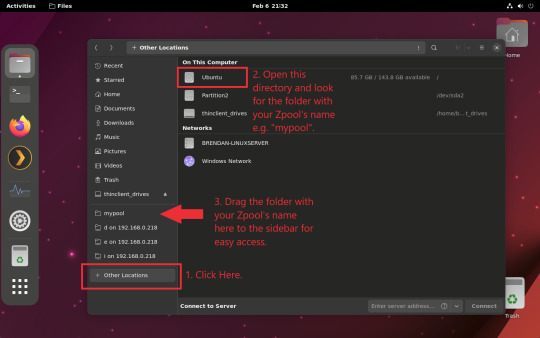
You can access the zpool file system through the GUI by opening the file manager (the Ubuntu default file manager is called Nautilus) and clicking on "Other Locations" on the sidebar, then entering the Ubuntu file system and looking for a folder with your pool's name. Bookmark the folder on the sidebar for easy access.
Your storage pool is now ready to go. Assuming that we already have some files on our Windows PC we want to copy to over, we're going to need to install and configure Samba to make the pool accessible in Windows.
Step Five: Setting Up Samba/Sharing
Samba is what's going to let us share the zpool with Windows and allow us to write to it from our Windows machine. First let's install Samba with the following commands:
sudo apt-get update
then
sudo apt-get install samba
Next create a password for Samba.
sudo smbpswd -a "yourlinuxusername"
It will then prompt you to create a password. Just reuse your username password for simplicity's sake.
Note: if you're using just a single external drive replace the zpool location in the following commands with wherever it is your external drive is mounted, for more information see this guide on mounting an external drive in Ubuntu.
After you've created a password we're going to create a shareable folder in our pool with this command
mkdir /"zpoolname"/"foldername"
Now we're going to open the smb.conf file and make that folder shareable Enter the following command.
sudo nano /etc/samba/smb.conf
This will open the .conf file in nano, the terminal text editor program. Now at the end of smb.conf add the following entry:
["foldername"]
path = /"zpoolname"/"foldername"
available = yes
valid users = "yourlinuxusername"
read only = no
writable = yes
browseable = yes
guest ok = no
Ensure that there are no line breaks between the lines and that there's a space on both sides of the equals sign. Next step is to allow Samba traffic through the firewall:
sudo ufw allow samba
Finally restart the Samba service:
sudo systemctl restart smbd
At this point we'll be able to access to the pool, browse its contents, and read/write to it from Windows. But there's one more thing left to do, Windows doesn't natively support the ZFS file systems and will read the used/available/total space in the pool incorrectly. Windows will read available space as total drive space, and all used space as null. This leads to Windows only displaying a dwindling amount of "available" space as the drives are filled. We can fix this! Functionally this doesn't actually matter, we can still write and read to and from the disk, it just makes it difficult to tell at a glance the proportion of used/available space, so this is an optional step but one I recommend (this step is also unnecessary if you're just using a single external drive). What we're going to do is write a little shell script in #bash. Open nano with the terminal with the command:
nano
Now insert the following code:
#!/bin/bash
CUR_PATH=`pwd`
ZFS_CHECK_OUTPUT=$(zfs get type $CUR_PATH 2>&1 > /dev/null) > /dev/null
if [[ $ZFS_CHECK_OUTPUT == *not\ a\ ZFS* ]]
then
IS_ZFS=false
else
IS_ZFS=true
fi
if [[ $IS_ZFS = false ]]
then
df $CUR_PATH | tail -1 | awk '{print $2" "$4}'
else USED=$((`zfs get -o value -Hp used $CUR_PATH` / 1024)) > /dev/null AVAIL=$((`zfs get -o value -Hp available $CUR_PATH` / 1024)) >
/dev/null
TOTAL=$(($USED+$AVAIL)) > /dev/null
echo $TOTAL $AVAIL
fi
Save the script as "dfree.sh" to /home/"yourlinuxusername" then change the ownership of the file to make it executable with this command:
sudo chmod 774 dfree.sh
Now open smb.conf with sudo again:
sudo nano /etc/samba/smb.conf
Now add this entry to the top of the configuration file to direct Samba to use the results of our script when Windows asks for a reading on the pool's used/available/total drive space:
[global]
dfree command = home/"yourlinuxusername"/defree.sh
Save the changes to smb.conf and then restart Samba again with the terminal:
sudo systemctl restart smbd
Now there’s one more thing we need to do to fully set up the Samba share, and that’s to modify a hidden group permission. In the terminal window type the following command:
usermod -a -G sambashare “yourlinuxusername”
Then restart samba again:
sudo systemctl restart smbd
If we don’t do this last step, while everything would appear to work fine, and you will be able to see and map the drive from Windows and even begin transferring files, you'd soon run into a lot of frustration. As every ten minutes or so a file would fail to transfer and you would get a window announcing “0x8007003B Unexpected Network Error”. This window would require your manual input to continue the transfer with the file that was next in the queue. It will reattempt to transfer whichever files failed the first time around at the end, and 99% of the time they’ll go through, but this is a major pain in the ass if you’ve got a lot of data you need to transfer and want to step away from the computer for a while. It turns out samba can act a little weirdly with the higher read/write speeds of RAIDz arrays and transfers from Windows, and will intermittently crash and restart itself if this group option isn’t changed. Inputting the above command will prevent you from ever seeing that window.
The last thing we're going to do in this part before switching over to our Windows PC is grab the IP address of our Linux machine. Enter the following command:
hostname -I
This will spit out this computer's IP address on the local network (it will look something like 192.168.0.x), write it down. It might be a good idea once you're done here to go into your router settings and reserving that IP for your Linux system in the DHCP settings. Check the manual for your specific model router on how to access its settings, typically it can be accessed by opening a browser and typing http:\\192.168.0.1 in the address bar, but your router may be different.
Okay we’re done with our Linux computer for now. Get on over to your Windows PC, open File Explorer, right click on Network and click "Map network drive". Select Z: as the drive letter (you don't want to map the network drive to a letter you could conceivably be using for other purposes) and enter the IP of your Linux machine and location of the share like so: \\"LINUXCOMPUTERLOCALIPADDRESSGOESHERE"\"zpoolnamegoeshere"\. Windows will then ask you for your username and password, enter the ones you set earlier in Samba and you're good. If you've done everything right it should look something like this:

You can now start moving media over from Windows to the share folder. It's a good idea to have a hard line running to all machines. Moving files over Wi-Fi is going to be tortuously slow, the only thing that’s going to make the transfer time tolerable (hours instead of days) is a solid wired connection between both machines and your router.
Step Six: Setting Up Remote Desktop Access to Your Server
After the server is up and going, you’ll want to be able to access it remotely from Windows. Barring serious maintenance/updates, this is how you'll access it most of the time. On your Linux system open the terminal and enter:
sudo apt install xrdp
Then:
sudo systemctl enable xrdp
Once it's finished installing, open “Settings” on the sidebar and turn off "automatic login" in the User category. Then log out of your account. Attempting to remotely connect to your Linux computer while you’re logged in will just result in a black screen!
Now get back on your Windows PC, open search and search for "RDP". A program called "Remote Desktop Connection" should pop up, open this program as an administrator by right-clicking and selecting “run as an administrator”. You’ll be greeted with a window, in the field marked “Computer” type in the IP address of your Linux computer. Press connect and you'll be greeted with a new window and a prompt asking for your username and password. Enter your Ubuntu username and password here.
If everything went right, you’ll be logged into your Linux computer. If the performance is too sluggish, adjust the display options, lowering the resolution and colour depth do a lot to make the interface feel snappier.
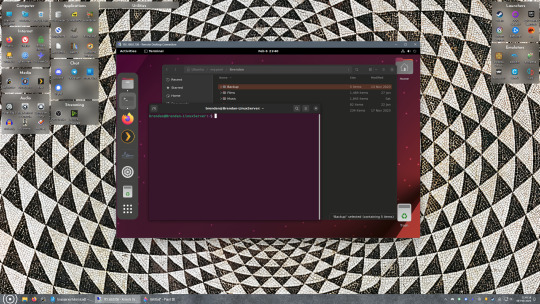
Remote access is how we're going to be using our Linux system from now, outside of some edge cases like needing to get into the BIOS or upgrading to a new version of Ubuntu. Everything else from performing maintenance like a monthly zpool scrub (this is important!!!) to checking zpool status and updating software can all be done remotely.

