#McAfee login portal
Text
mcafee account login
A Mcafee account gives information on the purchased antivirus software in the web account portal. Access the Mcafee account by using Mcafee login.
mcafee account login

0 notes
Text
MCAFEE SIGN IN
How do I log into my Mcafee account?
Mcafee Login
Every Mcafee user can log into their account after creating the same. A Mcafee account gives information on the purchased antivirus software in the web account portal. This account helps the user to understand the subscription timeline of each Mcafee product purchased by them. Hence, a Mcafee account has been a very crucial element in terms of its importance. Access the Mcafee account by using the Mcafee login portal/page. To log into a Mcafee account, follow the steps given below:
Launch a web browser and head towards the Mcafee login portal.
In the Mcafee login portal, enter the user's login credentials like the registered email address and password given during the time of Mcafee account creation.
If there is an issue with the login process, opt for "Forgot Your Password?" or "Forgot Your Email Address?"
A user can also log in from their smartphone by downloading the Mcafee antivirus software's mobile application. However, the respective smartphone or device must get registered with the Mcafee account.
How to Create a New Mcafee Account
Creating a new Mcafee account can never be a haunting work. Mcafee has a hassle-free set of steps to make an account or register with Mcafee. To create a Mcafee web account, perform the given set of directives mentioned below:

Power up the computer or laptop and wait for the time booting completes. When the desktop loads on the screen, double-click on the application icon of the web browser.
Once the web browser opens, go to the Mcafee login portal.
Click on the "Register Now" option present on the right side of the web page.
Next, enter the details like first name, last name, email address, and password. Give the password again to complete the entire account creation process.
Read the Mcafee end-user license agreement (EULA) by clicking on its link present just above the "I Agree" button.
After the terms and clauses present in the Mcafee license agreement, hit the "I Agree" button.
How to Change the Mcafee Account Password
Remembering the password of multiple accounts can be cumbersome. Hence, there may arise an instance when the user forgets the Mcafee login credentials, especially the password linked to their Mcafee web account. But, Mcafee offers easy solutions to resolve the same. To change the password, implement the mentioned below tasks chronologically:

Start a web browser application and enter the link for the Mcafee login page.
In the login portal, click on the "Forgot Your Password?" option.
Next, enter the registered email address related to the Mcafee web account.
Then, hit the Send Email tab on the pop-up message.
Now, login to the email account and check for the Mcafee support team's email to reset the password.
Click on the reset password link provided by the Mcafee support team and enter the same in the Mcafee reset password webpage. The password then gets updated.
Mcafee Auto-Renewal Service
Every Mcafee product and its related services have a fixed timeline between which a user can use the same. Once the subscription time is over, the user needs to renew the same to continue their digital protection. Hence, to not have any discontinuity, Mcafee comes with an auto-renewal policy. This auto-renewal policy lets the Mcafee team send alerts and notifications. To trigger the auto-renewal options, follow the steps given below:
Head towards the Mcafee login page by entering the relevant URL on the web browser application window's address bar section.
Enter the user's Mcafee login credentials. After the successful login attempt, go to the My Account section.
Next, tap on the Auto-Renewal tab and check the Uninterrupted protection.
Then, hit the toggle bar present adjacent to the Mcafee auto-renewal option after reading the Mcafee auto-renewal policy thoroughly.
Click on the "Agree & Opt-in" option.
1 note
·
View note
Text
Mcafee Login Portal | McAfee Login Account | McAfee security login
McAfee login portal is the best portal to protect your devices from fast growing online threats. We provide all support related to McAfee login portal and help to ease your work. We provide you with our 24/7 toll free customer support number to get your doubts clear regarding McAfee login portal. You can even visit our website www.mcafeepro.com to get more information and can self help to access the McAfee Login Portal.
0 notes
Photo
McAfee Security Login | McAfee Login Portal | McAfeePro
McAfee Security offers extensive security protection in order to concentrate on running your business without worrying if the computers or data of your employees are at risk. We support you to enroll for McAfee Security Login. Guide you to get a flexible licence for multiple devices protection. We ensure your data and device to be safe and secure. For more information please visit our website www.mcafeepro.com for call our 24/7 customer support number.
0 notes
Link
A Mcafee login account is required for downloading, installing, and activating any Mcafee product. You can log in to your Mcafee user account via the Mcafee login portal. By accessing your Mcafee account, you can upgrade your subscription plans, change passwords, add new devices, and much more.