This is how my server lives its life now, happily humming and chirping away on the floor next to the couch in the corner of the living room.
Step Seven: Plex Media Server/Jellyfin
Okay we’ve got all the ground work finished and our server is almost up and running: we’ve got Ubuntu up and running, the storage is primed, we’ve set up remote connections and sharing, and maybe we’ve moved over some of favourite movies and TV shows.
Now we need to decide on the media server software to use which will stream our media to us and organize our library. For most people I’d recommend Plex, it just simply works 99% of the time. That said, Jellyfin has a lot to recommend it by too even if it is rougher around the edges, some people even run both simultaneously, it’s not that big an extra strain. I do recommend doing a little bit of your own research into the features each platform offers. But as a quick run down, consider some of the following points.
Plex is closed source and is funded through PlexPass purchases while Jellyfin is open source and entirely user driven. This means a number of things, for one, Plex requires you to purchase a “PlexPass” (purchased as a one time lifetime fee $159.99 CDN/$120 USD or paid for on a monthly yearly subscription basis) for access to certain features, like hardware transcoding (and we want hardware transcoding) and automated intro/credits detection and skipping, while Jellyfin offers this for free. On the other hand, Plex supports a lot more devices than Jellyfin and updates more frequently. That said Jellyfin's Android/iOS apps are completely free, while the Plex Android/iOS apps must be activated for a one time cost of $6 CDN/$5 USD. Additionally the Plex Android/iOS apps are vastly unified in UI and functionality across platforms, offering a much more polished experience, while the Jellyfin apps are a bit of a mess and very different from each other. Jellyfin’s actual media player itself is more fully featured than Plex's, but on the other hand Jellyfin's UI, library customization and automatic media tagging really pale in comparison to Plex. Streaming your music library is free through both Jellyfin and Plex, but Plex offers the PlexAmp app for dedicated music streaming which boasts a number of fantastic features, unfortunately some of those fantastic features require a PlexPass. If your internet is down, Jellyfin can still do local streaming, while Plex can fail to play files. Jellyfin has a slew of neat niche features like support for Comic Book libraries with the .cbz/.cbt file types, but then Plex offers some free ad-supported TV and films, they even have a free channel that plays nothing but Classic Doctor Who.
Ultimately it's up to you, I settled on Plex because although some features are pay-walled, it just works. It's more reliable and easier to use, and a one-time fee is much easier to swallow than a subscription. I do also need to mention that Jellyfin does take a little extra bit of tinkering to get going in Ubuntu, you’ll have to set up process permissions, so if you're more tolerant to tinkering, Jellyfin might be up your alley and I’ll trust that you can follow their installation and configuration guide. For everyone else, I recommend Plex.
So pick your poison: Plex or Jellyfin.
Note: The easiest way to download and install either of these packages in Ubuntu is through Snap Store.
After you've installed one (or both), opening either app will launch a browser window into the browser version of the app allowing you to set all the options server side.
The process of adding creating media libraries is essentially the same in both Plex and Jellyfin. You create a separate libraries for Television, Movies, and Music and add the folders which contain the respective types of media to their respective libraries. The only difficult or time consuming aspect is ensuring that your files and folders follow the appropriate naming conventions:
Plex naming guide for Movies
Plex naming guide for Television
Jellyfin follows the same naming rules but I find their media scanner to be a lot less accurate and forgiving than Plex. Once you've selected the folders to be scanned the service will scan your files, tagging everything and adding metadata. Although I find do find Plex more accurate, it can still erroneously tag some things and you might have to manually clean up some tags in a large library. (When I initially created my library it tagged the 1963-1989 Doctor Who as some Korean soap opera and I needed to manually select the correct match after which everything was tagged normally.) It can also be a bit testy with anime (especially OVAs) be sure to check TVDB to ensure that you have your files and folders structured and named correctly. If something is not showing up at all, double check the name.
Once that's done, organizing and customizing your library is easy. You can set up collections, grouping items together to fit a theme or collect together all the entries in a franchise. You can make playlists, and add custom artwork to entries. It's fun setting up collections with posters to match, there are even several websites dedicated to help you do this like PosterDB. As an example, below are two collections in my library, one collecting all the entries in a franchise, the other follows a theme.

My Star Trek collection, featuring all eleven television series, and thirteen films.
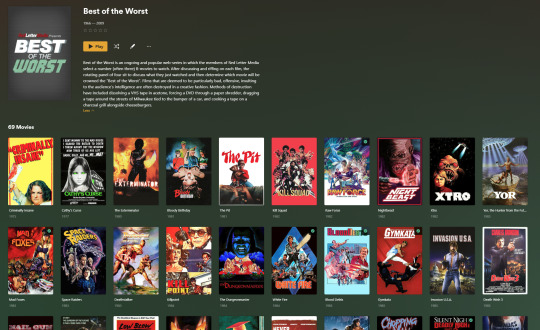
My Best of the Worst collection, featuring sixty-nine films previously showcased on RedLetterMedia’s Best of the Worst. They’re all absolutely terrible and I love them.
As for settings, ensure you've got Remote Access going, it should work automatically and be sure to set your upload speed after running a speed test. In the library settings set the database cache to 2000MB to ensure a snappier and more responsive browsing experience, and then check that playback quality is set to original/maximum. If you’re severely bandwidth limited on your upload and have remote users, you might want to limit the remote stream bitrate to something more reasonable, just as a note of comparison Netflix’s 1080p bitrate is approximately 5Mbps, although almost anyone watching through a chromium based browser is streaming at 720p and 3mbps. Other than that you should be good to go. For actually playing your files, there's a Plex app for just about every platform imaginable. I mostly watch television and films on my laptop using the Windows Plex app, but I also use the Android app which can broadcast to the chromecast connected to the TV. Both are fully functional and easy to navigate, and I can also attest to the OS X version being equally functional.
Part Eight: Finding Media
Now, this is not really a piracy tutorial, there are plenty of those out there. But if you’re unaware, BitTorrent is free and pretty easy to use, just pick a client (qBittorrent is the best) and go find some public trackers to peruse. Just know now that all the best trackers are private and invite only, and that they can be exceptionally difficult to get into. I’m already on a few, and even then, some of the best ones are wholly out of my reach.
If you decide to take the left hand path and turn to Usenet you’ll have to pay. First you’ll need to sign up with a provider like Newshosting or EasyNews for access to Usenet itself, and then to actually find anything you’re going to need to sign up with an indexer like NZBGeek or NZBFinder. There are dozens of indexers, and many people cross post between them, but for more obscure media it’s worth checking multiple. You’ll also need a binary downloader like SABnzbd. That caveat aside, Usenet is faster, bigger, older, less traceable than BitTorrent, and altogether slicker. I honestly prefer it, and I'm kicking myself for taking this long to start using it because I was scared off by the price. I’ve found so many things on Usenet that I had sought in vain elsewhere for years, like a 2010 Italian film about a massacre perpetrated by the SS that played the festival circuit but never received a home media release; some absolute hero uploaded a rip of a festival screener DVD to Usenet, that sort of thing. Anyway, figure out the rest of this shit on your own and remember to use protection, get yourself behind a VPN, use a SOCKS5 proxy with your BitTorrent client, etc.
On the legal side of things, if you’re around my age, you (or your family) probably have a big pile of DVDs and Blu-Rays sitting around unwatched and half forgotten. Why not do a bit of amateur media preservation, rip them and upload them to your server for easier access? (Your tools for this are going to be Handbrake to do the ripping and AnyDVD to break any encryption.) I went to the trouble of ripping all my SCTV DVDs (five box sets worth) because none of it is on streaming nor could it be found on any pirate source I tried. I’m glad I did, forty years on it’s still one of the funniest shows to ever be on TV.
Part Nine/Epilogue: Sonarr/Radarr/Lidarr and Overseerr
There are a lot of ways to automate your server for better functionality or to add features you and other users might find useful. Sonarr, Radarr, and Lidarr are a part of a suite of “Servarr” services (there’s also Readarr for books and Whisparr for adult content) that allow you to automate the collection of new episodes of TV shows (Sonarr), new movie releases (Radarr) and music releases (Lidarr). They hook in to your BitTorrent client or Usenet binary newsgroup downloader and crawl your preferred Torrent trackers and Usenet indexers, alerting you to new releases and automatically grabbing them. You can also use these services to manually search for new media, and even replace/upgrade your existing media with better quality uploads. They’re really a little tricky to set up on a bare metal Ubuntu install (ideally you should be running them in Docker Containers), and I won’t be providing a step by step on installing and running them, I’m simply making you aware of their existence.
The other bit of kit I want to make you aware of is Overseerr which is a program that scans your Plex media library and will serve recommendations based on what you like. It also allows you and your users to request specific media. It can even be integrated with Sonarr/Radarr/Lidarr so that fulfilling those requests is fully automated.
And you're done. It really wasn't all that hard. Enjoy your media. Enjoy the control you have over that media. And be safe in the knowledge that no hedgefund CEO motherfucker who hates the movies but who is somehow in control of a major studio will be able to disappear anything in your library as a tax write-off.
661 notes
·
View notes
Text
It's funny how most every cyberpunk story or setting thought that due to technology taking over people's lives and humanity, computer literacy would become commonplace enough that the very term would disappear. Everyone in Night City or whatever is super into hacking or can at least give you the difference between hardware, software, antivirus, spam, etc. To not know the basic gists or cybernetics and cyber security is paramount to not knowing how to count or how to read.
In reality we're about to enter an age where knowing how to create a folder or a zip file is back to being ancient lore inscribed in tablets that only the 30 year old who works at your IT office knows how to do. Phones and the growing marketability of easy-access no-customization technology means kids just don't use computers anymore. And it's crazy how fast it happened.
When I was in kindergarten we still had "computer class" once a week, and it was objectively useless for everyone in my class. Regardless of our age or interests, all of us had casual PC time either at home or in cyber cafes, all of us knew how to do things the teachers many times struggled with. The moment typing machine class became keyboard typing class, computers were already dominating most of our time. I learned how to navigate a computer the same way I learned English; by myself, because it was vital for my own interests.
And between highly streamlined video games, single umbrella closed OSs and everything being a fucking app, a 14 year old nowadays is lucky if they know what quotation marks do to your Google results. It's genuinely harrowing how the future is tech-dependent, yet we're becoming completely tech-illiterate.
The worst part is that it's completely on purpose by the tech industry. Much like not being able to fix your own products when they break, if you simply don't know what your phone or your computer can *do*, it's much easier to sell you a borderline identical one a little earlier than you'd actually need it. Phone updates are already pretty much semantic; you can't even see the difference between new models and old ones anymore, unless the visual difference is the point. And it all just gets more and more expensive for less and less bang for your buck.
We never expected the cyberpunk dystopia to be dull, and to rely on making us dumb. Crazy how well it worked.
#technology#tech#computer science#cybersecurity#these dang kids with their foortnoites and their moinecrafts#back in my day we learned to count with age of mythology#bit doom and gloom but seriously the amount of kids who dont know how to operate their own phones any more than boomers do is staggering#its all by design too of course
102 notes
·
View notes
Text
The Last Last Late Late Show With James Corden

HOW TO WATCH
North American fans can watch LLS on CBS at 12:37 AM EST, or through the Paramount Plus app. (You need to be a subscriber and they do a free trial!)
If you’re outside the US, a VPN is required to get the Paramount Plus content
If you don’t want to subscribe to paramount plus, you can always try these not ill*gal sites - one - two - three - they all can have a LOT of pop ups so make sure to have a good ad blocker/virus software installed (just in case)
There IS a Late Late Karaoke special at 10 PM EST tonight, but we’re not sure if he’ll be a part of it: best to check it out for yourselves!
Time Zone converter for those who need it! (just change the city!)
151 notes
·
View notes
Text
Pluto Square = internet observations
The World Wide Web was created on 6 August 1991, in Geneva, Switzerland.
According to the astro-databank, Tim Berners-Lee formally introduced his project to the world on the alt.hypertext newsgroup. This date marked the debut of the Web as a publicly available service. I am going with this date as this is the main … thing for … the world wide web lol.