0 notes
Link
Visit the McAfee login portal to sign in to your account and enjoy premium security for all your devices. Sign up for a McAfee account today.
0 notes
Text
"How we're tackling evolving online threats"
Major events like elections and COVID-19 present opportunities for threat actors, and Google’s Threat Analysis Group (TAG) is working to thwart these threats and protect our products and the people using them. As we head into the U.S. election, we wanted to share an update on what we’re seeing and how threat actors are changing their tactics.
What we’re seeing around the U.S. elections
In June, we announced that we saw phishing attempts against the personal email accounts of staffers on the Biden and Trump campaigns by Chinese and Iranian APTs (Advanced Persistent Threats) respectively. We haven’t seen any evidence of such attempts being successful.
The Iranian attacker group (APT35) and the Chinese attacker group (APT31) targeted campaign staffers’ personal emails with credential phishing emails and emails containing tracking links. As part of our wider tracking of APT31 activity, we've also seen them deploy targeted malware campaigns.
One APT31 campaign was based on emailing links that would ultimately download malware hosted on GitHub. The malware was a python-based implant using Dropbox for command and control. It would allow the attacker to upload and download files as well as execute arbitrary commands. Every malicious piece of this attack was hosted on legitimate services, making it harder for defenders to rely on network signals for detection.
In one example, attackers impersonated McAfee. The targets would be prompted to install a legitimate version of McAfee anti-virus software from GitHub, while malware was simultaneously silently installed to the system.
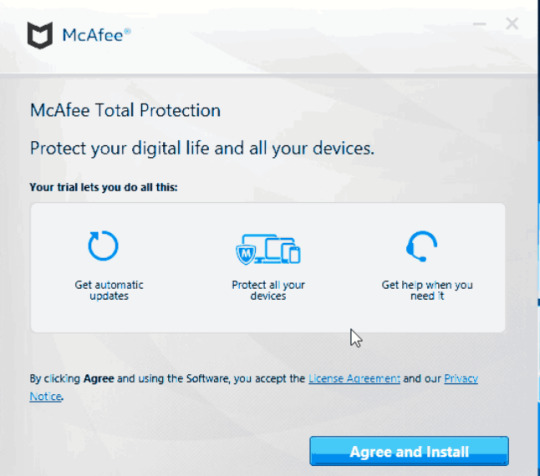
Example prompt from an APT31 campaign impersonating McAfee
When we detect that a user is the target of a government-backed attack, we send them a prominent warning. In these cases, we also shared our findings with the campaigns and the Federal Bureau of Investigation. This targeting is consistent with what others have subsequently reported.
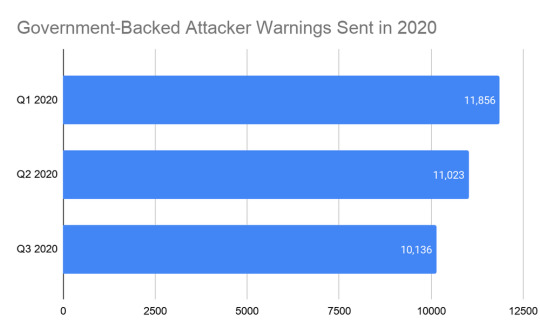
Number of “government backed attacker” warnings sent in 2020
Overall, we’ve seen increased attention on the threats posed by APTs in the context of the U.S. election. U.S government agencies have warned about different threat actors, and we’ve worked closely with those agencies and others in the tech industry to share leads and intelligence about what we’re seeing across the ecosystem. This has resulted in action on our platforms, as well as others. Shortly after the U.S. Treasury sanctioned Ukrainian Parliament member Andrii Derkach for attempting to influence the U.S. electoral process, we removed 14 Google accounts that were linked to him.
Coordinated influence operations
We’ve been sharing actions against coordinated influence operations in our quarterly TAG bulletin (check out our Q1, Q2 and Q3 updates). To date, TAG has not identified any significant coordinated influence campaigns targeting, or attempting to influence, U.S. voters on our platforms.