The internet, as we know it, is a largely Aquarian thing, with the dot-com bubble following as Pluto entered Sagittarius. But since we’re talking about Pluto, we’re going to look at the Internet. I think this is the most important example of what happens during a Pluto square. NOW, we have quite some time before Pluto perfects that square. Something that I am noticing about Plutonian energy is that yes, it is intense in nature. Naturally, you will start to feel the more intense things first, right? It’s how we’re beginning to see the effects of Pluto in Aquarius without it not actually being there yet.
Another thing I’m noticing is that pluto – though intense – likes to ease its way into signs. It usually stops in a sign for a few months, then most of the year, then it starts its 20 year path. That’s what I’m seeing with Pluto – we will spend 80% of the year with Pluto in Aquarius.
Except, of course, September 18th and November 18th. You know. During an election year. Very good news.
[I will write about Pluto in Capricorn thoughts later as this is turning into a ramble, but with Pluto relating to power and Capricorn relating to power structures built – this literally manifesting into power in the corporations and money making interests – I think that will be a very interesting look at those last few months during the election. At this point, I have given up on electoral politics entirely, but! I wonder how that last hurrah in Pluto in Capricorn will feel after spending 80% of the year with the Power materializing into the People.]
Back to what I was saying. Pluto will not yet be at 17 degrees Aquarius for some time, but I can already see changes brewing within the internet sphere.
People are exhausted with the social media sites. The draw of them was to help connect with people you knew in a different, more meaningful way – different than the forums, ircs and Bbs of the time. This was back when anonymity was valued, your art getting posted everywhere meant you made it big, AND there was little financial incentive to tie yourself to your online identity.
I will not pretend I understood the original draw of all of the social medias – I can’t even fathom an inference. I mean, it seemed obvious facebook was about sharing memories and making friends, creating groups and talking to people. IG was about sharing pics quick. YouTube was about recording yourself with rudimentary software and Twitter was about talking about what you were up to.
What. The hell. Happened?
As Pluto has been dipping its toe into Aquarius, I have been seeing a lot more complaints about this. I predicted this, but let’s elaborate in a more meaningful way so that you’re able to apply this with you and your friends.
There’s a lot to think about when it comes to the way that we use the internet. I believe it was Summie who said that gifs used to be just gifs, but now they’re all advertisements in some way. Like a Fresh Prince gif used to be a Fresh Prince gif. But now, it’s a Fresh Prince gif along with Paramount+, so you create that mental connection instantly to know where you *could* watch it if for some reason this dancing image of carlton spurred you into that.
Reminds me of when I watched Fresh Prince on TBS and I noticed that everything was so much faster, and then a few years later there was a reddit post about how all syndicated shows on TBS are like, xyz faster to fit in more ads.
Speaking of GIFs, GIFs used to be artful. 256 colors or less, a beautiful dither. We did so much more with so much less, and I think that’s what I’m trying to get at here.
Of course, with time, things change. That’s what Pluto squares kinda examine if we’re looking at it from an as above, so below perspective. But I don’t think it’s ever been this, shitty…
So many apps have hired psychologists to pick the right colors, use the right hand movements to keep us hooked. The algorithms are trended towards whatever the user is most likely to interact with – good or bad. People are being rewarded for spreading misinformation, DISinformation. Almost all socials (idk about tungle) are feeding every bit of UGC into their own personal LLMs to create … chat bots. Connecting any of these accounts shares data between the socials, and enhances each consumer profile to sell to advertisers.
And don’t get me started about this app listening shit.
No, what’s really infuriating is the apps that intentionally get shittier and then force you to pay for shit you already had previously. The ones that are baiting you into feeling miserable. The bird app is unusable because you have to block 10 people a day, mute 5 words, and lock comments in order to get a semblance of peace. Like, why do I want to use an app that does that? Why do I want to feed into this garbage? Why do I want to constantly get trapped into this machine?
I think in 2024, we’re standing on business as far as understanding the types of stimuli we let ourselves engage with. I feel like this square is helping us understand how far we strayed away – and I believe that with the Aquarius aspect, we’re going back to our roots as far as the internet goes. I see reddit being hyped up, and every time I see it it’s because of its forum like aspects. We could just go to a forum.
I go on forums all the time still. I plan on running one in 2024. I can’t STAND discord (which also uses LLMs) … Skype was always horrible too. Voice chatting, hmmm… well we’ll have to think ab this entirely bc of how GenA/I is working with voices… hmmm…
I feel like Streaming will be big. Public Access is coming back – I feel like there’s a lot of Power to the People and Power to the Demagoguery ass shit going on. Independent music (no spotify/apple music), independent videos (youtube, other apps ARE coming out though. Could YouTube be unseated? In 20 years, YES.) Independent creativity. The problem will *seem* to be the lack of funding, but just like I said earlier – we can do so much, with so little.
But Public Access TV shows are coming. If you haven’t started your stream or your YouTube or whatever, you should! Right now!
We’re straying away from algorithm based trends and aspects and we’re rebuilding our muscles into seeking out the things we believe we will like. I’m going to go back on soundcloud and I’m handcrafting my music tastes again, no algorithms.
[Sorry, another rant: there was nothing worse than me listening to a song and thinking I’m the only one in the world listening to it, and then I would hear it on numerous coworkers spotify radios without our accounts ever interacting. Like I couldn’t even bop to the song. As an Aquarius Venus this is so serious to me.]
Another thing is – we’re going back to internet safety. Four years ago, I had a dream that I needed to change my passwords. I changed them all immediately and told all my friends to do so as well. I’m not sure what happened after – I guess I could look it up. But, that restarted my journey into caring about my digital hygiene. I think that’s a big word in 2024. Digital Hygiene.
But, one thing to watch out for? Tech accelerationism. I am not sure why people are so vested into the end of humanity as we know it. Why do people want to transcend humanity when we haven’t even begun to understand the different parts of ourselves yet? I feel like research into humans is still deeply in its infancy to give up on humanity and the earth like this.
I think for my last little piece, one thing I’ve noticed is that when Pluto goes into a Sign, the connotation of the sign changes RADICALLY from what it used to. I saw this in a tweet (I’ll edit this post with the tweet when I find it) where Capricorns used to be seen as broke and miserable but now they’re seen as money makers, methodical, etc.
Aquarius is seen as futuristic, nostalgic, technological. People and the self. In the book I use for most of my correspondences, The Rulership Book by Rex Bills, and Capricorn and Aquarius had the least amount of rulerships. I think it’s because the outers didn’t really touch either of these signs until the late 20th century, so there wasn’t a lot of things to reference besides the inner planet stuff.
Pluto is the last of the outers to complete this most recent Aquarius transit. I feel like during this time, we will be looking at tech accelerationism and pushing future nostalgia to its limits. As I come up with more theories, I’ll let you know, but I’m excited!
30 notes
·
View notes
Text
I have no jokes for you this morning.
S2E06.
We start off with a group of Spartan-IIIs engaged in a simulation training exercise to board and take down a Covenant ship.
We find out that it's a training simulation because they get pulled out of the dumb VR zoom call technology from last season (y'all remember that? I barely did) and Kai tells them how they fucked up and that they need to be more like a swarm of bees when they're in space to not get shot.
Insanely, one of these trainees is apparently Perez.
We also get a ton of these in-helmet face shots I hate.




While Halsey and the Gang have been busy on Aleria, Spartan-III is.... proceeding with a bunch of adults who survived Reach.
Apparently.
I feel like anyone reading this post has been here long enough to understand my annoyance without my efforts to belabor the point. Maybe I'll get agitated enough to make a whole post out of it later.

But this also feels like the kind of thing a writer does when they've heavily foreshadowed something (the Kessler subplot, whatever the fuck was up with Ackerson having a dead sister clone) but want to make you think you didn't see it coming, so I am expecting we are not out of the child soldier woods yet.
You know how it is.
The children yearn for the child soldier woods.
Anyway, there's a ~thing~ with her and Kai where Kai clearly doesn't like her and Kai's like "I don't have a problem with you I have a problem with failure" while Perez is all YOU'RE JUST MAD YOU WEREN'T THERE AT REACH.

Anyway there's this fucking amazing line after Perez says she "knows what she signed up for."

Then, we cut to Parangosky and Twinkerson having a conversation about ONI (sorry, THE ONI), tea, stories, and empire because of course.

But actually, the point of the conversation is that Parangosky has heard someone snuck a ship through their security protocols and landed nearby, and also she has heard from a source that Halsey is probably alive.
And was seen traveling with a huge scarred man on a ship of the same description.


God dammit, roll the title sequence.
I've survived the first 10 minutes without needing to spit 30 images at you so you can understand my anguish, so maybe things are looking up.
Sort of.
For now.
God I need to fucking know how bad the Spartan-IIIs actually are because this is already so stupid.
Luckily, Halo show is going to leave that Jimmy Rings teaser alone for now. Hop over to Kai and Ackerson.
Kai has been using the VR zoom call software to make herself more miserable about how she wasn't at the battle of Reach by simming herself there, and Ackerson is calling her out on it. She believes her whole team is dead and she's having a very bad time.


She is not confident about the Spartan-III trainees. She says they're not Spartans.

Ackerson is like lol well that's your problem, they are Spartans...

10/10 #1 best boss of the year award.
OKAY NOW we get to go see Halsey and the gang, who are of course on Onyx.



Halsey casually does not explain her plan. Kwan wanders off into the woods and starts hallucinating the spooky woman again while Soren and Jimmy talk about how Onyx is a ~mysterious planet~ with ONI history or something, and how Laera and Soren want to go find/rescue Kessler.

Kessler is somewhere in that building, they think.
Security forces show up and they fight armorless Jimmy in the snow in a scene that Paramount Halo probably thinks looks cool but I just thought looked very silly.

Kwan follows her vision and jumps down a well, which we find out has weird Forerunner Stuff at the bottom and Halsey is already there.



Halsey apparently used to work here 20 years ago.

The funniest thing about the sequence is she credits meeting Kwan specifically for how Jimmy Rings stopped behaving "like a Spartan," which feels super un-earned because of how quickly season 1 separated these characters and how little they ultimately actually seemed to mean to one another. Kwan is about as bewildered as I am with it.
Then, we have THE MOST HILARIOUS SEQUENCE IN THE SHOW TO ME SO FAR.
Okay.
Setting the stage for you.
Lovingly fighting with how tumblr won't let me upload two videos in one post.
Remember this cutscene with me, how they show us the Arbiter's punishment, how it feels to watch that.
youtube
Remember it? Love it? Good.
Here's what we get in Halo TV Show.
[EDIT: tumblr had its chance to host this but I think it thinks it's content matched, porn, or both. So. Youtube.]
youtube
The prosecution is wheezing. The prosecution rests.
(And by that I mean I should probably go eat something besides bad tv show for breakfast.)
19 notes
·
View notes
Text
who: an open starter to anyone interested!
what: SciPNET Login SetUp
Loch fancied he could be forgiven for having been the first in line for this. It was, perhaps, a bit of overkill to have arrived as quickly as he did when he heard exactly what this was, but the mere possibility of being able to touch a keyboard again was enough to push him to a level of punctuality he'd never before demonstrated. It was as exciting as the first time Nathan Drake realized he had the ability to survive the impossible. Survival was not, perhaps, Loch's strength, but adapting was and he was confident in his ability to jailbreak even this limited system into something more useful. Christ on a bike, he was excited about this.
Turning to the person with the (mis)fortune of standing behind him, Loch began asking the questions he considered to be of paramount importance. "So, have you worked with this system before? Is it pretty standard, like Linux or Windows? I've heard it's more like a search engine before. Have you heard if it's particularly intuitive or is it running off of like Windows 84-style bullshit? And, most importantly, how good is the WiFi? If it only works on WiFi, we'll need a halfway decent connection, unless someone's willing to get into the details of hardware, which I'm not. I'm more than happy to optimize the software, but actual hardware is so far beyond me, it makes a summer trip to Andromeda feel feasible."

11 notes
·
View notes
Text
Boosting Efficiency: The Role of ERP Software in Modern Manufacturing Operations
In today's fast-paced manufacturing landscape, efficiency is not just a desirable trait; it's a necessity. To stay competitive and meet the demands of the market, manufacturers must streamline their processes, optimize resource utilization, and enhance decision-making capabilities. This is where Enterprise Resource Planning (ERP) software steps in as a game-changer. In this article, we'll delve into the pivotal role of ERP systems in revolutionizing manufacturing operations, particularly in India's thriving industrial sector.

Understanding ERP for Manufacturing Industry
ERP systems for manufacturing are comprehensive software solutions designed to integrate and automate core business processes such as production planning, inventory management, supply chain logistics, financial management, and human resources. By consolidating data and operations into a unified platform, ERP empowers manufacturers with real-time insights, facilitates collaboration across departments, and enables informed decision-making.
Streamlining Operations with ERP Solutions
In the dynamic environment of manufacturing, where every minute counts, efficiency gains translate directly into cost savings and competitive advantages. ERP software for manufacturing offers a multitude of features that streamline operations and drive efficiency:
1. Enhanced Production Planning: ERP systems enable manufacturers to create accurate production schedules based on demand forecasts, resource availability, and production capacity. By optimizing production timelines and minimizing idle time, manufacturers can fulfill orders promptly and reduce lead times.
2. Inventory Management: Efficient inventory management is crucial for balancing supply and demand while minimizing holding costs. ERP software provides real-time visibility into inventory levels, automates reorder points, and facilitates inventory optimization to prevent stockouts and overstock situations.
3. Supply Chain Optimization: ERP solutions for manufacturing integrate supply chain processes from procurement to distribution, enabling seamless coordination with suppliers and distributors. By optimizing procurement cycles, minimizing transportation costs, and reducing lead times, manufacturers can enhance supply chain resilience and responsiveness.
4. Quality Control: Maintaining product quality is paramount in manufacturing to uphold brand reputation and customer satisfaction. ERP systems offer quality management modules that streamline inspection processes, track product defects, and facilitate corrective actions to ensure adherence to quality standards.
5. Financial Management: Effective financial management is essential for sustaining manufacturing operations and driving profitability. ERP software provides robust accounting modules that automate financial transactions, streamline budgeting and forecasting, and generate comprehensive financial reports for informed decision-making.
6. Human Resource Management: People are the cornerstone of manufacturing operations, and managing workforce efficiently is critical for productivity and employee satisfaction. ERP systems for manufacturing include HR modules that automate payroll processing, manage employee records, and facilitate workforce planning to align staffing levels with production demands.
The Advantages of ERP for Manufacturing Companies in India
India's manufacturing sector is undergoing rapid transformation, fueled by factors such as government initiatives like "Make in India," technological advancements, and globalization. In this dynamic landscape, ERP software plays a pivotal role in empowering manufacturing companies to thrive and remain competitive:
1. Scalability: ERP solutions for manufacturing are scalable, making them suitable for companies of all sizes – from small and medium enterprises (SMEs) to large conglomerates. Whether a company is expanding its operations or diversifying its product portfolio, ERP systems can adapt to evolving business needs and support growth.
2. Compliance: Regulatory compliance is a significant concern for manufacturing companies in India, given the complex regulatory environment. ERP software incorporates compliance features that ensure adherence to industry regulations, tax laws, and reporting requirements, minimizing the risk of non-compliance penalties.
3. Localization: ERP vendors catering to the Indian manufacturing sector offer localized solutions tailored to the unique requirements of the Indian market. From multi-currency support to GST compliance features, these ERP systems are equipped with functionalities that address the specific challenges faced by Indian manufacturers.
4. Cost Efficiency: Implementing ERP software for manufacturing entails upfront investment, but the long-term benefits far outweigh the costs. By streamlining processes, optimizing resource utilization, and reducing operational inefficiencies, ERP systems drive cost savings and improve overall profitability.
5. Competitive Edge: In a fiercely competitive market, manufacturing companies in India must differentiate themselves through operational excellence and agility. ERP software equips companies with the tools and insights needed to outperform competitors, adapt to market dynamics, and capitalize on emerging opportunities.
Choosing the Right ERP Software for Manufacturing
Selecting the right ERP solution is crucial for maximizing the benefits and ensuring a smooth implementation process. When evaluating ERP software for manufacturing, companies should consider the following factors:
1. Industry-specific functionality: Choose an ERP system that offers industry-specific features and functionalities tailored to the unique requirements of manufacturing operations.
2. Scalability and flexibility: Ensure that the ERP software can scale with your business and accommodate future growth and expansion.
3. Ease of integration: Look for ERP systems that seamlessly integrate with existing software applications, such as CRM systems, MES solutions, and IoT devices, to create a cohesive technology ecosystem.
4. User-friendliness: A user-friendly interface and intuitive navigation are essential for ensuring widespread adoption and maximizing user productivity.
5. Vendor support and expertise: Select a reputable ERP vendor with a proven track record of success in the manufacturing industry and robust customer support services.
Conclusion
In conclusion, ERP software has emerged as a cornerstone of modern manufacturing operations, empowering companies to enhance efficiency, drive growth, and maintain a competitive edge in the global market. For manufacturing companies in India, where agility, scalability, and compliance are paramount, implementing the right ERP solution can be a transformative investment that paves the way for sustainable success. By harnessing the power of ERP, manufacturers can optimize processes, streamline operations, and unlock new opportunities for innovation and growth in the dynamic landscape of the manufacturing industry.
#ERP software providers in India#Manufacturing enterprise resource planning#ERP systems for manufacturing companies#ERP system for manufacturing industry#ERP for manufacturing companies#ERP software for engineering company#ERP software for engineering companies in India#ERP software for engineering companies in Mumbai#ERP solution providers in India#ERP for manufacturing industry#ERP systems for manufacturing#ERP solutions for manufacturing#ERP software manufacturing industry#ERP for manufacturing company in India#India
7 notes
·
View notes
Text
What Future Trends in Software Engineering Can Be Shaped by C++
The direction of innovation and advancement in the broad field of software engineering is greatly impacted by programming languages. C++ is a well-known programming language that is very efficient, versatile, and has excellent performance. In terms of the future, C++ will have a significant influence on software engineering, setting trends and encouraging innovation in a variety of fields.
In this blog, we'll look at three key areas where the shift to a dynamic future could be led by C++ developers.
1. High-Performance Computing (HPC) & Parallel Processing
Driving Scalability with Multithreading
Within high-performance computing (HPC), where managing large datasets and executing intricate algorithms in real time are critical tasks, C++ is still an essential tool. The fact that C++ supports multithreading and parallelism is becoming more and more important as parallel processing-oriented designs, like multicore CPUs and GPUs, become more commonplace.
Multithreading with C++
At the core of C++ lies robust support for multithreading, empowering developers to harness the full potential of modern hardware architectures. C++ developers adept in crafting multithreaded applications can architect scalable systems capable of efficiently tackling computationally intensive tasks.