Since last summer, TAG has tracked a large spam network linked to China attempting to run an influence operation, primarily on YouTube. This network has a presence across multiple platforms, and acts by primarily acquiring or hijacking existing accounts and posting spammy content in Mandarin such as videos of animals, music, food, plants, sports, and games. A small fraction of these spam channels will then post videos about current events. Such videos frequently feature clumsy translations and computer-generated voices. Researchers at Graphika and FireEye have detailed how this network behaves—including its shift from posting content in Mandarin about issues related to Hong Kong and China’s response to COVID-19, to including a small subset of content in English and Mandarin about current events in the U.S. (such as protests around racial justice, the wildfires on the West Coast, and the U.S. response to COVID-19).
We’ve taken an aggressive approach to identifying and removing content from this network—for example, in Q3 alone, our Trust and Safety teams terminated more than 3,000 YouTube channels. As a result, this network hasn’t been able to build an audience. Most of the videos we identify have fewer than 10 views, and most of these views appear to come from related spam accounts rather than actual users. So while this network has posted frequently, the majority of this content is spam and we haven’t seen it effectively reach an actual audience on YouTube. We’ve shared our findings on this network in our Q2 and Q3 TAG bulletins and will continue to update there.
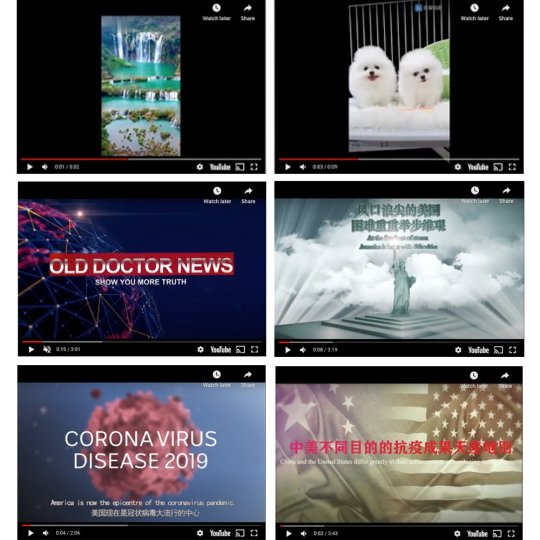
Examples of YouTube videos removed
New COVID-19 targets
As the course of the COVID-19 pandemic evolves, we’ve seen threat actors evolve their tactics as well. In previous posts, we discussed targeting of health organizations as well as attacker efforts to impersonate the World Health Organization. This summer, we and others observed threat actors from China, Russia and Iran targeting pharmaceutical companies and researchers involved in vaccine development efforts.
In September, we started to see multiple North Korea groups shifting their targeting towards COVID-19 researchers and pharmaceutical companies, including those based in South Korea. One campaign used URL shorteners and impersonated the target’s webmail portal in an attempt to harvest email credentials. In a separate campaign, attackers posed as recruiting professionals to lure targets into downloading malware.
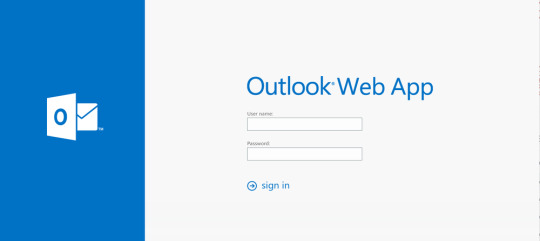
Spoofed Outlook login panel used by North Korean attackers attempting to harvest credentials
Tackling DDoS attacks as an industry
In the threat actor toolkit, different types of attacks are used for different purposes: Phishing campaigns can be used like a scalpel—targeting specific groups or individuals with personalized lures that are more likely to trick them into taking action (like clicking on a malware link), while DDoS attacks are more like a hatchet—disrupting or blocking a site or a service entirely. While it’s less common to see DDoS attacks rather than phishing or hacking campaigns coming from government-backed threat groups, we’ve seen bigger players increase their capabilities in launching large-scale attacks in recent years. For example in 2017, our Security Reliability Engineering team measured a record-breaking UDP amplification attack sourced out of several Chinese ISPs (ASNs 4134, 4837, 58453, and 9394), which remains the largest bandwidth attack of which we are aware.
Addressing state-sponsored DDoS attacks requires a coordinated response from the internet community, and we work with others to identify and dismantle infrastructure used to conduct attacks. Going forward, we’ll also use this blog to report attribution and activity we see in this space from state-backed actors when we can do so with a high degree of confidence and in a way that doesn’t disclose information to malicious actors.
Source : The Official Google Blog
via Source information
0 notes