C++ Empowering HPC Solutions
Developers may redefine efficiency and performance benchmarks in a variety of disciplines, from AI inference to financial modeling, by forging HPC solutions with C++ as their toolkit. Through the exploitation of C++'s low-level control and optimization tools, engineers are able to optimize hardware consumption and algorithmic efficiency while pushing the limits of processing capacity.
2. Embedded Systems & IoT
Real-Time Responsiveness Enabled
An ability to evaluate data and perform operations with low latency is required due to the widespread use of embedded systems, particularly in the quickly developing Internet of Things (IoT). With its special combination of system-level control, portability, and performance, C++ becomes the language of choice.
C++ for Embedded Development
C++ is well known for its near-to-hardware capabilities and effective memory management, which enable developers to create firmware and software that meet the demanding requirements of environments with limited resources and real-time responsiveness. C++ guarantees efficiency and dependability at all levels, whether powering autonomous cars or smart devices.
Securing IoT with C++
In the intricate web of IoT ecosystems, security is paramount. C++ emerges as a robust option, boasting strong type checking and emphasis on memory protection. By leveraging C++'s features, developers can fortify IoT devices against potential vulnerabilities, ensuring the integrity and safety of connected systems.
3. Gaming & VR Development
Pushing Immersive Experience Boundaries
In the dynamic domains of game development and virtual reality (VR), where performance and realism reign supreme, C++ remains the cornerstone. With its unparalleled speed and efficiency, C++ empowers developers to craft immersive worlds and captivating experiences that redefine the boundaries of reality.
Redefining VR Realities with C++
When it comes to virtual reality, where user immersion is crucial, C++ is essential for producing smooth experiences that take users to other worlds. The effectiveness of C++ is crucial for preserving high frame rates and preventing motion sickness, guaranteeing users a fluid and engaging VR experience across a range of applications.

C++ in Gaming Engines
C++ is used by top game engines like Unreal Engine and Unity because of its speed and versatility, which lets programmers build visually amazing graphics and seamless gameplay. Game developers can achieve previously unattainable levels of inventiveness and produce gaming experiences that are unmatched by utilizing C++'s capabilities.
Conclusion
In conclusion, there is no denying C++'s ongoing significance as we go forward in the field of software engineering. C++ is the trend-setter and innovator in a variety of fields, including embedded devices, game development, and high-performance computing. C++ engineers emerge as the vanguards of technological growth, creating a world where possibilities are endless and invention has no boundaries because of its unmatched combination of performance, versatility, and control.
FAQs about Future Trends in Software Engineering Shaped by C++
How does C++ contribute to future trends in software engineering?
C++ remains foundational in software development, influencing trends like high-performance computing, game development, and system programming due to its efficiency and versatility.
Is C++ still relevant in modern software engineering practices?
Absolutely! C++ continues to be a cornerstone language, powering critical systems, frameworks, and applications across various industries, ensuring robustness and performance.
What advancements can we expect in C++ to shape future software engineering trends?
Future C++ developments may focus on enhancing parallel computing capabilities, improving interoperability with other languages, and optimizing for emerging hardware architectures, paving the way for cutting-edge software innovations.
9 notes
·
View notes
Note
This is more of a technical question, but what version of C++ is most used in AAA nowadays? Is it still very much C++11/14 or has it transitioned to C++17/20?
It's a pretty broad mix. Most devs are still using C++11/14 to my knowledge, with several ongoing legacy titles continuing to use C++03 to support them.

One of the biggest pillars of development is that the ability for devs to work (stability) is paramount. If we were to make a change like an engine or software upgrade (e.g. Unreal 4 to Unreal 5), a major tool switch (e.g. Max to Blender), or a C++ version (e.g. C++11 to C++17), we will render a large number of developers temporarily unable to work. This is because most upgrades or switches no longer support the things the previous software or version supported perfectly, and those small breakages require time to identify and time to fix - during which those devs who depend on that software to work can't.

This kind of time cost eats a portion of the budget - we won't get extra dev time added because we're upgrading our tools and need time to iron the resulting issues out. This is why the decision has to be made - are the benefits from making the switch worth the cost of fielding all of the issues that could be caused by it? This varies on a project-by-project basis. If the project is early in development or only has a small number of affected developers, the cost is much lower than if there are hundreds of devs affected or thousands of finished assets that could be affected.

Live games, especially old established live games, only make these kind of changes when absolutely necessary because they have tons of existing resources and assets already live and can't sacrifice the dev time to go back and bring them all up to spec. Many well-established MMOGs are still using C++03 for this reason - they just have too much built on it and can't afford the change. SWTOR is still using the licensed Hero engine and are still using the build from 2012.
[Join us on Discord] and/or [Support us on Patreon]
Got a burning question you want answered?
Short questions: Ask a Game Dev on Twitter
Long questions: Ask a Game Dev on Tumblr
Frequent Questions: The FAQ
24 notes
·
View notes
Text
Effective B2B Contact Management: Unveiling Strategies to Harness B2B Database Leads and Elevate Sales Growth

In the ever-evolving landscape of B2B sales and marketing, the art of effective B2B contact management emerges as a critical force shaping success. This comprehensive guide delves into the intricate pathways of nurturing robust relationships, optimizing communication, and propelling substantial business growth. At the heart of this strategic journey lies the meticulously organized B2B contact database – a powerhouse for precision B2B lead generation, strategic sales leads, and amplified business development. This illuminating article embarks on a deep exploration of the core strategies that unveil the true potential of B2B databases, catalyzing a transformation from mere data reservoirs into dynamic engines driving precision and growth.
DOWNLOAD THE INFOGRAPHIC HERE
Defining a Clear Database Structure
Central to unlocking the potential of effective B2B contact management is the establishment of a crystal-clear database structure. This architectural marvel sets the stage for targeted B2B lead generation and strategic sales leads, akin to creating a roadmap for successful business development. Contacts are carefully categorized based on pertinent criteria – industry, company size, job titles, and geographic location. The creation of separate fields for pivotal contact details, encompassing names, email addresses, phone numbers, and company information, facilitates a streamlined approach for accessing crucial data. This structured foundation becomes the epicenter from which personalized B2B sales prospects are cultivated and business development thrives.
Regular Data Cleansing and Updates
Much like tending to a thriving garden, maintaining an accurate B2B contact database involves nurturing and pruning. Through consistent data cleansing practices, redundancies are eradicated, errors are rectified, and outdated information is supplanted. This meticulous process not only sharpens the efficacy of B2B lead generation but fortifies the database's integrity. The adoption of data cleansing tools or the strategic outsourcing of this task ensures the accuracy and dependability of sales leads. A refined database lays the groundwork for triumphant B2B sales endeavors.
Implementing a Centralized Database System
Efficiency and organization take center stage in the modern business ecosystem, and the implementation of a centralized database system or customer relationship management (CRM) software exemplifies this ethos. This unified platform serves as the nucleus for storing contact information, tracking interactions, and orchestrating seamless communication. A judicious selection of a system tailored to organizational requirements, boasting features such as customizable fields, tagging, and segmentation, transforms B2B lead generation and sales leads into actionable insights. This integration amplifies the potency of business development initiatives.
Segmenting Contacts for Targeted Outreach
In the dynamic realm of B2B interactions, precision is paramount. Enter the realm of contact segmentation – the art of categorizing contacts based on specific criteria that enrich B2B lead generation efforts. By grouping contacts according to industry, job roles, interests, or engagement levels, the potency of personalized outreach escalates. Each interaction becomes a personalized symphony, every correspondence speaks directly to the recipient's needs. This strategic approach metamorphoses sales leads into symbiotic partnerships, heralding a new era in business development.
youtube
Integrating the Database with Other Tools
The essence of modern business lies in interconnectedness. The harmonious integration of your B2B contact database with other tools and systems encapsulates this ethos. Picture seamless fusion with email marketing platforms, sales automation tools, and customer support systems – this synergy propels the fluid flow of data, automates repetitive tasks, and nurtures cross-functional collaboration. The integration augments B2B lead generation, amplifies business development, and charts a transformative course for your database's evolution into a hub of productivity.
Implementing Data Security Measures
In a landscape defined by digital interconnectedness, safeguarding data is paramount. Robust data security measures form an impervious barrier around the B2B contact information. Enforcing stringent password policies, limiting access to authorized personnel, and maintaining regular backups fortify defenses against potential breaches. Staying vigilant regarding data privacy regulations is a testament to your commitment to maintaining trust with B2B sales leads and partners.
Providing Training and Documentation
Empowerment extends beyond technology, encompassing adept handling of the contact management system by your team. Comprehensive training ensures flawless data entry, accurate updates, and optimal utilization of database features. In tandem, detailed documentation fosters a culture of effective database management, augmenting the value of B2B lead generation and sales prospects. As proficiency spreads, every interaction becomes an opportunity, every engagement a step towards nurturing enduring partnerships.
In summation, the art of effective B2B contact management strategies stands as the linchpin of impactful B2B lead generation, strategic sales leads, and business development. From structuring your database meticulously to integrating advanced tools such as AccountSend, each component harmonizes in a symphony of success. By embracing these strategies, you orchestrate growth, cultivate relationships, and pave a path toward enduring success in a competitive landscape. Embark on this enlightening journey, revolutionize your B2B endeavors, and witness your contact database morph into an instrumental asset fueling triumphant B2B lead generation, strategic sales prospects, and exponential growth.
#B2BLeadGeneration#B2B#LeadGeneration#B2BSales#SalesLeads#B2BDatabases#BusinessDevelopment#SalesFunnel#AccountSend#SalesProspecting#BusinessOwner#Youtube
17 notes
·
View notes
Text
Professional Website Hosting and Management Services
In today’s digital age, having a strong online presence is crucial for any business or organization. A well-designed website serves as a virtual storefront, allowing you to reach a global audience and showcase your products, services, or ideas. However, creating and maintaining a website requires technical expertise, time, and resources that not everyone possesses. That’s where professional website hosting and management services come into play.

What is Website Hosting?
Website hosting refers to the process of storing your website files on a server that is connected to the internet. When someone types your website’s domain name into their browser, their device connects to the server, retrieves the website files, and displays the webpages. Website hosting is a critical component of your online presence, as it ensures your website is accessible to visitors at all times.
The Benefits of Professional Website Hosting and Management Services
While it is possible to host a website on your own, opting for professional website hosting and management services offers numerous advantages. Let’s explore some of the key benefits:
1. Reliability and Uptime:
Professional hosting providers offer reliable and secure servers, ensuring that your website is accessible to visitors around the clock. They have redundant systems in place to minimize downtime and address any technical issues promptly. This ensures a seamless browsing experience for your users, enhancing their trust and satisfaction.
2. Technical Support:
Managing a website involves dealing with technical challenges such as server configuration, software updates, and security patches. With professional hosting services, you have access to a dedicated support team that can assist you with any technical issues that arise. This allows you to focus on your core business activities while leaving the technical aspects to the experts.
3. Scalability:
As your business grows, so does the traffic to your website. Professional hosting providers offer scalable solutions that can accommodate increased traffic and ensure optimal performance. They have the infrastructure and resources to handle high volumes of visitors, preventing your website from becoming slow or unresponsive.
4. Enhanced Security:
Website security is of paramount importance, especially in an era of increasing cyber threats. Professional hosting services implement robust security measures, including firewalls, malware scanning, and regular backups, to protect your website and its data. They stay updated with the latest security protocols and continuously monitor for any potential vulnerabilities.
5. Additional Services:
Many professional hosting providers offer a range of additional services to enhance your website’s functionality and performance. These may include content delivery networks (CDNs) to improve page load speeds, SSL certificates for secure data transmission, and automatic backups to safeguard your data in case of unforeseen events.
Choosing the Right Professional Hosting Provider
With numerous hosting providers available, selecting the right one for your specific needs can be daunting. Here are some factors to consider when choosing a professional hosting provider:
1. Reliability and Uptime Guarantee:
Ensure that the hosting provider has a proven track record of reliability and offers an uptime guarantee of at least 99%. You don’t want your website to be inaccessible due to server issues or maintenance downtime.
2. Scalability Options:
Consider the scalability options offered by the hosting provider. Can they accommodate your website’s growth and handle sudden traffic spikes? A flexible hosting solution is crucial to ensure your website performs well under varying loads.
3. Security Measures:
Check the security measures implemented by the hosting provider. Are they proactive in addressing security threats? Do they offer SSL certificates, regular backups, and malware scanning? Robust security measures are essential to protect your website and sensitive data.
4. Technical Support:
Ensure that the hosting provider offers reliable and responsive technical support. Look for providers that offer 24/7 support through various channels like live chat, email, or phone. Quick assistance during emergencies can save you valuable time and prevent potential losses.
5. Pricing and Value for Money:
While cost shouldn’t be the sole deciding factor, it’s important to compare pricing plans and determine the value for money offered by different hosting providers. Consider the features, performance, and support you receive for the price you pay.
Conclusion
Professional website hosting and management services provide businesses and organizations with a reliable, secure, and scalable online infrastructure. By outsourcing the technical aspects of website management, you can focus on your core activities while ensuring an optimal user experience for your website visitors. Choosing the right hosting provider is crucial to unlock the benefits of professional website hosting and maximize your online presence.
Investing in professional hosting services is a wise decision for any business or organization that values their online presence. It allows you to leverage the expertise and infrastructure of a dedicated team while ensuring your website remains accessible, secure, and performs at its best. Don’t underestimate the impact that a well-hosted and managed website can have on your brand, customer satisfaction, and business success.

Source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
22 notes
·
View notes
Text
Safeguarding your digital world: fundamental rules of information security
In today's interconnected and digitized world, ensuring the security of your information is paramount. Whether you're an individual user or a business owner, understanding and implementing basic rules of information security can protect you from cyber threats. Here are some fundamental principles to keep in mind.

Strong passwords. The foundation of any secure digital presence begins with strong passwords. Use a combination of upper and lower case letters, numbers, and special characters. Avoid easily guessable information, such as birthdays or names.
Update regularly. Keep your software, operating systems, and applications up to date. Developers release updates to fix security vulnerabilities, and by updating regularly, you ensure that your digital environment is equipped with the latest defenses.
Two-factor authentication (2FA). Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of identification, such as a code sent to your mobile device, in addition to your password.
Be wary of phishing. Phishing attacks often involve emails or messages that appear legitimate, tricking users into revealing sensitive information. Be cautious of unexpected emails, especially those requesting personal information or clicking on suspicious links.
Secure your devices. Whether it's a computer, smartphone, or tablet, secure your devices with passwords or biometric authentication. Encrypt sensitive data and enable remote tracking and wiping features in case your device is lost or stolen.
Regular backups. Create regular backups of important data. In the event of a cyber attack, having a recent backup ensures that you can recover your information without succumbing to ransom demands.
Limit access. Restrict access to sensitive information. Only grant access to those who need it, and regularly review and update permissions. This principle is crucial for both personal and organizational security.
Educate and train. Stay informed about the latest cyber threats and educate those around you. Regularly train employees on security best practices within organizations to create a culture of awareness and responsibility.
Use secure networks. Avoid using public Wi-Fi for sensitive transactions. If you must use public networks, consider using a virtual private network (VPN) to encrypt your connection and protect your data.
Monitor accounts. Regularly review your financial and online accounts for any suspicious activity. Early detection can prevent significant damage in case of a security breach.
16 notes
·
View notes
Text
Navigating DevOps: Unveiling the Pros and Cons of a Transformative Approach
DevOps, a portmanteau of "development" and "operations," has revolutionized the software development and IT operations landscape. This approach seeks to bridge the gap between traditionally siloed development and operations teams, fostering collaboration and efficiency. Like any methodology, DevOps comes with its own set of advantages and challenges. In this comprehensive exploration, we'll delve into the pros and cons of DevOps. We'll dissect how it leads to faster software delivery, improved collaboration, enhanced efficiency, better quality, and heightened security, while also acknowledging the initial investment, cultural resistance, complexity, potential security concerns, and the need for continuous learning.

Pros and Cons of DevOps:
Pros of DevOps:
Faster Delivery: DevOps is synonymous with speed. It streamlines the software development and deployment process, allowing organizations to release updates, new features, and fixes at an accelerated pace. This rapid delivery cycle is a game-changer in a world where agility and responsiveness to market demands are paramount.
Improved Collaboration: A core principle of DevOps is breaking down the traditional barriers between development and operations teams. By fostering better communication, collaboration, and shared responsibility, DevOps creates a culture of working together towards common goals. This alignment helps in eliminating the finger-pointing and blame games often seen in more traditional approaches.
Greater Efficiency: Automation is one of the cornerstones of DevOps. It automates repetitive and time-consuming tasks, such as code integration, testing, and deployment. This not only reduces manual errors but also results in quicker issue identification and resolution. Tasks that once took hours or days can now be accomplished in minutes.
Enhanced Quality: Continuous integration and continuous testing are fundamental practices in DevOps. These processes ensure that code is consistently tested as it's integrated into the shared repository. The result is higher-quality software with fewer defects, reducing the chances of post-release issues that can be costly and time-consuming to address.
Better Security: Security is a paramount concern in today's digital landscape. DevOps doesn't compromise on security; it integrates it into every phase of the development and deployment process. Continuous monitoring, automated compliance checks, and quick response to potential vulnerabilities are part of the DevOps culture. This proactive approach results in a more secure environment for software deployment.

Cons of DevOps:
Initial Investment: Implementing DevOps can require a significant upfront investment in tools, training, and cultural change. While the long-term benefits are substantial, some organizations may hesitate due to the initial cost associated with adopting DevOps practices.
Resistance to Change: Shifting to a DevOps culture isn't just about tools and processes; it's a cultural change. Some team members may resist this shift towards collaboration, automation, and shared responsibility. Overcoming cultural resistance and ensuring that everyone is on board can be a challenging aspect of adopting DevOps.
Complexity: Managing the various tools and processes in a DevOps pipeline can become complex. It necessitates expertise in different areas, including version control, continuous integration, continuous delivery, automation, and monitoring. Managing this complexity and ensuring that all components work seamlessly can be a formidable task.
Security Concerns: The rapid deployment facilitated by DevOps can lead to security oversights if not managed correctly. Continuous delivery requires rigorous security practices to ensure that vulnerabilities are not introduced into the system. Organizations must strike a balance between speed and security to avoid potential breaches and data leaks.
Continuous Learning: The world of DevOps is ever-evolving. New tools, best practices, and approaches emerge regularly. Staying up to date and continuously learning is not just an option; it's a necessity in the DevOps world. Professionals need to invest time in learning and adapting to new tools and practices to remain competitive.
DevOps is a transformative approach that offers numerous benefits, such as faster delivery, enhanced collaboration, efficiency, quality, and security. However, it's essential to be aware of the potential challenges, including an initial investment and the need for continuous learning. With the right training and support, professionals can harness the full potential of DevOps and navigate its complexities. ACTE Technologies is a trusted partner in this DevOps training journey, providing the knowledge and skills needed to excel in the dynamic realm of DevOps.
8 notes
·
View notes